Data Acquisition Filtering Focused on Optimizing Transmission in a LoRaWAN Network Applied to the WSN Forest Monitoring System
Abstract
:1. Introduction
2. Related Work
3. SAFe Project System and Data Transmission
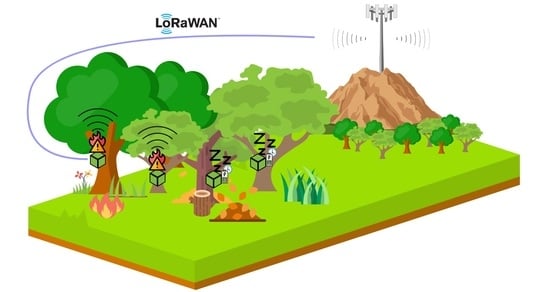
- The monitored region (➀) is where the WSN will be placed to collect data. The choice of these regions should consider the annual fire risk map provided by the Instituto da Conservação da Natureza e das Florestas (ICNF) [38];
- The WSN (➁) is responsible for real-time data acquisition at the forest. The Sensor Module allocation is determined through an optimization procedure that evaluates the fire hazard in each coordinate and must also consider the forest characteristics, such as soil type, cover tree density, and terrain relief, among others [13,39];
- The LoRaWAN Gateway (➃) receives data from each sensor module via the LoRaWAN protocol (➂). Then, it forwards the data through a 4G/LTE link (➄)—or by Ethernet where available—to a cloud server (➅);
- The Control Center (➆) receives all information, computes the data, and sends alerts about hazardous situations or forest fire ignitions, to the surveillance agent in the region. Therefore, this control center has an associated server (➅) that stores all collected data over the years and performs artificial intelligence procedures which will generate forest ignition alerts, warning rescue and combat teams;
- When rescue and combat teams receive the alerts provided by the algorithms, it becomes possible to elaborate an attack strategy as a support decision. Specifically, they can act against wildfires knowing the precise positioning of fire ignitions (➇).
Consumption’s Identification
4. Algorithms for Data Transmission Optimization
4.1. Exponential Smoothing Algorithm
4.2. Moving Average Based Algorithms
4.3. Least Squares Based Algorithm
5. Results
- Prepare the Area: Remove all flammable waste, cut dead grass and brush, and ensure the fire pit is at least 4 meters away from any structures, combustibles, and vegetation;
- Prepare the Fire: Place a stone ring or other fire-resistant barrier around the fire. Make sure the ring is flat and securely in place;
- Light the fire: Gather local firewood and dry kindling. Use only a lighter or matches to light the fire. Write down the WSE start time (visually);
- Monitor the fire: Observe it from a distance of at least 5 meters and ensure it is contained and not spreading;
- Put out the fire: When the fire is no longer needed, use a shovel or bucket of water to put out the fire. As indicated by the firefighter, do not exceed 60 min. Note the time the WSE ends;
- Cleanup: Ensure all embers, ashes, and debris are removed from the area and disposed of properly.
5.1. Results
| Algorithm 1: Pseudocode algorithm for testing the parameters of Exponential smoothing algorithm—. |
|
5.2. Results
| Algorithm 2: Pseudocode algorithm for testing the parameters of SMA algorithm—. |
|
5.3. Results
| Algorithm 3: Pseudocode algorithm for testing the parameters of Differences between two SMAs algorithm—. |
|
5.4. Results
| Algorithm 4: Pseudocode algorithm for testing the parameters of Least Squares algorithm—. |
|
5.5. Final Considerations
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| WSN | Wireless Sensor Network |
| JRC | Joint Research Centre |
| SAFe | Sistema de Monitorização de Alerta Florestal (Forest Alert Monitoring System) |
| LPWAN | Low Power Wide Area Network |
| LoRa | Long Range |
| LTE | Long Term Evolution |
| IoT | Internet of Things |
| TTN | The Things Network |
| FIR | Far Infrared |
| ICNF | Instituto da Conservação da Natureza e das Florestas |
| nRF-PPK2 | Power Profiler Kit II |
| PCB | Printed Circuit Board |
| DROWSIER | Data Re-send Only Warnings Sensing an Ignition Else Repose |
| SMA | Simple Moving Average |
| LSS | Least Squares Strategy |
| WSE | Wildfire Simulation Event |
References
- Hernández, L. The Mediterranean Burns: WWF’s Mediterrenean Proposal for the Prevention of Rural Fires; WWF: Gland, Switzerland, 2019. [Google Scholar]
- Alkhatib, A.A. A review on forest fire detection techniques. Int. J. Distrib. Sens. Netw. 2014, 10, 597368. [Google Scholar] [CrossRef] [Green Version]
- Pausas, J.G.; Keeley, J.E. Wildfires and global change. Front. Ecol. Environ. 2021, 19, 387–395. [Google Scholar] [CrossRef]
- Adámek, M.; Jankovská, Z.; Hadincová, V.; Kula, E.; Wild, J. Drivers of forest fire occurrence in the cultural landscape of Central Europe. Landsc. Ecol. 2018, 33, 2031–2045. [Google Scholar] [CrossRef]
- San-Miguel-Ayanz, J.; Durrant, T.; Boca, R.; Maianti, P.; Libertà, G.; Artés Vivancos, T.; Oom, D.; Branco, A.; De Rigo, D.; Ferrari, D.; et al. Forest Fires in Europe, Middle East and North Africa 2021; European Union: Luxembourg, 2022. [Google Scholar] [CrossRef]
- Freitas, T.R.; Santos, J.A.; Silva, A.P.; Martins, J.; Fraga, H. Climate Change Projections for Bioclimatic Distribution of Castanea sativa in Portugal. Agronomy 2022, 12, 1137. [Google Scholar] [CrossRef]
- POSEUR - Programa Operacional Sustentabilidade e Eficiência no Uso de Recursos. Sistemas de Videovigilância de Prevenção de Incêndios a Partir de 2017. Available online: https://poseur.portugal2020.pt/media/4140/plano_nacional_defesa_floresta_contra_incendios.pdf (accessed on 31 December 2022).
- Govil, K.; Welch, M.L.; Ball, J.T.; Pennypacker, C.R. Preliminary results from a wildfire detection system using deep learning on remote camera images. Remote. Sens. 2020, 12, 166. [Google Scholar] [CrossRef] [Green Version]
- SreeSouthry, S.V.; Khan, A.A.; Srinivasan, P. A highly accurate and fast identification of forest fire based on supervised multi model image classification algorithm (SMICA). J. Crit. Rev. 2020, 7. [Google Scholar]
- Catry, F.X.; Moreira, F.; Pausas, J.G.; Fernandes, P.M.; Rego, F.; Cardillo, E.; Curt, T. Cork oak vulnerability to fire: The role of bark harvesting, tree characteristics and abiotic factors. PLoS ONE 2012, 7, e39810. [Google Scholar] [CrossRef] [Green Version]
- Silva, J.S.; Rego, F.C.; Fernandes, P.; Rigolot, E. Towards Integrated Fire Management-Outcomes of the European Project Fire Paradox; European Forest Institute: Joensuu, Finland, 2010. [Google Scholar]
- Brito, T.; Pereira, A.I.; Lima, J.; Valente, A. Wireless sensor network for ignitions detection: An IoT approach. Electronics 2020, 9, 893. [Google Scholar] [CrossRef]
- Azevedo, B.F.; Brito, T.; Lima, J.; Pereira, A.I. Optimum sensors allocation for a forest fires monitoring system. Forests 2021, 12, 453. [Google Scholar] [CrossRef]
- Brito, T.; Zorawski, M.; Mendes, J.; Azevedo, B.F.; Pereira, A.I.; Lima, J.; Costa, P. Optimizing Data Transmission in a Wireless Sensor Network Based on LoRaWAN Protocol. In Optimization, Learning Algorithms and Applications, Proceedings of the International Conference on Optimization, Bragança, Portugal, 19–21 July 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 281–293. [Google Scholar]
- Brito, T.; Azevedo, B.F.; Valente, A.; Pereira, A.I.; Lima, J.; Costa, P. Environment monitoring modules with fire detection capability based on IoT methodology. In Science and Technologies for Smart Cities, Proceedings of the International Summit Smart City 360∘, Porto, Portugal, 24–26 November 2021; Springer: Cham, Switzerland, 2021; pp. 211–227. [Google Scholar]
- Olatinwo, D.D.; Abu-Mahfouz, A.; Hancke, G. A survey on LPWAN technologies in WBAN for remote health-care monitoring. Sensors 2019, 19, 5268. [Google Scholar] [CrossRef]
- Chaudhari, B.S.; Zennaro, M.; Borkar, S. LPWAN technologies: Emerging application characteristics, requirements, and design considerations. Future Internet 2020, 12, 46. [Google Scholar] [CrossRef] [Green Version]
- Lousado, J.P.; Antunes, S. Monitoring and Support for Elderly People Using LoRa Communication Technologies: IoT Concepts and Applications. Future Internet 2020, 12, 206. [Google Scholar] [CrossRef]
- Ragnoli, M.; Colaiuda, D.; Leoni, A.; Ferri, G.; Barile, G.; Rotilio, M.; Laurini, E.; De Berardinis, P.; Stornelli, V. A LoRaWAN Multi-Technological Architecture for Construction Site Monitoring. Sensors 2022, 22, 8685. [Google Scholar] [CrossRef] [PubMed]
- Wild, T.A.; van Schalkwyk, L.; Viljoen, P.; Heine, G.; Richter, N.; Vorneweg, B.; Koblitz, J.C.; Dechmann, D.K.; Rogers, W.; Partecke, J.; et al. A multi-species evaluation of digital wildlife monitoring using the Sigfox IoT network. Res. Square 2022. [Google Scholar] [CrossRef]
- Ikonen, J.; Nelimarkka, N.; Nardelli, P.H.; Mattila, N.; Melgarejo, D.C. Experimental Evaluation of End-to-End Delay in a Sigfox Network. IEEE Netw. Lett. 2022, 4, 194–198. [Google Scholar] [CrossRef]
- Fjodorov, A.; Masood, A.; Alam, M.M.; Pärand, S. 5G Testbed Implementation and Measurement Campaign for Ground and Aerial Coverage. In Proceedings of the 2022 18th Biennial Baltic Electronics Conference (BEC), Tallinn, Estonia, 4–6 October 2022; pp. 1–6. [Google Scholar]
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS-Aided Hybrid Satellite-Terrestrial Relay Networks: Joint Beamforming Design and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- Lin, Z.; An, K.; Niu, H.; Hu, Y.; Chatzinotas, S.; Zheng, G.; Wang, J. SLNR-based Secure Energy Efficient Beamforming in Multibeam Satellite Systems. IEEE Trans. Aerosp. Electron. Syst. 2022, 1–4. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; de Cola, T.; Wang, J.B.; Zhu, W.P.; Cheng, J. Supporting IoT With Rate-Splitting Multiple Access in Satellite and Aerial-Integrated Networks. IEEE IoT J. 2021, 8, 11123–11134. [Google Scholar] [CrossRef]
- Niu, H.; Lin, Z.; Chu, Z.; Zhu, Z.; Xiao, P.; Nguyen, H.X.; Lee, I.; Al-Dhahir, N. Joint Beamforming Design for Secure RIS-Assisted IoT Networks. IEEE IoT J. 2023, 10, 1628–1641. [Google Scholar] [CrossRef]
- Navarro-Ortiz, J.; Sendra, S.; Ameigeiras, P.; Lopez-Soler, J.M. Integration of LoRaWAN and 4G/5G for the Industrial Internet of Things. IEEE Commun. Mag. 2018, 56, 60–67. [Google Scholar] [CrossRef]
- Sendra, S.; García, L.; Lloret, J.; Bosch, I.; Vega-Rodríguez, R. LoRaWAN network for fire monitoring in rural environments. Electronics 2020, 9, 531. [Google Scholar] [CrossRef] [Green Version]
- Alliance, L. A Technical Overview of LoRa and LoRaWAN. Available online: https://lora-alliance.org/resource_hub/what-is-lorawan/ (accessed on 31 December 2022).
- Friha, O.; Ferrag, M.A.; Shu, L.; Maglaras, L.; Wang, X. Internet of things for the future of smart agriculture: A comprehensive survey of emerging technologies. IEEE/CAA J. Autom. Sin. 2021, 8, 718–752. [Google Scholar] [CrossRef]
- Szewczyk, J.; Nowak, M.; Remlein, P.; Głowacka, A. LoRaWAN Communication Implementation Platforms. Int. J. Electron. Telecommun. 2022, 68, 841–854. [Google Scholar]
- Industries, T.T. The Thing Network. Available online: https://www.thethingsnetwork.org/ (accessed on 31 December 2022).
- Antunes, M.; Ferreira, L.M.; Viegas, C.; Coimbra, A.P.; de Almeida, A.T. Low-cost system for early detection and deployment of countermeasures against wild fires. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 418–423. [Google Scholar]
- Blalack, T.; Ellis, D.; Long, M.; Brown, C.; Kemp, R.; Khan, M. Low-Power Distributed Sensor Network for Wildfire Detection. In Proceedings of the 2019 SoutheastCon, Huntsville, AL, USA, 11–14 April 2019; pp. 1–3. [Google Scholar]
- Saldamli, G.; Deshpande, S.; Jawalekar, K.; Gholap, P.; Tawalbeh, L.; Ertaul, L. Wildfire Detection using Wireless Mesh Network. In Proceedings of the 2019 Fourth International Conference on Fog and Mobile Edge Computing (FMEC), Rome, Italy, 10–13 June 2019; pp. 229–234. [Google Scholar] [CrossRef]
- Ramelan, A.; Hamka Ibrahim, M.; Chico Hermanu Brillianto, A.; Adriyanto, F.; Rizqi Subeno, M.; Latifah, A. A Preliminary Prototype of LoRa-Based Wireless Sensor Network for Forest Fire Monitoring. In Proceedings of the 2021 International Conference on ICT for Smart Society (ICISS), Bandung, Indonesia, 2–4 August 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Safi, A.; Ahmad, Z.; Jehangiri, A.I.; Latip, R.; Zaman, S.K.u.; Khan, M.A.; Ghoniem, R.M. A Fault Tolerant Surveillance System for Fire Detection and Prevention Using LoRaWAN in Smart Buildings. Sensors 2022, 22, 8411. [Google Scholar] [CrossRef] [PubMed]
- ICNF. Sistema de Gestao de Informacao de Incendios. In 5º relatóRio Provisório de incêNdios Rurais—1 de Janeiro a 31 de Agosto; Divisão de Gestão do Programa de Fogos Rurais: Lisbon, Portugal, 2022. [Google Scholar]
- Brito, T.; Pereira, A.I.; Lima, J.; Castro, J.P.; Valente, A. Optimal sensors positioning to detect forest fire ignitions. In Proceedings of the Proceedings of the 9th International Conference on Operations Research and Enterprise Systems, Valletta, Malta, 22–24 February 2020; pp. 411–418. [Google Scholar]
- Semiconductor, N. Power Profiler Kit II v1.0.1—User Guide. Available online: https://infocenter.nordicsemi.com/pdf/PPK2_User_Guide_20210226.pdf (accessed on 31 December 2022).
- Kuzior, A.; Brożek, P.; Kuzmenko, O.; Yarovenko, H.; Vasilyeva, T. Countering Cybercrime Risks in Financial Institutions: Forecasting Information Trends. J. Risk Financ. Manag. 2022, 15, 613. [Google Scholar] [CrossRef]
- Chan, K.Y.; Dillon, T.S.; Singh, J.; Chang, E. Neural-Network-Based Models for Short-Term Traffic Flow Forecasting Using a Hybrid Exponential Smoothing and Levenberg–Marquardt Algorithm. IEEE Trans. Intell. Transp. Syst. 2012, 13, 644–654. [Google Scholar] [CrossRef]
- Usaratniwart, E.; Sirisukprasert, S. Adaptive enhanced linear exponential smoothing technique to mitigate photovoltaic power fluctuation. In Proceedings of the 2016 IEEE Innovative Smart Grid Technologies-Asia (ISGT-Asia), Melbourne, Australia, 1 December 2016; pp. 712–717. [Google Scholar]
- Balouji, E.; Salor, O.; Ermis, M. Exponential Smoothing of Multiple Reference Frame Components With GPUs for Real-Time Detection of Time-Varying Harmonics and Interharmonics of EAF Currents. IEEE Trans. Ind. Appl. 2018, 54, 6566–6575. [Google Scholar] [CrossRef]
- Mahajan, S.; Chen, L.J.; Tsai, T.C. Short-term PM2.5 forecasting using exponential smoothing method: A comparative analysis. Sensors 2018, 18, 3223. [Google Scholar] [CrossRef] [Green Version]
- Gardner, E.S., Jr. Exponential smoothing: The state of the art. J. Forecast. 1985, 4, 1–28. [Google Scholar] [CrossRef]
- Gardner, E.S., Jr. Exponential smoothing: The state of the art—Part II. Int. J. Forecast. 2006, 22, 637–666. [Google Scholar] [CrossRef]
- Siregar, B.; Butar-Butar, I.; Rahmat, R.; Andayani, U.; Fahmi, F. Comparison of exponential smoothing methods in forecasting palm oil real production. In Proceedings of the Journal of Physics: Conference Series; IOP Publishing: Bristol, UK, 2017; Volume 801, p. 012004. [Google Scholar]
- Nguyen, T.; Qin, X.; Dinh, A.; Bui, F. Low resource complexity R-peak detection based on triangle template matching and moving average filter. Sensors 2019, 19, 3997. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Makridakis, S.; Wheelwright, S.C.; Hyndman, R.J. Forecasting: Methods and Applications; John Wiley & Sons: New York, NY, USA, 1998. [Google Scholar]
- Bhandari, S.; Bergmann, N.; Jurdak, R.; Kusy, B. Time series data analysis of wireless sensor network measurements of temperature. Sensors 2017, 17, 1221. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yu, S.; Liu, S. A novel adaptive recursive least squares filter to remove the motion artifact in seismocardiography. Sensors 2020, 20, 1596. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Zhang, Y.; Wang, R.; Li, S.; Qi, S. Temperature sensor denoising algorithm based on curve fitting and compound kalman filtering. Sensors 2020, 20, 1959. [Google Scholar] [CrossRef] [PubMed]
- Salkind, N.E. Encyclopedia of Measurement and Statistics; Sage: New York, NY, USA, 2007. [Google Scholar]


















| Module | Ground [m] | Bonfire [m] |
|---|---|---|
| Node 1 | 1.12 | 3.70 |
| Node 2 | 1.37 | 3.70 |
| Node 3 | 1.60 | 3.70 |
| Node 4 | 1.12 | 3.60 |
| Node 5 | 1.37 | 3.60 |
| Node 6 | 1.60 | 3.60 |
| Node 7 | 1.37 | 3.50 |
| Node 8 | 1.60 | 3.50 |
| Node 9 | 1.37 | 3.90 |
| Node 10 | 1.60 | 3.90 |
| Date [HH:mm] | Battery [V] | Humidty [%] | Temperature [ºC] | Flame Sensor 1 | Flamse Sensor 2 | Flame Sensor 3 | Flame Sensor 4 | Flame Sensor 5 | WSE (Fire) |
|---|---|---|---|---|---|---|---|---|---|
| Day 1 00:01 | 3.82 | 75 | 10 | 42 | 45 | 42 | 55 | 40 | False |
| Day 1 00:02 | 3.82 | 75 | 10 | 44 | 41 | 44 | 56 | 42 | False |
| … | … | … | … | … | … | … | … | … | … |
| Day 5 12:02 | 3.63 | 56 | 19 | 46 | 45 | 46 | 64 | 46 | True |
| Day 5 12:03 | 3.63 | 51 | 19 | 40 | 38 | 39 | 47 | 39 | True |
| … | … | … | … | … | … | … | … | .. | … |
| Day 20 23:58 | 3.48 | 70 | 17 | 1023 | 1023 | 1023 | 1023 | 1023 | False |
| Day 20 23:59 | 3.48 | 71 | 17 | 1023 | 1023 | 1023 | 1022 | 1023 | False |
| Approach | Variables | Values | Results with WSE |
|---|---|---|---|
| ;D | (0.7;0.1) | 0.834630350 | |
| (0.2;0.1) | 0.834630350 | ||
| (0.3;0.1) | 0.832684825 | ||
| (0.4;0.1) | 0.831712062 | ||
| (0.8;0.1) | 0.829766537 | ||
| n,D | (6;0.0) | 0.727626459 | |
| (6;0.0) | 0.709143969 | ||
| (8;0.0) | 0.696498054 | ||
| (8;0.05) | 0.458171206 | ||
| (8;0.1) | 0.458171206 | ||
| ,,D | (5;6;0.0) | 0.999027237 | |
| (4;6;1.0) | 0.999027237 | ||
| (3;6;3.0) | 0.999027237 | ||
| (2;6;7.0) | 0.999027237 | ||
| (2;4;6.0) | 0.998054475 | ||
| D | 0.2 | 0.795719844 | |
| 0.0 | 0.795719844 | ||
| 0.1 | 0.795719844 | ||
| 0.3 | 0.795719844 | ||
| 0.6 | 0.627431907 |
| Combination | WSE Intervals | Variable | Result | False Alert 1 | ||||
|---|---|---|---|---|---|---|---|---|
| Max. | Min. | Max. | Min. | |||||
| (; ) (; ) (; ; ) () | (; ) (; ) (; ; ) () | 0.60 | 0.45 | 0.60 | 0.38 | |||
| (; ) (; ; ) () | (; ) (; ; ) () | 0.69 | 0.57 | 0.46 | 0.47 | |||
| (; ) (; ; ) () | (; ) (; ; ) () | 0.69 | 0.61 | 0.42 | 0.42 | |||
| (; ) (; ) () | (; ) (; ) () | 0.60 | 0.45 | 0.38 | 0.38 | |||
| (; ) (; ) (; ; ) | (; ) (; ) (; ; ) | 0.73 | 0.54 | 0.50 | 0.50 | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Brito, T.; Azevedo, B.F.; Mendes, J.; Zorawski, M.; Fernandes, F.P.; Pereira, A.I.; Rufino, J.; Lima, J.; Costa, P. Data Acquisition Filtering Focused on Optimizing Transmission in a LoRaWAN Network Applied to the WSN Forest Monitoring System. Sensors 2023, 23, 1282. https://doi.org/10.3390/s23031282
Brito T, Azevedo BF, Mendes J, Zorawski M, Fernandes FP, Pereira AI, Rufino J, Lima J, Costa P. Data Acquisition Filtering Focused on Optimizing Transmission in a LoRaWAN Network Applied to the WSN Forest Monitoring System. Sensors. 2023; 23(3):1282. https://doi.org/10.3390/s23031282
Chicago/Turabian StyleBrito, Thadeu, Beatriz Flamia Azevedo, João Mendes, Matheus Zorawski, Florbela P. Fernandes, Ana I. Pereira, José Rufino, José Lima, and Paulo Costa. 2023. "Data Acquisition Filtering Focused on Optimizing Transmission in a LoRaWAN Network Applied to the WSN Forest Monitoring System" Sensors 23, no. 3: 1282. https://doi.org/10.3390/s23031282