Performance Analysis of Overcurrent Protection under Corrupted Sampled Value Frames: A Hardware-in-the-Loop Approach
Abstract
1. Introduction
2. Problem Description
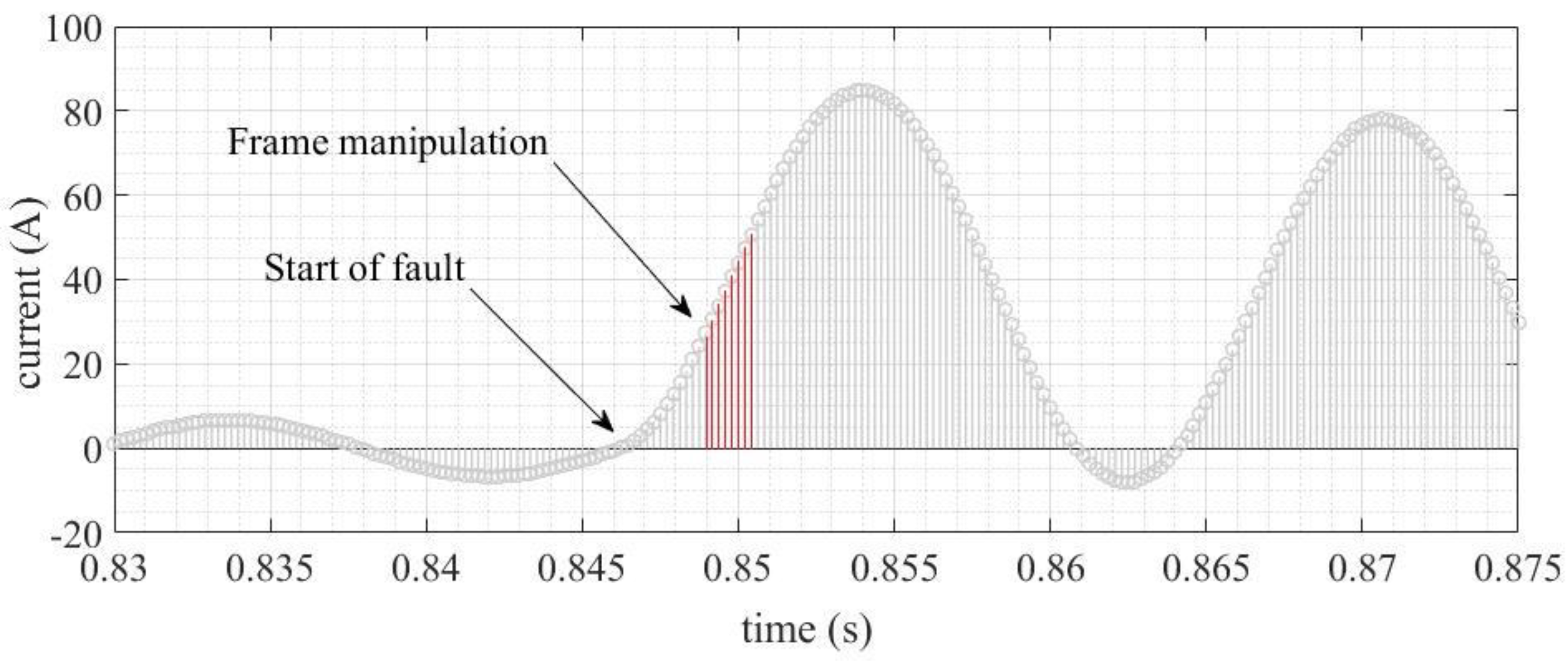
2.1. Sampled Value Manipulation
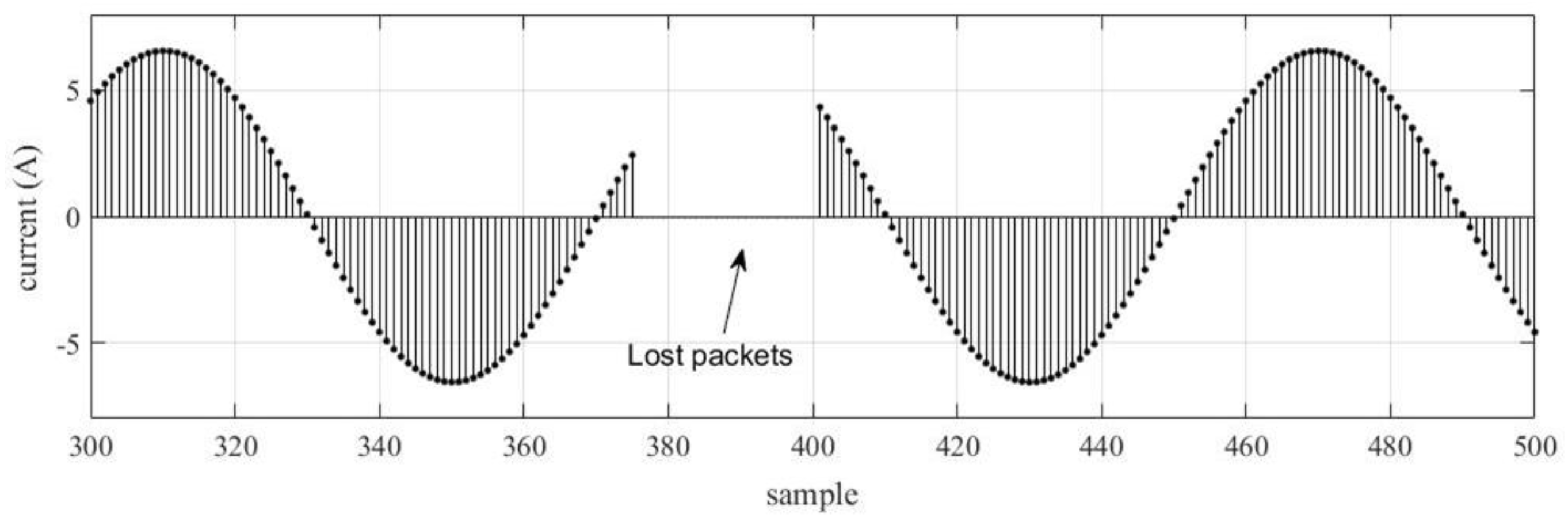
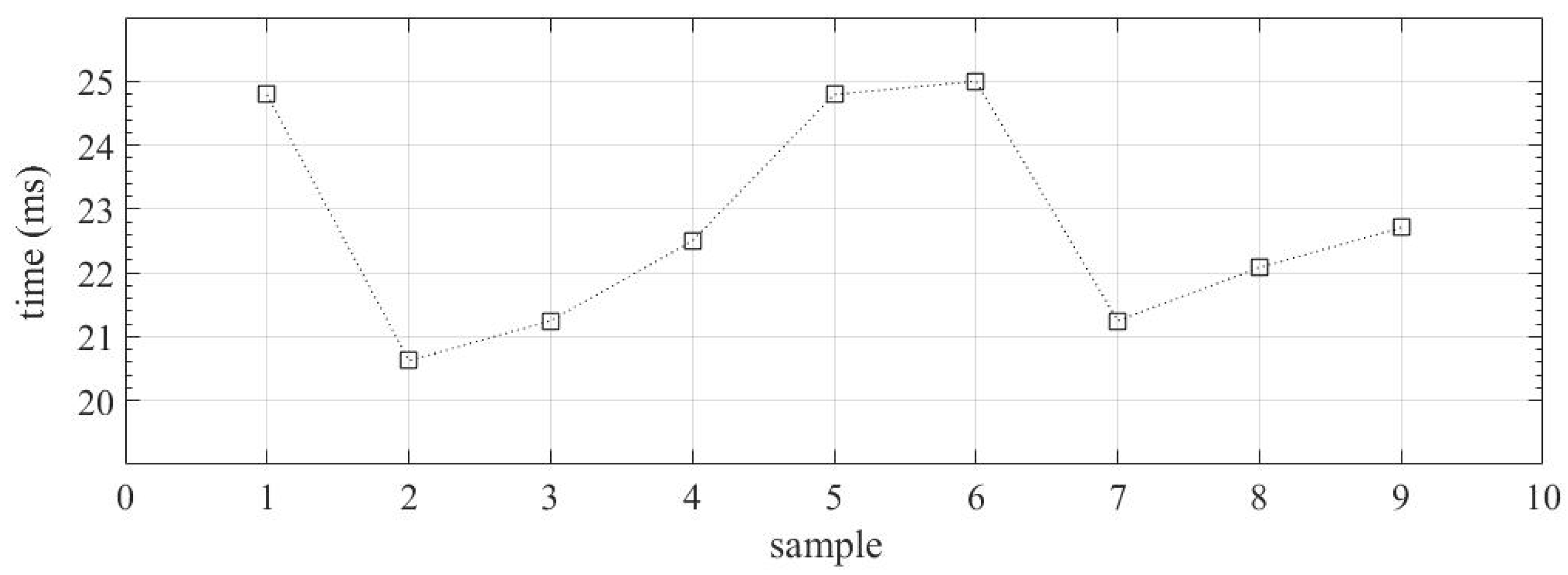
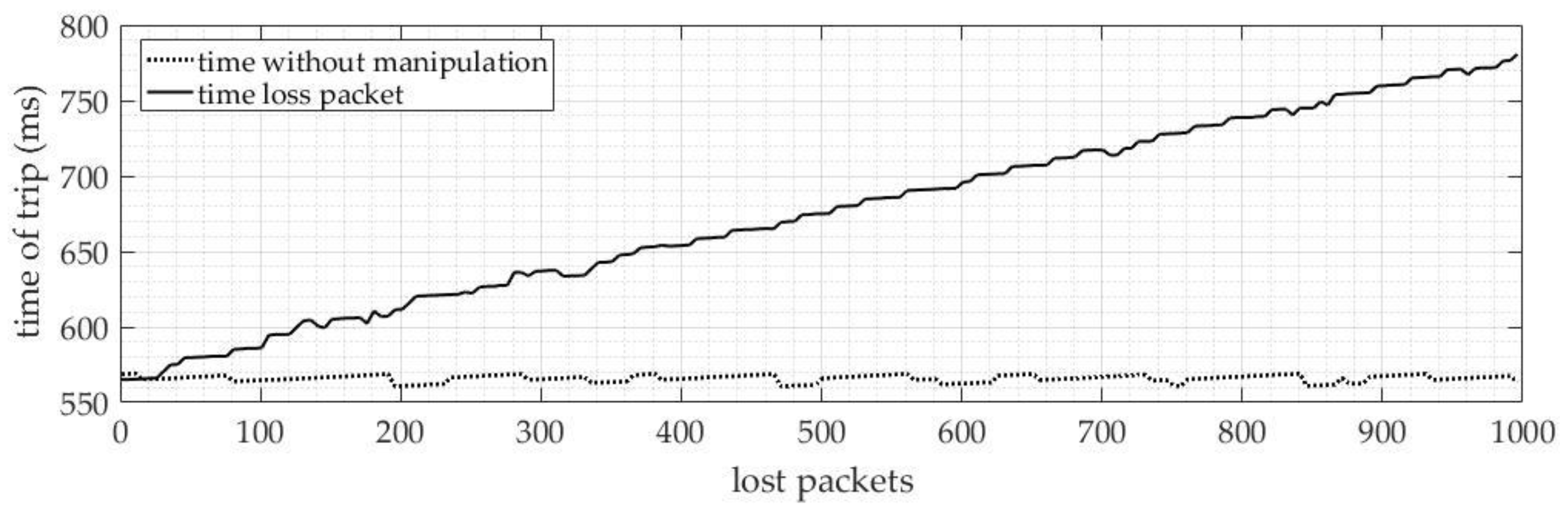
2.1.1. Packet Loss
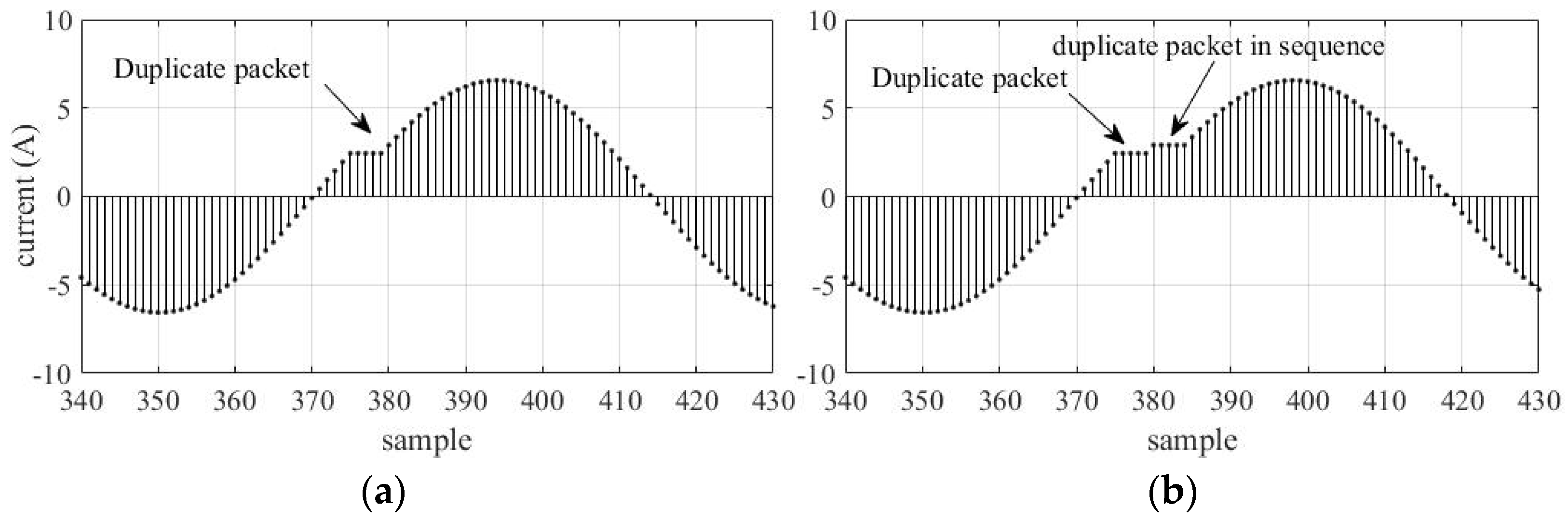
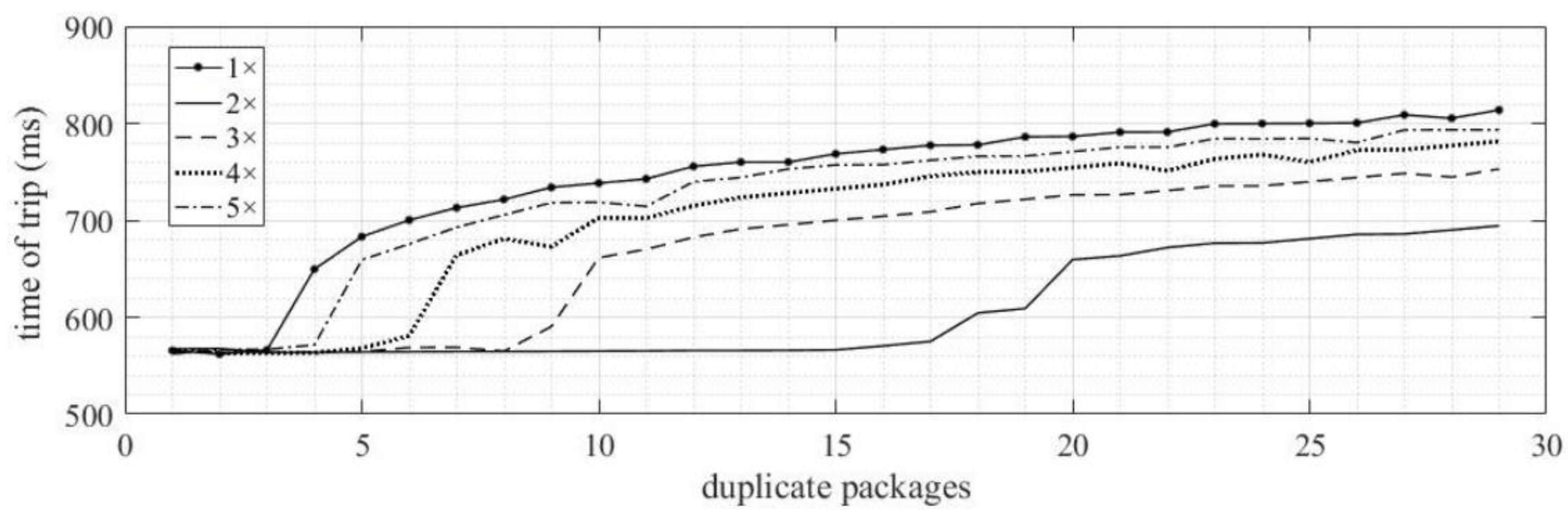
2.1.2. Duplicate Packets
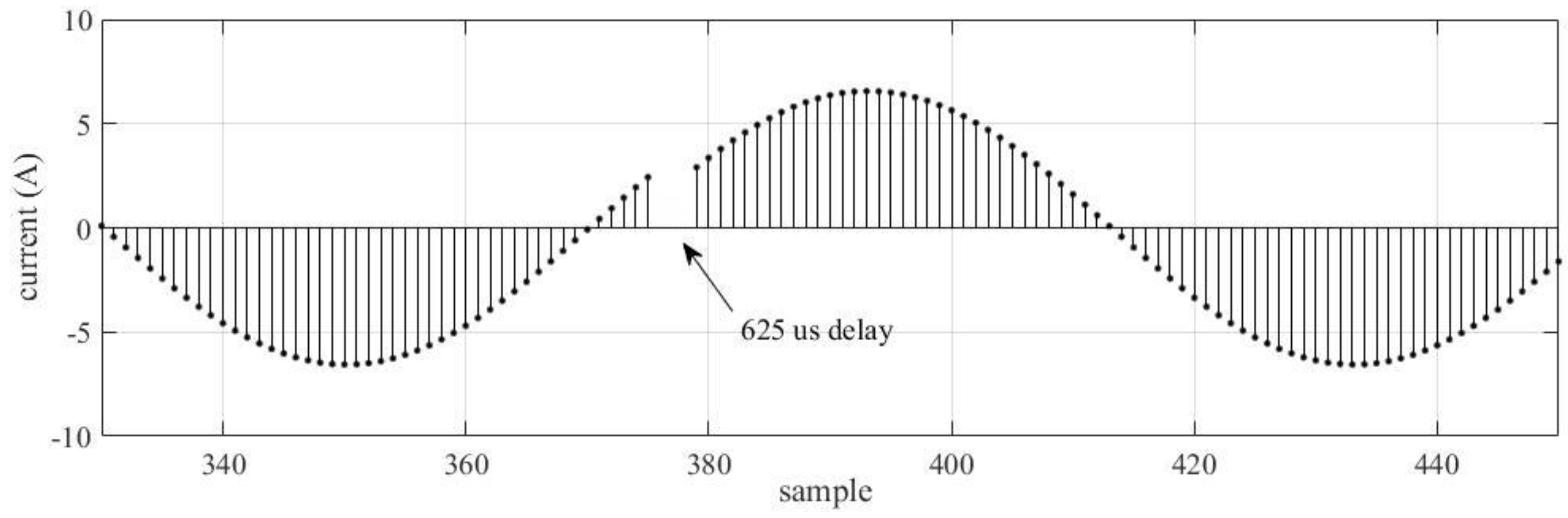
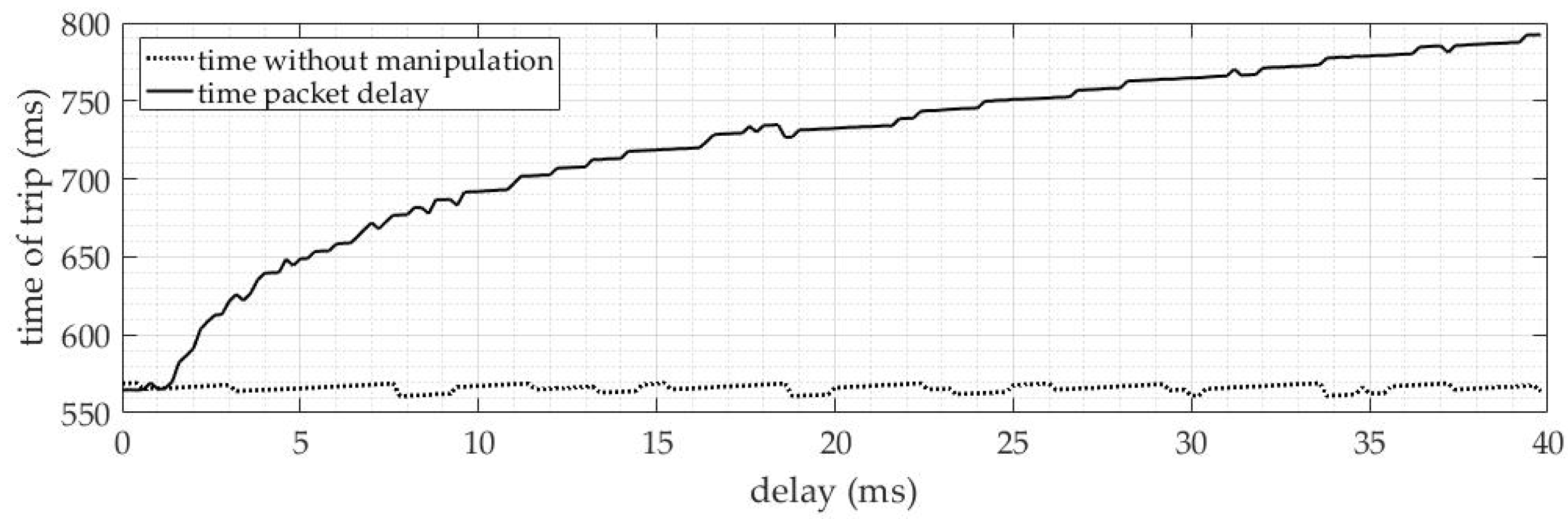
2.1.3. Delayed Packets
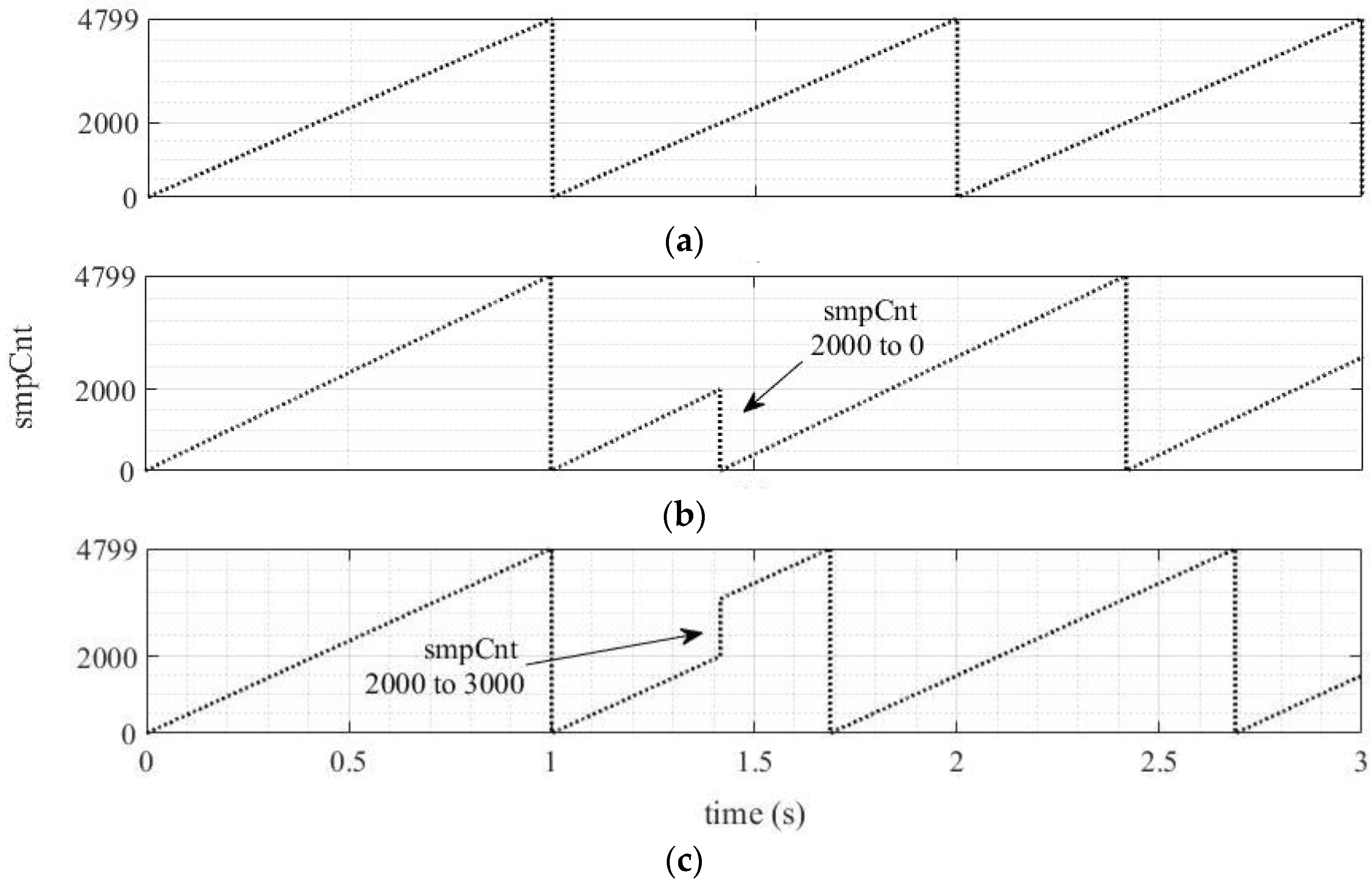
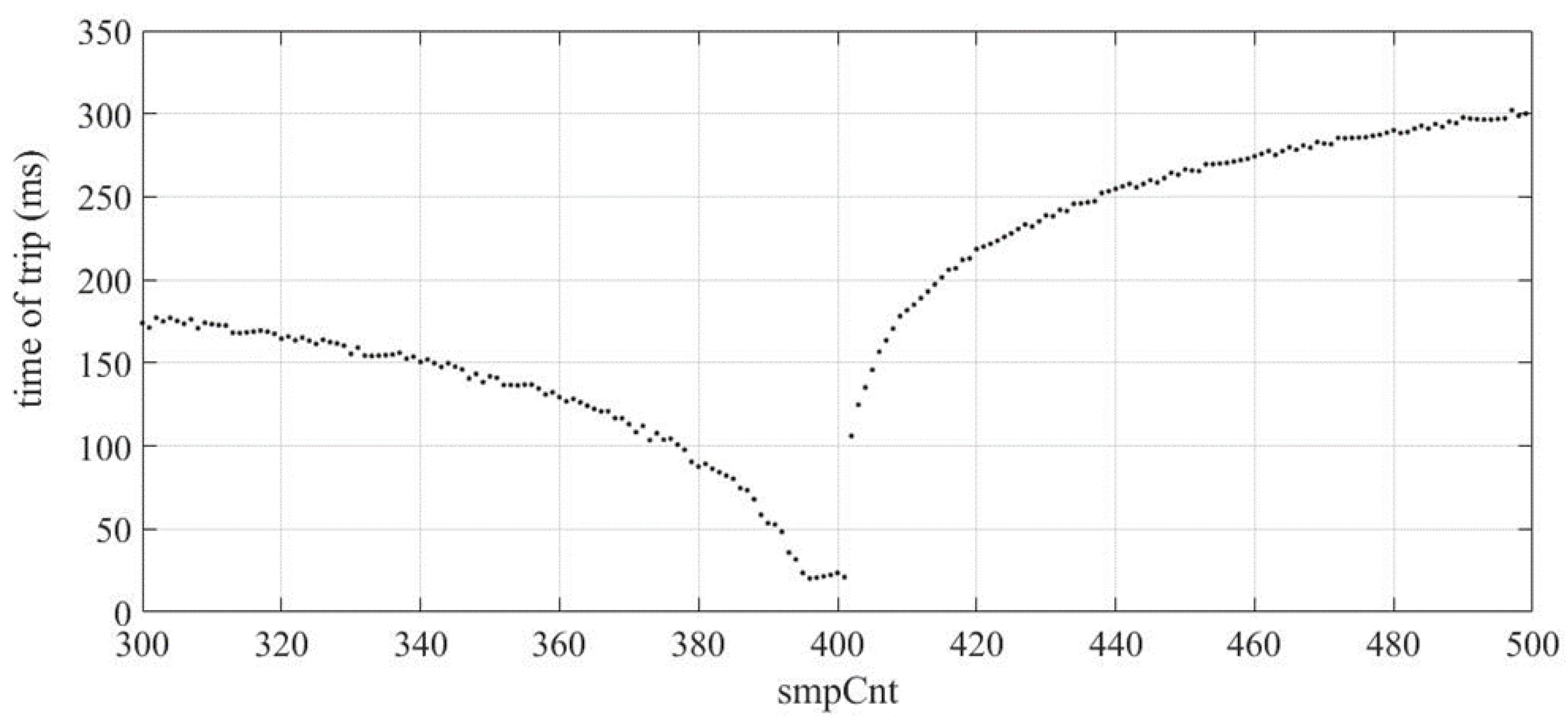
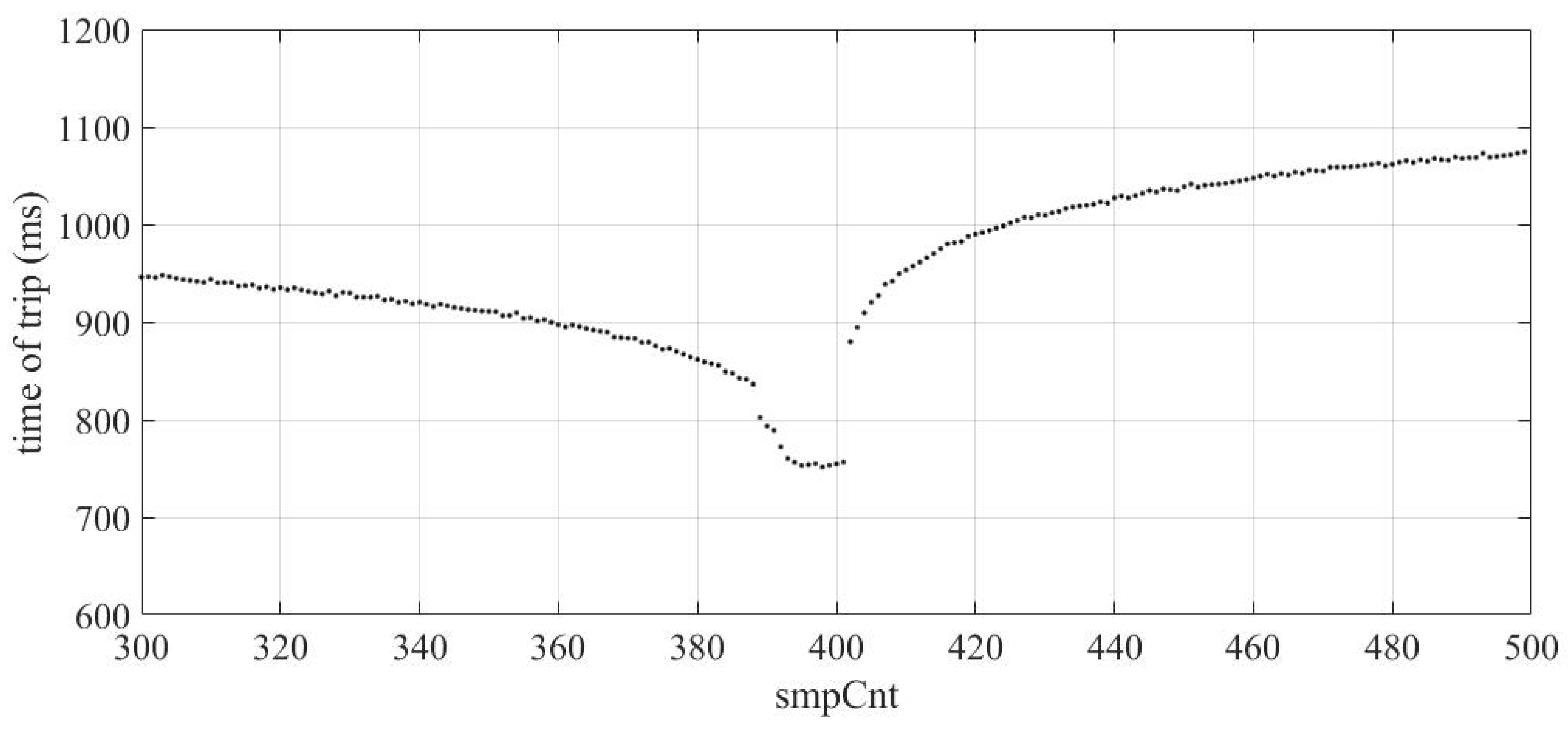
2.1.4. SmpCnt Manipulation
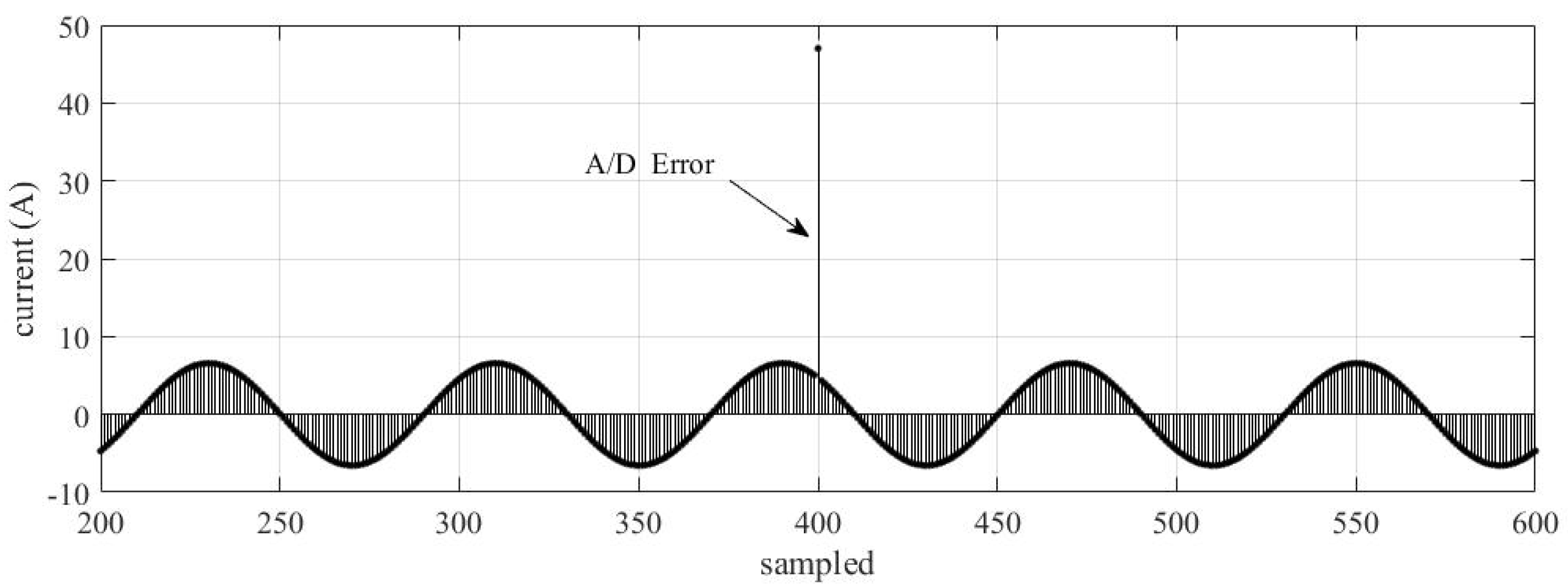
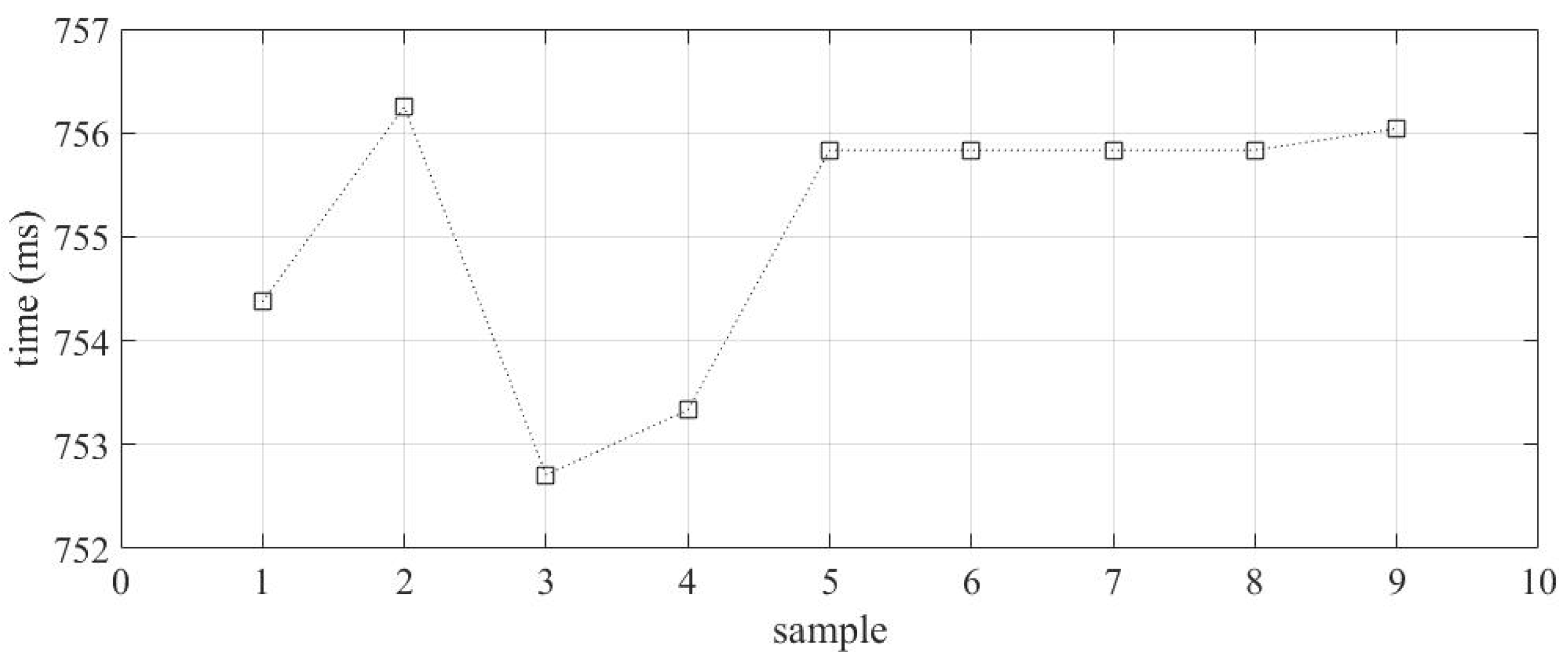
2.1.5. A/D Error
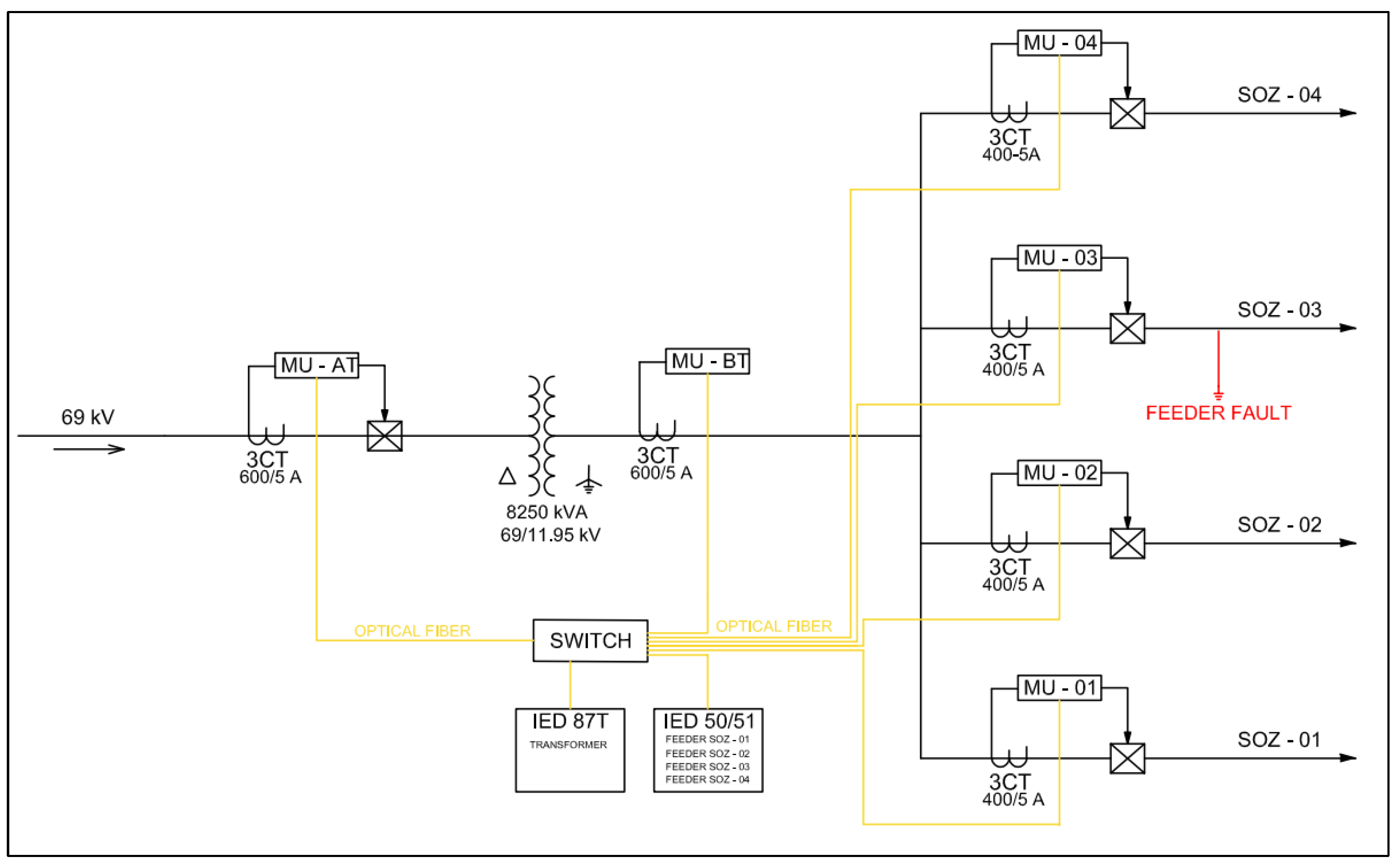
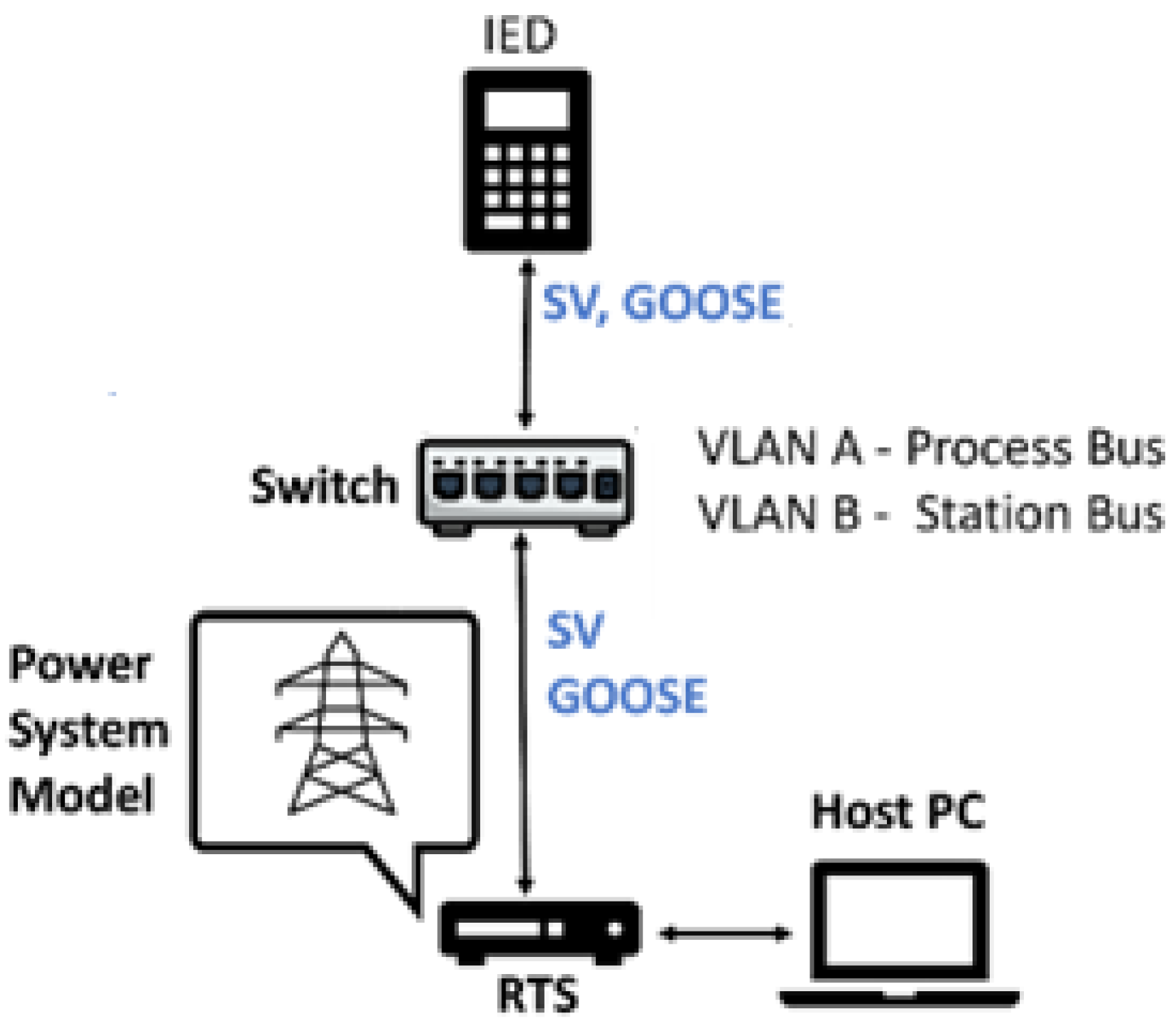
3. Methodological Procedure
4. Results
4.1. Instantaneous Overcurrent Element (ANSI 50)
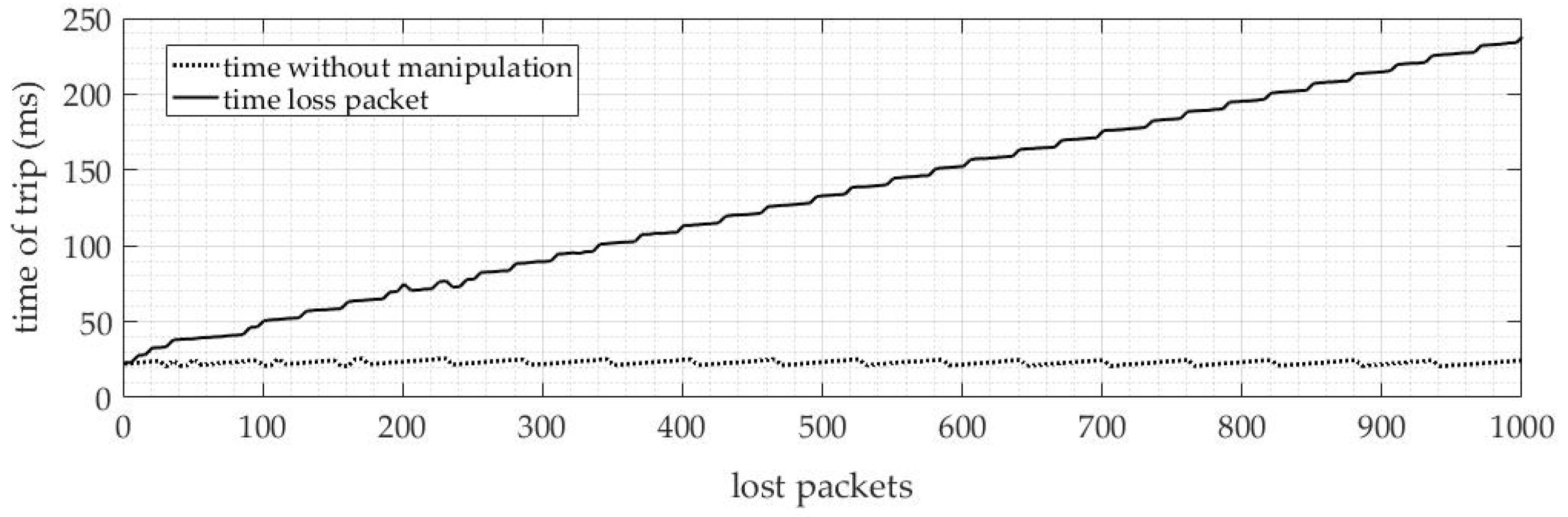
4.1.1. Packet Loss
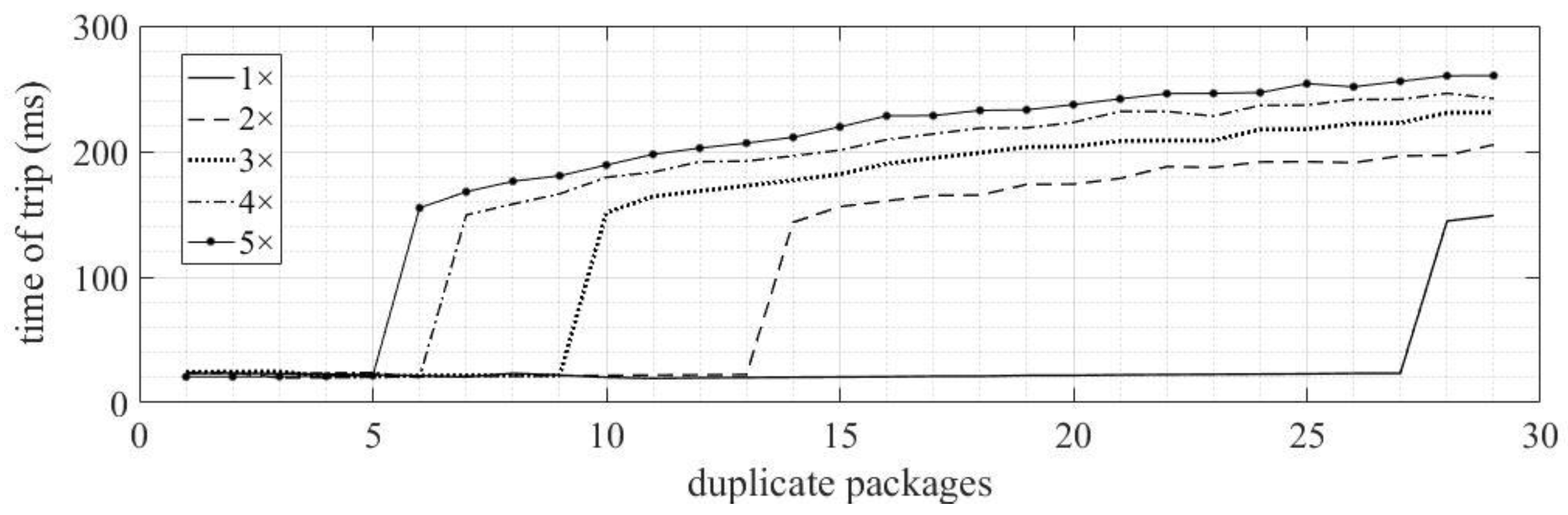
4.1.2. Duplicated Packets
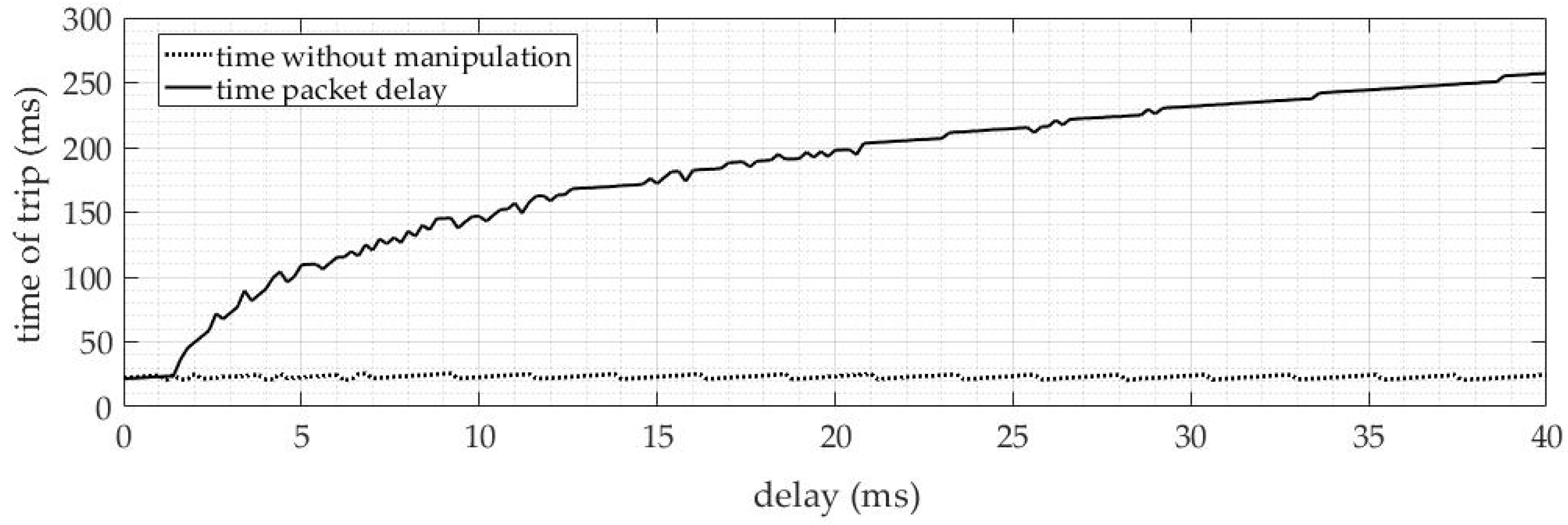
4.1.3. Delayed Packets
4.1.4. SmpCnt Manipulation
4.1.5. A/D Error on MU
4.2. Inverse Time-Overcurrent Element (ANSI 51)
4.2.1. Loss of SV Packets
4.2.2. Duplicate Packets
4.2.3. Delayed Packets
4.2.4. SmpCnt Manipulation
4.2.5. A/D Error
5. Comparative Manipulation/Protection
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Bhattacharjee, T.; Jamil, M.; Alotaibi, M.A.; Malik, H.; Nassar, M.E. Hardware Development and Interoperability Testing of a Multivendor-IEC-61850-Based Digital Substation. Energies 2022, 15, 1785. [Google Scholar] [CrossRef]
- Mirzoevich, B.G.; Kholnazarovich, M.S.; Nazrimadovich, I.O.; Ayombekovich, R.O. Review of Modern Methods for Busbar Protection Implementation. In Proceedings of the 2020 International Youth Conference on Radio Electronics, Electrical and Power Engineering (REEPE), Moscow, Russia, 12–14 March 2020; pp. 1–6. [Google Scholar]
- Adewole, A.C.; Tzoneva, R. Impact of IEC 61850-9-2 Standard-Based Process Bus on the Operating Performance of Protection IEDS: Comparative Study. In Proceedings of the 19th World Congress, Cape Town, South Africa, 24–29 August 2014. [Google Scholar]
- Song, M.-H.; Kang, S.-H.; Lee, N.-H.; Nam, S.-R. IEC 61850-Based Centralized Busbar Differential Protection with Data Desynchronization Compensation. Energies 2020, 13, 967. [Google Scholar] [CrossRef]
- Hong, J.; Ishchenko, D.; Kondabathini, A. Implementation of Resilient Self-Healing Microgrids with IEC 61850-Based Communications. Energies 2021, 14, 547. [Google Scholar] [CrossRef]
- Firouzi, S.R.; Vanfretti, L.; Ruiz-Alvarez, A.; Hooshyar, H.; Mahmood, F. Interpreting and Implementing IEC 61850-90-5 Routed-Sampled Value and Routed-GOOSE Protocols for IEEE C37.118.2 Compliant Wide-Area Synchrophasor Data Transfer. Electr. Power Syst. Res. 2017, 144, 255–267. [Google Scholar] [CrossRef]
- IEC. IEC 61850: Communication Networks and Systems for Power Utility Automation; IEC: Geneva, Switzerland, 2013. [Google Scholar]
- Kim, M.-S.; Kang, S.-H. Centralized Multiple Back-Up Protection Scheme with Sharing Data between Adjacent Substations Based on IEC 61850. Energies 2022, 15, 4195. [Google Scholar] [CrossRef]
- Apostolov, A. The Impact of IEC 61850 on Transmission and Distribution Substations Busbar Protection. In Proceedings of the 12th IET International Conference on Developments in Power System Protection (DPSP 2014), Copenhagen, Denmark, 31 March–3 April 2014; pp. 1–6. [Google Scholar]
- Memon, A.A.; Kauhaniemi, K. Real-Time Hardware-in-the-Loop Testing of IEC 61850 GOOSE-Based Logically Selective Adaptive Protection of AC Microgrid. IEEE Access 2021, 9, 154612–154639. [Google Scholar] [CrossRef]
- Westman, J.; Hadidi, R.; Fox, C.; Leonard, J.; Harrell, A. Controller Hardware-in-the-Loop Testing of an IEC 61850 GOOSE Based Control for Seamless Transition of a Microgrid Between Island and Grid-Connected Modes. IEEE Trans. Ind. Appl. 2021, 57, 61–69. [Google Scholar] [CrossRef]
- Patil, M.; Bhide, S.R.; Bhat, S.S. Experimenting with IEC 61850 and GOOSE Messaging. In Proceedings of the 2017 4th International Conference on Power, Control & Embedded Systems (ICPCES), Allahabad, India, 9–11 March 2017; pp. 1–6. [Google Scholar]
- Habib, H.; Fawzy, N.; Brahma, S. Hardware in the Loop Testing of a Protection Scheme for Microgrid Using RTDS with IEC 61850 Protocol. In Proceedings of the 2020 IEEE Industry Applications Society Annual Meeting, Detroit, MI, USA, 10–16 October 2020; pp. 1–8. [Google Scholar]
- Shoaib, M.; Vanfretti, L. Performance Evaluation of Protection Functions for IEC 61850-9-2 Process Bus Using Real-Time Hardware-in-the-Loop Simulation Approach. In Proceedings of the 22nd International Conference and Exhibition on Electricity Distribution (CIRED 2013), Stockholm, Sweden, 10–13 June 2013; pp. 1–4. [Google Scholar]
- Kang, B.; Maynard, P.; McLaughlin, K.; Sezer, S.; Andrén, F.; Seitl, C.; Kupzog, F.; Strasser, T. Investigating Cyber-Physical Attacks against IEC 61850 Photovoltaic Inverter Installations. In Proceedings of the 2015 IEEE 20th Conference on Emerging Technologies & Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar]
- Mocanu, S.; Thiriet, J.-M. Real-Time Performance and Security of IEC 61850 Process Bus Communications. JCSANDM 2021, 10, 1–42. [Google Scholar] [CrossRef]
- Kanabar, M.G.; Sidhu, T.S.; Zadeh, M.R.D. Laboratory Investigation of IEC 61850-9-2-Based Busbar and Distance Relaying with Corrective Measure for Sampled Value Loss/Delay. IEEE Trans. Power Deliv. 2011, 26, 2587–2595. [Google Scholar] [CrossRef]
- Hariri, M.E.; Youssef, T.A.; Habib, H.F.; Mohammed, O. Online False Data Detection and Lost Packet Forecasting System Using Time Series Neural Networks for IEC 61850 Sampled Measured Values. In Proceedings of the 2017 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 23–26 April 2017; pp. 1–5. [Google Scholar]
- Yu, L.; Zhang, S.; Wu, N.; Yu, C. FPGA-Based Hardware-in-the-Loop Simulation of User Selection Algorithms for Cooperative Transmission Technology Over LOS Channel on Geosynchronous Satellites. IEEE Access 2022, 10, 6071–6083. [Google Scholar] [CrossRef]
- Bian, D.; Kuzlu, M.; Pipattanasomporn, M.; Rahman, S.; Wu, Y. Real-Time Co-Simulation Platform Using OPAL-RT and OPNET for Analyzing Smart Grid Performance. In Proceedings of the 2015 IEEE Power & Energy Society General Meeting, Denver, CO, USA, 26–30 July 2015; pp. 1–5. [Google Scholar]



| Type of Manipulation | Description | |
|---|---|---|
| 1 | Stop transmission | Simulate the loss of packets on the network by stopping the SV publishing during a certain number of frames. |
| 2 | Delay transmission | Simulate an unwanted delay on the network by delaying the frames for a specified amount of time, in us. |
| 3 | Duplicate transmission | Simulate a wrong network topology where packets could be sent multiple times by duplicating frames for a certain number of frames. |
| 4 | smpCnt manipulation | Simulate an IED clock reset by manipulating the smpCnt of a given frame. |
| 5 | smpSynch manipulation | Simulate a loss of synchronization by manipulating the smpSynch of a stream for a certain number of frames. |
| 6 | Quality manipulation | Simulate a change in the IED performance by manipulating the quality of the voltage and cur-rent values in a stream. |
| 7 | A/D error | Simulates an error in the analog/digital (A/D) converter of a Merging Units. |
| Parameter | Phase | Neutral |
|---|---|---|
| Pickup current (51) | 400 A | 120 A |
| Pickup current (50) | 2400 A | 2000 A |
| Curve types | IEC standard inverse (C1) | IEC standard inverse (C1) |
| Time dial | 0.15 | 0.30 |
| CT raio | 400/5 A | 400/5 A |
| Gain in Error | Operation | Current Error (A rms) |
|---|---|---|
| 100 | correct | 9.23 |
| 500 | correct | 31.96 |
| 1000 | correct | 60.96 |
| 2000 | correct | 118.8 |
| 5000 | correct | 294.7 |
| Gain in Error | Operation | Error Current rms (A) |
|---|---|---|
| 100 | correct | 9.18 |
| 500 | correct | 31.97 |
| 1000 | correct | 60.80 |
| 2000 | correct | 121.4 |
| 5000 | correct | 297.6 |
| Error | ANSI 50 | ANSI 51 |
|---|---|---|
| Loss Packets | affected | affected |
| Duplicate Packets | affected | affected |
| Delay Packets | affected | affected |
| smpCnt manipulation | affected | affected |
| A/D Error | Unaffected | Unaffected |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sartori, Â.F.; de Morais, A.P.; Netto, U.C.; Lima, D.A.C.; Bernardon, D.P.; Hokama, W.S. Performance Analysis of Overcurrent Protection under Corrupted Sampled Value Frames: A Hardware-in-the-Loop Approach. Energies 2023, 16, 3386. https://doi.org/10.3390/en16083386
Sartori ÂF, de Morais AP, Netto UC, Lima DAC, Bernardon DP, Hokama WS. Performance Analysis of Overcurrent Protection under Corrupted Sampled Value Frames: A Hardware-in-the-Loop Approach. Energies. 2023; 16(8):3386. https://doi.org/10.3390/en16083386
Chicago/Turabian StyleSartori, Ângelo Felipe, Adriano Peres de Morais, Ulisses Chemin Netto, Diomar Adonis Copetti Lima, Daniel Pinheiro Bernardon, and Wagner Seizo Hokama. 2023. "Performance Analysis of Overcurrent Protection under Corrupted Sampled Value Frames: A Hardware-in-the-Loop Approach" Energies 16, no. 8: 3386. https://doi.org/10.3390/en16083386
APA StyleSartori, Â. F., de Morais, A. P., Netto, U. C., Lima, D. A. C., Bernardon, D. P., & Hokama, W. S. (2023). Performance Analysis of Overcurrent Protection under Corrupted Sampled Value Frames: A Hardware-in-the-Loop Approach. Energies, 16(8), 3386. https://doi.org/10.3390/en16083386






