A Survey on Energy Efficiency in Smart Homes and Smart Grids
Abstract
:1. Introduction
- a safer and more resilient electricity distribution network,
- self-healing protection mechanisms,
- advanced monitoring capabilities and load management,
- a cost reduction in network operations due to the dynamic balancing between production and demand,
- a cleaner, decentralized production of electricity,
- a reduction of the traditional costly peak production capacity,
- bidirectional flow of electricity.
- The architecture level, where it is necessary to consider problems as credentials distribution to enable end-to-end security between devices and applications. It also features dynamic fine-grain authorization management to control which application is entitled to use which data.
- Smart devices compose the hardware part of the grid. They can be hardened via secure elements in the devices [13]. Also, a challenge is defining low-cost, highly scalable secure element solutions, including hardware, provisioning, and deployment components, to use certain secure embedded elements well suited to SG applications.
- Software applications to manage the SG components.
2. Survey Methodology
3. Technical Solutions for Energy Efficiency with SGs and Homes
3.1. Smart Homes
- The Automation Ontology includes general concepts such as Resident and Location, but also ideas in the automation and the energy domain, such as device (with consumption per hour, peak power, on/off status), and Configuration (configuration data of an appliance),
- The Meter Data Ontology enables communication protocols for data exchange with the metering equipment,
- The Pricing Ontology is used for selecting the optimal tariff model for a specified time and energy load. It defines weighted criteria, which are then used by the reasoning engine for choosing the best tariff model.
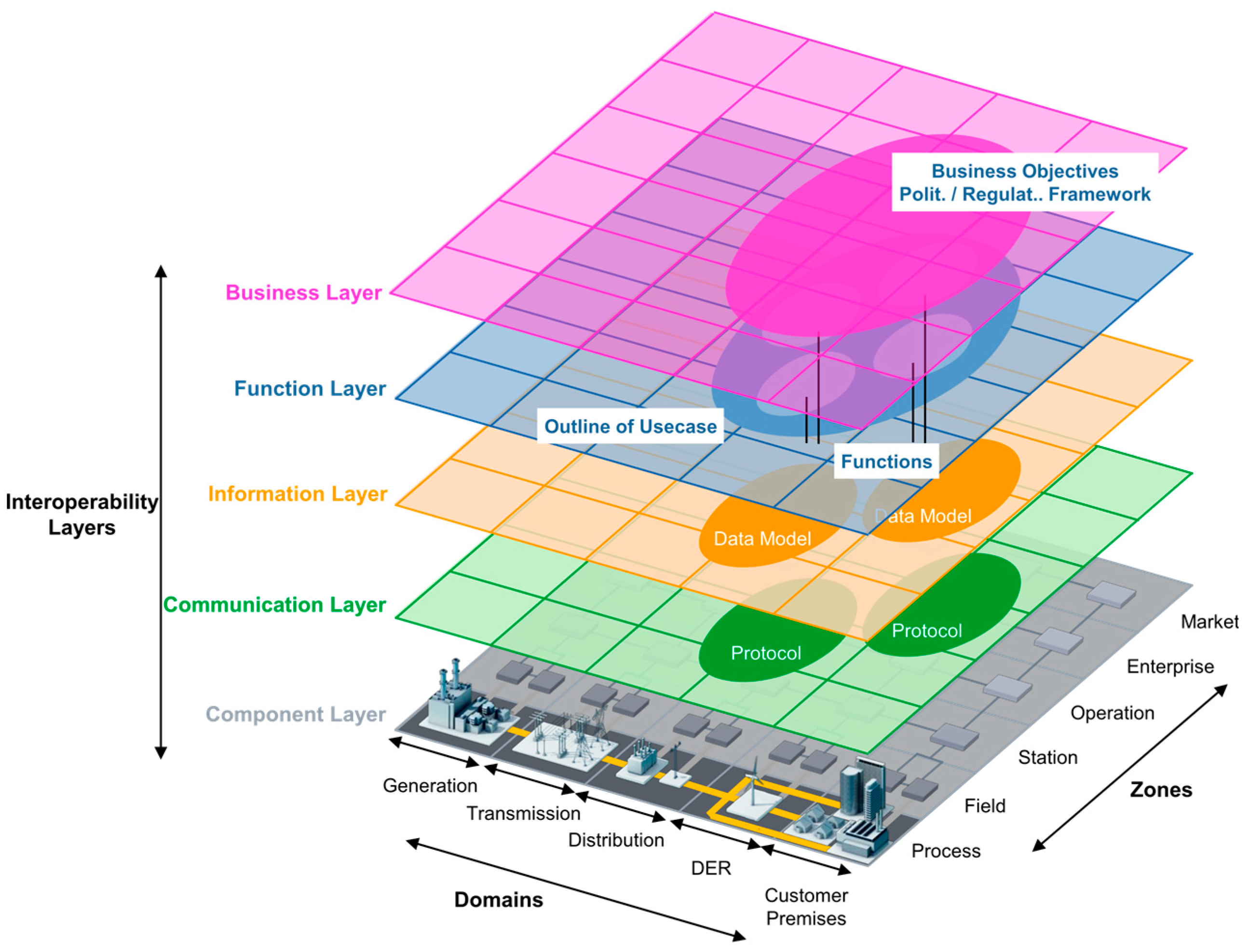
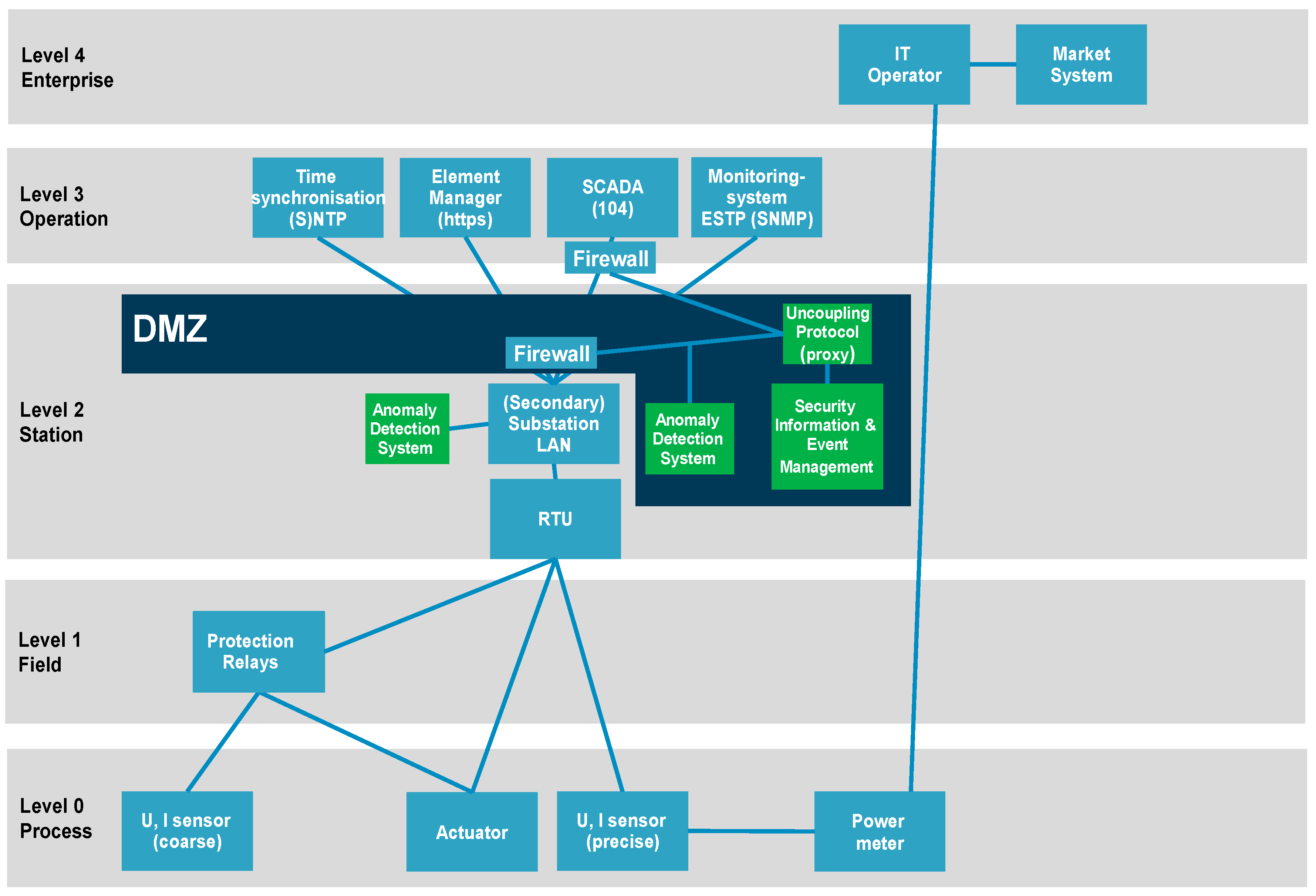
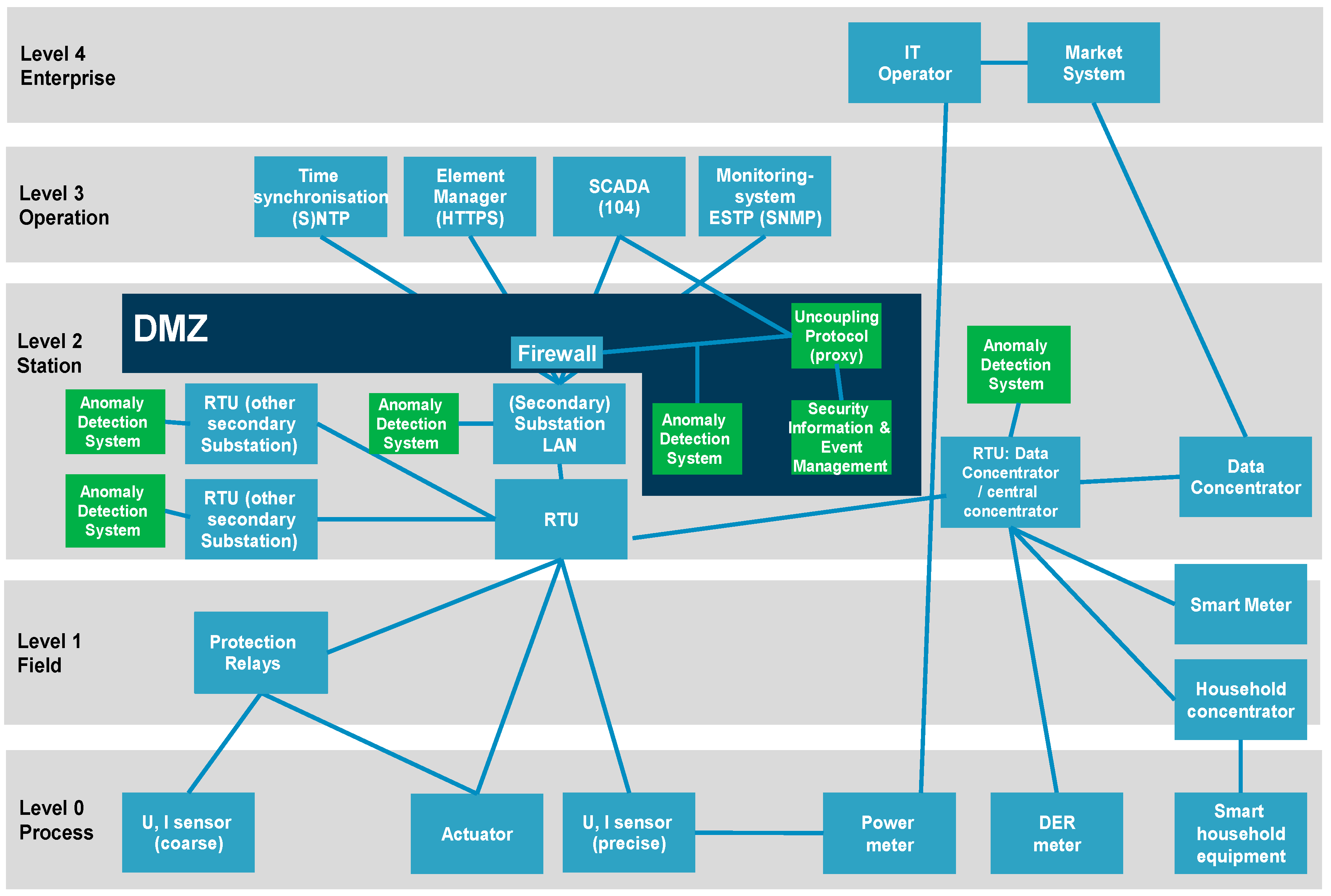
3.2. Smart Grids
4. Outlook and Future Work
4.1. Microgrids
4.2. Smart Homes
4.3. Smart Grids
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| ADS | Anomaly Detector Systems |
| AI | Artificial Intelligence |
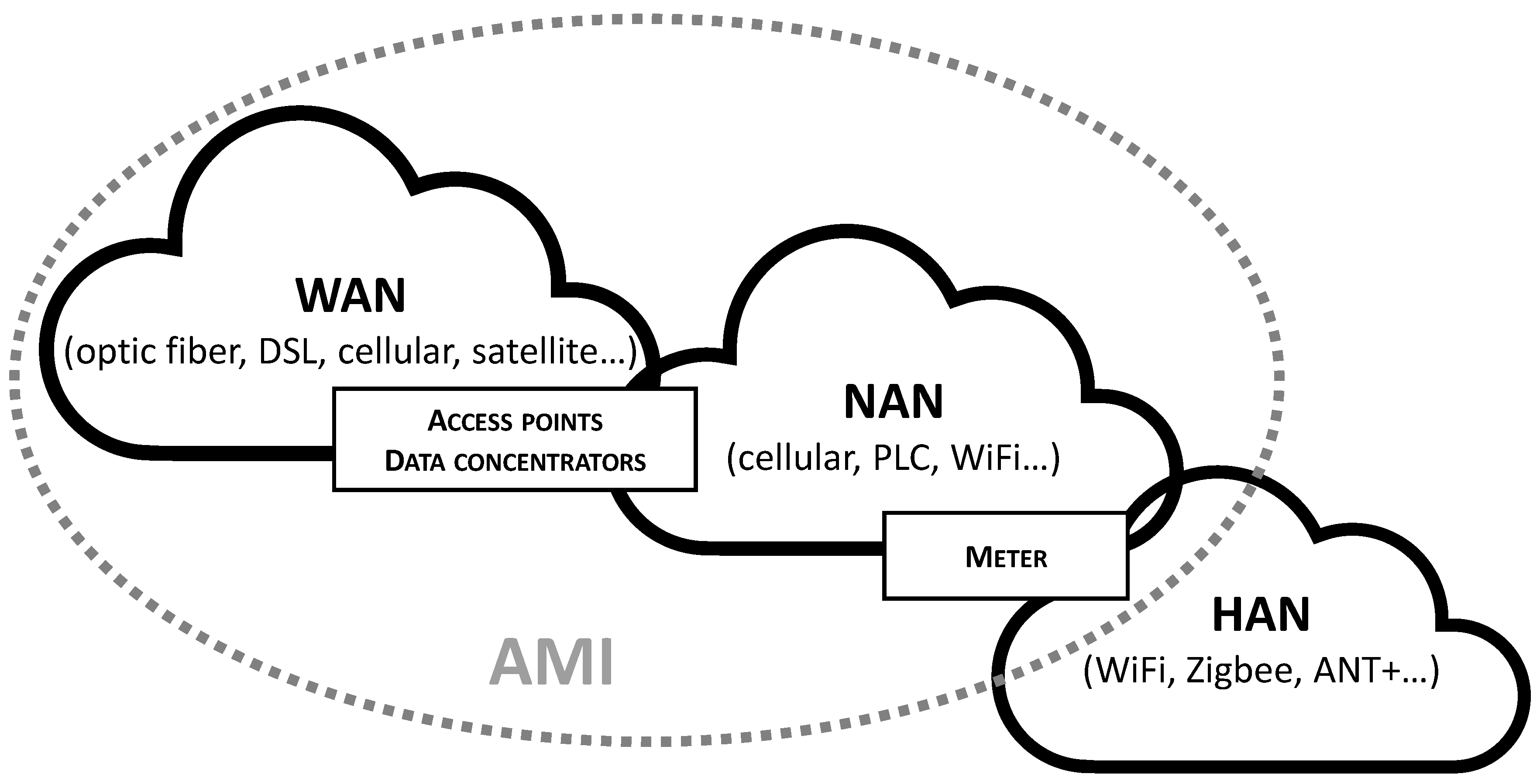
| AMI | Automated Metering Infrastructure |
| CPS | Cyber-Physical System |
| DMZ | Demilitarized Zone |
| HAN | Home Area Network |
| ICAS | Industrial Automation and Control Systems |
| ICT | Information and Communication Technologies |
| IDS | Intrusion Detection System |
| IED | Intelligent Electronic Device |
| IoT | Internet of Things |
| IS | Information Security |
| IT | Information Technologies |
| M2M | Machine-to-Machine |
| NAN | Neigborhood Area Network |
| OMS | Outage Management System |
| OT | Operational Technologies |
| PLC | Power Line Carrier |
| SCADA | Supervisory Control and Data Acquisition |
| SG | Smart Grid |
| SGAM | Smart Grid Architecture Model |
| WAN | Wide Area Network |
References
- Khan, B.; Getachew, H.; Alhelou, H.H. 17-Components of the smart-grid system. In Solving Urban Infrastructure Problems Using Smart City Technologies; Vacca, J.R., Ed.; Elsevier: Amsterdam, The Netherlands, 2021; pp. 385–397. ISBN 978-0-12-816816-5. [Google Scholar]
- Bigerna, S.; Bollino, C.A.; Micheli, S. Socio-economic acceptability for smart grid development—A comprehensive review. J. Clean. Prod. 2016, 131, 399–409. [Google Scholar] [CrossRef]
- Chen, Z.; An, H.; Sun, Z.; Cen, B.; Li, S. Comprehensive Evaluation of Smart Grid Development Level Under Electricity Market Layout. E3S Web Conf. 2018, 53, 02013. [Google Scholar] [CrossRef] [Green Version]
- Nafi, N.S.; Ahmed, K.; Gregory, M.A.; Datta, M. A survey of smart grid architectures, applications, benefits and standardization. J. Netw. Comput. Appl. 2016, 76, 23–36. [Google Scholar] [CrossRef]
- Han, W.; Xiao, Y. Edge computing enabled non-technical loss fraud detection for big data security analytic in Smart Grid. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 1697–1708. [Google Scholar] [CrossRef]
- Hasan, M.; Toma, R.N.; Nahid, A.-A.; Islam, M.; Kim, J.-M. Electricity theft detection in smart grid systems: A CNN-LSTM based approach. Energies 2019, 12, 3310. [Google Scholar] [CrossRef] [Green Version]
- Samudrala, A.N.; Amini, M.H.; Kar, S.; Blum, R.S. Distributed outage detection in power distribution networks. IEEE Trans. Smart Grid 2020, 11, 5124–5137. [Google Scholar] [CrossRef]
- Yuan, Y.; Dehghanpour, K.; Bu, F.; Wang, Z. Outage Detection in Partially Observable Distribution Systems using Smart Meters and Generative Adversarial Networks. IEEE Trans. Smart Grid 2020, 11, 5418–5430. [Google Scholar] [CrossRef]
- Chhaya, L.; Sharma, P.; Kumar, A.; Bhagwatikar, G. Cybersecurity for Smart Grid: Threats, Solutions and Standardization. In Advances in Greener Energy Technologies; Springer: New York, NY, USA, 2020; pp. 17–29. [Google Scholar]
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Comput. Netw. 2020, 169, 107094. [Google Scholar] [CrossRef]
- Marksteiner, S.; Vallant, H.; Nahrgang, K. Cyber security requirements engineering for low-voltage distribution smart grid architectures using threat modeling. J. Inf. Secur. Appl. 2019, 49, 102389. [Google Scholar] [CrossRef]
- Lamba, V.; Šimková, N.; Rossi, B. Recommendations for smart grid security risk management. Cyber-Phys. Syst. 2019, 5, 92–118. [Google Scholar] [CrossRef]
- Yekini, T.A.; Jaafar, F.; Zavarsky, P. Study of trust at device level of the internet of things architecture. In Proceedings of the 2019 IEEE 19th International Symposium on High Assurance Systems Engineering (HASE), Hangzhou, China, 3–5 January 2019; pp. 150–155. [Google Scholar]
- Naseer, O.; Ullah, S.; Anjum, L. Blockchain-Based Decentralized Lightweight Control Access Scheme for Smart Grids. Arab. J. Sci. Eng. 2021, 46, 8233–8243. [Google Scholar] [CrossRef]
- Khalid, R.; Samuel, O.; Javaid, N.; Aldegheishem, A.; Shafiq, M.; Alrajeh, N. A Secure Trust Method for Multi-Agent System in Smart Grids Using Blockchain. IEEE Access 2021, 9, 59848–59859. [Google Scholar] [CrossRef]
- Hasankhani, A.; Mehdi Hakimi, S.; Bisheh-Niasar, M.; Shafie-khah, M.; Asadolahi, H. Blockchain technology in the future smart grids: A comprehensive review and frameworks. Int. J. Electr. Power Energy Syst. 2021, 129, 106811. [Google Scholar] [CrossRef]
- Gough, D.; Oliver, S.; Thomas, J. An Introduction to Systematic Reviews; Sage: Thousand Oaks, CA, USA, 2017. [Google Scholar]
- Toma, R.N.; Hasan, M.N.; Nahid, A.-A.; Li, B. Electricity theft detection to reduce non-technical loss using support vector machine in smart grid. In Proceedings of the 2019 1st International Conference on Advances in Science, Engineering and Robotics Technology (ICASERT), Dhaka, Bangladesh, 3–5 May 2019; pp. 1–6. [Google Scholar]
- Abdulrahaman Okino Otuoze, M.W.M.; Sofimieari, I.E.; Dobi, A.M.; Sule, A.H.; Abioye, A.E.; Saeed, M.S. Electricity theft detection framework based on universal prediction algorithm. Indones. J. Electr. Eng. Comput. Sci. 2019, 15, 758–768. [Google Scholar] [CrossRef]
- Jindal, A.; Schaeffer-Filho, A.; Marnerides, A.K.; Smith, P.; Mauthe, A.; Granville, L. Tackling energy theft in smart grids through data-driven analysis. In Proceedings of the 2020 International Conference on Computing, Networking and Communications (ICNC), Big Island, HI, USA, 17–20 February 2020; pp. 410–414. [Google Scholar]
- Punmiya, R.; Choe, S. Energy theft detection using gradient boosting theft detector with feature engineering-based preprocessing. IEEE Trans. Smart Grid 2019, 10, 2326–2329. [Google Scholar] [CrossRef]
- Yao, D.; Wen, M.; Liang, X.; Fu, Z.; Zhang, K.; Yang, B. Energy theft detection with energy privacy preservation in the smart grid. IEEE Internet Things J. 2019, 6, 7659–7669. [Google Scholar] [CrossRef]
- Kement, C.E.; Gultekin, H.; Tavli, B. A Holistic Analysis of Privacy Aware Smart Grid Demand Response. IEEE Trans. Ind. Electron. 2020, 68, 7631–7641. [Google Scholar] [CrossRef]
- Aydeger, A.; Saputro, N.; Akkaya, K.; Uluagac, S. SDN-enabled recovery for Smart Grid teleprotection applications in post-disaster scenarios. J. Netw. Comput. Appl. 2019, 138, 39–50. [Google Scholar] [CrossRef]
- Singh, N.K.; Mahajan, V. Smart Grid: Cyber Attack Identification And Recovery Approach. In Proceedings of the 2019 2nd International Conference on Innovations in Electronics, Signal Processing and Communication (IESC), Shillong, India, 1–2 March 2019; pp. 1–5. [Google Scholar]
- Haggi, H.; Song, M.; Sun, W. A Review of Smart Grid Restoration to Enhance Cyber-Physical System Resilience. In Proceedings of the 2019 IEEE Innovative Smart Grid Technologies-Asia (ISGT Asia), Chengdu, China, 21–24 May 2019; pp. 4008–4013. [Google Scholar]
- Mohamed, A.; Refaat, S.S.; Abu-Rub, H. A review on big data management and decision-making in smart grid. Power Electron. Drives 2019, 4, 1–13. [Google Scholar] [CrossRef] [Green Version]
- Mishra, S.; Glaws, A.; Palanisamy, P. Predictive Analytics in Future Power Systems: A Panorama and State-Of-The-Art of Deep Learning Applications. In Optimization, Learning, and Control for Interdependent Complex Networks; Springer: New York, NY, USA, 2020; pp. 147–182. [Google Scholar]
- Kabir, E.; Guikema, S.D.; Quiring, S.M. Predicting thunderstorm-induced power outages to support utility restoration. IEEE Trans. Power Syst. 2019, 34, 4370–4381. [Google Scholar] [CrossRef]
- Kumar, P.; Lin, Y.; Bai, G.; Paverd, A.; Dong, J.S.; Martin, A. Smart grid metering networks: A survey on security, privacy and open research issues. IEEE Commun. Surv. Tutor. 2019, 21, 2886–2927. [Google Scholar] [CrossRef] [Green Version]
- Musleh, A.S.; Yao, G.; Muyeen, S. Blockchain applications in smart grid–review and frameworks. IEEE Access 2019, 7, 86746–86757. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Rodrigues, J.J.P.C.; Kozlov, S.A. Blockchain in Smart Grids: A Review on Different Use Cases. Sensors 2019, 19, 4862. [Google Scholar] [CrossRef] [Green Version]
- Jow, J.; Xiao, Y.; Han, W. A survey of intrusion detection systems in smart grid. Int. J. Sens. Netw. 2017, 23, 170–186. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L. DeepCoin: A Novel Deep Learning and Blockchain-Based Energy Exchange Framework for Smart Grids. IEEE Trans. Eng. Manag. 2020, 67, 1285–1297. [Google Scholar] [CrossRef] [Green Version]
- Karimipour, H.; Geris, S.; Dehghantanha, A.; Leung, H. Intelligent anomaly detection for large-scale smart grids. In Proceedings of the 2019 IEEE Canadian Conference of Electrical and Computer Engineering (CCECE), Edmonton, AB, Canada, 5–8 May 2019; pp. 1–4. [Google Scholar]
- Rossi, B.; Chren, S.; Buhnova, B.; Pitner, T. Anomaly detection in smart grid data: An experience report. In Proceedings of the 2016 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Budapest, Hungary, 9–12 October 2016; pp. 002313–002318. [Google Scholar]
- Karimipour, H.; Dehghantanha, A.; Parizi, R.M.; Choo, K.-K.R.; Leung, H. A deep and scalable unsupervised machine learning system for cyber-attack detection in large-scale smart grids. IEEE Access 2019, 7, 80778–80788. [Google Scholar] [CrossRef]
- do Prado, J.C.; Qiao, W.; Qu, L.; Agüero, J.R. The next-generation retail electricity market in the context of distributed energy resources: Vision and integrating framework. Energies 2019, 12, 491. [Google Scholar] [CrossRef] [Green Version]
- Sayed, K.; Gabbar, H.A. SCADA and smart energy grid control automation. In Smart Energy Grid Engineering; Elsevier: Amsterdam, The Netherlands, 2017; pp. 481–514. [Google Scholar]
- CEN-CENELEC-ETSI. Smart Grid Coordination Group Smart Grid Reference Architecture; European Commission: Luxembourg, 2012. [Google Scholar]
- Sreekumar, S.; Kumar, D.S.; Savier, J. A Case Study on Self Healing of Smart Grid with Islanding and Inverter Volt-VAR function. IEEE Trans. Ind. Appl. 2020, 56, 5408–5416. [Google Scholar]
- Tsitaitse, T.J.; Cai, Y.; Ditta, A. Secure self-healing group key distribution scheme with constant storage for SCADA systems in smart grid. Wirel. Pers. Commun. 2018, 101, 1749–1763. [Google Scholar] [CrossRef]
- Marikyan, D.; Papagiannidis, S.; Alamanos, E. A systematic review of the smart home literature: A user perspective. Technol. Forecast. Soc. Chang. 2019, 138, 139–154. [Google Scholar] [CrossRef]
- Mahmud, S.; Ahmed, S.; Shikder, K. A smart home automation and metering system using internet of things (IoT). In Proceedings of the 2019 International Conference on Robotics, Electrical and Signal Processing Techniques (ICREST), Dhaka, Bangladesh, 10–12 January 2019; pp. 451–454. [Google Scholar]
- Harsha, S.S.; Reddy, S.C.; Mary, S.P. Enhanced home automation system using Internet of Things. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 10–11 February 2017; pp. 89–93. [Google Scholar]
- The European Parliament and the Council of the European Union. Directive 2012/27/EU of the European Parliament and of the Council of 25 October 2012 on Energy Efficiency, Amending Directives 2009/125/EC and 2010/30/EU and Repealing Directives 2004/8/EC and 2006/32/EC Text. with EEA Relevance; Office Journal 315; European Union: Maastricht, The Netherlands, 2012. [Google Scholar]
- Spencer, R. 5 Ways the Internet of Things Could Help Combat Climate Change. Available online: https://www.lanner-america.com/blog/5-ways-internet-things-help-combat-climate-change/ (accessed on 1 October 2020).
- Dobler, C.; Pfeifer, D.; Streicher, W. Reaching energy autonomy in a medium-sized city–three scenarios to model possible future energy developments in the residential building sector. Sustain. Dev. 2018, 26, 859–869. [Google Scholar] [CrossRef] [Green Version]
- Tomic, S.; Fensel, A.; Pellegrini, T. Sesame demonstrator: Ontologies, services and policies for energy efficiency. In Proceedings of the 6th International Conference on Semantic Systems, Graz, Austria, 1–3 September 2010; pp. 1–4. [Google Scholar]
- Tomic, S.; Fensel, A.; Schwanzer, M.; Veljovic, M.K.; Stefanovic, M. Semantics for energy efficiency in smart home environments. In Applied Semantic Web Technologies; Taylor & Fancis Group: New York, NY, USA, 2012; pp. 429–454. [Google Scholar]
- H2020 ENTROPY | Smartcities Information System. Available online: https://smartcities-infosystem.eu/sites-projects/projects/entropy (accessed on 2 October 2020).
- Fotopoulou, E.; Zafeiropoulos, A.; Terroso-Sáenz, F.; Şimşek, U.; González-Vidal, A.; Tsiolis, G.; Gouvas, P.; Liapis, P.; Fensel, A.; Skarmeta, A. Providing personalized energy management and awareness services for energy efficiency in smart buildings. Sensors 2017, 17, 2054. [Google Scholar] [CrossRef] [Green Version]
- Kapourani, B.; Fotopoulou, E.; Papaspyros, D.; Zafeiropoulos, A.; Mouzakitis, S.; Koussouris, S. Propelling SMEs business intelligence through linked data production and consumption. In Proceedings of the OTM Confederated International Conferences “On the Move to Meaningful Internet Systems”, Rhodes, Greece, 21–25 October 2015; pp. 107–116. [Google Scholar]
- JSON-LD 1.0. Available online: https://www.w3.org/TR/json-ld/ (accessed on 3 December 2016).
- Drools—Business Rules Management System (JavaTM, Open Source). Available online: https://www.drools.org/ (accessed on 2 October 2020).
- González-Vidal, A.; Ramallo-González, A.P.; Terroso-Sáenz, F.; Skarmeta, A. Data driven modeling for energy consumption prediction in smart buildings. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 4562–4569. [Google Scholar]
- Krebs, B. Smart Meters—Krebs on Security. Available online: https://krebsonsecurity.com/2012/04/fbi-smart-meter-hacks-likely-to-spread/ (accessed on 2 October 2020).
- Han, W.; Xiao, Y. Non-technical loss fraud in advanced metering infrastructure in smart grid. In Proceedings of the International Conference on Cloud Computing and Security, Nanjing, China, 29–31 July 2016; pp. 163–172. [Google Scholar]
- Han, W.; Xiao, Y. A novel detector to detect colluded non-technical loss frauds in smart grid. Comput. Netw. 2017, 117, 19–31. [Google Scholar] [CrossRef] [Green Version]
- Buzau, M.M.; Tejedor-Aguilera, J.; Cruz-Romero, P.; Gómez-Expósito, A. Detection of non-technical losses using smart meter data and supervised learning. IEEE Trans. Smart Grid 2018, 10, 2661–2670. [Google Scholar] [CrossRef]
- He, H.; Yan, J. Cyber-physical attacks and defences in the smart grid: A survey. IET Cyber-Phys. Syst. Theory Appl. 2016, 1, 13–27. [Google Scholar] [CrossRef] [Green Version]
- Ghansah, I. Smart Grid Cyber Security Potential Threats, Vulnerabilities and Risks: Interim Project Report; California Energy Commission: Sacramento, CA, USA, 2012. [Google Scholar]
- Pillitteri, V.Y.; Brewer, T.L. Guidelines for Smart Grid Cybersecurity; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2014. [Google Scholar]
- European Commission Smart Grids Task Force. Available online: https://ec.europa.eu/energy/topics/markets-and-consumers/smart-grids-and-meters/smart-grids-task-force_en (accessed on 2 October 2020).
- Kovacs, E.; Bauer, M.; Kim, J.; Yun, J.; Le Gall, F.; Zhao, M. Standards-based worldwide semantic interoperability for IoT. IEEE Commun. Mag. 2016, 54, 40–46. [Google Scholar] [CrossRef]
- Fortino, G.; Savaglio, C.; Palau, C.E.; de Puga, J.S.; Ganzha, M.; Paprzycki, M.; Montesinos, M.; Liotta, A.; Llop, M. Towards multi-layer interoperability of heterogeneous IoT platforms: The INTER-IoT approach. In Integration, Interconnection, and Interoperability of IoT Systems; Springer: New York, NY, USA, 2018; pp. 199–232. [Google Scholar]
- Tuna, G.; Kogias, D.G.; Gungor, V.C.; Gezer, C.; Taşkın, E.; Ayday, E. A survey on information security threats and solutions for Machine to Machine (M2M) communications. J. Parallel Distrib. Comput. 2017, 109, 142–154. [Google Scholar] [CrossRef] [Green Version]
- Odelu, V.; Das, A.K.; Wazid, M.; Conti, M. Provably secure authenticated key agreement scheme for smart grid. IEEE Trans. Smart Grid 2016, 9, 1900–1910. [Google Scholar] [CrossRef]
- Zhang, H.; Wang, J.; Ding, Y. Blockchain-based decentralized and secure keyless signature scheme for smart grid. Energy 2019, 180, 955–967. [Google Scholar] [CrossRef]
- Fensel, A.; Gómez Berbís, J.M. Energy Efficiency in Smart Homes and Smart Grids. Energies 2021, 14, 2054. [Google Scholar] [CrossRef]

Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Prieto González, L.; Fensel, A.; Gómez Berbís, J.M.; Popa, A.; de Amescua Seco, A. A Survey on Energy Efficiency in Smart Homes and Smart Grids. Energies 2021, 14, 7273. https://doi.org/10.3390/en14217273
Prieto González L, Fensel A, Gómez Berbís JM, Popa A, de Amescua Seco A. A Survey on Energy Efficiency in Smart Homes and Smart Grids. Energies. 2021; 14(21):7273. https://doi.org/10.3390/en14217273
Chicago/Turabian StylePrieto González, Lisardo, Anna Fensel, Juan Miguel Gómez Berbís, Angela Popa, and Antonio de Amescua Seco. 2021. "A Survey on Energy Efficiency in Smart Homes and Smart Grids" Energies 14, no. 21: 7273. https://doi.org/10.3390/en14217273
APA StylePrieto González, L., Fensel, A., Gómez Berbís, J. M., Popa, A., & de Amescua Seco, A. (2021). A Survey on Energy Efficiency in Smart Homes and Smart Grids. Energies, 14(21), 7273. https://doi.org/10.3390/en14217273







