Analysis of 105 IT Project Risks
Abstract
:1. Introduction
- Sources of 105 risks relevant to IT projects were identified.
- Models of cause-and-effect relationships between universal compliance and project risks have been created.
- A criterion for assessing the management maturity of a contractor (performer, supplier) planning to develop a computer program within an IT project has been developed.
2. Background
3. Methodology
4. Results
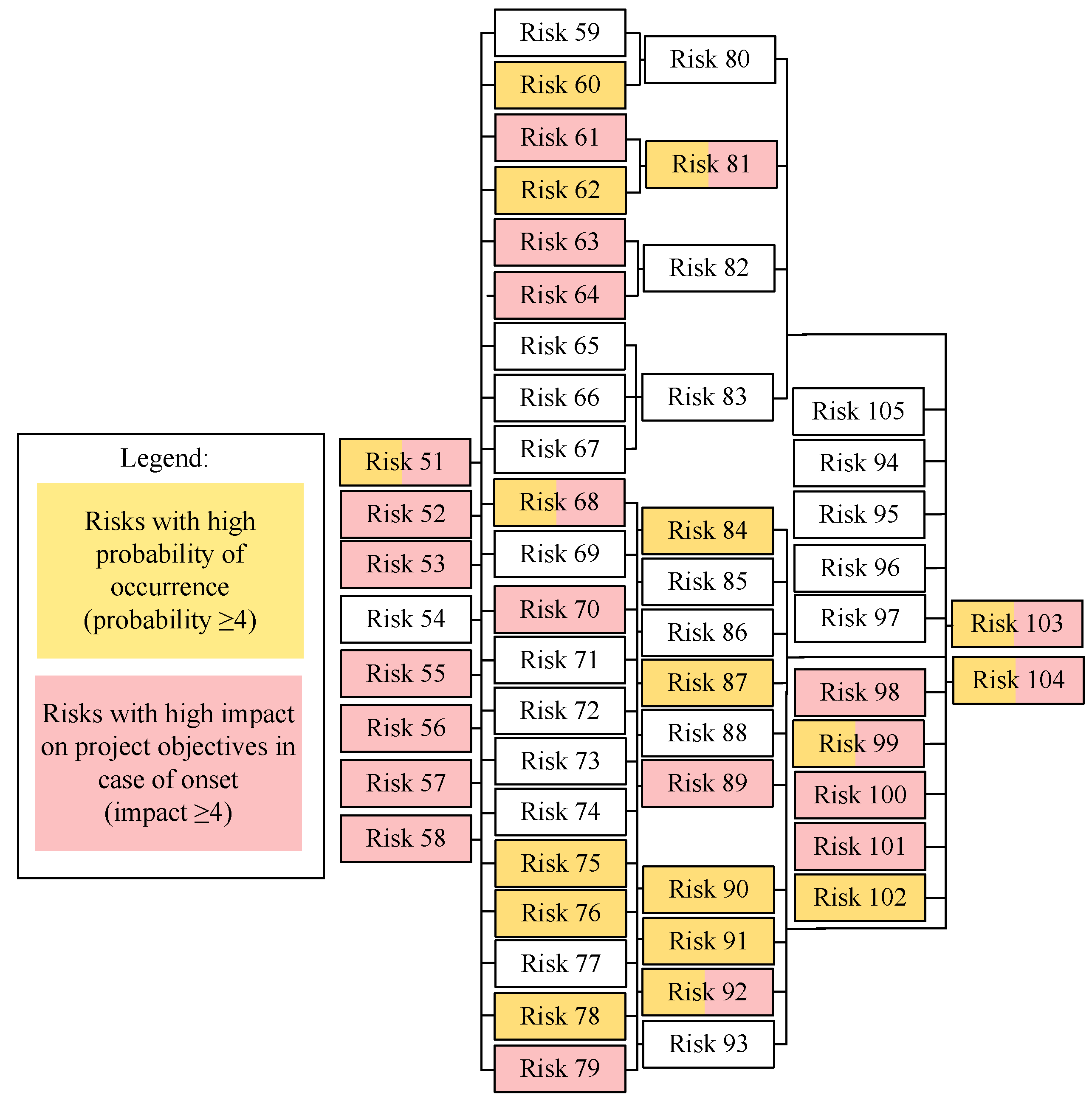
4.1. Results of Risk Analysis Using the 5Why Method
4.2. Results of Risk Analysis Using the SWIFT Method
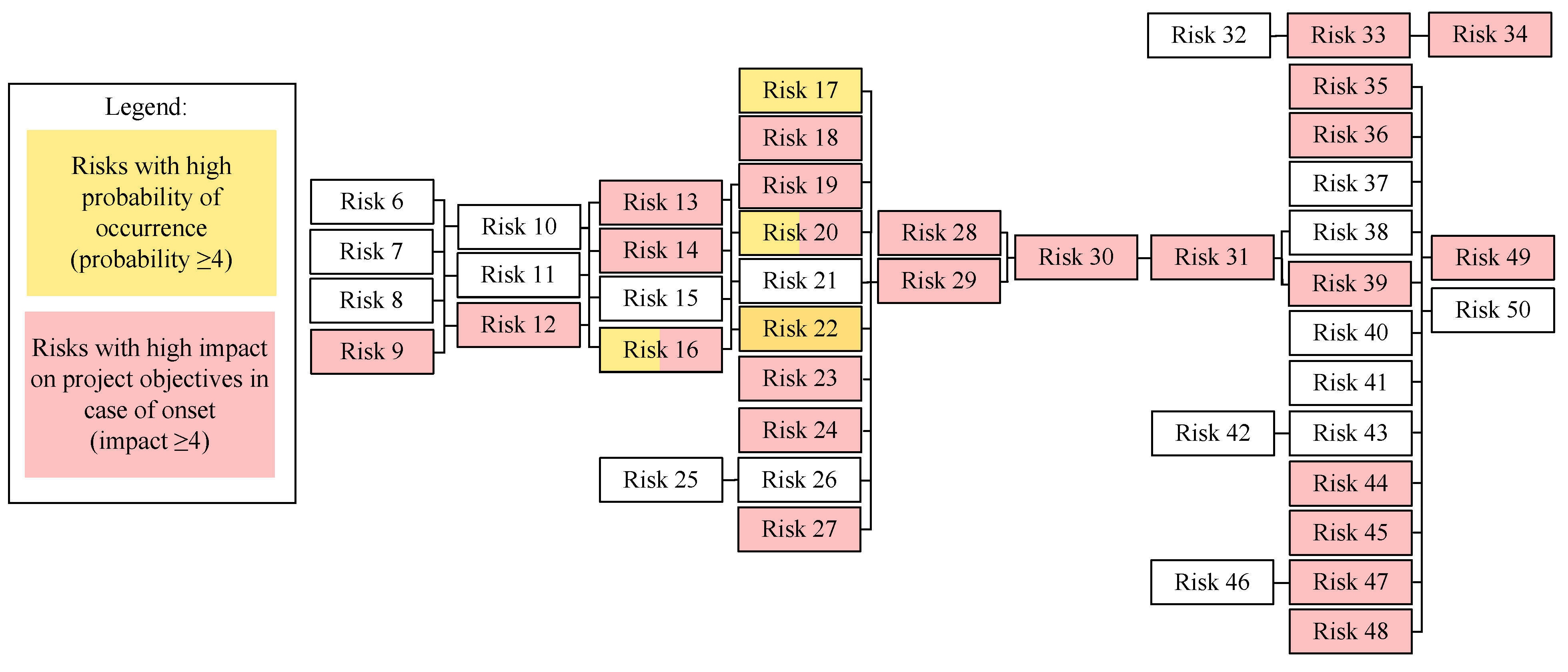
- Initiating risks, whose materialization leads to subsequent risk occurrence, are risk events associated with the customer. In particular, «the risk that the customer does not have a corporate culture, employees and experience in conducting activities in a single information space»; «the risk that the customer will not have well-functioning corporate procedures for information interaction»; «the risk that there are no key and qualified specialists on the customer’s side»; and «the risk that there will be customer restructuring». In this regard, it is logical to assume that in order to reduce the likelihood of the possible subsequent occurrence of compliance risks, it is necessary to take actions in advance to prevent the above probable events.
- Compliance risks of the external environment, such as «the risk of changing the norms of the current legislation»; «the risk of violating the norms of the current legislation»; and «the risk of fines for violating the current legislation» are not included in the general causal relationship of the model. This circumstance can be explained by the indirect influence of these compliance risks on the process of implementing IT projects and the progress of creating programs.
- The risk that the work performed (service rendered) will not meet the customer’s expectations is the most dangerous position in the scenario.
- For IT projects, in the negative scenario development, three outcomes are relevant: receiving a fine for violating the current legislation; lawsuit from the customer (contractor); lawsuit from a subcontractor.
4.3. Criteria for Evaluating the Maturity of IT Project Management
5. Discussion
- Addison T. and Vallabh S. risk list identifies the most dangerous risks for IT projects, the materialization of which can have a significant impact on the process of achieving project goals. However, the Nikolaenko V.S. risk list is of greater practical interest, as it captures not only dangerous risks for IT projects but also evaluates them, groups them, and establishes a causal relationship between them.
- There are no commercial or compliance risks in the risk lists of Addison T. and Vallabh S. According to the authors of this article, this is a significant omission, since the material damage of one compliance risk occurrence is on average $12,000.
- The list developed by Addison T. and Vallabh S. contains 14 risks, which, according to the authors of this article, is insufficient. In particular, the authors of the article believe that leveling the risks presented in Table 8 cannot guarantee the successful achievement of project objectives since the list does not contain such dangerous risks as “the risk of changing the norms of the current legislation”, “the risk of violating the norms of the current legislation” and others, the materialization of which can completely shut down the work in the IT project.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Addison, Tom, and Seema Vallabh. 2002. Controlling Software Project Risks—An Empirical Study of Methods used by Experienced Project Managers. Paper presented at 2002 Annual Research Conference of the South African Institute of Computer Scientists and Information Technologists on Enablement through Technology, Gqeberha, South Africa, September 16–18; pp. 128–40. [Google Scholar]
- Aven, Terje. 2012. The risk concept—Historical and recent development trends. Reliability Engineering and System Safety 99: 33–44. [Google Scholar] [CrossRef]
- Backlund, Fredrick, Diana Chronéer, and Erik Sundqvist. 2014. Project Management Maturity Models—A Critical Review. A case study within Swedish engineering and construction organizations. Procedia-Social and Behavioral Sciences 119: 837–46. [Google Scholar] [CrossRef] [Green Version]
- Basel Committee. 2005. Compliance and the Compliance Function in Banks. Basel: Basel Committee on Banking Supervision. [Google Scholar]
- Beer, Martina, Thomas Wolf, and Tirazheh Zare Garizy. 2015. Systemic risk in IT portfolios—An integrated quantification approach. Paper presented at International Conference on Information Systems: Exploring the Information Frontier, Fort Worth, TX, USA, December 13–16; pp. 1–18. [Google Scholar]
- Brandas, Claudiu, Otniel Didraga, and Nicolae Aurelian Bibu. 2012. Study on risk approaches in software development project. Informatica Economica 16: 148–57. [Google Scholar]
- Bushuyev, Sergey D., and Reinhard Friedrich Wagner. 2014. IPMA Delta® and IPMA Organisational Competence Baseline (OCB): New approaches in the field of project management maturity. International Journal of Managing Projects in Business 7: 1–12. [Google Scholar] [CrossRef]
- Card, Alan J., James R. Ward, and P. John Clarkson. 2012. Beyond FMEA: The structured what-if technique (SWIFT). Healthcare Risk Manage 31: 23–29. [Google Scholar] [CrossRef]
- Crawford, Kent. 2006. Project Management Maturity Model. New York: Auerbach Publications. [Google Scholar]
- Cule, Pual, Roy Schmidt, Kalle Lyytinen, and Mark Keil. 2000. Strategies for Нeading off Project Failure. Information Systems Management 17: 65–73. [Google Scholar] [CrossRef]
- De Bakker, Karel, Albert Boonstra, and Hans Wortmann. 2014. The Communicative Effect of Risk Identification on Project Success. Project Organisation and Management 6: 138–56. [Google Scholar] [CrossRef]
- ERP. 2017. Enterprise Risk Management. Integrating with Strategy and Performance. New York: Committee of Sponsoring Organizations of the Treadway Commission. [Google Scholar]
- Ewusi-Mensah, Kweku, and Zbigniew H. Przasnyski. 1991. On Information Systems Project Abandonment: An Exploratory Study of Organizational Practice. MIS Quarterly 15: 67–88. [Google Scholar] [CrossRef]
- Gładysz, Barbara, and Dorota Kuchta. 2022. Sustainable Metrics in Project Financial Risk Management. Sustainability 12: 4247. [Google Scholar] [CrossRef]
- Heemstra, Fred J., and Rob J. Kusters. 1996. Dealing with Risk: A Practical Approach. Journal of Information Technology 11: 333–46. [Google Scholar] [CrossRef] [Green Version]
- Hochstetter, Jorge, Carla Vairetti, Carlos Cares, Mauricio García Ojeda, and Sebastián Maldonado. 2021. A Transparency Maturity Model for Government Software Tenders. IEEE Access 9: 45668–82. [Google Scholar] [CrossRef]
- Hutabarat, Novalina, Teguh Raharjo, Bob Hardian, Agus Suhanto, and Andi Wahbi. 2021. PMMM Kenzner Questionnaire Validation for Project Management Maturity Level Assessment: One of the Largest Indonesia’s State-Owned Banks. Paper presented at 2021 International Conference on Advanced Computer Science and Information Systems (ICACSIS), Depok, Indonesia, December 14; pp. 1–5. [Google Scholar]
- International Organization for Standardization (ISO). 2018. ISO 31000:2018 Risk Management—Guidelines. Geneva: International Organization for Standardization. [Google Scholar]
- Keil, Mark, Kambiz Saffarizadeh, and Wael Jabr. 2018. Update Assimilation in App Markets: Is There Such a Thing as Too Many Updates? Paper presented at Thirty Ninth International Conference on Information Systems, San Francisco, CA, USA, December 13–16; pp. 1–9. [Google Scholar]
- Lee, One-Ki Daniel, and Deepa Varghese Baby. 2013. Managing dynamic risks in global IT projects: Agile risk management using the principles of service-oriented architecture. International Journal of Information Technology & Decision Making 12: 1121–50. [Google Scholar]
- Luckmann, John Arthur. 2015. Positive risk management: Hidden wealth in surface mining. The Journal of The Southem Africa Institute of Mining and Metallurgy 115: 1027–34. [Google Scholar] [CrossRef]
- Martínez, Pablo, Isidro A. Pérez, María Luisa Sánchez, María de los Ángeles García, and Nuria Pardo. 2021. Wind Speed Analysis of Hurricane Sandy. 2021. Wind Speed Analysis of Hurricane Sandy. Atmosphere 12: 1480. [Google Scholar] [CrossRef]
- Merna, Tony, and Faisal F. Al-Thani. 2008. Corporate Risk Management. New York: John Wiley & Sons, Ltd. [Google Scholar]
- Mishra, Anant, Sidhartha Das, and James Murray. 2014. Managing Risk in Government Information Technology Projects: Does Process Maturity Matter? Production and Operations Management 24: 365–68. [Google Scholar] [CrossRef]
- Nikolaenko, Valentin S. 2016. Implementation of Risk Management in IT projects. Public Administration. E-Journal 54: 63–88. [Google Scholar]
- Nikolaenko, Valentin S. 2018a. Negative and Positive Risks in IT projects. Moscow University Bulletin. Series 21. Public Administration 3: 91–124. [Google Scholar]
- Nikolaenko, Valentin S. 2018b. Risk, risk management and uncertainty: Clarifying concepts. Public Administration. E-Journal 81: 91–119. [Google Scholar] [CrossRef]
- Nikolaenko, Valentin S. 2022. With the hope of taking a risk. A new approach to project management is proposed. Search 30–31: 4–5. [Google Scholar]
- O’Neill, D. 2018. The Way Forward: A Strategy for Harmonizing Agile and CMMI. CrossTalk. The Journal of Defense Software Engineering 29: 4–9. [Google Scholar]
- Odeh, Ammar, Ammar El-Hassan, Ismail Keshta, and Tareq AlHajahjeh. 2021. A Model for Understanding Project Requirements based on CMMI Specifications. Paper presented at 7th International Conference on Engineering and Emerging Technologies (ICEET), Istanbul, Turkey, October 27–28; pp. 1–6. [Google Scholar]
- Paladino, Bob, Larry Cuy, and Mark L. Frigo. 2009. Missed opportunities in performance and enterprise risk management. Journal of Corporate Accounting & Finance 20: 43–51. [Google Scholar]
- Perez-Apaza, Fernando, Andre Ramírez-Valenzuela, and Juan D. Perez-Apaza. 2021. The Toyota Kata methodology for managing the maturity level pf Last Planner® System. Paper presented at 29th Annual Conference of the International Group for Lean Construction (IGLC29), Lima, Perú, July 12–18; pp. 514–23. [Google Scholar]
- Petroșanu, Dana-Mihaela, Alexandru Pîrjan, George Căruţaşu, Alexandru Tăbușcă, Daniela-Lenuța Zirra, and Alexandra Perju-Mitran. 2022. E-Commerce Sales Revenues Forecasting by Means of Dynamically Designing, Developing and Validating a Directed Acyclic Graph (DAG) Network for Deep Learning. Electronics 11: 2940. [Google Scholar] [CrossRef]
- Phan, Dien, Douglas Vogel, and Jay Nunamaker. 1998. The Search for Perfect Project Management. Computerworld 22: 95–100. [Google Scholar]
- Phelps, Robert. 1996. Risk Management and Agency Theory in IS Projects: An Exploratory Study. Journal of Information Technology 11: 297–307. [Google Scholar]
- PMBOK Guide®. 2017. Project Management Body of Knowledge, Guide, 6th ed.Newtown Square: Project Management Institute. [Google Scholar]
- Powell, Philip L., and Jonathan H. Klein. 1996. Risk Management for Information Systems Development. Journal of Information Technology 11: 309–19. [Google Scholar] [CrossRef]
- Ropponen, Janne, and Kalle Lyytinen. 2000. Components of Software Development Risk: How to Address Them? IEEE Transactions on Software Engineering 26: 98–111. [Google Scholar] [CrossRef] [Green Version]
- Sahu, Rekhraj, Bhuneshwar Choudhuri, and Shravan Yadav. 2022. Usages of six sigma in library services. Paper presented at Conference: Library as a Medium of Communication; Available online: https://www.researchgate.net/publication/364011786_Usages_of_six_sigma_in_library_services (accessed on 20 November 2022).
- Shirinkina, Elena, Alsu Kuramshina, Nadezhda Antonova, and Oleg Kravets. 2022. Multi-aspect model for lean manufacturing implementation. Paper presented at II International Scientific Conference on Advances in Science, Engineering and Digital Education: (Asedu-II 2021), Krasnoyarsk, Russia, October 28. [Google Scholar]
- Sidorov, Anatoly, and Pavel Senchenko. 2020. Regional Digital Economy: Assessment of Development Levels. Mathematics 8: 2143. [Google Scholar] [CrossRef]
- Stevens, Kenneth, and Sue Fowell. 2003. Perspective on E-Business Software Project Risk. Paper presented at 7th Pacific Asia Conference on Information Systems, Adelaide, Australia, July 10–13; pp. 95–107. [Google Scholar]
- Sumner, Mary. 2000. Risk factors in enterprise-wide/ERP projects. Journal of Information Technology 15: 317–27. [Google Scholar] [CrossRef]
- The Standish Group. 2014. The CHAOS Manifesto. West Yarmouth: The Standish Group. [Google Scholar]
- Vujovic, Vuk, Nebojša Denić, Vesna Stevanović, Mališa Stevanović, Jelena Stojanović, Yan Cao, Yasir Alhammadi, Kittisak Jermsittiparsert, Hiep Van Le, Karzan Wakil, and et al. 2020. Project planning and risk management as a success factor for IT project in agricultural schools in Serbia. Technology in Society 63: 101371. [Google Scholar] [CrossRef]
- Wiegers, Karl, and Joy Beatty. 2013. Software Requirements. Redmond: Microsoft Press. [Google Scholar]
- Wijayanti, Dewayani Nur, Tatan Sukwika, and Soehatman Ramli. 2022. Analisis Insiden Fatality Akibat Covid-19 Menggunakan Metode 5 Why, SCAT, BowTie, dan ISM. Jurnal Migasian 6: 84–92. [Google Scholar] [CrossRef]

| The Degree of Risk Impact | Harrington Coefficient | Comments |
|---|---|---|
| Very high | 5 | Work on the IT project was completely stopped |
| High | 4 | Work on the IT project was completed, but with a long delay |
| Medium | 3 | There is a delay in the completion of work, but the IT project is accepted |
| Low | 2 | Work on the IT project was completed with a short delay |
| Very low | 1 | Slightly behind schedule |
| No impact | 0 | No material damage |
| Risk Materialization Probability | Harrington Coefficient | Comments |
|---|---|---|
| Very high | 5 | Guaranteed risk materialization |
| High | 4 | Risk will materialize |
| Medium | 3 | Risk materialization is not guaranteed but possible |
| Low | 2 | Risk materialization is possible |
| Very low | 1 | Low materialization probability but still possible |
| No impact | 0 | No materialization probability |
| Respondents № | Experience in IT, Years | Availability of Professional Education | Age, Years | Using the Risk Register during IT Project Implementation |
|---|---|---|---|---|
| 1 | 4 | Yes | 26 | No |
| 2 | 4 | Yes | 26 | No |
| 3 | 4 | Yes | 27 | Yes |
| 4 | 10 | Yes | 34 | Yes |
| 5 | 6 | Yes | 28 | Yes |
| 6 | 5 | Yes | 27 | Yes |
| 7 | 4 | Yes | 26 | No |
| 8 | 4 | Yes | 26 | Yes |
| 9 | 25 | Yes | 47 | Yes |
| 10 | 7 | Yes | 29 | Yes |
| № | Source Name | Share of Total Volume, % | Comments |
|---|---|---|---|
| 1 | User | 2 | A person (or group of persons) who, following the completion of an IT project, will use the created program in their own interests. The analysis of universal risks showed that the end user is the source for three risks. |
| 2 | Customer | 15 | A person (group of persons) who issues a task to create a ECM program and/or to provide an IT service and, upon the IT project completion, accepts and pays for the result of the work performed and/or the IT service provided. The customer is the source of 27 risks. |
| 3 | Project manager | 43 | A contractor specialist (executor, supplier), responsible for the effective achievement of the project goals within the requirements, budgets and deadlines approved by the customer. The project manager is the source of 81 risks. |
| 4 | Project team | 36 | A group of specialists that cooperates for the IT project duration to create a program and/or to provide an ITservice. IT project team may include project managers, programmers, testers, database administrators, system analysts, designers, lawyers, and others. The project team is the source of 69 risks. |
| 5 | Subcontractor (co-contractor) | 2 | If the terms of the IT project do not imply the obligation of the contractor to create a program and/or provide an ITservice personally, then the contractor has the right to involve a third person, i.e., a subcontractor, in the performance. The subcontractor is the source of four risks. |
| 6 | Competitor | 2 | A person (group of persons) that competes for the loyalty of an end user with another person (group of persons). The competitor is the source of three risks. |
| № | Name of the Risk | Risk Materialization Probability | Impact of the Risk Materialization | Sphere |
|---|---|---|---|---|
| Risk 1 | Risk that the work performed (service rendered, goods delivered) will not meet the expectations of the user (client) | 3.7 | 4.8 | Risks associated with the user (client) |
| Risk 2 | Risk of low user’s (client’s) involvement in the process of performing work (rendering a service, supplying goods) | 1.7 | 3.5 | Risks associated with the user (client) |
| Risk 3 | Risk that the work performed (service rendered, goods delivered) will not have the expected commercial effect | 3.8 | 4.9 | Risks associated with the commercial effect |
| Risk 4 | Risk that competitors will influence the progress of work (delivery of services, delivery of goods) | 1.5 | 3.7 | Risks associated with competitors |
| Risk 5 | Risk that substitute goods will affect the progress of the work (delivery of a service, delivery of goods) | 4.3 | 3.7 | Risks associated with substitute products |
| № | Name of the Risk | Risk Materialization Probability | Impact of the Risk Materialization | Sphere |
|---|---|---|---|---|
| Risk 6 | Risk that the customer does not have a corporate culture, employees and experience of doing business in a single information space | 1.7 | 2.7 | Risks associated with the customer |
| Risk 7 | Risk that the customer will not have well-established corporate procedures for information exchange | 2.4 | 2.7 | Risks associated with the customer |
| Risk 8 | Risk that there are no key and qualified specialists on the customer’s side | 2.8 | 2.8 | Risks associated with the customer |
| Risk 9 | Risk that there will be a customer restructuring | 0.3 | 4.8 | Risks associated with the customer |
| Risk 10 | Risk of low customer involvement in the performing work (rendering a service) process | 2.1 | 2.3 | Risks associated with the customer |
| Risk 11 | Risk of absence of a common vision of the final product among stakeholders | 2.3 | 3.8 | Risks associated with the contractor (executor, supplier) |
| Risk 12 | Risk that not all interested parties on the customer side are included in the project documents | 2.1 | 4.1 | Risks associated with the customer |
| Risk 13 | Risk that the contract subject matter will be formulated inaccurately and/or formalized incorrectly | 1.9 | 4 | Risks associated with the customer |
| Risk 14 | Risk of incorrect and imprecise formulation in the contract text | 2 | 4.7 | Risks associated with the customer |
| Risk 15 | Risk of incorrect transaction type qualification | 2.5 | 3 | Risks associated with the customer |
| Risk 16 | Risk that the specification is incomplete, unreliable and/or does not meet the requirements of national standards | 4.3 | 4.3 | Risks associated with the customer |
| Risk 17 | Risk of absence of communication with the customer | 4.6 | 2.6 | Risks associated with the customer |
| Risk 18 | Risk that the customer will not provide and/or will provide with a long delay the information necessary for the work performance | 3.6 | 4.1 | Risks associated with the customer |
| Risk 19 | Risk that the transaction concluded between the parties will be invalid | 0.5 | 4.8 | Risks associated with the customer |
| Risk 20 | Risk of changing requirements in the work course | 4.6 | 4.8 | Risks associated with the customer |
| Risk 21 | Risk that during the work performing process the contractor will not be able to fulfill the obligations stated in the contract on his own | 2.7 | 4.1 | Risks associated with the contractor (executor, supplier) |
| Risk 22 | Risk that the contractor will reveal hidden sources of additional costs that were not discovered at the planning stage | 4.1 | 2 | Risks associated with the contractor (executor, supplier) |
| Risk 23 | Risk of loss and/or damage to electronic equipment and other property due to fire, water flooding, etc. | 0.3 | 4.8 | Risks associated with property |
| Risk 24 | Risk of loss and/or damage to electronic equipment and other property as the result of illegal actions of third parties | 0.3 | 4.8 | Risks associated with property |
| Risk 25 | Risk of lack of communication with the subcontractor | 3.6 | 2.1 | Subcontractor risk |
| Risk 26 | Risk that the result obtained by the subcontractor will not meet the expectations of interested parties | 4.2 | 3.2 | Subcontractor risk |
| Risk 27 | Risk of force majeure circumstances will materialization and have a significant impact on the work progress | 0.3 | 4.2 | Risks associated with the contractor (executor, supplier) |
| Risk 28 | Risk that the contractor will withhold information about the real state of affairs from the customer and/or distort it | 0.4 | 4.1 | Risks associated with the contractor (executor, supplier) |
| Risk 29 | Risk that the contractor (executor) will not fulfill his obligations under the contract | 2.2 | 4.5 | Risks associated with the contractor (executor, supplier) |
| Risk 30 | Risk that the work performed (service rendered) will not meet the customer’s expectations | 2.1 | 4.8 | Risks associated with the customer |
| Risk 31 | Risk that the customer will refuse to accept the work performed (service rendered) | 3.5 | 4.9 | Risks associated with the customer |
| Risk 32 | Risk of changing the norms of the current legislation | 3.2 | 3.2 | Risks associated with the contractor (executor, supplier) |
| Risk 33 | The risk of violating the norms of the current legislation | 4.2 | 4.8 | Risks associated with the contractor (executor, supplier) |
| Risk 34 | Risk of fines for violating the norms of the current legislation | 2.6 | 4.9 | Risks associated with the contractor (executor, supplier) |
| Risk 35 | Risk of dissemination of information discrediting the business contractor (performer)reputation | 2.2 | 4.3 | Risks associated with the contractor (executor, supplier) |
| Risk 36 | Risk of industrial espionage | 1.3 | 4 | Criminal risks |
| Risk 37 | Risk of confidential data leakage | 2 | 3.6 | Criminal risks |
| Risk 38 | Risk of a delay in payment for the work performed by the contractor (services rendered by the contractor) | 3 | 3.2 | Risks associated with the customer |
| Risk 39 | Risk of a customer’s refusal to pay for the work performed (service rendered) | 3.2 | 4.9 | Risks associated with the customer |
| Risk 40 | Risk of impossibility to terminate the transaction early and unilaterally | 1.7 | 3.9 | Risks associated with the customer |
| Risk 41 | Risk that the parties will not negotiate the distribution of savings that can be obtained | 1.4 | 3.8 | Risks associated with the customer |
| Risk 42 | Risk of limitation for subsequent sublicensing agreements | 0.5 | 3.1 | Risks associated with the exclusive right to the result of intellectual activity |
| Risk 43 | Risk of contract termination in the «sublicense chain» of contracts | 0.3 | 3.1 | Risks associated with the exclusive right to the result of intellectual activity |
| Risk 44 | Risk of creating an unwanted derivative work | 0.3 | 4.8 | Risks associated with the exclusive right to the result of intellectual activity |
| Risk 45 | Risk of collection of compensation by the right holder for the use of his exclusive rights to the results of intellectual activity | 0.6 | 4.8 | Risks associated with the exclusive right to the result of intellectual activity |
| Risk 46 | Risks associated with the exclusive right to the result of intellectual activity | 1.4 | 3.6 | Risks associated with the exclusive right to the result of intellectual activity |
| Risk 47 | Risk that the copyright holder (author) will prohibit the use of the result of intellectual activity | 0.7 | 4.9 | Risks associated with the exclusive right to the result of intellectual activity |
| Risk 48 | Risk of impossibility to recognize the exclusive right to the result of intellectual activity for the right holder (author) | 0.3 | 4.9 | Risk associated with the prohibition of using intellectual activity by the copyright holder (author) |
| Risk 49 | Risk of legal action from the customer/contractor (executor, supplier) | 1.8 | 4.7 | Risks associated with the contractor (executor, supplier) |
| Risk 50 | Subcontractor lawsuit risk | 1.5 | 3.4 | Subcontractor risk |
| № | Name of the Risk | Risk Materialization Probability | Impact of the Risk Materialization | Sphere |
|---|---|---|---|---|
| Risk 51 | Risk that the project manager does not have knowledge, skills and experience | 4.3 | 4.7 | Project Manager |
| Risk 52 | Risk that the project participants do not have the knowledge, skills and experience necessary to implement the requirements | 3.6 | 4.2 | Risks associated with project participants |
| Risk 53 | Risk of a lack of project management tools in the project | 2.3 | 4.1 | Project Manager |
| Risk 54 | Risk that information about materialized risks that the project manager may need in subsequent projects will be lost | 3.4 | 2.5 | Project Manager |
| Risk 55 | Risk of involving a project manager who has a professional education in the project management field | 1.4 | 4.4 | Project Manager |
| Risk 56 | Risk of involving a project manager who has more than 2 years’ experience in project management | 2.5 | 4.7 | Project Manager |
| Risk 57 | Risk that the project manager will form the project team independently | 1.1 | 4.3 | Project Manager |
| Risk 58 | Risk of involvement of a highly qualified worker to the project | 1.3 | 4.8 | Risks associated with project participants |
| Risk 59 | Risk that project participants do not understand what result should be obtained at the end of the project | 2.1 | 1.4 | Risks associated with project participants |
| Risk 60 | Risk that, in fact, the design work will turn out to be much more difficult than originally envisaged | 4.8 | 3 | Risks associated with project participants |
| Risk 61 | Risk of overestimating quality by the project manager | 2 | 4.2 | Project Manager |
| Risk 62 | Risk of making mistakes by project participants in the project implementation (bugs) | 4.1 | 2.6 | Risks associated with project participants |
| Risk 63 | Risks of conflict of interest among stakeholders | 1.4 | 4.1 | Risks associated with project participants |
| Risk 64 | Risk of conflict between the project manager and stakeholders (e.g., customer, team members, etc.) | 1.2 | 4.3 | Project Manager |
| Risk 65 | Risk of the Cassandra effect, i.e., there will be an overabundance of communication channels conveying up-to-date information | 3 | 2.1 | Risks associated with project participants |
| Risk 66 | Risk of long-term coordination of information by interested parties in the management decisions development | 2 | 1.7 | Project Manager |
| Risk 67 | Risk of a significant time delay in obtaining answers to questions asked between project participants | 3.6 | 2.3 | Risks associated with project participants |
| Risk 68 | Risk that the project manager will make a mistake when estimating the project’s work duration | 4.5 | 4.5 | Project Manager |
| Risk 69 | Risk of incorrect ranking of tasks by the project manager | 2.3 | 3.1 | Project Manager |
| Risk 70 | Risk of loss and/or lack of control by the project manager | 3.9 | 4.4 | Project Manager |
| Risk 71 | Risk of lack of interest among project participants in the successful completion of the project | 0.4 | 2.1 | Risks associated with project participants |
| Risk 72 | Risk of lack of interest among project participants in the successful completion of the project | 1.2 | 2 | Project Manager |
| Risk 73 | Risk of low project manager labor productivity | 4.1 | 2.6 | Project Manager |
| Risk 74 | Risk of low labor productivity among project participants | 2.1 | 2.6 | Risks associated with project participants |
| Risk 75 | Risk that the project manager will make a mistake when estimating the project’s work cost | 4.5 | 4 | Project Manager |
| Risk 76 | Risk that the project manager will make a mistake when estimating resources | 4.1 | 3 | Project Manager |
| Risk 77 | The risk that project participants will not correctly estimate the labor costs that are necessary to complete the design work | 3.6 | 3.6 | Risks associated with project participants |
| Risk 78 | Risk that project participants will not correctly decompose design work | 4.3 | 3.2 | Risks associated with project participants |
| Risk 79 | Risk of changing the project participants list in the process of project implementation | 3.8 | 4.1 | Risks associated with project participants |
| Risk 80 | Risk of changing the scope of the project | 3.4 | 4.6 | Project Manager |
| Risk 81 | Project quality risk | 4.9 | 4.5 | Project Manager |
| Risk 82 | Risk of a negative socio-psychological atmosphere | 3 | 1.7 | Risks associated with project participants |
| Risk 83 | Risk of insufficient communication between project participants | 2.9 | 3.7 | Risks associated with project participants |
| Risk 84 | Risk that the actual working time of project participants will be less than 8 h per day | 4.3 | 2.1 | Risks associated with project participants |
| Risk 85 | Risk of not accounting for vacations and public holidays when creating a project plan | 3.6 | 2.1 | Project Manager |
| Risk 86 | Risk of downtime for labor resources | 3.7 | 2.2 | Risks associated with project participants |
| Risk 87 | Risk of uncoordinated actions by project participants | 4.6 | 1.2 | Risks associated with project participants |
| Risk 88 | Risk that the number of project participants will not exceed 6 people | 0.5 | 2.7 | Risks associated with project participants |
| Risk 89 | Risk of involving third-party experts and advisers in the project | 0.4 | 4.6 | Risks associated with project participants |
| Risk 90 | Risk of lack of resources necessary for the implementation of design work | 4.2 | 3.1 | Project Manager |
| Risk 91 | Risk of overloading labor resources (for example, due to working long hours and overtime, etc.) | 4.2 | 2.1 | Risks associated with project participants |
| Risk 92 | Risk of misappropriation of limited project resources | 4.3 | 4.7 | Project Manager |
| Risk 93 | Risk of a lack of reserves necessary to accept materialized risks | 2.7 | 3.7 | Project Manager |
| Risk 94 | The risk of using previously unused technologies by project participants (for example, programming languages, etc.) | 2.6 | 1.4 | Risks associated with machinery, technologies and equipment |
| Risk 95 | Power outage risk | 2.6 | 1.3 | Risks associated with machinery, technologies and equipment |
| Risk 96 | Risk of collaboration between the leader and project participants | 1.3 | 1.2 | Risks associated with project participants |
| Risk 97 | Risk of using outdated technologies by project participants | 1.3 | 2.1 | Risks associated with project participants |
| Risk 98 | Risk of project participants’ involvement in other projects | 3.5 | 4.3 | Risks associated with project participants |
| Risk 99 | Risk of project manager involvement in other projects | 4 | 4.6 | Project Manager |
| Risk 100 | Risk that the PM will leave the project | 2 | 4.5 | Project Manager |
| Risk 101 | Risk that the key participant on the project will leave the project. | 2.1 | 4.7 | Pиcки, cвязaнныe c yчacтникaми пpoeктa |
| Risk 102 | Project participant’s sick leave risk | 4.8 | 2.1 | Pиcки, cвязaнныe c yчacтникaми пpoeктa |
| Risk 103 | Project duration risk | 4.2 | 4.1 | Project Manager |
| Risk 104 | Project cost risk | 4.3 | 4.8 | Project Manager |
| Risk 105 | Internet outage risk | 2.6 | 1.3 | Risks associated with machinery, technologies and equipment |
| № | Risk |
|---|---|
| Risk 1 | Risk of unclear objectives |
| Risk 2 | Risk of «unrealistic» project schedules and budgets |
| Risk 3 | Risk that manager will not be interested in the successful completion of the project |
| Risk 4 | Risk of a lack of senior management involvement |
| Risk 5 | Risk of failure to gain user involvement |
| Risk 6 | Risk of aclack of effective project management methodology |
| Risk 7 | Risk of misunderstanding the requirements |
| Risk 8 | The risk of overestimating the quality of the project or «gold platting» |
| Risk 9 | Risk of continuous requirement changes |
| Risk 10 | Risk of software functionality incorrect development |
| Risk 11 | Risk of default by subcontractors |
| Risk 12 | Risk of low productivity |
| Risk 13 | Risk of introduction of new technology |
| Risk 14 | Risk of not managing user expectations |
| № | Risk |
|---|---|
| Risk 1 | Risk of a lack of top management commitment to the project |
| Risk 2 | Risk of failure to gain user commitment to the project |
| Risk 3 | Risk of misunderstanding of requirements by the developers |
| Risk 4 | Risk of a lack of adequate user involvement (absence) in the project |
| Risk 5 | Risk of failure to manage end-user expectations with regard to the project’s outcomes |
| Risk 6 | Risk of changing the objectives of the project |
| Risk 7 | Risk of a lack of required knowledge/skills in the project personnel |
| Risk 8 | Risk of a lack of «frozen» requirements |
| Risk 9 | Risk of introduction of new technology |
| Risk 10 | Risk of insufficient/inappropriate staffing |
| Risk 11 | Risk of conflict between project stakeholders |
| № | Risk |
|---|---|
| Risk 1 | Risk of failure to redesign business processes |
| Risk 2 | Risk that the manager will not be interested in the successful completion of the project |
| Risk 3 | Risk of a lack of appropriate workshops |
| Risk 4 | Risk of key employees leaving the project |
| Risk 5 | Risk of a lack of appropriate workshops |
| Risk 6 | Risk that in fact the project will be much more complicated |
| Risk 7 | Risk of failure to manage end-user expectations with regard to the project’s outcomes |
| Risk 8 | Risk of a lack of integration with other platforms |
| Risk 9 | Lack of proper management control structure |
| Risk 10 | Risk of a lack of internal expertise |
| Risk 11 | Risk of a lack of a champion |
| Risk 12 | Risk of a lack of a business analyst |
| Risk 13 | Risk of reducing the quality of work |
| Risk 14 | Risk of insufficient information in project documentation |
| Risk 15 | Risk of a lack of standardization and discipline |
| Risk 16 | Risk of ineffective communications |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nikolaenko, V.; Sidorov, A. Analysis of 105 IT Project Risks. J. Risk Financial Manag. 2023, 16, 33. https://doi.org/10.3390/jrfm16010033
Nikolaenko V, Sidorov A. Analysis of 105 IT Project Risks. Journal of Risk and Financial Management. 2023; 16(1):33. https://doi.org/10.3390/jrfm16010033
Chicago/Turabian StyleNikolaenko, Valentin, and Anatoly Sidorov. 2023. "Analysis of 105 IT Project Risks" Journal of Risk and Financial Management 16, no. 1: 33. https://doi.org/10.3390/jrfm16010033
APA StyleNikolaenko, V., & Sidorov, A. (2023). Analysis of 105 IT Project Risks. Journal of Risk and Financial Management, 16(1), 33. https://doi.org/10.3390/jrfm16010033





