A Review of Denial of Service Attack and Mitigation in the Smart Grid Using Reinforcement Learning
Abstract
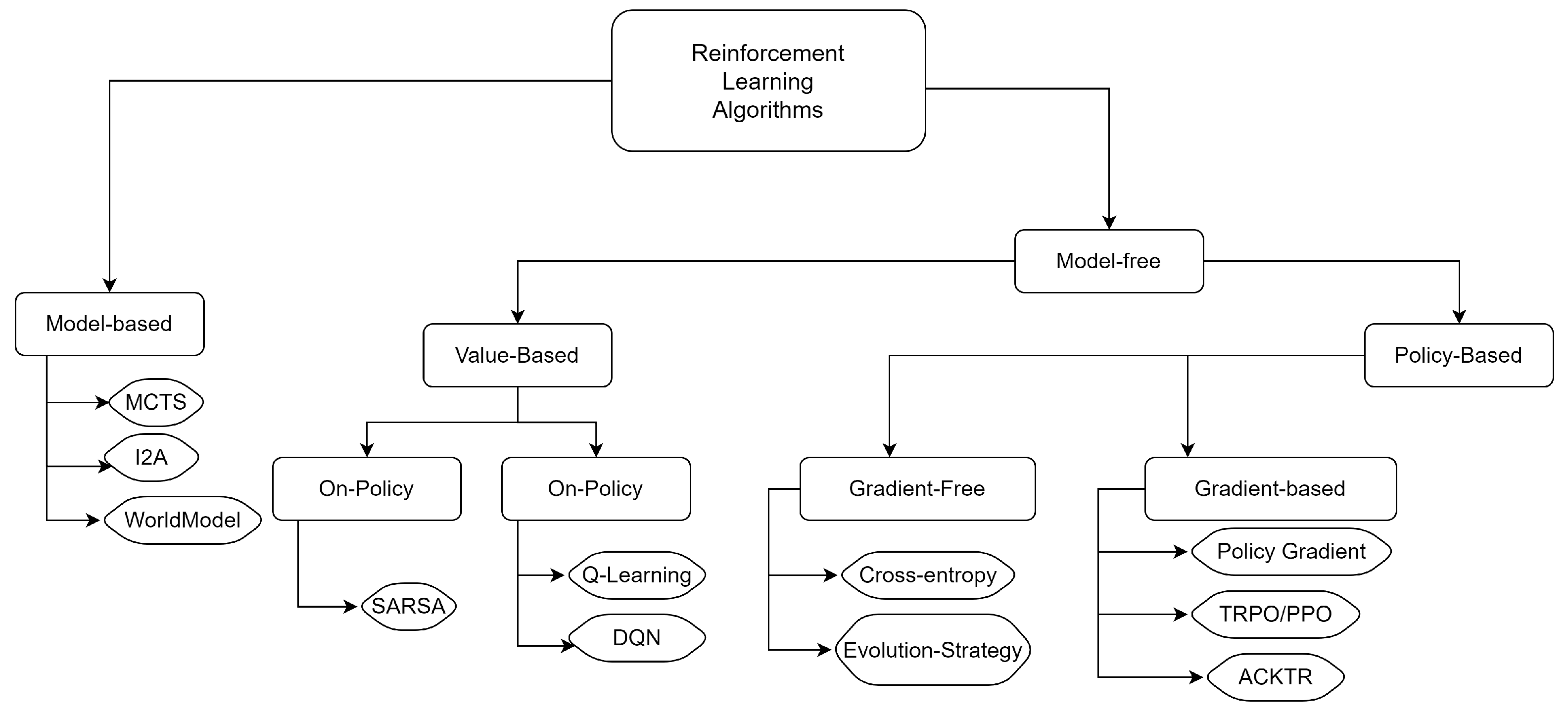
1. Introduction
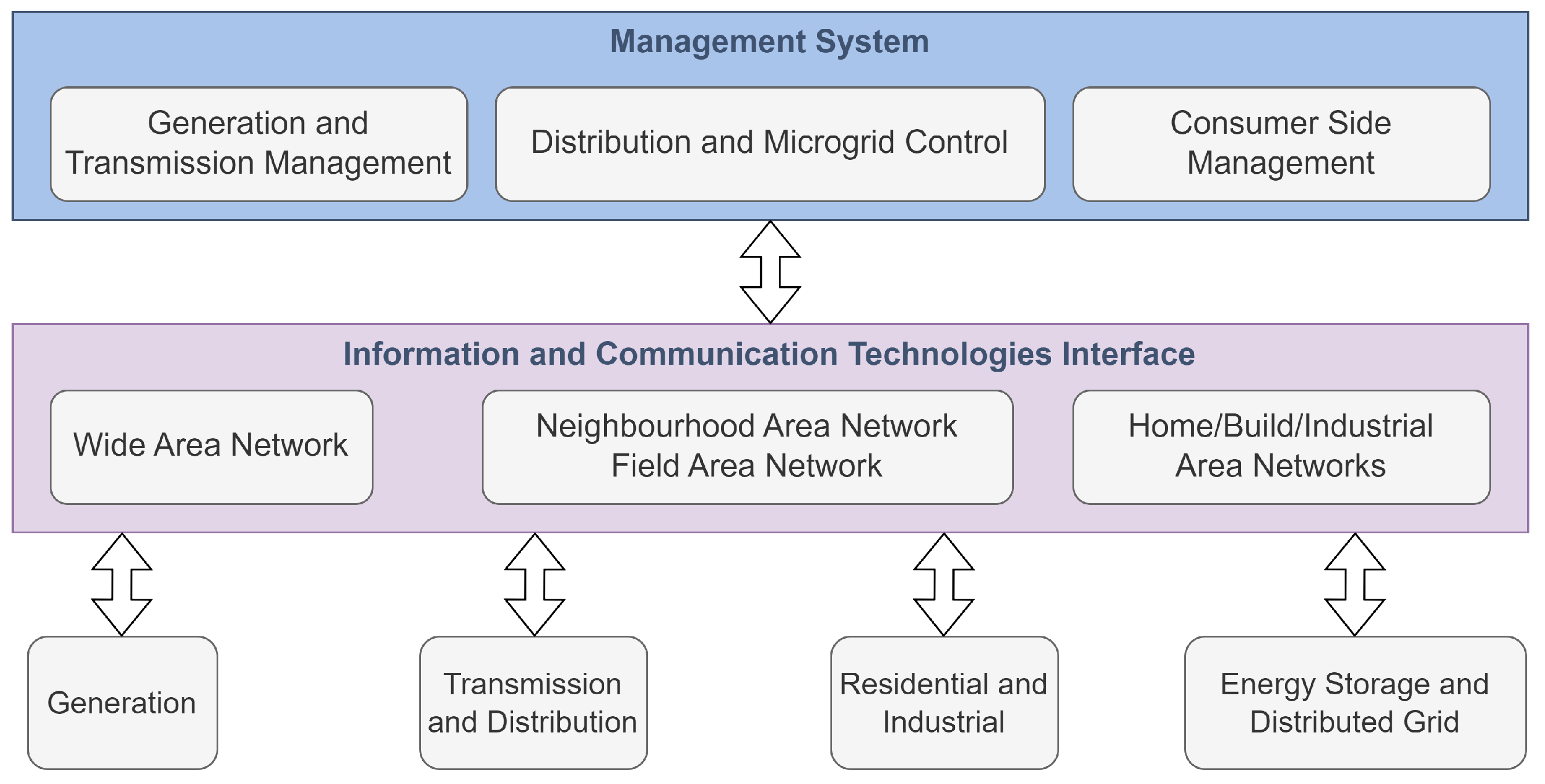
- The Advanced Metering Infrastructure provides smart meters with bidirectional communication capabilities and data transfer with the control centre. It is a common target of DoS attacks.
- The Distribution Management System monitors, protects, controls and optimizes the assets of the distribution grid, and might be affected by load frequency disturbance caused by a DoS attack.
- Demand Side Management might be affected by DoS attacks that target the devices in charge of maintaining the load and supply balance from the demand side.
- At last, the Energy Management System is in charge of keeping the balance between the energy supply and the demand. A Distributed DoS (DDoS) targeting the Energy Management System will prevent it from controlling the power ratio between consumption and generation, causing problems such as voltage drop/rise.
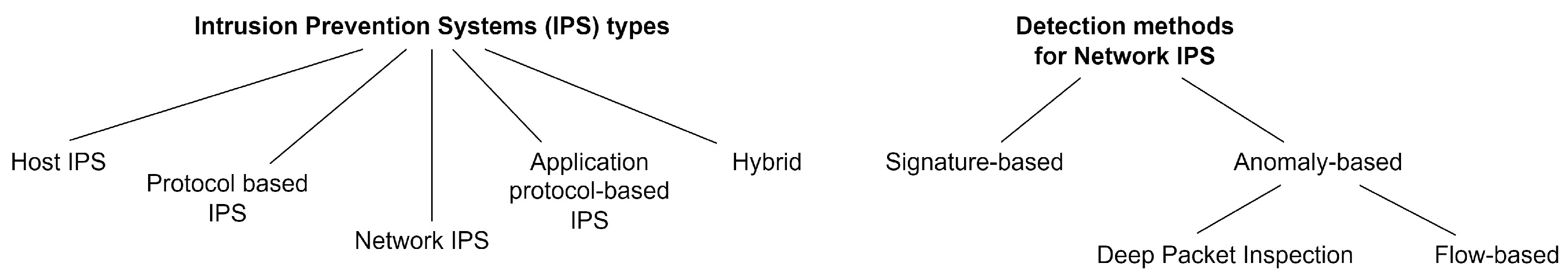
- Signature-based IPSs, which use signatures and patterns of well-known DoS attacks to compare current network traffic with its expected pattern, raising an alarm when the current behaviour does not match the learned signature or rule. Although these methods are easy to implement, they fail to detect novel or unknown attacks [11].
- Anomaly-based IPSs, which learn a pattern of the normal behaviour of a network by means of statistical properties, and raise an alarm when the current behaviour does not match the expected pattern, allowing the IPS to detect unknown attacks [12]. However, anomaly-based IPSs are more costly to train and tune, and it is more difficult to obtain the exact root cause of the detected anomaly. The pattern of legitimate behaviour may be learned with a variety of techniques: traditionally, pattern-based intrusion detection has been performed by analysing the contents of each individual network packet to find anomalies that deviate from the learned pattern, using a set of techniques named Deep Packet Inspection. However, inspecting each packet is not efficient in large networks, and is even impossible at network speeds of Gigabits per second. The main alternative to Deep Packet Inspection is flow-based anomaly detection, where the communication patterns (in Netflow [13] or IPFIX [14] format) are studied, instead of the content of each individual packet [15].
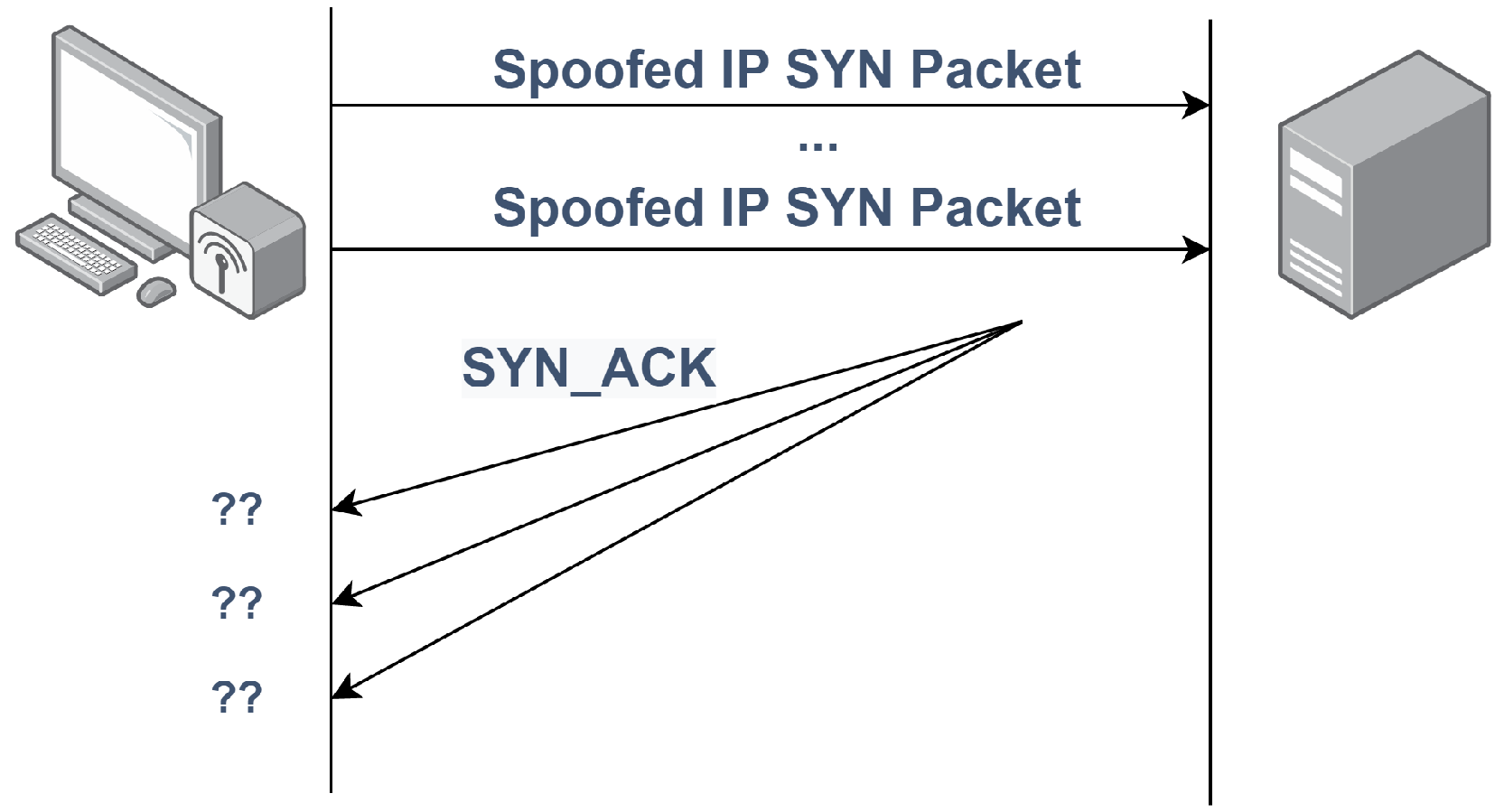
- Flooding attacks, which overwhelm the communication network with packets to disturb legitimate communication.
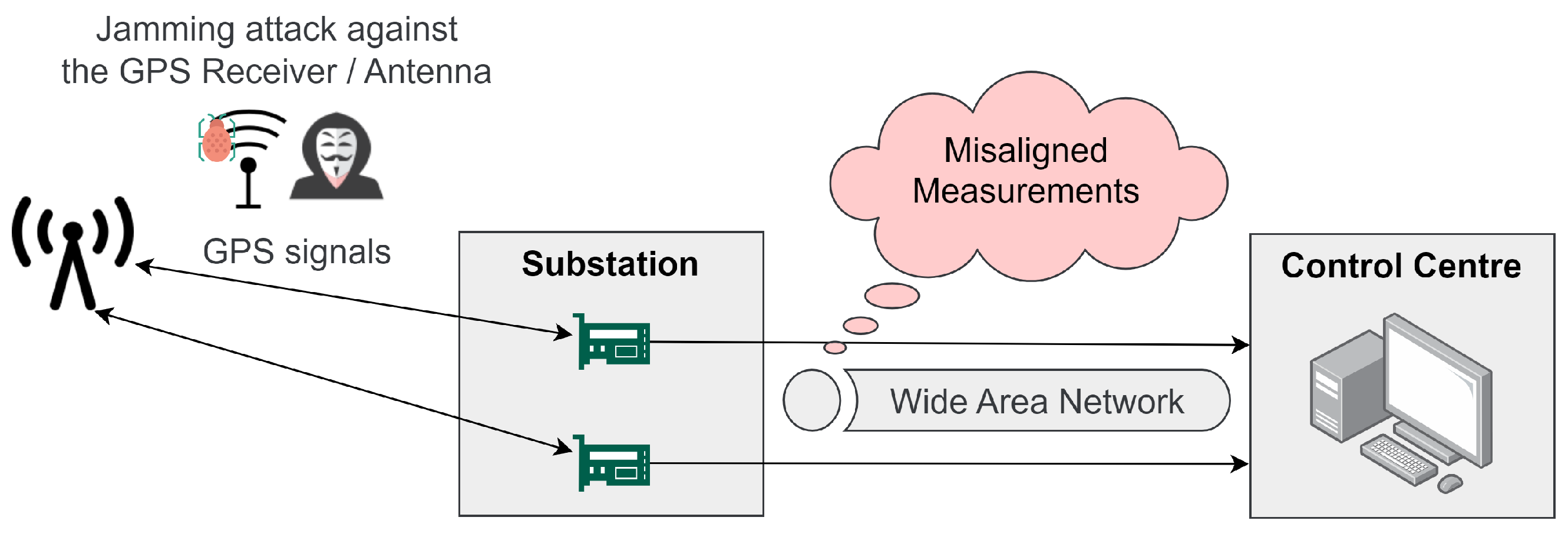
- Jamming attacks, which interfere with the wireless signals at the physical layer to deny or delay the communication between smart grid devices.
- De-synchronization attacks, which target smart grid systems which rely on exact timing and synchronized measurements.
- Amplification attacks, which take advantage of networking protocols to overwhelm the communication network or exhaust device resources.
- False Data Injection attacks, which alter the packet content with the aim of disrupting smart grid services.
2. DoS Attacks in the Smart Grid
2.1. Flooding Attacks
2.2. Jamming Attacks
2.3. De-Synchronization Attacks
2.4. Amplification Attacks
- Distributed: usually, multiple servers using the UDP protocol are used to launch the attack.
- Camouflage: attackers spoof their IP addresses into the addresses of the victim. Victims receive a lot of traffic from amplifiers (the server that is abused by the attackers).
- Reflexivity: the traffic is never received directly from the attacker, but indirectly by the amplifier’s reflection.
- Amplification: the traffic reflected from the amplifier servers to the victims is much larger than the traffic sent to amplifiers from the attackers.
2.5. False Data Injection Attacks
3. Detection and Mitigation Mechanisms against Cyberattacks with RL
| RL Algorithm | Attack Type | Learning Goal | Strengths (+) and Limitations (−) |
|---|---|---|---|
| DQDN [52] | False Data Injection | Optimize defence strategy by quantifying the observation space with a sliding window | (+) Improves previous approaches in several IEEE bus systems (−) Only considers the physical layer (−) Time complexity grows exponentially with the number of devices (−) Non-realistic scenario, lack of advanced simulation or complex Smart Grid |
| DPDG [53] | DDoS | Monitor the network load to drop excess traffic to maximize the available bandwidth in the network | (+) Efficient monitoring scheme (−) Not focused on Smart Grid |
| DPDG [55] | False Data Injection | Find the optimal re-close transmission time after an attack | (+) The implemented attacks affect the asynchronous behaviour of the generator rotors (−) Only acts when the attack already happened (−) Simulated attack scenario with dynamic equations of the power system (−) Only considers the physical layer |
| Actor-critic NN [51] | Multiple | Learn the optimal strategy to timely defend a CPS by observing the state of the CPS at the cyber and physical level | (+) Real-time operation (+) Learns optimal defence and worst attack policies (−) Non-realistic scenario, lack of advanced simulation or complex Smart Grid (−) Only considers the physical layer |
| POMDP [54] | DoS FDI/Jamming topology attacks | Lessen its detection delay and false alarm rate by choosing the optimal actions | (+) Model-free algorithm that is able to work online in real time (−) Only considers two actions, continue operation or stop the system (−) Fails to mitigate the attack without stopping the system (−) Their approach does not distinguish between cyberattacks and other kinds of anomalies |
| Q-learning [56] | Multiple | Learn the optimal actions to mitigate different cyberattacks in ZigBee home area networks | (+) Six different attacks evaluated (+) Combines detection and prevention using different ML-based techniques (−) Focused on IEEE 802.15.4 (−) Requires deep packet inspection |
| Inverse RL [57] | Back-off attack | Novel general defence mechanism based on Generative Adversarial Imitation Learning | (+) Good performance against back-off attacks (+) Evaluated in both offline and online settings (+) Combines detection and prevention (−) Evaluated only against back-off attack (−) Potentially high computational complexity on online settings |
| DQN [58] | Jamming | Learn the recursive characteristics of the spectrum waterfall, optimizing the discretized transmission frequency | (+) Considers SINR-based transmission rate and the cost for frequency switching (+) Reduced average detection time and false alarm rate (−) Not focused on Smart Grid |
| Q-learning [41] | DoS amplification | Learn the optimal actions to eliminate network congestion in a DNS server after an amplification attack | (+) Realistic DNS amplification attack (−) The agent only learns to either transmit or drop all the traffic in a specified time window (−) Not focused on Smart Grid |
| POMDP [50] | FDI | Maintain optimal power flow | (+) Enhancing the grid resilience with MLE (−) Only considers the physical layer |
4. Conclusions and Prospects for Future Research
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| CPS | Cyber–Physical System |
| DDPG | Deep Deterministic Policy Gradient |
| DDoS | Distributed Denial of Service |
| DNS | Domain Name System |
| DoS | Denial of Service |
| DQN | Deep Q Learning |
| FDI | False Data Injection |
| GPS | Global Positioning System |
| IPS | Intrusion Prevention System |
| NIDS | Network Intrusion Detection Systems |
| NTP | Network Time Protocol |
| POMDP | Partially observable Markov decision process |
| PTP | Precision Time Protocol |
| RL | Reinforcement Learning |
| SCADA | Supervisory Control and Data Acquisition |
| SDN | Software Defined Networks |
| SNMP | Simple Network Management Protocol |
References
- Pham, L.N.H. Exploring Cyber-Physical Energy and Power System: Concepts, Applications, Challenges, and Simulation Approaches. Energies 2023, 16, 42. [Google Scholar] [CrossRef]
- Fang, X.; Misra, S.; Xue, G.; Yang, D. Smart Grid—The New and Improved Power Grid: A Survey. IEEE Commun. Surv. Tutor. 2012, 14, 944–980. [Google Scholar] [CrossRef]
- Radoglou-Grammatikis, P.I.; Sarigiannidis, P.G. Securing the Smart Grid: A Comprehensive Compilation of Intrusion Detection and Prevention Systems. IEEE Access 2019, 7, 46595–46620. [Google Scholar] [CrossRef]
- Pillitteri, V.Y.; Brewer, T.L. Guidelines for Smart Grid Cybersecurity; NIST: Gaithersburg, MD, USA, 2014. [Google Scholar]
- Huseinović, A.; Mrdović, S.; Bicakci, K.; Uludag, S. A survey of denial-of-service attacks and solutions in the smart grid. IEEE Access 2020, 8, 177447–177470. [Google Scholar] [CrossRef]
- Cheng, Z.; Yue, D.; Hu, S.; Huang, C.; Dou, C.; Chen, L. Resilient load frequency control design: DoS attacks against additional control loop. Int. J. Electr. Power Energy Syst. 2020, 115, 105496. [Google Scholar] [CrossRef]
- Fekete, B.M.; Revenga, C.; Todd, M. The Global Risks Report 2018 13th Edition. Available online: http://www3.weforum.org/docs/WEF_GRR18_Report.pdf (accessed on 15 October 2022).
- Liu, J.; Xiao, Y.; Li, S.; Liang, W.; Chen, C.P. Cyber security and privacy issues in smart grids. IEEE Commun. Surv. Tutor. 2012, 14, 981–997. [Google Scholar] [CrossRef]
- Goudarzi, A.; Ghayoor, F.; Waseem, M.; Fahad, S.; Traore, I. A Survey on IoT-Enabled Smart Grids: Emerging, Applications, Challenges, and Outlook. Energies 2022, 15, 6984. [Google Scholar] [CrossRef]
- Fares, A.A.Y.R.; de Caldas Filho, F.L.; Giozza, W.F.; Canedo, E.D.; Lopes de Mendonça, F.L.; Amvame Nze, G.D. DoS Attack Prevention on IPS SDN Networks. In Proceedings of the 2019 Workshop on Communication Networks and Power Systems (WCNPS), Brasilia, Brazil, 3–4 October 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Raja, D.J.S.; Sriranjani, R.; Parvathy, A.; Hemavathi, N. A Review on Distributed Denial of Service Attack in Smart Grid. In Proceedings of the IEEE 2022 7th International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 2–24 June 2022; pp. 812–819. [Google Scholar]
- Berthier, R.; Sanders, W.H.; Khurana, H. Intrusion Detection for Advanced Metering Infrastructures: Requirements and Architectural Directions. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 350–355. [Google Scholar] [CrossRef]
- Cisco, I. NetFlow Configuration Guide Release 12.4; Cisco Documentation; Cisco Systems: San Jose, CA, USA, 2007. [Google Scholar]
- Quittek, J.; Zseby, T.; Claise, B.; Zander, S. Requirements for IP Flow Information Export (IPFIX); RFC Editor, October 2004. Available online: https://www.rfc-editor.org/info/rfc3917 (accessed on 15 October 2022).
- Sperotto, A.; Schaffrath, G.; Sadre, R.; Morariu, C.; Pras, A.; Stiller, B. An overview of IP flow-based intrusion detection. IEEE Commun. Surv. Tutor. 2010, 12, 343–356. [Google Scholar] [CrossRef]
- Kaelbling, L.P.; Littman, M.L.; Moore, A.W. Reinforcement learning: A survey. J. Artif. Intell. Res. 1996, 4, 237–285. [Google Scholar] [CrossRef]
- Asri, S.; Pranggono, B. Impact of distributed denial-of-service attack on advanced metering infrastructure. Wirel. Pers. Commun. 2015, 83, 2211–2223. [Google Scholar] [CrossRef]
- Groat, S.; Dunlop, M.; Urbanksi, W.; Marchany, R.; Tront, J. Using an IPv6 moving target defense to protect the Smart Grid. In Proceedings of the 2012 IEEE PES Innovative Smart Grid Technologies (ISGT), Washington, DC, USA, 16–20 January 2012; pp. 1–7. [Google Scholar] [CrossRef]
- Choi, K.; Chen, X.; Li, S.; Kim, M.; Chae, K.; Na, J. Intrusion Detection of NSM Based DoS Attacks Using Data Mining in Smart Grid. Energies 2012, 5, 4091–4109. [Google Scholar] [CrossRef]
- Jin, D.; Nicol, D.M.; Yan, G. An event buffer flooding attack in DNP3 controlled SCADA systems. In Proceedings of the 2011 Winter Simulation Conference (WSC), Phoenix, AZ, USA, 11–14 December 2011; pp. 2614–2626. [Google Scholar] [CrossRef]
- Zhang, F.; Mahler, M.; Li, Q. Flooding attacks against secure time-critical communications in the power grid. In Proceedings of the 2017 IEEE International Conference on Smart Grid Communications (SmartGridComm), Dresden, Germany, 23–27 October 2017; pp. 449–454. [Google Scholar] [CrossRef]
- Li, Q.; Ross, C.; Yang, J.; Di, J.; Balda, J.C.; Mantooth, H.A. The effects of flooding attacks on time-critical communications in the smart grid. In Proceedings of the 2015 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 18–20 February 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Pelechrinis, K.; Iliofotou, M.; Krishnamurthy, S.V. Denial of Service Attacks in Wireless Networks: The Case of Jammers. IEEE Commun. Surv. Tutor. 2011, 13, 245–257. [Google Scholar] [CrossRef]
- Temple, W.G.; Chen, B.; Tippenhauer, N.O. Delay makes a difference: Smart grid resilience under remote meter disconnect attack. In Proceedings of the 2013 IEEE International Conference on Smart Grid Communications (SmartGridComm), Vancouver, BC, Canada, 21–24 October 2013; pp. 462–467. [Google Scholar] [CrossRef]
- Li, H.; Lai, L.; Qiu, R.C. A denial-of-service jamming game for remote state monitoring in smart grid. In Proceedings of the 2011 45th Annual Conference on Information Sciences and Systems, Baltimore, MD, USA, 23–25 March 2011; pp. 1–6. [Google Scholar] [CrossRef]
- Chatfield, B.; Haddad, R.J.; Chen, L. Low-Computational Complexity Intrusion Detection System for Jamming Attacks in Smart Grids. In Proceedings of the 2018 International Conference on Computing, Networking and Communications (ICNC), Maui, HI, USA, 5–8 March 2018; pp. 367–371. [Google Scholar] [CrossRef]
- Zhang, Z.; Gong, S.; Dimitrovski, A.D.; Li, H. Time Synchronization Attack in Smart Grid: Impact and Analysis. IEEE Trans. Smart Grid 2013, 4, 87–98. [Google Scholar] [CrossRef]
- Gaderer, G.; Treytl, A.; Sauter, T. Security aspects for IEEE 1588 based clock synchronization protocols. In Proceedings of the 2006 IEEE International Workshop on Factory Communication Systems, Turin, Italy, 28–30 June 2006; pp. 247–250. [Google Scholar] [CrossRef]
- Moussa, B.; Debbabi, M.; Assi, C. A Detection and Mitigation Model for PTP Delay Attack in an IEC 61850 Substation. IEEE Trans. Smart Grid 2018, 9, 3954–3965. [Google Scholar] [CrossRef]
- Yang, Y.; McLaughlin, K.; Sezer, S.; Littler, T.; Pranggono, B.; Brogan, P.; Wang, H. Intrusion detection system for network security in synchrophasor systems. In Proceedings of the IET International Conference on Information and Communications Technologies, Beijing, China, 27–29 April 2013. [Google Scholar]
- Vuković, O.; Dán, G. Security of Fully Distributed Power System State Estimation: Detection and Mitigation of Data Integrity Attacks. IEEE J. Sel. Areas Commun. 2014, 32, 1500–1508. [Google Scholar] [CrossRef]
- Chen, P.Y.; Yang, S.; McCann, J.A.; Lin, J.; Yang, X. Detection of false data injection attacks in smart-grid systems. IEEE Commun. Mag. 2015, 53, 206–213. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, J.; Chen, B. Detecting False Data Injection Attacks in Smart Grids: A Semi-Supervised Deep Learning Approach. IEEE Trans. Smart Grid 2021, 12, 623–634. [Google Scholar] [CrossRef]
- Bogdanoski, M.; Suminoski, T.; Risteski, A. Analysis of the SYN flood DoS attack. Int. J. Comput. Netw. Inf. Secur. 2013, 5, 1–11. [Google Scholar] [CrossRef]
- Gupta, N.; Jain, A.; Saini, P.; Gupta, V. DDoS attack algorithm using ICMP flood. In Proceedings of the IEEE 2016 3rd International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 16–18 March 2016; pp. 4082–4084. [Google Scholar]
- Huseinovic, A.; Mrdovic, S.; Bicakci, K.; Uludag, S. A Taxonomy of the Emerging Denial-of-Service Attacks in the Smart Grid and Countermeasures. In Proceedings of the 2018 26th Telecommunications Forum (TELFOR), Belgrade, Serbia, 20–21 November 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Eidson, J.C.; Fischer, M.; White, J. IEEE-1588 Standard for a precision clock synchronization protocol for networked measurement and control systems. In Proceedings of the 34th Annual Precise Time and Time Interval Systems and Applications Meeting, Reston, VA, USA, 3–5 December 2002; pp. 243–254. [Google Scholar]
- Fan, Y.; Zhang, Z.; Trinkle, M.; Dimitrovski, A.D.; Song, J.B.; Li, H. A Cross-Layer Defense Mechanism Against GPS Spoofing Attacks on PMUs in Smart Grids. IEEE Trans. Smart Grid 2015, 6, 2659–2668. [Google Scholar] [CrossRef]
- Baumgartner, B.; Riesch, C.; Schenk, W. The impact of gps vulnerabilities on the electric power grid. In Proceedings of the XX IMEKO TC–4 International Symposium on Research on Electrical and Electronic Measurement for the Economic Upturn, Benevento, Italy, 15–17 September 2014; pp. 183–188. [Google Scholar]
- Anagnostopoulos, M. Amplification DoS Attacks. In Encyclopedia of Cryptography, Security and Privacy; Jajodia, S., Samarati, P., Yung, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2019; pp. 1–3. [Google Scholar] [CrossRef]
- Zhang, Y.; Cheng, Y. An Amplification DDoS Attack Defence Mechanism using Reinforcement Learning. In Proceedings of the 2019 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Leicester, UK, 19–23 August 2019; pp. 634–639. [Google Scholar] [CrossRef]
- Anagnostopoulos, M.; Kambourakis, G.; Kopanos, P.; Louloudakis, G.; Gritzalis, S. DNS amplification attack revisited. Comput. Secur. 2013, 39, 475–485. [Google Scholar] [CrossRef]
- Gondim, J.J.; de Oliveira Albuquerque, R.; Orozco, A.L.S. Mirror saturation in amplified reflection Distributed Denial of Service: A case of study using SNMP, SSDP, NTP and DNS protocols. Future Gener. Comput. Syst. 2020, 108, 68–81. [Google Scholar] [CrossRef]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 Ukraine Blackout: Implications for False Data Injection Attacks. IEEE Trans. Power Syst. 2017, 32, 3317–3318. [Google Scholar] [CrossRef]
- Rahman, M.A.; Mohsenian-Rad, H. False data injection attacks with incomplete information against smart power grids. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; pp. 3153–3158. [Google Scholar] [CrossRef]
- Wan, Z.; Li, H.; He, H.; Prokhorov, D. Model-free real-time EV charging scheduling based on deep reinforcement learning. IEEE Trans. Smart Grid 2018, 10, 5246–5257. [Google Scholar] [CrossRef]
- Wan, Z.; Jiang, C.; Fahad, M.; Ni, Z.; Guo, Y.; He, H. Robot-assisted pedestrian regulation based on deep reinforcement learning. IEEE Trans. Cybern. 2018, 50, 1669–1682. [Google Scholar] [CrossRef]
- Duan, J.; Yi, Z.; Shi, D.; Lin, C.; Lu, X.; Wang, Z. Reinforcement-learning-based optimal control of hybrid energy storage systems in hybrid AC–DC microgrids. IEEE Trans. Ind. Inform. 2019, 15, 5355–5364. [Google Scholar] [CrossRef]
- Yan, J.; He, H.; Zhong, X.; Tang, Y. Q-learning-based vulnerability analysis of smart grid against sequential topology attacks. IEEE Trans. Inf. Forensics Secur. 2016, 12, 200–210. [Google Scholar] [CrossRef]
- Chen, Y.; Huang, S.; Liu, F.; Wang, Z.; Sun, X. Evaluation of Reinforcement Learning-Based False Data Injection Attack to Automatic Voltage Control. IEEE Trans. Smart Grid 2019, 10, 2158–2169. [Google Scholar] [CrossRef]
- Feng, M.; Xu, H. Deep reinforecement learning based optimal defense for cyber-physical system in presence of unknown cyber-attack. In Proceedings of the 2017 IEEE Symposium Series on Computational Intelligence (SSCI), Honolulu, HI, USA, 27 November–1 December 2017; pp. 1–8. [Google Scholar] [CrossRef]
- An, D.; Yang, Q.; Liu, W.; Zhang, Y. Defending against Data Integrity Attacks in Smart Grid: A Deep Reinforcement Learning-Based Approach. IEEE Access 2019, 7, 110835–110845. [Google Scholar] [CrossRef]
- Liu, Y.; Dong, M.; Ota, K.; Li, J.; Wu, J. Deep Reinforcement Learning based Smart Mitigation of DDoS Flooding in Software-Defined Networks. In Proceedings of the 2018 IEEE 23rd International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Barcelona, Spain, 17–19 September 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Kurt, M.N.; Ogundijo, O.; Li, C.; Wang, X. Online Cyber-Attack Detection in Smart Grid: A Reinforcement Learning Approach. IEEE Trans. Smart Grid 2019, 10, 5174–5185. [Google Scholar] [CrossRef]
- Wei, F.; Wan, Z.; He, H. Cyber-Attack Recovery Strategy for Smart Grid Based on Deep Reinforcement Learning. IEEE Trans. Smart Grid 2020, 11, 2476–2486. [Google Scholar] [CrossRef]
- Jokar, P.; Leung, V.C.M. Intrusion Detection and Prevention for ZigBee-Based Home Area Networks in Smart Grids. IEEE Trans. Smart Grid 2018, 9, 1800–1811. [Google Scholar] [CrossRef]
- Parras, J.; Almodóvar, A.; Apellániz, P.A.; Zazo, S. Inverse Reinforcement Learning: A New Framework to Mitigate an Intelligent Backoff Attack. IEEE Internet Things J. 2022, 9, 24790–24799. [Google Scholar] [CrossRef]
- Liu, X.; Xu, Y.; Jia, L.; Wu, Q.; Anpalagan, A. Anti-jamming communications using spectrum waterfall: A deep reinforcement learning approach. IEEE Commun. Lett. 2018, 22, 998–1001. [Google Scholar] [CrossRef]
- Zhang, D.; Han, X.; Deng, C. Review on the research and practice of deep learning and reinforcement learning in smart grids. CSEE J. Power Energy Syst. 2018, 4, 362–370. [Google Scholar] [CrossRef]
| Attack | Target | Defence Strategy | Relevant Works |
|---|---|---|---|
| Flooding | ICMP UDP TCP | Network monitoring with NIDS Moving Target Defence Drop or filter traffic Anomaly Detection | [17] [18] [19] [20] [21] [22] |
| Jamming | Wireless Communication Layer | Signal Strength Measurements Monitoring of the Carrier Sensing Time Threshold based detection on the PDR Consistency Checks Network monitoring with NIDS Delayed Disconnect Intelligent selection of wireless channels Drop/filter traffic | [23] [24] [25] [26] [26] |
| De-synchronization | Global Positioning System (GPS) Network Time Protocol (NTP) | Monitor system stability Monitor the GPS carrier-to-noise ratio Use IEEE 1588-2008 precision time protocol Use stable atomic clocks | [27] [28] [29] |
| Amplification | UDP | Network monitoring with NIDS Filter or drop traffic Deep Packet Inspection Anomaly detection | [30] |
| False Data Injection | Unencrypted, unauthenticated communications | Deep Packet Inspection Anomaly Detection | [31] [32] [33] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ortega-Fernandez, I.; Liberati, F. A Review of Denial of Service Attack and Mitigation in the Smart Grid Using Reinforcement Learning. Energies 2023, 16, 635. https://doi.org/10.3390/en16020635
Ortega-Fernandez I, Liberati F. A Review of Denial of Service Attack and Mitigation in the Smart Grid Using Reinforcement Learning. Energies. 2023; 16(2):635. https://doi.org/10.3390/en16020635
Chicago/Turabian StyleOrtega-Fernandez, Ines, and Francesco Liberati. 2023. "A Review of Denial of Service Attack and Mitigation in the Smart Grid Using Reinforcement Learning" Energies 16, no. 2: 635. https://doi.org/10.3390/en16020635
APA StyleOrtega-Fernandez, I., & Liberati, F. (2023). A Review of Denial of Service Attack and Mitigation in the Smart Grid Using Reinforcement Learning. Energies, 16(2), 635. https://doi.org/10.3390/en16020635








