1. Introduction
The use of new information technologies (IT) in different environments in which the development of society is most evident has had a considerable impact on the ways of life of many people. These are also considered to be emerging technologies since they have had to combine several ideal situations in order to demonstrate their potential [
1]. Some examples are technologies such as the Internet of Things (IoT), big data, and cloud computing. These technologies are recognized as key elements of the vertiginous development that society has undergone. Through these technologies, the ways in which we communicate, work, learn and, in general, the ways in which we live have been improved. These outcomes have had a positive impact on people’s quality of life [
2]. Technology provides tools that are exploited by different segments of society and help to improve processes or control actions that are generally carried out by one or more people.
Technological progress is reflected in the development of society and in the ways in which we live. The ecosystems by which society develops have changed so much that the use of IT is now essential to ensure their sustainability [
3]. The relationship that exists between people and nature is framed as an issue with regard to the proper use of resources. However, dealing with such an issue within a society requires great effort and the deployment of technological infrastructures that cities and countries are not willing to implement due to the high costs involved. However, it is essential that such a development takes place, and one way to achieve this is to delegate innovation, creation, implementation, and testing to small environments. These environments must be controlled and possess a resemblance to environments such as large cities [
4].
The new approach to and understanding of technology in society has transformed the concept of an environment by introducing the concept of digital or, as they are more commonly known, intelligent environments. An example of this is the smart city, which gradually delegates the monitoring and control of certain variables to IT. Similarly, universities are gradually becoming intelligent campuses, and technology is becoming the main element in their development. The government of a university is similar to that of a city, whereby those responsible are forced to take on technological challenges in order to meet the needs of their members [
5]. However, even the concept of satisfaction of needs has changed in that services must now be adapted to the user by personalizing them to the point that user satisfaction is measured in terms of the quality of the product or service, and their experience within the environment [
6]. It is in this way that universities have become ideal places for the evolution of digital environments that can be replicated in larger environments, reducing economic problems and encouraging or facilitating infrastructure deployment.
One of the most common problems in these environments is that deficiencies in process management can lead to missed opportunities or economic losses. The management of processes in the administration of a university can focus on two aspects—the management of physical resources and that of academic resources [
7]. The management of physical resources is responsible for enabling the university environment to implement an educational model. The management of academic resources has a deeper connotation because there are variables that can be used to measure the development of learning. The management of these variables includes the discovery of paradigms such as detecting the learning habits of students [
8].
This work focuses specifically on improving the management of administrative processes in a university through the use of the IoT. The characteristics of the IoT make this technology one of the most successful in terms of improving different management models, and it is based on improving the user experience. The fields of action of the IoT in a university are varied, and it is necessary to define the advantages and disadvantages of its application in these various fields [
9]. On the one hand, the IoT has the ability to interact with users and facilitate their work, as well as the ability to control environments through the use of sensors and actuators. On the other hand, a topic that is currently attracting a great deal of attention is the management of information; it is well known that the implementation of the IoT in architectures that do not have appropriate security measures in place can lead to problems [
10].
One of the specific problems associated with universities is the lack of a flexible system for reserving spaces. For example, although it should be an easy action to perform, reserving a classroom or laboratory can be a difficult process [
11]. Sometimes, universities have obsolete systems that are not user-friendly, or processes by which requests must be approved by a certain area or person. There are extreme cases wherein the university may not have a system that allows the reservation of spaces. Consequently, in terms of a flexible system, the IoT can present a solution in the form of virtual assistants or voice assistants that, through a conversation with the user, can manage the entire space reservation process [
12]. Another problem associated with universities is campus security; due to the high attendance at a university, a large number of people are required to provide information and ensure the safety of the people and infrastructure. The IoT in terms of university footfall is very useful and presents solutions ranging from sensors and cameras with recognition capabilities to embedded systems that include artificial intelligence models [
13,
14]. This paper proposes an IoT model capable of interacting with the university administration to improve the management of both space reservation and security.
The work is distributed according to the following sections:
Section 2 presents the method, in which the development of the system is carried out is explained step by step.
Section 3 presents the results collected from the development of the proposal.
Section 4 contains the discussion based on the results finally obtained and
Section 5 presents the conclusions and future work.
2. Materials and Methods
For the development of the IoT model, it is important to know the environment in which it is intended to be applied, as well as the infrastructure of the campus in which the university carries out its activities [
15]. A university campus has features that can be exploited or reused by the IoT architecture. Therefore, to guarantee its operation, it is necessary to guarantee navigation. Within the campus, this can become a problem since the services are on an intranet, and for them to leave, they must go through the network security layer [
16]. In this layer, both inbound and outbound access to the network is filtered and monitored. This process causes navigation to be restricted, with port blockages in place to maintain network security [
13]. Such restrictions and blockages can directly affect the IoT devices that are being applied to the campus by subtracting them from functionalities or rendering them useless. To avoid any problem in the design of the model, it is important to identify the IoT requirements and the network architecture available to the university under consideration [
17].
The IoT requirements established for the proposed model are as follows:
Security: IoT introduces new security risks and challenges at the level of devices, platforms, operating systems, communications, and connected systems [
18]. IoT security is even more complicated in dealing with basic “things” that do not allow sophisticated security mechanisms.
IoT analytics: IoT business models exploit the information collected from things in many ways in order to understand customer behavior, improve products, and provide new services [
19]. IoT requires new analytical approaches involving new tools and algorithms [
20].
Management of IoT devices: things require management and monitoring of the device, the firmware, software updates, reporting, and security management. Therefore, the tools must be scalable for thousands and millions of devices [
21].
Low-power and short-range networks: selecting a wireless network for an IoT device requires balancing various contradictory requirements such as battery life, bandwidth, range, device costs, operational costs, etc. Such low-power and short-range networks dominate IoT wireless connectivity [
22].
IoT processors: processors and architectures for IoT devices define their capabilities. The different characteristics sought, hardware cost, software cost, updates, and encryption must be considered.
2.1. Architecture of a University Campus
In general, university campuses have a layered network architecture that guarantees scalability and modularity.
Figure 1 identifies the layers of the architecture of a university campus, the first of which is the access layer that is responsible for providing services to end-users [
23]. The distribution layer provides policy-based connectivity and controls the boundary between the access and the core layers. The core layer provides fast transport between distribution switches within the campus [
24]. The benefit of dividing a flat network into smaller and easier to manage blocks is that local traffic remains local. Only traffic destined for other networks is moved to a higher layer.
The proposal for the IoT model applied to a university is based on the one proposed in [
25] that starts from a network architecture, as presented in
Figure 2. It should be considered that any increase in IoT devices will affect the performance of the network. Certainly, in a traditional campus network, the performance of wireless networks suffers. With the inclusion of devices that use the wireless medium as the main communication channel, the problems increase. However, this problem can be overcome by updating the network or even integrating a network that specifically handles the connectivity of IoT devices [
26].
The proposed IoT solution for the management of certain processes and resources of a university necessarily responds to a distributed technological architecture, where the devices can interact with each other in a scalable, flexible, robust, efficient, and secure way [
18]. For this purpose, it is proposed to apply the basic IoT architecture adapted to the requirements of a university environment. These requirements relate to connectivity and communication, the management and control of devices, as well as data collection and analysis [
27]. This architecture responds to the needs of the university that is considered in this paper, with the requirements of each of the three layers being easily solved by the infrastructure owned by the university.
Figure 2 shows the IoT architecture based on the three-layer model.
2.1.1. Perception Layer
This layer contains the devices that monitor or act on the environment. There are several types of devices, but those considered with regard to the IoT have the characteristic of responding to a type of communication (direct or indirect) that links it to the Internet [
28]. Such a system has the ability to integrate sensor type devices that allow them to measure parameters such as temperature, position, amount of light, etc. They incorporate actuators that transform energy into action in order to automate a process [
29]. These IoT-oriented devices are recognized as intelligent sensors in that, in addition to obtaining the value of the physical parameters which they measure, they can perform other functions. Most of these devices connect through wireless communication which enables autonomous interactivity between devices even if they are in motion [
30].
Other devices used in this layer are smart tags which allow the university to trace the entire administrative process. For example, in order to allow the university to properly manage the laboratory equipment that students use, it is necessary to answer questions such as where and when has laboratory equipment been provided? Who has lent it? Which equipment is the most frequently used? To answer such questions, it is necessary for the university to capture the relevant data and track the time it is used, using its trace and added features. There are several types of smart tags available, the best known of which are barcode labels and QR codes [
8].
2.1.2. Network Layer
The network layer is responsible for connecting smart devices to one another or to network devices or servers. This layer has sufficient tools and protocols to allow the transmission of data between devices or servers [
31]. Depending on the requirements in each location, several of the traditional communication protocols remain in effect in the IoT, such as local network connections via Ethernet or wireless transmission through mobile connectivity. In larger environments, the operability depends on the connection speeds allowed by the new protocols such as 5G. These are the basis of the long-range connectivity of the IoT [
32].
In the university considered, in addition to the traditional protocols, the protocols that have been designed with respect to the IoT and the communication between devices and services are also used. An example is NFC or Bluetooth 4.0, which are part of the low energy provision precisely because they are intended to be implemented in systems with reduced batteries. Making the physical connection between the end devices is not sufficient to enable effective communication [
33]. For such communication to occur, devices must know how to communicate.
Figure 3 shows the necessary components that are needed in order to establish effective communication. Communication begins with a message, or information, which is sent from a source to a destination. This process is governed by protocols that must be respected so that the message is sent and understood correctly. Communication protocols include tasks such as encoding that are responsible for converting information into an acceptable form for transmission [
34]. This task includes decoding which involves reversing the coding process so that the information is interpreted correctly. The way in which this task works is that the sending device converts messages sent over the network into bits. Each bit is encoded in a pattern of sounds, light waves, or electronic impulses, depending on the network medium used. The host or destination device receives and decodes the signal in order to interpret the message. In addition to this process, the communication task in an IoT environment is governed by a common communication model in a particular data medium. The protocols that govern it are the format and encapsulation of the message, the frame size, segmentation, message timing, flow control, response timeout, and message delivery options.
2.1.3. Application Layer
In terms of the application layer within the university, the IoT takes advantage of the wireless technology that has already been implemented to connect and improve the infrastructure, efficiency, convenience, and quality of life of those involved [
35]. This has allowed the application of this technology in the management of supplies, which in turn implies managing spaces and security within the university. Other applications can consider situations in greater depth, such as the monitoring and notification of air quality through embedded systems.
There are a variety of applications that can apply to other environments and can be applied to the reality of a university environment. However, this architecture has the main objective of being applied in such a way that the university can take the next step and become an intelligent campus [
11]. The IoT contributes to this step with the inclusion of devices that monitor and evaluate each variable that is generated in a university. Integrating this technology with cloud computing and big data enhances this architecture and improves the learning environment.
2.2. IoT Model for Process Management
To generate an IoT model that improves the management of processes within a campus, it is necessary to identify the requirements that exist in the areas that manage resources. By establishing both the network architecture of a university and the basic IoT architecture, it is possible to generate a model that is born from the needs that arise in the management of the administrative processes of the university.
Table 1 establishes the requirements which the proposed model can meet [
36]. In the first column, the processes that are carried out on the university campus are identified. Seven processes that have been reported by the members of the university were chosen as those that present the greatest difficulty in terms of management. The channel column corresponds to the way in which each process is executed—either through a computer system or through the assignment of the task to a person. The effectiveness column evaluates the execution of the process in terms of it being high, medium, or low [
37]. The availability column shows how the processes can be requested and assigned; two means have been established as a local process. This indicates that the process can be executed only within the university and for this particular purpose when the intranet is used. External availability means that the process can be executed outside the university’s internal network. This includes the use of the Internet or virtual private networks (VPNs).
Given these requirements, it is possible to establish a model that allows each process to be improved through the use of IoT devices. A reading that helps us to understand how each process in the table is carried out is as follows. To reserve a space in the university and to develop a specific activity, a member of the university—a teacher, administrator, or student—must enter the computer system to register and request the reservation. The system verifies the availability and approves the request, with several similar systems depending on a person who is responsible for giving priority to a certain event, depending on the type of activity [
11]. This creates several problems for people who need space to perform extra activities or set up an event.
However, through its devices, is the IoT capable of improving this process, eliminating the dependence of a third person, and speeding up the reservation? To answer this question, it is important to establish a model that is capable of handling information in the computer system but is also capable of improving aspects such as user interaction. A consideration of user experience is sometimes necessary in an IoT solution. For this, it is important to go further in the service [
8]. If the above example is taken as a basis for establishing the IoT model, it is proposed that, in addition to reserving a space, the system is responsible for notifying all persons who are part of the event of the place and the time where the event is going to be carried out [
38].
In
Figure 4, a performance representation using a traditional model is presented for the request of a process and is compared with the proposal using the model that uses the IoT.
Figure 4a represents the traditional model, and
Figure 4b represents the process management model used by the IoT. This figure indicates that the IoT model has a certain similarity to the traditional model. However, there are differences in the components of the former that makes them totally different. In
Figure 4a, the process starts when the user registers in the system to generate a request. The data are validated and, if they are correct, the computer system starts the interface to register the request process. The system verifies availability. If there is no availability, the system terminates the request. If the system finds that there is availability, it sends the request to the administrator who is responsible for validating the availability for verification who, based on specific criteria, decides on the importance of the event and approves or denies the request [
39].
As shown in
Figure 4b the process starts with the user registration. If the validation is wrong, the model again requests the data from the user. If the registration is correct, the user initiates the request through the IoT devices. These can be voice assistants or virtual assistants that respond to artificial intelligence (AI) models [
40,
41]. The application is processed based on the analysis of data from the different sources in the university [
42]. For this, it is possible to use business intelligence (BI) or big data architectures [
43,
44,
45]. Data analysis architectures can be run in local environments, or they can make use of cloud computing, depending on the IoT devices and services available. Based on the results of the analysis, the model is able to determine the availability in order to execute the process. In the event that there is no availability, the model feeds back and interacts with the user, proposing other options in an attempt to satisfy their request [
46]. On the other hand, if there is availability, the model is responsible for sending notifications to those interested in the activity or the process that is to be executed. With regard to additional events, the user is always consulted to define them as complementary tasks. Once the action is executed, the system again interacts with the user to make one or more additional requests. If there is no additional order, the system closes. However, since each request is scheduled and notified, the model is in constant communication with the user.
3. Results
The model, within the architecture of the university, has been evaluated through several systems. The environment considered for this improvement is the management of spaces through the use of a voice assistant and the physical security systems of the university campus. To this end, devices such as sensors, actuators, and various systems contribute to the collection of data that help administrators to monitor and control the environment.
3.1. Space Management through Voice Assistants
Usually, the management of spaces in a university is carried out by an interested party who can be a teacher or an administrator. In the case of a teacher, they usually request a specific laboratory or classroom to carry out activities such as classes, seminars, workshops, etc. Using their profiles, administrators can reserve a space such as a meeting room, office, etc. Due to the large number of events and activities in a university setting, all these spaces generally present problems of availability.
The model used to execute a request is a computerized reservation system. This system registers a request, but this is susceptible to changes by an administrator, who verifies the suitability and importance of the event before executing it [
47]. This model works, and the user adapts to it. However, the process can be improved to make it more efficient. One aspect that needs to be improved is the availability of the service because the process can only be accessed locally through the intranet of the university participating in the study. Another area that needs to be improved is the interaction with the user. Technological advances force the system to make use of personal assistants whose use transforms the user experience into a positive one. Finally, what is expected of the model is that it takes care of the whole process, from the making of the request to facilitating the notification of the event to those interested.
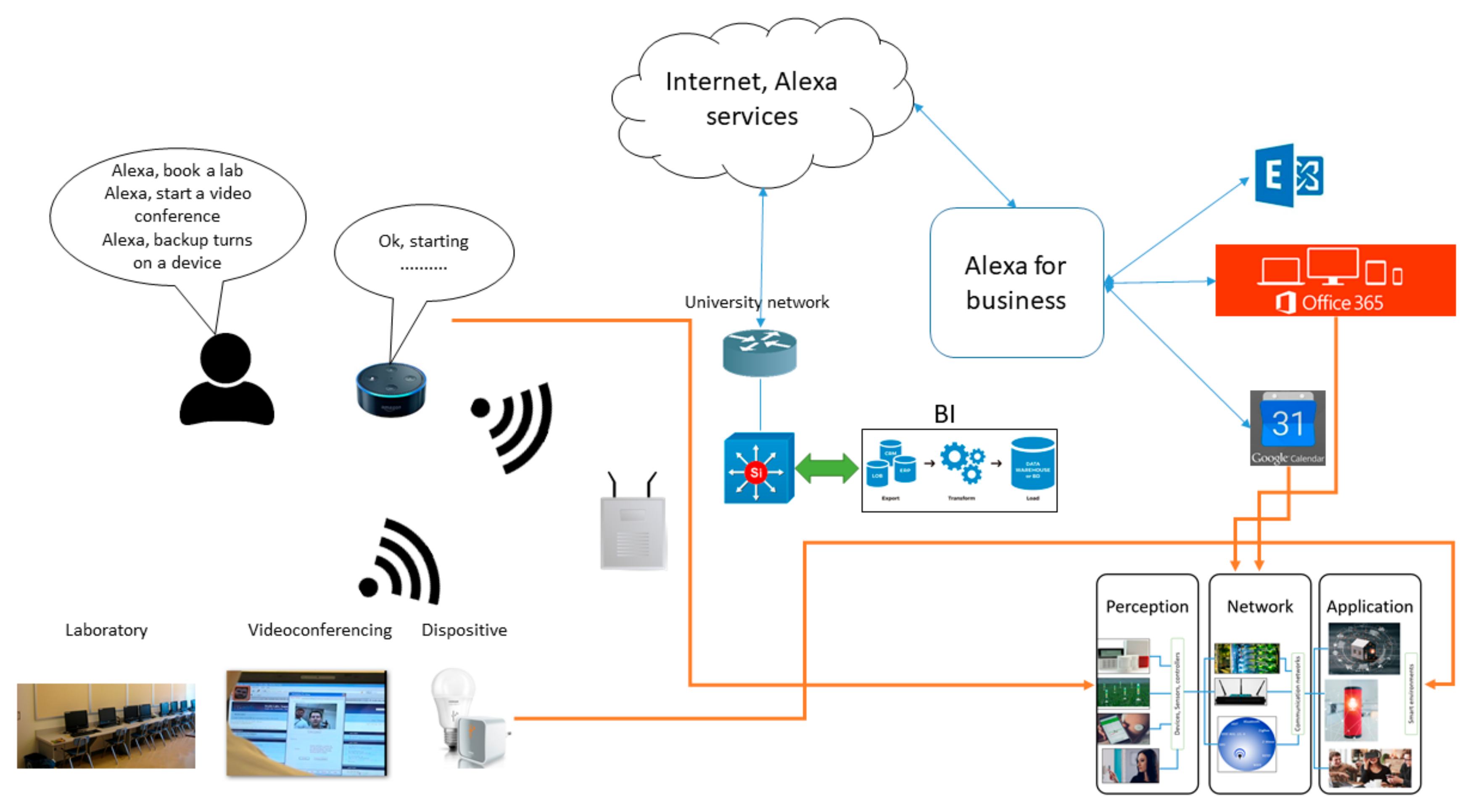
In
Figure 5, it is possible to see how the model works and the devices it uses. The model uses voice assistants that use Amazon Echo (Alexa) technology. These devices are currently used in homes or offices in order to perform a range of tasks such as managing several devices that use the Amazon protocol to performing a specific action [
48]. The capacity of these devices and the facilities which they present for the generation of skills mean that these devices can carry out several complicated tasks at once and provide access to different sectors of society.
For this work, an application has been generated that connects to the database that is responsible for registering space reservations. In addition, the system also uses the results of a BI. This platform is responsible for verifying the availability of each of the spaces that the university has available and gives weight to the importance of each event. Weights are assigned based on the number of attendees, the number of people outside the university attending the events, the number of exhibitors, and whether these are external or internal. These are some of the parameters that the BI uses to define the importance of an event in order to allow it to allocate the appropriate space efficiently [
49]. The interaction with the applicant takes place in natural language and uses voice recognition to determine who the applicant is and his/her profile. Once the system has all the data it requires, Alexa Echo takes control and makes available to the applicant all the options for the proposed reservation, such as day, time, available rooms, etc. The user interacts with the device according to their needs and the options presented by the model, as would traditionally be done by a human assistant.
Once the space has been reserved, the device asks the user if it should send a notification to the interested parties and to make the agenda for the event. If the response is positive, the system immediately sends a notification via email using Office 365 and adds the event data to the calendar of each interested party. The use of this technology improves the user experience while at the same time reducing the personnel needed to perform this process.
Figure 5 aligns each of the components of the model with the components of the university campus architecture. The model even allows the university to make reservations or launch a videoconference immediately. This is part of the reservation process with regard to available spaces, and it also presents an option for certain events. To improve availability, Amazon’s cloud services are used to perform cloud computing processes such as voice profile identification. To send notifications and to record events on the calendar, the system uses the Office 365 services in the cloud [
50]. The BI platform runs locally and uses the infrastructure of the university in order to provide high availability and scalability in terms of the data handled by the system to identify the necessary parameters for registration.
3.2. Physical Security through the Use of IoT Devices
Security within a university relates to both the assets of the institution and the people who are part of it. However, guaranteeing the levels of security required by a university campus involves a high cost due to the amount of specialized personnel required to cover all areas of the campus. A novel alternative that contributes to this field is the IoT, where the capacity of the devices and online communication allows the university to reduce costs and improve the universal security of the campus [
51].
In terms of the management of assets, various means of control have been deployed to improve this aspect within the university. For example, a variety of network equipment such as routers, switches, access points, firewalls, etc. is available in communication engineering laboratories. This equipment is for academic use, where students participate in internships and simulate real environments. The problem is that there is not adequate control in terms of the use of such equipment, given the existing amount of personnel and the number of laboratories [
52]. As a control measure, the university has integrated personnel in order to control its assets. However, the loss percentages have not been reduced, and its management has been exceeded by the volume of requests for use of the equipment.
The solution has been supported by the use of the IoT and the implementation of active tags. These devices emit a signal that is read by antennae to verify their position and status. This system has an advantage over other types of control and does not require a direct view between the transmitter and the receiver of the signal. Therefore, radio frequency identification (RFID) guarantees unequivocal identification in order to provide immediate monitoring and location, allowing the “visibility” of the asset in real time [
53].
In addition to tracking, this identification allows the system to access all the information related to that particular asset. Regarding the control of physical facilities, the antennae are located throughout the university campus and allow the system to monitor the exact location of the asset. The data generated from these systems are stored in a cloud computing model, which allows the university to manage historical usage and to identify the most frequently used equipment in different class periods. In addition, the total connectivity of the university campus allows the university to upload data to a public cloud, providing greater accessibility to those in charge of the administration of the equipment.
In the university under consideration, laboratories have installed optical readers to read the value of the label attached to each item of equipment and to send it to a computer that stores the information in a database. This information depends on the policies established by each university but generally includes sensor values, meter readings, energy values, and device identification. Another type of device used is RFID tags, each of which has a chip and an antenna that allows the user to write information by using an RFID reader/receiver, without the need for direct contact between the two. The RFID chip stores the identification number of each piece of equipment and even stores maintenance history data [
54]. In this way, asset managers, as well as laboratories, know the complete traceability of any device, equipment, or asset using a reader. RFID technology is also applied in other areas of the university. Some of this helps with administrative management, others with security, and others with learning. In terms of administrative management, in addition to asset management, it facilitates the inventory of machines and computer equipment for security purposes. It is also used in access control identification and the location of personnel. In learning, it facilitates the use of resources such as library management [
33].
Other IoT devices used are embedded systems. These devices perform dedicated and real-time functions. Contrary to what has happened in the case of common computers which are designed to cover a wide range of needs, embedded systems are designed to meet specific needs and are therefore part of a multitude of products that require a certain process power, including appliances, vehicles, machines, etc. Embedded systems are used within the university to generate safe environments such as access to restricted areas through facial recognition. In laboratories, these devices are used as support for learning when creating practices within teams, where students can monitor and control different variables in order to improve their understanding and knowledge of various technologies.
In terms of access to restricted areas, facial recognition is used to determine access to the university campus data center. Such control is vital because of the value of the available information. For this purpose, Azure APIs from the web application and universal windows platform UWP are used under the scheme detailed in
Figure 6. The components used are a webcam installed at the entrance of the area to be controlled, which is connected to an embedded system (Raspberry Pi 3, model b), which has the necessary programming for the proper functioning of the equipment [
55]. The Raspberry connects wirelessly to the university network which it uses as a gateway and connects to the Face API services and Azure SQL database.
The objects that manage access to the data center are created in the database, among which are the users with their roles and profiles [
56]. This database handles a connection to a web page developed in ASP.NET with C # language that is responsible for user administration and a universal Windows platform (UWP) application that is physically installed in the data center. The application is divided into three components—model, view, and controller (MVC). MVC is a software architecture pattern which separates the data and business logic of an application from its representation and from the module responsible for managing events and communications. It defines components for the representation of information on one hand and for interaction with the user on the other.
For this, the system incorporates several verification processes including, in the first instance, the need for the vehicles of officials and students who have access to the campus to undergo a due registration process. The objective is to identify the characteristics of both the vehicle and the person to whom it belongs, in order to generate the roles, profiles, and accesses that each user has. Campus access is controlled by cameras that meet IoT requirements. Once a car enters the vehicle detection zone, it activates the software in the camera that verifies the vehicle’s license plate. The camera sends the data to the access controller at the entrance which verifies the approved plates in the database and decides whether or not to grant access. If the license plate is not approved for access, the monitoring staff will decide whether or not to allow access to the campus. Transaction data describing the event are recorded and stored and can be used in a data analysis stage.
4. Discussion
Similar studies focused on productive sectors such as manufacturing or agriculture have considered the potential of the IoT. In smaller environments, IoT is applied to home automation by combining technology to generate automated and comfortable environments. However, there has been very little experience in the educational field and even less in learning. This is a topic that is currently being developed and is mentioned as an aspect of future work, because when it comes to emerging technologies, the development comes from large companies such as Microsoft, Cisco, and Amazon, among others. In addition, it is the task of academia to research topics such as the one developed in this paper. It is under these conditions that, in this work, technology has been adapted to a university environment. It has been pointed out that the communication and infrastructure technologies generally used by universities are similar in terms of their architecture. This work has great value because it indicates that the method used in the university under consideration can be considered a generic architecture that can be deployed in any type of university.
The deployment of the IoT carried out in this work does not include a consideration of a method of data storage and analysis. However, the findings converge with those of previous works where the concepts are complemented to the point that it is possible to discuss intelligent environments. The concept of intelligent environments depends largely on the ability of the user to analyze variables and make decisions efficiently and effectively. However, the first line that answers all the problems that require data analysis is the monitoring and acquisition of data through the IoT. It is here that this work is of great importance and becomes the cornerstone of a whole process such as the one mentioned. It is important to note that there are currently devices whose manufacturers offer accommodation in public clouds where even data analysis is performed. These solutions are not acceptable in a university context due to the importance of having centralized data in the university’s own infrastructure. The centralization of the data guarantees the location of the data and its security, while for the students, it expands their knowledge in terms of being able to visualize how they are generated and treated in a private cloud environment.
Having all the resources necessary to meet the needs of the university available to the university has allowed us to solve problems such as physical and resource security. Previously, the university under consideration has increased its budget considerably to guarantee the internal and external security of its facilities. The use of the IoT has reduced these costs, and people have seen their work improve by avoiding repetitive tasks or those that are considered to be of little value. This has given a boost to security specialists, who have seen how their work now focuses on the use of technology which leads to constant training, which opens up the possibility of continuous improvement.
The IoT is the ideal assistant for tasks that are framed to facilitate processes, so that both teachers and students develop in environments that are ideal for the generation of knowledge. The processes that involve the inclusion of the IoT have aroused great interest in the learning environment and the results have generated greater interest and acceptance regarding the use of IoT devices in academic areas. Another area that has welcomed the potential of the use of the IoT and this model in particular is the generation of content, and the integration of technology and learning that has resulted in m-learning. M-learning facilitates the construction of knowledge, problem-solving, and the development of diverse skills and abilities autonomously and ubiquitously, thanks to the mediation of portable mobile devices. This means that the content developed by the teachers are always available and readily accessible.
Future work should consider clearly establishing the levels of security that should exist within an intelligent university environment commonly known as a smart campus. These environments depend on the deployment of many devices and technologies, which in turn entails taking measures with regard to the management of information and establishing policies for its use.
5. Conclusions
In this work, we have responded to the problem that a university has in terms of administrative management. The deployment of the IoT has the ability to handle these environments without any restrictions, which opens up a world of possibilities when it comes to handling any event. As presented in the applications deployed at an IoT university, it helps to change the traditional models by which learning develops and how it develops. Universities that integrate these technologies into their administrative or academic management are better adapted to the current requirements and challenges that society presents.
The application of the IoT as an assistant helps the teacher in tasks such as the registration and control of attendance at classes and arranging academic events within the university. The detection of the presence of students in the classroom at the assigned time is a useful variable for purposes such as the early diagnosis of student dropout. In addition, it serves to identify students who are in danger of failing courses due to low attendance. For learning assessment departments, this system is useful for the registration of teachers in the classroom as part of their performance evaluation.
In response to the research question that initiated this article, in this work, the relationships between the university and the IoT with areas of learning and administrative management were identified. This serves to update and improve the technological infrastructure to improve processes and, with this, administrative management has benefited from being able to develop more and better applications with the support of a scalable infrastructure. Similarly, the university that participated in the study, which has seen the potential of the IoT applied to learning, has modified its academic programs to include topics related to the IoT. In this way, it prepares professionals with the skills and knowledge necessary to solve the new challenges that arise in today’s society.
The Internet of Things applied in a management model within a university helps to improve response times and user experience. It is important to realize the options for using this technology and to include it in deeper topics such as learning. With this work, the potential of the IoT has been proven in such an environment. In addition, its introduction has generated high expectations on the part of students. Welcoming students’ curiosity and directing them towards the use of the IoT will establish new opportunities for creating new skills, as well as innovation on the part of academics.
In terms of security, it is important to work in line with the rules and policies of each country. Therefore, information management is an issue that should be considered as a fundamental pillar in the implementation of the IoT. Having a model that guarantees the management of security generates confidence on the part of users, which allows for improvements in the interaction between devices and those who use them. It is also important to make known exactly how data are used and how work is begun to analyze them. This avoids confusion in terms of future problems that might incur penalties and misunderstandings between parties.