1. Introduction
The Internet of Things (IoT) involves multifaceted communication across different networks. These networks include sensing devices; automobiles; household appliances; devices based on sensors, electronics, and software connections. With seamless connectivity between devices and rapid information exchange, this concept provides advanced services that are available, regardless of the time, space, and person. The IoT can include various wireless networks and mobile ad hoc networks (MANETs). The deployment of IoT devices has increased significantly in recent years for buildings (houses, schools, factories, and offices), transportation, automobiles, and health organizations [
1].
MANETs consist of several mobile nodes that connect to or leave during the operations of the intended network. In large communication networks, image hashing-based authentication provides resilience against several security attacks. Existing routing studies include obstacles and methods based on control [
1]. The integration of MANETs and the IoT forms a developing paradigm to allow communication among smart devices in the IoT. Furthermore, the weak infrastructure increases the chances of security attacks by the malicious nodes that compromise confidential information. Thus, in MANET–IoT, security against strong competitors is still difficult [
2]. MANET is a low-cost, dynamic, and distributed network with self-adjusting capabilities [
3,
4]. It consists of a cluster of mobile nodes that establish the communication opportunistically. MANET follows the architecture of infrastructure at a centralized station or rolling mill. Specific features of MANET include the following: dynamic topology, multi-hop communication, decentralization infrastructure, scalability, and short connection. The rapid development of wireless technology increases the current demand for IoT [
5]. The IoT can be described as a network made up of millions of different devices that allow intelligent “stuff” in between. The expansion of opportunistic communication is noticeable in IoT devices, as they are associated with dynamic devices and integrated with IoT enabling adaptable communication between IoT MANET devices [
6]. The introduction of MANET into the IoT facilitates improved connectivity through multi-hop connectivity and also supports high scaling. With the integration of MANET, IoT applications can be deployed in military scenarios, smart city applications, waste management, and disaster management, etc. However, the lack of infrastructure and centralized controls increases the risk for the MANET–IoT environment. MANET is susceptible to security attacks, e.g., jamming, Black-hole attack, Sibyl attacks, and packet dropping attacks. These attacks slow down the whole network [
7,
8]. MANET is more vulnerable to attacks compared to the networks based on infrastructure. Creating a secure MANET connection is difficult due to: (1) a public wireless device, (2) an unclear defense line, (3) a self-regulatory and self-motivated network, (4) a large number of broadcast messages, (5) hop-by-hop messages, and 6) limited nodes’ charge and capacity of batteries [
2].
Trust is initiated from the sociology domain [
3]. Trust plays a vital role in enhancing the security of specialized networks by a priori assessments or by evaluating the trust of their peers before making any route decisions. Due to resource constraints (e.g., power and bandwidth), not all nodes can participate in the routing and then send packets. Node reliability is a good measure to guarantee the accessibility of the nodes and to ensure reliable communication between them [
4]. The mechanisms of cryptography cannot assist in the sensing/blocking of such network-based accidental threats. The trust management concept does not interchange cryptography; however, it improves it. The cryptography and credentials framework decision work manually to achieve the security of MANET-IoT. To provide consistent, protected, and well-timed network packages, this work is based on a cluster in MANET-IoT [
5]. The MANET-IoTnodes were grouped into single clusters [
6], and a predictive model based on trust management was established to calculate and distribute trust. Moreover, an ideal model for identifying malicious nodes and progressing network functioning was also established.
The main problem addressed in the paper is the mobility of the nodes. Therefore, a node is out of the group and wants to join another group so it can be easily attacked from the middle. Attackers can now easily find the device and link the cluster with official approval. The group head (GH) should not permit the pairing of soldiers and devices that are attacker nodes. This paper presents an efficient authentication scheme based on image hashing (IHA) to provide the secure joining and mobility of nodes in the network. In the system model, asymmetric keys are utilized for secure communication in the network. GHs and the network administrator (NA) collaborate to authenticate the node based on security credentials and image hashing. The main contributions of this paper are as follows:
We evaluated the literature and identified the research from recent and related schemes.
An image hashing-based authentication scheme is proposed to migrate the nodes to other groups securely. Asymmetric keys were employed for secure communication.
The proposed image hashing-based node joining and migration mechanisms are presented. These mechanisms provide secure mobility of the node within the network.
Finally, extensive simulations were conducted to extract the results from trace files.
The rest of the paper is organized as follows:
Section 2 provides a review of the existing and related literature;
Section 3 demonstrates our system model;
Section 4 presents the proposed work;
Section 5 provides the results and analysis; finally,
Section 6 concludes the paper.
2. Related Work
MANET has been widely explored over the last decade. In recent years, the explosion of the Internet has significantly increased the use and benefits of MANET. MANET-IoT is an important and emerging concept, as wireless devices are self-connected and self-organized. The safety and consistency necessities of this kind of network should, therefore, be re-examined. Regarding next-generation computing, in the IoT, MANET is expected to be a significant key player. A smart concept of MANET in 5G is presented by Tanveer in [
9]. A robust image hashing scheme provides efficient authentication. The dominant coefficients are employed to minimize the computational cost. A novel approach is applied for image hashing-based authentication. Moreover, this scheme provides secure data transmission over the network. [
10].
An image hashing-based scheme provides multiple attack detection and adaptive thresholding for image authentication. A hashing algorithm is applied to the image to extract hash values for authentication [
11]. Waleed proposed a new predictive trust-based model for MANET in the IoT [
12] that calculates the final node value based on direct and indirect opinions of trust. A secure routing protocol is also designed to transfer the data packets securely. Numerous protocols of routing based on trust were proposed and appraised in an ad hoc network development. Most trust management plans are created for joint routing to identify the wrong nodes that are self-destructive or harmful. When designing safer route protocols, researchers have adopted reputational associations concerning mobile nodes. In [
13], Desai et al. presented a predictive route model that numerically identifies different security attacks. In [
14], Rath et al. explained the key security problems for the IoT in MANET. They concentrated on security and vulnerability threats for ad hoc networks and the creation of a comprehensive flight network using the IoT. Riyaz et al. proposed a scheme in MANET based on routing protocols [
15]. In this approach, protocols of routing are employed to transfer the data packets to the concerned destination in MANET. An effective approach based on the triple factor is used to transmit the data into a secure path. K. Dhanya et al. [
16] presented a proposal based on secure autonomic MANET in a trusted routing path. This research work is based on trust using routing protocols in MANET. Moreover, several surveys and various approaches are presented from the perspective of MANET. F. Khan [
17] presented a scheme based on secure communication for IoT-based networks in MANET. In his research work, the quality of services (QoS) can be improved using existing resources that enhance the performance of a network.
H. Y. Zhao et al. [
18] presented an energy consumption scheme based on an ant colony for MANET-IoT. A novel algorithm has been proposed for node computing and the joining and disjoining of nodes in the transmission route of energy consumption in IoT–MANET. Moreover, a novel ant colony architecture is presented in which nodes join a greedy approach that massively shortens the run-time. M. A. Saleem [
19] proposed a routing scheme based on group routing for the framework of data clusters to obtain the optimal route. He also explored the conventional standards of MANET and VANET (Vehicular Ad Hoc Network) and their behaviors in smart cities. In [
20], a novel approach using a fluctuating topology for securing the exchange key is presented. He used a MANET-based advanced model and designed a key exchange scheme. This scheme shortened the attacker’s accessibility. Degan Zhang et al. [
21] proposed an approach with trust matrices by using an adaptive approach. This method calculates the trust by using data packets. The proposed approach successfully protects the data from attackers. Burhan ul Islam Khan [
22] designed an efficient model based on computation to enhance security. As security is a key issue in MANET and the secure transmission of data is more crucial in recent years, several efficient solutions are proposed in his research to overcome these security issues. A game-based model is presented that detects different security attacks and secures all nodes. Rashidah et al. [
23] proposed a security-based model for MANETs. This model has analyzed the performance and behavior of nodes and the reputation of the system simultaneously. Moreover, results show that the system’s performance has significantly improved, and throughput has been enhanced. S. N. Mohammad et al. [
24] presented a novel security architecture, ESMBMCRT. Security is enhanced to protect against black hole attacks and reduces energy consumption.
Nguyen proposed a scheme based on an asymmetric key for the classification and verification of a large-scale MANET [
25]. The team leader issues certificates to all nodes. Each node provides the certificate without the assistance of any authority of trusted certification. Moreover, this scheme reduces network consumption and increases network deployment. Team leaders have membership nodes, and other team members can communicate with one another. As shown in
Figure 1, the sender transmits the image hash to the receiver node by encrypting it with the public key of the receiver node. The receiving node decrypts the received image by using its private key. Vincent and Pushpa have proposed a structured approach of key management; [
26] the cluster head (CH) is selected for a group that contains the ultimate value of reliability. To calculate public and private keys for nodes, private key generation (PKG) has been utilized widely. The NA chooses the CH after the election, and the CA’s offline limit is set to request a new node to connect to the network. The agent mobile is the segment of an application that obtains confidential data from several trusted network nodes and also information of nodes that the certificates have passed. SRIH [
27], a secure and robust image hashing-based scheme, employs a Gaussian pyramid. Key-based encryption is utilized to secure the hash, and authentication is conducted based on image hashing. This scheme detects different malicious attacks and also provides resilience against malicious attacks. ESIH [
28], an efficient and secure image hashing-based authentication scheme, is utilized with an improved design. Sufficient time must be provided for efficient authentication and verification.
This plan has the following benefits: the node generates a public key based on a similar origin and CA assigned to its node ID. Each node has a public key of self-disconnection, known as a cluster. Therefore, the cluster nodes do not press their public keys on all adjacent nodes, which occupy less of the network storage space and bandwidth simultaneously. The CH public key changes at times, and each CH compares its new public key against the value of the trust and the previous (larger) public key. The key renewal process is easily accomplished by using the timer in key numbers.
3. Problem Formalization and System Model
Our proposed model is an IoT-based reliable authentication approach to provide the authentication and permission of a soldier by using a mobile device. The authentication is conducted at the fog node/NA and the GH. Each soldier acts as a smart node denoted by where n is the total number of soldiers in the network. In our system model, the soldier sends an encrypted message to the GH to join the group. The GH authenticates the received soldier information by comparing the received values with the actual stored information received from the NA. Moreover, when a soldier is transferred from the present group to another group, the request message is forwarded to the GH. On receiving the request, the GH cooperates with a member node and transfers security credentials to the destination group GHs. Then, the soldier sends the group joining request to the new group. The GH of that group matches the security credentials of the soldier with the pre-received information of the soldier. The GH sends approval to the soldiers and permits soldiers to join the group when the security credentials are matched. Otherwise, the GH cannot join this group. Moreover, NA locally stored and processed the security credentials of the soldiers. The information of soldiers is not available, as the fog node request message is forwarded to the private cloud server for the information of a specific soldier. The information of all soldiers is in the permanent storage of a private cloud server. Security is a necessary element of our proposed scheme to protect the network from several security threats. The authentication process of most existing schemes that use image hashing techniques enhances the communication and computational cost while processing the image. As a solution to this, we provide a secure and lightweight image hashing model. In the case an attacker kills a soldier and takes his mobile device to join the group, the attacker cannot join the group until their security credentials are matched with the security credentials of the soldier that are stored in the private cloud server. In our proposed communication model, Ns, GHs, and NA are the main devices. We utilized asymmetric key-based encryption for secure communication. Moreover, each soldier can only communicate with his GH in the network. The GH can communicate with other GHs in the network and with the NA.
4. Proposed Image Hashing-Based Authentication Scheme
In this section, we present an image hashing-based authentication scheme (IHA). Security is a vital requirement for authentication-based IoT applications. Our scheme provides a solution for secure communication and authentication schemes for emergencies in war. The proposed scheme is subdivided into three phases, namely, node registration, node joining in a group, and the migration of nodes in a group, as shown in
Figure 2.
In the registration phase, a soldier is registered at the time of his recruitment. The NA takes the image and other credentials of the soldier stored in the local repositories and further uploads them to the private cloud server for permanent storage. Furthermore, the NA embeds this info (e.g., id, login id, password, and image hash) into the mobile device of the soldier. There will be separate mobile allocations to each soldier. In a war scenario, several soldiers leave and join the groups based on the emergency scenario. In this context, effective authentication and communication are required.
Therefore, the proposed scheme employs a fog node that locally processes the information at the edge of the network. Fog nodes act as a NA that manages the information on the count of groups in the specific network. Moreover, the node count is also considered within these groups. NA forwards the request message for the joining of a soldier in a specific group or the migration of the soldier to a specific group in war situations. A list of notations for the proposed scheme is shown in
Table 1.
4.1. Node Joining Algorithm
In this scenario, the node joining mechanism is explored where the node (
) joins a specific group,
. First of all,
transmits the join request to
in the form of an encrypted message, as shown in Equations (1) and (2).
The message
comprises the login ID (
), the password (
), and a hash of the soldier image
. The soldier acts as a node and is represented as
. Moreover,
includes the node ID (
), timestamp (
), nonce value (
), and a hash of (
) encrypted with the public key (
) of the
. After receiving the join request, the
checks the timestamp of the received message (
−
) < Δt. If the timestamp is greater than the threshold value, then the message is discarded and a request to resend the join request is sent. Otherwise, the
transmits the request message
to the
by its public key,
, for encryption. Then, the
forwards the required information based on the
, as shown in Equations (3) and (4).
When a message is received from the , checks the difference of time stamps ( − ) < Δt of the received message. In the case of an outdated message, the received message is discarded, and the resend request is shared with the . Otherwise, the authenticates the by comparing the hashes and equals received from the and . In the case where both the hashes are matched, adds the to the list of group members. Moreover, the stores the ’s information in the group table. Otherwise, the join request is failed as the user is not legitimate or an attacker. The feasible verified steps are shown in Algorithm 1.
| Algorithm 1. Node Joining Algorithm |
| 1. : |
| 2. : If ( − ) < Δt then |
| 3. : |
| 4. : |
| 5. : If ( − ) < Δt then |
| 6. : If equals then |
| 7. Add in the group and store data |
| 8. Forward success message to and |
| 9. Else |
| 10. Join request failed |
| 11. End if |
| 12. Else |
| 13. Drop message and forward resent request of required data |
| 14. End if |
| 15. Else |
| 16. Discard message and send acknowledgment to for resending join request |
| 17. End if |
4.2. Node Migration Algorithm
In the case of node migration, a request message is sent to . After receiving a request from the , the informs node members. Next, the transfers security credentials to destination group . The node migration mechanism is explored in a stepwise manner in Algorithm 2.
| Algorithm 2. Node Migration |
| 1. : Send migration request |
| 2. : Send reply message |
| 3. : Send data of to as |
| 4. If ( − ) < Δt then |
| 5. : Receive join request from as |
| 6. If ( − ) < Δt then |
| 7. If equals then |
| 8. Add in the group and store data |
| 9. Forward success message to and |
| 10. Else |
| 11. Migration request and join request failed |
| 12. End if |
| 13. Else |
| 14. Discard the join request of node |
| 15. End if |
| 16. Else |
| 17. Discard migration request and transmit resend request to |
| 18. End if |
In this scenario, the node leaves the current group to migrate to the remote group . First of all, forwards the migration request message to the current . The request message is encrypted using the public key of . Then, the forwards the message by encrypting with as a public key of the . This reply message also includes the as a public key of the remote , as will forward the security credentials to the for authentication at the time of joining. Moreover, also forwards the encrypted message, , to the for authentication purposes. After receiving the security credentials, the verifies the differences in timestamps as − , which should be less than the threshold time Δt. If the timestamp is greater than the threshold value, then the migration request is discarded, and the resend request is transmitted to the . Otherwise, the will receive the message, , from the , encrypted using , to join the new group when the reaches the remote group.
verifies that the differences in time stamps (
−
) are lower than the threshold Δt. In the case of an outdated message, the received message is discarded. Otherwise,
further compares the hashes
and
for the verification of message integrity. When both the hashes are matched,
accepts the migration and join request of the
and stores its information in the group table. Otherwise, the migration and join requests fail, and this node is considered as an unauthenticated node or attacker. The scenario of intergroup migration is shown in
Figure 3.
The proposed scheme is evaluated for providing security against the reply attack by including the timestamp and recording the differences between timestamps at the receiving side. This scheme ensures the challenge response from the nodes to ensure authentication and provides secure access control. It involves the hash of values to ensure message integrity against bit-alteration attacks. The image hashing ensures the efficient comparison among the images to reduce computational costs. The proposed scheme ensures that the intruder cannot forge the security parameters taken from the intermediary node traveling from one group to another due to a join or migration operation.
5. Results and Analysis for Performance Evaluation
The proposed work was verified through extensive simulation where nodes were deployed at 1200 m × 1200 m. A simulation was conducted using simulation tool NS 2.35 on Fedora Core 20. In this scenario, TCL was used to create nodes and deploy the network, and for message initiation at particular timeslots. The results were extracted using AWK scripts applied to the trace files. The C language was used for implementing the send, receive, hash, image hash, and security functions. We created separate classes for different levels of devices, such as the GH and NA member nodes. A list of simulation parameters is shown in
Table 2.
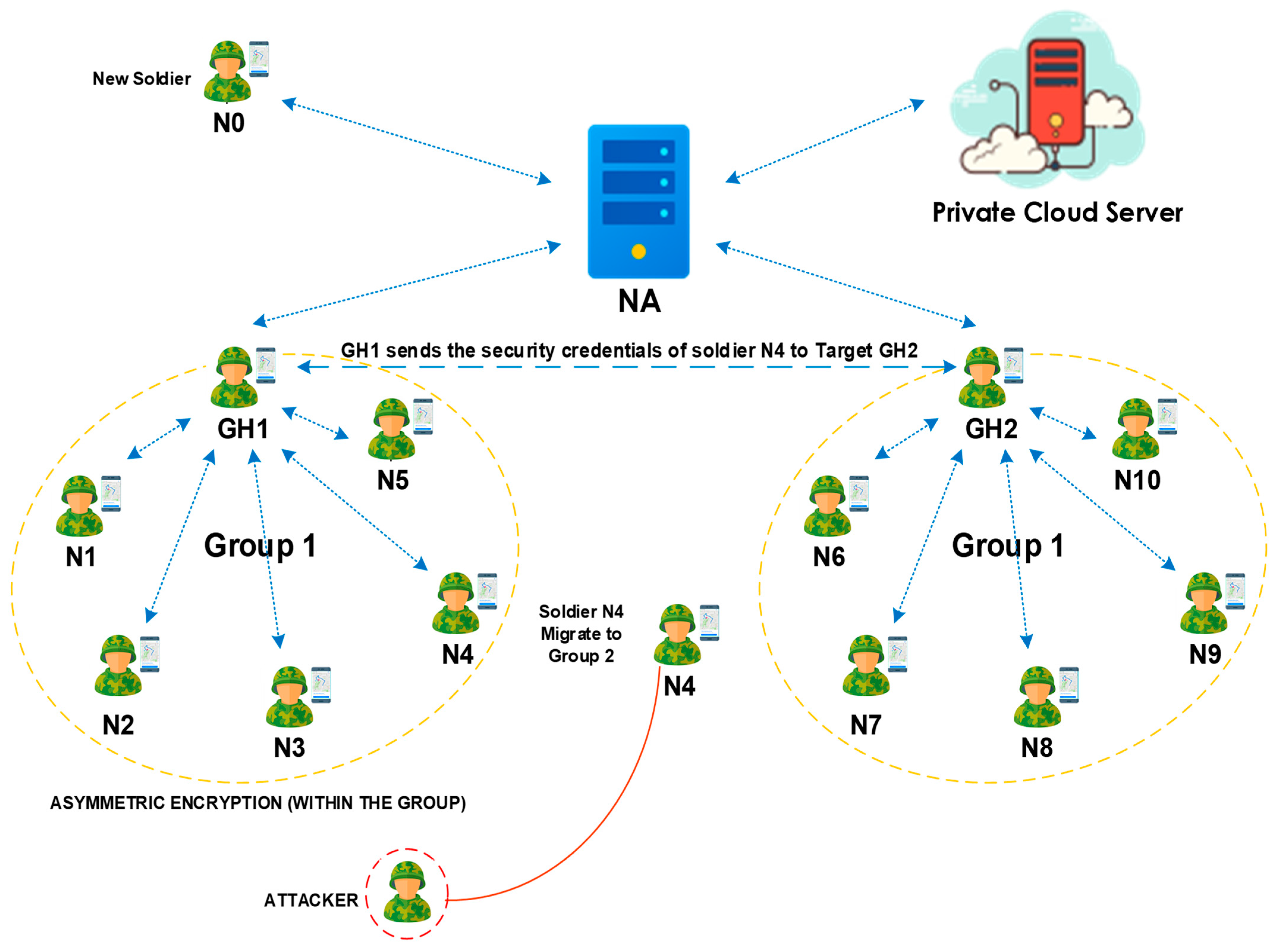
In the modeling message, node 0 is a GH at group 1 that forwards the group migration requests of node 4 to the target GH at group 2. Node 6 is a GH at the target group. The message display has a receiving function in node 6 of the target GH, and the message depends on the TCL modeling script sending function.
Figure 3 represents the complete setup. However, if the password and image of the node are unverified, then that node will not be permitted from the targeted GH. For example, the source GH (node 0) request for the
(node 4) is received at the target GH (node 6). The denied responses for joining node 4 are replied to by the target GH (node 6). In this setup, node 4 was unverified, as the hash image and password were not similar to endangered standards.
In this section, the proposed Scheme IHA was examined based on security and efficiency. We compared the proposed IHA scheme with two recent schemes, namely, SRIH [
27] and ESIH [
28], to prove the supremacy of our proposed scheme. We analyzed our scheme in terms of communication cost, computational cost, memory overhead, failure cost for cluster authentication, and reliability against malicious nodes.
5.1. Memory Overhead
The node of each member holds its public key g-1 and a private key, which is a group size g. For a 64-bit key, if a group consists of 15 soldiers, then each device will have
stored bytes for public keys of 14 soldiers, as well as their private keys. Likewise, when a key has 128 bits, then each device holds 240 bytes. Its group size effect on the requirements for the maintenance of individual nodes is shown in
Figure 4a. The results show that increasing the number of bands also enhances the requirement of memory for a device.
For a key with a 64-bits size, if a group consists of 20 soldiers, then every soldier has
store bytes for 19 public keys and a private key. If the network size increases and the bandwidth remains the same, the storage requirement on a single node will remain the same.
Figure 4b illustrates where the size of the network fluctuates from 200 to 2,000 soldiers with a constant number of 20 soldiers. The 128-bit key size results are also presented, where every soldier has
stored bytes, the public keys of 19 soldiers, and their private keys.
5.2. Failure Authentication Cost and Reliability
During the migration process of a node, four internal clusters and two or more cluster messages are shared. The total cost of internal clusters for the process of authentication is wasted when a soldier is attacked before joining. Computational and communication efforts can be lost in this scenario. During the process of joining, before testing, four messages will be shared among , , and NA.
The overall failure authentication cost can be considered as
Total Cost = Hfail × Mfail, where
Hfail is an authentication failure, and
Mfail represents the amount of failed authentication. The default value
Hfail is calculated as in Equation (5), where
are messages to be accounted for, and
demonstrate the ability to transmit a message during and between cluster interactions. We observed that during the migration of a node, four cluster messages are transferred within the network, so the value is 4 × 0.1 mJ = 0.4 mJ, as shown in
Figure 5a.
Therefore, if in four groups of 20 nodes, four authentication attempts fail, the total value of the above formula is 1.6 mJ.
Thus, the cost of sending cluster messages is shown separately in
Figure 5b, which is estimated to be unsuccessful by an increase in failed authentication. Malicious nodes have an impact on the message transmission reliability of the nodes. When two nodes have a loss of 20 nodes in a group, the reliability of our group is 0.9. This means that our system provides 90% reliability when two combined messages are lost due to two malicious nodes. In this process, 18 nodes can be joined to the group.
5.3. Computational Cost
In the authentication scenario, the
forwards the security credentials to the GH in the request message to join the specific group. Moreover, the image hashing technique is utilized for node authentication. As shown in
Figure 6a, we computed the computational cost in terms of the number of nodes at the GH. The results show that the computational cost varies with the number of nodes. We consider the communication cost when the number of nodes is 200. Then, the computational cost of the IHA, ESIH, and SRIH is 36.79 ms, 98.23 ms, and 104.51 ms, respectively. As shown in
Figure 6b, we computed the computational cost in terms of the number of nodes at the NA.
The results show that the computational cost varies with the number of nodes. We consider the communication cost when the number of nodes is 200. Then, the computational cost of the IHA, ESIH, and SRIH is 33.29 ms, 112.04 ms, and 119.61 ms, respectively. The results show that the computational cost of our proposed scheme is lower than that for the SRIH and ESIH, as these schemes also consider the image processing along with image hashing in the node authentication phases. The network administrator forwards the encrypted message with the required security credentials to the GH as per the request. The authentication of the node depends upon the information of the NA.
5.4. Communication Cost
We compared our scheme with SRIH and ESIH schemes to calculate the communication cost with the number of nodes. The registration phase of all the nodes is already established when these nodes join the network. Therefore, the proposed IHA remains efficient with the increase in the number of nodes. The authentication phase is further divided into two phases, communication between
and
and communication between
and NA.
Figure 7a elaborates the communication cost for phase 1 authentication. In phase 1, for a better understanding, we considered the communication cost for a single node authorization. Thus,
forwards the join request to
. In this request,
forwards the ID of 16 bits, 64 bits of timestamp, 64 bits of the nonce value, and 256 bits of the hash message. In this case, 400 bits are forwarded to
. The proposed IHA was compared with SRIH and ESIH for the communication cost of authentication phase 1 in terms of the number of nodes.
Figure 7b elaborates the communication cost for phase 2 authentication. In phase 2, for a better understanding, we considered the communication cost for a single node. Thus,
forwards the request message of 256 bits to the NA. In reply, the NA forwards the required information message of 400 bits. The proposed IHA was compared with SRIH and ESIH for the communication cost of authentication phase 1 in terms of the number of nodes. The total communication cost was analyzed in both cases based on the total number of nodes. The results show that the communication cost of our proposed scheme is lower than that of the SRIH and ESIH, as these schemes also consider the image processing along with image hashing in the node authentication phases.
6. Conclusions
Mobile ad hoc networks (MANETs) have an essential role to play in future smart environments involving the Internet of Things (IoT) for managing node mobility. In IoT-based systems, they provide self-formation and self-connectedness of networks. Since any node can freely join or leave the network in MANETS, it renders the networks and applications vulnerable to security attacks. Therefore, the provision of secure communication is an essential requirement for nodes in MANETs.
This paper presents a node joining and node migration algorithm for war situations. It involves effective authentication using an image hashing-based security approach which involves a timestamp to guard against a replay attack. The scheme protects against the intruder’s attack during the mobility of the node to join the target group. To allow joining, the GH receives the security credentials and hash of images from the node and verifies them with the credentials received from the NA. This reduces the infiltration of vulnerable nodes in the group for war situations or troop-based operations. Moreover, the age of the message is also crosschecked to guard against bit alteration attacks. The proposed work was validated through extensive simulations using NS 2.35. Results elucidate that the proposed scheme dominates its counterparts in terms of computational cost and communication cost for the GH and NA. Moreover, the failure cost of cluster authentication and reliability of malicious nodes is also presented. Results prove the supremacy of our proposed scheme. For the authentication of a node within a group, IHA provides 33% and 30% lower computational costs than SRIH and ESIH, respectively. Moreover, IHA provides 22% and 17% lower communication costs than ESIH and SRIH, respectively.
In the future, we plan to manage two-group fusion and security credential handling under one elected GH with more member nodes.