Game Theory-Based Authentication Framework to Secure Internet of Vehicles with Blockchain
Abstract
:1. Introduction
1.1. Problem Statement
1.2. Motivation
- For better authentication efficiency and to reduce communication time, we have proposed blockchain-enabled RSUs that aid authorization by shifting the majority of the burden to the RSUs.
- Our method uses only a few cryptographic techniques, such as hash operations, XOR operations, and “pseudo-random” numbers, to reduce the amount of time the authentication framework needs to spend computing.
- The multi-trusted authorities network model that has been proposed in our framework is more realistic. Blockchain technology allows all trusted authorities in our framework to use the same ledger to record vehicle information, which not only enables the cross-trusted authority’s authentication but also improves its efficiency.
- The proposed framework proposes layer 1 vehicles powered with PUFs to provide lower level authentication via challenge response pair gaming technique, as well as layer 2 and layer 3 authentications via the duel game technique [18]. Hence, providing end-to-end authentication.
1.3. Organization of Paper
2. Literature Review
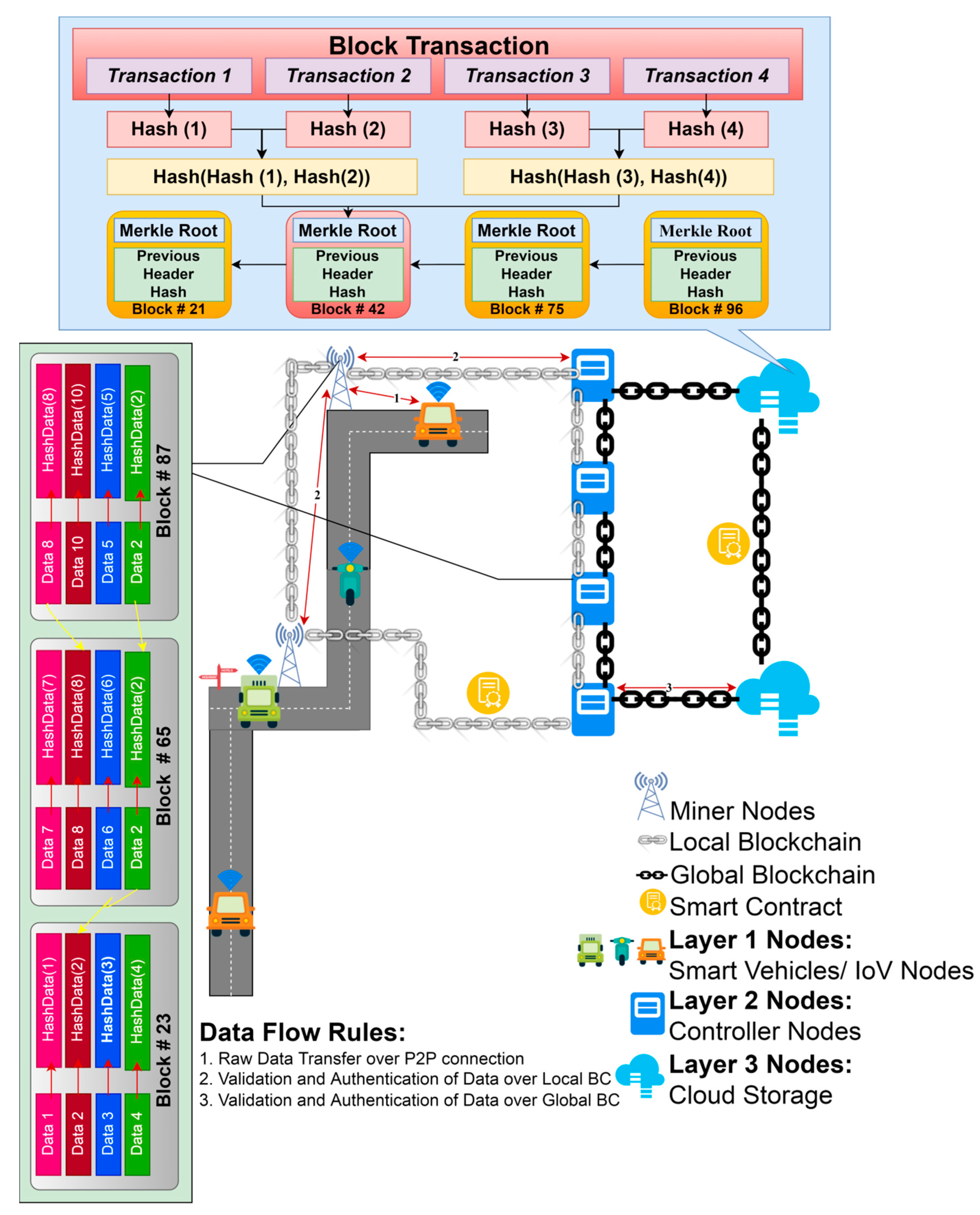
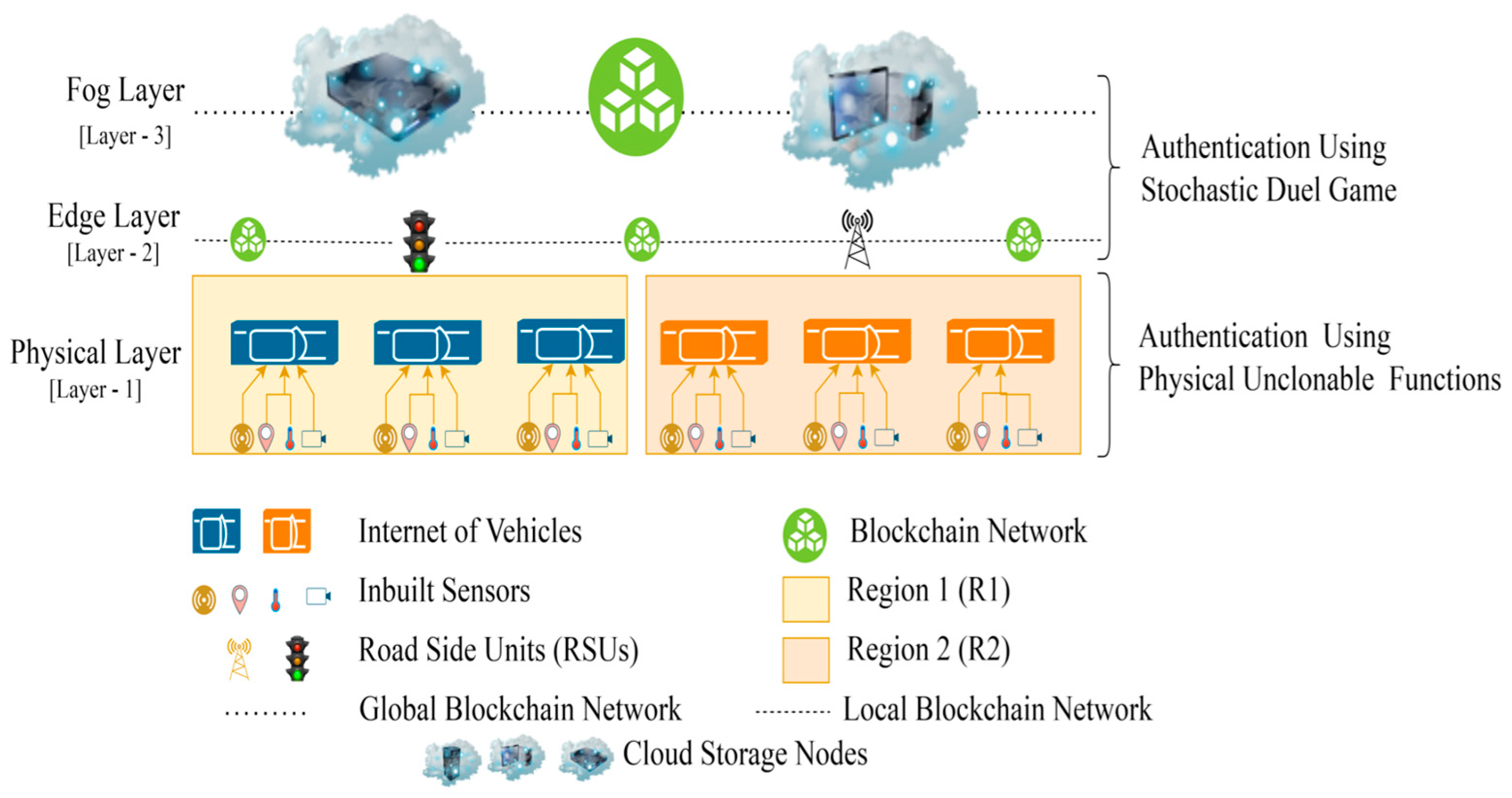
3. Proposed Authentication Framework for IoVs
3.1. Layer 1
3.2. Layer 2
3.3. Layer 3
4. Security Investigations
4.1. Assumptions
- Every vehicle/node is equipped with a PUF.
- The data from the IoV is sent through a public network.
- There are two categories of adversary: an internal attacker who has been granted access to data but whose illicit activity is difficult to detect; and an external attacker whose threats are only somewhat less severe.
- The adversary cannot penetrate data transferred through the private channel in the IoVs, which is one of two types of communication—public and private communications. The malicious node, on the other hand, has access to data delivered through a public channel and may alter, delete, or retransmit it.
4.2. Formal Security Analysis
4.3. Informal Security Analysis
5. Framework Implementation
| Algorithm 1: Vehicle Permission |
| function:VehPer input:new_vehicle output: true/false procedure: get((‘hello’, nonce_CH), CH) ← v∗[n].node ifdist_key==1 then get(vehicle_ID, sessionKeyRequest_ID, nonce_CH, nonce_v, distKey) ← v∗[n].node get(nonce_v, SessionKey[ ], distKey) ← CH else get(vehicle_ID, sessionKeyRequest_ID, nonce_CH, nonce_v, PK(CH)) ← v∗[n].node get(nonce_v, SessionKey[ ], distKey) ← CH get(distKey, PK(CH), PK(veh)) ← CH set(SessionKey[v]=1, CH) ← permissioned[v] search(commReq_ID, SessionKeyID[v], nonce_v, distKey) ifcommReq_ID==1 then get(nonce_v, nonce_s, SessionKey[ ])← permissioned[v] comm._Flag[v] = true else comm._Flag[v] = false return comm._Flag[v] |
| Algorithm 2: Validate Neighbours for BC Network |
| function:safeNodeBC output:Validated Neighbours procedure: fori in,∀∗=1, …, n do adj.n∗[i].node={}← create empty sorted list of adjacency nodes forj in,∀∗=1, …, n and j ≠ ido ← Calculatefirst point of time for communication if====do adj.n∗[i].node ← j else return adj.n∗ |
| Algorithm 3: Data Flow |
| function: DataFlow(n1, n2) output: updated_BC procedure: whilesimulationdo T, B← initialize for x ← 1 to T do for y ← 1 to B do Transfer data from n1to n2 Block ← b(y) Validate Block on n2 Deploy Block from n2to BC |
| Algorithm 4: Check Successor |
| function:FindSuccessor input:ID output:successor procedure: if ID∈ (v, successor)then return successor else for i = vo to 1do if name[i]∈ (v, ID) then returnAlgorithm 4← name[i] returnAlgorithm 4← v |
| Algorithm 5: Node Initialization |
| function:NodeSetUp input:n procedure: genesis.block← create n ← generate node n.node← create account n.node.account← allocate resource n.predecessor = null n.successor = null |
| Algorithm 6: Simulating the Framework |
| whilesimulationdo //Initialization fori in r∗, r∗∈R∀∗ = 1, 2, 3, …, n do Algorithm 5← call forj in ido xi∗[j].node← compile contract xi∗[j].node← deploy for i in v∗, v∗∈V∀∗= 1, 2, 3, …, n do Algorithm 5← call //Network Update for i in x*, x*∈(v*, r*) do for j in adj.m∗, ∀∗=1, …, n do if Algorithm 1(new_v)== truethen Algorithm 5← call contract ← sendMessage() ← v*[i].node r∗[j].node← contract ← v*[i].node while msgrequest(v*[i].node)==1 do for k in v∗, v∗∈V ∀∗=1, 2, 3, …, n do if v∗[k].cert == true then v∗[k].cert← Permission generate v∗[k].ID for m in kdo vi∗[m].node← compile contract vi∗[m].node← deploy vi∗[m].predecessor = null vi∗[m].node.successor = reg_veh.find_suc(v) sp = { vk∗[m].predecessor, vk∗[m].node.successor} ifsp∈ (v, vk∗[m].node.successor)then sp = vk∗[m].node.successor if ((vk∗[m].predecessor == null)or vi∗[j].predecessor ∈ (v, vi∗[j].predecessor)then vk∗[m].predecessor = reg_veh name[t++] = Algorithm 4(v + 2t−1) else ifv∗[k].reg ==1 then whilemsgrequest(v*[k].node)==1 do if PUFCRP(v∗[k]) ==1 then v∗[k].cert ← Issue Set v∗[k].cert = 1 else v∗[k].cert ← Reject Set v∗[k].cert = 0 else v∗[k].cert ← Reject Set v∗[k].cert = 0 //Update LocalBC for i in , ∀∗=1, …, n do Algorithm 2← call for j in adj.m∗, ∀∗=1, …, n do while MINdo contract ← sendMessage() ← r*[i].node r∗[j].node← contract ← r*[i].node Algorithm 3(MinerNode, ControllerNode)← call Clear Block from bB-1 to bB-N //Update GlobalBC for i in r∗, r∗∈G∀∗=1, 2, 3, …, n do Algorithm 2← call for j in adj.m∗, ∀∗=1, …, n do while MINdo contract ← sendMessage() ← r*[i].node r∗[j].node← contract ← r*[i].node Algorithm 3(ControllerNode, CloudServer)← call Update GlobalBC Replicate and filter data from GlobalBC to Cloud_Server |
6. Performance Analysis and Discussion
6.1. Initial Setup
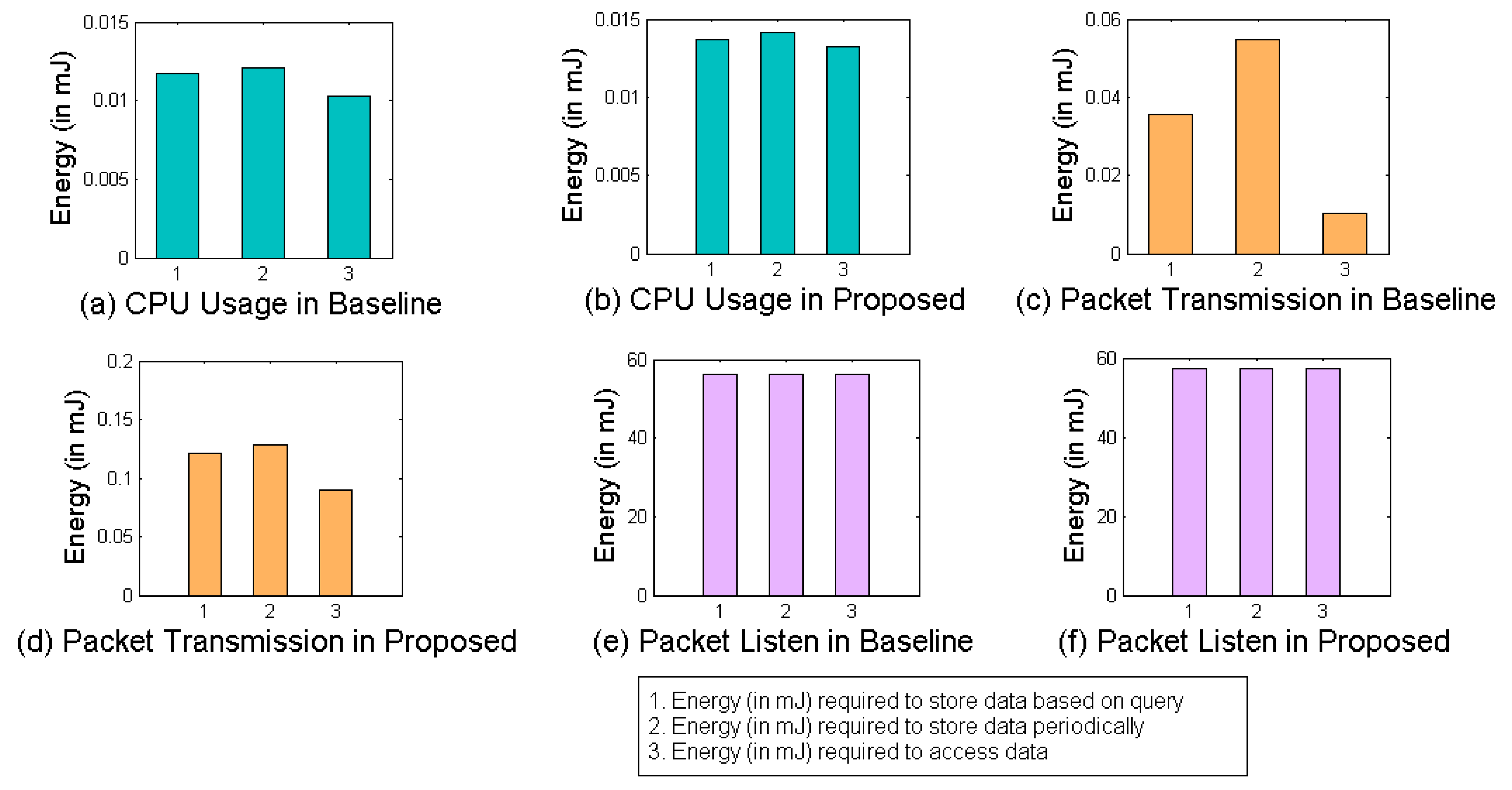
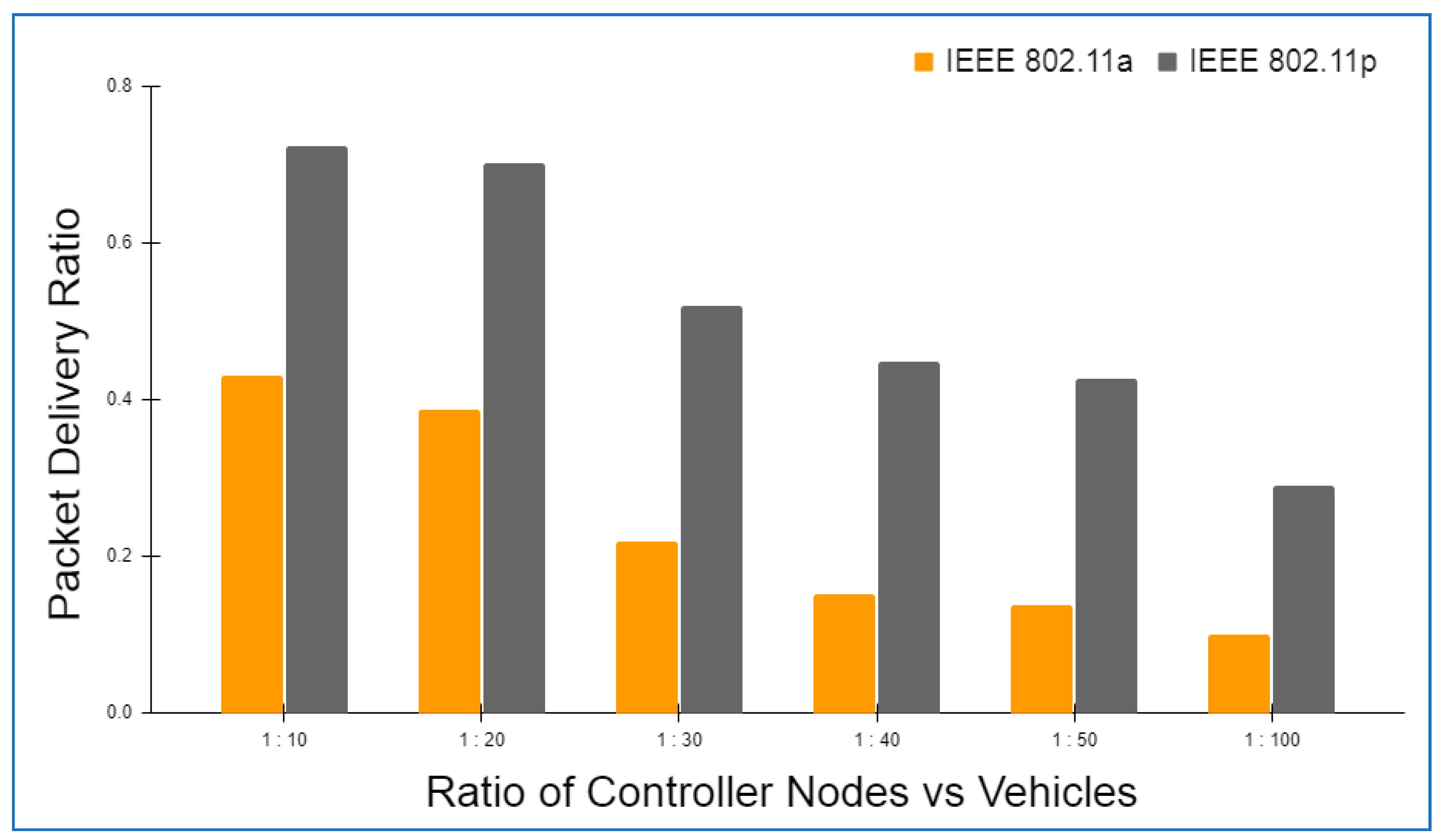
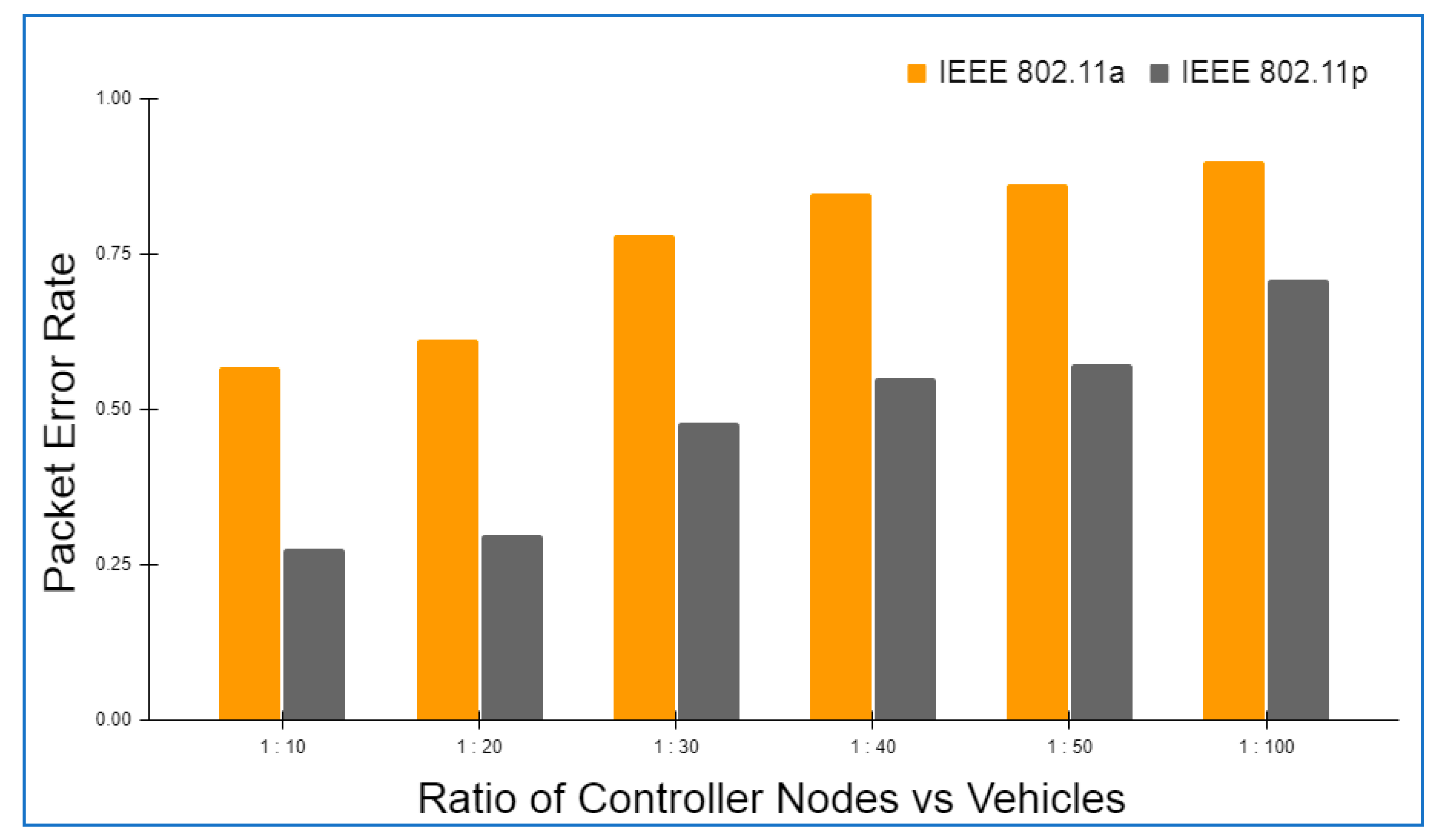
6.2. Framework Evaluation
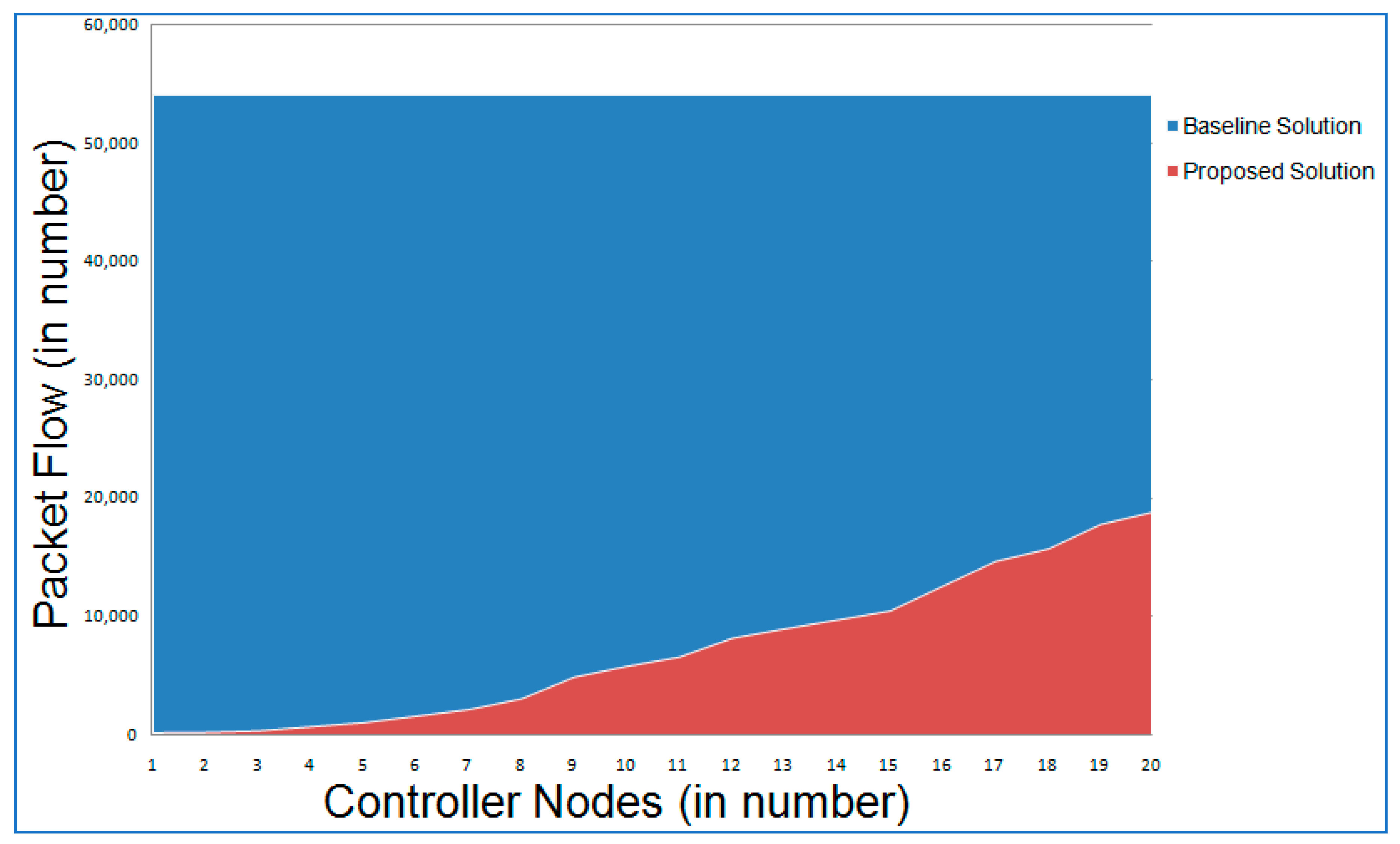
6.3. Operational Cost
6.4. Comparative Analysis
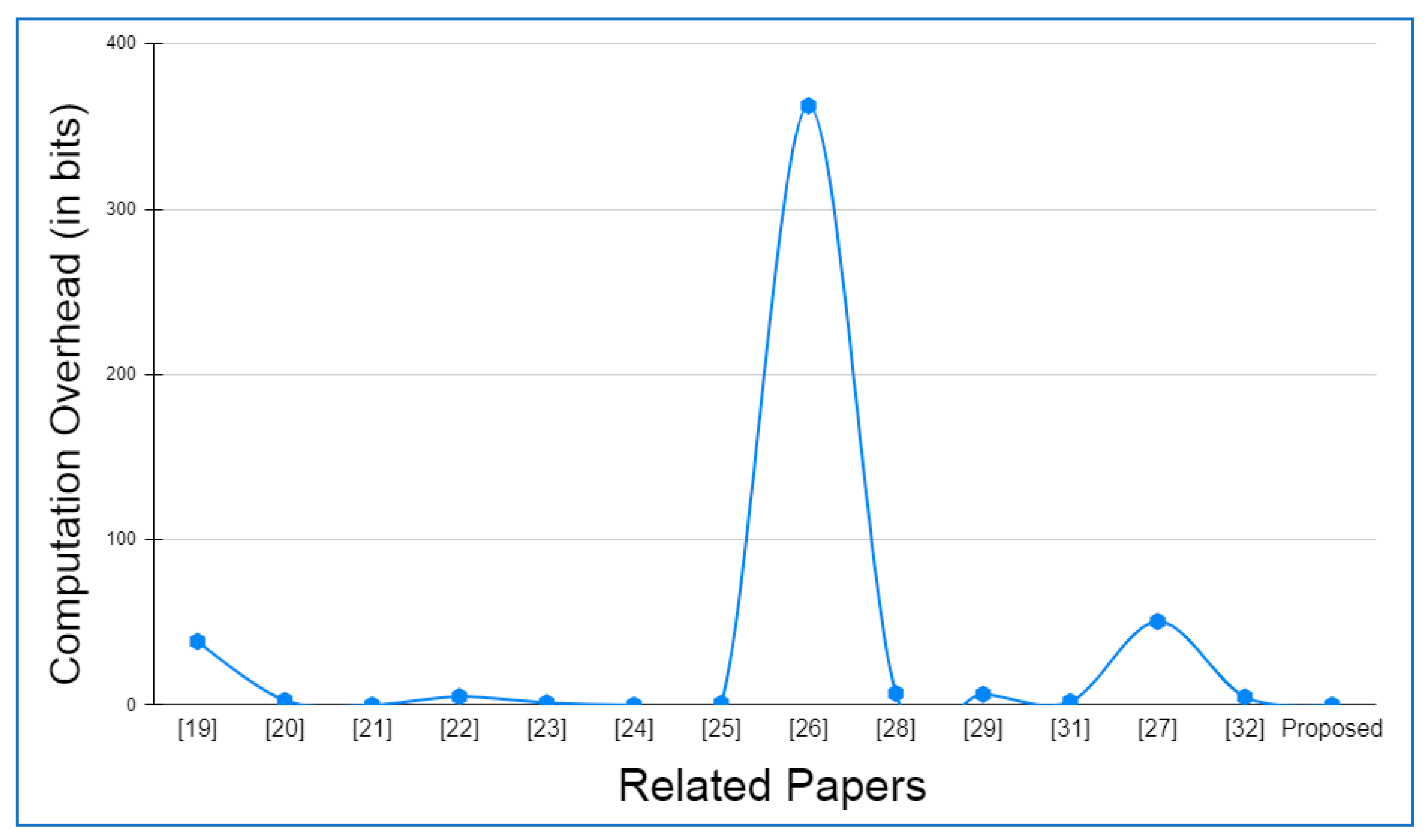
6.4.1. Computation Overhead
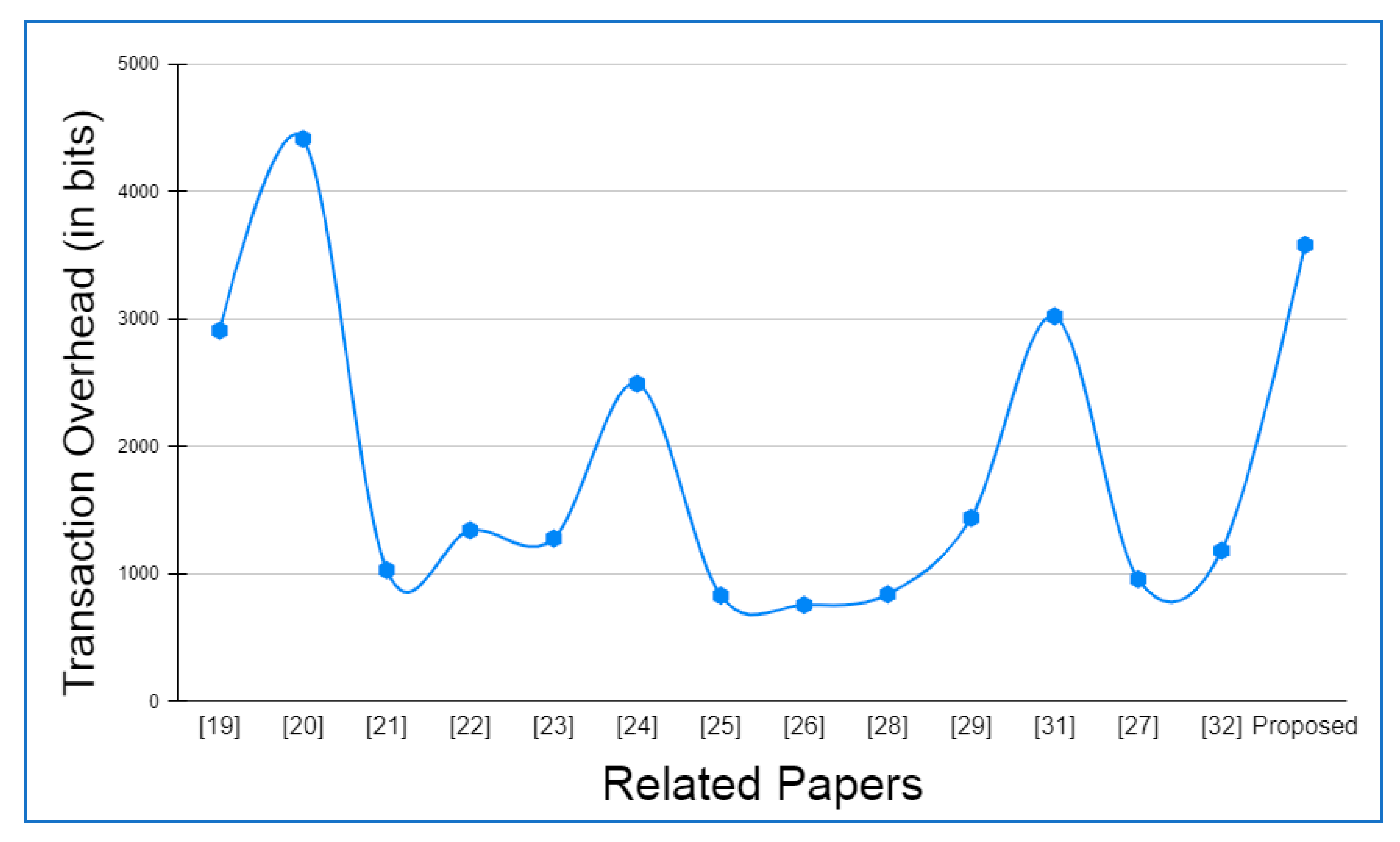
6.4.2. Transaction Overhead
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Liang, W.; Long, J.; Weng, T.H.; Chen, X.; Li, K.C.; Zomaya, A.Y. TBRS: A trust based recommendation scheme for vehicular CPS network. Future Gener. Comput. Syst. 2019, 92, 383–398. [Google Scholar] [CrossRef]
- Kenney, J.B. Dedicated short-range communications (DSRC) standards in the United States. Proc. IEEE 2011, 99, 1162–1182. [Google Scholar] [CrossRef]
- Dhaou, I.B.; Tenhunen, H. A High-Throughput Architecture for the SHA-256/224 Compliant with the DSRC Standard. Int. J. Embed. Real-Time Commun. Syst. 2019, 10, 98–118. [Google Scholar] [CrossRef]
- Zhou, H.; Xu, W.; Chen, J.; Wang, W. Evolutionary V2X technologies toward the Internet of vehicles: Challenges and opportunities. Proc. IEEE 2020, 108, 308–323. [Google Scholar] [CrossRef]
- Alouache, L.; Nguyen, N.; Aliouat, M.; Chelouah, R. Survey on IoV routing protocols: Security and network architecture. Int. J. Commun. Syst. 2019, 32, e3849. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. Security and privacy in vehicular ad hoc network and vehicle cloud computing: A survey. Wirel. Commun. Mob. Comput. 2020, 2020, 5129620. [Google Scholar] [CrossRef] [Green Version]
- Liang, H.; Wu, J.; Mumtaz, S.; Li, J.; Lin, X.; Wen, M. MBID: Micro-blockchain-based geographical dynamic intrusion detection for V2X. IEEE Commun. Mag. 2019, 57, 77–83. [Google Scholar] [CrossRef]
- Hahn, D.; Munir, A.; Behzadan, V. Security and privacy issues in intelligent transportation systems: Classification and challenges. IEEE Intell. Transp. Syst. Mag. 2019, 13, 181–196. [Google Scholar] [CrossRef] [Green Version]
- Wu, W.; Yang, Z.; Li, K. Internet of Vehicles and applications. In Internet of Things; Morgan Kaufmann: Burlington, MA, USA, 2016; pp. 299–317. [Google Scholar]
- Ngabo, D.; Wang, D.; Iwendi, C.; Anajemba, J.H.; Ajao, L.A.; Biamba, C. Blockchain-based security mechanism for the medical data at fog computing architecture of internet of things. Electronics 2021, 10, 2110. [Google Scholar] [CrossRef]
- Alrebdi, N.; Alabdulatif, A.; Iwendi, C.; Lian, Z. SVBE: Searchable and verifiable blockchain-based electronic medical records system. Sci. Rep. 2022, 12, 266. [Google Scholar] [CrossRef]
- Gupta, M.; Patel, R.B.; Jain, S. Lightweight Security Framework for IoT Enabled Tracking of COVID-19 and its Variants. In Proceedings of the 2021 2nd International Conference on Computational Methods in Science & Technology (ICCMST), Mohali, India, 17–18 December 2021; pp. 287–292. [Google Scholar]
- Iwendi, C.; Mahboob, K.; Khalid, Z.; Javed, A.R.; Rizwan, M.; Ghosh, U. Classification of COVID-19 individuals using adaptive neuro-fuzzy inference system. Multimed. Syst. 2021, 1–15. [Google Scholar] [CrossRef] [PubMed]
- Li, X.; Ma, J.; Wang, W.; Xiong, Y.; Zhang, J. A novel smart card and dynamic ID based remote user authentication scheme for multi-server environments. Math. Comput. Model. 2013, 58, 85–95. [Google Scholar] [CrossRef]
- Li, X.; Xiong, Y.; Ma, J.; Wang, W. An efficient and security dynamic identity based authentication protocol for multi-server architecture using smart cards. J. Netw. Comput. Appl. 2012, 35, 763–769. [Google Scholar] [CrossRef]
- Wang, X.; Zeng, P.; Patterson, N.; Jiang, F.; Doss, R. An improved authentication scheme for internet of vehicles based on blockchain technology. IEEE Access 2019, 7, 45061–45072. [Google Scholar] [CrossRef]
- Gao, Y.; Al-Sarawi, S.F.; Abbott, D. Physical unclonable functions. Nat. Electron. 2020, 3, 81–91. [Google Scholar] [CrossRef]
- Gupta, M.; Sharma, B.; Tripathi, A.; Singh, S.; Bhola, A.; Singh, R.; Dwivedi, A.D. n-Player Stochastic Duel Game Model with Applied Deep Learning and Its Modern Implications. Sensors 2022, 22, 2422. [Google Scholar] [CrossRef]
- Bagga, P.; Sutrala, A.K.; Das, A.K.; Vijayakumar, P. Blockchain-based batch authentication protocol for Internet of Vehicles. J. Syst. Archit. 2021, 113, 101877. [Google Scholar] [CrossRef]
- Xu, Z.; Liang, W.; Li, K.C.; Xu, J.; Jin, H. A blockchain-based roadside unit-assisted authentication and key agreement protocol for internet of vehicles. J. Parallel Distrib. Comput. 2021, 149, 29–39. [Google Scholar] [CrossRef]
- Gupta, M.; Patel, R.B.; Jain, S.; Garg, H.; Sharma, B. Lightweight branched blockchain security framework for Internet of Vehicles. Trans. Emerg. Telecommun. Technol. 2022, e4520. [Google Scholar] [CrossRef]
- Bagga, P.; Das, A.K.; Wazid, M.; Rodrigues, J.J.; Choo, K.K.R.; Park, Y. On the design of mutual authentication and key agreement protocol in internet of vehicles-enabled intelligent transportation system. IEEE Trans. Veh. Technol. 2021, 70, 1736–1751. [Google Scholar] [CrossRef]
- Sharma, S.; Kaushik, B.; Rahmani MK, I.; Ahmed, M.E. Cryptographic Solution-Based Secure Elliptic Curve Cryptography Enabled Radio Frequency Identification Mutual Authentication Protocol for Internet of Vehicles. IEEE Access 2021, 9, 147114–147128. [Google Scholar] [CrossRef]
- Vasudev, H.; Deshpande, V.; Das, D.; Das, S.K. A lightweight mutual authentication protocol for V2V communication in internet of vehicles. IEEE Trans. Veh. Technol. 2020, 69, 6709–6717. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Hasbullah, I.H.; Manickam, S.; Hanshi, S.M. Efficient conditional privacy preservation with mutual authentication in vehicular ad hoc networks. IEEE Access 2020, 8, 144957–144968. [Google Scholar] [CrossRef]
- Cui, J.; Wu, D.; Zhang, J.; Xu, Y.; Zhong, H. An efficient authentication scheme based on semi-trusted authority in VANETs. IEEE Trans. Veh. Technol. 2019, 68, 2972–2986. [Google Scholar] [CrossRef]
- Bayat, M.; Pournaghi, M.; Rahimi, M.; Barmshoory, M. NERA: A new and efficient RSU based authentication scheme for VANETs. Wirel. Netw. 2020, 26, 3083–3098. [Google Scholar] [CrossRef]
- Wu, L.; Sun, Q.; Wang, X.; Wang, J.; Yu, S.; Zou, Y.; Zhu, Z. An efficient privacy-preserving mutual authentication scheme for secure V2V communication in vehicular ad hoc network. IEEE Access 2019, 7, 55050–55063. [Google Scholar] [CrossRef]
- Dinarvand, N.; Barati, H. An efficient and secure RFID authentication protocol using elliptic curve cryptography. Wirel. Netw. 2019, 25, 415–428. [Google Scholar] [CrossRef]
- Ying, B.; Nayak, A. Efficient authentication protocol for secure vehicular communications. In Proceedings of the 2014 IEEE 79th Vehicular Technology Conference (VTC Spring), Seoul, Korea, 18–21 May 2014; pp. 1–5. [Google Scholar]
- Chen, C.M.; Xiang, B.; Liu, Y.; Wang, K.H. A secure authentication protocol for internet of vehicles. IEEE Access 2019, 7, 12047–12057. [Google Scholar] [CrossRef]
- Alazzawi, M.A.; Lu, H.; Yassin, A.A.; Chen, K. Efficient conditional anonymity with message integrity and authentication in a vehicular ad-hoc network. IEEE Access 2019, 7, 71424–71435. [Google Scholar] [CrossRef]
- Stoica, I.; Morris, R.; Liben-Nowell, D.; Karger, D.R.; Kaashoek, M.F.; Dabek, F.; Balakrishnan, H. Chord: A scalable peer-to-peer lookup protocol for internet applications. IEEE/ACM Trans. Netw. 2003, 11, 17–32. [Google Scholar] [CrossRef]
- Lofstrom, K.; Daasch, W.R.; Taylor, D. IC identification circuit using device mismatch. In Proceedings of the 2000 IEEE International Solid-State Circuits Conference. Digest of Technical Papers (Cat. No. 00CH37056), San Francisco, CA, USA, 9 February 2000; pp. 372–373. [Google Scholar]
- CoinMarketCap Alexandria. coinmarketcap.com. Available online: https://coinmarketcap.com/alexandria/article/why-nobody-can-hack-a-blockchain (accessed on 17 May 2022).
- Polak, B. Discussion of Duel. Open Yale Courses. 2008. Available online: http://oyc.yale.edu/economics/econ-159/lecture-16 (accessed on 1 May 2022).
- Kim, S.K.A. A Versatile Stochastic Duel Game. Mathematics 2020, 8, 678. [Google Scholar] [CrossRef]
- Kim, S.K.A. Antagonistic One-To-N Stochastic Duel Game. Mathematics 2020, 8, 1114. [Google Scholar] [CrossRef]
- Dshalalow, J.H.; Huang, W.; Ke, H.J.; Treerattrakoon, A. On Antagonistic Game with a Constant Initial Condition. Marginal Functionals and Probability Distributions. Nonlinear Dyn. Syst. Theory 2016, 16, 268–275. [Google Scholar]
- Wendt, J.B.; Potkonjak, M. Hardware obfuscation using PUF-based logic. In Proceedings of the 2014 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Jose, CA, USA, 2–6 November 2014; pp. 270–271. [Google Scholar]
- Xu, T.; Wendt, J.B.; Potkonjak, M. Secure remote sensing and communication using digital PUFs. In Proceedings of the 2014 ACM/IEEE Symposium on Architectures for Networking and Communications Systems (ANCS), Marina del Rey, CA, USA, 20–21 October 2014; pp. 173–184. [Google Scholar]
- Mahmoud, A.; Rührmair, U.; Majzoobi, M.; Koushanfar, F. Combined modeling and side channel attacks on strong PUFs. Cryptol. Eprint Arch. 2013, 632, 1–9. [Google Scholar]
- Singh, A.K.; Raj, M. A study of Analytics and Exploration of Bitcoin Challenges and Blockchain. In Proceedings of the 2022 International Conference on Electronics and Renewable Systems (ICEARS), Tuticorin, India, 16–18 March 2022; pp. 929–933. [Google Scholar]
- TRON Network|Decentralize the Web Network. Available online: https://tron.network/ (accessed on 6 June 2022).
- Sisodiya, V.S.; Garg, H. A comprehensive study of Blockchain and its various Applications. In Proceedings of the 2020 International Conference on Power Electronics & IoT Applications in Renewable Energy and Its Control (PARC), Mathura, India, 28–29 February 2020; pp. 475–480. [Google Scholar]
- Rathor, S.; Agrawal, A.; Yadav, D.P. The Efficient use of Blockchain for Reducing Frauds in Parental Property Distribution. In Proceedings of the 2020 International Conference on Power Electronics & IoT Applications in Renewable Energy and Its Control (PARC), Mathura, India, 28–29 February 2020; pp. 46–49. [Google Scholar]
- Rathor, S.; Agrawal, A. A robust verification system for recruitment process by using blockchain technology. Int. J. Blockchains Cryptocurrencies 2020, 1, 389–399. [Google Scholar] [CrossRef]
- Datta, P.; Sharma, B. A survey on IoT architectures, protocols, security and smart city based applications. In Proceedings of the 2017 8th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Delhi, India, 3–5 July 2017; pp. 1–5. [Google Scholar]
- Bajaj, K.; Sharma, B.; Singh, R. Integration of WSN with IoT applications: A vision, architecture, and future challenges. In Integration of WSN and IoT for Smart Cities; Springer: Cham, Switzerland, 2020; pp. 79–102. [Google Scholar]






| Paper | Year | Network Type | Multilayer Authorization | Blockchain Usage | Authentication Technique | |
|---|---|---|---|---|---|---|
| VANET | IoV | |||||
| [19] | 2021 | N | Y | N | Y | Batch authentication |
| [20] | 2021 | N | Y | N | Y | Roadside Unit-assisted authentication |
| [21] | 2021 | N | Y | N | Y | Blockchain-based authentication |
| [22] | 2021 | N | Y | N | N | Mutual authentication and key agreement |
| [23] | 2021 | N | Y | N | Y | Elliptic Curve Cryptography-Enabled Radio Frequency Identification Mutual Authentication |
| [24] | 2020 | N | Y | N | N | Cryptography-Based Authentication |
| [25] | 2020 | Y | N | N | N | Elliptic Curve Cryptography (ECC) and general one-way hash function |
| [26] | 2019 | Y | N | N | N | Authentication based on semi-trusted authority |
| [27] | 2019 | Y | N | N | N | RSU-based authentication |
| [28] | 2019 | Y | N | N | N | Cryptography-Based Authentication |
| [29] | 2019 | Y | N | N | N | Elliptic Curve Cryptography-Enabled Radio Frequency Identification Mutual Authentication |
| [31] | 2019 | Y | N | N | N | Cryptography-Based Authentication |
| [32] | 2019 | Y | N | Y | N | Cryptography-Based Authentication |
| Acronym | Definition |
|---|---|
| An(t) | payoff function of each node n in the network, where n ranges from 1 to N, at time tn |
| maximum allowed time for an iteration cycle | |
| set of positive real numbers | |
| probability function that it may come with a threat message | |
| probability function of a node to avoid threat | |
| first point of time when a set of nodes in the network establishes successful communication | |
| instance when any two nodes say m and n in the network wait to establish communication | |
| (Ω, F, P) | Probability triplet (representing node n) |
| Ω | collection of all potential outcomes, i.e., a sample space |
| F | space in which events occur, i.e., event space |
| P | probabilistic function that assigns a probability to each event in the event space |
| time space representing node n | |
| time when two nodes try to connect | |
| when node n maximizes the chance of avoiding threats in continuous time domain t | |
| exit index of node n | |
| PUF | Physical Unclonable Function |
| IoT | Internet of Things |
| IoV | Internet of Vehicles |
| dPoW | Dynamic Proof of Work |
| V2X | Vehicle to Everything |
| V2V | Vehicle to Vehicle |
| V2R | Vehicle to Roadside |
| V2H | Vehicle to Human |
| V2S | Vehicle to Sensor |
| RSU | Roadside Unit |
| RFID | Radio-Frequency Identification Technology |
| ECC | Elliptic Curve Cryptography |
| (DoS) | Denial of Service |
| CRL | Certificate Revocation List |
| VANET | Vehicular Ad Hoc Network |
| MITM | Man-in-the-Middle Attack |
| IC | Integrated Circuits |
| MAC | Message Authentication Code |
| MSP | Membership Service Provider |
| HLF | Hyperledger Fabric |
| DHT | Distributed Hash Table |
| Serial Number | Propositions | Attack Description | Security Defense Explanation |
|---|---|---|---|
| P1 | The proposed framework is resilient against impersonation attacks. | The attacker may undertake a vehicle impersonation attack by intercepting the login message and obtaining the secret values from the vehicle’s smart card in an unlawful manner to listen in on, intercept, and change any message in the public communication channel. | Assume the attacker intercepts the message and attempts to construct another acceptable message that the network will validate. It is never going to happen because each and every message is recorded in the ledger over the blockchain maintained among all the RSUs and controller nodes in the network. So, any unlawful activity may not get a positive response from the rest of the network. Furthermore, guessing all of the unknown restrictions in polynomial time is impossible. As a result, the attacker will not be able to construct or guess further legitimate messages in polynomial time. Further, it is also not feasible to impersonate the vehicles by altering the message. As a legitimate message cannot be computed by the attacker unless he or she has access to all of the parameters necessary to calculate it, including the nonce of the sink node. |
| P2 | The proposed framework is secured against offline password guessing attacks. | A password guessing attack is one in which an attacker attempts to impersonate a user by repeatedly guessing his password or other login information. Password guessing attacks may be carried out online by connecting to a server and trying to guess a user’s password. There are no limits on how many times an adversary may try to login in this version of the attack, unlike the offline version, which does. In the offline variant, an adversary obtains a user’s password-related data (e.g., a hashed password) and then repeatedly attempts to guess a password while comparing the hashed version to the intercepted one. | If the attacker wants to launch an offline password guessing attack on the vehicle, the attacker must first get the stored settings from the smart card. Two scenarios have been presumptively considered. One in which the attacker has stolen the vehicle’s smart card, and the other in which it is presumed that most users utilize low entropy IDs and passwords for memorizing purposes, which can be readily guessed in polynomial time. If an attacker manages to get its hands on the vehicle’s secret information, the attacker will still be unable to guess the proper password simultaneously in polynomial time. This is because no one can know a vehicle’s true identify except the vehicle itself through its smart card or messages communicated over the public channel since our approach uses blockchain to establish identity protection and passwords are safeguarded by a non-invertible one-way hash function. Hence, the attacker is unable to get access to the user’s personal information. |
| P3 | Replay attacks can be protected by the proposed framework. | As the name suggests, this kind of attack involves an attacker intercepting and then fraudulently delaying or resending an already intercepted secure network communication. It is common for an attacker to re-transmit previously delivered communications in order to verify that a certain message was sent by the intended sender, hoping that this time the recipient would make a mistake and do what the attacker wants. | It is possible that a malicious actor may attempt to replay previous messages. Every time a message is sent using the proposed framework, it generates a new random number. Assume another scenario in which an antagonist has obtained one of the CRPs for a PUF and is attempting to reuse a prior challenge. This is why a CRP should never be reused. By allowing PUFs to be reprogrammed after each CRP, the system will be impervious to replay attacks. As a result, replay attacks are not a concern for the proposed methodology under development. |
| P4 | The proposed framework is guarded from linking attacks. | In such kinds of attacks, to discover the real world identification of an incognito node, an adversary, who might be a controller node or cloud storage node, connects various data in the cloud or blockchain transactions with the same ID. | Each transaction in layer 3 is assigned a unique public key by the overlay nodes. Separate cloud accounts are used to verify the identity of each connected device. This makes it impossible for an attacker to connect data from various devices belonging to the same user. |
| P5 | The proposed framework can protect against man-in-the-middle attacks. | An adversary node breaches the communication between two nodes in the network and obtains or compromises the information they communicate in a man-in-the-middle attack. An adversary may capture a ledger wallet by installing a malicious program on a target node and changing the address of the destination of blockchain transactions. | The information on all of the public constraints and messages’ exchange in sessions, as well as how to communicate with other roles of model, has been revealed to the adversary. Its objective is to identify all known vulnerabilities such as interception and replay the traffic, decrypt the secret keys, reveal the data of protected sessions, and threaten the legitimacy of entities. By implementing the framework, these back ends check of an attack can be detected. There are certain models that report safe, but others describe how the harm may be done and whose security objective cannot be fulfilled if the model is not secure enough. As proposed by Theorem 1, the proposed framework is protected against passive and active attacks, such as replay and man-in-the-middle attacks.Let us consider at any time a PUF gets its hands on one of the CRPs, an adversary can attempt to repeat an earlier challenge. As a result, it is preferred that a CRP be never reused. After each CRP, PUFs may be reconfigured, making the system resistant to man-in-the-middle attacks. |
| P6 | Attacks such as Denial ofService(DOS) or Distributed Denial ofService(DDOS) can not affect the network security guarded with the proposed framework. | Attacks such as Distributed Denial of Service (DdoS) or Denial of Service (DOS) are meant to take advantage of weak spots in a system. This is performed by flooding a program with more requests than it can process, exceeding its network card’s capacity. Blockchain servers are overloaded with queries, which cause them to lose connectivity to other apps. | Before being sent to the global blockchain, all transactions in a local blockchain are authorized by the RSU or controller nodes. The global blockchain transactions are invalid on the local blockchain because the local blockchain and the global blockchain use different encryption algorithms. In the region cluster, a vehicle can only connect with another vehicle if the RSU has created a shared key between them. To avoid sending transactions to other vehicles in the cluster, RSUs search for matches in their key-list before sending any. Depending on the RSU’s capacity, the maximum number of transactions it may accept is limited. As soon as the limit is reached, vehicles are prevented from transmitting transactions to the destination vehicle. |
| P7 | The proposed framework can defend well against the 51% attack. | An attacker must gain control of all the mining power on a specific blockchain in order to commit a 51% attack. With a mining advantage of more than 50% and the ability to mine faster than everyone else, the adversaries are doing quite well. | Based on the consensus method, the attack may be handled during the validation of neighbors or by other layer 2 nodes entirely via mutual authentication. |
| P8 | Public BC modification attack is not possible in the proposed framework. | False blocks are advertised as the longest ledger by the attacker. As a result, every node acknowledges the ledger maintained by the attacker as the authentic ledger. | Layer 2 nodes, such as RSU and controllers, are limited in the number of blocks they can create in a given period of time. This restricts the number of malicious blocks that a layer 2 node may add, preventing the attacker from producing a ledger that is longer than the genuine ledger. |
| P9 | Physical and cloning attacks are absolutely not possible with the proposed framework. | The investigation of information systems in order to uncover the concealed features of devices and systems by making use of the attributes of their implementation is known as cryptanalysis. One sort of cryptanalysis is known as physical attacks. | A vehicle or an IoV device might be cloned by an adversary to seem legitimate. An adversary may clone a device if it is physically compromised and the secrets from the seized device are extracted. The employment of PUFs, on the other hand, makes it exceedingly difficult for an opponent to conduct such attacks. In order to reliably assess PUF delays, a cloning attack on PUFs would require the deployment of intrusive procedures, which are not economically practical. To protect IoT devices with PUFs against physical and cloning threats, PUFs have been proven in [40,41] to be effective. |
| P10 | The proposed framework is immune to side-channel attacks. | A security vulnerability known as a “side-channel attack” aims to harvest information from a chip or a system via an open channel. Various physical characteristics may be measured or analyzed to do this. Side-channel attacks are made possible by the ease with which an attacker may get access to IoT devices. Timing, power monitoring, electromagnetic attacks, and differential fault analysis are prominent examples of attacks in this category. | Statistical measurement of the time needed by a CPU to complete cryptographic operations is often used in timing attacks to discover the secret key. PUFs, on the other hand, employ a challenge response model instead of secret keys, making it more difficult to correctly measure the timing delays of a circuit in an IC. In addition, PUFs are deemed isochronous, which makes them immune to timing attacks. Attacks that rely on power consumption monitoring during calculations are known as power monitoring attacks. A data analysis method has been used by [42] to demonstrate a power side-channel attack against PUFs. They demonstrated that the number of zeros and ones stored in the latches of an arbiter PUF may be determined by utilizing power consumption information. PUFs, on the other hand, may be made safe against these attacks if the amount of zeroes and ones in the latches remains consistent. Electromagnetic attacks are a lot more difficult to carry out than power-monitoring attacks. As with power analysis attacks, the PUF may be protected against electromagnetic attacks by decreasing current fluctuations. Differential fault analysis is performed by exposing security hardware to aberrant environmental circumstances in order to introduce defects within it. Physical data corruption in cryptographic systems is often exploited by these approaches. Because of their sensitivity to temperature and voltage fluctuations, certain PUF types (such as delay-based PUFs) may be exploited by an adversary, although the physical data contained inside these PUFs cannot be exploited. |
| Parameter | Year |
|---|---|
| Speed of Vehicle | 10–60 km/h |
| Number of Vehicles | 1000 |
| Communication Range of Vehicles | 300 m |
| Communication Range of RSUs | 1000 m |
| Routing Protocol | AODV |
| Simulation Time | 1000 s |
| Wireless Protocol | 802.11a/802.11p |
| Area | 10 km2 |
| Parameters | IEEE 802.11a | IEEE 802.11p |
|---|---|---|
| Data Transmission Rate | Upto 54 Mbps | Upto 27 Mbps |
| Channel Bandwidth | 20 MHz | 10 MHz |
| Guard Time | 0.8 µs | 1.6 µs |
| Subcarrier Spacing | 0.3125 MHz | 0.15625 MHz |
| Orthogonal Frequency Division Multiplexing Symbol Duration | 4 µs | 8 µs |
| Preamble Duration | 16 µs | 32 µs |
| Subcarrier Count | 52 | 52 |
| Coding Rate | Upto ¾ | Upto ¾ |
| Basic Modulations Used | Binary Phase Shit Keying (BPSK), Quadrature Phase Shift Keying (QPSK) | Binary Phase Shit Keying (BPSK), Quadrature Phase Shift Keying (QPSK) |
| Quadrature Amplitude Modulation (QAM) | 16QAM, 64QAM | 16QAM, 64QAM |
| Serial Number | Proposed Framework | [19] | [20] | [21] | [22] | [23] | [24] | [25] | [26] | [28] | [29] | [31] | [27] | [32] | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Possibility of Attack | Attack Defense Measurement | ||||||||||||||
| P1 | Least Probable | Adequate | Y | Y | Y | Y | N | Y | Y | Y | Y | N | Y | Y | Y |
| P2 | Least Probable | Adequate | N | Y | N | N | N | Y | N | N | N | N | Y | N | N |
| P3 | Improbable | High | Y | Y | Y | Y | Y | N | Y | Y | Y | Y | Y | N | Y |
| P4 | Improbable | High | N | N | N | Y | N | N | Y | N | N | N | N | N | N |
| P5 | Improbable | High | Y | N | Y | N | N | Y | Y | N | N | N | N | N | Y |
| P6 | Improbable | Very High | N | N | Y | N | Y | N | N | N | N | Y | Y | Y | Y |
| P7 | Improbable | Very High | N | N | Y | N | N | N | N | N | N | N | N | N | N |
| P8 | Improbable | Very High | N | N | Y | N | N | N | N | N | N | N | N | N | N |
| P9 | Improbable | Very High | N | N | N | N | N | N | N | N | N | N | N | N | N |
| P10 | Improbable | Very High | N | N | N | N | N | N | N | N | N | N | N | N | N |
| Paper | Major Computation Overhead |
|---|---|
| [19] | 3B + 5vM + (3v + 1)A + (3v + 2)H + M + vE |
| [20] | 20H |
| [21] | 12H + 2log2vH |
| [22] | 16H |
| [23] | (6M + 4A + 2H)t + (6M + 2A + S + 2H)s |
| [24] | 17H |
| [25] | (n + 2) H |
| [26] | 13M + 3A + (8 + 2L)H + 9SED |
| [28] | 22H |
| [29] | 3M(t + s) |
| [31] | 12H + 6X + 2SED |
| [27] | 3P + N(M + O) |
| [32] | 5M + (3 + n)H+(n + 2)A |
| Proposed | (16 + log2v)H |
| Notations Used in Computational Cost Calculation | |
| H: Hash Operation | SED: symmetric key encryption/decryption |
| L: the length of forward and backward hash chain | E: Encryption Operation |
| n: Number of random integers generated by RSUs | X: modular exponentiation |
| M: Scalar Multiplication Operation | N: no of signature verifications |
| I: Inversion Operation | P: Pairing |
| A: Addition Operation | O: Map to Point |
| S: Subtraction Operation | s: server operations |
| B: Bilinear Pairing Operation | t: tag operations |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gupta, M.; Kumar, R.; Shekhar, S.; Sharma, B.; Patel, R.B.; Jain, S.; Dhaou, I.B.; Iwendi, C. Game Theory-Based Authentication Framework to Secure Internet of Vehicles with Blockchain. Sensors 2022, 22, 5119. https://doi.org/10.3390/s22145119
Gupta M, Kumar R, Shekhar S, Sharma B, Patel RB, Jain S, Dhaou IB, Iwendi C. Game Theory-Based Authentication Framework to Secure Internet of Vehicles with Blockchain. Sensors. 2022; 22(14):5119. https://doi.org/10.3390/s22145119
Chicago/Turabian StyleGupta, Manik, Rakesh Kumar, Shashi Shekhar, Bhisham Sharma, Ram Bahadur Patel, Shaily Jain, Imed Ben Dhaou, and Celestine Iwendi. 2022. "Game Theory-Based Authentication Framework to Secure Internet of Vehicles with Blockchain" Sensors 22, no. 14: 5119. https://doi.org/10.3390/s22145119
APA StyleGupta, M., Kumar, R., Shekhar, S., Sharma, B., Patel, R. B., Jain, S., Dhaou, I. B., & Iwendi, C. (2022). Game Theory-Based Authentication Framework to Secure Internet of Vehicles with Blockchain. Sensors, 22(14), 5119. https://doi.org/10.3390/s22145119









