Improved Secure Encryption with Energy Optimization Using Random Permutation Pseudo Algorithm Based on Internet of Thing in Wireless Sensor Networks
Abstract
1. Introduction
2. Related Work
3. Contribution of the Proposed Work
- The proposed protocol aims to enhance performance of communication and network lifetime. It can be achieved by minimizing energy consumption and communication delay.
- The implementation of secure encryption random permutation pseudo algorithm (SERPPA) for enhancing energy efficient communication.
- The proposed model contains work cluster member who is responsible for cluster head selection.
- The cluster head has a significant role, and its activities monitor and backup the nodes’ activities in the network.
- In this work, several existing protocols are described with their advantages and disadvantages. The proposed model is different from the existing models, and the overall result will enhance the data traffic, energy consumption, and throughput rate through stable routing.
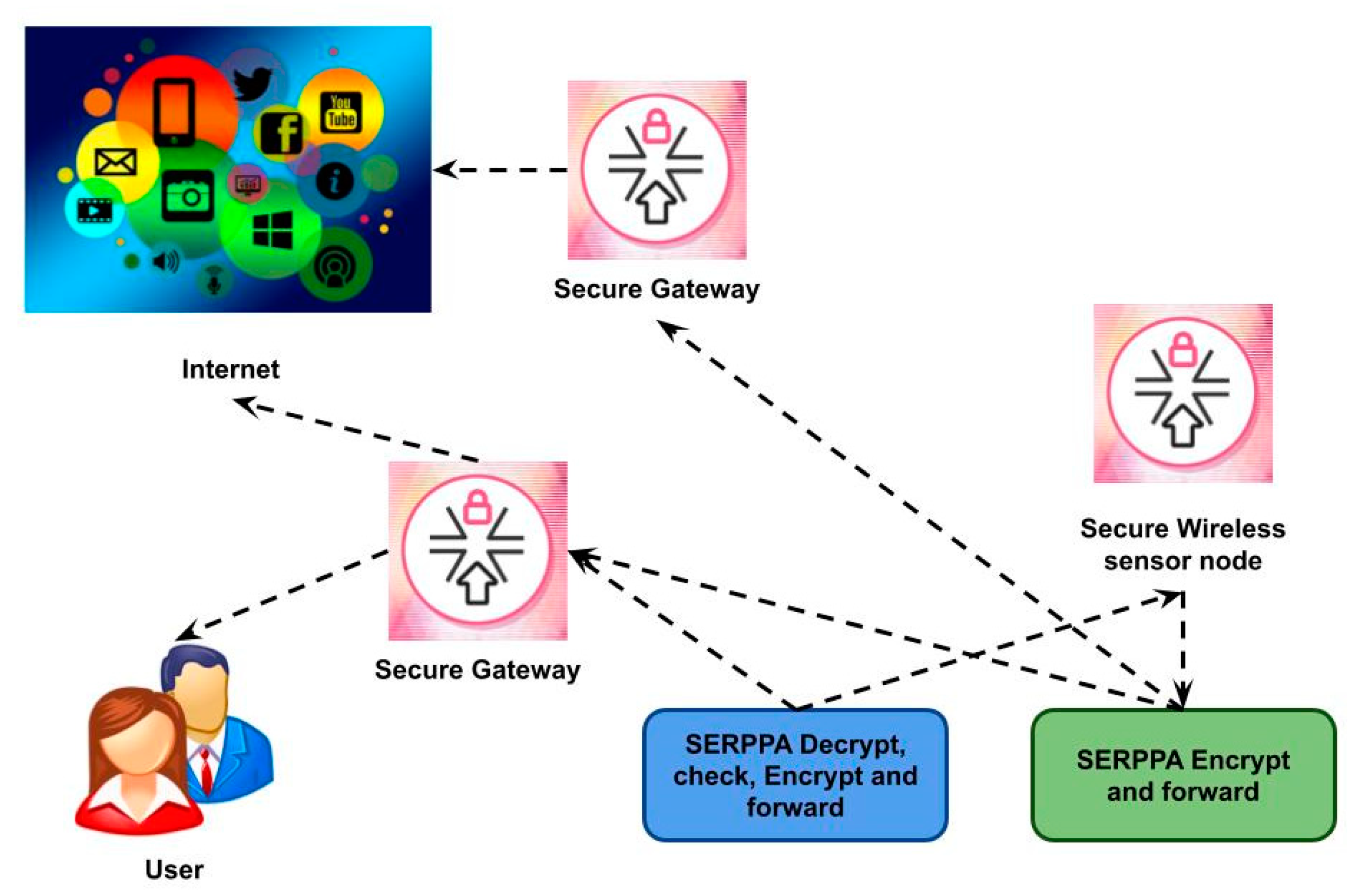
Secure Encryption Random Permutation Pseudo Algorithm (SERPPA)
| Algorithm 1: of SERPPA |
| Begin |
| start the process of getting 512-bitlength inputs |
| remove the presence of same character at multiple times |
| do |
| assign the encryption vector values [5,15,22,8,9,11] for the 512 bits |
| where “x” is first character |
| ex: x = 5 of key length is assigned |
| then |
| taken key [15,22,8,9,11] |
| assign to remaining characters of 512 bits |
| if |
| presence of space between a letter |
| assign a special character (\, #, $, &, *) |
| end |
| do |
| encryption |
| apply k = [5,15,22,8,9,11] values to first set of 512 input message |
| next |
| apply k = [11,9,8,22,15,5] to next set of same 512 input message |
| Continue… |
| Stop once the character get over |
| end |
| end |
| end |
| Algorithm 2: for Secure Encryption Random Permutation Pseudo Algorithm (SERPPA) for Energy Consumption |
| 1. Begin |
| 2. Step-1 creates the simulation network (1500 × 1500) |
| 3. { |
| 4. Set of nodes are deployed randomly; ; |
| 5. Check the node’s availability state (idle, active) |
| 6. { |
| 7. Send the request “ hello” to all neighboring sensor nodes []; |
| 8. If received the message and send the acknowledgment nodes states is active ; |
| 9. Else if |
| 10. Message not received the sensor node, the node is the idle state [; |
| 11. Collect the cooperative node list; |
| 12. } |
| 13. Ready to form the network ; |
| 14. } |
| 15. Step-2 creates the cluster formation and CH election process-based energy factor. |
| 16. Create the cluster according to with cooperative node list |
| 17. // , x,i coordinates and, y,j coordinates calculate with x and y coordinate distance |
| 18. Energy factor is patched up with the node cluster for transferring to BS |
| 19. //node energy defines |
| 20. Packet transfer received Total ratio ; |
| 21. EDA is the maximum number of node hops in network, and hop(i) is the hop numbers from node i to Sink. |
| 22. ETX = where Df represents the calculated likelihood that a packet will be received by a neighbour and Dr is the calculated likelihood that an acknowledgement packet will be successfully received. |
| 23. Determine optimum distance of a node; |
| 24. if (distance >= d0) nodeArch. Node(chNo). energy = else nodeArch. Node(chNo). energy = end nodeArch. Node(chNo). energy = nodeArch. Node(chNo). energy –ctrPacketLength * ERX * round (nodeArch.numNode/clusterModel. NumCluster); |
| 25. end |
| a. ClusterModel. NodeArch = nodeArch; |
| 26. end |
4. Experimental Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Rehman, R.A.; Khan, B. IoT Elements, Layered Architectures and Security Issues: A Comprehensive Survey. Sensors 2018, 18, 2796. [Google Scholar]
- Salah, K. The Era of Internet of Things, 2nd ed.; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Rayes, A.; Samer, S. Internet of Things from Hype to Reality, 2nd ed.; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Atlam, H.; Walters, R.J.; Wills, G.B. Internet of Things: State-of-the-art, Challenges, Applications, and Open Issues. Int. J. Intell. Comput. Res. 2018, 9, 928–938. [Google Scholar] [CrossRef]
- Costa, D.G.; Figuerêdo, S.; Oliveira, G. Cryptography in Wireless Multimedia Sensor Networks: A Survey and Research Directions. Cryptography 2017, 1, 4. [Google Scholar] [CrossRef]
- Kambourakis, G.; Marmol, F.G.; Wang, G. Security and Privacy in Wireless and Mobile Networks. Future Internet 2018, 10, 18. [Google Scholar] [CrossRef]
- Ziegler, S. Internet of Things Security and Data Protection, 2nd ed.; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Cheruvu, S.; Kumar, A.; Smith, N.; Wheeler, D.M. Demystifying Internet of Things Security: Successful IoT Device/Edge and Platform Security Deployment; Apress: Berkeley, CA, USA, 2019. [Google Scholar]
- Mahmood, Z. (Ed.) Security, Privacy and Trust in the IoT Environment; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Banday, M.T. Cryptographic Security Solutions for the Internet of Things; IGI Global: Hershey, PA, USA, 2019. [Google Scholar]
- Biryukov, A.; Perrin, L. State of the Art in Lightweight Symmetric Cryptography. IACR Cryptology ePrint Archive. 2017. Available online: https://eprint.iacr.org/2017/511 (accessed on 28 October 2019).
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating Critical Security Issues of the IoT World: Present and Future Challenges. IEEE Internet Things J. 2017, 5, 2483–2495. [Google Scholar] [CrossRef]
- Hamad, F.; Smalov, L.; James, A. Energy-aware Security in M-Commerce and the Internet of Things. IETE Tech. Rev. 2009, 26, 357–362. [Google Scholar] [CrossRef]
- Bilal, M.; Kang, S.G. An Authentication Protocol for Future Sensor Networks. Sensors 2017, 17, 979. [Google Scholar] [CrossRef]
- Saraiva, D.A.F.; Leithardt, V.R.Q.; de Paula, D.; Sales Mendes, A.; González, G.V.; Crocker, P. PRISEC: Comparison of Symmetric Key Algorithms for IoT Devices. Sensors 2019, 19, 4312. [Google Scholar] [CrossRef]
- Von zur Gathen, J. CryptoSchool; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Rivest, R.; Schuldt, J. Spritz—A Spongy RC4-Like Stream Cipher and Hash Function. Available online: https://en.wikipedia.org/wiki/RC4#cite_note-Rivest2014-14 (accessed on 27 October 2014).
- Tang, H.; Zhu, L.; Zhang, Z. A Novel Authenticated Group Key Agreement Protocol Based on Elliptic Curve Diffie-Hellman. In Proceedings of the 2008 4th International Conference on Wireless Communications, Dalian, China, 12–17 October 2008; pp. 1–4. [Google Scholar]
- Zhang, Z.; Jiang, C.; Deng, J. A novel group key agreement protocol for wireless sensor networks. In Proceedings of the 2010 International Conference on Measuring Technology and Mechatronics Automation, Changsha, China, 13–14 March 2010; pp. 230–233. [Google Scholar]
- Pramod, N.D.B.; Sharnappa, G.R. Review on fault detection and recovery in WSN. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2015, 5. [Google Scholar]
- Abi-Char, P.E.; Mhamed, A.; El-Hassan, B. A secure authenticated key agreement protocol based on elliptic curve cryptography. In Proceedings of the 3rd International Symposium on Information Assurance and Security, Manchester, UK, 29–31 August 2007; pp. 89–94. [Google Scholar]
- Meingast, M.; Roosta, T.; Sastry, S. Security and privacy issues with health care information technology. In Proceedings of the 2006 International Conference of the IEEE Engineering in Medicine and Biology Society, New York, NY, USA, 30 August–3 September 2006; pp. 5453–5458. [Google Scholar]
- Singelée, D.; Latré, B.; Braem, B.; Peeters, M.; De Soete, M.; De Cleyn, P.; Preneel, B.; Moerman, I.; Blondia, C. A secure low-delay protocol for wireless body area networks. Adhoc. Sens. Wirel. Netw. 2010, 9, 53–72. [Google Scholar]
- Ertaul, L.; Lu, W. ECC Based Treshold Cryptography for Secure Data Forwarding and Secure Key Exchange; University of Waterloo: Waterloo, ON, Canada, 2005. [Google Scholar]
- Ertaul, L.; Chudinov, P.; Morales, B. IoT security: Authenticated lightweight key exchange (ALIKE). In Proceedings of the International Conference on Wireless Networks (ICWN), Rome, Italy, 30 June–4 July 2019; pp. 45–50. [Google Scholar]
- Eldefrawy, M.H.; Khan, M.K.; Alghathbar, K. A key agreement algorithm with rekeying for wireless sensor networks using public key cryptography. In Proceedings of the 2010 International Conference on Anti-Counterfeiting, Hoboken, NJ, USA, 22–24 March 2010; pp. 1–6. [Google Scholar]
- Wu, J.; Stinson, D.R. Three improved algorithms for multipath key establishment in sensor networks using protocols for secure message transmission. IEEE Trans. Dependable Secur. Comput. 2010, 8, 929–937. [Google Scholar]
- Gope, P.; Das, A.K.; Kumar, N.; Cheng, Y. Lightweight and Physically Secure Anonymous Mutual Authentication Protocol for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2019, 15, 4957–4968. [Google Scholar] [CrossRef]
- He, D.; Ma, M.; Zeadally, S.; Kumar, N.; Liang, K. Certificateless Public Key Authenticated Encryption with Keyword Search for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3618–3627. [Google Scholar] [CrossRef]
- Dua, A.; Kumar, N.; Das, A.K.; Susilo, W. Secure Message Communication Protocol Among Vehicles in Smart City. IEEE Trans. Veh. Technol. 2017, 67, 4359–4373. [Google Scholar] [CrossRef]
- Tyagi, S.; Kumar, N. A systematic review on clustering and routing techniques based upon LEACH protocol for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 623–645. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kumar, N.; Lee, J.-H. Anonymous Authentication for Wireless Body Area Networks with Provable Security. IEEE Syst. J. 2016, 11, 2590–2601. [Google Scholar] [CrossRef]
- Yousefpoor, M.S.; Barati, H. Dynamic key management algorithms in wireless sensor networks: A survey. Comput. Commun. 2018, 134, 52–69. [Google Scholar] [CrossRef]
- Yousefpoor, M.S.; Barati, H. DSKMS: A dynamic smart key management system based on fuzzy logic in wireless Complexity 9 sensor networks. Wirel. Netw. 2020, 26, 2515–2535. [Google Scholar] [CrossRef]
- Sampathkumar, A.; Tesfayohani, M.; Shandilya, S.K.; Goyal, S.B.; Jamal, S.S.; Shukla, P.K.; Bedi, P.; Albeedan, M. Internet of Medical Things (IoMT) and Reflective Belief Design-Based Big Data Analytics with Convolution Neural Network-Metaheuristic Optimization Procedure (CNN-MOP). Comput. Intell. Neurosci. 2022, 2022, 2898061. [Google Scholar] [CrossRef]
- Ramanan, M.; Singh, L.; Kumar, A.S.; Suresh, A.; Sampathkumar, A.; Jain, V.; Bacanin, N. Secure blockchain enabled Cyber- Physical health systems using ensemble convolution neural network classification. Comput. Electr. Eng. 2022, 101, 108058. [Google Scholar] [CrossRef]
- Arumugam, S.; Shandilya, S.K.; Bacanin, N. Federated Learning-Based Privacy Preservation with Blockchain Assistance in IoT 5G Heterogeneous Networks. J. Web Eng. 2022, 21, 1323–1346. [Google Scholar] [CrossRef]
- Bedi, P.; Goyal, S.B.; Rajawat, A.S.; Shaw, R.N.; Ghosh, A. Application of AI/IoT for Smart Renewable Energy Management in Smart Cities. In AI and IoT for Smart City Applications; Studies in Computational Intelligence; Piuri, V., Shaw, R.N., Ghosh, A., Islam, R., Eds.; Springer: Singapore, 2022; Volume 1002. [Google Scholar] [CrossRef]
- Sharma, S.; Rani, M.; Goyal, S. Energy Efficient Data Dissemination with ATIM Window and Dynamic Sink in Wireless Sensor Networks. In Proceedings of the 2009 International Conference on Advances in Recent Technologies in Communication and Computing, Kerala, India, 27–28 October 2009; pp. 559–564. [Google Scholar] [CrossRef]
- Sharma, S.; Goyal, S.B.; Qamar, S. Four-Layer Architecture Model for Energy Conservation in Wireless Sensor Networks. In Proceedings of the 2009 4th International Conference on Embedded and Multimedia Computing, Jeju, Republic of Korea, 10–12 December 2009; pp. 1–3. [Google Scholar] [CrossRef]
- Kaliappan, V.K.; Lalpet Ranganathan, A.B.; Periasamy, S.; Thirumalai, P.; Nguyen, T.A.; Jeon, S.; Min, D.; Choi, E. Energy-Efficient Offloading Based on Efficient Cognitive Energy Management Scheme in Edge Computing Device with Energy Optimization. Energies 2022, 15, 8273. [Google Scholar] [CrossRef]
- Ibrahim, B.; Rabelo, L.; Gutierrez-Franco, E.; Clavijo-Buritica, N. Machine Learning for Short-Term Load Forecasting in Smart Grids. Energies 2022, 15, 8079. [Google Scholar] [CrossRef]
- Banuselvasaraswathy, B.; Sampathkumar, A.; Jayarajan, P.; Sheriff, N.; Ashwin, M.; Sivasankaran, V. A Review on Thermal and QoS Aware Routing Protocols for Health Care Applications in WBASN. In Proceedings of the 2020 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 28–30 July 2020; pp. 1472–1477. [Google Scholar] [CrossRef]
- Subrahmanyam, R.; Rukma Rekha, N.; Subba Rao, Y.V. Multipartite Verifiable Secret Sharing Based on CRT. In Computer Networks and Inventive Communication Technologies; Lecture Notes on Data Engineering and Communications Technologies; Smys, S., Bestak, R., Palanisamy, R., Kotuliak, I., Eds.; Springer: Singapore, 2022; Volume 75. [Google Scholar] [CrossRef]
- Subramani, N.; Mohan, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. An Efficient Metaheuristic-Based Clustering with Routing Protocol for Underwater Wireless Sensor Networks. Sensors 2022, 22, 415. [Google Scholar] [CrossRef]
- Bacanin, N.; Arnaut, U.; Zivkovic, M.; Bezdan, T.; Rashid, T.A. Energy Efficient Clustering in Wireless Sensor Networks by Opposition-Based Initialization Bat Algorithm. In Computer Networks and Inventive Communication Technologies; Lecture Notes on Data Engineering and Communications Technologies; Smys, S., Bestak, R., Palanisamy, R., Kotuliak, I., Eds.; Springer: Singapore, 2022; Volume 75. [Google Scholar] [CrossRef]
- Lakshmanna, K.; Subramani, N.; Alotaibi, Y.; Alghamdi, S.; Khalafand, O.I.; Nanda, A.K. Improved Metaheuristic-Driven Energy-Aware Cluster-Based Routing Scheme for IoT-Assisted Wireless Sensor Networks. Sustainability 2022, 14, 7712. [Google Scholar] [CrossRef]
- Mehrotra, S.; Sharan, A. Comparative Analysis of K-Means Algorithm and Particle Swarm Optimization for Search Result Clustering. In Smart Trends in Computing and Communications; Springer: Singapore, 2020; pp. 109–114. [Google Scholar] [CrossRef]






| Simulation Parameter | Value |
|---|---|
| Simulator | Network Simulator-2 |
| Number of nodes | 100 |
| Simulation time | 200 s |
| Mac Protocol | IEEE 802.11 |
| Simulation area | 1800 × 1800 m2 |
| Mobility model | accidental waypoint model |
| Radio range | 100 m |
| Data rate | 24 Mbps |
| Antenna | Omnidirectional antenna |
| Traffic type | Multicast constant bit ratio |
| Packet size | 512 bytes |
| Node speed | 10–35 m/s |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nagaraj, S.; Kathole, A.B.; Arya, L.; Tyagi, N.; Goyal, S.B.; Rajawat, A.S.; Raboaca, M.S.; Mihaltan, T.C.; Verma, C.; Suciu, G. Improved Secure Encryption with Energy Optimization Using Random Permutation Pseudo Algorithm Based on Internet of Thing in Wireless Sensor Networks. Energies 2023, 16, 8. https://doi.org/10.3390/en16010008
Nagaraj S, Kathole AB, Arya L, Tyagi N, Goyal SB, Rajawat AS, Raboaca MS, Mihaltan TC, Verma C, Suciu G. Improved Secure Encryption with Energy Optimization Using Random Permutation Pseudo Algorithm Based on Internet of Thing in Wireless Sensor Networks. Energies. 2023; 16(1):8. https://doi.org/10.3390/en16010008
Chicago/Turabian StyleNagaraj, S., Atul B. Kathole, Leena Arya, Neha Tyagi, S. B. Goyal, Anand Singh Rajawat, Maria Simona Raboaca, Traian Candin Mihaltan, Chaman Verma, and George Suciu. 2023. "Improved Secure Encryption with Energy Optimization Using Random Permutation Pseudo Algorithm Based on Internet of Thing in Wireless Sensor Networks" Energies 16, no. 1: 8. https://doi.org/10.3390/en16010008
APA StyleNagaraj, S., Kathole, A. B., Arya, L., Tyagi, N., Goyal, S. B., Rajawat, A. S., Raboaca, M. S., Mihaltan, T. C., Verma, C., & Suciu, G. (2023). Improved Secure Encryption with Energy Optimization Using Random Permutation Pseudo Algorithm Based on Internet of Thing in Wireless Sensor Networks. Energies, 16(1), 8. https://doi.org/10.3390/en16010008











