An Interdisciplinary Overview on Ambient Assisted Living Systems for Health Monitoring at Home: Trade-Offs and Challenges
Abstract
1. Introduction
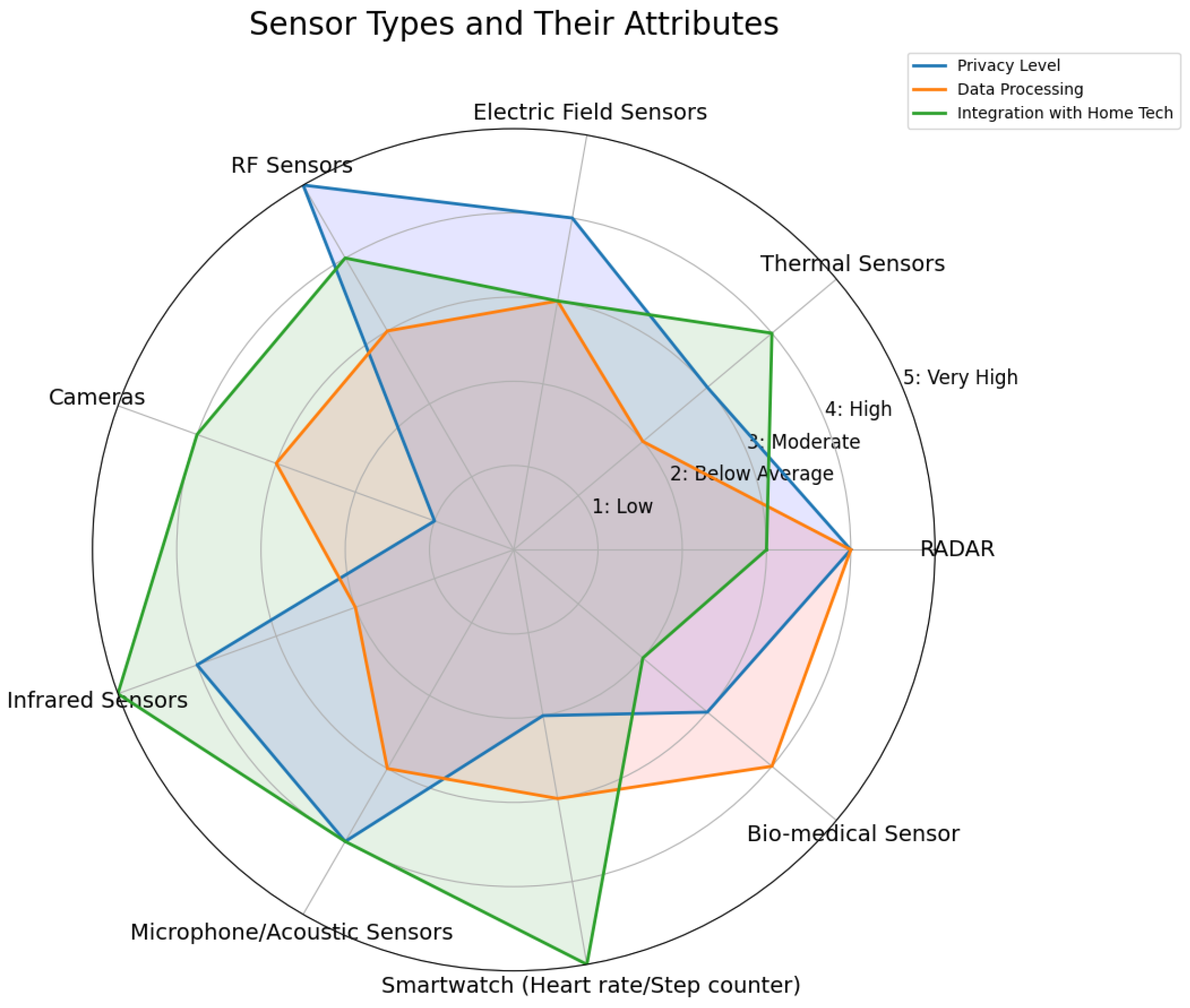
2. AAL Sensors
2.1. AAL Sensor Classification
2.1.1. Contact Direct Devices (Body-Worn Sensors)
2.1.2. Non-Contact Direct Devices (Ambient Sensors)
2.1.3. In-Direct Devices
2.2. Data Types in AAL Environment
- Behavioral Data: Presence, Activity Duration, and Levels: monitored using ambient sensors such as motion detectors, contact sensors, and pressure sensors.
- Functional Data: Gait Velocity and Step Time: these are assessed through depth video analysis. Walking Speed: estimated using passive Iifrared motion sensors.
- Bio (Physiological) Data: Heart Rate: monitored using ballistocardiography (BCG) sensors like pressure or bed sensors, or through electrocardiogram (ECG) electrodes, which can be dry or capacitive. Respiration Rate: tracked via bed sensors. Body Temperature: measured with an infrared thermometer.
- Environmental Data: Air Quality: Includes gas concentrations and humidity levels, monitored through air sensors. Sound Levels: Captured by sound sensors to assess the ambient noise environment.
2.3. Sensing Challenges and Trade-Offs
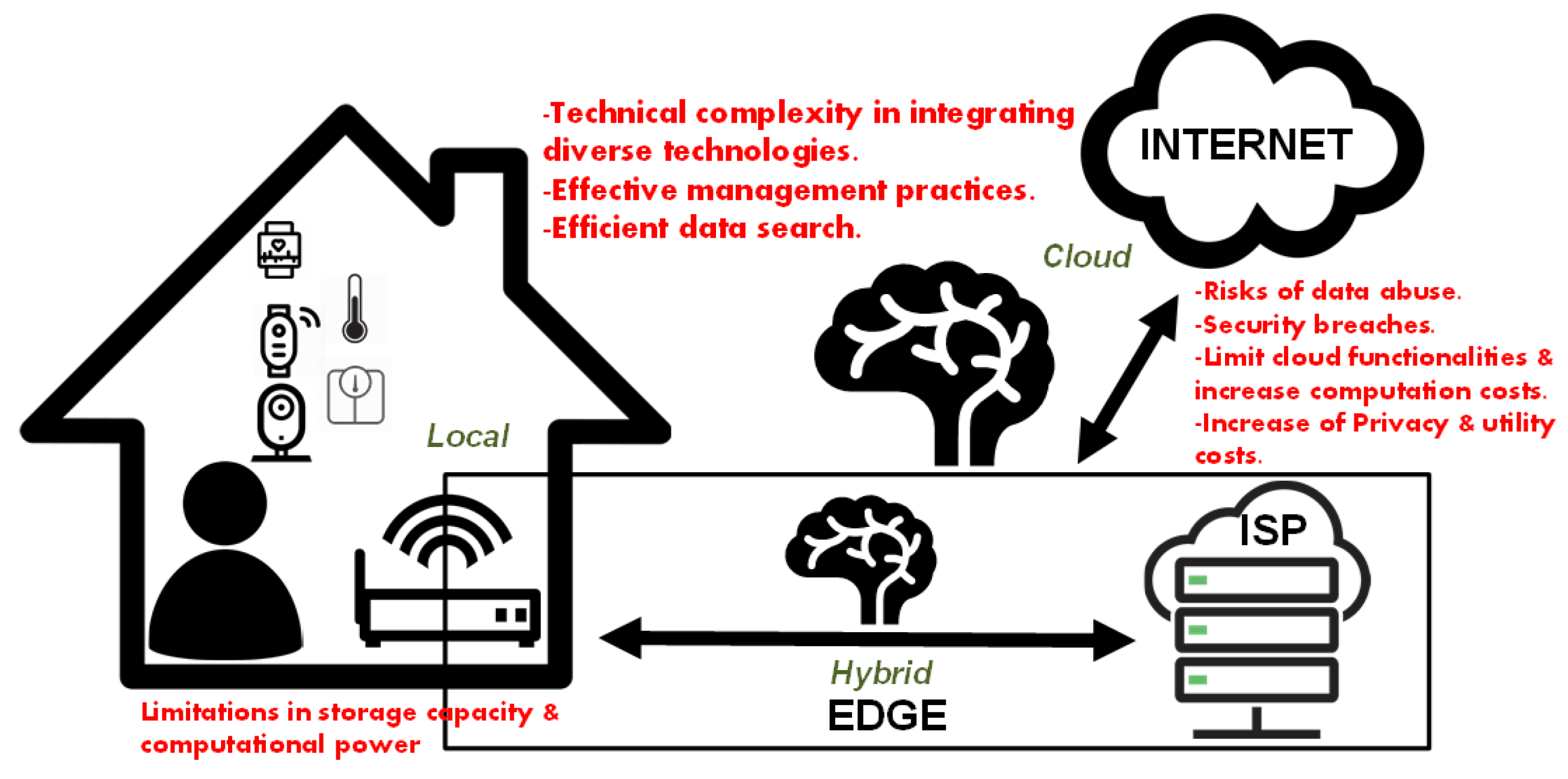
3. Data Management, Storage, and Communication
3.1. Data Management, Network Structure, and Communication
Communication Protocols
3.2. Data and Communication Challenges and Trade-Offs
3.2.1. Privacy, Security, and Data Management
3.2.2. Privacy and Data Quality
4. Decision-Making Process
4.1. Decision-Making Challenges and Trade-Offs
4.1.1. Privacy
4.1.2. AI-Related Challenges
4.1.3. Cyber–Physical Security
5. AAL System Challenges and Trade-Offs
5.1. Privacy and Security
5.1.1. Privacy
5.1.2. Security
5.1.3. Regulatory Laws and Compliance
| Regulatory Approval and Key Regulatory Bodies | Device Type and Estimated Cost Range | Performance Metrics | Key Challenges and Requirements |
|---|---|---|---|
| MDR CE (EU) Medical Device Coordination Group (MDCG) [158,159] | Wearables, Sensors, Medical Devices Cost: EUR 5000–50,000 for Class I (low-risk, self-certification) to over EUR 150,000 for high-risk Class III devices. | Accuracy, Reliability, Data Integration, Long-term Safety | Stringent clinical trials, performance evaluations, and documentation required for market approval. High workload for notified bodies delays market entry. Additional costs for post-market surveillance. |
| FDA (US) Food and Drug Administration (FDA) [160] | Wearables, Sensors, Medical Devices Cost: USD 1000–10,000 for Class I (low-risk) devices to USD 2,000,000+ for high-risk devices. | Clinical Accuracy, Health Metrics | Requires premarket approval (PMA) or 510(k) clearance. High-risk devices demand extensive clinical evidence. Post-market surveillance emphasized through Medical Device Reporting (MDR) system. |
| MHRA (UK) Medicines and Healthcare products Regulatory Agency (MHRA) [161] | Wearables, Medical Devices Cost: GBP 1000–5000 for low-risk Class I devices and up to GBP 100,000+ for medium-risk devices. | Durability, Usability, Safety | Ensures compliance with performance standards and conducts regular audits. Challenges include meeting evolving regulations and maintaining continuous surveillance. |
| ISO 13485 (Quality) Global Standard [162] | Medical and Health-Monitoring Devices Cost: USD 5000–30,000 | Durability, Usability, Safety | Focuses on quality system compliance, risk management, and operational effectiveness. Requires comprehensive documentation and compliance auditing, which can be resource-intensive. |
| Data Privacy Standards GDPR (EU) [163], HIPAA [164] (US) | Wearables, IoT Medical Devices Variable Cost | Data Integrity, Encryption | Compliance with regional data privacy laws. Challenges with cloud-based storage, patient consent, and ensuring data sovereignty. |
5.2. Performance, Reliability, and Integration
5.3. Cost
5.3.1. Financial
5.3.2. Energy Consumption, Storage, and AI
5.4. Usability and User Friendliness
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Consel, C.; Jeffrey, A. Aging with the Internet of Things. Bridge 2019, 49, 6–12. [Google Scholar]
- Zhou, H.; Hu, H. Inertial sensors for motion detection of human upper limbs. Sens. Rev. 2007, 27, 151–158. [Google Scholar] [CrossRef]
- Yan, T.; Wang, Z.; Pan, Z.J. Flexible strain sensors fabricated using carbon-based nanomaterials: A review. Curr. Opin. Solid State Mater. Sci. 2018, 22, 213–228. [Google Scholar] [CrossRef]
- Igual, R.; Medrano, C.; Plaza, I. Challenges, issues and trends in fall detection systems. Biomed. Eng. Online 2013, 12, 66. [Google Scholar] [CrossRef]
- Cardenas, J.D.; Gutierrez, C.A.; Aguilar-Ponce, R. Deep learning multi-class approach for human fall detection based on doppler signatures. Int. J. Environ. Res. Public Health 2023, 20, 1123. [Google Scholar] [CrossRef]
- Marco, A.; Casas, R.; Falco, J.; Gracia, H.; Artigas, J.I.; Roy, A. Location-based services for elderly and disabled people. Comput. Commun. 2008, 31, 1055–1066. [Google Scholar] [CrossRef]
- Panagiotou, C.; Panagiotakopoulos, T.; Kameas, A. A multi: Modal Decision Making System for an Ambient Assisted Living Environment. In Proceedings of the 8th ACM International Conference on Pervasive Technologies Related to Assistive Environments, Corfu, Greece, 1–3 July 2015; pp. 1–8. [Google Scholar]
- Blasco, R.; Marco, Á.; Casas, R.; Cirujano, D.; Picking, R. A smart kitchen for ambient assisted living. Sensors 2014, 14, 1629–1653. [Google Scholar] [CrossRef]
- Kim, J.; Campbell, A.S.; de Ávila, B.E.F.; Wang, J. Wearable biosensors for healthcare monitoring. Nat. Biotechnol. 2019, 37, 389–406. [Google Scholar] [CrossRef]
- Karimi-Maleh, H.; Orooji, Y.; Karimi, F.; Alizadeh, M.; Baghayeri, M.; Rouhi, J.; Tajik, S.; Beitollahi, H.; Agarwal, S.; Gupta, V.K.; et al. A critical review on the use of potentiometric based biosensors for biomarkers detection. Biosens. Bioelectron. 2021, 184, 113252. [Google Scholar] [CrossRef]
- Krishnan, S.K.; Singh, E.; Singh, P.; Meyyappan, M.; Nalwa, H.S. A review on graphene-based nanocomposites for electrochemical and fluorescent biosensors. RSC Adv. 2019, 9, 8778–8881. [Google Scholar] [CrossRef]
- Aldeer, M.; Javanmard, M.; Martin, R.P. A review of medication adherence monitoring technologies. Appl. Syst. Innov. 2018, 1, 14. [Google Scholar] [CrossRef]
- Ahmad, I.; Asghar, Z.; Kumar, T.; Li, G.; Manzoor, A.; Mikhaylov, K.; Shah, S.A.; Höyhtyä, M.; Reponen, J.; Huusko, J.; et al. Emerging technologies for next generation remote health care and assisted living. IEEE Access 2022, 10, 56094–56132. [Google Scholar] [CrossRef]
- Shetti, N.P.; Bukkitgar, S.D.; Reddy, K.R.; Reddy, C.V.; Aminabhavi, T.M. ZnO-based nanostructured electrodes for electrochemical sensors and biosensors in biomedical applications. Biosens. Bioelectron. 2019, 141, 111417. [Google Scholar] [CrossRef] [PubMed]
- Wang, J.; Bauer, J.; Becker, M.; Bente, P.; Dasenbrock, L.; Elbers, K.; Hein, A.; Kohlmann, M.; Kolb, G.; Lammel-Polchau, C.; et al. A novel approach for discovering human behavior patterns using unsupervised methods. Z. Gerontol. Geriatr. 2014, 47. [Google Scholar] [CrossRef]
- Wang, J.; Spicher, N.; Warnecke, J.M.; Haghi, M.; Schwartze, J.; Deserno, T.M. Unobtrusive health monitoring in private spaces: The smart home. Sensors 2021, 21, 864. [Google Scholar] [CrossRef]
- McGrath, M.J.; Scanaill, C.N. Sensor Technologies: Healthcare, Wellness, and Environmental Applications; Springer Nature: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Addante, F.; Gaetani, F.; Patrono, L.; Sancarlo, D.; Sergi, I.; Vergari, G. An innovative AAL system based on IoT technologies for patients with sarcopenia. Sensors 2019, 19, 4951. [Google Scholar] [CrossRef]
- Landi, F.; Liperoti, R.; Russo, A.; Giovannini, S.; Tosato, M.; Capoluongo, E.; Bernabei, R.; Onder, G. Sarcopenia as a risk factor for falls in elderly individuals: Results from the ilSIRENTE study. Clin. Nutr. 2012, 31, 652–658. [Google Scholar] [CrossRef]
- Xiao, Z.; Xiao, Y. Security and privacy in cloud computing. IEEE Commun. Surv. Tutor. 2012, 15, 843–859. [Google Scholar] [CrossRef]
- Dasios, A.; Gavalas, D.; Pantziou, G.; Konstantopoulos, C. Hands-on experiences in deploying cost-effective ambient-assisted living systems. Sensors 2015, 15, 14487–14512. [Google Scholar] [CrossRef]
- Tunca, C.; Alemdar, H.; Ertan, H.; Incel, O.D.; Ersoy, C. Multimodal wireless sensor network-based ambient assisted living in real homes with multiple residents. Sensors 2014, 14, 9692–9719. [Google Scholar] [CrossRef]
- Patel, A.; Shah, J. Sensor-based activity recognition in the context of ambient assisted living systems: A review. J. Ambient Intell. Smart Environ. 2019, 11, 301–322. [Google Scholar] [CrossRef]
- Sadek, I.; Rehman, S.U.; Codjo, J.; Abdulrazak, B. Privacy and Security of IoT Based Healthcare Systems: Concerns, Solutions, and Recommendations. In How AI Impacts Urban Living and Public Health, Proceedings of the 17th International Conference, ICOST 2019, New York City, NY, USA, 14–16 October 2019; Proceedings 17; Springer International Publishing: Cham, Switzerland, 2019; pp. 3–17. [Google Scholar]
- Annaswamy, A.M.; Johansson, K.H.; Pappas, G. Control for societal-scale challenges: Road map 2030. IEEE Control Syst. Mag. 2024, 44, 30–32. [Google Scholar] [CrossRef]
- Lamnabhi-Lagarrigue, F.; Annaswamy, A.; Engell, S.; Isaksson, A.; Khargonekar, P.; Murray, R.M.; Nijmeijer, H.; Samad, T.; Tilbury, D.; Van den Hof, P. Systems & control for the future of humanity, research agenda: Current and future roles, impact and grand challenges. Annu. Rev. Control 2017, 43, 1–64. [Google Scholar]
- Calvaresi, D.; Cesarini, D.; Sernani, P.; Marinoni, M.; Dragoni, A.F.; Sturm, A. Exploring the ambient assisted living domain: A systematic review. J. Ambient Intell. Humaniz. Comput. 2017, 8, 239–257. [Google Scholar] [CrossRef]
- Rashidi, P.; Mihailidis, A. A survey on ambient-assisted living tools for older adults. IEEE J. Biomed. Health Inform. 2012, 17, 579–590. [Google Scholar] [CrossRef]
- Cicirelli, G.; Marani, R.; Petitti, A.; Milella, A.; D’Orazio, T. Ambient assisted living: A review of technologies, methodologies and future perspectives for healthy aging of population. Sensors 2021, 21, 3549. [Google Scholar] [CrossRef]
- Li, R.; Lu, B.; McDonald-Maier, K.D. Cognitive assisted living ambient system: A survey. Digit. Commun. Netw. 2015, 1, 229–252. [Google Scholar] [CrossRef]
- Yusif, S.; Soar, J.; Hafeez-Baig, A. Older people, assistive technologies, and the barriers to adoption: A systematic review. Int. J. Med. Inform. 2016, 94, 112–116. [Google Scholar] [CrossRef]
- Vimarlund, V.; Borycki, E.M.; Kushniruk, A.W.; Avenberg, K. Ambient assisted living: Identifying new challenges and needs for digital technologies and service innovation. Yearb. Med. Inform. 2021, 30, 141–149. [Google Scholar] [CrossRef]
- Caballero, P.; Ortiz, G.; Medina-Bulo, I. Systematic literature review of ambient assisted living systems supported by the Internet of Things. Univers. Access Inf. Soc. 2024, 23, 1631–1656. [Google Scholar] [CrossRef]
- Abdulmalek, S.; Nasir, A.; Jabbar, W.A.; Almuhaya, M.A.; Bairagi, A.K.; Khan, M.A.M.; Kee, S.H. IoT-based healthcare-monitoring system towards improving quality of life: A review. Healthcare 2022, 10, 1993. [Google Scholar] [CrossRef] [PubMed]
- Choukou, M.A.; Polyvyana, A.; Sakamoto, Y.; Osterreicher, A. Ambient assisted living technologies to support older adults’ health and wellness: A systematic mapping review. Eur. Rev. Med. Pharmacol. Sci. 2021, 25, 4289–4307. [Google Scholar] [PubMed]
- Dimitrievski, A.; Zdravevski, E.; Lameski, P.; Trajkovik, V. A Survey of Ambient Assisted Living Systems: Challenges and Opportunities. In Proceedings of the 2016 IEEE 12th International Conference on Intelligent Computer Communication and Processing (ICCP), Cluj-Napoca, Romania, 8–10 September 2016; pp. 49–53. [Google Scholar]
- Javaid, M.; Haleem, A.; Rab, S.; Singh, R.P.; Suman, R. Sensors for daily life: A review. Sens. Int. 2021, 2, 100121. [Google Scholar] [CrossRef]
- Postolache, O.A.; Mukhopadhyay, S.C.; Jayasundera, K.P.; Swain, A.K. Sensors for Everyday Life; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Nam, Y.; Rho, S.; Lee, C. Physical activity recognition using multiple sensors embedded in a wearable device. ACM Trans. Embed. Comput. Syst. 2013, 12, 26. [Google Scholar] [CrossRef]
- Hafeez, S.; Jalal, A.; Kamal, S. Multi-Fusion Sensors for Action Recognition Based on Discriminative Motion Cues and Random Forest. In Proceedings of the 2021 International Conference on Communication Technologies (ComTech), Rawalpindi, Pakistan, 21–22 September 2021; pp. 91–96. [Google Scholar]
- Broer, A.A.; Benedictus, R.; Zarouchas, D. The need for multi-sensor data fusion in structural health monitoring of composite aircraft structures. Aerospace 2022, 9, 183. [Google Scholar] [CrossRef]
- Bartels, J.H.; Potthast, T.; Möller, S.; Grießmann, T.; Rolfes, R.; Beer, M.; Marx, S. Robust SHM: Redundancy approach with different sensor integration levels for long life monitoring systems. e-J. Nondestruct. Test. 2024, 29, 1–10. [Google Scholar] [CrossRef]
- Sood, K.; Nosouhi, M.R.; Kumar, N.; Gaddam, A.; Feng, B.; Yu, S. Accurate detection of IoT sensor behaviors in legitimate, faulty and compromised scenarios. IEEE Trans. Dependable Secur. Comput. 2021, 20, 288–300. [Google Scholar] [CrossRef]
- Beltrán, J.; Guindel, C.; De La Escalera, A.; García, F. Automatic extrinsic calibration method for lidar and camera sensor setups. IEEE Trans. Intell. Transp. Syst. 2022, 23, 17677–17689. [Google Scholar] [CrossRef]
- Taraldsen, K.; Chastin, S.F.; Riphagen, I.I.; Vereijken, B.; Helbostad, J.L. Physical activity monitoring by use of accelerometer-based body-worn sensors in older adults: A systematic literature review of current knowledge and applications. Maturitas 2012, 71, 13–19. [Google Scholar] [CrossRef]
- Wu, H. Multiscale entropy with electrocardiograph, electromyography, electroencephalography, and photoplethysmography signals in healthcare: A twelve-year systematic review. Biomed. Signal Process. Control 2024, 93, 106124. [Google Scholar] [CrossRef]
- Middleton, C. Delivering services over next generation broadband networks: Exploring devices, applications and networks. Telecommun. J. Aust. 2010, 60, 59.1–59.13. [Google Scholar] [CrossRef]
- Palavicini, G. Intelligent Health: Progress and Benefit of Artificial Intelligence in Sensing-Based Monitoring and Disease Diagnosis. Sensors 2023, 23, 9053. [Google Scholar] [CrossRef] [PubMed]
- Denis, S.; Berkvens, R.; Weyn, M. A survey on detection, tracking and identification in radio frequency-based device-free localization. Sensors 2019, 19, 5329. [Google Scholar] [CrossRef] [PubMed]
- Chalmers, C.; Fergus, P.; Montanez, C.A.C.; Sikdar, S.; Ball, F.; Kendall, B. Detecting activities of daily living and routine behaviours in dementia patients living alone using smart meter load disaggregation. IEEE Trans. Emerg. Top. Comput. 2020, 10, 157–169. [Google Scholar] [CrossRef]
- Devlin, M.A.; Hayes, B.P. Non-intrusive load monitoring and classification of activities of daily living using residential smart meter data. IEEE Trans. Consum. Electron. 2019, 65, 339–348. [Google Scholar] [CrossRef]
- Klemenjak, C.; Makonin, S.; Elmenreich, W. Towards Comparability in Non-Intrusive Load Monitoring: On Data and Performance Evaluation. In Proceedings of the 2020 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 17–20 February 2020; pp. 1–5. [Google Scholar]
- Kelly, J.; Knottenbelt, W. Neural Nilm: Deep Neural Networks Applied to Energy Disaggregation. In Proceedings of the 2nd ACM International Conference on Embedded Systems for Energy-Efficient Built Environments, Seoul, Republic of Korea, 4–5 November 2015; pp. 55–64. [Google Scholar]
- Sasaki, Y. A survey on IoT big data analytic systems: Current and future. IEEE Internet Things J. 2021, 9, 1024–1036. [Google Scholar] [CrossRef]
- Alabdulatif, A.; Khalil, I.; Forkan, A.R.M.; Atiquzzaman, M. Real-time secure health surveillance for smarter health communities. IEEE Commun. Mag. 2018, 57, 122–129. [Google Scholar] [CrossRef]
- Natgunanathan, I.; Mehmood, A.; Xiang, Y.; Gao, L.; Yu, S. Location privacy protection in smart health care system. IEEE Internet Things J. 2018, 6, 3055–3069. [Google Scholar] [CrossRef]
- Gupta, R.; Tanwar, S.; Tyagi, S.; Kumar, N. Machine learning models for secure data analytics: A taxonomy and threat model. Comput. Commun. 2020, 153, 406–440. [Google Scholar] [CrossRef]
- Goshvarpour, A.; Abbasi, A.; Goshvarpour, A. An accurate emotion recognition system using ECG and GSR signals and matching pursuit method. Biomed. J. 2017, 40, 355–368. [Google Scholar] [CrossRef]
- Catherwood, P.A.; Steele, D.; Little, M.; Mccomb, S.; McLaughlin, J. A community-based IoT personalized wireless healthcare solution trial. IEEE J. Transl. Eng. Health Med. 2018, 6, 2800313. [Google Scholar] [CrossRef]
- Prerna, D.; Tekchandani, R.; Kumar, N. Device-to-device content caching techniques in 5G: A taxonomy, solutions, and challenges. Comput. Commun. 2020, 153, 48–84. [Google Scholar] [CrossRef]
- Ren, Y.; Wang, C.; Chen, Y.; Yang, J.; Li, H. Noninvasive fine-grained sleep monitoring leveraging smartphones. IEEE Internet Things J. 2019, 6, 8248–8261. [Google Scholar] [CrossRef]
- Liu, L.; Xu, J.; Huan, Y.; Zou, Z.; Yeh, S.C.; Zheng, L.R. A smart dental health-IoT platform based on intelligent hardware, deep learning, and mobile terminal. IEEE J. Biomed. Health Inform. 2019, 24, 898–906. [Google Scholar] [CrossRef] [PubMed]
- Zuo, Z.; Watson, M.; Budgen, D.; Hall, R.; Kennelly, C.; Al Moubayed, N. Data anonymisation for pervasive health care: Systematic literature mapping study. JMIR Med. Inform. 2021, 9, e29871. [Google Scholar] [CrossRef]
- Zhu, H.; Liu, M.; Fang, C.; Deng, R.; Cheng, P. Detection-performance tradeoff for watermarking in industrial control systems. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2780–2793. [Google Scholar] [CrossRef]
- Brown, E.A. The Fitbit fault line: Two proposals to protect health and fitness data at work. Yale J. Health Policy Law Ethics 2016, 16, 1–49. [Google Scholar]
- Mhatre, V.; Rosenberg, C. Homogeneous vs. Heterogeneous Clustered Sensor Networks: A comparative study. In Proceedings of the 2004 IEEE International Conference on Communications (IEEE Cat. No. 04CH37577), Paris, France, 20–24 June 2004; Volume 6, pp. 3646–3651. [Google Scholar]
- Khriji, S.; Benbelgacem, Y.; Chéour, R.; Houssaini, D.E.; Kanoun, O. Design and implementation of a cloud-based event-driven architecture for real-time data processing in wireless sensor networks. J. Supercomput. 2022, 78, 3374–3401. [Google Scholar] [CrossRef]
- Alzahrani, A.; Alyas, T.; Alissa, K.; Abbas, Q.; Alsaawy, Y.; Tabassum, N. Hybrid approach for improving the performance of data reliability in cloud storage management. Sensors 2022, 22, 5966. [Google Scholar] [CrossRef]
- Wang, K.; Shao, Y.; Shu, L.; Han, G.; Zhu, C. LDPA: A local data processing architecture in ambient assisted living communications. IEEE Commun. Mag. 2015, 53, 56–63. [Google Scholar] [CrossRef]
- Aloi, G.; Fortino, G.; Gravina, R.; Pace, P.; Savaglio, C. Simulation-driven platform for Edge-based AAL systems. IEEE J. Sel. Areas Commun. 2020, 39, 446–462. [Google Scholar] [CrossRef]
- Khan, A.A.; Laghari, A.A.; Awan, S.; Jumani, A.K. Fourth Industrial Revolution Application: Network Forensics Cloud Security Issues. Security Issues and Privacy Concerns in Industry 4.0 Applications; Wiley-Scrivener: New York, NY, USA, 2021; pp. 15–33. [Google Scholar]
- Yang, J.J.; Li, J.Q.; Niu, Y. A hybrid solution for privacy preserving medical data sharing in the cloud environment. Future Gener. Comput. Syst. 2015, 43, 74–86. [Google Scholar] [CrossRef]
- Khan, S.U.; Ullah, N. Challenges in the adoption of hybrid cloud: An exploratory study using systematic literature review. J. Eng. 2016, 2016, 107–118. [Google Scholar] [CrossRef]
- Yan, S.; Chen, C.; Zhao, G.; Lee, B.S. Cloud Service Recommendation and Selection for Enterprises. In Proceedings of the 2012 8th iNternational Conference on Network and Service Management (cnsm) and 2012 Workshop on Systems Virtualiztion Management (svm), Las Vegas, NV, USA, 22–26 October 2012; pp. 430–434. [Google Scholar]
- Li, J.; Li, J.; Chen, X.; Jia, C.; Liu, Z. Efficient Keyword Search Over Encrypted Data with Fine-Grained Access Control in Hybrid Cloud. In Network and System Security, Proceedings of the 6th International Conference, NSS 2012, Wuyishan, China, 21–23 November 2012; Proceedings 6; Springer: Berlin/Heidelberg, Germany, 2012; pp. 490–502. [Google Scholar]
- Naresh, V.S.; Pericherla, S.S.; Murty, P.S.R.; Reddi, S. Internet of Things in Healthcare: Architecture, Applications, Challenges, and Solutions. Comput. Syst. Sci. Eng. 2020, 35. [Google Scholar] [CrossRef]
- Fernandes, C.D.; Depari, A.; Sisinni, E.; Ferrari, P.; Flammini, A.; Rinaldi, S.; Pasetti, M. Hybrid Indoor and Outdoor Localization for Elderly Care Applications with LoRaWAN. In Proceedings of the 2020 IEEE International Symposium on Medical Measurements and Applications (MeMeA), Bari, Italy, 1 June–1 July 2020; pp. 1–6. [Google Scholar]
- Vineetha, Y.; Misra, Y.; Kishore, K.K. A real time IoT based patient health monitoring system using machine learning algorithms. Eur. J. Mol. Clin. Med 2020, 7, 2912–2925. [Google Scholar]
- Hiraguri, T.; Aoyagi, M.; Morino, Y.; Akimoto, T.; Nishimori, K.; Hiraguri, T. Proposal of ZigBee systems for the provision of location information and transmission of sensor data in medical welfare. E-Health Telecommun. Syst. Netw. 2015, 4, 45–55. [Google Scholar] [CrossRef][Green Version]
- Alwan, O.S.; Prahald Rao, K. Dedicated real-time monitoring system for health care using ZigBee. Healthc. Technol. Lett. 2017, 4, 142–144. [Google Scholar] [CrossRef]
- Khan, M.A.A.; Kabir, M.A. Comparison among short range wireless networks: Bluetooth, Zig Bee & Wi-Fi. Daffodil Int. Univ. J. Sci. Technol. 2016, 11, 1–8. [Google Scholar]
- Kumar, P.; Silambarasan, K. Enhancing the performance of healthcare service in IoT and cloud using optimized techniques. IETE J. Res. 2022, 68, 1475–1484. [Google Scholar] [CrossRef]
- Verma, N.; Singh, S.; Prasad, D. A review on existing IoT architecture and communication protocols used in healthcare monitoring system. J. Inst. Eng. Ser. B 2022, 103, 245–257. [Google Scholar] [CrossRef]
- Abdulghani, H.A.; Nijdam, N.A.; Collen, A.; Konstantas, D. A study on security and privacy guidelines, countermeasures, threats: IoT data at rest perspective. Symmetry 2019, 11, 774. [Google Scholar] [CrossRef]
- Sivan, R.; Zukarnain, Z.A. Security and privacy in cloud-based e-health system. Symmetry 2021, 13, 742. [Google Scholar] [CrossRef]
- Hutchinson, B. Million Facebook Users to Find Out if Their Personal Data Was Breached, 87. Available online: https://abcnews.go.com/US/87-million-facebook-users-find-personal-data-breached/story?id=54334187 (accessed on 15 November 2024).
- Garun, N. Yahoo Says All 3 Billion User Accounts Were Impacted by 2013 Security Breach. 2017. Available online: https://www.nytimes.com/2017/10/03/technology/yahoo-hack-3-billion-users.html (accessed on 15 November 2024).
- Yao, M. Your Electronic Medical Records Could Be Worth $1000 to Hackers. Forbes. 18 April 2017. Available online: https://www.forbes.com/sites/mariyayao/2017/04/14/your-electronic-medical-records-can-be-worth-1000-to-hackers (accessed on 12 September 2024).
- Srivastava, A.; Singh, P. Security Issues in Cloud Computing. J. Manag. Serv. Sci. 2022, 2, 1–11. [Google Scholar] [CrossRef]
- Ullah, I.; Adhikari, D.; Su, X.; Palmieri, F.; Wu, C.; Choi, C. Integration of data science with the intelligent IoT (IIoT): Current challenges and future perspectives. Digit. Commun. Netw. 2024. (in press)
- Seixas, F.L.; Zadrozny, B.; Laks, J.; Conci, A.; Saade, D.C.M. A Bayesian network decision model for supporting the diagnosis of dementia, Alzheimer disease and mild cognitive impairment. Comput. Biol. Med. 2014, 51, 140–158. [Google Scholar] [CrossRef] [PubMed]
- Cheng, B.C.; Tsai, Y.A.; Liao, G.T.; Byeon, E.S. HMM machine learning and inference for activities of daily living recognition. J. Supercomput. 2010, 54, 29–42. [Google Scholar] [CrossRef]
- Reichman, O.J.; Jones, M.B.; Schildhauer, M.P. Challenges and opportunities of open data in ecology. Science 2011, 331, 703–705. [Google Scholar] [CrossRef]
- Venkataramanan, M. My Identity for Sale. WIRED Magazine, November 2014; 98–105. [Google Scholar]
- De Montjoye, Y.A.; Hidalgo, C.A.; Verleysen, M.; Blondel, V.D. Unique in the crowd: The privacy bounds of human mobility. Sci. Rep. 2013, 3, 1376. [Google Scholar] [CrossRef]
- Kosinski, M.; Stillwell, D.; Graepel, T. Private traits and attributes are predictable from digital records of human behavior. Proc. Natl. Acad. Sci. USA 2013, 110, 5802–5805. [Google Scholar] [CrossRef]
- Lambiotte, R.; Kosinski, M. Tracking the digital footprints of personality. Proc. IEEE 2014, 102, 1934–1939. [Google Scholar] [CrossRef]
- Seh, A.H.; Zarour, M.; Alenezi, M.; Sarkar, A.K.; Agrawal, A.; Kumar, R.; Ahmad Khan, R. Healthcare data breaches: Insights and implications. Healthcare 2020, 8, 133. [Google Scholar] [CrossRef] [PubMed]
- Shachmurove, N.C.; McCulloch, W. Health care companies face financial strain from data breaches. Am. Bankruptcy Inst. J. 2021, 40, 20–52. [Google Scholar]
- Shojaei, P.; Vlahu-Gjorgievska, E.; Chow, Y.W. Security and privacy of technologies in health information systems: A systematic literature review. Computers 2024, 13, 41. [Google Scholar] [CrossRef]
- Moore, D.H.; Algase, D.L.; Powell-Cope, G.; Applegarth, S.; Beattie, E.R. A framework for managing wandering and preventing elopement. Am. J. Alzheimer’s Dis. Other Dementias 2009, 24, 208–219. [Google Scholar] [CrossRef]
- Hein, A.; Kirste, T. Activity Recognition for Ambient Assisted Living: Potential and Challenges. In Ambient Assisted Living; CRC Press: Boca Raton, FL, USA, 2008; pp. 263–268. [Google Scholar]
- Bao, L.; Intille, S.S. Activity Recognition from User-Annotated Acceleration Data. In Proceedings of the Conference on Pervasive Computing, Vienna, Austria, 21–23 April 2004; pp. 1–17. [Google Scholar]
- Gulati, N.; Kaur, P.D. An argumentation enabled decision making approach for Fall Activity Recognition in Social IoT based Ambient Assisted Living systems. Future Gener. Comput. Syst. 2021, 122, 82–97. [Google Scholar] [CrossRef]
- Mishra, P.K.; Iaboni, A.; Ye, B.; Newman, K.; Mihailidis, A.; Khan, S.S. Privacy-protecting behaviours of risk detection in people with dementia using videos. BioMed. Eng. OnLine 2023, 22, 4. [Google Scholar] [CrossRef]
- Mohan, D.; Al-Hamid, D.Z.; Chong, P.H.J.; Sudheera, K.L.K.; Gutierrez, J.; Chan, H.C.; Li, H. Artificial Intelligence and IoT in Elderly Fall Prevention: A Review. IEEE Sens. J. 2024, 24, 4181–4198. [Google Scholar] [CrossRef]
- Denkovski, S.; Khan, S.S.; Mihailidis, A. Temporal Shift-Multi-Objective Loss Function for Improved Anomaly Fall Detection. In Proceedings of the Asian Conference on Machine Learning, PMLR, Hanoi, Vietnam, 5–7 December 2024; pp. 295–310. [Google Scholar]
- Deep, S.; Zheng, X.; Karmakar, C.; Yu, D.; Hamey, L.G.; Jin, J. A survey on anomalous behavior detection for elderly care using dense-sensing networks. IEEE Commun. Surv. Tutorials 2019, 22, 352–370. [Google Scholar] [CrossRef]
- Garcés, L.; Oquendo, F.; Nakagawa, E.Y. A Quality Model for AAL Software Systems. In Proceedings of the 2016 IEEE 29th International Symposium on Computer-Based Medical Systems (CBMS), Belfast and Dublin, Ireland, 20–24 June 2016; pp. 175–180. [Google Scholar]
- Kawano, Y.; Cao, M. Design of privacy-preserving dynamic controllers. IEEE Trans. Autom. Control 2020, 65, 3863–3878. [Google Scholar] [CrossRef]
- Zakka, V.G.; Dai, Z.; Manso, L.J. Action Recognition for Privacy-Preserving Ambient Assisted Living. In Proceedings of the International Conference on AI in Healthcare, Swansea, UK, 4–6 September 2024; pp. 203–217. [Google Scholar]
- Climent-Pérez, P.; Florez-Revuelta, F. Privacy-preserving human action recognition with a many-objective evolutionary algorithm. Sensors 2022, 22, 764. [Google Scholar] [CrossRef]
- Dankar, F.K.; El Emam, K. The Application of Differential Privacy to Health Data. In Proceedings of the 2012 Joint EDBT/ICDT Workshops, Berlin, Germany, 30 March 2012; pp. 158–166. [Google Scholar]
- Dankar, F.K.; El Emam, K. Practicing differential privacy in health care: A review. Trans. Data Priv. 2013, 6, 35–67. [Google Scholar]
- Ferrari, R.M.; Teixeira, A.M. Safety, Security and Privacy for Cyber-Physical Systems; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Rubio-Hernan, J.; De Cicco, L.; Garcia-Alfaro, J. On the use of watermark-based schemes to detect cyber-physical attacks. EURASIP J. Inf. Secur. 2017, 2017, 8. [Google Scholar] [CrossRef]
- Satchidanandan, B.; Kumar, P.R. Dynamic watermarking: Active defense of networked cyber–physical systems. Proc. IEEE 2016, 105, 219–240. [Google Scholar] [CrossRef]
- Kogiso, K.; Fujita, T. Cyber-Security Enhancement of Networked Control Systems Using Homomorphic Encryption. In Proceedings of the 2015 54th IEEE Conference on Decision and Control (CDC), Osaka, Japan, 15–18 December 2015; pp. 6836–6843. [Google Scholar]
- Zhou, L.; Varadharajan, V.; Hitchens, M. Achieving secure role-based access control on encrypted data in cloud storage. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1947–1960. [Google Scholar] [CrossRef]
- Li, F.; Luo, B.; Liu, P. Secure Information Aggregation for Smart Grids Using Homomorphic Encryption. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 327–332. [Google Scholar]
- Si, F.; Zhang, N.; Wang, Y.; Kong, P.Y.; Qiao, W. Distributed optimization for integrated energy systems with secure multiparty computation. IEEE Internet Things J. 2022, 10, 7655–7666. [Google Scholar] [CrossRef]
- Barboni, A. Diagnosis of Stealthy Local Cyber-Attacks in Large-Scale Systems. Ph.D. Thesis, Imperial College London, London, UK, 2020. [Google Scholar]
- Chen, Z.; Pasqualetti, F.; He, J.; Cheng, P.; Trentelman, H.L.; Bullo, F. Guest editorial: Special issue on security and privacy of distributed algorithms and network systems. IEEE Trans. Autom. Control 2020, 65, 3725–3727. [Google Scholar]
- Mohan, V.; Anand, H. Biosensor: An emerging analytical tool. J. Biosens. Bioelectron 2019, 10, 269. [Google Scholar]
- Olawade, D.B.; Wada, O.J.; David-Olawade, A.C.; Kunonga, E.; Abaire, O.; Ling, J. Using artificial intelligence to improve public health: A narrative review. Front. Public Health 2023, 11, 1196397. [Google Scholar] [CrossRef]
- Lee, D.; Yoon, S.N. Application of artificial intelligence-based technologies in the healthcare industry: Opportunities and challenges. Int. J. Environ. Res. Public Health 2021, 18, 271. [Google Scholar] [CrossRef]
- Erion, G.; Janizek, J.D.; Hudelson, C.; Utarnachitt, R.B.; McCoy, A.M.; Sayre, M.R.; White, N.J.; Lee, S.I. A cost-aware framework for the development of AI models for healthcare applications. Nat. Biomed. Eng. 2022, 6, 1384–1398. [Google Scholar] [CrossRef]
- Price, W.N.; Cohen, I.G. Privacy in the age of medical big data. Nat. Med. 2019, 25, 37–43. [Google Scholar] [CrossRef] [PubMed]
- Sheller, M.J.; Edwards, B.; Reina, G.A.; Martin, J.; Pati, S.; Kotrotsou, A.; Milchenko, M.; Xu, W.; Marcus, D.; Colen, R.R.; et al. Federated learning in medicine: Facilitating multi-institutional collaborations without sharing patient data. Sci. Rep. 2020, 10, 12598. [Google Scholar] [CrossRef] [PubMed]
- Edemekong, P.F.; Annamaraju, P.; Haydel, M.J. Health Insurance Portability and Accountability Act. 2018. Available online: https://pubmed.ncbi.nlm.nih.gov/29763195 (accessed on 24 December 2024).
- Rajkomar, A.; Hardt, M.; Howell, M.D.; Corrado, G.; Chin, M.H. Ensuring fairness in machine learning to advance health equity. Ann. Intern. Med. 2018, 169, 866–872. [Google Scholar] [CrossRef] [PubMed]
- Hardt, M.; How Big Data is Unfair. Medium. 2014. Available online: https://medium.com/@mrtz/how-big-data-is-unfair-9aa544d739de (accessed on 12 January 2025).
- Schönberger, D. Artificial intelligence in healthcare: A critical analysis of the legal and ethical implications. Int. J. Law Inf. Technol. 2019, 27, 171–203. [Google Scholar] [CrossRef]
- Gianfrancesco, M.A.; Tamang, S.; Yazdany, J.; Schmajuk, G. Potential biases in machine learning algorithms using electronic health record data. JAMA Intern. Med. 2018, 178, 1544–1547. [Google Scholar] [CrossRef]
- Ebong, O.; Edet, A.; Uwah, A.; Udoetor, N. Comprehensive Impact Assessment of Intrusion Detection and Mitigation Strategies Using Support Vector Machine Classification. Res. J. Pure Sci. Technol. 2024, 7, 50–69. [Google Scholar]
- Buczak, A.L.; Guven, E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutorials 2015, 18, 1153–1176. [Google Scholar] [CrossRef]
- Alexander, B.; Neira, V.; Campbell, D.; Crystal, E.; Simpson, C.; Enriquez, A.; Chacko, S.; Abdollah, H.; Redfearn, D.; Baranchuk, A. Implantable Cardioverter-Defibrillator–Cybersecurity. Circ. Arrhythmia Electrophysiol. 2020, 13, e008261. [Google Scholar] [CrossRef]
- Alhussan, M.; Boem, F.; Ghoreishizadeh, S.S.; Mandalari, A.M. From Eavesdropping to Exploitation: Exposing Vulnerabilities in BLE-Enabled Wearable Medical Devices. In Proceedings of the EWSN, The 21st International Conference on Embedded Wireless Systems and Networks, Abu Dhabi, United Arab Emirates, 10–13 December 2024. [Google Scholar]
- Patel, B.; Makaryus, A.N. Cardiac implantable electronic devices and cybersecurity. Expert Rev. Med. Devices 2021, 18, 69–77. [Google Scholar] [CrossRef]
- Crossley, G.H.; Boyle, A.; Vitense, H.; Chang, Y.; Mead, R.H.; Investigators, C. The CONNECT (Clinical Evaluation of Remote Notification to Reduce Time to Clinical Decision) trial: The value of wireless remote monitoring with automatic clinician alerts. J. Am. Coll. Cardiol. 2011, 57, 1181–1189. [Google Scholar] [CrossRef]
- Das, S.; Siroky, G.P.; Lee, S.; Mehta, D.; Suri, R. Cybersecurity: The need for data and patient safety with cardiac implantable electronic devices. Heart Rhythm 2021, 18, 473–481. [Google Scholar] [CrossRef] [PubMed]
- Bour, G.; Lie, A.W.; Kok, J.S.; Markussen, B.; Moe, M.E.G.; Borgaonkar, R. Security Analysis of the Internet of Medical Things (IoMT): Case Study of the Pacemaker Ecosystem. In Proceedings of the International Joint Conference on Biomedical Engineering Systems and Technologies, Virtual Event, 9–11 February 2022; pp. 73–96. [Google Scholar]
- Guo, L.; Dong, M.; Ota, K.; Li, Q.; Ye, T.; Wu, J.; Li, J. A secure mechanism for big data collection in large scale internet of vehicle. IEEE Internet Things J. 2017, 4, 601–610. [Google Scholar] [CrossRef]
- Muhammed, T.; Mehmood, R.; Albeshri, A.; Katib, I. UbeHealth: A personalized ubiquitous cloud and edge-enabled networked healthcare system for smart cities. IEEE Access 2018, 6, 32258–32285. [Google Scholar] [CrossRef]
- Janbi, N.; Katib, I.; Albeshri, A.; Mehmood, R. Distributed artificial intelligence-as-a-service (DAIaaS) for smarter IoE and 6G environments. Sensors 2020, 20, 5796. [Google Scholar] [CrossRef]
- Vora, J.; Tanwar, S.; Tyagi, S.; Kumar, N.; Rodrigues, J.J. FAAL: Fog Computing-Based Patient Monitoring System for Ambient Assisted Living. In Proceedings of the 2017 IEEE 19th International Conference on e-Health Networking, Applications and Services (Healthcom), Dalian, China, 12–15 October 2017; pp. 1–6. [Google Scholar]
- Malin, B.; Sweeney, L. How (not) to protect genomic data privacy in a distributed network: Using trail re-identification to evaluate and design anonymity protection systems. J. Biomed. Inform. 2004, 37, 179–192. [Google Scholar] [CrossRef]
- Beck, E.; Goin, M.E.; Ho, A.; Parks, A.; Rowe, S. Critical digital literacy as method for teaching tactics of response to online surveillance and privacy erosion. Comput. Compos. 2021, 61, 102654. [Google Scholar] [CrossRef]
- Sarker, I.H.; Kayes, A.; Badsha, S.; Alqahtani, H.; Watters, P.; Ng, A. Cybersecurity data science: An overview from machine learning perspective. J. Big Data 2020, 7, 1–29. [Google Scholar] [CrossRef]
- Kirk, S. The Wearables Revolution: Is Standardization a Help or a Hindrance?: Mainstream technology or just a passing phase? IEEE Consum. Electron. Mag. 2014, 3, 45–50. [Google Scholar] [CrossRef]
- Xie, M.; Huang, W.; Yang, L.; Yang, Y. VOAuth: A solution to protect OAuth against phishing. Comput. Ind. 2016, 82, 151–159. [Google Scholar] [CrossRef]
- Navas, J.; Beltrán, M. Understanding and mitigating OpenID Connect threats. Comput. Secur. 2019, 84, 1–16. [Google Scholar] [CrossRef]
- Huda, S.; Islam, M.R.; Kottala, V.N.V.; Abawajy, J.H. A Cyber Risk Assessment Approach to Federated Identity Management Framework Based Digital Healthcare System. Sensors 2024, 24, 5282. [Google Scholar] [CrossRef] [PubMed]
- Altenstetter, C. Medical device regulation in the European Union, Japan and the United States. Commonalities, differences and challenges. Innov. Eur. J. Soc. Sci. Res. 2012, 25, 362–388. [Google Scholar] [CrossRef]
- Zieni, B.; Heckel, R. TEM: A Transparency Engineering Methodology Enabling Users’ Trust Judgement. In Proceedings of the 2021 IEEE 29th International Requirements Engineering Conference (RE), Notre Dame, IN, USA, 20–24 September 2021; pp. 94–105. [Google Scholar]
- Zieni, B.; Spagnuelo, D.; Heckel, R. Transparency by Default: GDPR Patterns for Agile Development. In Proceedings of the International Conference on Electronic Government and the Information Systems Perspective, Virtual Event, 27–30 September 2021; pp. 89–102. [Google Scholar]
- Siddiqui, Z.; Shukla, V.K.; Sharma, N. A Review of the New European Medical Device Regulations. 2024. Available online: https://www.wjpr.net/abstract_show/25248 (accessed on 10 January 2025).
- Melvin, T.; Torre, M. New medical device regulations: The regulator’s view. Efort Open Rev. 2019, 4, 351–356. [Google Scholar] [CrossRef] [PubMed]
- Carl, A.K.; Hochmann, D. Impact of the new European medical device regulation: A two-year comparison. Biomed. Eng. Tech. 2024, 69, 317–326. [Google Scholar] [CrossRef]
- Darrow, J.J.; Avorn, J.; Kesselheim, A.S. FDA regulation and approval of medical devices: 1976–2020. JAMA 2021, 326, 420–432. [Google Scholar] [CrossRef]
- Beharry, M. DBS: A UK (MHRA) regulatory perspective. Bioanalysis 2010, 2, 1363–1364. [Google Scholar] [CrossRef]
- Karthika, B.; Vijayakumar, A. ISO 13485: Medical Devices—Quality Management Systems, Requirements for Regulatory Purposes. In Medical Device Guidelines and Regulations Handbook; Springer: Berlin/Heidelberg, Germany, 2022; pp. 19–29. [Google Scholar]
- Tzanou, M. Health Data Privacy Under the GDPR; Taylor Francis Limited: Abingdon, UK, 2023. [Google Scholar]
- Riad, A.K.I.; Barek, M.A.; Rahman, M.M.; Akter, M.S.; Islam, T.; Rahman, M.A.; Mia, M.R.; Shahriar, H.; Wu, F.; Ahamed, S.I. Enhancing HIPAA Compliance in AI-driven mHealth Devices Security and Privacy. In Proceedings of the 2024 IEEE 48th Annual Computers, Software, and Applications Conference (COMPSAC), Osaka, Japan, 2–4 July 2024; pp. 2430–2435. [Google Scholar]
- Soman, R.; Onoufriou, T.; Votsis, R.; Chrysostomou, C.; Kyriakides, M. Optimisation of Multi-type Sensor Placement for SHM Based on Application Demands. In Proceedings of the IABSE Symposium Report, Kolkata, India, 24–27 September 2013; Volume 101, pp. 1–9. [Google Scholar]
- Soman, R.N.; Onoufrioua, T.; Kyriakidesb, M.A.; Votsisc, R.A.; Chrysostomou, C.Z. Multi-type, multi-sensor placement optimization for structural health monitoring of long span bridges. Smart Struct. Syst. 2014, 14, 55–70. [Google Scholar] [CrossRef]
- Sun, X.; Hou, G.; Wang, Z. Sensitivity-Based Optimal Sensor Placement of Multi-Type Sensor. In Proceedings of the Health Monitoring of Structural and Biological Systems, San Diego, CA, USA, 10–14 March 2013; Volume 8695, pp. 924–933. [Google Scholar]
- Chan, P.Y.; Ripin, Z.M.; Halim, S.A.; Arifin, W.N.; Yahya, A.S.; Eow, G.B.; Tan, K.; Hor, J.Y.; Wong, C.K. Motion characteristics of subclinical tremors in Parkinson’s disease and normal subjects. Sci. Rep. 2022, 12, 4021. [Google Scholar] [CrossRef]
- Channa, A.; Ruggeri, G.; Ifrim, R.C.; Mammone, N.; Iera, A.; Popescu, N. Cloud-Connected Bracelet for Continuous Monitoring of Parkinson’s Disease Patients: Integrating Advanced Wearable Technologies and Machine Learning. Electronics 2024, 13, 1002. [Google Scholar] [CrossRef]
- Pratihar, R.; Sankar, R. Advancements in Parkinson’s Disease Diagnosis: A Comprehensive Survey on Biomarker Integration and Machine Learning. Computers 2024, 13, 293. [Google Scholar] [CrossRef]
- Moore, K.; O’Shea, E.; Kenny, L.; Barton, J.; Tedesco, S.; Sica, M.; Crowe, C.; Alamäki, A.; Condell, J.; Nordström, A.; et al. Older adults’ experiences with using wearable devices: Qualitative systematic review and meta-synthesis. JMIR MHealth UHealth 2021, 9, e23832. [Google Scholar] [CrossRef] [PubMed]
- Rahme, M.; Folkeard, P.; Scollie, S. Evaluating the accuracy of step tracking and fall detection in the Starkey Livio artificial intelligence hearing aids: A pilot study. Am. J. Audiol. 2021, 30, 182–189. [Google Scholar] [CrossRef] [PubMed]
- Brognara, L.; Palumbo, P.; Grimm, B.; Palmerini, L. Assessing gait in Parkinson’s disease using wearable motion sensors: A systematic review. Diseases 2019, 7, 18. [Google Scholar] [CrossRef] [PubMed]
- Barman, J.; Uswatte, G.; Ghaffari, T.; Sokal, B.; Byrom, E.; Trinh, E.; Brewer, M.; Varghese, C.; Sarkar, N. Sensor-enabled RFID system for monitoring arm activity: Reliability and validity. IEEE Trans. Neural Syst. Rehabil. Eng. 2012, 20, 771–777. [Google Scholar] [CrossRef]
- Barman, J.; Uswatte, G.; Sarkar, N.; Ghaffari, T.; Sokal, B. Sensor-Enabled RFID System for Monitoring Arm Activity in Daily Life. In Proceedings of the 2011 Annual International Conference of the IEEE Engineering in Medicine and Biology Society, Boston, MA, USA, 30 August–3 September 2011; pp. 5219–5223. [Google Scholar]
- Yared, R.; Negassi, M.E.; Yang, L. Physical Activity Classification and Assessment Using Smartphone. In Proceedings of the 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 1–3 November 2018; pp. 140–144. [Google Scholar]
- Song, M.; Kim, J. An ambulatory gait monitoring system with activity classification and gait parameter calculation based on a single foot inertial sensor. IEEE Trans. Biomed. Eng. 2017, 65, 885–893. [Google Scholar] [CrossRef]
- Cornacchia, M.; Ozcan, K.; Zheng, Y.; Velipasalar, S. A survey on activity detection and classification using wearable sensors. IEEE Sens. J. 2016, 17, 386–403. [Google Scholar] [CrossRef]
- Doherty, A.R.; Kelly, P.; Kerr, J.; Marshall, S.; Oliver, M.; Badland, H.; Hamilton, A.; Foster, C. Using wearable cameras to categorise type and context of accelerometer-identified episodes of physical activity. Int. J. Behav. Nutr. Phys. Act. 2013, 10, 22. [Google Scholar] [CrossRef]
- Liang, B.; Zheng, L. A Survey on Human Action Recognition Using Depth Sensors. In Proceedings of the 2015 International Conference on Digital Image Computing: Techniques and Applications (DICTA), Adelaide, Australia, 23–25 November 2015; pp. 1–8. [Google Scholar]
- Vahdani, E.; Tian, Y. Deep learning-based action detection in untrimmed videos: A survey. IEEE Trans. Pattern Anal. Mach. Intell. 2022, 45, 4302–4320. [Google Scholar] [CrossRef]
- Hadjidj, A.; Souil, M.; Bouabdallah, A.; Challal, Y.; Owen, H. Wireless sensor networks for rehabilitation applications: Challenges and opportunities. J. Netw. Comput. Appl. 2013, 36, 1–15. [Google Scholar] [CrossRef]
- Bijalwan, V.; Semwal, V.B.; Singh, G.; Mandal, T.K. HDL-PSR: Modelling spatio-temporal features using hybrid deep learning approach for post-stroke rehabilitation. Neural Process. Lett. 2023, 55, 279–298. [Google Scholar] [CrossRef]
- Nam, Y.H.; Bai, Y.; Lee, J.A.; Kim, Y.; Lee, J.M.; Meier, N.F.; Welk, G.J. Validity Of Consumer-based Physical Activity Monitors In Semi-structured Activities: 982 Board# 3 May 27, 3: 15 PM-5: 15 PM. Med. Sci. Sport. Exerc. 2015, 47, 260–261. [Google Scholar]
- Case, M.A.; Burwick, H.A.; Volpp, K.G.; Patel, M.S. Accuracy of smartphone applications and wearable devices for tracking physical activity data. JAMA 2015, 313, 625–626. [Google Scholar] [CrossRef] [PubMed]
- Kelly, J.T.; Campbell, K.L.; Gong, E.; Scuffham, P. The Internet of Things: Impact and implications for health care delivery. J. Med. Internet Res. 2020, 22, e20135. [Google Scholar] [CrossRef] [PubMed]
- Tuckson, R.V.; Edmunds, M.; Hodgkins, M.L. Telehealth. N. Engl. J. Med. 2017, 377, 1585–1592. [Google Scholar] [CrossRef]
- Thakur, N.; Han, C.Y. A simplistic and cost-effective design for real-world development of an ambient assisted living system for fall detection and indoor localization: Proof-of-concept. Information 2022, 13, 363. [Google Scholar] [CrossRef]
- Future, M.R. Ambient Assisted Living Market Worth USD 23.5 Billion at a CAGR of 19.1% by 2030. 2023. Available online: https://www.globenewswire.com/news-release/2023/03/02/2619001/0/en/Ambient-Assisted-Living-Market-Worth-USD-23-5-Billion-at-a-CAGR-of-19-1-by-2030-Report-by-Market-Research-Future-MRFR.html (accessed on 12 January 2025).
- Cryer, L.; Shannon, S.B.; Van Amsterdam, M.; Leff, B. Costs for ‘hospital at home’patients were 19 percent lower, with equal or better outcomes compared to similar inpatients. Health Aff. 2012, 31, 1237–1243. [Google Scholar] [CrossRef]
- Klein, S. “Hospital at Home” Programs Improve Outcomes, Lower Costs But Face Resistance from Providers and Payers; The Commonwealth Fund: New York, NY, USA, 2022. [Google Scholar]
- Megido, I.; Sela, Y.; Grinberg, K. Cost effectiveness of home care versus hospital care: A retrospective analysis. Cost Eff. Resour. Alloc. 2023, 21, 13. [Google Scholar] [CrossRef]
- The National Council on Aging. Falls Prevention Facts. Available online: https://www.ncoa.org/news/resources-for-reporters/get-the-facts/falls-prevention-facts/ (accessed on 9 May 2022).
- Centers for Disease Control and Prevention. Older Adult Falls Reported by State. Available online: https://www.cdc.gov/falls/data-research/facts-stats/index.html (accessed on 9 May 2022).
- Hassan, C.A.U.; Karim, F.K.; Abbas, A.; Iqbal, J.; Elmannai, H.; Hussain, S.; Ullah, S.S.; Khan, M.S. A Cost-Effective Fall-Detection Framework for the Elderly Using Sensor-Based Technologies. Sustainability 2023, 15, 3982. [Google Scholar] [CrossRef]
- Living, M.S. The Financial Impact of Fall Detection Wearable Devices on Senior Living Communities. 2023. Available online: https://www.mcknightsseniorliving.com/home/columns/marketplace-columns/the-financial-impact-of-falls-detection-wearable-devices-on-senior-living-communities-noi/ (accessed on 12 January 2025).
- Giovanelli, D.; Milosevic, B.; Brunelli, D.; Farella, E. Enhancing Bluetooth Low Energy with wake-up radios for IoT applications. In Proceedings of the 2017 13th International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; pp. 1622–1627. [Google Scholar]
- Corbellini, G.; Schmid, S.; Mangold, S. Two-Way Communication Protocol Using Bluetooth Low Energy Advertisement Frames. In Proceedings of the 1st International Workshop on Experiences with the Design and Implementation of Smart Objects, Paris, France, 7 September 2015; pp. 19–24. [Google Scholar]
- Akrivopoulos, O.; Chatzigiannakis, I.; Tselios, C.; Antoniou, A. On the Deployment of Healthcare Applications over Fog Computing Infrastructure. In Proceedings of the 2017 IEEE 41st annual computer software and applications conference (COMPSAC), Turin, Italy, 4–8 July 2017; Volume 2, pp. 288–293. [Google Scholar]
- Qaim, W.B.; Ometov, A.; Molinaro, A.; Lener, I.; Campolo, C.; Lohan, E.S.; Nurmi, J. Towards energy efficiency in the internet of wearable things: A systematic review. IEEE Access 2020, 8, 175412–175435. [Google Scholar] [CrossRef]
- Zhou, D.; Li, Z.; Zhu, J.; Zhang, H.; Hou, L. State of health monitoring and remaining useful life prediction of lithium-ion batteries based on temporal convolutional network. IEEE Access 2020, 8, 53307–53320. [Google Scholar] [CrossRef]
- Kalantarian, H.; Sideris, C.; Mortazavi, B.; Alshurafa, N.; Sarrafzadeh, M. Dynamic computation offloading for low-power wearable health monitoring systems. IEEE Trans. Biomed. Eng. 2016, 64, 621–628. [Google Scholar] [CrossRef] [PubMed]
- Mansourkiaie, F.; Ismail, L.S.; Elfouly, T.M.; Ahmed, M.H. Maximizing lifetime in wireless sensor network for structural health monitoring with and without energy harvesting. IEEE Access 2017, 5, 2383–2395. [Google Scholar] [CrossRef]
- Nasr, M.; Islam, M.M.; Shehata, S.; Karray, F.; Quintana, Y. Smart healthcare in the age of AI: Recent advances, challenges, and future prospects. IEEE Access 2021, 9, 145248–145270. [Google Scholar] [CrossRef]
- Nižetić, S.; Šolić, P.; Gonzalez-De, D.L.d.I.; Patrono, L. Internet of Things (IoT): Opportunities, issues and challenges towards a smart and sustainable future. J. Clean. Prod. 2020, 274, 122877. [Google Scholar] [CrossRef]
- Wang, C.; He, T.; Zhou, H.; Zhang, Z.; Lee, C. Artificial intelligence enhanced sensors-enabling technologies to next-generation healthcare and biomedical platform. Bioelectron. Med. 2023, 9, 17. [Google Scholar] [CrossRef]
- Foy, K. New Tools Are Available to Help Reduce the Energy That AI Models Devour. 2023. Available online: https://news.mit.edu/2023/new-tools-available-reduce-energy-that-ai-models-devour-1005 (accessed on 25 May 2022).
- Chuah, S.H.W.; Rauschnabel, P.A.; Krey, N.; Nguyen, B.; Ramayah, T.; Lade, S. Wearable technologies: The role of usefulness and visibility in smartwatch adoption. Comput. Hum. Behav. 2016, 65, 276–284. [Google Scholar] [CrossRef]
- Park, E. User acceptance of smart wearable devices: An expectation-confirmation model approach. Telemat. Inform. 2020, 47, 101318. [Google Scholar] [CrossRef]
- Sui, A.; Sui, W.; Liu, S.; Rhodes, R. Ethical considerations for the use of consumer wearables in health research. Digit. Health 2023, 9, 20552076231153740. [Google Scholar] [CrossRef]
- Ledger, D.; McCaffrey, D. Inside wearables: How the science of human behavior change offers the secret to long-term engagement. Endeav. Partners 2014, 200, 1. [Google Scholar]
- Piwek, L.; Ellis, D.A.; Andrews, S.; Joinson, A. The rise of consumer health wearables: Promises and barriers. PLoS Med. 2016, 13, e1001953. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zieni, B.; Ritchie, M.A.; Mandalari, A.M.; Boem, F. An Interdisciplinary Overview on Ambient Assisted Living Systems for Health Monitoring at Home: Trade-Offs and Challenges. Sensors 2025, 25, 853. https://doi.org/10.3390/s25030853
Zieni B, Ritchie MA, Mandalari AM, Boem F. An Interdisciplinary Overview on Ambient Assisted Living Systems for Health Monitoring at Home: Trade-Offs and Challenges. Sensors. 2025; 25(3):853. https://doi.org/10.3390/s25030853
Chicago/Turabian StyleZieni, Baraa, Matthew A. Ritchie, Anna Maria Mandalari, and Francesca Boem. 2025. "An Interdisciplinary Overview on Ambient Assisted Living Systems for Health Monitoring at Home: Trade-Offs and Challenges" Sensors 25, no. 3: 853. https://doi.org/10.3390/s25030853
APA StyleZieni, B., Ritchie, M. A., Mandalari, A. M., & Boem, F. (2025). An Interdisciplinary Overview on Ambient Assisted Living Systems for Health Monitoring at Home: Trade-Offs and Challenges. Sensors, 25(3), 853. https://doi.org/10.3390/s25030853









