Three-Dimensional Single Random Phase Encryption
Abstract
1. Introduction
2. Three-Dimensional Double Random Phase Encryption
2.1. Double Random Phase Encryption
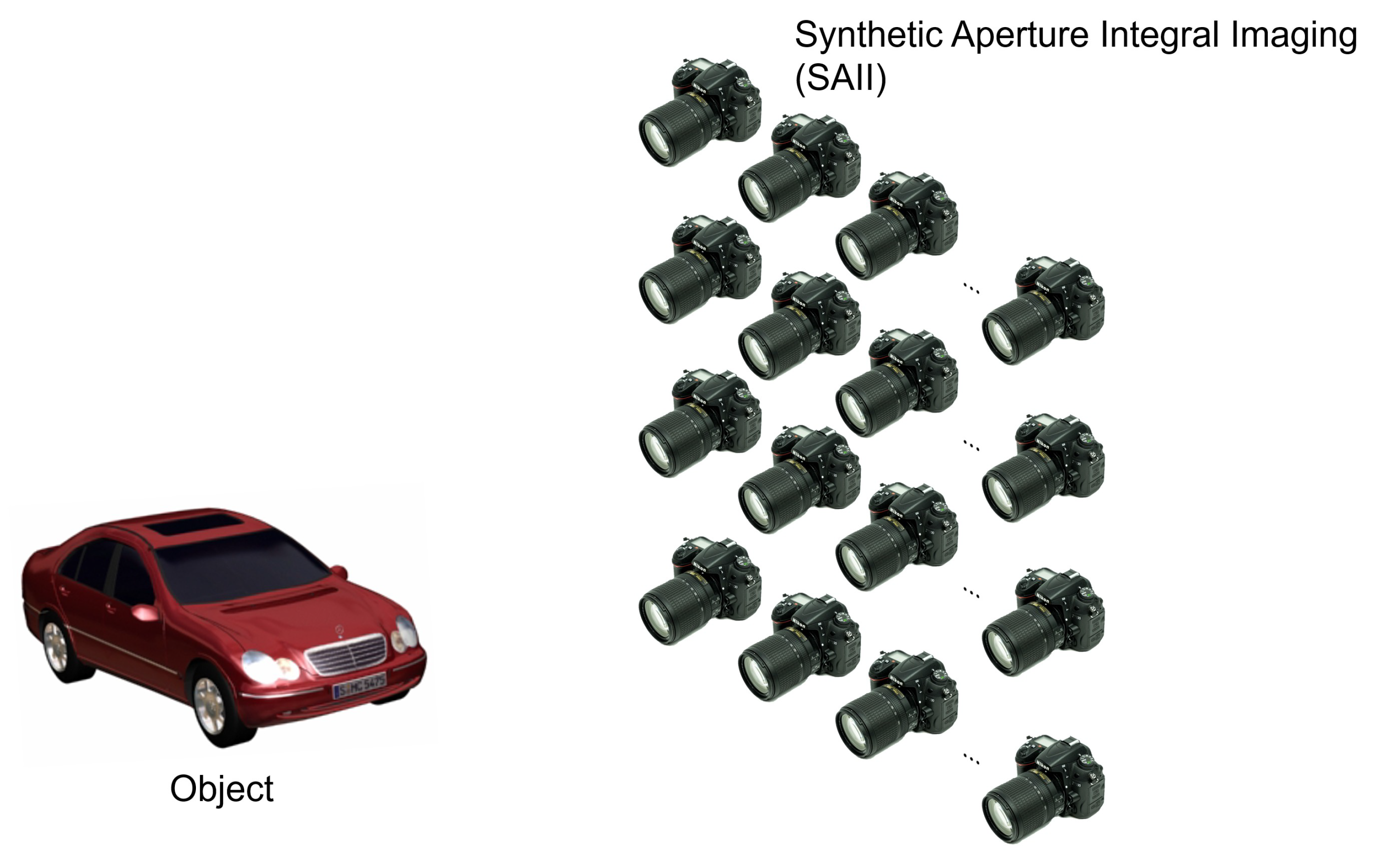
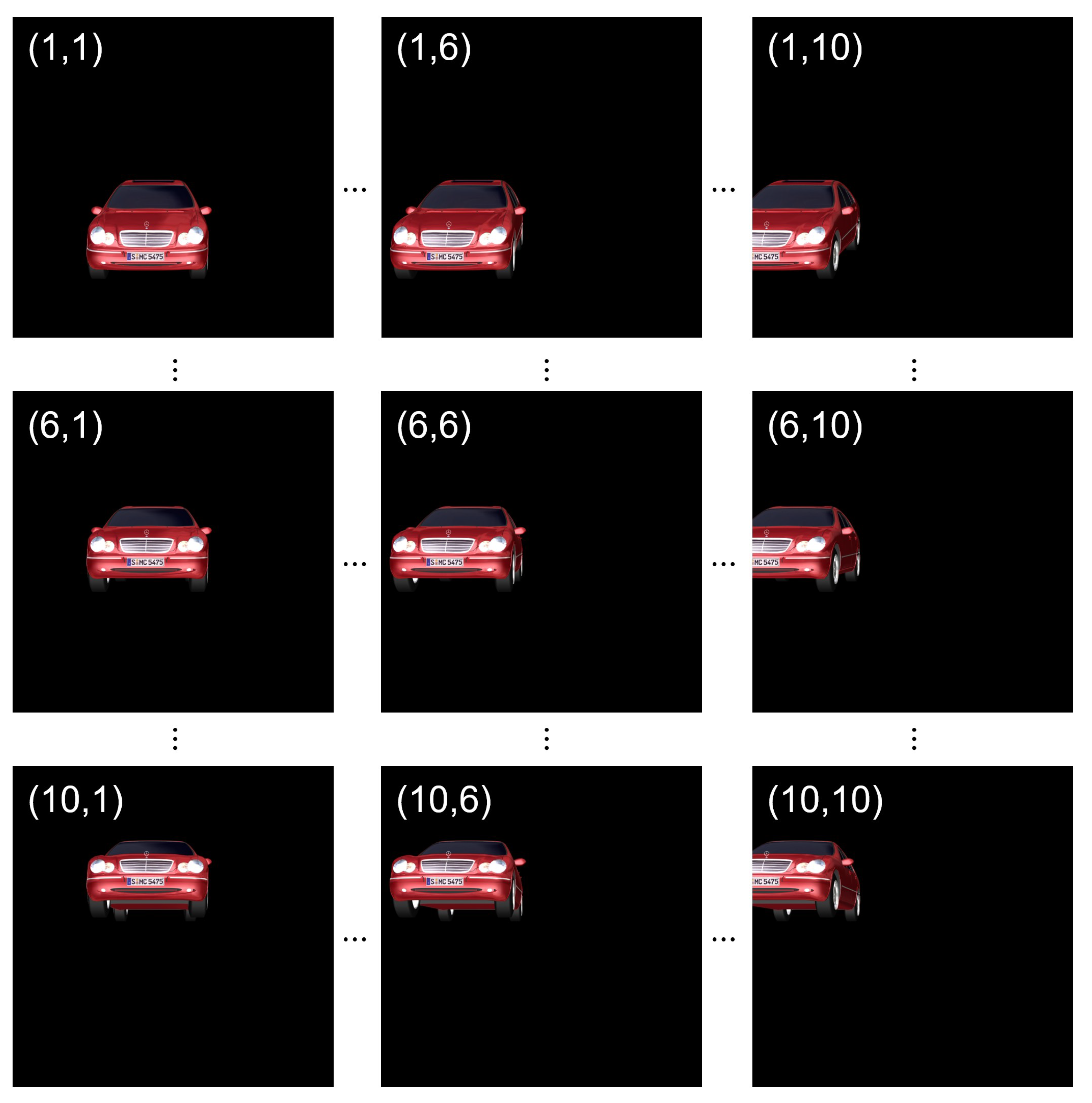
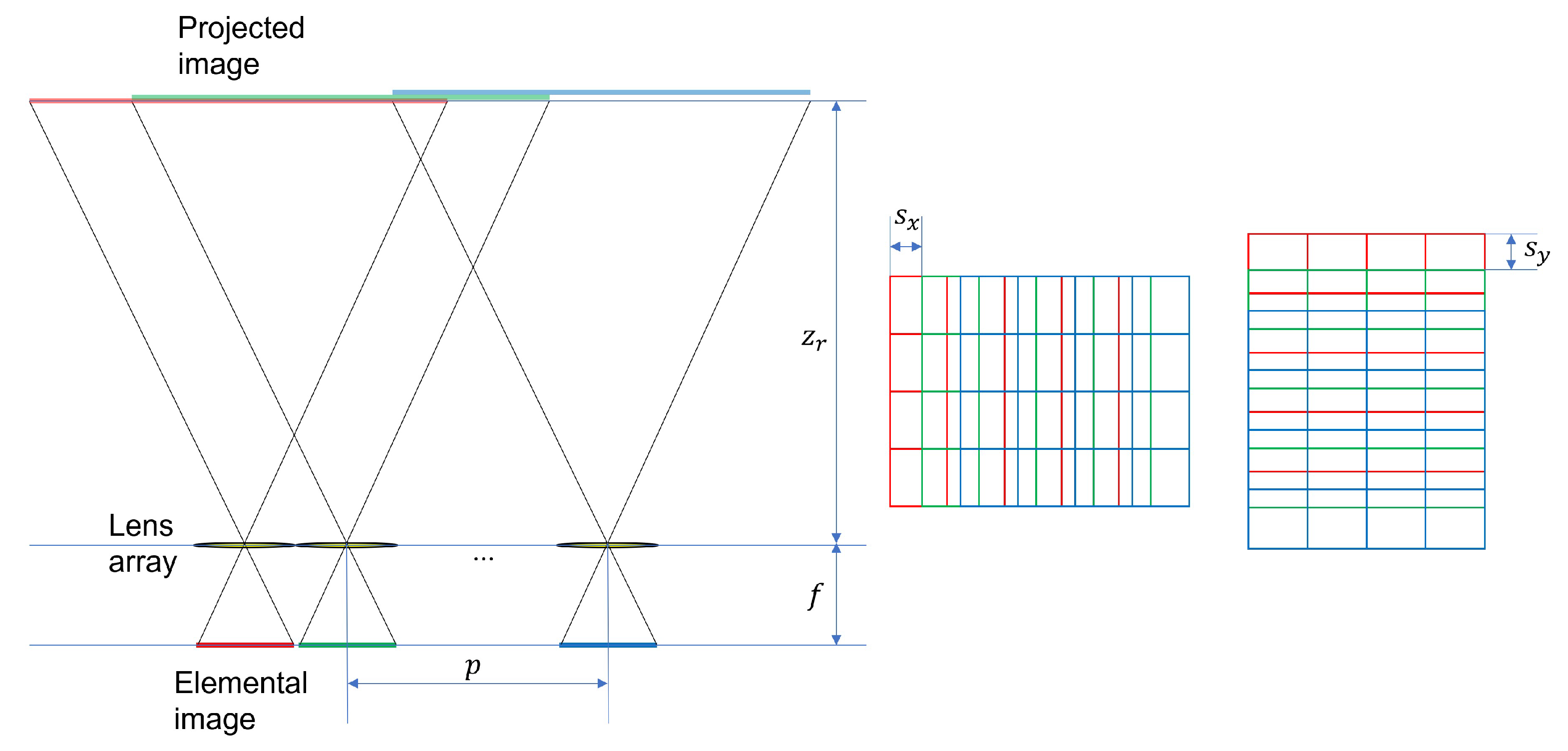
2.2. Integral Imaging and Three-Dimensional Double Random Phase Encryption
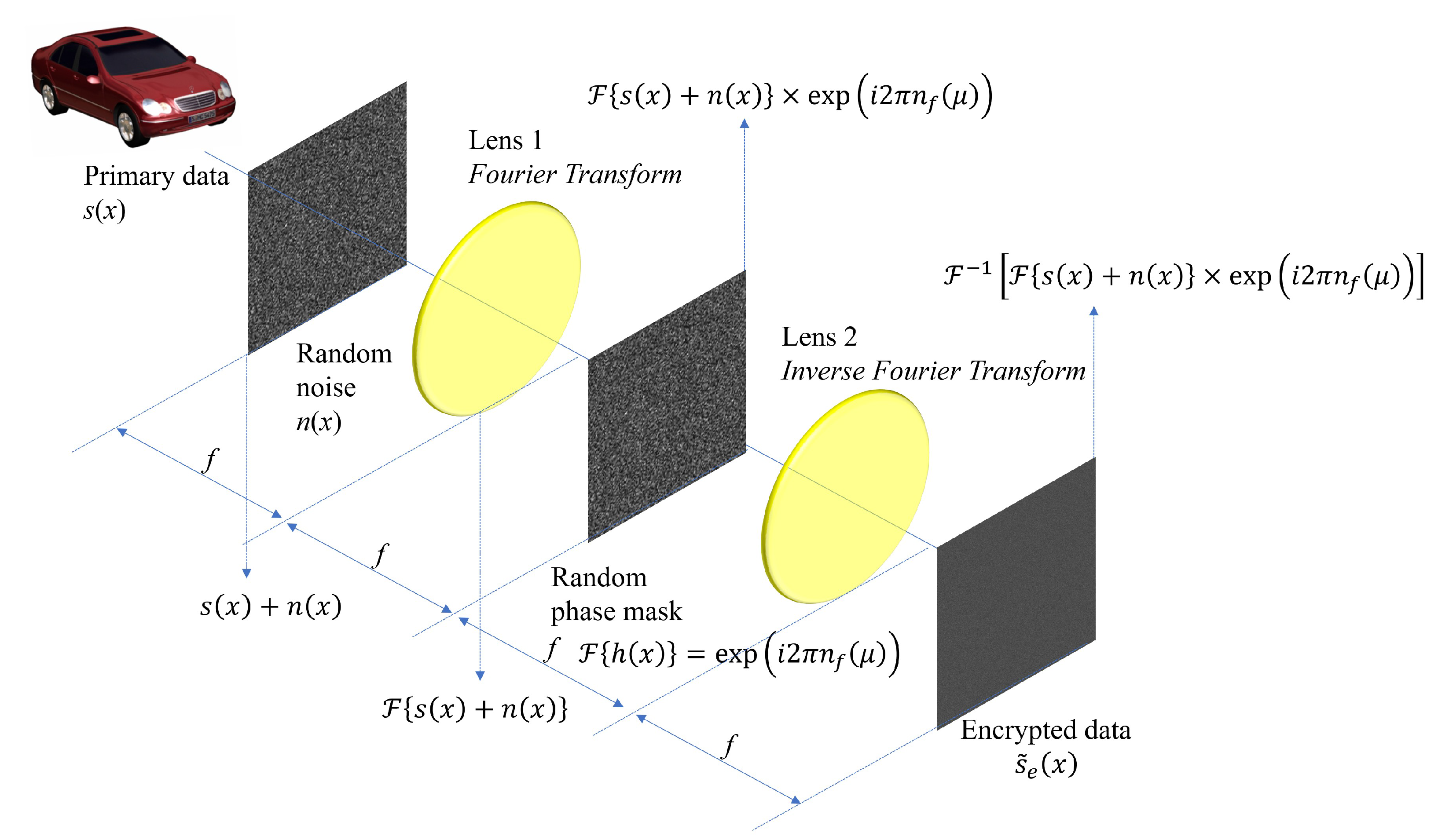
3. Three-Dimensional Single Random Phase Encryption
3.1. Principle of Three-Dimensional Single Random Phase Encryption
3.2. Computational Procedure of Three-Dimensional Single Random Phase Encryption
| Algorithm 1: Single Random Phase Encryption |
|
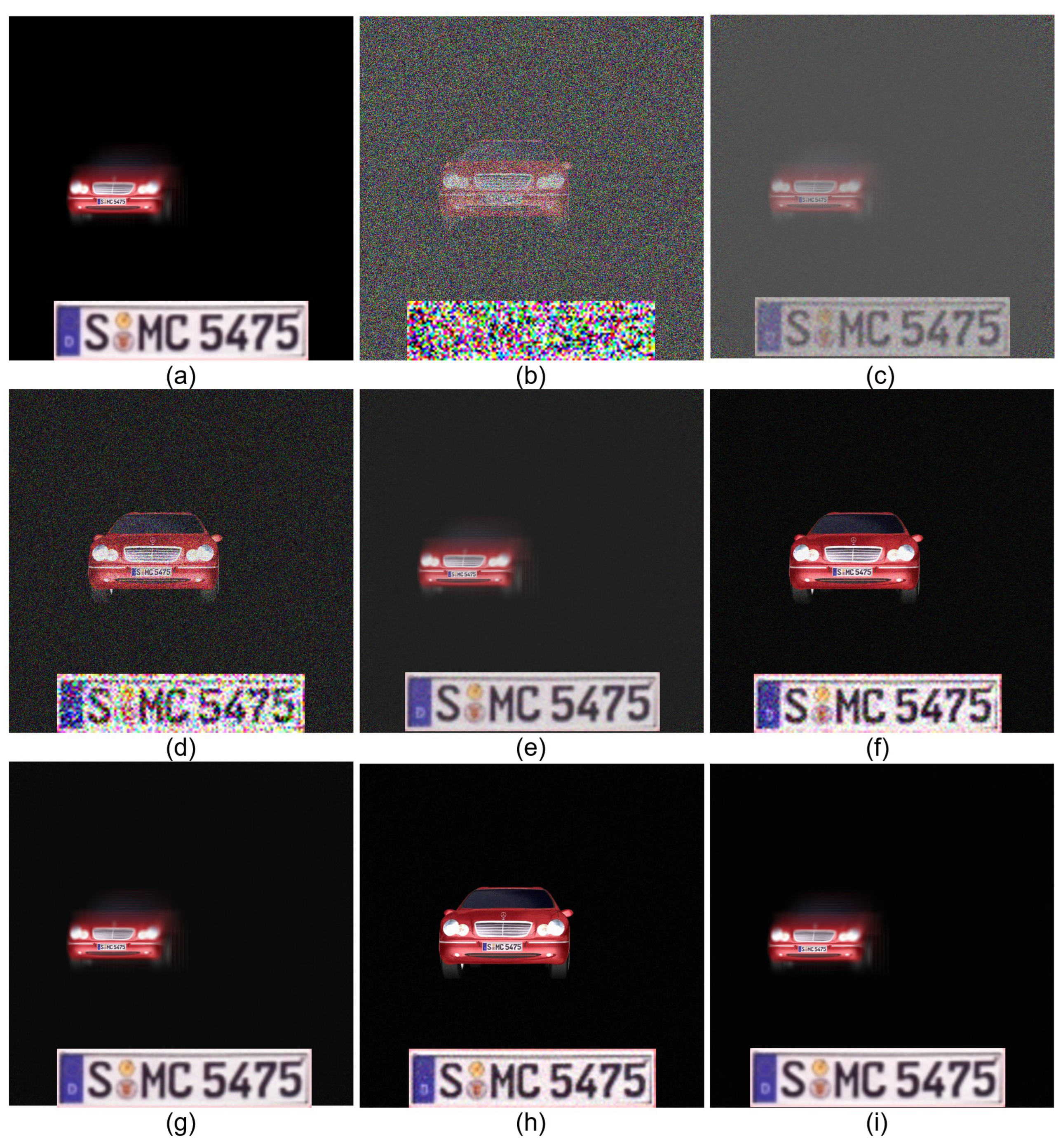
4. Simulation Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AI | Artificially intelligence |
| AWGN | Additive white Gaussian noise |
| CCD | Charge-coupled device |
| DRPE | Double random phase encryption |
| MLE | Maximum likelihood estimation |
| PSR | Peak sidelobe ratio |
| SAII | Synthetic aperture integral imaging |
| SRPE | Single random phase encryption |
| SSIM | Structural similarity |
| VCR | Volumetric computational reconstruction |
References
- Javidi, B.; Horner, J.L. Optical pattern recognition for validation and security verification. Opt. Eng. 1994, 33, 1752–1756. [Google Scholar] [CrossRef]
- Refregier, P.; Javidi, B. Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 1995, 20, 767–769. [Google Scholar] [CrossRef] [PubMed]
- Matoba, O.; Javidi, B. Encrypted optical memory system using three-dimensional keys in the Fresnel domain. Opt. Lett. 1999, 24, 762–764. [Google Scholar] [CrossRef] [PubMed]
- Tan, X.; Matoba, O.; Okada-Sudo, Y.; Ide, M.; Shimura, T.; Kuroda, K. Secure optical memory system with polarization encryption. Appl. Opt. 2001, 40, 2310–2315. [Google Scholar] [CrossRef] [PubMed]
- Javidi, B.; Nomura, T. Securing information by use of digital holography. Opt. Lett. 2000, 25, 28–30. [Google Scholar] [CrossRef] [PubMed]
- Mogensen, P.C.; Gluckstad, J. Phase-only optical encryption. Opt. Lett. 2000, 25, 566–568. [Google Scholar] [CrossRef] [PubMed]
- Goudail, F.; Bollaro, F.; Javidi, B.; Refregier, P. Influence of a perturbation in a double random phase encoding system. JOSA A 1998, 15, 2629–2638. [Google Scholar] [CrossRef]
- Matoba, O.; Nomura, T.; Perez-Cabre, E.; Millan, M.S.; Javidi, B. Optical techniques for information security. Proc. IEEE 2009, 97, 1128–1148. [Google Scholar] [CrossRef]
- Carnicer, A.; Montes-Usategui, M.; Arcos, S.; Juvells, I. Vulnerability to chosen-cyphertext attacks of optical encryption schemes based on double random phase keys. Opt. Lett. 2005, 30, 1644–1646. [Google Scholar] [CrossRef]
- Clemente, P.; Duran, V.; Torres-Company, V.; Tajahuerce, E.; Lancis, J. Optical encryption based on computational ghost imaging. Opt. Lett. 2010, 35, 2391–2393. [Google Scholar] [CrossRef]
- Liao, M.; Zheng, S.; Pan, S.; Lu, D.; He, W.; Situ, G.; Peng, X. Deep-learning-based ciphertext-only attack on optical double random phase encryption. Opto-Elec. Adv. 2021, 4, 200016. [Google Scholar] [CrossRef]
- Tian, P.; Su, R. A novel virtual optical image encryption scheme created by combining chaotic S-Box with double random phase encoding. Sensors 2022, 22, 5325. [Google Scholar] [CrossRef] [PubMed]
- Li, M.; Wang, M.; Fan, H.; Liu, Y.; Zhang, H.; Nan, H. On the security of image cryptosystems using DRPE based on scrambling and diffusion. Opt. Quan. Elec. 2024, 56, 241. [Google Scholar] [CrossRef]
- Perez-Cabre, E.; Cho, M.; Javidi, B. Information authentication using photon-counting double-random-phase encrypted images. Opt. Lett. 2011, 36, 22–24. [Google Scholar] [CrossRef]
- Markman, A.; Javidi, B.; Tehranipoor, M. Photon-counting security tagging and verification using optically encoded QR codes. IEEE. Photo. J. 2013, 6, 1–9. [Google Scholar] [CrossRef]
- Markman, A.; Javidi, B. Full-phase photon-counting double-random-phase encryption. JOSA A 2014, 31, 394–403. [Google Scholar] [CrossRef]
- Cho, M.; Javidi, B. Three-dimensional photon counting double-random-phase encryption. Opt. Lett. 2013, 38, 3198–3201. [Google Scholar] [CrossRef]
- Fragkos, G.; Minwalla, C.; Plusquellic, J.; Tsiropoulou, E.E. Artificially intelligent electronic money. IEEE Con. Elec. Mag. 2020, 10, 81–89. [Google Scholar] [CrossRef]
- Hong, S.-H.; Jang, J.-S.; Javidi, B. Three-dimensional volumetric object reconstruction using computational integral imaging. Opt. Exp. 2004, 12, 483–491. [Google Scholar] [CrossRef]
- Cho, B.; Kopycki, P.; Martinez-Corral, M.; Cho, M. Computational volumetric reconstruction of integral imaging with improved depth resolution considering continuously non-uniform shifting pixels. Opt. Laser Eng. 2018, 111, 114–121. [Google Scholar] [CrossRef]
- Jang, J.-S.; Javidi, B. Three-dimensional synthetic aperture integral imaging. Opt. Lett. 2002, 27, 1144–1146. [Google Scholar] [CrossRef] [PubMed]
- Javidi, B. Nonlinear joint power spectrum based optical correlation. Appl. Opt. 1989, 28, 2358–2367. [Google Scholar] [CrossRef] [PubMed]


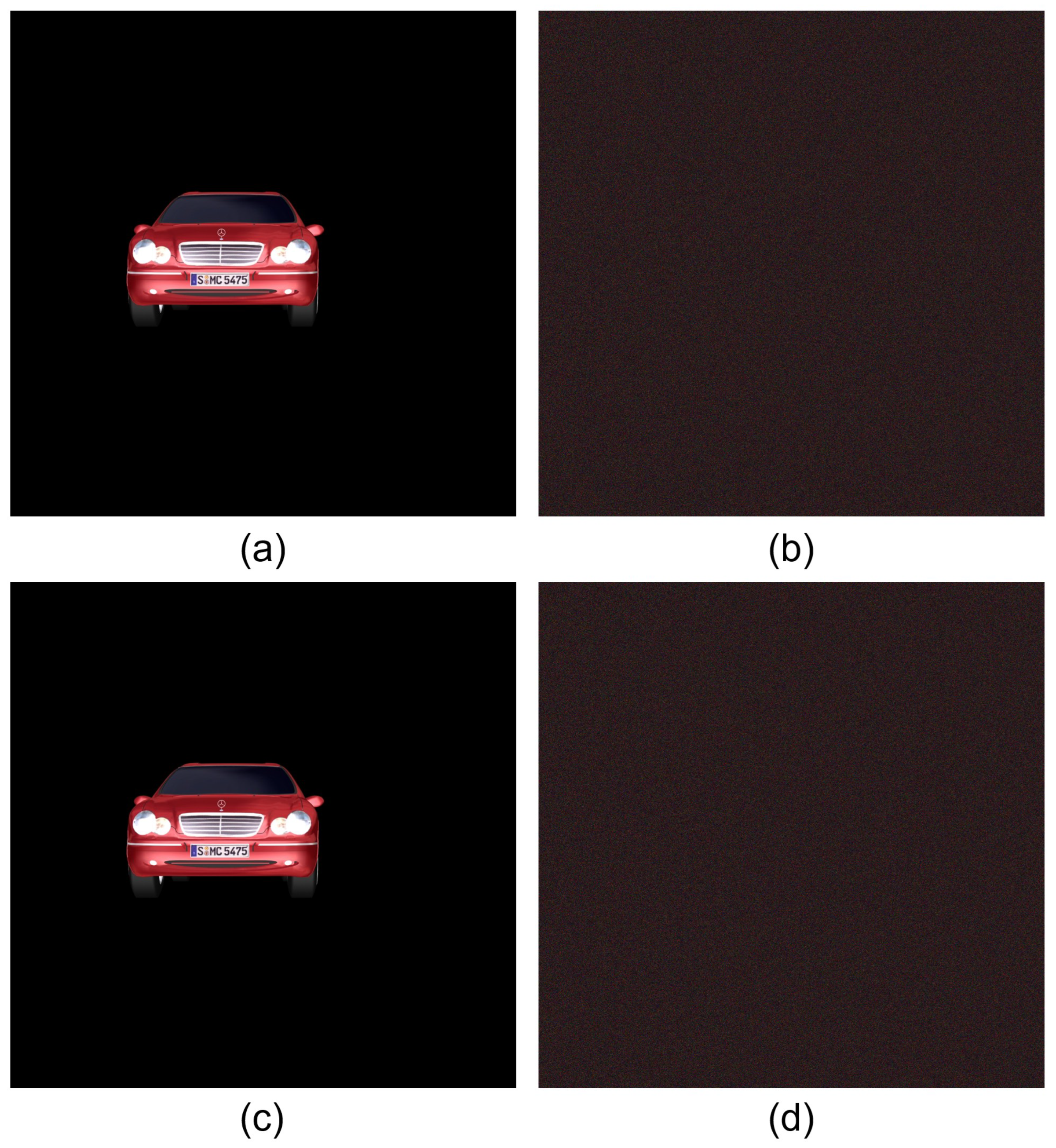







| 0.1319 | 0.4893 | 0.8710 | 0.9823 |
| 2D | 3D | 3D/2D (Times) | |
|---|---|---|---|
| N = 1 | 0.1319 | 0.6176 | 4.68 |
| N = 10 | 0.4893 | 0.9536 | 1.95 |
| N = 100 | 0.8710 | 0.9968 | 1.14 |
| N = 1000 | 0.9823 | 1.0000 | 1.02 |
| CPU | RAM | Software | OS |
|---|---|---|---|
| AMD Ryzen 7 3700X | 32 GB | MATLAB 2023a | Windows 11 Pro |
| Generation | Elemental Images | DRPE | SRPE | ||
|---|---|---|---|---|---|
| Encryption (Second) | Decryption (Second) | Encryption (Second) | Decryption (Second) | ||
| N = 1 | 1 | 0.217534 | 0.0863 | 0.211983 | 0.0773 |
| 100 | 17.666209 | 8.0791 | 16.533440 | 7.5473 | |
| N = 10 | 1 | 1.589549 | 0.7458 | ||
| 100 | 153.771801 | 73.8643 | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cho, B.; Cho, M. Three-Dimensional Single Random Phase Encryption. Sensors 2024, 24, 1952. https://doi.org/10.3390/s24061952
Cho B, Cho M. Three-Dimensional Single Random Phase Encryption. Sensors. 2024; 24(6):1952. https://doi.org/10.3390/s24061952
Chicago/Turabian StyleCho, Byungwoo, and Myungjin Cho. 2024. "Three-Dimensional Single Random Phase Encryption" Sensors 24, no. 6: 1952. https://doi.org/10.3390/s24061952
APA StyleCho, B., & Cho, M. (2024). Three-Dimensional Single Random Phase Encryption. Sensors, 24(6), 1952. https://doi.org/10.3390/s24061952






