The Internet of Vehicles and Sustainability—Reflections on Environmental, Social, and Corporate Governance
Abstract
:1. Introduction
2. IoV and Related Concepts
| Definition | Year of Publication | Reference |
|---|---|---|
| “In the Internet of Vehicles, smart cars, equipped with both computational and communication resources, can provide intelligent vehicle control, traffic management and interactive applications.” (the definition given by application) | 2022 | [49] |
| “In general, the vast revolution in the IoT (a system that enables objects such as sensors and actuators to communicate and talk with each other without human intervention to achieve a common goal) helped to reduce traffic accidents by embedding some IoT objects in vehicles; and this created the IoV concept [50].” (the definition given through conceptual transfer of IoT) | 2020 | [47] |
| The IoV with big data technologies “creates new opportunities to diminish real-world problems such as traffic congestion, responsive and effective government processes for traffic monitoring, controlling, route management and urban planning etc.” | 2021 | [37] |
| “(…) an integration of three networks (…): an inter-vehicle network, an intra-vehicle network, and the vehicular mobile Internet.” “(…) Internet of Vehicles plays a significant role in the safe delivery of goods as it enables realtime tracking of shipments, warehouse-capacity optimization, predictive asset maintenance, route optimization, and improved last-mile delivery” (the definition given by application) | 2021 | Sukanya Mandal, IEEE member (India) quoted in [42] |
| “V2V communication enables vehicles to communicate directly with one another. This enables a vehicle to be alerted to the presence of other vehicles that are difficult for the vehicle to see” (the definition given by V2V technology) | 2020 | [43] (p. 17) |
| “system for sharing vehicle-to-vehicle (V2V) information among vehicles to prompt appropriate driving control” “infrastructure-to-vehicle (I2V) system is needed to communicate information among vehicles to prompt appropriate driving control” (the definition given by V2V and I2V technologies) | 2020 | [44] (p. 88) |
| V2V: “OBUs communicate between themselves” V2I: “OBUs communicate directly with RSUs” (the definition given by V2V and I2V technologies) | 2020 | [25] (p. 225). |
| “Vehicle-to-Everything (V2X) technologies constitute the most critical and important components for communication infrastructure (between the consumer-vehicle-infrastructure-management center) to provide smarter, safer and faster travel in addition to the efficient use of the resources.” (the definition given by V2X technology) | 2020 | [25] (p. 259) |
| “Vehicles exchange information with each other with the use of V2V communication and also access the network infrastructure through the Road Side Units (RSUs) or through the cellular network components e.g., eNodeBs (V2N communication).” (the definition given by V2X technology) | 2020 | [25] (p. 261). |
| Vehicle connection with other infrastructures such as buildings, lights, stations, etc., is called Vehicle to Infrastructure (V2I) connection, while connecting vehicles with other vehicle systems are called V2V connection. The combination of both connection types V2I and V2V is known as Vehicle to Everything (V2X) connection. | 2018 | [51] |
| “The Internet of things (IoT) is a global network connecting smart objects and enabling them to communicate with each other. Whenever those smart objects being connected over Internet are e xclusively vehicles, then IoT becomes Internet of Vehicles (IoV).” (the definition given through conceptual transfer of IoT) | 2018 | [46] |
| The definition given for specific purposes: “vehicles can broadcast information about their states to other vehicles (V2V), including speed, heading, and location, as well as the information related to the environment while adverse weather conditions or obstacles can be acquired from infrastructure (V2I).” “In vehicle-to-infrastructure (V2I) systems, the vehicles communicate with RSUs or cellular base stations at fixed positions. This allows the RSUs to communicate their location, weather conditions, traffic flow, etc. with vehicles to estimate their own position more accurately.” | 2018 | [26] |
| “The Social Internet of Vehicles (SIoV) is an example of a SIoT [SIoT stand for Social Internet of Things—added by this papers authors] where the objects are smart vehicles (mostly cars). The social connections can be made between vehicles, drivers and other users and between these two groups.” (the definition given through conceptual transfer of IoT) | 2015 | [48] |
| “Providing wireless connectivity to vehicles enables communication with internal and external environments, supporting vehicle-to-vehicle (V2V), vehicle-to-infrastructure (V2I), vehicle-to-sensor, and vehicle-to-Internet communications” (the definition given for specific purposes) | 2014 | [26,45] |
| “The Internet of Vehicles (IoV) is an integration of three networks: an inter-vehicle network, an intra-vehicle network, and vehicular mobile Internet. Based on this concept of three networks integrated into one, we define an Internet of Vehicles as a large-scale distributed system for wireless communication and information exchange between vehicle2X (X: vehicle, road, human and internet) according to agreed communication protocols and data interaction standards (examples include the IEEE 802.11p WAVE standard, and potentially cellular technologies). It is an integrated network for supporting intelligent traffic management, intelligent dynamic information service, and intelligent vehicle control, representing a typical application of Internet of Things (IoT) technology in intelligent transportation system (ITS).” | 2014 | [33] |
3. ESG in IoV Design and Application
3.1. IoV: An Environmental Perspective
- Devices and software environments (including IoV network environments, V2X environments, etc.), namely systems involving IoV technology. In general, that type of “environment” can be summed up as a software and/or hardware environment [52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71] (in [65], a network environment is understood by its parameters as a quantity of vehicles, load, speed, etc.). An interesting application of IoV control methods in the context of device and software environments is given in [72], where the authors developed a smart terminal-box for unmanned earthwork machinery (including bulldozers, graders, and rollers) which works in the tough environments of varied weather. Additionally, it may be underlined here that the authors of [73] mentioned blockchain to be envisioned as a type of enforcement applied to ensure trustworthiness in diverse IoT environments (and consequently in IoV environments, which is a subject matter of [74]).
- Internal and external environments of an organization, e.g., the manufacturing environment, the supplier’s competitive environment, the sales competition environment, and the customer usage environment as mentioned in [59].
- An environment as acreage was given in [75].
- A small environment, as in the concept in biology, was applied to the IoV by [90].
- An environment consisting of vehicles, tasks, wireless channels, and mobile edge computing servers was mentioned in [91].
- Various types of environments were mentioned in [92], without any unification.
3.2. IoV: A Social Perspective
3.3. IoV: A Governance Perspective
- Data security and information privacy;
- Leakage of personal data and personal privacy;
- Compliance with the GDPR;
- Serious security breaches related to the broadcasting of false alarms;
- Blockchain-based IoV network architecture aims to protect connected vehicles from attacks and is based on a sophisticated secure IoT network [158].
- Policy hidden attribute-based encryption with dynamic service (PH-ABE-DS) and edge-assisted policy hidden attribute-based encryption with dynamic service (EA-PH-ABE-DS) are two solutions dealing with internal and external security issues that simultaneously offer an appropriate level of usability and enable full policy hiding [152].
- Blockchain solutions can support high privacy levels, preserve full data disclosure, and facilitate lower costs for owned redundant storage and related procedures [156].
- False alarm detection methods, e.g., outlier detection, intrusion detection, the detection of security attacks, inconsistency detection applied to communicating, and messages misbehavior detection are relevant [28,153] (these methods were developed through the application of a hidden Markov model-based prediction framework based on a probabilistic model).
- PPIoV (i.e., Privacy Preserving-based framework for IoV-fog environment) is a federated learning and blockchain-based method aimed at ensuring the short information processing times which are necessary for the IoV environment, as well as ensuring trust [155].
- (TITLE-ABS-KEY (iov) AND TITLE-ABS-KEY (governance)); four documents; 2019–2022;
- (TITLE-ABS-KEY (iov) AND TITLE-ABS-KEY (data) AND TITLE-ABS-KEY (privacy)); 230 documents; 2013–2023, where 91% of publications is dated from 2019 to 2023;
- (TITLE-ABS-KEY (iov) AND TITLE-ABS-KEY (data) AND TITLE-ABS-KEY (risk)); 83 documents (2007–2022), where 78% of publications was dated from 2019 to 2022.
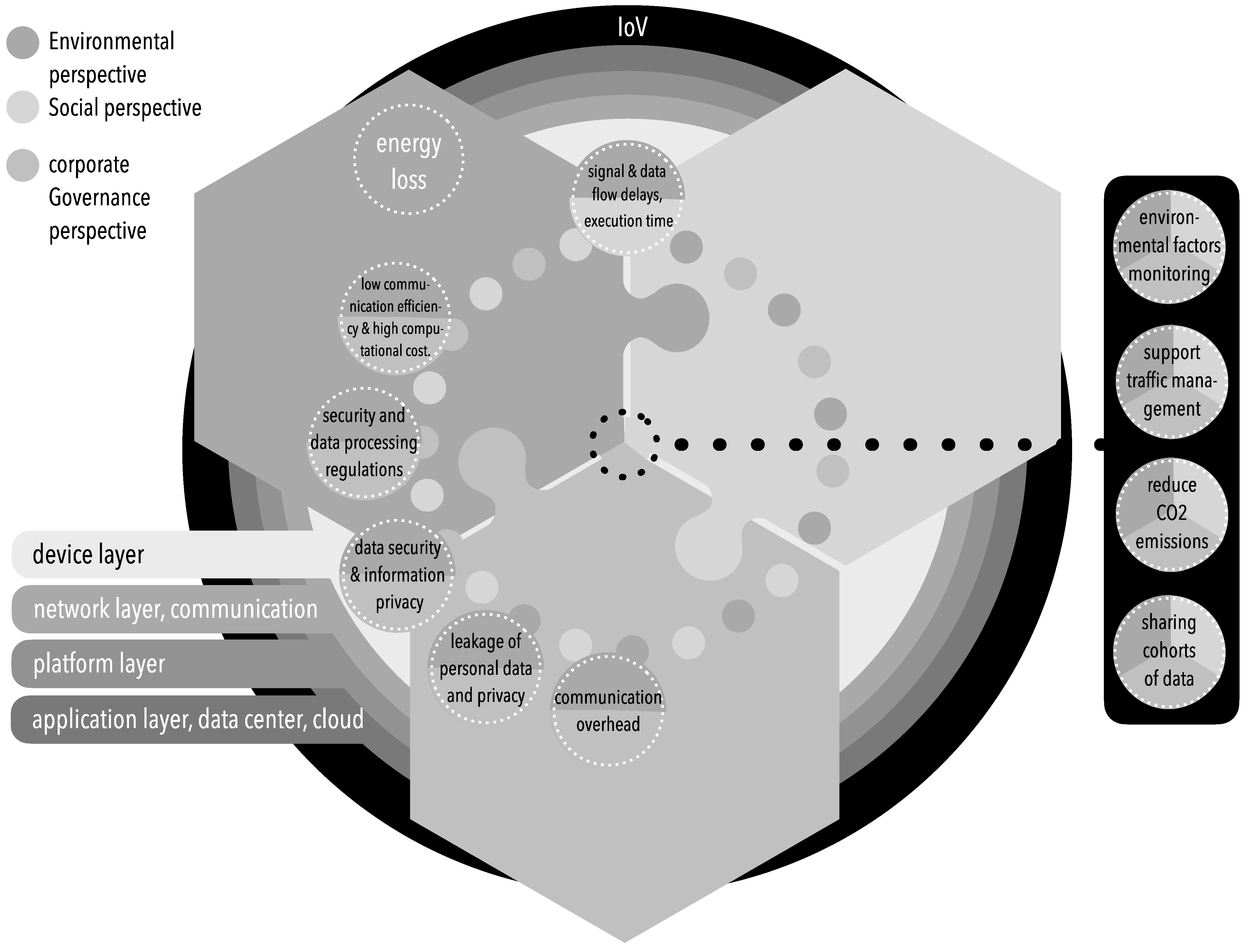
4. Discussion
- The elimination of energy losses;
- Data which can be used for environmental monitoring (weather, health, security, etc.);
- Routing protocols to maintain efficient energy consumption;
- A reasonable amount of renewable energy for IoV issues;
- The IoV next to hybrid electric vehicles as an input to energy problems;
- Vehicles, thanks to IoV technology, acting as sensing points whose measurement results ensure more services, safety, and efficiency for transportation systems;
- IoV sensors for environmental conditions, which can meet the needs of smart cities;
- Systems supporting superior traffic management and CO2 emissions reduction.
- Data security and information privacy;
- Data leakage;
- Personal privacy and compliance with the GDPR;
- Serious security breaches related to the broadcasting of false alarms;
- Limited effectiveness of IoV systems related to poorly managed private data sharing in the cloud;
- A variety of potential attacks that can affect IoV networks and infrastructure and target availability, authentication, data integrity, confidentiality, and routing.
5. Conclusions and Future Research Directions
- Environmental factors monitoring;
- Supporting traffic management;
- Reducing CO2 emissions;
- Sharing cohorts of data.
- Signal and data flow delays and execution time;
- Energy loss.
- Communication efficiency, computational cost, and expenditures;
- Data security and information privacy;
- Communication overhead;
- Security and data processing regulations;
- Energy loss.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Balasubramaniam, A.; Paul, A.; Hong, W.-H.; Seo, H.; Kim, J.H. Comparative Analysis of Intelligent Transportation Systems for Sustainable Environment in Smart Cities. Sustainability 2017, 9, 1120. [Google Scholar] [CrossRef] [Green Version]
- Balasubramaniam, A.; Paul, A. Comparative study of sustainable transportation systems: A futuristic approach. In Proceedings of the ICSNS 2018—IEEE International Conference on Soft-Computing and Network Security 2018, Coimbatore, India, 14–16 February 2018; Curran Associates: Ney York, NY, USA, 2018. [Google Scholar] [CrossRef]
- Aamir, M.; Masroor, S.; Ali, Z.A.; Ting, B.T. Sustainable Framework for Smart Transportation System: A Case Study of Karachi. Wirel. Pers. Commun. 2019, 106, 27–40. [Google Scholar] [CrossRef]
- Hussain, H.I.; Kamarudin, F.; Mohd-Sanusi, Z.; Shuhidan, S.M.; Saad Al-Dhubaibi, A.A.; Ahmad Razimi, M.S. Governance in the internet of vehicles (IoV) context: Examination of information privacy, transport anxiety, intention, and usage. J. Adv. Transp. 2021, 2021, 5563260. [Google Scholar] [CrossRef]
- Zhao, L.; Jia, Y. Intelligent transportation system for sustainable environment in smart cities. Int. J. Electr. Eng. Educ. 2021, 1–9. [Google Scholar] [CrossRef]
- Eccles, N.; Viviers, S. The Origins and Meanings of Names Describing Investment Practices that Integrate a Consideration of ESG Issues in the Academic Literature. J. Bus. Ethics 2011, 104, 389–402. [Google Scholar] [CrossRef]
- Nirino, N.; Santoro, G.; Miglietta, N.; Quaglia, R. Corporate controversies and company’s financial performance: Exploring the moderating role of ESG practices. Technol. Forecast. Soc. Chang. 2021, 162, 120341. [Google Scholar] [CrossRef]
- Capelle-Blancard, G.; Petit, A. Every Little Helps? ESG News and Stock Market Reaction. J. Bus. Ethics 2019, 157, 543–565. [Google Scholar] [CrossRef]
- Daugaard, D. Emerging new themes in environmental, social and governance investing: A systematic literature review. Account. Financ. 2020, 60, 1501–1530. [Google Scholar] [CrossRef]
- Friede, G. Why don’t we see more action? A metasynthesis of the investor impediments to integrate environmental, social, and governance factors. Bus. Strategy Environ. 2019, 28, 1260–1282. [Google Scholar] [CrossRef]
- Cordeiro, J.J.; Profumo, G.; Tutore, I. Family ownership and stockholder reactions to environmental performance disclosure: A test of secondary agency relationships. Bus. Strategy Environ. 2021, 30, 2091–2107. [Google Scholar] [CrossRef]
- Mukandwal, P.S.; Cantor, D.E.; Grimm, C.M.; Elking, I.; Hofer, C. Do Firms Spend More on Suppliers That Have Environmental Expertise? An Empirical Study of U.S. Manufacturers’ Procurement Spend. J. Bus. Logist. 2020, 41, 129–148. [Google Scholar] [CrossRef]
- Fritz, M.M.C.; Ruel, S.; Kallmuenzer, A.; Harms, R. Sustainability management in supply chains: The role of familiness. Technol. Forecast. Soc. Chang. 2021, 173, 121078. [Google Scholar] [CrossRef]
- Brooks, C.; Oikonomou, I. The effects of environmental, social and governance disclosures and performance on firm value: A review of the literature in accounting and finance. Br. Account. Rev. 2018, 50, 1–15. [Google Scholar] [CrossRef]
- Grant, M.J.; Booth, A. A Typology of Reviews: An Analysis of 14 Review Types and Associated Methodologies. Health Inf. Libr. J. 2009, 26, 91–108. [Google Scholar] [CrossRef]
- Daudt, H.M.; van Mossel, C.; Scott, S.J. Enhancing the Scoping Study Methodology: A Large, Inter-Professional Team’s Experience with Arksey and O’Malley’s Framework. BMC Med. Res. Methodol. 2013, 13, 1–9. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Colquhoun, H.L.; Levac, D.; O’Brien, K.K.; Straus, S.; Tricco, A.C.; Perrier, L.; Kastner, M.; Moher, D. Scoping Reviews: Time for Clarity in Definition Methods, and Reporting. J. Clin. Epidemiol. 2014, 67, 1291–1294. [Google Scholar] [CrossRef] [PubMed]
- Zia, K.; Muhammad, A.; Khalid, A.; Din, A.; Ferscha, A. Towards Exploration of Social in Social Internet of Vehicles Using an Agent-Based Simulation. Complexity 2019, 2019, 8201396. [Google Scholar] [CrossRef]
- Talib, M.A.; Abbas, S.; Nasir, Q.; Mowakeh, M.F. Systematic literature review on Internet-of-Vehicles communication security. Int. J. Distrib. Sens. Netw. 2018, 14, 1550147718815054. [Google Scholar] [CrossRef] [Green Version]
- Atzori, L.; Floris, A.; Girau, R.; Nitti, M.; Pau, G. Towards the implementation of the Social Internet of Vehicles. Comput. Netw. 2018, 147, 132–145. [Google Scholar] [CrossRef]
- Yang, F.; Wang, S.; Li, J.; Liu, Z.; Sun, Q. An overview of Internet of Vehicles. China Commun. 2014, 11, 1–15. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. A Survey of Security Services, Attacks, and Applications for Vehicular Ad Hoc Networks (VANETs). Sensors 2019, 19, 3589. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Xu, X.; Wang, Y.; Wang, P. Review Article Comprehensive Review on Misbehavior Detection for Vehicular Ad Hoc Networks. J. Adv. Transp. 2022, 2022, 4725805. [Google Scholar] [CrossRef]
- Mejri, N.; Ben-Othman, J.; Hamdi, M. Survey on VANET security challenges and possible cryptographic solutions. Veh. Commun. 2014, 1, 53–66. [Google Scholar] [CrossRef]
- Mouftah, H.T.; Erol-Kantarci, M.; Sorour, S. (Eds.) Connected and Autonomous Vehicles in Smart Cities, 1st ed.; CRC Press: Boca Raton, FL, USA, 2020. [Google Scholar] [CrossRef]
- Kuutti, S.; Fallah, S.; Katsaros, K.; Dianati, M.; Mccullough, F.; Mouzakitis, A. A Survey of the State-of-the-Art Localization Techniques and Their Potentials for Autonomous Vehicle Applications. IEEE Internet Things J. 2018, 5, 829–846. [Google Scholar] [CrossRef]
- Minerva, R.; Biru, A.; Rotondi, D. Towards a Definition of the Internet of Things (IoT). IEEE Internet Initiat. 2015, 1, 1–86. [Google Scholar]
- Dua, A.; Kumar, N.; Bawa, S. A systematic review on routing protocols for Vehicular Ad Hoc Networks. Veh. Commun. 2014, 1, 33–52. [Google Scholar] [CrossRef]
- Liu, K.; Ng, J.K.Y.; Lee, V.C.S.; Son, S.H.; Stojmenovic, I. Cooperative data scheduling in hybrid vehicular ad hoc networks: VANET as a software defined network. IEEE/ACM Trans. Netw. 2016, 24, 1759–1773. [Google Scholar] [CrossRef]
- Chahal, M.; Harit, S.; Mishra, K.K.; Sangaiah, A.K.; Zheng, Z. A Survey on software-defined networking in vehicular ad hoc networks: Challenges, applications and use cases. Sustain. Cities Soc. 2017, 35, 830–840. [Google Scholar] [CrossRef]
- Wang, J.; Shao, Y.; Ge, Y.; Yu, R. A Survey of Vehicle to Everything (V2X) Testing. Sensors 2019, 19, 334. [Google Scholar] [CrossRef] [Green Version]
- 5G Americas. Cellular V2X Communications Towards 5G. March 2018. Available online: http://www.5gamericas.org/en/resources/white-papers/ (accessed on 12 June 2022).
- White Paper of Internet of Vehicles (IoV). Available online: http://mddb.apec.org/Documents/2014/TEL/TEL50-PLEN/14_tel50_plen_020.pdf (accessed on 4 June 2022).
- Kong, Q.; Lu, R.; Ma, M.; Bao, H. A privacy-preserving sensory data sharing scheme in Internet of Vehicles. Future Gener. Comput. Syst. 2019, 92, 644–655. [Google Scholar] [CrossRef]
- Sun, X.; Yu, F.R.; Zhang, P.; Xie, W.; Peng, X. A Survey on Secure Computation Based on Homomorphic Encryption in Vehicular Ad Hoc Networks. Sensors 2020, 20, 4253. [Google Scholar] [CrossRef] [PubMed]
- Langley, D.J.; van Doorn, J.; Ng, I.C.L.; Stieglitz, S.; Lazovik, A.; Boonstra, A. The Internet of Everything: Smart things and their impact on business models. J. Bus. Res. 2021, 122, 853–863. [Google Scholar] [CrossRef]
- Arooj, A.; Farooq, M.S.; Akram, A.; Iqbal, R.; Sharma, A.; Dhiman, G. Big Data Processing and Analysis in Internet of Vehicles: Architecture, Taxonomy, and Open Research Challenges. Arch. Comput. Methods Eng. 2022, 29, 793–829. [Google Scholar] [CrossRef]
- Lyamin, N.; Kleyko, D.; Delooz, Q.; Vinel, A. AI-Based Malicious Network Traffic Detection in VANETs. IEEE Netw. 2018, 32, 15–21. [Google Scholar] [CrossRef]
- Keshari, N.; Singh, D.; Maurya, A.K. A survey on Vehicular Fog Computing: Current state-of-the-art and future directions. Veh. Commun. 2022, 38, 100512. [Google Scholar] [CrossRef]
- Zhang, L. Key Management Scheme for Secure Channel Establishment in Fog Computing. IEEE Trans. Cloud Comput. 2021, 9, 1117–1128. [Google Scholar] [CrossRef]
- Mo, T.; Lau, K.-T.; Li, Y.; Poon, C.-k.; Wu, Y.; Chu, P.K.; Luo, Y. Commercialization of Electric Vehicles in Hong Kong. Energies 2022, 15, 942. [Google Scholar] [CrossRef]
- Garg, S.; Mehrotra, D.; Pandey, H.M.; Pandey, S. Accessible review of internet of vehicle models for intelligent transportation and research gaps for potential future directions. Peer-to-Peer Netw. Appl. 2021, 14, 978–1005. [Google Scholar] [CrossRef]
- Sakai, K. Japan perspective. In Smart Sensing for Traffic Monitoring; Ozaki, N., Ed.; The Institution of Engineering and Technology: Herts, UK, 2021. [Google Scholar]
- Ishikawa, H.; Yamauchi, Y.; Mizouchi, K. Vehicle detection at intersection by LIDAR system. In Smart Sensing for Traffic Monitoring; Ozaki, N., Ed.; The Institution of Engineering and Technology: Herts, UK, 2021. [Google Scholar]
- Lu, N.; Cheng, N.; Zhang, N.; Shen, X.; Mark, J.W. Connected vehicles: Solutions and challenges. IEEE Internet Things J. 2014, 1, 289–299. [Google Scholar] [CrossRef]
- Sadiku, M.N.O.; Tembely, M.; Musa, S.M. Internet of Vehicles: An Introduction. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2018, 8, 11–13. [Google Scholar] [CrossRef] [Green Version]
- Fadhil, J.A.; Sarhan, Q.I. Internet of Vehicles (IoV): A Survey of Challenges and Solutions. In Proceedings of the 2020 21st International Arab Conference on Information Technology (ACIT), Muscat, Oman, 28–30 November 2020; pp. 1–10. [Google Scholar] [CrossRef]
- Alam, K.M.; Saini, M.; El Saddik, A.E. Toward social internet of vehicles: Concept, architecture, and applications. IEEE Access 2015, 3, 343–357. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, R.; Li, Q.; Ma, C.; Shi, X. A mobile edge computing-based applications execution framework for Internet of Vehicles. Front. Comput. Sci. 2022, 16, 165506. [Google Scholar] [CrossRef]
- Richter, A.; Löwner, M.O.; Ebendt, R.; Scholz, M. Towards an integrated urban development considering novel intelligent transportation systems: Urban Development Considering Novel Transport. Technol. Forecast. Soc. Chang. 2020, 155, 119970. [Google Scholar] [CrossRef]
- Internet of Vehicles (IoV). Available online: https://www.techtarget.com/whatis/definition/Internet-of-Vehicles (accessed on 2 December 2020).
- Chen, C.; Quan, S. Review Article A Summary of Security Techniques-Based Blockchain in IoV. Secur. Commun. Netw. 2022, 2022, 8689651. [Google Scholar] [CrossRef]
- Latif, M.B.; Liu, F.; Liu, K. A TDMA-Based MAC Protocol for Mitigating Mobility-Caused Packet Collisions in Vehicular Ad Hoc Networks. Sensors 2022, 22, 643. [Google Scholar] [CrossRef]
- Huang, J.; Xu, C.; Ji, Z.; Xiao, S.; Liu, T.; Ma, N.; Zhou, Q. Research Article AFLPC: An Asynchronous Federated Learning Privacy-Preserving Computing Model Applied to 5G-V2X. Secur. Commun. Netw. 2022, 2022, 9334943. [Google Scholar] [CrossRef]
- Wu, H.; Liu, Q.; Liu, Q.; Zhang, Y.; Yang, Z. An edge-assisted cloud framework using a residual concatenate FCN approach to beam correction in the internet of weather radars. World Wide Web 2022, 25, 1923–1949. [Google Scholar] [CrossRef]
- Yin, D.; Gong, B. Auto-Adaptive Trust Measurement Model Based on Multidimensional Decision-Making Attributes for Internet of Vehicles. Wirel. Commun. Mob. Comput. 2022, 2022, 3537771. [Google Scholar] [CrossRef]
- Tomar, A.; Tripathi, S. BCAV: Blockchain-based certificateless authentication system for vehicular network. Peer-to-Peer Netw. Appl. 2022, 15, 1733–1756. [Google Scholar] [CrossRef]
- Shah, K.; Chadotra, S.; Tanwar, S.; Gupta, R.; Kumar, N. Blockchain for IoV in 6G environment: Review solutions and challenges. Cluster Comput. 2022, 25, 1927–1955. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, J.; Liu, T.; He, X. BSS-ITS: Blockchain Scaling Scheme with Sharding for Intelligent Transportation System. Scale Blockchain for Better Data Exchange and Storage with Full Sharding for Intelligent Transportation System. In Proceedings of the ICBTA 2021, Xi’an, China, 17–19 December 2021; pp. 128–134. [Google Scholar]
- Evariste, T.; Rwigema, J.; Datta, R. Design and Deployment of Vehicular Internet of Things for Smart City Applications. Sustainability 2022, 14, 176. [Google Scholar] [CrossRef]
- Kakkavas, G.; Diamanti, M.; Stamou, A.; Karyotis, V.; Bouali, F.; Pinola, J.; Apilo, O.; Papavassiliou, S.; Moessner, K. Design, Development, and Evaluation of 5G-Enabled Vehicular Services: The 5G-HEART Perspective. Sensors 2022, 22, 426. [Google Scholar] [CrossRef] [PubMed]
- Xu, W.; Li, N.; Liang, W.; Liu, H. Research Article Dissipation Characteristics of Vehicle Queue in V2X Environment Based on Improved Car-Following Model. Math. Probl. Eng. 2022, 2022, 8281919. [Google Scholar] [CrossRef]
- Shiny, G.S.; Kumar, B.M. E2IA-HWSN: Energy Efficient Dual Intelligent Agents based Data Gathering and Emergency Event Delivery in Heterogeneous WSN Enabled IoT. Wirel. Pers. Commun. 2022, 122, 379–408. [Google Scholar] [CrossRef]
- Ullah, S.; Khan, M.A.; Ahmad, J.; Jamal, S.S.; e Huma, Z.; Hassan, M.T.; Pitropakis, N.; Arshad; Buchanan, W.J. HDL-IDS: A Hybrid Deep Learning Architecture for Intrusion Detection in the Internet of Vehicles. Sensors 2022, 22, 1340. [Google Scholar] [CrossRef] [PubMed]
- Smida, K.; Tounsi, H.; Frikha, M. Intelligent and resizable control plane for software defined vehicular network: A deep reinforcement learning approach. Telecommun. Syst. 2022, 79, 163–180. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, X.; Huang, Z.; Li, W.; Xu, S. Joint optimization of dynamic resource allocation and packet scheduling for virtual switches in cognitive internet of vehicles. EURASIP J. Adv. Signal Process. 2022, 2022, 32. [Google Scholar] [CrossRef]
- Pachala, S.; Rupa, C.; Sumalatha, L. l−PEES-IMP: Lightweight proxy re-encryption-based identity management protocol for enhancing privacy over multi-cloud environment. Autom. Softw. Eng. 2022, 29, 4. [Google Scholar] [CrossRef]
- Khan, S.; Shah, I.A.; Tairan, N.; Shah, H.; Nadeem, M.F. Optimal Resource Allocation in Fog Computing for Healthcare Applications. Comput. Mater. Contin. 2022, 71, 6147–6163. [Google Scholar] [CrossRef]
- Yuan, Z.; Wu, T.; Wang, Q.; Yang, Y.; Li, L.; Zhang, L. T3 OMVP: A Transformer-Based Time and Team Reinforcement Learning Scheme for Observation-Constrained MultiVehicle Pursuit in Urban Area. Electronics 2022, 11, 1339. [Google Scholar] [CrossRef]
- Bhabani, B.; Mahapatro, J. ReUse: Reliable and efficient RSU-enabled relay vehicle selection using harmony search and EDAS for message dissemination in VANETs. Ad Hoc Netw. 2022, 137, 102985. [Google Scholar] [CrossRef]
- Zhang, L.; Zhou, W.; Xia, J.; Ou, J. DQN-based mobile edge computing for smart Internet of vehicle. EURASIP J. Adv. Signal Process. 2022, 2022, 45. [Google Scholar] [CrossRef]
- You, K.; Peng, G.; Ding, L.; Dou, Q.; Wu, Z.; Zhou, C. Smart T-box of unmanned earthwork machinery for Internet of Vehicles. Autom. Constr. 2022, 144, 104589. [Google Scholar] [CrossRef]
- Sellami, B.; Hakiri, A.; Yahiac, S.B. Deep Reinforcement Learning for energy-aware task offloading in join SDN-Blockchain 5G massive IoT edge network. Future Gener. Comput. Syst. 2022, 137, 363–379. [Google Scholar] [CrossRef]
- Peng, H.; Dong, L.; Sun, Y.; Jiang, Y. Analysis of Marketing Prediction Model Based on Genetic Neural Network: Taking Clothing Marketing as an Example. J. Math. 2022, 2022, 8743568. [Google Scholar] [CrossRef]
- Jamalzadeh, M.; Maadani, M.; Mahdavi, M. EC-MOPSO: An edge computing-assisted hybrid cluster and MOPSO-based routing protocol for the Internet of Vehicles. Ann. Telecommun. 2022, 77, 491–503. [Google Scholar] [CrossRef]
- Li, Q.; Wu, H.; Wu, X.; Zhao, N.; Dong, L. A Road Truncation-Based Location Privacy-Preserving Method against Side-Weight Inference Attack. Appl. Sci. 2022, 12, 1107. [Google Scholar] [CrossRef]
- Hemavathi; Akhila, S.R.; Alotaibi, Y.; Khalaf, O.I.; Alghamdi, S. Authentication and Resource Allocation Strategies during Handoff for 5G IoVs Using Deep Learning. Energies 2022, 15, 2006. [Google Scholar] [CrossRef]
- Gurumoorthi, E.; Ayyasamy, A. Performance analysis of Geocast based location aided routing using Cache agent in VANET. Int. J. Inf. Technol. 2022, 14, 125–134. [Google Scholar] [CrossRef]
- Zhang, L.; Zhong, W.; Zhang, J.; Lin, Z.; Yang, Z.; Wang, J. mmWave Beam Tracking for V2I Communication Systems Based on Spectrum Environment Awareness. Symmetry 2022, 14, 677. [Google Scholar] [CrossRef]
- Wang, M.; Chen, T.; Du, F.; Wang, J.; Yin, G.; Zhang, Y. Research on adaptive beacon message transmission power in VANETs. J. Ambient. Intell. Humaniz. Comput. 2022, 13, 1307–1319. [Google Scholar] [CrossRef]
- Chen, X.; Jin, Z.; Zhang, Q.; Li, P.; Zhang, S.; Sun, J.; Tian, X.; Wang, Y.; Zhang, J. Research on Automatic Driving Simulation Test System Based on Digital Twin. J. Phys. Conf. Ser. 2022, 2170, 012039. [Google Scholar] [CrossRef]
- Khasawneh, A.M.; Helou, M.A.; Khatri, A.; Aggarwal, G.; Kaiwartya, O.; Altalhi, M.; Abu-ulbeh, W.; AlShboul, R. Service-Centric Heterogeneous Vehicular Network Modeling for Connected Traffic Environments. Sensors 2022, 22, 1247. [Google Scholar] [CrossRef] [PubMed]
- González-Saavedra, J.F.; Figueroa, M.; Céspedes, S.; Montejo-Sánchez, S. Survey of Cooperative Advanced Driver Assistance Systems: From a Holistic and Systemic Vision. Sensors 2022, 22, 3040. [Google Scholar] [CrossRef]
- Zhu, C.; Ye, D.; Zhu, T.; Zhou, W. Time-optimal and privacy preserving route planning for carpool policy. World Wide Web 2022, 25, 1151–1168. [Google Scholar] [CrossRef]
- Xie, H.; Zhu, J.; Duan, H. Research Article Analysis of the Relationship between the Density and Lane-Changing Behavior of Circular Multilane Urban Expressway in Mixed Traffic. J. Adv. Transp. 2022, 2022, 4499477. [Google Scholar] [CrossRef]
- Dhanare, R.; Nagwanshi, K.K.; Varma, S. Enhancing the Route Optimization Using Hybrid MAF Optimization Algorithm for the Internet of Vehicle. Wirel. Pers. Commun. 2022, 125, 1715–1735. [Google Scholar] [CrossRef]
- Guerna, A.; Bitam, S.; Calafate, C.T. Roadside Unit Deployment in Internet of Vehicles Systems: A Survey. Sensors 2022, 22, 3190. [Google Scholar] [CrossRef]
- Wang, L.; Li, H.; Guo, M.; Chen, Y. The Effects of Dynamic Complexity on Drivers’ Secondary Task Scanning Behavior under a Car-Following Scenario. Int. J. Environ. Res. Public Health 2022, 19, 1881. [Google Scholar] [CrossRef]
- Bustamante-Bello, R.; García-Barba, A.; Arce-Saenz, L.A.; Curiel-Ramirez, L.A.; Izquierdo-Reyes, J.; Ramirez-Mendoza, R.A. Visualizing Street Pavement Anomalies through Fog Computing V2I Networks and Machine Learning. Sensors 2022, 22, 456. [Google Scholar] [CrossRef]
- Lu, Y.; Wang, X.; Yi, B.; Huang, M. The reliable routing for software-defined vehicular networks towards beyond 5G. Peer-to-Peer Netw. Appl. 2022, 15, 134–148. [Google Scholar] [CrossRef]
- Dai, F.; Liu, G.; Mo, Q.; Xu, W.H.; Huang, B. Task offloading for vehicular edge computing with edge-cloud cooperation. World Wide Web 2022, 25, 1999–2017. [Google Scholar] [CrossRef]
- Seng, K.P.; Ang, L.M.; Ngharamike, E. Artificial intelligence Internet of Things: A new paradigm of distributed sensor networks. Int. J. Distrib. Sens. Netw. 2022, 18, 15501477211062835. [Google Scholar] [CrossRef]
- Mir, M.; Yaghoobi, M.; Khairabadi, M. A new approach to energy-aware routing in the Internet of Things using improved Grasshopper Metaheuristic Algorithm with Chaos theory and Fuzzy Logic. Multimed. Tools Appl. 2022, 82, 5133–5159. [Google Scholar] [CrossRef]
- Khezri, E.; Zeinali, E.; Sargolzaey, H. A Novel Highway Routing Protocol in Vehicular Ad Hoc Networks Using VMaSC-LTE and DBA-MAC Protocols. Wirel. Commun. Mob. Comput. 2022, 2022, 1680507. [Google Scholar] [CrossRef]
- Safara, F.; Souri, A.; Baker, T.; Al Ridhawi, I.; Aloqaily, M. A priority-based energy-efficient routing method for IoT systems. J. Supercomput. 2020, 76, 8609–8626. [Google Scholar] [CrossRef]
- Li, H.; Ou, D.; Rasheed, I.; Tu, M. Research Article A Software-Defined Networking Roadside Unit Cloud Resource Management Framework for Vehicle Ad Hoc Networks. J. Adv. Transp. 2022, 2022, 5918128. [Google Scholar] [CrossRef]
- Guan, Z.; Wang, Y.; He, M. Deep Reinforcement Learning-Based Spectrum Allocation Algorithm in Internet of Vehicles Discriminating Services. Appl. Sci. 2022, 12, 1764. [Google Scholar] [CrossRef]
- Pereira, P.; Melo, C.; Araujo, J.; Dantas, J.; Santos, V.; Maciel, P. Availability model for edge-fog-cloud continuum: An evaluation of an end-to-end infrastructure of intelligent traffic management service. J. Supercomput. 2022, 78, 4421–4448. [Google Scholar] [CrossRef]
- Hasan, M.K.; Alkhalifah, A.; Islam, S.; Babiker, N.B.M.; Habib, A.K.M.A.; Mohd Aman, A.H.; Hossain, M.A. Blockchain Technology on Smart Grid, Energy Trading, and Big Data: Security Issues, Challenges, and Recommendations. Wirel. Commun. Mob. Comput. 2022, 2022, 9065768. [Google Scholar] [CrossRef]
- Zhu, Y.; Li, X.; Liu, Q.; Li, Q.; Xu, Y. A comprehensive review of energy management strategies for hybrid electric vehicles. Mech. Sci. 2022, 13, 147–188. [Google Scholar] [CrossRef]
- Alsaawy, Y.; Alkhodre, A.; Abi Sen, A.; Alshanqiti, A.; Bhat, W.A.; Bahbouh, N.M. A Comprehensive and Effective Framework for Traffic Congestion Problem Based on the Integration of IoT and Data Analytics. Appl. Sci. 2022, 12, 2043. [Google Scholar] [CrossRef]
- Ang, L.M.; Seng, K.P.; Ijemaru, G.K.; Zungeru, A.M. Deployment of IoV for smart cities: Applications, architecture, and challenges. IEEE Access 2018, 7, 6473–6492. [Google Scholar] [CrossRef]
- Salih, K.O.M.; Rashid, T.A.; Radovanovic, D.; Bacanin, N. A Comprehensive Survey on the Internet of Things with the Industrial Marketplace. Sensors 2022, 22, 730. [Google Scholar] [CrossRef]
- Tan, L.; Wang, N. Future Internet: The Internet of Things. In Proceedings of the 3rd International Conference on Advanced Computer Theory and Engineering, ICACTE 2010, Chengdu, China, 20–22 August 2010; pp. V5-376–V5-380. [Google Scholar] [CrossRef]
- Kopelias, P.; Demiridi, E.; Vogiatzis, K.; Skabardonis, A.; Zafiropoulou, V. Connected & autonomous vehicles—Environmental impacts—A review. Sci. Total Environ. 2020, 712, 135237. [Google Scholar] [CrossRef]
- Sharma, N.; Habibullah, P.S. A Review of IoT Technology for the Connected Autonomous Vehicles Ecosystem. Trends Sci. 2022, 19, 3072. [Google Scholar] [CrossRef]
- Butt, T.A.; Iqbal, R.; Shah, S.C.; Umar, T. Social Internet of Vehicles: Architecture and enabling technologies. Comput. Electr. Eng. 2018, 69, 68–84. [Google Scholar] [CrossRef]
- Zhang, L.; Zhao, Z.; Wu, Q.; Zhao, H.; Xu, H.; Wu, X. Energy-aware dynamic resource allocation in UAV assisted mobile edge computing over social internet of vehicles. IEEE Access 2018, 6, 56700–56715. [Google Scholar] [CrossRef]
- Silva, R.; Iqbal, R. Ethical Implications of Social Internet of Vehicles Systems. IEEE Internet Things J. 2019, 6, 517–531. [Google Scholar] [CrossRef] [Green Version]
- Javaid, U.; Sikdar, B. A Secure and Scalable Framework for Blockchain Based Edge Computation Offloading in Social Internet of Vehicles. IEEE Trans. Veh. Technol. 2021, 70, 4022–4036. [Google Scholar] [CrossRef]
- Zhao, Y.; Liu, W.; Li, B.; Zhou, X.; Ning, Z.; Qiu, T.; Atiquzzaman, M. Entity and Sociality Trust-Aware Model for Content Distribution in Social Internet of Vehicles. IEEE Trans. Veh. Technol. 2022, 71, 12511–12522. [Google Scholar] [CrossRef]
- Howard, M.; Sparrow, R. When human beings are like drunk robots: Driverless vehicles, ethics, and the future of transport. Transp. Res. C Emerg. Technol. 2017, 80, 206–215. [Google Scholar] [CrossRef]
- Maglaras, L.A.; Al-Bayatti, A.H.; He, Y.; Wagner, I.; Janicke, H. Social Internet of Vehicles for Smart Cities. J. Sens. Actuator Netw. 2016, 5, 3. [Google Scholar] [CrossRef] [Green Version]
- Butt, T.A.; Iqbal, R.; Salah, K.; Aloqaily, M.; Jararweh, Y. Privacy Management in Social Internet of Vehicles: Review, Challenges and Blockchain Based Solutions. IEEE Access 2019, 7, 79694–79713. [Google Scholar] [CrossRef]
- Loscri, V.; Manzoni, O.; Nitti, M.; Ruggeri, G.; Vegni, A.M. A social internet of vehicles sharing SIoT relationships. In Proceedings of the MobiHoc 2019: Twentieth International Symposium on Mobile Ad Hoc Networking, Catania, Italy, 2–5 July 2019; Association for Computing Machinery: New York, NY, USA, 2019. [Google Scholar] [CrossRef]
- Eftekhari, S.A.; Nikooghadam, M.; Rafighi, M. Robust session key generation protocol for social internet of vehicles with enhanced security provision. J. Supercomput. 2021, 77, 2511–2544. [Google Scholar] [CrossRef]
- Khan, S.; Zhu, L.; Yu, X.; Zhang, Z.; Rahim, M.A.; Khan, M.; Du, X.; Guizani, M. Accountable credential management system for vehicular communication. Veh. Commun. 2020, 25, 100279. [Google Scholar] [CrossRef]
- Li, Y.; Tao, X.; Zhang, X.; Xu, J.; Wang, Y.; Xia, W. A DAG-based reputation mechanism for preventing peer disclosure in SIoV. IEEE Internet Things J. 2022, 9, 24095–24106. [Google Scholar] [CrossRef]
- García-Magariño, I.; Sendra, S.; Lacuesta, R.; Lloret, J. Security in vehicles with iot by prioritization rules, vehicle certificates and trust management. IEEE Int. Things J. 2019, 6, 5927–5934. [Google Scholar] [CrossRef]
- Lin, K.; Li, C.; Fortino, G.; Rodrigues, J.J. Vehicle route selection based on game evolution in social internet of vehicles. IEEE Int. Things J. 2018, 5, 2423–2430. [Google Scholar] [CrossRef]
- Tang, C.; Wei, X.; Liu, C.; Jiang, H.; Wu, H.; Li, Q. UAV-enabled social internet of vehicles: Roles, security issues and use cases. In Proceedings of the Security and Privacy in Social Networks and Big Data: 6th International Symposium, SocialSec 2020, Tianjin, China, 26–27 September 2020; Springer: Singapore, 2020; pp. 153–163. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G.; Nitti, M. The social internet of things (SIoT) when social networks meet the internet of things: Concept, architecture and network characterization. Comput. Netw. 2012, 56, 3594–3608. [Google Scholar] [CrossRef]
- Hussain, R.; Kim, D.; Son, J.; Lee, J.; Kerrache, C.A.; Benslimane, A.; Oh, H. Secure and Privacy-Aware Incentives-Based Witness Service in Social Internet of Vehicles Clouds. IEEE Internet Things J. 2018, 5, 2441–2448. [Google Scholar] [CrossRef]
- Jain, B.; Brar, G.; Malhotra, J.; Rani, S.; Ahmed, S.H. A cross layer protocol for traffic management in social internet of vehicles. Future Gener. Comput. Syst. 2018, 82, 707–714. [Google Scholar] [CrossRef]
- Raza, N.; Jabbar, S.; Han, J.; Han, K. Social Vehicle-To-Everything (V2X) communication model for Intelligent Transportation Systems based on 5G scenario. ACM Int. Conf. Proceeding Ser. 2018, 54, 1–8. [Google Scholar] [CrossRef]
- Zualkernan, I.A.; Aloul, F.; Al Qasimi, S.; AlShamsi, A.; Al Marashda, M.; Ahli, A. DigiMesh-based Social Internet of Vehicles (SIoV) for Driver Safety. In Proceedings of the 2018 International Symposium in Sensing and Instrumentation in IoT Era, ISSI 2018, Shanghai, China, 6–7 September 2018; IEEE: Piscataway, NJ, USA, 2018; p. 8538167. [Google Scholar] [CrossRef]
- Wang, T.; Hussain, A.; Zhang, L.; Zhao, C. Collaborative Edge Computing for Social Internet of Vehicles to Alleviate Traffic Congestion. IEEE Trans. Comput. Soc. Syst. 2022, 9, 184–196. [Google Scholar] [CrossRef]
- Roopa, M.S.; Ayesha Siddiq, S.; Buyya, R.; Venugopal, K.R.; Iyengar, S.S.; Patnaik, L.M. Dynamic traffic congestion management in Social Internet of Vehicles (SIoV). Internet Things 2021, 16, 100311. [Google Scholar] [CrossRef]
- Tang, C.; Wu, H. Reputation-based service provisioning for vehicular fog computing. J. Syst. Archit. 2022, 131, 102735. [Google Scholar] [CrossRef]
- Jennath, H.S.; Asharaf, S. Reputation management in vehicular network using blockchain. Peer-to-Peer Netw. Appl. 2022, 15, 901–920. [Google Scholar] [CrossRef]
- Ochoa-Zambrano, J.; Garbajosa, J. Social Internet of Things: Architectural Approaches and Challenges. In Proceedings of the Actas de las 24th Jornadas de Ingenieria del Software y Bases de Datos, JISBD 2019, Caceres, Spain, 2–4 September 2019. [Google Scholar]
- Kehal, M.; Zhang, Z. Social internet of vehicles: An epistemological and systematic perspective. Library Hi Tech 2020, 38, 221–231. [Google Scholar] [CrossRef]
- Kerrache, C.A.; Lagraa, N.; Hussain, R.; Ahmed, S.H.; Benslimane, A.; Calafate, C.T.; Cano, J.-C.; Vegni, A.M. TACASHI: Trust-Aware Communication Architecture for Social Internet of Vehicles. IEEE Internet Things J. 2019, 6, 5870–5877. [Google Scholar] [CrossRef]
- Xia, Z.; Mao, X.; Gu, K.; Jia, W.J. Dual-Mode Data Forwarding Scheme Based on Interest Tags for Fog Computing-based SIoVs. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2780–2797. [Google Scholar] [CrossRef]
- Xia, Z.; Mao, X.; Gu, K.; Jia, W. Two-Dimensional Behavior-Marker-Based Data Forwarding Incentive Scheme for Fog-Computing-Based SIoVs. IEEE Trans. Comput. Soc. Syst. 2022, 9, 1406–1418. [Google Scholar] [CrossRef]
- Ruan, Z.; Liang, W.; Luo, H.; Yan, H. A novel data sharing mechanism via cloud-based dynamic audit for social internet of vehicles. In Proceedings of the Internet of Vehicles-Safe and Intelligent Mobility: Second International Conference, IOV 2015, Chengdu, China, 19–21 December 2015; pp. 78–88. [Google Scholar] [CrossRef]
- Nitti, M.; Girau, R.; Floris, A.; Atzori, L. On adding the social dimension to the Internet of Vehicles: Friendship and middleware. In Proceedings of the 2014 IEEE International Black Sea Conference on Communications and Networking, BlackSeaCom 2014, Chişinău, Moldova, 27–30 May 2014; pp. 134–138. [Google Scholar] [CrossRef]
- Wang, X.; Ning, Z.; Hu, X.; Ngai, E.C.-H.; Wang, L.; Hu, B.; Kwok, R.Y.K. A City-Wide Real-Time Traffic Management System: Enabling Crowdsensing in Social Internet of Vehicles. IEEE Commun. Mag. 2018, 56, 19–25. [Google Scholar] [CrossRef] [Green Version]
- Zhao, P.-C.; Huang, Y.-H.; Zhang, D.-X.; Xing, L.; Wu, H.-H.; Gao, J.-P. CCP-federated deep learning based on user trust chain in social IoV. Wirel. Netw. 2022, 2022, 1–12. [Google Scholar] [CrossRef]
- Li, Y.; Cao, B.; Peng, M.; Zhang, L.; Zhang, L.; Feng, D.; Yu, J. Direct Acyclic Graph-Based Ledger for Internet of Things: Performance and Security Analysis. IEEE/ACM Trans. Netw. 2020, 28, 1643–1656. [Google Scholar] [CrossRef]
- Zhao, P.; Huang, Y.; Gao, J.; Xing, L.; Wu, H.; Ma, H. Federated Learning-Based Collaborative Authentication Protocol for Shared Data in Social IoV. IEEE Sens. J. 2022, 22, 7385–7398. [Google Scholar] [CrossRef]
- Kong, X.; Gao, H.; Shen, G.; Duan, G.; Das, S.K. FedVCP: A Federated-Learning-Based Cooperative Positioning Scheme for Social Internet of Vehicles. IEEE Trans. Comput. Soc. Syst. 2022, 9, 197–206. [Google Scholar] [CrossRef]
- Jia, X.; Xing, L.; Gao, J.; Wu, H. A Survey of Location Privacy Preservation in Social Internet of Vehicles. IEEE Access 2020, 8, 201966–201984. [Google Scholar] [CrossRef]
- Xing, L.; Jia, X.; Gao, J.; Wu, H. A Location Privacy Protection Algorithm Based on Double K-Anonymity in the Social Internet of Vehicles. IEEE Commun. Lett. 2021, 25, 3199–3203. [Google Scholar] [CrossRef]
- Li, Z.; Miao, Q.; Chaudhry, S.A.; Chen, C.-M. A provably secure and lightweight mutual authentication protocol in fog-enabled social Internet of vehicles. Int. J. Distrib. Sens. Netw. 2022, 18, 15501329221104332. [Google Scholar] [CrossRef]
- Wu, T.Y.; Guo, X.; Yang, L.; Meng, Q.; Chen, C.-M. A lightweight authenticated key agreement protocol using fog nodes in social Internet of vehicles. Mob. Inf. Syst. 2021, 2021, 3277113. [Google Scholar] [CrossRef]
- Chen, P.-Y.; Cheng, S.-M.; Sung, M.-H. Analysis of Data Dissemination and Control in Social Internet of Vehicles. IEEE Internet Things J. 2018, 5, 2466–2477. [Google Scholar] [CrossRef]
- Kumar, N.; Chaudhry, R.; Kaiwartya, O.; Kumar, N.; Ahmed, S.H. Green Computing in Software Defined Social Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3644–3653. [Google Scholar] [CrossRef]
- Kumar, T.A.; Rajmohan, R.; Julie, E.G.; Robinson, Y.H.; Vimal, S.; Kadry, S. Reinforced resource management in vehicular fog computing using deep beacon power control protocol. Int. J. Web Grid Serv. 2021, 17, 371–388. [Google Scholar] [CrossRef]
- Gulati, A.; Aujla, G.S.; Chaudhary, R.; Kumar, N.; Obaidat, M.S.; Benslimane, A. DiLSe: Lattice-Based Secure and Dependable Data Dissemination Scheme for Social Internet of Vehicles. IEEE Trans. Dependable Secur. Comput. 2021, 18, 2520–2534. [Google Scholar] [CrossRef]
- Liu, Y.; Xiong, Z.; Hu, Q.; Niyato, D.; Zhang, J.; Miao, C.; Leung, C.; Tian, Z. VRepChain: A Decentralized and Privacy-preserving Reputation System for Social Internet of Vehicles Based on Blockchain. IEEE Trans. Veh. Technol. 2022, 71, 13242–13253. [Google Scholar] [CrossRef]
- Bao, Y.; Qiu, W.; Cheng, X.; Sun, J. Fine-Grained Data Sharing with Enhanced Privacy Protection and Dynamic Users Group Service for the IoV. IEEE Trans. Intell. Transp. Syst. 2022, 2022, 3187980. [Google Scholar] [CrossRef]
- Al Zamil, M.G.; Samarah, S.; Rawashdeh, M.; Hossain, M.S.; Alhamid, M.F.; Guizani, M.; Alnusair, A. False-Alarm Detection in the Fog-Based Internet of Connected Vehicles. IEEE Trans. Veh. Technol. 2019, 68, 7035–7044. [Google Scholar] [CrossRef]
- Qian, Y.; Chen, M.; Chen, J.; Hossain, M.S.; Alamri, A. Secure enforcement in cognitive Internet of Vehicles. IEEE Internet Things J. 2018, 5, 1242–1250. [Google Scholar] [CrossRef]
- Alotaibi, J.; Alazzawi, L. PPIoV: A privacy preserving-based framework for IoV-fog environment using federated learning and blockchain. In Proceedings of the 2022 IEEE World AI IoT Congress, AIIoT 2022, Seattle, DC, USA, 6–9 June 2022; pp. 597–603. [Google Scholar] [CrossRef]
- Campanile, L.; Iacono, M.; Marulli, F.; Mastroianni, M. Designing a GDPR compliant blockchain-based IoV distributed information tracking system. Inf. Process. Manag. 2021, 58, 102511. [Google Scholar] [CrossRef]
- Wu, X.; Xu, X.; Bilal, M. Towards privacy protection composition framework on internet of vehicles. IEEE Consum. Electron. Mag. 2021, 11, 32–38. [Google Scholar] [CrossRef]
- Kim, S.-K. Enhanced IoV Security Network by Using Blockchain Governance Game. Mathematics 2021, 9, 109. [Google Scholar] [CrossRef]
- Abbas, S.; Talib, M.A.; Ahmed, A.; Khan, F.; Ahmad, S.; Kim, D.-H. Blockchain-Based Authentication in Internet of Vehicles: A Survey. Sensors 2021, 21, 7927. [Google Scholar] [CrossRef]
- Feng, X.; Li, C.; Chen, D.; Tang, J. A method for defensing against multi-source Sybil attacks in VANET. Peer-to-Peer Netw. Appl. 2017, 10, 305–314. [Google Scholar] [CrossRef] [Green Version]
- Xie, Y.; Wu, L.; Shen, J.; Alelaiwi, A. EIAS-CP: New efficient identity-based authentication scheme with conditional privacy preserving for VANETs. Telecommun. Syst. 2017, 65, 229–240. [Google Scholar] [CrossRef]
- Biswas, S.; Misic, J. A cross-layer approach to privacy-preserving authentication in WAVE-enabled VANETs. IEEE Trans. Veh. Technol. 2013, 62, 2182–2192. [Google Scholar] [CrossRef]
- Sahraoui, Y.; Kerrache, C.A.; Korichi, A.; Vegni, A.M.; Amadeo, M. LearnPhi: A real-time learning model for early prediction of phishing attacks in IoV. In Proceedings of the IEEE Consumer Communications and Networking Conference, CCNC 2022, Virtual, 8–11 January 2022; pp. 252–255. [Google Scholar] [CrossRef]
- Kumar, A.; Das, D. SIoVChain: Efficient and secure blockchain based internet of vehicles (IoV). In Proceedings of the 23rd International Conference on Distributed Computing and Networking, Association for Computing Machinery International Conference Proceeding Series, Delhi, India, 4–7 January 2022; Association for Computing Machinery: New York, NY, USA, 2022; pp. 284–289. [Google Scholar] [CrossRef]
- Li, F.; Li, X.; Fu, Y.; Zhao, P.; Liu, S. A secure and privacy preserving incentive mechanism for vehicular crowdsensing with data quality assurance. In Proceedings of the IEEE Vehicular Technology Conference 2021, Virtual, 27 September–28 October 2021. [Google Scholar] [CrossRef]
- Bai, X.; Chen, S.; Shi, Y.; Liang, C.; Lv, X. Blockchain-based authentication and proof-of-reputation mechanism for trust data sharing in internet of vehicles. Ad-Hoc Sens. Wirel. Netw. 2022, 53, 85–113. [Google Scholar] [CrossRef]
- Hou, B.; Zhu, H.; Xin, Y.; Wang, J.; Yang, Y. MPoR: A modified consensus for blockchain-based internet of vehicles. Wirel. Commun. Mob. Comput. 2022, 2022, 1644851. [Google Scholar] [CrossRef]
- Zhang, J.; Wu, M. Blockchain-based authentication with optional privacy preservation for internet of vehicles. Math. Probl. Eng. 2021, 2021, 9954599. [Google Scholar] [CrossRef]
- Ma, Z.; Wang, L.; Zhao, W. Blockchain-driven trusted data sharing with privacy protection in IoT sensor network. IEEE Sens. J. 2021, 21, 25472–25479. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, G.; Sun, R.; Du, X.; Guizani, M. A blockchain-based conditional privacy-preserving traffic data sharing in cloud. In Proceedings of the IEEE International Conference on Communications 2020, Virtual, 7–11 June 2020. [Google Scholar] [CrossRef]
- Firdaus, M.; Rahmadika, S.; Rhee, K. Decentralized trusted data sharing management on internet of vehicle edge computing (iovec) networks using consortium blockchain. Sensors 2021, 21, 2410. [Google Scholar] [CrossRef]
- Haddaji, A.; Ayed, S.; Chaari, L. Federated Learning with Blockchain Approach for Trust Management in IoV. In Advanced Information Networking and Applications. AINA 2022; Lecture Notes in Networks and Systems; Barolli, L., Hussain, F., Enokido, T., Eds.; Springer: Cham, Switzerland, 2022; Volume 449, pp. 411–423. [Google Scholar] [CrossRef]
- Shrivastava, A.L.; Dwivedi, R.K. A secure design of the smart vehicular IoT system using blockchain technology. In Proceedings of the 2022 9th International Conference on Computing for Sustainable Global Development, INDIACom 2022, New Delhi, India, 23–25 March 2022; pp. 616–620. [Google Scholar] [CrossRef]
- Gong, Y.; Feng, H.; Zhang, C. Research on the Development Strategy of the Internet of Vehicles. J. Phys. Conf. Ser. 2021, 1907, 012063. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kostrzewski, M.; Marczewska, M.; Uden, L. The Internet of Vehicles and Sustainability—Reflections on Environmental, Social, and Corporate Governance. Energies 2023, 16, 3208. https://doi.org/10.3390/en16073208
Kostrzewski M, Marczewska M, Uden L. The Internet of Vehicles and Sustainability—Reflections on Environmental, Social, and Corporate Governance. Energies. 2023; 16(7):3208. https://doi.org/10.3390/en16073208
Chicago/Turabian StyleKostrzewski, Mariusz, Magdalena Marczewska, and Lorna Uden. 2023. "The Internet of Vehicles and Sustainability—Reflections on Environmental, Social, and Corporate Governance" Energies 16, no. 7: 3208. https://doi.org/10.3390/en16073208
APA StyleKostrzewski, M., Marczewska, M., & Uden, L. (2023). The Internet of Vehicles and Sustainability—Reflections on Environmental, Social, and Corporate Governance. Energies, 16(7), 3208. https://doi.org/10.3390/en16073208








