Two-Level Congestion Control Mechanism (2LCCM) for Information-Centric Networking
Abstract
1. Introduction
- This paper is the first paper to explicitly propose a two-level congestion control mechanism for ICN, where replica nodes will be changed to avoid congestion paths under heavy congestion, and only the request sending rate will be adjusted under light congestion. Specific definitions of heavy congestion and light congestion that distinguish the two-level mechanism are provided, and the switching strategy is discussed to reduce the transmission time.
- To implement the 2LCCM proposed in this paper, we further designed an NST-based replica selection method for selecting the most appropriate replica, a receiver-driven BBR congestion control algorithm applicable to ICN, and a detailed transport layer protocol.
- The experimental results show that switching replicas for successive transmission under heavy congestion can effectively shorten the transmission time, which verifies the effectiveness of 2LCCM. In addition, the results also show that the Bandwidth-Delay Product (BDP)-based BBR algorithm has better bandwidth utilization than a loss-based algorithm.
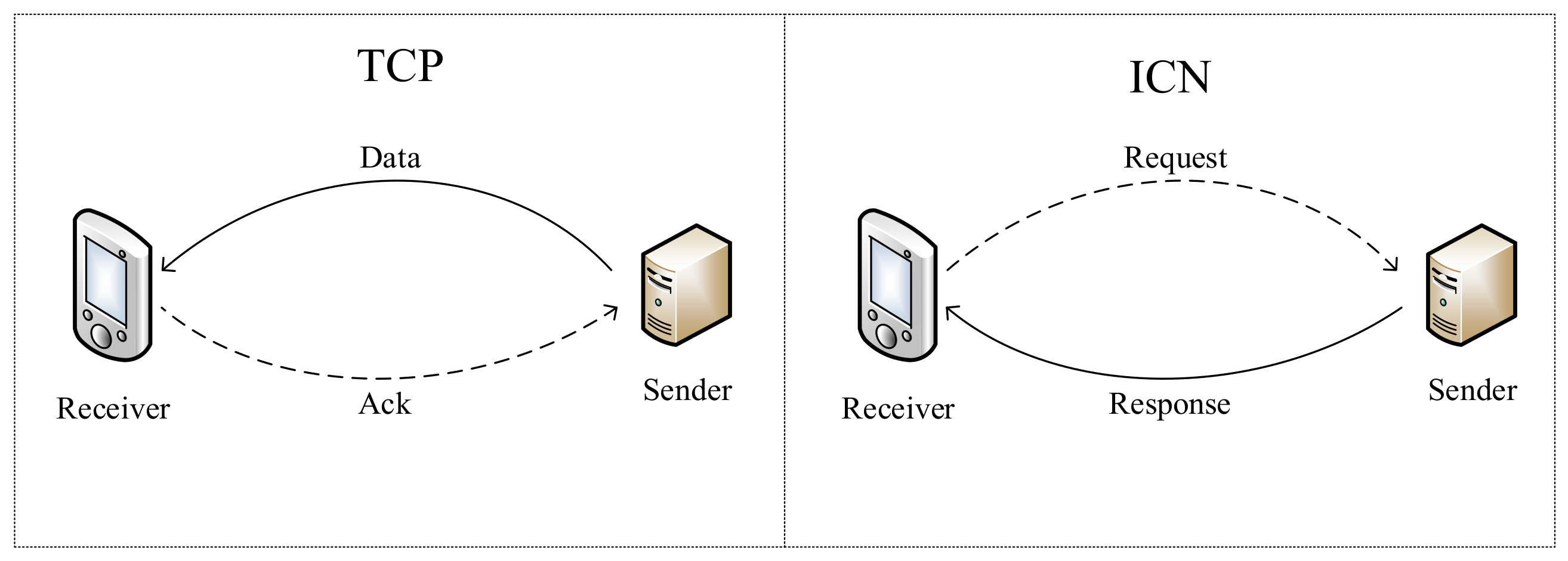
2. Related Work
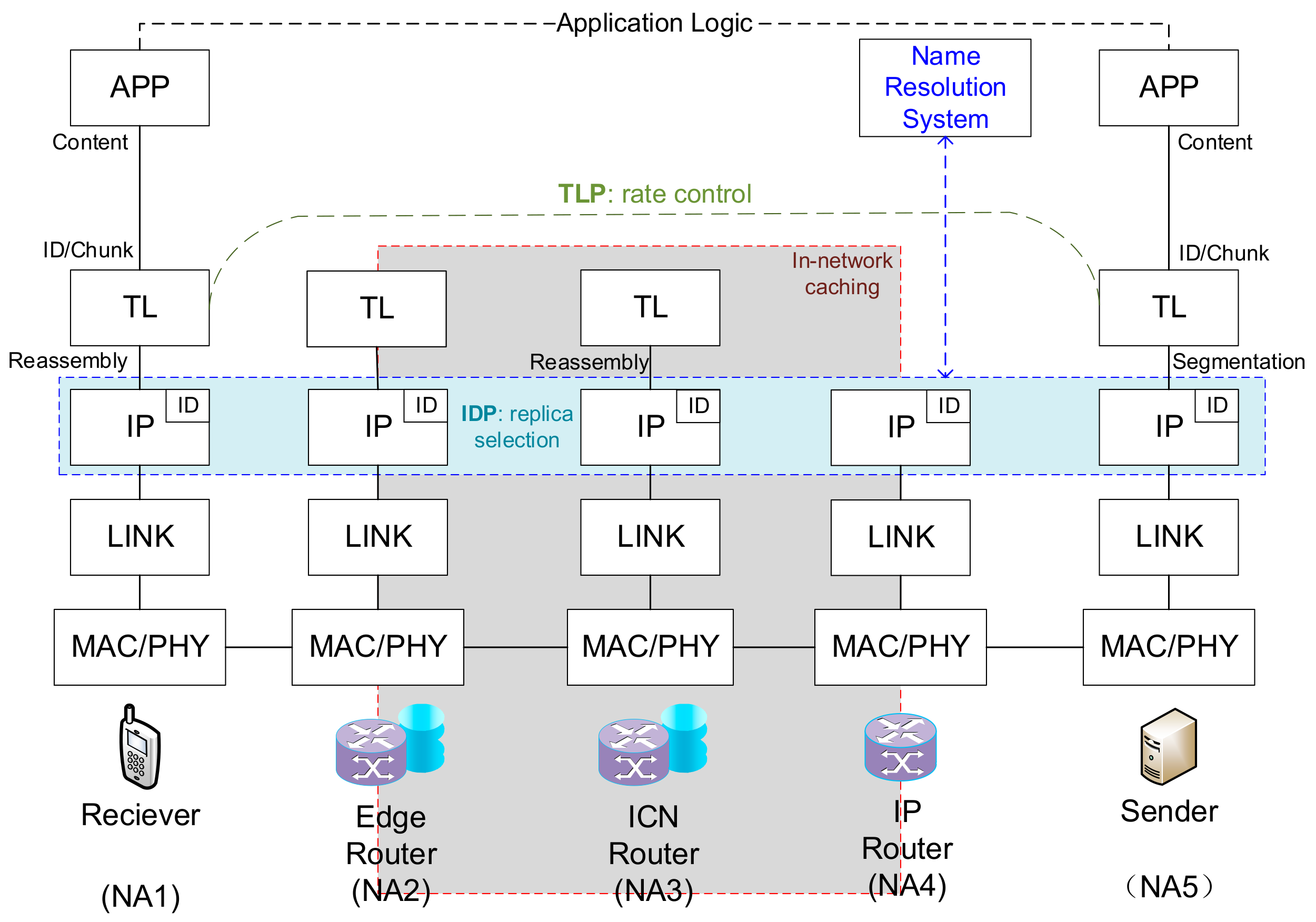
3. Design
3.1. Overview of 2LCCM
3.2. Heavy Congestion and Light Congestion
3.3. Switching Strategy
| Algorithm 1: Operation Process in Receiver |
| 1: if timeout to receive any packet then 2: switch to another replica 3: else if receiver receives a response packet then 4: heavy_congestion_flag or light_congestion_flag ← Equation (3) 5: if heavy_congestion_flag 1 then 6: switch_flag ← Equation (4) 7: if then 8: switch to another replica 9: else 10: adjust current request sending rate 11: else if light_congestion_flag == 1 then 12: adjust current request sending rate |
4. Implementation
4.1. Replica Selection Approach
4.2. Congestion Control Algorithm
| Algorithm 2: Receiver-Driven BBR Congestion Control Algotirhm |
| 1: State ← Obtain the state of current transmission 2: Inflight ← Obtain the size of inflight data of current transmission 3: B ← Probe the realtime bandwidth of current transmission 4: RTT ← Probe the realtime RTT of current transmission 5: if State == STARTUP then 6: pacing_gain ← 2/ln2 7: cwnd_gain ← 2/ln2 8: else if State == DRAIN then 9: pacing_gain ← ln2/2 10: cwnd_gain ← ln2/2 11: else if State == PROBE_BW then 12: pacing_gain ← Change according array [1.25, 0.75, 1, 1, 1, 1, 1, 1] periodically 13: else if State == PROBE_RTT then 14: cwnd ← 4 15: BDP ← Equation (7) 16: if not State == PROBE_RTT then 17: cwnd ← BDP*cwnd_gain-Inflight 18: pacing_rate ← Equation (8) 19: Receiver sends request packets smoothly by pacing_rate |
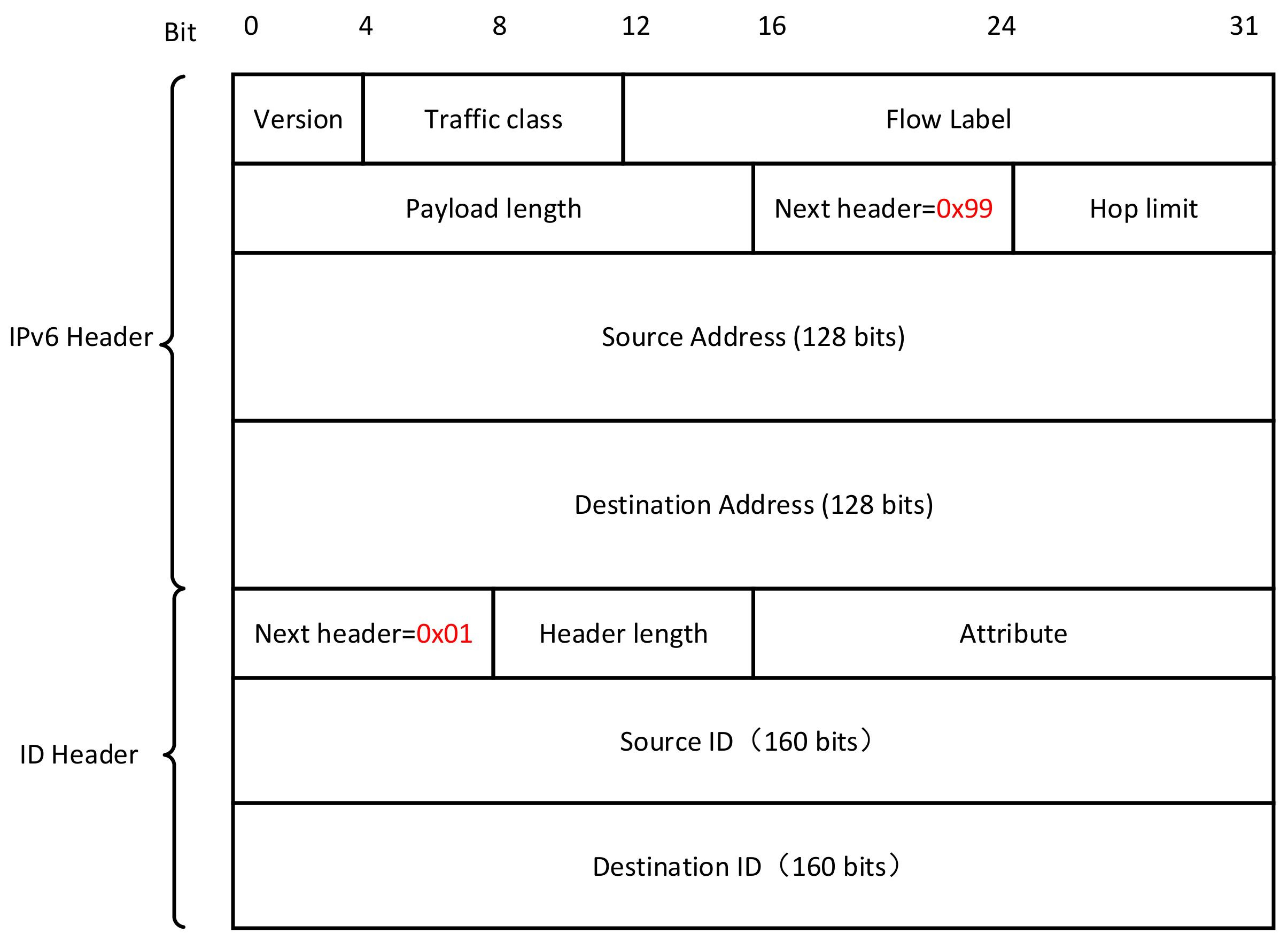
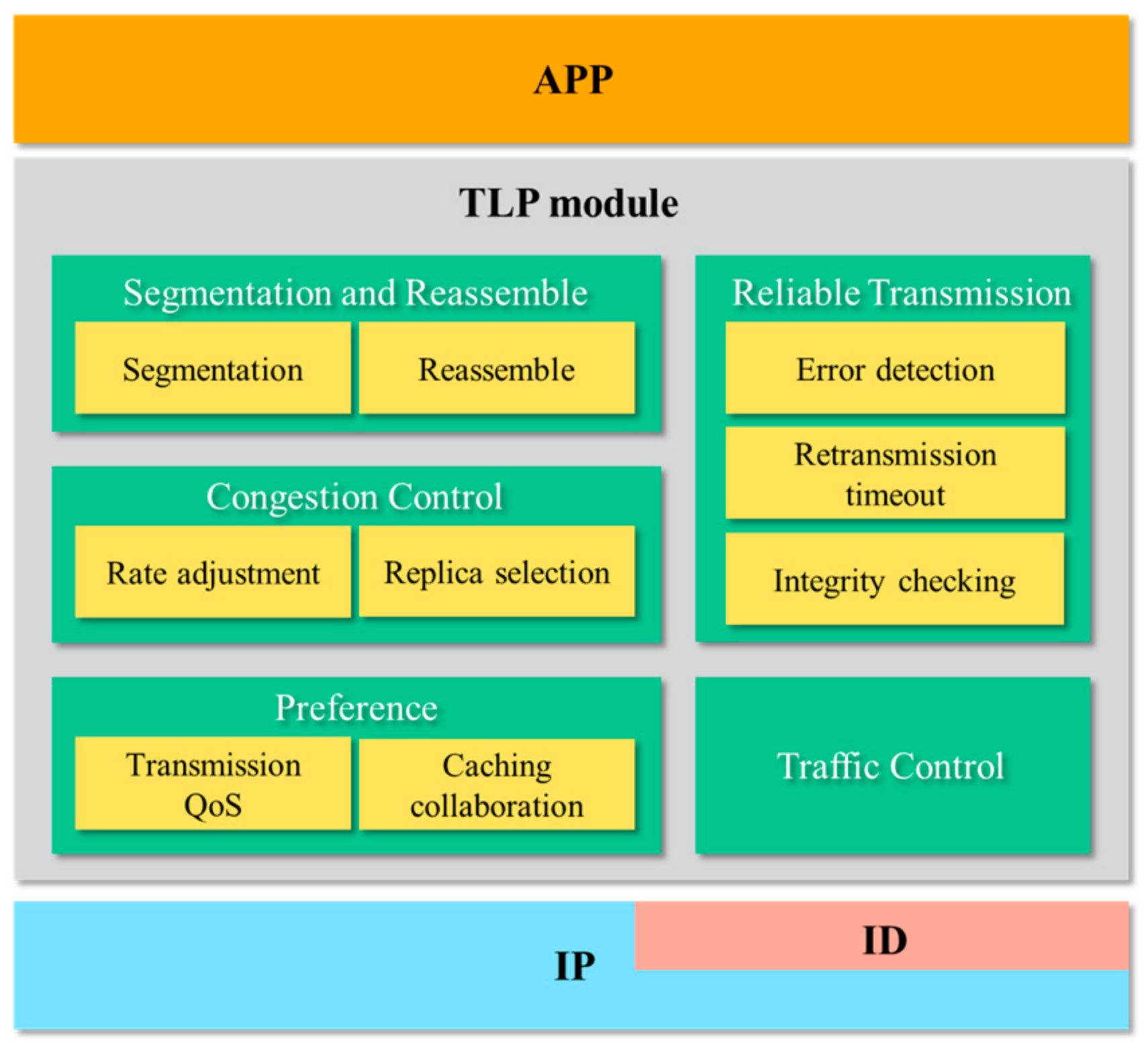
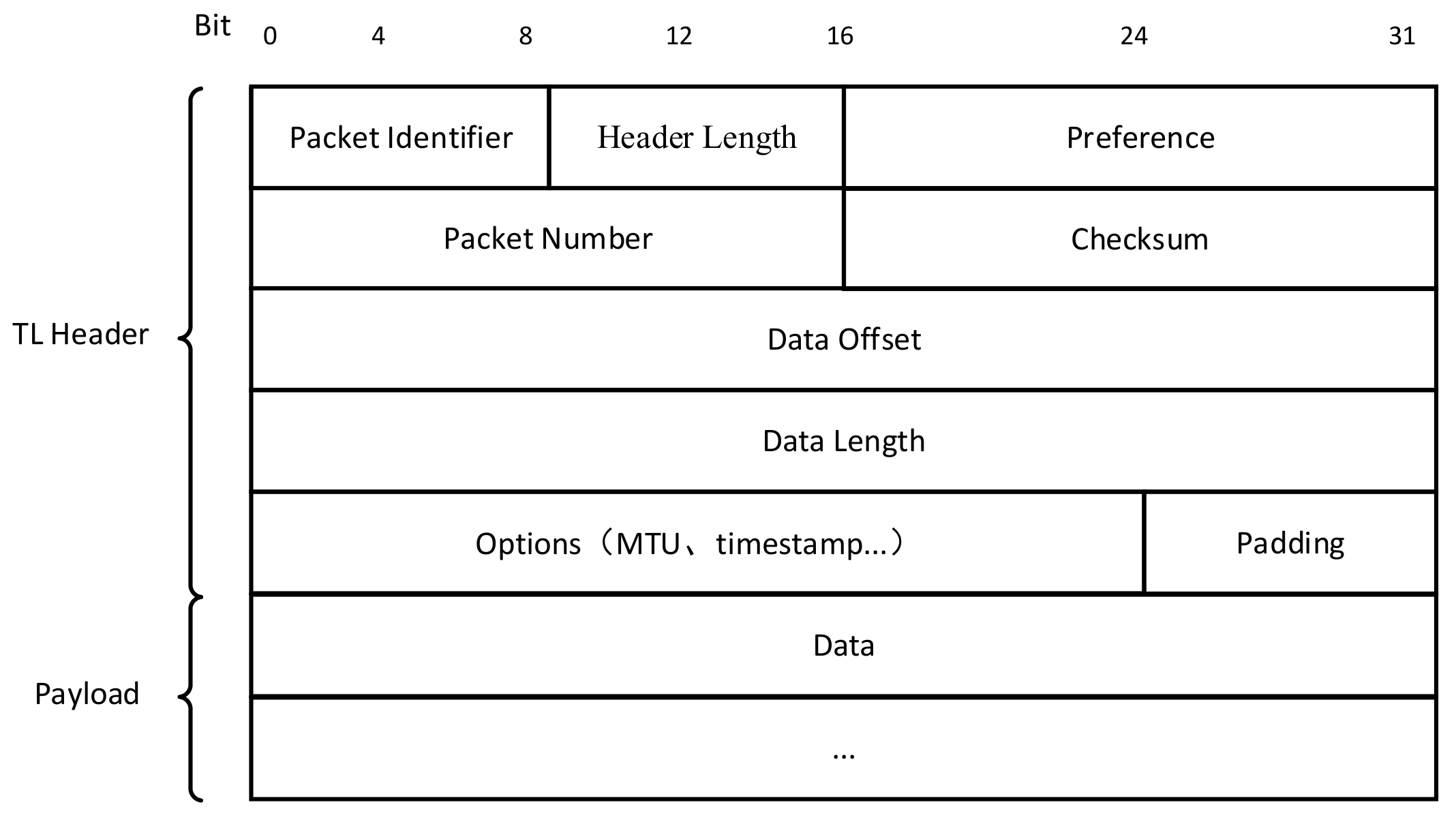
4.3. Transport Layer Protocol
5. Evaluation
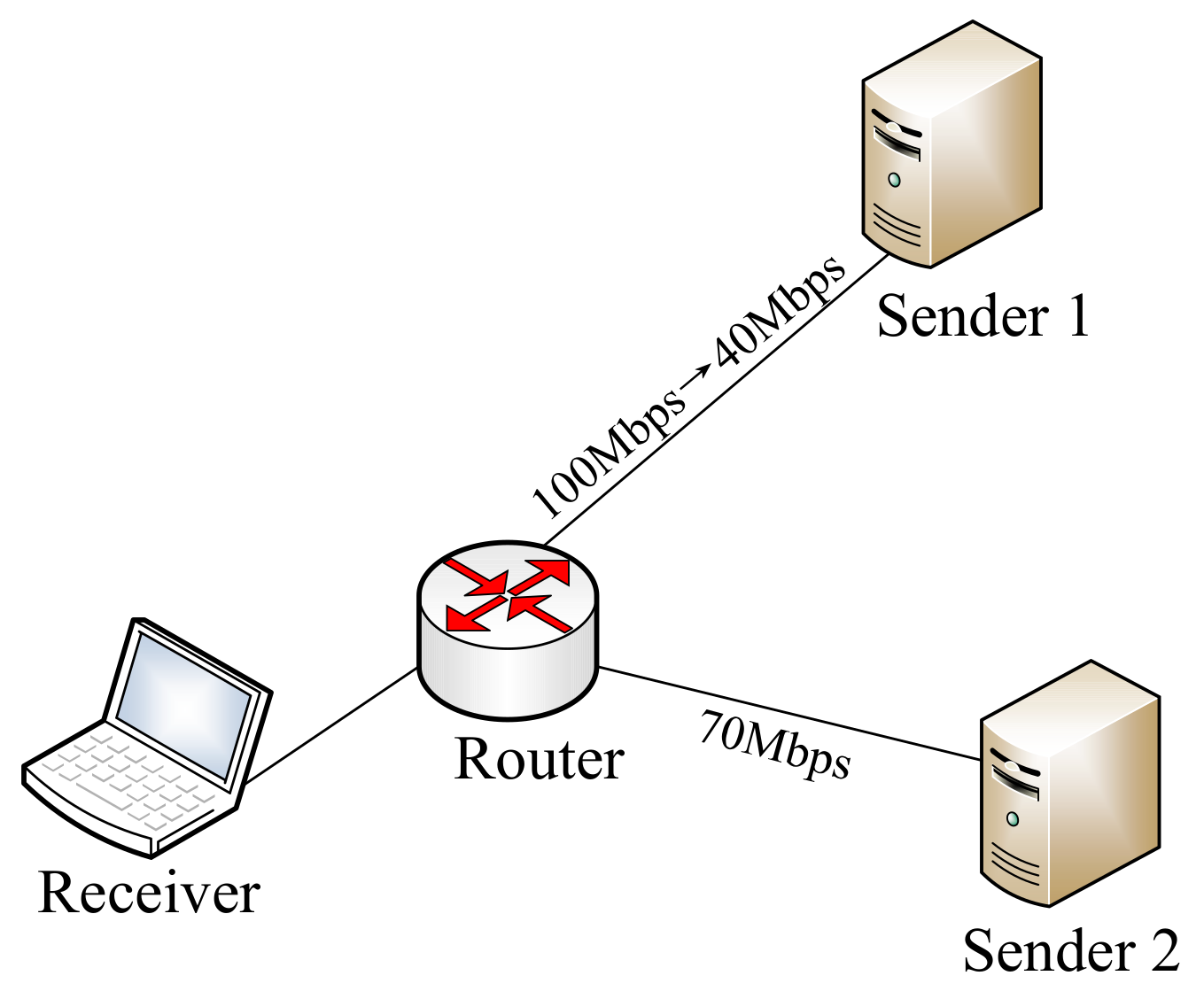
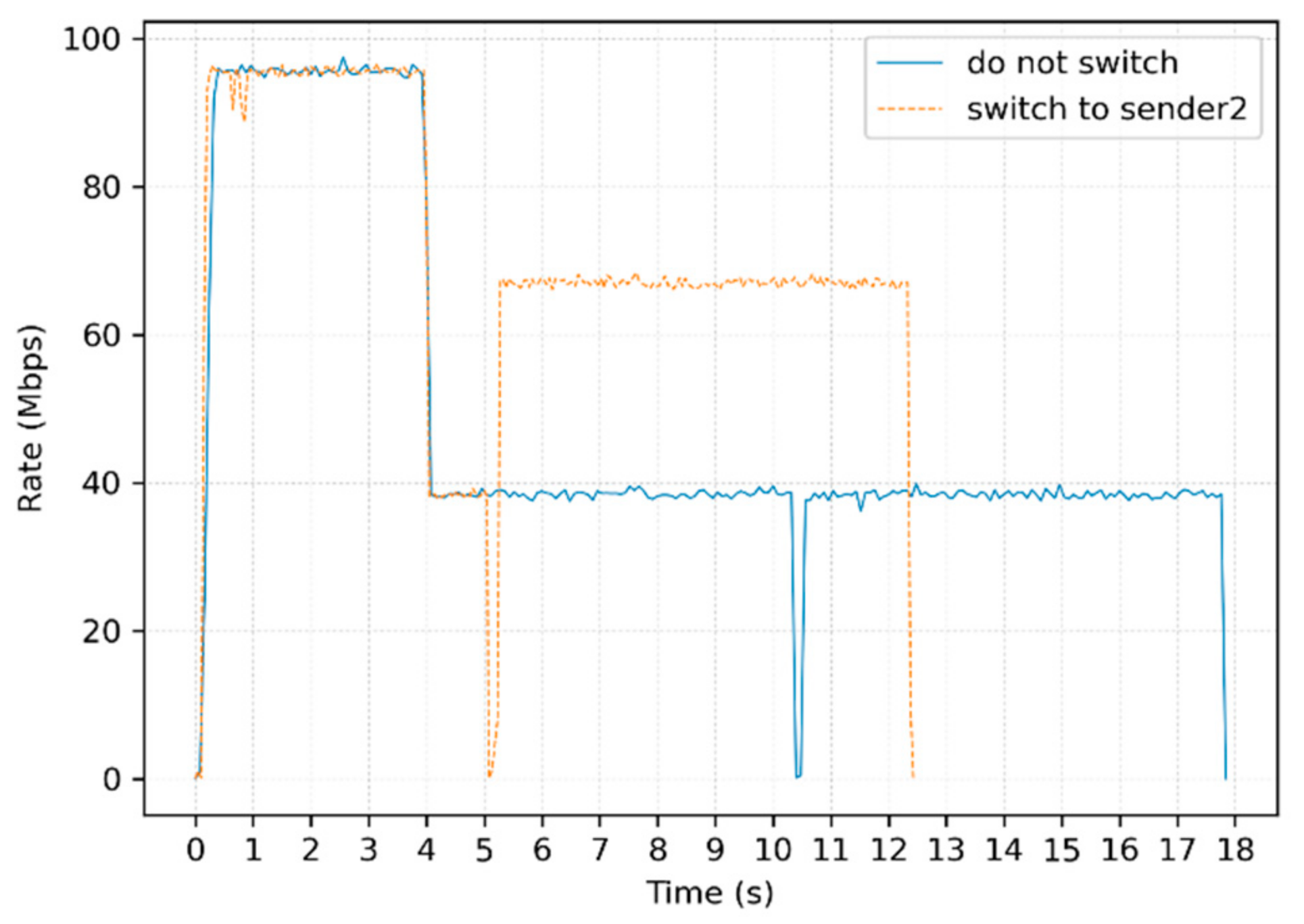
5.1. Performance of Switching Strategy
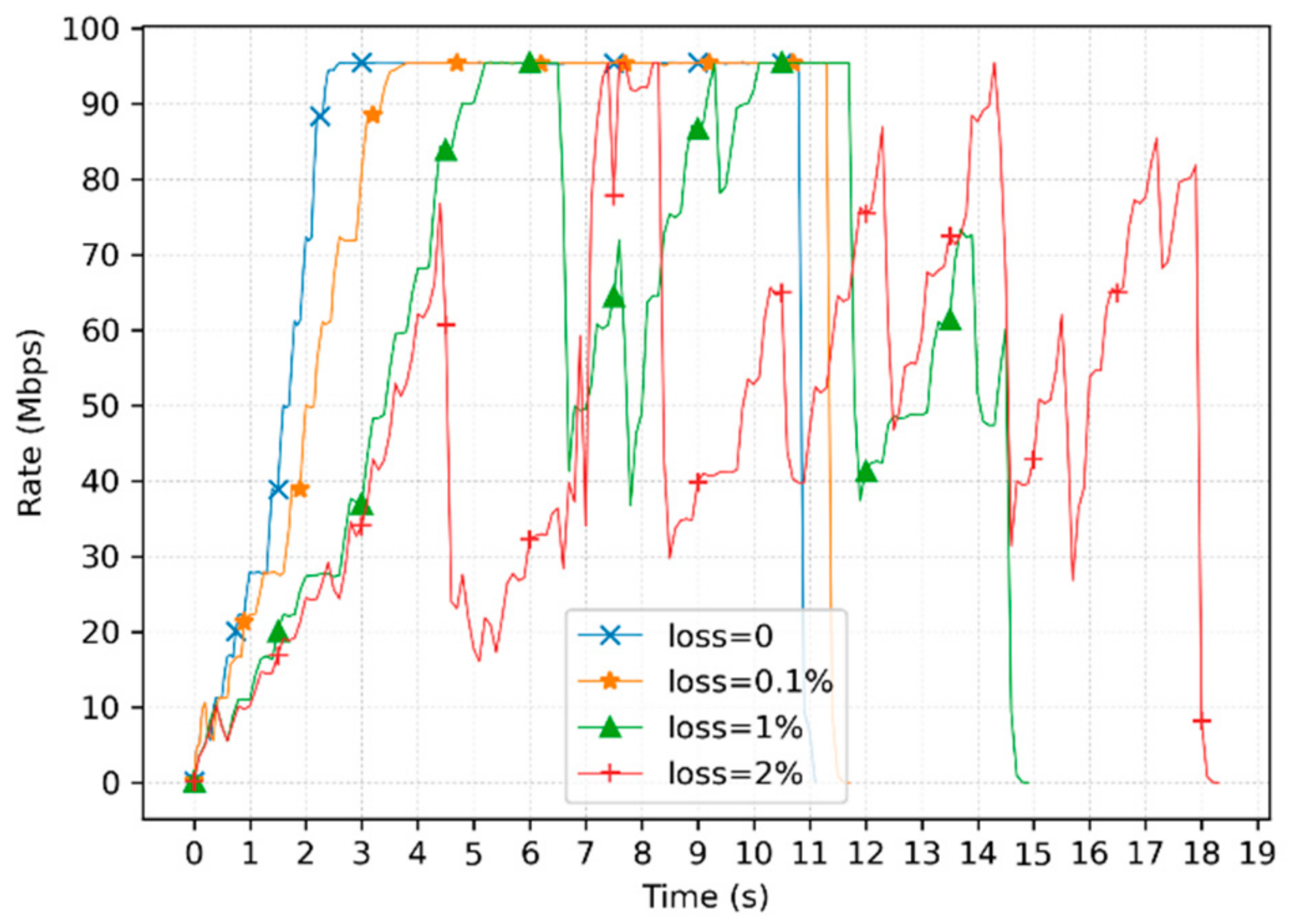
5.2. Performance of Receiver-Driven BBR Algorithm
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Gupta, A.; Jha, R.K. A Survey of 5G Network: Architecture and Emerging Technologies. IEEE Access 2015, 3, 1206–1232. [Google Scholar] [CrossRef]
- Schulz, P.; Matthe, M.; Klessig, H.; Simsek, M.; Fettweis, G.; Ansari, J.; Ashraf, S.A.; Almeroth, B.; Voigt, J.; Riedel, I.; et al. Latency Critical IoT Applications in 5G: Perspective on the Design of Radio Interface and Network Architecture. IEEE Commun. Mag. 2017, 55, 70–78. [Google Scholar] [CrossRef]
- Xylomenos, G.; Ververidis, C.N.; Siris, V.A.; Fotiou, N.; Tsilopoulos, C.; Vasilakos, X.; Katsaros, K.V.; Polyzos, G.C. A survey of information-centric networking research. IEEE Commun. Surv. Tutor. 2014, 16, 1024–1049. [Google Scholar] [CrossRef]
- Proof-of-Concept for Data Service Using Information Centric Networking in IMT-2020. Available online: https://www.itu.int/itu-t/recommendations/rec.aspx?rec=13655 (accessed on 20 May 2020).
- Jacobson, V.; Smetters, D.K.; Thornton, J.D.; Plass, M.F.; Briggs, N.H.; Braynard, R.L. Networking named content. In Proceedings of the 5th International Conference on Emerging Networking Experiments and Technologies, Rome, Italy, 1–4 December 2009; pp. 1–12. [Google Scholar]
- Koponen, T.; Chawla, M.; Chun, B.-G.; Ermolinskiy, A.; Kim, K.H.; Shenker, S.; Stoica, I. A data-oriented (and beyond) network architecture. In Proceedings of the ACM SIGCOMM Computer Communication Review, Kyoto, Japan, 27 August 2007; pp. 181–192. [Google Scholar]
- Raychaudhuri, D.; Nagaraja, K.; Venkataramani, A. MobilityFirst: A robust and trustworthy mobility-centric architecture for the future internet. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2012, 16, 2–13. [Google Scholar] [CrossRef]
- Dannewitz, C.; Kutscher, D.; Ohlman, B.; Farrell, S.; Ahlgren, B.; Karl, H. Network of Information (NetInf)—An information- centric networking architecture. Comput. Commun. 2013, 36, 721–735. [Google Scholar] [CrossRef]
- Wang, J.; Chen, G.; You, J.; Sun, P. SEANet: Architecture and Technologies of an On-site, Elastic, Autonomous Network. J. Netw. New Media 2020, 9, 1–8. [Google Scholar]
- Ren, Y.; Li, J.; Shi, S.; Li, L.; Wang, G.; Zhang, B. Congestion control in named data networking—A survey. Comput. Commun. 2016, 86, 1–11. [Google Scholar] [CrossRef]
- Zhang, J.; Ren, F.; Lin, C. Survey on transport control in data center networks. IEEE Netw. 2013, 27, 22–26. [Google Scholar] [CrossRef]
- Zhang, F.; Zhang, Y.; Raychaudhuri, D. Edge caching and nearest replica routing in information-centric networking. In Proceedings of the 37th IEEE Sarnoff Symposium, Newark, NJ, USA, 19–21 September 2016; pp. 181–186. [Google Scholar]
- Lee, M.; Song, J.; Cho, K.; Pack, S.; Kwon, T.; Kangasharju, J.; Choi, Y. Content discovery for information-centric networking. Comput. Netw. 2015, 83, 1–14. [Google Scholar] [CrossRef]
- Rozhnova, N.; Fdida, S. An effective hop-by-hop interest shaping mechanism for CCN communications. In Proceedings of the 2012 IEEE INFOCOM Workshops, Orlando, FL, USA, 25–30 March 2012; pp. 322–327. [Google Scholar]
- Zhang, F.; Zhang, Y.; Reznik, A.; Liu, H.; Qian, C.; Xu, C. A transport protocol for content-centric networking with explicit congestion control. In Proceedings of the 23rd International Conference on Computer Communications and Networks, Shanghai, China, 4–7 August 2014; pp. 1–8. [Google Scholar]
- Detti, A.; Salsano, S.; Cancellieri, M.; Blefari-Melazzi, N.; Pomposini, M. Transport-layer issues in information centric networks. In Proceedings of the 2nd edition of the ICN Workshop on Information-Centric Networking, Helsinki, Finland, 17 August 2012; pp. 19–24. [Google Scholar]
- Siddiqui, S.; Waqas, A.; Khan, A.; Zareen, F.; Iqbal, M.N. Congestion controlling mechanisms in content centric networking and named data networking—A survey. In Proceedings of the 2nd International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), Sukkur, Pakistan, 30–31 January 2019; pp. 1–7. [Google Scholar]
- Xia, C.; Xu, M.; Wang, Y. A loss-based TCP design in ICN. In Proceedings of the 22nd Wireless and Optical Communications Conference, Chongqing, China, 16–18 May 2013; pp. 449–454. [Google Scholar]
- Fall, K.; Floyd, S. Simulation-based comparisons of Tahoe, Reno and SACK TCP. ACM SIGCOMM Comput. Commun. Rev. 1996, 26, 5–21. [Google Scholar]
- Carofiglio, G.; Gallo, M.; Muscariello, L. ICP: Design and Evaluation of an Interest Control Protocol for Content-Centric Networking. In Proceedings of the 2012 IEEE INFOCOM Workshops, Orlando, FL, USA, 25–30 March 2012; pp. 304–309. [Google Scholar]
- Potys, R.A.; Ali, N.M.; Marsh, I.; Osmani, F. NetInf TP: A receiver-driven protocol for ICN data transport. In Proceedings of the 2015 IEEE 23rd International Symposium on Quality of Service (IWQoS), Portland, OR, USA, 15–16 June 2015; pp. 267–272. [Google Scholar] [CrossRef]
- Wang, L.; Bayhan, S.; Kangasharju, J. Optimal chunking and partial caching in information-centric networks. Comput. Commun. 2015, 61, 48–57. [Google Scholar] [CrossRef]
- Saino, L.; Cocora, C.; Pavlou, G. CCTCP: A scalable receiver-driven congestion control protocol for content centric networking. IEEE Int. Conf. Commun. 2013, 3775–3780. [Google Scholar] [CrossRef]
- Arianfar, S.; Ott, J.; Eggert, L.; Nikander, P. ConTug: A transport protocol for content-centric networks. In Proceedings of the IEEE International Conference on Network Protocols, Kyoto, Japan, 5–10 October 2010; pp. 1–9. [Google Scholar]
- Agarwal, A.; Tahiliani, M.P. BCON: Back pressure based congestion avoidance model for Named Data Networks. In Proceedings of the 2016 IEEE International Conference on Advanced Networks and Telecommunications Systems, Bangalore, India, 6–9 November 2016; pp. 1–5. [Google Scholar]
- Schneider, K.; Yi, C.; Zhang, B.; Zhang, L. A practical congestion control scheme for named data networking. In Proceedings of the 3rd ACM Conference on Information-Centric Networking, Kyoto, Japan, 26–28 September 2016; pp. 21–30. [Google Scholar]
- Su, K.; Bronzino, F.; Ramakrishnan, K.K.; Raychaudhuri, D. MFTP: A clean-slate transport protocol for the information centric mobilityfirst network. In Proceedings of the 2nd International Conference on Information-Centric Networking, San Francisco, CA, USA, 30 September–2 October 2015; pp. 127–136. [Google Scholar]
- Wang, Z.; Luo, H.; Zhou, H.; Li, J. R2T: A Rapid and Reliable Hop-by-Hop Transport Mechanism for Information-Centric Networking. IEEE Access 2018, 6, 15311–15325. [Google Scholar] [CrossRef]
- Jacobson, V. Congestion avoidance and control. ACM SIGCOMM Comput. Commun. Rev. 1988, 18, 314–329. [Google Scholar] [CrossRef]
- Detti, A.; Blefari Melazzi, N.; Salsano, S.; Pomposini, M. CONET: A content centric inter-networking architecture. In Proceedings of the ACM SIGCOMM Workshop on Information-Centric Networking, Toronto, ON, Canada, 19 August 2011; pp. 50–55. [Google Scholar]
- Guoqing, W.; Jiang, L.; Xiuqin, L.; Shaoyu, Y.; Guojia, L. Modeling chunk-based content placement in information centric networking. J. China Univ. Posts Telecommun. 2017, 24, 44–50. [Google Scholar] [CrossRef]
- Zeng, L.; Ni, H.; Han, R. An incrementally deployable IP-compatible information-centric networking hierarchical cache system. Appl. Sci. 2020, 10, 6228. [Google Scholar] [CrossRef]
- Saino, L.; Psaras, I.; Pavlou, G. Hash-routing schemes for information centric networking. In Proceedings of the 3rd ACM SIGCOMM Workshop on Information-Centric Networking, Hong Kong, China, 12 August 2013; pp. 27–32. [Google Scholar]
- Kong, L.; Zhu, J.; Dai, R.; Sadat, M.N. Impact of distributed caching on video streaming quality in information centric networks. In Proceedings of the 2017 IEEE International Symposium on Multimedia, Taichung, Taiwan, 11–13 December 2017 ; pp. 399–402. [Google Scholar]
- Brakmo, L.S.; Peterson, L.L. TCP Vegas: End to End Congestion Avoidance on a Global Internet. IEEE J. Sel. Areas Commun. 1995, 13, 1465–1480. [Google Scholar] [CrossRef]
- Song, Y.; Ni, H.; Zhu, X. An enhanced replica selection approach based on distance constraint in ICN. Electronics 2021, 10, 490. [Google Scholar] [CrossRef]
- Eum, S.; Nakauchi, K.; Murata, M.; Shoji, Y.; Nishinaga, N. CATT: Potential based routing with content caching for ICN. In Proceedings of the 2nd Edition of the ICN Workshop on Information-Centric Networking, Helsinki, Finland, 17 August 2012; pp. 49–54. [Google Scholar]
- Ha, S.; Rhee, I.; Xu, L. CUBIC: A new TCP-friendly high-speed TCP variant. Oper. Syst. Rev. 2008, 42, 64–74. [Google Scholar] [CrossRef]
- Cardwell, N.; Cheng, Y.; Gunn, S.C.; Yeganeh, S.H.; Jacobson, V. BBR: Congestion-Based Congestion Control. Commun. ACM 2017, 60, 58–66. [Google Scholar] [CrossRef]
- Gettys, J.; Nichols, K. Bufferbloat: Dark buffers in the internet. Commun. ACM 2012, 55, 57–65. [Google Scholar] [CrossRef]
- Dong Hanze, G.Z. Performance improvement of BBR congestion control algorithm in wireless network. J. Harbin Inst. Technol. 2019, 51, 63–67. [Google Scholar] [CrossRef]
- Hemminger, S. Network emulation with NetEm. In Proceedings of the 6th Australian National Linux Conference, Canberra, Australia, 18–23 April 2005; pp. 1–9. [Google Scholar]

Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, Y.; Ni, H.; Zhu, X. Two-Level Congestion Control Mechanism (2LCCM) for Information-Centric Networking. Future Internet 2021, 13, 149. https://doi.org/10.3390/fi13060149
Song Y, Ni H, Zhu X. Two-Level Congestion Control Mechanism (2LCCM) for Information-Centric Networking. Future Internet. 2021; 13(6):149. https://doi.org/10.3390/fi13060149
Chicago/Turabian StyleSong, Yaqin, Hong Ni, and Xiaoyong Zhu. 2021. "Two-Level Congestion Control Mechanism (2LCCM) for Information-Centric Networking" Future Internet 13, no. 6: 149. https://doi.org/10.3390/fi13060149
APA StyleSong, Y., Ni, H., & Zhu, X. (2021). Two-Level Congestion Control Mechanism (2LCCM) for Information-Centric Networking. Future Internet, 13(6), 149. https://doi.org/10.3390/fi13060149





