1. Introduction
The use of fossil fuels for energy production has been the origin of many improvements to human life. However, it is also the cause of several problems, such as pollution and climate change. For that reason, research efforts have been focused on the utilization of alternative energy sources, like wind [
1], geo-thermal [
2], sun-based [
3], biomass [
4], hydrogen [
5], bio-fuels [
6], or even tidal [
7]. Contrary to fossil fuels, these are considered renewable because they are sustainable, cost-effective, and environmentally friendly [
8,
9]. Because of its abundance and availability in many places around the world, the sun is the most critical source. Therefore, much research has focused on improvements to the associated technologies to extract its energy, such as photo-voltaic and concentrated solar power (CSP) systems [
10].
In CSP systems of the parabolic trough collector (PTC) type, heat pipes (HPs) receive the concentrated solar power to transfer the temperature into a heat transfer fluid (HTF) that is later utilized to perform mechanical work. Among all the components of PTCs, HPs are considered the most crucial element to increase the efficiency in energy harvesting [
11,
12] by boosting the transformation of sunlight to heat. One way to improve the receiver efficiency is by modifying its parameters. Thus, the optimal design of HPs is an essential need to be covered by research endeavors [
13]. This work proposes a comparison of four metaheuristic methods when they are used to increase the capillarity angle of micro-grooved pipes.
Various components of CSP systems are feasible for optimization, such as (1) the reflector, (2) the collector, (3) the heat receiver, (4) heat transport, (5) power production, and (6) thermal storage. The use of metaheuristic algorithms is a relatively recent trend in research related to CSP improvements. In that sense, several studies have been made, particularly in the last four decades. There are two optimization methods that can be used: classical and evolutionary. The second class of techniques are the main focus of this work. For example, Wang and Yang [
14] proposed the optimization a prism-based solar concentrator via genetic algorithm, achieving improvements in brightness of around 400% when compared with a similar approach. In this case, the main idea is to find the optimal combination of prismatic crystals to enhance sunlight energy transmission via optic fiber. Nazemi and Boroushaki describe the optimal design of a dish/stirling system in [
15]. The model considers the parabolic dish and the cavity receiver as the optimization problem, and the metaheuristic used was particle swarm optimization. The obtained design and a real system were compared, finding that the approach gave a good approximation of real devices. In the same venue, authors in [
16] optimized the coefficients of a photovoltaic/thermal system through a genetic algorithm, finding improvements in the thermal addition to its exergetic efficiency.
The mentioned articles pay attention mainly to the collector; however, the heat transmission between the collector and the HTF is another vital aspect of CSP research. In that sense, Petersont began studies related to pipes with V-shaped micro-grooves [
17], although other kinds of improvements to pipes have been put forth. For instance, authors in [
18] propose the insertion of twisted tapes in that kind of exchanger, with the idea of increasing the heat transfer by modifying the Reynolds and Nusselt numbers. In [
19], the pipe optimization considered two criteria: (1) the investment costs, and (2) the coupling between the CSP system and the steam turbine discharge. The authors found that the use of finned hexagonal tubes is the best option to reduce cost in commercial production, packing, and storage. Another proposal is the use of helically finned tubes; for example, authors in [
20] made numerical simulations for the utilization of those pipes in the design of a CSP, and they found that the whole system’s efficiency could be increased with their use. A recent attempt to optimize the design of an HP using evolutionary algorithms was made in [
21]. Here, the use of genetic algorithms was proposed [
22] to improve the design of the absorber in a parabolic trough. Several variables were examined and used to improve the capillarity. Additionally, an adiabatic model was proposed to calculate the liquid front, as well as its establishment velocity. The authors made improvements of around 10% in comparison with another study [
23].
Our proposal improves upon the results shown in [
21], with different metaheuristic algorithms: discrete binary differential evolution (DBDE), clonal selection algorithm (CSA), binary particle swarm optimization (BPSO), and genetic algorithm (GA). Because of their configuration, these metaheuristic algorithms are capable of searching in mixed numerical spaces. In that sense, this work contributes, on the one hand, to the search for better algorithms [
24] to solve the capillarity problem in the design of micro-grooved pipes in CSP systems. On the other hand, it contributes to the use of the capillary-driven two-phase flow model proposed by [
21]. The approach obtained improved upon HP designs by maximizing the capillarity angle. Even though other fluids (e.g., vegetable oils, synthetic oil) are used frequently as HTFs for CSPs [
25], in the present study only four commonly utilized fluids are considered for the design optimization of CSP systems: liquid sodium, water, and two molten salts [
26]. From the compared techniques, BPSO achieved improvements in the wet front, via the capillarity angle, from around 11% against the study reported in [
21]. The results suggest that metaheuristic algorithms are a good option for the optimal design of micro-grooved HPs in CSP systems. The rest of the article is structured as follows:
Section 2 explains the details concerning the micro-groove pipe design, particularly its governing equations.
Section 3 deals with the details regarding the utilized metaheuristic algorithms, whereas
Section 4 describes the experimental part.
Section 5 provides some conclusions of the present work.
2. Design of Micro-Grooved Pipe
The study made in [
21,
27] considered the capillarity angle and the velocity of a heat transfer fluid (HTF) inside a heat pipe (HP) in the model. This work used the same design and held the same assumptions. The mathematical explanation of the model is in the next subsection, and the other paragraph describes its solution methodology.
Governing Equations
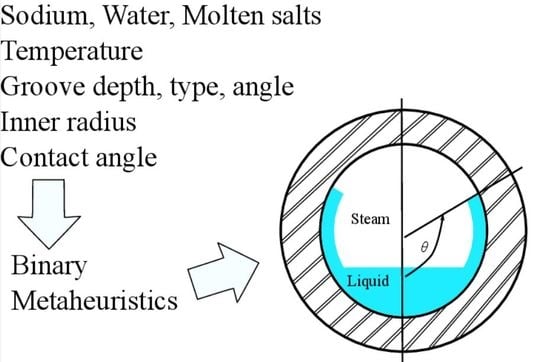
The use of micro-grooved pipes as a heat receiver is frequent in CSP systems. Authors in [
27] developed a capillary-driven two-phase model with several design variables. In the first phase, it is assumed, that there is no heat flux for the calculus of the liquid front velocity. The second stage establishes two relationships: heat flux vs. liquid front velocity, and mass of liquid vs. liquid front velocity. Those relations are crucial to calculate the fluid supply to a micro-grooved pipe (
Figure 1) under the CSP working conditions.
It is important to remark that the model only predicts the behavior of saturated liquids with different operating temperatures. Additionally, the steam being displaced by the moving fluid in the micro-grooves is non-negligible. By considering those situations, the flow behavior in this kind of pipe is influenced only by the momentum balance of the liquid in the direction of the capillarity angle,
, as shown in
Figure 1. The momentum balance is given by:
where
are the inertial forces over the liquid layer,
are the capillarity-driven forces,
are the gravitational forces, and
are the viscous forces. Other assumptions are:
Laminar and Newtonian flux in the micro-groove;
Isothermal layer of fluid, therefore its internal friction is negligible; and
The thickness of the liquid layer advancing on the micro-groove insignificant.
If we consider a mass for the liquid that flows in the direction of the capillarity angle, with a liquid front velocity, then Equation (
1) becomes [
23]:
where the meaning of every variable and constant is in
Appendix A. In this work, the objective is to maximize the capillarity angle (e.g., liquid front position). Equation (
2) is prone to errors if used to calculate
, the maximum capillarity angle. Therefore, authors in [
23] proposed its reformulation using time as the independent variable:
Methodology to Solve the Governing Equations
Equation (
3) can be re-formulated as a system of differential algebraic equations:
with initial conditions
and
. In the experimental part, Equation (
4) is evaluated in 10 seconds by using the Matlab solver
, to find the stable values of
and
. An illustrative example of the evaluation of Equation (
4) is in
Figure 2, where the initial conditions are
and
. This Figure also depicts the dynamics of the capillarity angle and the velocity of the liquid front. Concerning the angle, it surpasses the stable point around the first second, with a tendency to stability after around
s. We consider maximizing the value of the capillarity angle in the stable state of the simulation.
The optimization process produces an increase in the capillarity angle, which enhances the heat transfer to the micro-grooved pipe. Then, the objective function can be described as the maximization of the capillarity angle:
The value
is function of several variables that are defined in
Appendix A. In this work, four fluids (
Appendix B) are used in the optimization of the capillarity angle; while some parameters depend on the kind of fluid (
), such as liquid density, viscosity and dynamic density (
Appendix C,
Appendix D,
Appendix E and
Appendix F), other are independent of such variable, e.g. the micro-groove geometry (
Appendix G).
3. Metaheuristic Algorithms
This section briefly explains the four selected metaheuristic algorithms utilized to solve the problem of pipe design in the parabolic trough. In each technique, the individual codification was as binary strings, because they are capable of encoding the two kinds of variables optimized in this article: integers and real values. Another critical remark is the fact that in every algorithm, the initialization of the population is performed by considering a uniform probability distribution [
28].
3.1. Discrete Binary Differential Evolution
This motivation of this metaheuristic is the evolutionary process, similar to the genetic algorithms. Nevertheless, and even though the operators’ names are the same, they function in a slightly different manner. Such operators explore the search space efficiently, allowing the algorithm to achieve the right balance between exploration and exploitation [
29]. The algorithm was first proposed to minimize nonlinear and non-differentiable functions. In their seminal paper, Storn and Price considered some essential features of this optimization technique: few control variables, easily parallelizable, and excellent convergence properties, among others [
28]. The basic algorithm for real candidate solutions utilizes three operators, which modify the whole population of vectors: (1) mutation, (2) crossover, and (3) re-selection of the best individual, which are mostly the same operators used in the discrete binary differential evolution (DBDE) [
30] utilized in this work. A detailed description of those mathematical operators is given in the following.
Mutation
For DBDE, this operator must select three random parents from the original population with the restriction that
, where
i is the actual individual and
and
are three randomly generated integers from a uniform distribution. Once selected, the mutated vector is calculated by
where
represents the step size, and the binarization is achieved by
with
being a uniform random number.
Crossover
The mutated vector, as well as the actual candidate solution, serve to construct a trial vector:
where
is a uniform random number,
is the crossover rate,
is an integer number generated from a uniform distribution. This value is to ensure that at least one bit is mutated.
Selection
The final step of the algorithm consists of a greedy re-selection of the objective function value of the actual candidate solution, and the fitness value of the trial vector:
3.2. Clonal Selection Algorithm
The environment is a source of many health imbalances to many living beings, particularly mammals. To counteract that situation, those individuals have several internal systems, one of them being the immune system. This system has compelling attributes, such as learning capability, pattern recognition, and memory [
31]. A theory formulated by immunologists is called the clonal selection theory; in this theory, the immune system’s elements (antibodies) are continually monitoring for external substances which attacked the body in the past. If a component of that kind appears (e.g., an antigen), then an immune response is triggered, with the following steps: cloning, mutation, destruction of the foreign agent, re-selection, and memory. Those characteristics have served as an inspiration to computer scientists to create an area of soft computing called artificial immune systems, which has several variants. The version utilized in this paper is the clonal selection algorithm [
32], whose steps are: (1) cloning, (2) hyper-mutation, (3) re-selection, and (4) diversity introduction.
Cloning and Hyper-Mutation
Even though there are other schemes, this paper uses the one related to the simple cloning of the individuals, considering a certain percentage,
. First, it generates a cloned population,
, which has
clones
and then mutation is carried out with a probability
to every bit in the population, to get a new cloned and mutated population,
It is essential to say that those individuals will compete against the original parents from B. Consequently, the evaluation of clones will be in groups: the fitness value of every parent will be contrasted against the fitness of its mutated clones, repeating the procedure for each parent of the original population.
Re-Selection and Diversity Introduction
In order to evaluate each individual from
, it is necessary to transform those binary strings to real and integer values, obtaining
:
where
f is the objective function,
is the real version of
,
are the real version of the clones corresponding to individual
i, and
is the best binary candidate solution extracted from the clones corresponding to individual
i. Once the re-selection between
and
is complete, the last phase of the CSA is a diversity introduction consisting of replacing a percentage of the worst individuals in
with random individuals created with Equation (
22). As in other evolutionary metaheuristics, all the steps repeat until a criterion is reached, usually until a maximum iteration number.
3.3. Binary Particle Swarm Optimization
This metaheuristic takes as inspiration the behavior of flocks of bird flocks and schools of fish. It was initially proposed as an optimizer by Kennedy and Eberhart in 1995 [
33]. The algorithm considers a population of individuals called particles, which represent candidate solutions for a problem (usually an optimization problem); this set also describes a swarm from the analogous point of view. In the algorithmic implementation, the particles evolve by moving around the space of solutions, considering the velocity of each particle around itself and the best global particle found so far. In that sense, the original technique has two operators: (1) the velocity calculus, which considers the global and the local social behavior of each particle, and (2) position upgrade. The next lines describe the operators mathematically for the binary particle swarm optimization (BPSO) used in this paper [
34].
Velocity Calculus
In BPSO, the global velocity change utilizes two vectors which hold the probability that every bit changes either to zero or to one; the respective equations to calculate these vectors are
where
w represents the inertia weight, and
,
,
, and
are temporary values calculated with the following conditions:
if = 1 then = and = ,
if = 0 then = and = ,
if = 1 then = and = ,
if = 0 then = and = ,
with the indexes
i and
j representing the actual individual and the bit, respectively;
are the constriction factors taken from the original PSO;
and
are random numbers drawn from a uniform distribution; and
are the bits that belong to the local and global best individuals, respectively. After calculating
and
, the next step consists of transforming those probabilities into the velocity change of the actual particle:
Position Upgrade and Selection
The position calculus of the actual particle in the next iteration is
where
is the 2 complement of
, and
is a uniform random number. The last stage in the BPSO is the comparison of the generated candidate solution against the local best as well as the global best:
iff(xi) > f(xibest) then f(xibest) = f(xi) and bibest = bi,
iff(xi) > f(xgbest) then f(xgbest) = f(xi) and bgbest = bi,
where , , and are the real versions of the binary , , and , respectively.
3.4. Genetic Algorithms
Considered as an evolutionary algorithm [
22,
35], this metaheuristic was proposed in the 1960s. This algorithm is based on Darwin’s theory of evolution, where individuals are represented by bit strings; similar to the previous algorithms, this description is useful to codify simple data structures. As an optimizer, this technique is capable of finding competitive solutions to complex optimization problems [
35]. Therefore, it has been extensively used to solve problems from different domains (machine learning, operations research, image processing, etc.), and it was even utilized in a similar study to the one presented in this article [
21]. The operators used in the canonical version of the genetic algorithm (GA) are (1) interchange of genetic material, (2) a mutation scheme, and (3) re-selection of the fittest. Below is the mathematical description of these operators.
Crossover
One method to achieve crossover in GA is the roulette technique, in which it is necessary to calculate the fitness of every individual, and then the cumulative fitness as
where
is the real representation of the binary individual
. Later, the selection probability as well as the cumulative selection probability of every individual are computed according to their fitness (Equations (
17) and (
18)):
Two random numbers, and , from a uniform distribution are generated after the previous calculus, and the selection applies to the parents that meet and . After the selection of two parents in the prior step of the GA, the next step corresponds to the crossover, which is the crossover of one point in this paper. This method works by choosing, with a given probability , a point of the selected parents to generate two new individuals by an interchange of genetic information. The crossover points are calculated with and .
Mutation and Reselection
The mutation considers the change of every bit in the binary individual by taking the mutation probability
:
where
is the binary and mutated child number 1; the same procedure applies for child number 2. Finally, the last step in GA is the competence between the two parents and the two children:
3.5. Population Initialization
As mentioned previously, the optimization tool utilized in the problem of pipe design in a parabolic trough must be capable of searching in two numerical spaces, namely, real, and integer. For that reason we use binary versions of the aforementioned algorithms, which allow the management of those codifications. In that sense, the conformation of each individual both as real and as integer values is
whose binary representation—denoted by
—is a string of 150 bits. A more detailed explanation of each variable, their limits, as well as the number of bits used for a particular codification, is given in
Table 1.
In the four compared algorithms, the population is created by
where
is the population size,
is the total number of bits in each string,
is a row vector of
uniformly generated random numbers,
is a positive limiting function, and
l,
u are respectively the lower and upper limits of the search space. Finally, Equation (
5) representing the objective function can be written as: