Abstract
Internet of Things (IoT) user authentication protocols enable secure authentication and session key negotiation between users and IoT devices via an intermediate server, allowing users to access sensor data or control devices remotely. However, the existing IoT user authentication schemes often assume that the servers (registration center and intermediate servers) are fully trusted, overlooking the potential risk of insider attackers. Moreover, most of the existing schemes lack critical security properties, such as resistance to ephemeral secret leakage attacks and offline password guessing attacks, and they are unable to provide perfect forward security. Furthermore, with the rapid growth regarding IoT devices, the servers must manage a large number of users and device connections, making the performance of the authentication scheme heavily reliant on the server’s computational capacity, thereby impacting the system’s scalability and efficiency. The design of security protocols is based on the underlying security model, and the current IoT user authentication models fail to cover crucial threats like insider attacks and ephemeral secret leakage. To overcome these limitations, we propose a new security model, IoT-3eCK, which assumes semi-trusted servers and strengthens the adversary model to better meet the IoT authentication requirements. Based on this model, we design an efficient protocol that ensures user passwords, biometric data, and long-term keys are protected from insider users during registration, mitigating insider attacks. The protocol also integrates dynamic pseudo-identity anonymous authentication and ECC key exchange to satisfy the security properties. The performance analysis shows that, compared to the existing schemes, the new protocol reduces the communication costs by over 23% and the computational overhead by more than 22%, with a particularly significant reduction of over 95% in the computational overhead at the intermediate server. Furthermore, the security of the protocol is rigorously demonstrated using the random oracle model and verified with automated tools, further confirming its security and reliability.
1. Introduction
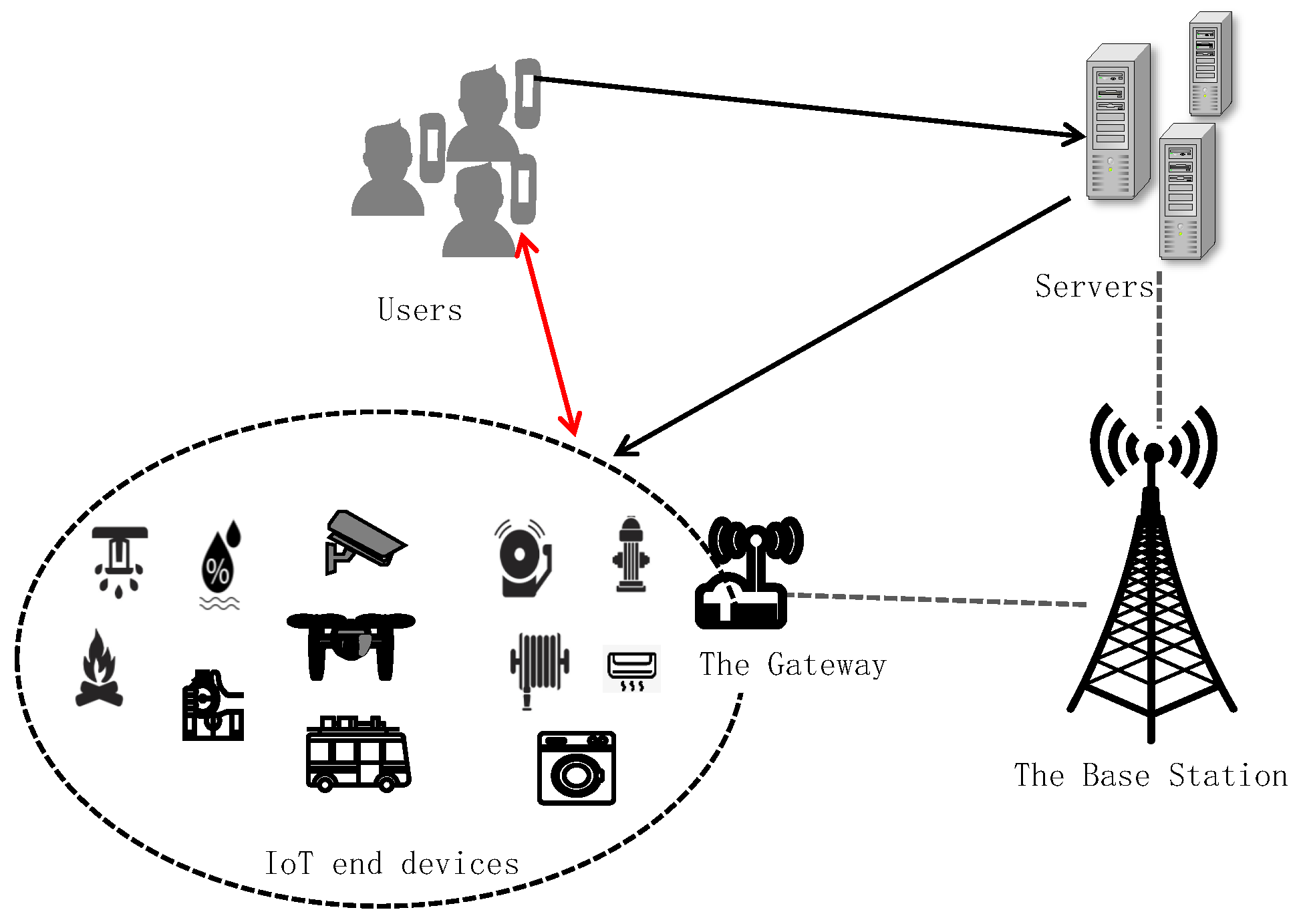
The Internet of Things (IoT) is transforming the way we interact with the physical world by connecting everyday devices to the Internet, creating an intelligent and automated ecosystem [1]. The IoT is transforming multiple fields, including industry, agriculture, power grids, transportation, the environment, healthcare, smart homes, and security and surveillance. As illustrated in Figure 1, the IoT system is composed of IoT devices, gateways, servers, and remote users, which form the foundation to enable the acquisition, processing, and transmission of real-time data. In smart homes, smart healthcare, and industrial IoT application systems, users need to remotely access or control IoT devices and send them specific instructions [2]. Without effective user authentication, attackers can impersonate legitimate users and send fake malicious instructions to IoT devices, threatening the security of the entire system. IoT user authentication protocols enable secure authentication and session key negotiation between users and IoT devices through an intermediate server, allowing users to access or control IoT devices directly and securely. Therefore, establishing a robust IoT authentication mechanism is crucial to ensuring these systems’ security [3].
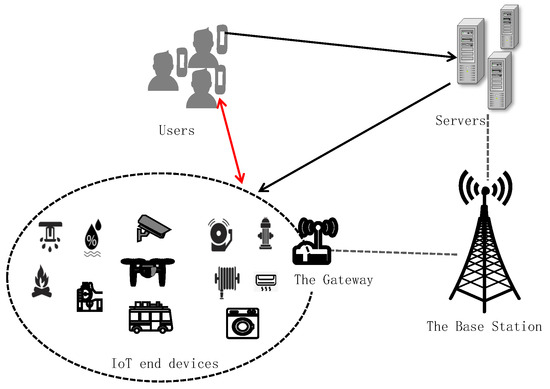
Figure 1.
Structure of IoT systems.
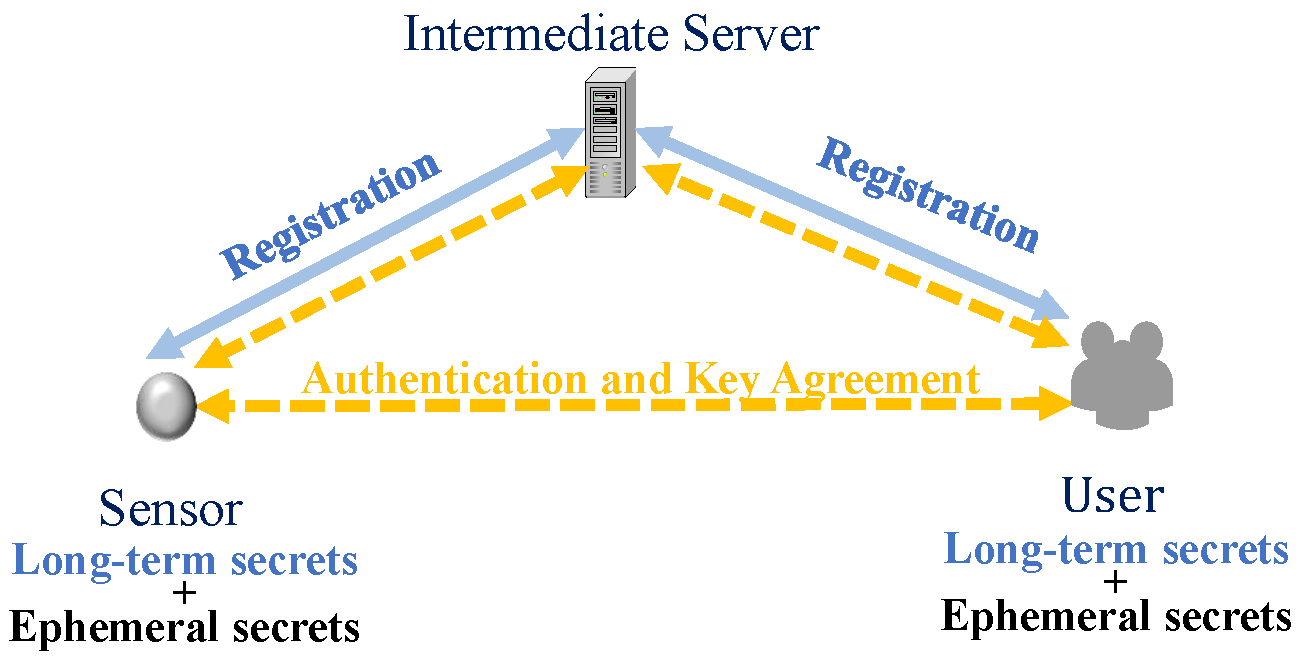
As illustrated in Figure 2, in the IoT user authentication protocols, after the devices and users register, each entity obtains its own long-term key. Subsequently, the user and the IoT device use these long-term keys, as well as the temporary keys generated during authentication, to generate authentication messages. These messages are then exchanged between the two entities for mutual authentication and negotiation of session keys. However, IoT devices are easily captured physically when they are usually deployed in unattended environments. Attackers may gain access to long-term secrets through side-channel attacks [4,5]. In addition, servers may suffer from data leakage and unauthorized access due to malware or misconfigurations [6,7]. Given that IoT systems often involve sensitive data, including user location information, network activities, and consumption habits, as well as potentially confidential corporate or national security information, authentication and authorized data access have become essential security requirements for IoT applications. In addition, the design of authentication protocols is particularly challenging as IoT devices are resource-limited, usually powered by batteries, and have limited computing, storage, and communication capabilities [8].
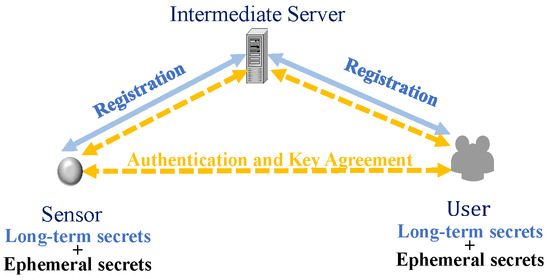
Figure 2.
IoT user authentication protocol.
In recent years, numerous IoT user authentication protocols [9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26] have been proposed as shown in Table 1. However, the existing schemes generally assume that the servers (registration center (RC) and intermediate server) are fully trusted, overlooking the potential threat of insider attackers. In real applications, server data breaches and unauthorized port listening events are common due to issues such as misconfigurations, memory leaks, and malware. In addition, insider-infected actions (such as employees, contractors, or partners) pose significant security risks to IoT systems [6,7]. During registration, the RC generates long-term keys for the IoT devices and stores them on both the devices and the intermediate server. This setup allows insiders on the servers to access the keys, potentially enabling insider attacks. For example, insider users on the intermediate server can perform insider impersonation attacks [9,10,12,13,14,15,17,19,22,23,24,25,26] or derive session keys negotiated between users and IoT devices, resulting in protocols with no key privacy security [9,10,12,13,15,26]. Another critical issue is the handling of ephemeral secrets, which are often precalculated and stored in insecure memory [27]. Unfortunately, this risk is largely neglected in current IoT user authentication protocols [9,10,12,13,14,15,16,17,18,19,20,21,22,24,25,26], leaving these schemes vulnerable to ephemeral secret leakage (ESL) attacks. Furthermore, many protocols lack essential features, such as perfect forward security (PFS) and anonymity. They are also prone to offline password guessing attacks and are inefficient for resource-constrained IoT devices. More importantly, with the rapid growth regarding IoT devices, intermediate servers must manage a large number of users and device connections, which makes the performance of authentication schemes highly dependent on the server’s computational and processing capabilities [25]. However, there is still a lack of substantial research focused on optimizing server overhead in the current studies.

Table 1.
Summary of relevant ECC-based user AKA protocols.
The design of security protocols is based on the underlying security model, where the attacker model defines the potential capabilities and goals of the attackers. This model not only determines the security assumptions of the protocol but also directly shapes the evaluation framework for security analysis. In the existing research, the Dolev–Yao security model [29] and the eCK security model [30] are the most widely accepted. The Dolev–Yao model assumes that the attacker has full control over the communication channel, allowing him to intercept, modify, forge, and replay messages. The eCK model extends this by allowing the attacker to access sensitive information, such as long-term keys, session keys, and ephemeral secrets. However, the eCK model focuses mainly on two-party single-factor authentication protocols and does not fully address multifactor or three-party authentication scenarios. In recent years, there has been growing attention regarding attacker models for multifactor user authentication protocols. Yoneyama [31] extended the eCK model to password-based three-party authentication key-exchange protocols but did not account for threats related to smart card loss and offline password guessing attacks. Wang et al. [32] studied the impact of the loss of smart cards and offline password guessing attacks on the security of two-factor authentication protocols, and their results have been adopted as a standard in many subsequent schemes. However, their work did not address the leakage of ephemeral secrets. In conclusion, the existing security models for IoT user authentication fail to fully cover key security threats, such as insider attacks and ephemeral secrets.
To address the issues in the existing IoT user authentication protocols, we introduce a new security model, IoT-3eCK. This model is based on real-world network threats, enhances the attacker’s capabilities, and refines the evaluation criteria for IoT user authentication protocols. In the IoT-3eCK model, the servers are assumed to be semi-trusted entities, and the attackers may be insiders from either the RC or the intermediate server. The attacker has access to the registration information of users, servers, and IoT devices and can acquire the ephemeral secrets of all the protocol participants, including users, servers, and IoT devices. Based on this new security model, we analyze the Wang et al. scheme [25], identifying the challenges posed by insider and ESL attacks and uncovering the causes of their vulnerabilities. Then, we propose a new IoT user authentication protocol that effectively defends against insider attacks while meeting various security requirements. The protocol integrates a dynamic pseudonym-based anonymous authentication mechanism with an ECC key-exchange mechanism, ensuring anonymity and other critical security properties while significantly reducing the computational overhead on the intermediate server. The performance analysis shows that, compared to the existing solutions, the proposed protocol reduces communication overhead by more than 23%, computational overhead by over 22%, and, most notably, computational overhead on the intermediate server by over 95%, greatly improving the system efficiency.
The main contributions of this paper are as follows.
- (1)
- A new security model, IoT-3eCK, is proposed, which enhances the attacker’s capabilities regarding IoT user authentication protocols and refines the evaluation criteria for these protocols.
- (2)
- Based on the new security model, analysis of the Wang et al. scheme [25] is provided, identifying the challenges of insider and ESL attacks and uncovering the causes of their vulnerabilities.
- (3)
- A secure and efficient IoT user authentication protocol is introduced. The proposed scheme offers security properties such as key privacy and perfect forward security and is resilient to insider attacks, ESL attacks, and other common threats.
- (4)
- The security of the protocol is formally proven using the random oracle model, and its correctness is verified with the ProVerif 2.0 automated verification tool. In addition, performance comparisons demonstrate significant reductions in communication and computation costs.
The paper is structured as follows. Section 2 reviews the related work. Section 3 presents the proposed new security model. Section 4 provides a cryptanalysis of the scheme by Wang et al. [25]. Section 5 outlines the proposed IoT user authentication protocol. Section 6, Section 7, Section 8 and Section 9 present the security analysis and performance comparison, respectively. Finally, Section 10 concludes the paper.
2. Related Work
With low computational complexity and high efficiency, many user authentication protocols based on symmetric cryptography [33,34,35] have been proposed. However, these proposals require users and designated IoT devices to share symmetric keys beforehand, which is impractical due to the large number of IoT devices. Physically Unclonable Functions (PUFs), a promising lightweight hardware security primitive, have been used in numerous user authentication protocols for the IoT [3,36,37]. In these schemes, each entity needs to register one or more challenge–response pairs of its individual PUF with the server beforehand to enable authentication between the registered entity and the server, which leads to inflexibility and inefficiency. Halevi et al. [38] and Wang et al. [39] also indicated that most symmetric cryptography and hash-based user authentication proposals are insecure when dealing with user anonymity, PFS, and smart card security breach attacks. Public-key technology is vital for improving security, but it has high computational and communication overhead. Elliptic curve cryptography (ECC) has been adopted in IoT user authentication to balance security and efficiency because it provides a smaller key size compared to other methods with the same level of security [40,41].
In recent years, many ECC-based IoT user authentication protocols have been introduced. In 2016, Jiang et al. [9] introduced a user authentication protocol for wireless sensor networks (WSNs), a critical component of the IoT. This protocol employs two-factor authentication through temporary credentials and claims to resist various attacks, ensuring both the anonymity and untraceability of communications. However, the protocol assumes that the servers are fully trusted, neglecting the security threat posed by insider attackers within the servers. During registration, the RC generates and preloads long-term secrets for the sensors, storing these credentials on the intermediate server. This design exposes the protocol to insider impersonation attacks and key privacy issues, where insider users of the servers can impersonate sensors to complete authentication and key agreement with users, as well as obtain the session key negotiated between the user and the sensor during the authentication process. In addition, the scheme does not account for the possibility that an attacker may gain access to the ephemeral secret, making it vulnerable to ESL attacks. Furthermore, the scheme is also susceptible to offline password guessing attacks and does not provide PFS and timely typo detection. In 2017, Wu et al. [10] indicated that Chang et al. [11] were unable to resist offline password guessing attacks and could not maintain PFS. Then, they presented an improved one for WSNs, but it lacks user untraceability, key privacy, and PFS and suffers from offline password guessing, ESL, and insider sensor impersonation attacks. Challa et al. [12] introduced signature-based user authentication for the IoT. However, it is incapable of withstanding attacks of offline password guessing, impersonation, and insider IoT device impersonation, as well as failing to provide key privacy, user anonymity, and untraceability. In 2018, Li et al. [13] presented an IoT user authentication protocol for industrial IoT to ensure legitimate access to sensitive sensor data. But, this proposal [13] suffers from offline password guessing, replay, insider sensor impersonation, and impersonation attacks and lacks key privacy. Li et al. [14] identified the deficiencies of the scheme [9] and then presented an enhanced scheme for WSNs. However, the enhanced scheme [14] is prone to offline password guessing, insider sensor impersonation, and ESL attacks and cannot offer user untraceability, key privacy, and PFS. In 2019, Shuai et al. [15] presented an IoT user authentication scheme for smart homes. However, this scheme is subject to offline password guessing, insider IoT device impersonation, and ESL attacks and is unable to offer user untraceability, key privacy, and PFS. Lu et al. [28] introduced an IoT user authentication scheme for WSNs. Moreover, this scheme had a design flaw: i.e., an attacker could quickly determine the session key based on the sensor ID and the information detected throughout the open channels. In 2020, Li et al. [17] stated that most of the existing AKA proposals could not fulfill local password change and PFS while being vulnerable to stolen smart card attacks, and then introduced an improved version. Unfortunately, the scheme [17] is prone to sensor impersonation and offline password guessing attacks with poor usability. The server must enumerate the stored information and then calculate the relevant values to determine the sender’s ID when a reply message is received during authentication.
In 2021, Sadhukhan et al. [18] presented an authentication scheme for remote IoT users, but it suffers from replay, ESL, man-in-the-middle, and DoS attacks and cannot offer user anonymity and timely typo detection. Wazid et al. [19] introduced an IoT user authentication protocol to secure 6G-enabled networks in a box deployed in industrial applications. Wang et al. [25] revealed that the scheme [19] fails to provide user untraceability and PFS; it is also vulnerable to offline password guessing, desynchronization, and man-in-the-middle attacks. Additionally, the scheme lacks key privacy and cannot withstand insider IoT device impersonation attacks. Srinivas et al. [20] proposed an IoT user authentication scheme for IoT big data collection. However, this scheme [20] is fragile to device impersonation attacks and device session key compromise attacks and cannot afford user anonymity and PFS [22]. In 2022, Sutrala et al. [21] introduced an IoT user authentication scheme for software-defined network-based industrial cyberphysical systems [21]. Later, Wang et al. [23] stated that the scheme [21] is not able to resist smart card/device loss attacks and offline password guessing attacks and cannot offer user untraceability. Tanveer et al. [22] analyzed previous related IoT user authentication protocols and then proposed an improved version for the Internet of Drones. However, the scheme [22] cannot maintain user untraceability, PFS, or resistance to man-in-the-middle attacks and offline password guessing attacks. In 2023, Chen et al. [24] introduced a two-factor user authentication protocol for multi-gateway WSNs. Unfortunately, this scheme suffers from insider sensor impersonation and ESL attacks. Wang et al. [25] analyzed Wazid et al. [19] and then proposed an IoT user authentication scheme for cloud-assisted IoT with four parties prone to insider IoT device impersonation and ESL attacks. In 2024, Kumar et al. [26] proposed an IoT user authentication scheme to access sensitive data from sensor nodes by executives in coal mining scenarios. But, this scheme is not resistant to insider sensor impersonation attacks and ESL attacks, lacking PFS and key privacy.
In summary, the previous IoT user authentication schemes suffered from insider sensor impersonation attacks. Furthermore, most of the schemes are vulnerable to ESL and offline password guessing attacks, lack essential security features such as PFS, key privacy, and anonymity, or are unsuitable for resource-constrained IoT due to inefficiencies.
3. Security Model Based on Semi-Trusted Servers
This section defines a practical security model, IoT-3eCK, based on the network model. The model enhances the attacker’s capabilities and introduces an evaluation framework consisting of 10 attributes and 12 security goals, which supports a comprehensive analysis of IoT user authentication schemes.
3.1. IoT User Authentication Network Model
As illustrated in Figure 1, the network model consists of remote users, intermediate servers, IoT devices, and adversaries. RCs are specialized servers that are responsible for overseeing key generation, distribution, management, and communication activities within an application system or group. We assume that an IoT user authentication protocol, , involves and , where , r, s, and t denote the number of users, servers, and IoT devices, respectively. The servers are considered semi-trusted, meaning they will reliably execute the protocol but may also collaborate with other participants to potentially gain private information. Each remote user can dynamically join different systems or groups by registering with a different RC. However, a sensor can belong to a single system or group.
3.2. Adversary Model
To characterize the insider threat, we introduce the attacker capability A7: assume that is an insider user of RC, capable of corrupting servers, learning the long-term private key of the servers, and eavesdropping on and stealing messages during the registration, login, and authentication phases. To address the threat of ephemeral key disclosure, we introduce the attacker capability A8: assume that can obtain ephemeral secrets of the user, sensor, and RC. The primary capabilities of in the new adversary model, IoT-3eCK, for the IoT user authentication protocol are as follows:
- A1.
- takes full control over communication channels, intercepting, modifying, blocking, and deleting messages exchanged between the user, the RC, and the IoT devices at will.
- A2.
- can offline all items in the set of the space and password space within polynomial time.
- A3.
- is able to capture the previous session keys between the user and the sensor.
- A4.
- can learn the user’s passwords, extract long-term secrets from the smart card, and obtain the user’s biometrics, but not all three at the same time.
- A5.
- is able to compromise the sensor and extract its long-term secrets.
- A6.
- can obtain the secret key of RC when evaluating forward secrecy.
- A7.
- The adversary could be an insider user of the RC or compromise the server S, gaining access to its long-term private key and intercepting/stalling messages during any phase (registration, log-in, authentication).
- A8.
- can obtain ephemeral secrets of the user, sensor, and RC.
3.3. Evaluation Criteria
Our evaluation criteria are modified from widely accepted frameworks [2,8,25,42,43]. To mitigate insider attacks, C1 and C2 are introduced. First, during the registration phase, the authentication secrets must be protected, ensuring that the long-term secrets of the user and sensor, as well as the user’s password and biometric data, are not accessible to insider users of the RC. Second, insider users of intermediate servers, including those in the RC, should not have access to the session keys established between the user and the sensor. Furthermore, C10 has been improved to include resistance to ESL attacks and insider impersonation attacks, further strengthening its defenses against known threats.
- C1.
- No registering confidential exposure: When registering the long-term secrets of the user and sensor, the user’s password and biometrics cannot be derived by the insider user of RC.
- C2.
- Key privacy: The insider user of RC or the intermediate server cannot access the session keys between the user and the sensor.
- C3.
- No password verifier-table: RC does not store user passwords or any derived password values in a database.
- C4.
- Password-friendly: The user should freely choose and change an easy-to-remember password locally.
- C5.
- Sound repairability: The scheme enables the easy revocation of smart cards, that is, the users are able to revoke their cards with unchanging identity.
- C6.
- Mutual authentication and key agreement: The user and the sensor can verify each other and agree on a shared session key.
- C7.
- Forward secrecy: The shared session key could not be captured even if the adversary obtained the long-term secrets of the user, the RC, and the sensor.
- C8.
- Timely typo detection: If a user enters an incorrect password or biometrics when logging in, he or she will be informed in time.
- C9.
- User anonymity: The scheme is designed to protect user identity and prevent user activities from being traced.
- C10.
- Resistance to known attacks: The scheme resists known attacks, including ESL attacks, insider impersonation attacks, unknown key share attacks, known key attacks, smart card loss attacks, stolen verifier attacks, impersonation attacks, desynchronization attacks, parallel session attacks, replay attacks, offline password guessing attacks, key control, and node capture attack.
4. Analysis of Wang et al.’s Protocol
Wang et al. [25] proposed a secure and efficient IoT user authentication protocol for cloud-assisted IoT systems. Participants include IoT devices, gateways, cloud servers, and external users. Security analysis concluded that this scheme is vulnerable to insider impersonation attacks and ESL attacks.
4.1. Review of Wang et al.’s Protocol
The notations used are listed in Table 2.

Table 2.
Notations of the protocols.
4.1.1. Registration Phase
In the registration phase, the IoT device is registered with the gateway, and both the gateway and the user are registered with the cloud server. The cloud server first selects an elliptical curve E, with a base point P. After initialization, the cloud server possesses long-term secret keys x and y(), shared with the user and the gateway, respectively. The cloud server distributes the gateway secret key to the gateway as an authentication credential. The gateway and the IoT devices share a secret key , where is the long-term secret key of the gateway.
The user registration process is as follows:
- R1.
- first selects the identity and password , and inputs the biometric factor . Then, selects a random number and calculates and . Next, sends the registration request to the cloud server.
- R2.
- The cloud server selects a timestamp and a random number and then calculates and . The cloud server stores in the database and sends to .
- R3.
- Upon receiving , selects a random number a and then calculates , , , , . Finally, stores .
4.1.2. Login and Authentication
If wants to access the IoT device , can initiate the following login and authentication request to the gateway as follows:
- A1.
- inputs and calculates , , , and . Then, verifies whether is valid. If it is true, selects and computes , , , , , and . Finally, sends to the cloud server.
- A2.
- After receiving , the cloud server first calculates and . Then, it retrieves using . If , the cloud server terminates the session; otherwise, the cloud server calculates , , and . If , the cloud server terminates the session; otherwise, it determines the gateway to which belongs, selects a random number r, and calculates , , , and . The cloud server then sends to the gateway.
- A3.
- Upon receiving , the gateway first calculates , , and . Then, it verifies whether . If it is true, the gateway selects a random number and computes , , and . The gateway then sends to .
- A4.
- Upon receiving , calculates and . If , terminates the session; otherwise, selects a random number and then calculates and . Then, calculates the session key and . Finally, sends to the gateway.
- A5.
- After receiving the response from , the gateway calculates . If , the gateway terminates the session; otherwise, the gateway calculates and sends to the cloud server.
- A6.
- After receiving the response from the gateway, the cloud server calculates . If , the cloud server terminates the session; otherwise, it calculates and sends to .
- A7.
- Once receives the response from the cloud server, it calculates . If , calculates as the session key.
4.2. Flaws of Wang et al.’s Protocol
4.2.1. Vulnerability to Insider IoT Device Impersonation Attacks
Consider an attacker as an insider user of the gateway. The attacker first selects a random number and computes , , and . The attacker then calculates and sends to the cloud server. Upon receiving , the cloud server computes . Since , the cloud server computes and sends to . Upon receiving the response from the cloud server, calculates . Clearly, , and computes as the session key. Similarly, insider users of the cloud server can also initiate impersonation attacks.
4.2.2. Vulnerability to ESL Attacks
If is compromised, the attacker can combine the channel messages and to calculate . Similarly, if is leaked, the attacker can combine channel messages and to compute , , and . Thus, the scheme is vulnerable to ESL attacks.
5. Proposed Protocol
The proposed protocol has four phases: system initialization, registration, login and authentication, and user password and biometric update.
5.1. System Initialization
The implementation of the system is carried out by RC online. Firstly, chooses an elliptic curve over with a base point P. In addition, a medium number is chosen. Second, RC opts for its identifier and its long-term private key and computes as its public key. Then, RC chooses two one-way hash functions, and , for generating hashes and one-time credential identifiers, respectively. Finally, RC keeps secure and issues the public parameters of the system .
5.2. Registration
5.2.1. IoT Device Registration
IoT device selects an RC to complete registration and obtain authentication credentials before the entry of the system. The registration process is as follows:
- R1:
- selects its identifier and a random number and then computes . Third, sends the registration requisition request message, {}, to through secure channels.
- R2:
- In response, checks if has been registered. If so, is required for a new request. Otherwise, RC opts for a random number as the partial private key of and computes as the public key of . After that, RC publishes and replies to through secure channels. Lastly, RC computes and stores secretly.
- R3:
- After receiving , computes as its private key. Then, checks whether . If it holds, computes and stores .
Remark 1.
5.2.2. User Registration and Revocation
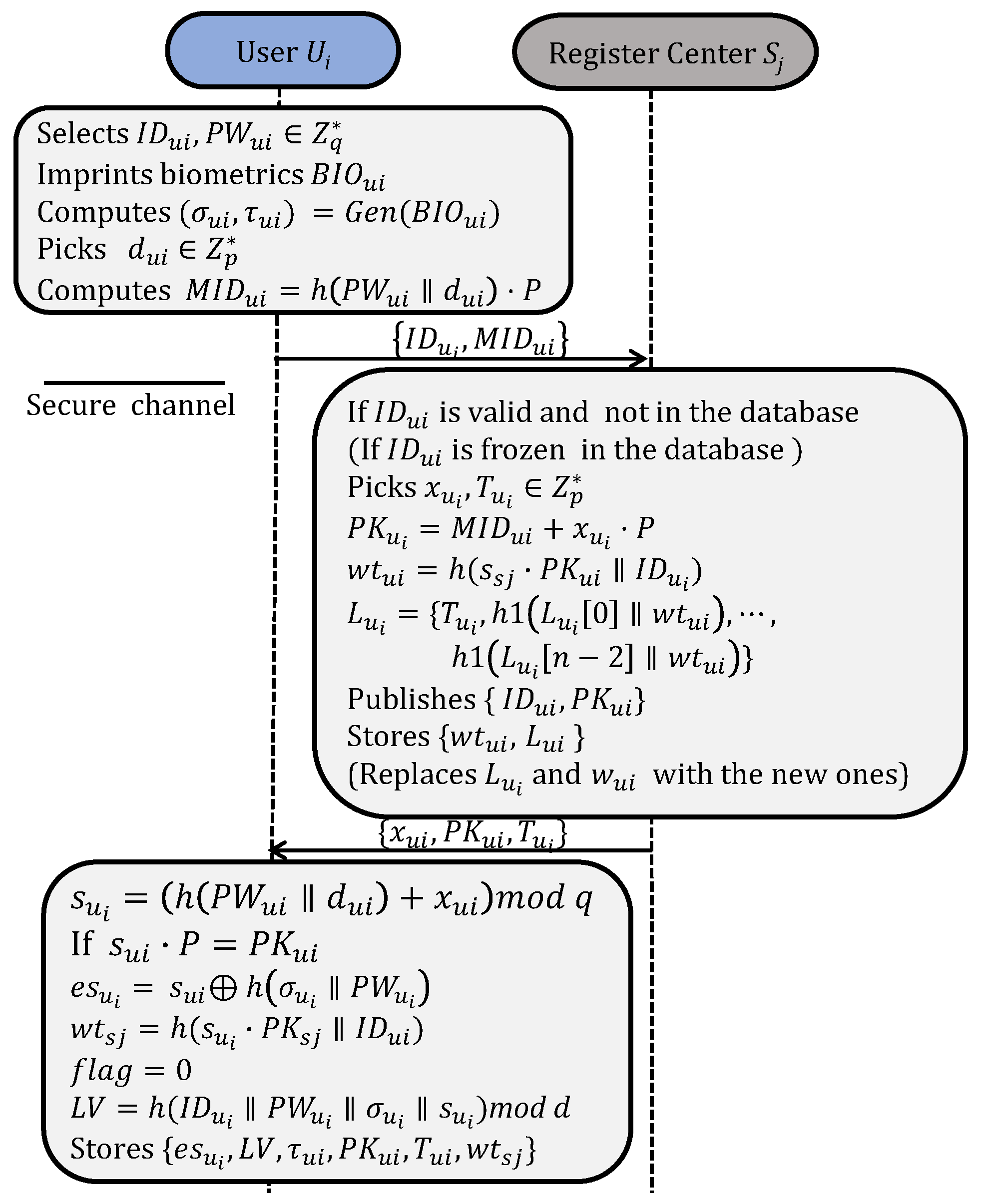
Users can dynamically join different systems through the registration processes shown in Figure 3. The fuzzy verifier [2,44] is used to eliminate offline password guessing attacks. is a temporary one-time credential assigned to the user and is marked with to indicate that has not been used. A corresponding untraceable list is generated and stored in RC, where n represents the number of times a user is permitted to re-initiate the authentication. After registration, stores . publishes and stores secretly. A user account can be updated with the same process if it is frozen.
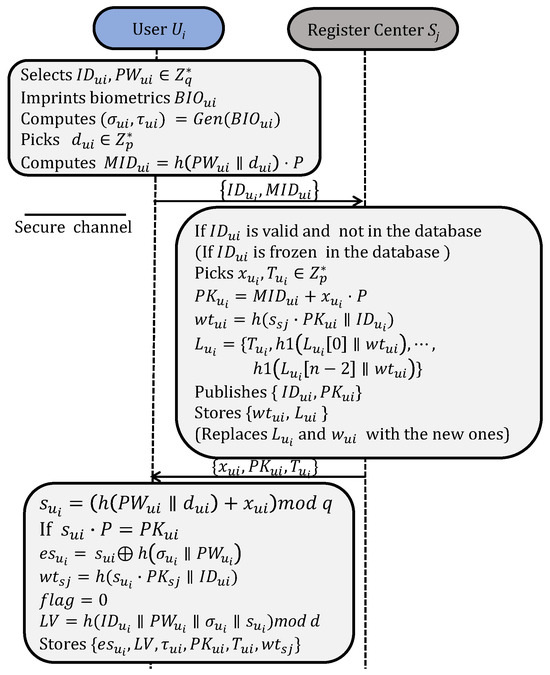
Figure 3.
User registration and revocation.
5.3. Login and Authentication
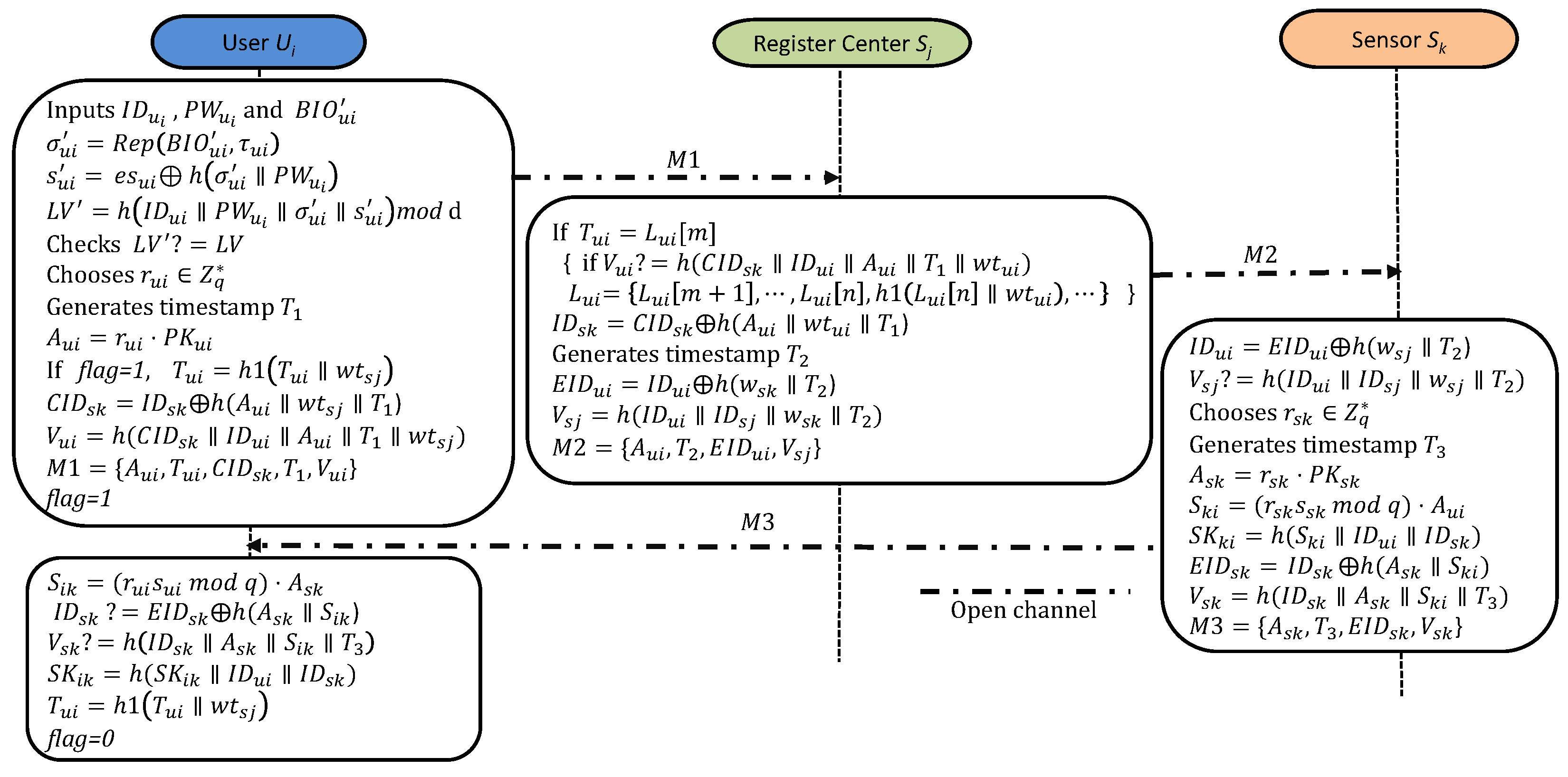
This phase between the user , the RC , and the sensor is shown in Figure 4.
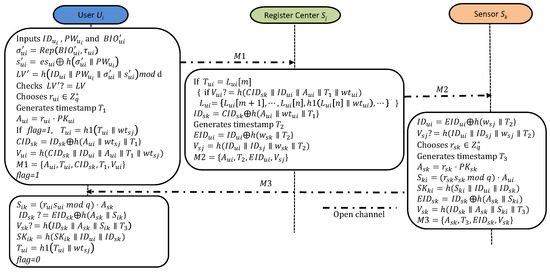
Figure 4.
Login and authentication.
- A1:
- To begin, inputs , , and . Then, calculates and and obtains a verifier . Finally, verifies if . If this condition is not met, the log-in process will end.
- A2:
- chooses a random and generates the current timestamp . Afterwards, calculates . If , it indicates that has been used. In this case, updates to . Third, encodes the identity of the desired sensor into dynamic identity as . Finally, generates a verifier and sends the request message to .
- A3:
- Upon receiving , verifies its freshness with the timestamp . Next, verifies using temporary credentials . If and , then confirms that the sender is and updates the untraceable list for as follows: . Otherwise, will reject the session.
- A4:
- generates the time stamp and encodes the identity of as . Finally, generates a verifier and sends the message to the IoT device .
- A5:
- Upon receiving M2, checks its freshness with the timestamp . Following that, decodes . Finally, verifies the authenticity of by checking whether and ensures the integrity of the message received. If not, will terminate the verification immediately.
- A6:
- Firstly, selects a random and generates the current timestamp . After that, calculates , , and obtains the session key shared with as . Then, encodes . Third, generates its verifier as . Finally, transmits the response message to .
- A7:
- Upon receiving M3, first checks its freshness with the timestamp . After that, calculates . Third, verifies whether and . If not, will terminate the session. Finally, obtains the session key shared with as and updates as with .
5.4. User Password and Biometric Update
A registered user can renew her password and biometric information following the steps outlined below.
first inputs , and and then computes , , and . Third, checks if . If so, inputs and and computes , , and . Finally, replaces with .
6. Formal Security Analysis
This section provides the formal proof of the proposed protocol in the IoT-3eCK security model.
6.1. Relevant Definitions
Participants: The proposed protocol involves three participants: , , and . Each participant has several instances denoted by , , and ), respectively. Any instance can be referred to as . A session identifier, , is created by concatenating all messages sent and received for the current session. An instance can exist in three states. If the most recent expected protocol message is received, the instance enters the state . If an incorrect message is received, the instance transitions to the state. An instance will become ⊥ if the input is not responded to.
Partners: Instances I and are considered only if all three conditions are met: (i) Both instances are currently in the state. (ii) They have mutually authenticated and shared the same . (iii) They are partners with each other.
Freshness: An instance is considered fresh if fails to obtain the session key (or ) between and by making , (, or queries before performing a query.
Adversary: Under the IoT-3eCK adversary model, can interact with , , and through the following queries:
- (1)
- : can observe all messages transmitted between , , and .
- (2)
- : can send a message m to I and receive a response.
- (3)
- : This query reveals the ephemeral secret key of I to .
- (4)
- : can obtain the session key between I and its partner.
- (5)
- : can obtain the security credentials held by .
- : acquires and .
- : acquires and .
- : acquires and .
- (6)
- : can retrieve all the security credentials held by .
- (7)
- : can retrieve all the security credentials held by .
- (8)
- : This query is used to simulate the semantic security of the session key.
- If the session key is not established or I is not fresh, ⊥ will be returned.
- Otherwise, a coin is flipped.
- −
- If , I returns the session key to .
- −
- If , I returns a random string of the same length as the session key.
- (9)
- : The query provides with a randomly generated number that serves as the hash output of M.
- (10)
- : Once this query is executed, the session key held by I is deleted.
6.2. Provable Security Analysis
Before the security analysis, we first define the complexity assumptions. We then provide a formal proof to evaluate the security of the session key (or ) under the ROM model.
Let denote a non-singular elliptic curve over a finite field , G be an additive group of order q of , and P be the base point of the group.
Definition 1.
Elliptic Curve Discrete Logarithm (ECDL) Hardness Assumption: Given , finding is computationally hard, and the probability that is able to resolve the problem, , is negligible for sufficiently small ϵ,
Definition 2.
Computational Diffie–Hellman (CDH) Hardness Assumption: Given , figuring out is computationally hard, and the probability of resolving the problem is negligible for sufficiently small ϵ,
Definition 3.
The security of (or ) is modeled by the game . In this game, is allowed to perform one query, where I is both and , and I returns a single bit . can issue many other queries to I.
Let denote the probability that successfully wins the game . The advantage of in breaking the semantic security of (or ) is defined as
Definition 4.
In the context of the adversarial model eCK, a user authentication scheme is semantically secure if is negligible for any adversary.
Theorem 1.
Let be an adversary that can break the semantic security of (or ) by creating up to queries and and queries, all within polynomial time t. Let the random numbers and hash outputs be l-bit values, the password dictionary space be N, following Zipf’s law as in [17], and the biometric secret key have a length of bits with a false-positive probability of . Then, the advantage of is that
where and are Zipf’s parameters.
Proof.
The semantic security of (or ) is defined by a series of games . In these games, represents the value of b in the query correctly predicted by , and denotes the probability that the event will occur.
: The game begins by simulating a real attack in ROM mode. Thus, we have the following:
: In this game, can be the query to obtain , , and exchanged between , , and . Then, can use and to verify whether the calculated key (or ) is genuine or not. Since (or ) cannot be determined directly from these messages, there is no distinguishable difference between and . Therefore,
Three lists are used to store related results: for the inputs and outputs of queries, for the answers to queries asked by , and for the inputs and outputs of queries.
: The game ends when message transcripts and hash queries collide. The components of messages , , and are evenly distributed. Based on the birthday paradox, we obtain
: In this game, attempts to forge the messages , , and without access to the oracle. The process is as follows:
- Constructing M1: needs to issue queries to successfully construct . Thus, the following values must be in : (. The probability of success is .
- Constructing M2: Similarly, we have , , and the probability is .
- Constructing M3: Again, we have , , and the probability is .
Thus, is indistinguishable from game unless successfully constructs , , and . Thus,
: This game terminates if is able to retrieve (or ). If manages to compute the session key, this implies that it has solved the ECDL or ECD problems. Furthermore, the tuple must be stored in . The following cases may occur for to compute or :
- (1)
- issues and .
- : acquires and , and then guesses in queries with a success probability of .
- : acquires and , and then attempts to obtain using two methods. can guess in queries with bits with probability , or replace with collected biometric data with a probability of , where is the probability of similarity of the biometric data. So, the probability is .
- : acquires and , and then attempts to guess in queries. According to Zipf’s law, the probability of password distribution is , where and are Zipf’s parameters.
Next, issues an to obtain of , and then attempts to guess using queries with the probability of . - (2)
- issues and .Firstly, issues a query as summarized above. Next, issues an query to obtain the ephemeral secret of . Then, attempts to guess within attempts, with a probability of .
- (3)
- issues and .Firstly, obtains and . Then, attempts to guess and .
- (4)
- issues and .Firstly, obtains and . Then, tries to guess and .
In all the above cases, cannot figure out (or ) unless it has solved the problem of ECDL or ECD. Hence,
: This game emulates , but the query will terminate if issues an query. The probability of acquiring is at most . Therefore,
Without proper input to the query, cannot differentiate the actual session key from a random one. Therefore,
Given all the probabilities and conditions above, Theorem 1 holds. □
7. Automatic Verification Using ProVerif
ProVerif is a powerful tool for the formal verification of cryptographic protocols. Written in Prolog, it uses Horn clauses and algorithms to perform its tasks. ProVerif is capable of precisely modeling a variety of cryptographic primitives, including shared-key cryptography, public-key cryptography, hash functions, and Diffie–Hellman key-exchange protocols, along with supporting rewriting rules and equations. The tool can demonstrate several important security properties, such as reachability properties, correspondence assertions, and observational equivalence.
The proposed scheme has been verified formally using ProVerif. Table 3 illustrates the processes for , as outlined in Section 4. In this setup, represents a private channel that facilitates communication between and during the registration phase, while and are public channels, with and communicating over and and communicating over during login and authentication. The three participants execute their respective processes, and the scheme is simulated to run in parallel as .

Table 3.
Codes for users with ProVerif.
As shown in Table 4, queries and results confirm that is unable to break the authentication process or determine session keys, ephemeral keys, and long-term keys. The proposed scheme ensures high levels of anonymity, consistency, and mutual authentication.

Table 4.
Simulation results.
8. Analysis of Security Features
8.1. User Anonymity and Untracibility
During authentication, each is used only once, regardless of whether authentication is successful, and the values of and other authentication parameters are unique for each session. Furthermore, due to the secrecy of and , even insider users of RC cannot determine . As a result, the scheme ensures anonymity and untraceability.
8.2. Perfect Forward Security
Even if long-term secrets and are compromised, is still unable to deduce the session key , for , where and . This is due to the fact that the ephemeral secrets and are unknown to . Also, even if is aware of and , he/she cannot deduce .
8.3. Key Privacy
During registration, the system does not store or expose password-related data, nor are any password authentication tables maintained. The user information maintained by RC does not consist of the user’s password and its variants. The long-term keys of and are neither generated by the RC nor known to it. Furthermore, the component of session keys and does not involve RC. Due to the hardness of the ECDL and ECD problems, cannot figure out and even if or are exposed. In a nutshell, no insider user of RC can break the security of the proposal.
8.4. Ephemeral Secret Leakage Attack Resistance
Resistance to ESL attacks comprises the fact that, even if captures the ephemeral keys, and , he/she is unable to obtain the session key or . For , where and , even if and are compromised, cannot deduce because the long-term keys and are unknown to him. Also, even if is aware of and , she cannot deduce .
8.5. IoT Node Capture Attack Resistance
Sensors may be positioned in unattended environments and physically captured by . The credentials can then be easily retrieved. In the protocol, different sensors have different credentials. Therefore, it only leads to the disclosure of session keys between and user , but not between the uncorrupted sensor and user . In other words, the proposed scheme is resistant to IoT node capture attacks and limits the impact of such compromises to the specific nodes affected.
8.6. Timely Typo Detection
The parameter stored on the user’s device enables immediate validation of user inputs. If the user inputs an incorrect ID or password, the computed value will differ from the stored value . As a result, the log-in request will be rejected, ensuring prompt detection and mitigation of typographical errors during authentication.
9. Performance Comparison
9.1. Security Feature Comparison
As shown in Table 5, the comparison of security features indicates that the proposal offers better security and functionality than the related scheme [17,19,20,21,22,25,26]. Compared to existing schemes, the recommended approach effectively provides anonymity, untraceability, PFS, key privacy, and resistance to insider impersonation, ESL, man-in-the-middle, and other attacks.

Table 5.
Security feature comparison.
9.2. Communication Cost
Assume that the lengths of the random number (R), hash output (H), identity (ID), ECC point (G), and timestamp (TS) are 128, 256, 256, 384, and 32 bits, respectively. In the proposed scheme, three messages , , and are transmitted during the login and authentication phase, where , , and . The lengths of , , and are bits, bits, and bits. The total communication cost is bits. The communication overheads of [17,19,20,21,22,25,26] are 3584, 4384, 3296, 3872, 3680, 3456, and 3392 bits, respectively. Table 6 shows that the proposed scheme reduces communication costs from 23% to 42%.

Table 6.
Communication costs.
9.3. Computation Cost
To compare the computational overhead of different schemes, the run times of other cryptographic primitives are tested. A laptop with Intel Core i5-8250U 1.60 GHZ + 16 GB RAM (Intel Corporation, Santa Clara, CA, USA) and Windows 11 serves as the server. A Raspberry Pi 3 Model B+ (Raspberry Pi Ltd., Cambridge, UK) board with ARM Cortex-A53 1.4 GHz + 1 GB RAM (ARM Ltd., Cambridge, UK) serves as the sensor node and user. When p = , the elliptic curve is Curve25519, and the point length is 384 bits; the average running time is shown in Table 7. Table 8 illustrates that our scheme reduces computation costs by comparing 22% to 56% with the related scheme. In particular, the computational overhead of the intermediate server is reduced by more than 95%. These results highlight significant optimization of resource consumption in the proposed scheme, particularly in resource-constrained IoT environments and scenarios where the intermediate server is connected to many nodes.

Table 7.
Run times of different cryptographic primitives.

Table 8.
Computation costs.
10. Conclusions
In IoT systems such as smart homes and smart healthcare, IoT user authentication protocols enable secure authentication and session key negotiation between users and IoT devices through an intermediate server, thereby ensuring that users can securely access sensor data directly or control IoT devices remotely. However, the existing IoT user authentication schemes typically assume that the server is fully trusted, ignoring the risk of potential attacks from inside entities. For example, an insider user may launch an insider impersonation attack and steal the session key negotiated between the user and the end device. In addition, most of the existing protocols lack key security properties, such as effective defense against ESL attacks and offline password guessing attacks, as well as perfect forward security. Furthermore, as the scale of IoT devices grows dramatically, intermediate servers need to manage a large number of user and device connections, making the performance of authentication schemes highly dependent on the computational power of the servers.
The design of security protocols is based on the security model, and the existing security model for IoT user authentication still has limitations, making it difficult to comprehensively deal with insider attacks and temporary random number leakage. To enhance the security of IoT user authentication protocols, this paper proposes a new security model for IoT user authentication, IoT-3eCK, which assumes that the intermediate server is semi-trusted and enhances the attacker model to improve the security requirements of IoT user authentication protocols. Based on this security model, this paper designs an enhanced and efficient IoT user authentication protocol. In the registration phase, the protocol ensures that long-term secrets, user passwords, and biometric data of users and end devices are not deduced by insider users in the registration center, effectively preventing internal attacks. In the authentication phase, the protocol combines a dynamic pseudo-identity anonymization mechanism and an ECC key-exchange mechanism to ensure that the protocol satisfies additional security properties. The performance analysis shows that, compared to the existing schemes, the protocol reduces the communication cost by more than 22% and the computational overhead by more than 23%, especially on the intermediate server side by more than 95%, which significantly improves system efficiency. In addition, the security of the new protocol is rigorously proved using a randomized predicate machine model and verified using an automated verification tool.
Author Contributions
Conceptualization, S.H.; methodology, S.H.; software, S.H.; validation, S.H.; formal analysis, S.H.; investigation, S.H. and L.C.; resources, S.H.; data curation, S.H.; writing—original draft preparation, S.H.; writing—review and editing, S.H., Y.Z., Y.G., Y.C., W.Z. and L.C.; visualization, S.H.; supervision, S.H. and L.C.; project administration, S.H., Y.C. and L.C.; funding acquisition, S.H. and L.C. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by National Natural Science Foundation of China (Grant 62302324), in part by Sichuan Province Science and Technology Support Program (Grants 2024NSFSC0500 and 2024YFHZ0023), and in part by the Fundamental Research Funds for the Central Universities (Grant YJ202420).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article. The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding authors.
Conflicts of Interest
The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
References
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A Survey on Internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Gope, P.; Das, A.K.; Kumar, N.; Cheng, Y. Lightweight and Physically Secure Anonymous Mutual Authentication Protocol for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2019, 15, 4957–4968. [Google Scholar] [CrossRef]
- Prouff, E.; Rivain, M.; Bevan, R. Statistical Analysis of Second Order Differential Power Analysis. IEEE Trans. Comput. 2009, 58, 799–811. [Google Scholar] [CrossRef]
- Wang, P.J.; Zhang, Y.J.; Zhang, X.L. Research of differential power analysis countermeasures. Dian Zi Yu Xin Xi Xue = Bao J. Electron. Inf. Technol. 2012, 34, 2774–2784. [Google Scholar] [CrossRef]
- Abulencia, J. Insider attacks: Human-factors attacks and mitigation. Comput. Fraud. Secur. 2021, 2021, 14–17. [Google Scholar] [CrossRef]
- Robayo, T.A. The Enemy Within: A Framework for Understanding the Lifecycle of the Malicious Insider Threat to Information Systems. Ph.D. Thesis, Saint Leo University, Saint Leo, FL, USA, 2022. [Google Scholar]
- Wang, D.; Wang, P. Two Birds with One Stone: Two-Factor Authentication with Security Beyond Conventional Bound. IEEE Trans. Dependable Secur. Comput. 2018, 15, 708–722. [Google Scholar]
- Jiang, Q.; Ma, J.; Wei, F.; Tian, Y.; Shen, J.; Yang, Y. An untraceable temporal-credential-based two-factor authentication scheme using ECC for wireless sensor networks. J. Netw. Comput. Appl. 2016, 76, 37–48. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S. A privacy-preserving and provable user authentication scheme for wireless sensor networks based on Internet of Things security. J. Ambient. Intell. Humaniz. Comput. 2017, 8, 101–116. [Google Scholar] [CrossRef]
- Chang, C.C.; Le, H.D. A Provably Secure, Efficient, and Flexible Authentication Scheme for Ad hoc Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2016, 15, 357–366. [Google Scholar] [CrossRef]
- Challa, S.; Wazid, M.; Das, A.K.; Kumar, N.; Goutham Reddy, A.; Yoon, E.J.; Yoo, K.Y. Secure Signature-Based Authenticated Key Establishment Scheme for Future IoT Applications. IEEE Access 2017, 5, 3028–3043. [Google Scholar]
- Li, X.; Niu, J.; Bhuiyan, M.Z.A.; Wu, F.; Karuppiah, M.; Kumari, S. A Robust ECC-Based Provable Secure Authentication Protocol with Privacy Preserving for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3599–3609. [Google Scholar]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Sangaiah, A.K.; Choo, K.K.R. A three-factor anonymous authentication scheme for wireless sensor networks in internet of things environments. J. Netw. Comput. Appl. 2018, 103, 194–204. [Google Scholar]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar]
- Yeh, H.L.; Chen, T.H.; Liu, P.C.; Kim, T.H.; Wei, H.W. A Secured Authentication Protocol for Wireless Sensor Networks Using Elliptic Curves Cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A Secure Three-Factor User Authentication Protocol with Forward Secrecy for Wireless Medical Sensor Network Systems. IEEE Syst. J. 2020, 14, 39–50. [Google Scholar]
- Sadhukhan, D.; Ray, S.; Biswas, G.P.; Khan, M.K.; Dasgupta, M. A lightweight remote user authentication scheme for IoT communication using elliptic curve cryptography. J. Supercomput. 2021, 77, 1114–1151. [Google Scholar]
- Wazid, M.; Das, A.K.; Kumar, N.; Alazab, M. Designing Authenticated Key Management Scheme in 6G-Enabled Network in a Box Deployed for Industrial Applications. IEEE Trans. Ind. Inform. 2021, 17, 7174–7184. [Google Scholar]
- Srinivas, J.; Das, A.K.; Wazid, M.; Vasilakos, A.V. Designing Secure User Authentication Protocol for Big Data Collection in IoT-Based Intelligent Transportation System. IEEE Internet Things J. 2021, 8, 7727–7744. [Google Scholar]
- Sutrala, A.K.; Obaidat, M.S.; Saha, S.; Das, A.K.; Alazab, M.; Park, Y. Authenticated Key Agreement Scheme with User Anonymity and Untraceability for 5G-Enabled Softwarized Industrial Cyber-Physical Systems. IEEE Trans. Intell. Transp. Syst. 2022, 23, 2316–2330. [Google Scholar]
- Tanveer, M.; Khan, A.U.; Kumar, N.; Hassan, M.M. RAMP-IoD: A Robust Authenticated Key Management Protocol for the Internet of Drones. IEEE Internet Things J. 2022, 9, 1339–1353. [Google Scholar] [CrossRef]
- Wang, Q.; Wang, D. Understanding Failures in Security Proofs of Multi-Factor Authentication for Mobile Devices. IEEE Trans. Inf. Forensics Secur. 2023, 18, 597–612. [Google Scholar] [CrossRef]
- Chen, C.; Guo, H.; Wu, Y.; Gao, Y.; Liu, J. A novel two-factor multi-gateway authentication protocol for WSNs. Ad Hoc Netw. 2023, 141, 103089. [Google Scholar] [CrossRef]
- Wang, C.; Wang, D.; Duan, Y.; Tao, X. Secure and Lightweight User Authentication Scheme for Cloud-Assisted Internet of Things. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2961–2976. [Google Scholar] [CrossRef]
- Kumar, C.M.; Dwivedi, S.K.; Brindha, M.; Al-Shehari, T.; Alfakih, T.; Alsalman, H.; Amin, R. REPACA: Robust ECC based privacy-controlled mutual authentication and session key sharing protocol in coalmines application with provable security. Peer-to-Peer Netw. Appl. 2024, 17, 4264–4285. [Google Scholar] [CrossRef]
- Krawczyk, H. HMQV: A high-performance secure diffie-hellman protocol. In Advances in Cryptology—CRYPTO 2005: 25th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2005; Volume 3621, pp. 546–566. [Google Scholar]
- Lu, Y.; Xu, G.; Li, L.; Yang, Y. Anonymous three-factor authenticated key agreement for wireless sensor networks. Wirel. Netw. 2019, 25, 1461–1475. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- LaMacchia, B.; Lauter, K.; Mityagin, A. Stronger security of authenticated key exchange. In Provable Security: First International Conference, ProvSec 2007, Wollongong, Australia, 1–2 November 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 1–16. [Google Scholar]
- Yoneyama, K. Efficient and strongly secure password-based server aided key exchange. Inf. Media Technol. 2009, 4, 1046–1059. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Dependable Secur. Comput. 2014, 12, 428–442. [Google Scholar] [CrossRef]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar]
- Gope, P.; Hwang, T. A Realistic Lightweight Anonymous Authentication Protocol for Securing Real-Time Application Data Access in Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2016, 63, 7124–7132. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar]
- Subramani, J.; Maria, A.; Rajasekaran, A.S.; Al-Turjman, F. Lightweight Privacy and Confidentiality Preserving Anonymous Authentication Scheme for WBANs. IEEE Trans. Ind. Inform. 2022, 18, 3484–3491. [Google Scholar]
- Gope, P.; Sikdar, B. An Efficient Privacy-Preserving Authenticated Key Agreement Scheme for Edge-Assisted Internet of Drones. IEEE Trans. Veh. Technol. 2020, 69, 13621–13630. [Google Scholar] [CrossRef]
- Halevi, S.; Krawczyk, H. Public-Key Cryptography and Password Protocols. ACM Trans. Inf. Syst. Secur. 1999, 2, 230–268. [Google Scholar]
- Wang, D.; Wang, P. Understanding security failures of two-factor authentication schemes for real-time applications in hierarchical wireless sensor networks. Ad Hoc Netw. 2014, 20, 1–15. [Google Scholar] [CrossRef]
- Hankerson, D.; Menezes, A.J.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer: New York, NY, USA, 2003. [Google Scholar]
- Gura, N.; Patel, A.; Wander, A.; Eberle, H.; Shantz, S.C. Comparing Elliptic Curve Cryptography and RSA on 8-bit CPUs. In Cryptographic Hardware and Embedded Systems—CHES 2004: 6th International Workshop Cambridge, MA, USA, 11–13 August 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 119–132. [Google Scholar]
- Srinivas, J.; Das, A.K.; Li, X.; Khan, M.K.; Jo, M. Designing Anonymous Signature-Based Authenticated Key Exchange Scheme for Internet of Things-Enabled Smart Grid Systems. IEEE Trans. Ind. Inform. 2021, 17, 4425–4436. [Google Scholar]
- Guo, Y.; Guo, Y. CS-LAKA: A Lightweight Authenticated Key Agreement Protocol with Critical Security Properties for IoT Environments. IEEE Trans. Serv. Comput. 2023, 16, 4102–4114. [Google Scholar]
- Wang, P.; Li, B.; Shi, H.; Shen, Y.; Wang, D.; Li, F. Revisiting Anonymous Two-Factor Authentication Schemes for IoT-Enabled Devices in Cloud Computing Environments. Secur. Commun. Netw. 2019, 2019, 2516963. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).