A Survey on Botnets: Incentives, Evolution, Detection and Current Trends
Abstract
:1. Introduction
1.1. Contribution and Research Questions
- What incentives are behind the development of botnet attacks?
- How have botnet attacks evolved over time?
- What has the research industry proposed to mitigate the threat of botnets?
- What current trends and challenges related to botnets have been identified by contemporary research?
1.2. Outline
2. Related Work
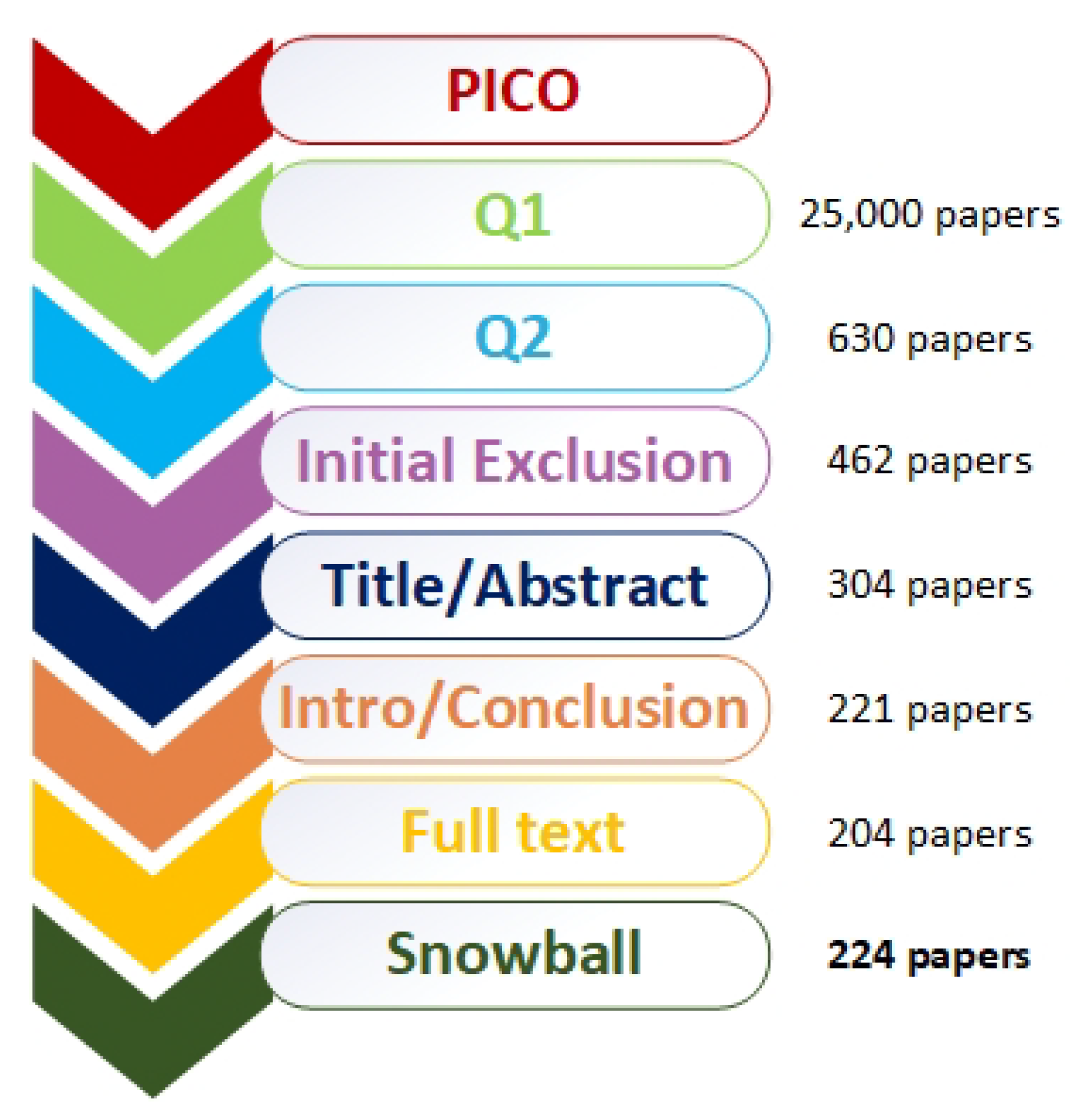
3. Methodology
3.1. Search Strategy
- Population: The paper is interested in all research focused on botnet incentives, evolution, detection and mitigation, including other surveys. Malware in general is considered too broad, and only papers focused specifically on botnets are included.
- Intervention: Does not apply as all papers within the research space of botnets are interesting for the purpose of the survey.
- Comparison: Different approaches to the detection of botnets in particular are compared to identify advantages/disadvantages. The frequency distribution of detection and mitigation mechanisms described in papers are also compared.
- Outcomes: Expected results are an overview of botnet progression and mitigation mechanisms as well as an identification of current trends based on the aforementioned overview.
3.2. Exclusion/Inclusion Process
3.2.1. Initial Exclusion
- Papers from 2005 or newer
- English language papers only
- Botnet-related papers only
- Open Access or free for DTU students to read through DTU FindIt
- Has a Digital Object Identifier (DOI) [40]
- Peer Reviewed.
3.2.2. Title and Abstract Review
3.2.3. Introduction/Conclusions Review
3.2.4. Full Text Review
3.2.5. Backwards Snowball Sampling
4. Incentives
4.1. Malevolent Botnets
- A desire to harm a designated target or group of targets.
- A desire to better one’s (often the C&C master) monetary situation.
4.1.1. Designated Targets
4.1.2. Reasons for Attack
4.2. Benevolent Botnets
- A decentralised P2P distributed hash table, rather than Mirai’s C&C approach.
- A far greater number of ways to infect new hosts.
- The usage of a custom made protocol for disseminating files.
5. Evolution of Botnets
5.1. Disguises and Subterfuge
5.2. P2P-Based Botnets and Their Intricacies
5.3. Extension and Browser Based Botnets
5.4. Smartphone-Based Botnets
5.5. Vehicular Botnets and Its Effect on Modern Traffic
5.6. Blockchain-Based Botnets
5.7. IoT-Based Botnets
5.8. Atypical New Botnet Variants
6. Detection and Mitigation
6.1. Detection Mechanisms—Techniques
6.1.1. Neural Network Detection Mechanisms
6.1.2. Machine Learning and Network-Based Detection Mechanisms
6.1.3. Domain Name System (DNS) Based Detection
6.1.4. Detection Mechanisms—Pervasive Computing Paradigms
6.1.5. IoT and P2P Botnets
6.1.6. Mobile Botnets
6.1.7. Vehicle Networks
6.1.8. Social Network Botnets
6.2. Mitigation Mechanisms
6.2.1. Best Practices for End-Users and Organisations
- Updating/changing passwords: typically, botnets will try to access credentials from all connected devices and web accounts. The best way of protection is to follow the rules of ensuring high entropy of random password generation and execute frequent updates.
- Updating devices: infections are coming from unwanted vulnerabilities. Updating the operating system and the integrated software can help prevent devices from being compromised.
- Updating/using anti-malware and anti-virus tools: remediation tools and anti-viruses can erase malware infection and protect the device against new ones.
- Being aware: the hardest part to protect from is human behaviour. There ar multiple incentives, but botnets such as GOZ are mostly coming from spam and phishing messages, which can be avoided if the potential victim is aware of this potential threat source.
6.2.2. Network-Level Blocking and Packet Analysis
6.2.3. Honeypots and Botnet Isolation
6.2.4. Attacking P2P Botnets
6.2.5. Mitigation against IoT Attacks and Botnets
6.2.6. Community Driven Tools against Botnets
6.2.7. Botnet Mitigation with Potential Ethical Issues
7. Current Trends and Challenges
7.1. The Continued Spread of Botnets within Pervasive Computing (VANETs, IoT and Mobile)
7.2. Increasing Complexity of Botnets
7.3. Social Botnets
7.4. Machine Learning and Neural Networks for Botnet Detection
7.5. Proactive Botnet Mitigation
7.6. Cloud-Based Botnets
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Silva, S.S.; Silva, R.M.; Pinto, R.C.; Salles, R.M. Botnets: A survey. Comput. Netw. 2013, 57, 378–403, Botnet Activity: Analysis, Detection and Shutdown. [Google Scholar] [CrossRef]
- Margolis, J.; Oh, T.T.; Jadhav, S.; Kim, Y.H.; Kim, J.N. An In-Depth Analysis of the Mirai Botnet. In Proceedings of the 2017 International Conference on Software Security and Assurance (ICSSA), Altoona, PA, USA, 24–25 July 2017; pp. 6–12. [Google Scholar] [CrossRef]
- Haria, S. The growth of the hide and seek botnet. Netw. Secur. 2019, 2019, 14–17. [Google Scholar] [CrossRef]
- ENISA Threat Landscape 2020—Botnet. Available online: https://www.enisa.europa.eu/publications/enisa-threat-landscape-2020-botnet (accessed on 28 May 2021).
- Hsiao, S.; Chen, Y.-N.; Sun, Y.S.; Chen, M.C. A cooperative botnet profiling and detection in virtualized environment. In Proceedings of the 2013 IEEE Conference on Communications and Network Security (CNS), National Harbor, MD, USA, 14–16 October 2013; pp. 154–162. [Google Scholar] [CrossRef] [Green Version]
- European Union Agency Cybersecurity. Available online: https://www.enisa.europa.eu/topics/csirts-in-europe/glossary/botnets (accessed on 30 July 2020).
- Zhang, W.; Wang, Y.J.; Wang, X.L. A Survey of Defense against P2P Botnets. In Proceedings of the 2014 IEEE 12th International Conference on Dependable, Autonomic and Secure Computing, Dalian, China, 24–27 August 2014; pp. 97–102. [Google Scholar] [CrossRef]
- Ianelli, N.; Hackworth, A. Botnets as a Vehicle for Online Crime. CERT Coord. Cent. 2005, 28, 19–39. [Google Scholar] [CrossRef]
- Etaher, N.; Weir, G.R.S.; Alazab, M. From ZeuS to Zitmo: Trends in Banking Malware. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; Volume 1, pp. 1386–1391. [Google Scholar] [CrossRef] [Green Version]
- Elliott, C. Botnets: To what extent are they a threat to information security? Inf. Secur. Tech. Rep. 2010, 15, 79–103, Computer Crime—A 2011 Update. [Google Scholar] [CrossRef]
- Eslahi, M.; Salleh, R.; Anuar, N.B. Bots and botnets: An overview of characteristics, detection and challenges. In Proceedings of the 2012 IEEE International Conference on Control System, Computing and Engineering, Penang, Malaysia, 23–25 November 2012; pp. 349–354. [Google Scholar] [CrossRef]
- Garip, M.T.; Lin, J.; Reiher, P.; Gerla, M. SHIELDNET: An Adaptive Detection Mechanism against Vehicular Botnets in VANETs. In Proceedings of the 2019 IEEE Vehicular Networking Conference (VNC), Los Angeles, CA, USA, 4–6 December 2019; p. 9062790. [Google Scholar] [CrossRef]
- Garg, S.; Sharma, R.M. Anatomy of botnet on application layer: Mechanism and mitigation. In Proceedings of the 2017 2nd International Conference for Convergence in Technology, I2CT 2017, Mumbai, India, 7–9 April 2017; pp. 1024–1029. [Google Scholar] [CrossRef]
- Lange, T.; Kettani, H. On Security Threats of Botnets to Cyber Systems. In Proceedings of the 2019 6th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 7–8 March 2019; pp. 176–183. [Google Scholar] [CrossRef]
- García, S.; Zunino, A.; Campo, M. Survey on network-based botnet detection methods. Secur. Commun. Netw. 2014, 7, 878–903. [Google Scholar] [CrossRef]
- Karim, A.; Salleh, R.; Shiraz, M.; Shah, S.; AWAN, I.; Anuar, N. Botnet detection techniques: Review, future trends and issues. J. Zhejian Univ. Comput. Electron. 2014, 15, 943–983. [Google Scholar] [CrossRef]
- Khehra, G.; Sofat, S. Botnet Detection Techniques: A Review. In Proceedings of the 2018 Second International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 14–15 June 2018; pp. 1319–1326. [Google Scholar] [CrossRef]
- Abdullah, Z.; Saudi, M. RAPID-Risk Assessment of Android Permission and Application Programming Interface (API) Call for Android Botnet. Int. J. Emerg. Technol. Learn. 2018, 7, 49–54. [Google Scholar] [CrossRef] [Green Version]
- Kothari, S. Real Time Analysis of Android Applications by Calculating Risk Factor to Identify Botnet Attack. Lect. Notes Electr. Eng. 2020, 570, 55–62. [Google Scholar] [CrossRef]
- Eslahi, M.; Salleh, R.; Anuar, N.B. MoBots: A new generation of botnets on mobile devices and networks. In Proceedings of the ISCAIE 2012—2012 IEEE Symposium on Computer Applications and Industrial Electronics, Kota Kinabalu, Malaysia, 3–4 December 2012; p. 6482109. [Google Scholar] [CrossRef]
- Kaur, N.; Singh, M. Botnet and botnet detection techniques in cyber realm. In Proceedings of the 2016 International Conference on Inventive Computation Technologies (ICICT), Tamilnadu, India, 26–27 August 2016; Volume 3, pp. 1–7. [Google Scholar] [CrossRef]
- Feily, M.; Shahrestani, A.; Ramadass, S. A Survey of Botnet and Botnet Detection. In Proceedings of the 2009 Third International Conference on Emerging Security Information, Systems and Technologies, Athens, Greece, 18–23 June 2009; pp. 268–273. [Google Scholar] [CrossRef]
- Abdullah, R.; Abu, N.; Abdollah, M.; Muhamad Noh, Z.A. Understanding the Threats of Botnets Detection: A Wide Scale Survey. Res. J. Inf. Technol. 2014, 6, 135–153. [Google Scholar] [CrossRef] [Green Version]
- Gaonkar, S.; Dessai, N.F.; Costa, J.; Borkar, A.; Aswale, S.; Shetgaonkar, P. A Survey on Botnet Detection Techniques. In Proceedings of the 2020 International Conference on Emerging Trends in Information Technology and Engineering (IC-ETITE), Vellore, India, 24–25 February 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Shetu, S.F.; Saifuzzaman, M.; Moon, N.N.; Nur, F.N. A Survey of Botnet in Cyber Security. In Proceedings of the 2019 2nd International Conference on Intelligent Communication and Computational Techniques (ICCT), Jaipur, India, 28–29 September 2019; pp. 174–177. [Google Scholar] [CrossRef]
- Stevanovic, M.; Pedersen, J.M. An analysis of network traffic classification for botnet detection. In Proceedings of the 2015 International Conference on Cyber Situational Awareness, Data Analytics and Assessment (Cybersa), London, UK, 8–9 June 2015; p. 8. [Google Scholar] [CrossRef]
- Haddadi, F.; Le Cong, D.; Porter, L.; Zincir-Heywood, A.N. On the Effectiveness of Different Botnet Detection Approaches. In Information Security Practice and Experience; Lopez, J., Wu, Y., Eds.; Springer International Publishing: Cham, Switzerland, 2015; pp. 121–135. [Google Scholar]
- Alazzam, H.; Alsmady, A.; Shorman, A.A. Supervised Detection of IoT Botnet Attacks. In Proceedings of the Second International Conference on Data Science, E-Learning and Information Systems, DATA ’19, Dubai, United Arab Emirates, 2–5 December 2019; Association for Computing Machinery: New York, NY, USA, 2019. [Google Scholar] [CrossRef]
- Falco, G.; Li, C.; Fedorov, P.; Caldera, C.; Arora, R.; Jackson, K. NeuroMesh: IoT security enabled by a blockchain powered botnet vaccine. ACM Int. Conf. Proc. Ser. 2019, 148162, 1–6. [Google Scholar] [CrossRef] [Green Version]
- Hoque, N.; Bhattacharyya, D.K.; Kalita, J.K. Botnet in DDoS Attacks: Trends and Challenges. IEEE Commun. Surv. Tutor. 2015, 17, 2242–2270. [Google Scholar] [CrossRef]
- Dange, S.; Chatterjee, M. IoT Botnet: The Largest Threat to the IoT Network. Adv. Intell. Syst. Comput. 2020, 1049, 137–157. [Google Scholar] [CrossRef]
- Wazzan, M.; Algazzawi, D.; Bamasaq, O.; Albeshri, A.; Cheng, L. Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research. Appl. Sci. 2021, 11, 5713. [Google Scholar] [CrossRef]
- Raghava, N.S.; Sahgal, D.; Chandna, S. Classification of Botnet Detection Based on Botnet Architechture. In Proceedings of the 2012 International Conference on Communication Systems and Network Technologies, Bangalore, India, 3–7 January 2012; pp. 569–572. [Google Scholar] [CrossRef]
- Zhang, W.; Jin, C. The Research on Approaches for Botnet Detection. Energy Procedia 2011, 13, 9726–9732. [Google Scholar] [CrossRef]
- Soe, Y.N.; Feng, Y.; Santosa, P.I.; Hartanto, R.; Sakurai, K. Machine learning-based IoT-botnet attack detection with sequential architecture. Sensors 2020, 20, 4372. [Google Scholar] [CrossRef] [PubMed]
- Abraham, B.; Mandya, A.; Bapat, R.; Alali, F.; Brown, D.E.; Veeraraghavan, M. A Comparison of Machine Learning Approaches to Detect Botnet Traffic. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de janeiro, Brazil, 8–13 July 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Petersen, K.; Vakkalanka, S.; Kuzniarz, L. Guidelines for conducting systematic mapping studies in software engineering: An update. Inf. Softw. Technol. 2015, 64, 1–18. [Google Scholar] [CrossRef]
- Wohlin, C. Guidelines for Snowballing in Systematic Literature Studies and a Replication in Software Engineering; EASE ’14.; Association for Computing Machinery: New York, NY, USA, 2014. [Google Scholar] [CrossRef]
- Petticrew, M.; Roberts, H. Systematic Reviews in the Social Sciences: A Practical Guide; John Wiley & Sons: Hoboken, NJ, USA, 2008. [Google Scholar] [CrossRef]
- Digital Object Identifier FAQs. Available online: https://www.doi.org/faq.html (accessed on 14 December 2020).
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Nazario, J. Politically motivated denial of service attacks. Cryptol. Inf. Secur. Ser. 2009, 3, 163–181. [Google Scholar] [CrossRef]
- Sgouras, K.I.; Kyriakidis, A.N.; Labridis, D.P. Short-term risk assessment of botnet attacks on advanced metering infrastructure. IET Cyber-Phys. Syst. Theory Appl. 2017, 2, 143–151. [Google Scholar] [CrossRef]
- Li, Z.; Liao, Q.; Blaich, A.; Striegel, A. Fighting botnets with economic uncertainty. Secur. Commun. Netw. 2011, 4, 1104–1113. [Google Scholar] [CrossRef]
- Salamatian, S.; Huleihel, W.; Beirami, A.; Cohen, A.; Médard, M. Why Botnets Work: Distributed Brute-Force Attacks Need No Synchronization. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2288–2299. [Google Scholar] [CrossRef]
- Dev, J.A. Usage of botnets for high speed MD5 hash cracking. In Proceedings of the 2013 3rd International Conference on Innovative Computing Technology, Intech 2013, London, UK, 29–31 August 2013; p. 6653658. [Google Scholar] [CrossRef]
- Bederna, Z.; Szadeczky, T. Cyber espionage through Botnets. Secur. J. 2020, 33, 43–62. [Google Scholar] [CrossRef] [Green Version]
- Herwig, S.; Harvey, K.; Hughey, G.; Roberts, R.; Levin, D. Measurement and Analysis of Hajime, a Peer-to-peer IoT Botnet. In Proceedings of the Network and Distributed Systems Security (NDSS) Symposium, San Diego, CA, USA, 24–27 February 2019; p. 15. [Google Scholar] [CrossRef]
- Xiang, C.; Lihua, Y.; Shuyuan, J.; Zhiyu, H.; Shuhao, L. Botnet spoofing: Fighting botnet with itself. Secur. Commun. Netw. 2015, 8, 80–89. [Google Scholar] [CrossRef]
- Osagie, M.S.U.; Enagbonma, O.; Inyang, A.I. The Historical Perspective of Botnet Tools. arXiv 2019, arXiv:1904.00948. [Google Scholar] [CrossRef]
- Goodin, D. Record-Breaking DDoS Reportedly Delivered by >145 k hacked Cameras. Available online: arstechnica.com/information-technology/2016/09/botnet-of-145k-cameras-reportedly-deliver-internets-biggest-ddos-ever/ (accessed on 30 July 2021).
- Fruhlinger, J. The Mirai Botnet Explained: How Teen Scammers and CCTV Cameras almost Brought down the Internet. Available online: csoonline.com/article/3258748/the-mirai-botnet-explained-how-teen-scammers-and-cctv-cameras-almost-brought-down-the-internet.html (accessed on 30 July 2021).
- Office of Public Affairs (USA Department of Justice)—“U.S. Leads Multi-National Action against Gameover Zeus Botnet and Cryptolocker Ransomware, Charges Botnet Administrator”. Available online: https://www.justice.gov/opa/pr/us-leads-multi-national-action-against-gameover-zeus-botnet-and-cryptolocker-ransomware (accessed on 30 July 2021).
- Dabrowski, A.; Ullrich, J.; Weippl, E.R. Botnets causing blackouts: How coordinated load attacks can destabilize the power grid. Elektrotechnik Und Informationstechnik 2018, 135, 250–255. [Google Scholar] [CrossRef]
- Zou, C.C.; Cunningham, R. Honeypot-aware advanced botnet construction and maintenance. Proc. Int. Conf. Dependable Syst. Netw. 2006, 2006, 1633509. [Google Scholar] [CrossRef] [Green Version]
- Zeng, J.; Tang, W.; Liu, C.; Hu, J.; Peng, L. Efficient detect scheme of botnet command and control communication. Commun. Comput. Inf. Sci. 2012, 307, 576–581. [Google Scholar] [CrossRef]
- Abu Rajab, M.; Zarfoss, J.; Monrose, F.; Terzis, A. A multifaceted approach to understanding the botnet phenomenon. In Proceedings of the 6th ACM SIGCOMM Conference on Internet Measurement, Rio de Janeriro, Brazil, 25–27 October 2006; pp. 41–52. [Google Scholar] [CrossRef]
- Heron, S. Working the botnet: How dynamic DNS is revitalising the zombie army. Netw. Secur. 2007, 2007, 9–11. [Google Scholar] [CrossRef]
- Liu, C.; Lu, W.; Zhang, Z.; Liao, P.; Cui, X. A recoverable hybrid C C botnet. In Proceedings of the 2011 6th International Conference on Malicious and Unwanted Software, Fajardo, PR, USA, 18–19 October 2011; pp. 110–118. [Google Scholar] [CrossRef]
- Yin, T.; Zhang, Y.; Li, S. DR-SNBot: A Social Network-Based Botnet with Strong Destroy-Resistance. In Proceedings of the 2014 9th IEEE International Conference on Networking, Architecture, and Storage, Tianjin, China, 6–8 August 2014; pp. 191–199. [Google Scholar] [CrossRef]
- Sood, A.K.; Zeadally, S.; Enbody, R.J. An Empirical Study of HTTP-based Financial Botnets. IEEE Trans. Dependable Secur. Comput. 2016, 13, 6991594. [Google Scholar] [CrossRef]
- Wang, H.; Gong, Z. Collaboration-based botnet detection architecture. In Proceedings of the 2009 2nd International Conference on Intelligent Computing Technology and Automation, ICICTA 2009, Changsha, China, 10–11 October 2009; Volume 2, p. 5287910. [Google Scholar] [CrossRef]
- Ogu, E.C.; Ojesanmi, O.A.; Awodele, O.; Kuyoro, S. A botnets circumspection: The current threat landscape, and what we know so far. Information 2019, 10, 337. [Google Scholar] [CrossRef] [Green Version]
- Chen, Z.; Chen, C.; Wang, Q. Delay-Tolerant botnets. In Proceedings of the International Conference on Computer Communications and Networks, ICCCN, San Francisco, CA, USA, 3–6 August 2009; p. 5235321. [Google Scholar] [CrossRef]
- Anagnostopoulos, M.; Kambourakis, G.; Gritzalis, S. New facets of mobile botnet: Architecture and evaluation. Int. J. Inf. Secur. 2016, 15, 455–473. [Google Scholar] [CrossRef]
- Hamon, V. Android botnets for multi-targeted attacks. J. Comput. Virol. Hacking Tech. 2015, 11, 193–202. [Google Scholar] [CrossRef]
- Mulliner, C.; Seifert, J.P. Rise of the iBots: Owning a telco network. In Proceedings of the 5th IEEE International Conference on Malicious and Unwanted Software, Malware 2010, Nancy, France, 19–20 October 2010; p. 5665790. [Google Scholar] [CrossRef]
- Malatras, A.; Freyssinet, E.; Beslay, L. Mobile Botnets Taxonomy and Challenges. In Proceedings of the 2015 European Intelligence and Security Informatics Conference, EISIC 2015, Manchester, UK, 7–9 September 2015; p. 7379739. [Google Scholar] [CrossRef]
- Rodriguez-Gomez, R.A.; Macia-Fernandez, G.; Garcia-Teodoro, P. Survey and taxonomy of botnet research through life-cycle. ACM Comput. Surv. 2013, 45, 2501659. [Google Scholar] [CrossRef]
- Pieterse, H.; Olivier, M.S. Android botnets on the rise: Trends and characteristics. In Proceedings of the 2012 Information Security for South Africa—Proceedings of the ISSA 2012 Conference, Johannesburg, South Africa, 15–17 August 2012; p. 6320432. [Google Scholar] [CrossRef]
- Chang, W.; Wang, A.; Mohaisen, A.; Chen, S. Characterizing botnets-as-a-service. In Proceedings of the Sigcomm 2014 ACM Conference on Special Interest Group on Data Communication, Chicago, IL, USA, 17–22 August 2014; Volume 44, pp. 585–586. [Google Scholar] [CrossRef]
- Li, H.; Hu, G.; Yang, Y. Research on P2P botnet network behaviors and modeling. Commun. Comput. Inf. Sci. 2012, 307, 82–89. [Google Scholar] [CrossRef]
- Aanjankumar, S.; Poonkuntran, S. An efficient soft computing approach for securing information over GAMEOVER Zeus Botnets with modified CPA algorithm. Soft Comput. 2020, 24, 16499–16507. [Google Scholar] [CrossRef]
- Yan, G.; Ha, D.T.; Eidenbenz, S. AntBot: Anti-pollution peer-to-peer botnets. Comput. Netw. 2011, 55, 1941–1956. [Google Scholar] [CrossRef]
- Andriesse, D.; Rossow, C.; Stone-Gross, B.; Plohmann, D.; Bos, H. Highly resilient peer-to-peer botnets are here: An analysis of Gameover Zeus. In Proceedings of the 2013 8th International Conference on Malicious and Unwanted Software: “The Americas”, Malware 2013, Fajardo, PR, USA, 22–24 October 2013; p. 6703693. [Google Scholar] [CrossRef] [Green Version]
- Zhuang, D.; Morris Chang, J. Enhanced PeerHunter: Detecting Peer-To-Peer Botnets Through Network-Flow Level Community Behavior Analysis. IEEE Trans. Inf. Forensics Secur. 2019, 14, 8536452. [Google Scholar] [CrossRef] [Green Version]
- Rossow, C.; Andriesse, D.; Werner, T.; Stone-Gross, B.; Plohmann, D.; Dietrich, C.J.; Bos, H. SoK: P2PWNED—Modeling and evaluating the resilience of peer-to-peer botnets. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; p. 6547104. [Google Scholar] [CrossRef] [Green Version]
- Wang, T.; Wang, H.; Liu, B.; Shi, P. What is the pattern of a botnet? In Proceedings of the 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Trustcom 2013, Melbourne, Australia, 16–18 July 2013; p. 6680849. [Google Scholar] [CrossRef]
- Perrotta, R.; Hao, F. Botnet in the browser: Understanding threats caused by malicious browser extensions. IEEE Secur. Priv. 2018, 16, 8425617. [Google Scholar] [CrossRef] [Green Version]
- Boshmaf, Y.; Muslukhov, I.; Beznosov, K.; Ripeanu, M. Design and analysis of a social botnet. Comput. Netw. 2013, 57, 556–578. [Google Scholar] [CrossRef] [Green Version]
- Garip, M.T.; Reiher, P.; Gerla, M. Ghost: Concealing vehicular botnet communication in the VANET control channel. In Proceedings of the 2016 International Wireless Communications and Mobile Computing Conference, IWCMC 2016, Paphos, Cyprus, 5–9 September 2016; p. 7577024. [Google Scholar] [CrossRef]
- Yamaguchi, S. Botnet defense system: Concept, design, and basic strategy. Information 2020, 11, 516. [Google Scholar] [CrossRef]
- Bertino, E.; Islam, N. Botnets and Internet of Things Security. Computer 2017, 50, 7842850. [Google Scholar] [CrossRef]
- Mendes, L.D.; Aloi, J.; Pimenta, T.C. Analysis of IoT botnet architectures and recent defense proposals. Proc. Int. Conf. Microelectron. ICM 2019, 2019, 9021715. [Google Scholar] [CrossRef]
- Kudo, T.; Kimura, T.; Inoue, Y.; Aman, H.; Hirata, K. Behavior analysis of self-evolving botnets. In Proceedings of the IEEE CITS 2016—2016 International Conference on Computer, Information and Telecommunication Systems, Kunming, China, 6–8 July 2016; p. 7546428. [Google Scholar] [CrossRef]
- Bock, L.; Alexopoulos, N.; Saracoglu, E.; Muhlhauser, M.; Vasilomanolakis, E. Assessing the Threat of Blockchain-based Botnets. Ecrime Res. Summit Ecrime 2019, 2019, 9037600. [Google Scholar] [CrossRef]
- Yin, J.; Lv, H.; Zhang, F.; Tian, Z.; Cui, X. Study on advanced botnet based on publicly available resources. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2018; Volume 11149, pp. 57–74. [Google Scholar] [CrossRef]
- Hua, J.; Sakurai, K. A SMS-Based Mobile Botnet Using Flooding Algorithm. In Information Security Theory and Practice. Security and Privacy of Mobile Devices in Wireless Communication; Ardagna, C.A., Zhou, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 264–279. [Google Scholar]
- Geng, G.; Xu, G.; Zhang, M.; Yang, Y.; Yang, G. An improved SMS based heterogeneous mobile botnet model. In Proceedings of the 2011 IEEE International Conference on Information and Automation, ICIA 2011, Shenzhen, China, 6–8 June 2011; p. 5948987. [Google Scholar] [CrossRef]
- Lee, H.; Kang, T.; Lee, S.; Kim, J.; Kim, Y. Punobot: Mobile Botnet Using Push Notification Service in Android. In Information Security Applications; Kim, Y., Lee, H., Perrig, A., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 124–137. [Google Scholar]
- Porras, P.; Saidi, H.; Yegneswaran, V. An Analysis of the iKee.B iPhone Botnet. In Security and Privacy in Mobile Information and Communication; Springer: Berlin/Heidelberg, Germany, 2010; pp. 141–152. [Google Scholar]
- Li, X.G.; Wang, J.F. Traffic detection of transmission of botnet threat using BP neural network. Neural Netw. World 2018, 28, 511–522. [Google Scholar] [CrossRef] [Green Version]
- Nguyen, H.T.; Ngo, Q.D.; Le, V.H. A novel graph-based approach for IoT botnet detection. Int. J. Inf. Secur. 2020, 19, 567–577. [Google Scholar] [CrossRef]
- Pei, Z.; Gan, G. Research on p2p botnet traffic identification technology based on neural network. IOP Conf. Ser. Earth Environ. Sci. 2020, 428, 012011. [Google Scholar] [CrossRef]
- Taheri, S.; Salem, M.; Yuan, J.S. Leveraging image representation of network traffic data and transfer learning in botnet detection. Big Data Cogn. Comput. 2018, 2, 37. [Google Scholar] [CrossRef] [Green Version]
- Jung, W.; Zhao, H.; Sun, M.; Zhou, G. IoT botnet detection via power consumption modeling. Smart Health 2020, 15, 100103. [Google Scholar] [CrossRef]
- Kim, J.; Shim, M.; Hong, S.; Shin, Y.; Choi, E. Intelligent detection of iot botnets using machine learning and deep learning. Appl. Sci. 2020, 10, 7009. [Google Scholar] [CrossRef]
- Nogueira, A.; Salvador, P.; Blessa, F. A botnet detection system based on neural networks. In Proceedings of the 5th International Conference on Digital Telecommunications, ICDT 2010, Athens, Greece, 13–19 June 2010; p. 5532380. [Google Scholar] [CrossRef]
- Javed, Y.; Rajabi, N. Multi-Layer Perceptron Artificial Neural Network Based IoT Botnet Traffic Classification. Adv. Intell. Syst. Comput. 2020, 1069, 973–984. [Google Scholar] [CrossRef]
- Zeidanloo, H.R.; Hosseinpour, F.; Borazjani, P.N. Botnet detection based on common network behaviors by utilizing Artificial Immune System(AIS). In Proceedings of the ICSTE 2010—2010 2nd International Conference on Software Technology and Engineering, San Juan, PR, USA, 3–5 October 2010; Volume 1, p. 5608967. [Google Scholar] [CrossRef]
- Sriram, S.; Vinayakumar, R.; Alazab, M.; Soman, K.P. Network flow based IoT botnet attack detection using deep learning. In Proceedings of the IEEE Infocom 2020—IEEE Conference on Computer Communications Workshops, Infocom WKSHPS 2020, Toronto, ON, Canada, 6–9 July 2020; p. 9162668. [Google Scholar] [CrossRef]
- Jithu, P.; Shareena, J.; Ramdas, A.; Haripriya, A.P. Intrusion Detection System for IOT Botnet Attacks Using Deep Learning. SN Comput. Sci. 2021, 2, 1–8. [Google Scholar] [CrossRef]
- Alharbi, A.; Alosaimi, W.; Alyami, H.; Rauf, H.T.; Damasevicius, R. Botnet Attack Detection Using Local Global Best Bat Algorithm for Industrial Internet of Things. Electronics 2021, 10, 1341. [Google Scholar] [CrossRef]
- Kanehara, H.; Takahashi, T.; Murakami, Y.; Inoue, D.; Shimamura, J.; Murata, N. Real-time botnet detection using nonnegative tucker decomposition. Proc. ACM Symp. Appl. Comput. 2019, 147772, 1337–1344. [Google Scholar] [CrossRef]
- Bansal, A.; Mahapatra, S. A Comparative Analysis of Machine Learning Techniques for Botnet Detection. In Proceedings of the 10th International Conference on Security of Information and Networks, Jaipur, India, 13–15 October 2017; pp. 91–100. [Google Scholar] [CrossRef]
- Eustis, A.G. The Mirai Botnet and the Importance of IoT Device Security. In Proceedings of the 16th International Conference on Information Technology-New Generations (ITNG 2019), Las Vegas, NV, USA, 1–3 April 2019; Latifi, S., Ed.; Springer International Publishing: Cham, Switzerland, 2019; pp. 85–89. [Google Scholar]
- Ribeiro, G.H.; De Faria Paiva, E.R.; Miani, R.S. A comparison of stream mining algorithms on botnet detection. In Proceedings of the 15th International Conference on Availability, Reliability and Security, Dublin, Ireland, 25–28 August 2020; pp. 1–10. [Google Scholar] [CrossRef]
- Chu, Z.; Han, Y.; Zhao, K. Botnet Vulnerability Intelligence Clustering Classification Mining and Countermeasure Algorithm Based on Machine Learning. IEEE Access 2019, 7, 8935236. [Google Scholar] [CrossRef]
- Tuan, T.A.; Long, H.V.; Son, L.H.; Kumar, R.; Priyadarshini, I.; Son, N.T.K. Performance evaluation of Botnet DDoS attack detection using machine learning. Evol. Intell. 2020, 13, 283–294. [Google Scholar] [CrossRef]
- Indre, I.; Lemnaru, C. Detection and prevention system against cyber attacks and botnet malware for information systems and Internet of Things. In Proceedings of the 2016 IEEE 12th International Conference on Intelligent Computer Communication and Processing, ICCP 2016, Cluj-Napoca, Romania, 8–10 September 2016; p. 7737142. [Google Scholar] [CrossRef]
- Park, Y.; Kengalahalli, N.V.; Chang, S.Y. Distributed Security Network Functions against Botnet Attacks in Software-defined Networks. In Proceedings of the 2018 IEEE Conference on Network Function Virtualization and Software Defined Networks, NFV-SDN 2018, Verona, Italy, 27–29 November 2018; p. 8725657. [Google Scholar] [CrossRef]
- Lu, W.; Tavallaee, M.; Ghorbani, A.A. Automatic Discovery of Botnet Communities on Large-Scale Communication Networks. In Proceedings of the 4th International Symposium on Information, Computer, and Communications Security, ASIACCS ’09, Auckland, New Zealand, 9–12 July 2009; Association for Computing Machinery: New York, NY, USA, 2009; pp. 1–10. [Google Scholar] [CrossRef]
- Goyal, M.; Sahoo, I.; Geethakumari, G. HTTP Botnet Detection in IOT Devices using Network Traffic Analysis. In Proceedings of the 2019 International Conference on Recent Advances in Energy-Efficient Computing and Communication, ICRAECC 2019, Nagercoil, India, 7–20 March 2019; p. 8995160. [Google Scholar] [CrossRef]
- Heydari, B.; Yajam, H.; Akhaee, M.A.; Salehkalaibar, S. Utilizing Features of Aggregated Flows to Identify Botnet Network Traffic. In Proceedings of the 2017 14th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology, ISCISC 2017, Shiraz, Iran, 6–7 September 2017; p. 8488370. [Google Scholar] [CrossRef]
- Haddadi, F.; Morgan, J.; Filho, E.G.; Zincir-Heywood, A.N. Botnet behaviour analysis using IP flows: With http filters using classifiers. In Proceedings of the 2014 IEEE 28th International Conference on Advanced Information Networking and Applications Workshops, IEEE Waina 2014, Victoria, BC, Canada, 13–16 May 2014; p. 6844605. [Google Scholar] [CrossRef]
- Yong, W.; Tefera, S.H.; Beshah, Y.K. Understanding botnet: From mathematical modelling to integrated detection and mitigation framework. In Proceedings of the 13th ACIS International Conference on Software Engineering, Artificial Intelligence, Networking, and Parallel/distributed Computing, SNPD 2012, Kyoto, Japan, 8–10 August 2012; p. 6299259. [Google Scholar] [CrossRef]
- AsSadhan, B.; Bashaiwth, A.; Al-Muhtadi, J.; Alshebeili, S. Analysis of P2P, IRC and HTTP traffic for botnets detection. Peer-to-Peer Netw. Appl. 2018, 11, 848–861. [Google Scholar] [CrossRef]
- Zand, A.; Vigna, G.; Yan, X.; Kruegel, C. Extracting probable command and control signatures for detecting botnets. In Proceedings of the 29th Annual ACM Symposium on Applied Computing, Gyeongju, Korea, 24–28 March; pp. 1657–1662. [CrossRef]
- Khattak, S.; Ahmed, Z.; Syed, A.A.; Khayam, S.A. BotFlex: A community-driven tool for botnet detection. J. Netw. Comput. Appl. 2015, 58, 144–154. [Google Scholar] [CrossRef]
- Richer, T.J. Entropy-based detection of botnet command and control. In Proceedings of the Australasian Computer Science Week Multiconference, Geelong, Australia, 31 January–3 February 2017; p. a75. [Google Scholar] [CrossRef]
- AsSadhan, B.; Moura, J.M. An efficient method to detect periodic behavior in botnet traffic by analyzing control plane traffic. J. Adv. Res. 2014, 5, 435–448. [Google Scholar] [CrossRef] [Green Version]
- Lagraa, S.; François, J.; Lahmadi, A.; Miner, M.; Hammerschmidt, C.; State, R. BotGM: Unsupervised graph mining to detect botnets in traffic flows. In Proceedings of the 2017 1st Cyber Security in Networking Conference, CSNET 2017, Rio de Janeiro, Brazil, 18–20 October 2017; pp. 1–8. [Google Scholar] [CrossRef] [Green Version]
- Sousa, R.; Rodrigues, N.; Salvador, P.; Nogueira, A. Analyzing the Behavior of Top Spam Botnets. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; pp. 6540–6544. [Google Scholar] [CrossRef]
- Kozik, R.; Choraś, M. Pattern Extraction Algorithm for NetFlow-Based Botnet Activities Detection. Secur. Commun. Netw. 2017, 2017, 6047053. [Google Scholar] [CrossRef] [Green Version]
- Chen, R.; Niu, W.; Zhang, X.; Zhuo, Z.; Lv, F. An Effective Conversation-Based Botnet Detection Method. Math. Probl. Eng. 2017, 2017, 4934082. [Google Scholar] [CrossRef] [Green Version]
- Pandey, A.; Thaseen, S.; Aswani Kumar, C.; Li, G. Identification of botnet attacks using hybrid machine learning models. Adv. Intell. Syst. Comput. 2021, 1179, 249–257. [Google Scholar] [CrossRef]
- Kirubavathi, G.; Anitha, R. Botnet detection via mining of traffic flow characteristics. Comput. Electr. Eng. 2016, 50, 91–101. [Google Scholar] [CrossRef]
- Li, S.H.; Kao, Y.C.; Zhang, Z.C.; Chuang, Y.P.; Yen, D.C. A network behavior-based botnet detection mechanism using PSO and K-means. ACM Trans. Manag. Inf. Syst. 2015, 6, 3. [Google Scholar] [CrossRef]
- Su, S.C.; Chen, Y.R.; Tsai, S.C.; Lin, Y.B. Detecting P2P Botnet in Software Defined Networks. Secur. Commun. Netw. 2018, 2018, 4723862. [Google Scholar] [CrossRef] [Green Version]
- Vishwakarma, R.; Jain, A.K. A Honeypot with Machine Learning based Detection Framework for defending IoT based Botnet DDoS Attacks. In Proceedings of the 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 23–25 April 2019; pp. 1019–1024. [Google Scholar] [CrossRef]
- Al-Hakbani, M.M.; Dahshan, M.H. Avoiding honeypot detection in peer-to-peer botnets. In Proceedings of the ICETECH 2015—2015 IEEE International Conference on Engineering and Technology, Coimbatore, India, 20 March 2015; p. 7275017. [Google Scholar] [CrossRef]
- Dwyer, O.P.; Marnerides, A.K.; Giotsas, V.; Mursch, T. Profiling iot-based botnet traffic using DNS. In Proceedings of the 2019 IEEE Global Communications Conference, Globecom 2019, Waikoloa, HI, USA, 9–13 December 2019; p. 9014300. [Google Scholar] [CrossRef] [Green Version]
- Wang, K.; Huang, C.Y.; Tsai, L.Y.; Lin, Y.D. Behavior-based botnet detection in parallel. Secur. Commun. Netw. 2014, 7, 1849–1859. [Google Scholar] [CrossRef]
- Bahsi, H.; Nomm, S.; La Torre, F.B. Dimensionality Reduction for Machine Learning Based IoT Botnet Detection. In Proceedings of the 2018 15th International Conference on Control, Automation, Robotics and Vision (ICARCV), Singapore, 18–21 November 2018; pp. 1857–1862. [Google Scholar] [CrossRef]
- Beigi, E.B.; Jazi, H.H.; Stakhanova, N.; Ghorbani, A.A. Towards effective feature selection in machine learning-based botnet detection approaches. In Proceedings of the 2014 IEEE Conference on Communications and Network Security, CNS 2014, San Francisco, CA, USA, 29–31 October 2014; p. 6997492. [Google Scholar] [CrossRef]
- Lysenko, S.; Savenko, O.; Bobrovnikova, K.; Kryshchuk, A. Self-adaptive system for the corporate area network resilience in the presence of botnet cyberattacks. Commun. Comput. Inf. Sci. 2018, 860, 385–401. [Google Scholar] [CrossRef]
- Hung, C.L.; Wang, H.H. Parallel botnet detection system by using GPU. In Proceedings of the 2014 IEEE/ACIS 13th International Conference on Computer and Information Science, ICIS 2014, Taiyuan, China, 4–6 June 2014; p. 6912109. [Google Scholar] [CrossRef]
- Blaise, A.; Bouet, M.; Conan, V.; Secci, S. Botnet Fingerprinting: A Frequency Distributions Scheme for Lightweight Bot Detection. IEEE Trans. Netw. Serv. Manag. 2020, 17, 9097931. [Google Scholar] [CrossRef]
- Lin, S.C.; Chen, P.S.; Chang, C.C. A novel method of mining network flow to detect P2P botnets. Peer-to-Peer Netw. Appl. 2014, 7, 645–654. [Google Scholar] [CrossRef]
- Lee, Y.C.; Tseng, C.M.; Liu, T.J. A HTTP botnet detection system based on ranking mechanism. In Proceedings of the 2017 12th International Conference on Digital Information Management, ICDIM 2017, Fukuoka, Japan, 12–14 September2017; pp. 115–120. [Google Scholar] [CrossRef]
- Mai, L.; Noh, D.K. Cluster Ensemble with Link-Based Approach for Botnet Detection. J. Netw. Syst. Manag. 2018, 26, 616–639. [Google Scholar] [CrossRef]
- Lu, W.; Ghorbani, A.A. Botnets Detection Based on IRC-Community. In Proceedings of the IEEE GLOBECOM 2008—2008 IEEE Global Telecommunications Conference, New Orleans, LA, USA, 30 November–4 December 2008; pp. 1–5. [Google Scholar] [CrossRef]
- Hoang, X.D.; Nguyen, Q.C. Botnet detection based on machine learning techniques using DNS query data. Future Internet 2018, 10, 43. [Google Scholar] [CrossRef] [Green Version]
- Wang, Z.; Qin, M.; Chen, M.; Jia, C.; Ma, Y. A learning evasive email-based P2P-Like botnet. China Commun. 2018, 15, 15–24. [Google Scholar] [CrossRef]
- Rezaei, A. Using Ensemble Learning Technique for Detecting Botnet on IoT. SN Comput. Sci. 2021, 2, 1–14. [Google Scholar] [CrossRef]
- Lee, S.; Abdullah, A.; Jhanjhi, N.Z.; Kok, S.H. Honeypot Coupled Machine Learning Model for Botnet Detection and Classification in IoT Smart Factory—An Investigation. MATEC Web Conf. 2021, 335, 04003. [Google Scholar] [CrossRef]
- Ibrahim, W.N.H.; Anuar, S.; Selamat, A.; Krejcar, O.; Gonzalez Crespo, R.; Herrera-Viedma, E.; Fujita, H. Multilayer Framework for Botnet Detection Using Machine Learning Algorithms. IEEE Access 2021, 9, 9359784. [Google Scholar] [CrossRef]
- Hao, S.; Liu, D.; Baldi, S.; Yu, W. Unsupervised detection of botnet activities using frequent pattern tree mining. Complex Intell. Syst. 2021, 1–9. [Google Scholar] [CrossRef]
- Asadi, M. Detecting IoT botnets based on the combination of cooperative game theory with deep and machine learning approaches. J. Ambient. Intell. Humaniz. Comput. 2021, 1–15. [Google Scholar] [CrossRef]
- Bhatt, P.; Thakker, B. A Novel Forecastive Anomaly Based Botnet Revelation Framework for Competing Concerns in Internet of Things. J. Appl. Secur. Res. 2021, 16, 258–278. [Google Scholar] [CrossRef]
- Soleymani, A.; Arabgol, F. A Novel Approach for Detecting DGA-Based Botnets in DNS Queries Using Machine Learning Techniques. J. Comput. Netw. Commun. 2021, 2021, 4767388. [Google Scholar] [CrossRef]
- Panda, M.; Allah A. Mousa, A.; Ella Hassanien, A. Developing an Efficient Feature Engineering and Machine Learning Model for Detecting IoT-Botnet Cyber Attacks. IEEE Access 2021, 9, 91038–91052. [Google Scholar] [CrossRef]
- Kwon, J.; Lee, J.; Lee, H.; Perrig, A. PsyBoG: A scalable botnet detection method for large-scale DNS traffic. Comput. Netw. 2016, 97, 48–73. [Google Scholar] [CrossRef]
- Wang, T.S.; Lin, H.T.; Cheng, W.T.; Chen, C.Y. DBod: Clustering and detecting DGA-based botnets using DNS traffic analysis. Comput. Secur. 2017, 64, 1–15. [Google Scholar] [CrossRef]
- Zhao, D.; Traore, I.; Sayed, B.; Lu, W.; Saad, S.; Ghorbani, A.; Garant, D. Botnet detection based on traffic behavior analysis and flow intervals. Comput. Secur. 2013, 39, 2–16. [Google Scholar] [CrossRef]
- Ichise, H.; Jin, Y.; Iida, K. Analysis of via-resolver DNS TXT queries and detection possibility of botnet communications. In Proceedings of the IEEE Pacific Rim Conference on Communications, Computers, and Signal Processing, Victoria, BC, Canada, 24–26 August 2015; p. 7334837. [Google Scholar] [CrossRef]
- Jin, Y.; Ichise, H.; Iida, K. Design of Detecting Botnet Communication by Monitoring Direct Outbound DNS Queries. In Proceedings of the 2nd IEEE International Conference on Cyber Security and Cloud Computing, Cscloud 2015—IEEE International Symposium of Smart Cloud, IEEE SSC 2015, New York, NY, USA, 3–5 November 2015; p. 7371456. [Google Scholar] [CrossRef]
- Nguyen, T.D.; Dung, T.C.; Nguyen, L.G. DGA botnet detection using collaborative filtering and density-based clustering. In Proceedings of the Sixth International Symposium on Information and Communication Technology, Hue, Vietnam, 3–4 December 2015; pp. 203–209. [Google Scholar] [CrossRef]
- Mohd Safar, N.; Abdullah, N.; Kamaludin, H.; Abd Ishak, S.; Isa, M. Characterising and detection of botnet in P2P network for UDP protocol. Indones. J. Electr. Eng. Comput. Sci. 2020, 18, 1584–1595. [Google Scholar] [CrossRef]
- Tsai, M.H.; Chang, K.C.; Lin, C.C.; Mao, C.H.; Lee, H.M. C&C tracer: Botnet command and control behavior tracing. In Proceedings of the IEEE International Conference on Systems, Man and Cybernetics, Anchorage, AK, USA, 9–12 October 2011; p. 6083942. [Google Scholar] [CrossRef]
- Lysenko, S.; Bobrovnikova, K.; Savenko, O.; Kryshchuk, A. BotGRABBER: SVM-Based Self-Adaptive System for the Network Resilience against the Botnets Cyberattacks. Commun. Comput. Inf. Sci. 2019, 1039, 127–143. [Google Scholar] [CrossRef]
- Tong, V.; Nguyen, G. A method for detecting DGA botnet based on semantic and cluster analysis. In Proceedings of the Seventh Symposium on Information and Communication Technology, Ho Chi Minh, Vietnam, 8–9 December 2016; pp. 272–277. [Google Scholar] [CrossRef]
- Kelley, T.; Furey, E. Getting Prepared for the Next Botnet Attack: Detecting Algorithmically Generated Domains in Botnet Command and Control. In Proceedings of the 2018 29th Irish Signals and Systems Conference (ISSC), Belfast, UK, 21–22 June 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Vishvakarma, D.K.; Bhatia, A.; Riha, Z. Detection of Algorithmically Generated Domain Names in Botnets. In Advanced Information Networking and Applications; Barolli, L., Takizawa, M., Xhafa, F., Enokido, T., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 1279–1290. [Google Scholar]
- Truong, D.T.; Cheng, G. Detecting domain-flux botnet based on DNS traffic features in managed network. Secur. Commun. Netw. 2016, 9, 2338–2347. [Google Scholar] [CrossRef] [Green Version]
- Natarajan, V.; Sheen, S.; Anitha, R. Multilevel analysis to detect covert social botnet in multimedia social networks. Comput. J. 2015, 58, 679–687. [Google Scholar] [CrossRef]
- Alhomoud, A.; Awan, I.; Pagna Disso, J.F.; Younas, M. A next-generation approach to combating botnets. Computer 2013, 46, 6459493. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Gharib, A.; Lashkari, A.H.; Ghorbani, A.A. BotViz: A memory forensic-based botnet detection and visualization approach. In Proceedings of the 2017 International Carnahan Conference on Security Technology (ICCST), Madrid, Spain, 23–26 October 2017; pp. 1–8. [Google Scholar] [CrossRef]
- Virustotal.com. 2020. Available online: Virustotal.com (accessed on 18 December 2020).
- Zago, M.; Gil Perez, M.; Martinez Perez, G. UMUDGA: A dataset for profiling algorithmically generated domain names in botnet detection. Data Brief 2020, 30, 105400. [Google Scholar] [CrossRef]
- k. Idriss, H. Mirai Botnet In Lebanon. In Proceedings of the 2020 8th International Symposium on Digital Forensics and Security (ISDFS), Beirut, Lebanon, 1–2 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Balasubramanian, Y.; Baggam, D.S.; Venkatraman, S.; Ramaswamy, V. Quantum IDS for mitigation of DDoS attacks by mirai botnets. Commun. Comput. Inf. Sci. 2018, 828, 488–501. [Google Scholar] [CrossRef]
- Tzagkarakis, C.; Petroulakis, N.; Ioannidis, S. Botnet Attack Detection at the IoT Edge Based on Sparse Representation. In Proceedings of the 2019 Global IoT Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Prokofiev, A.O.; Smirnova, Y.S.; Surov, V.A. A method to detect Internet of Things botnets. In Proceedings of the 2018 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering, Elconrus 2018, Moscow, Russia; St. Petersburg, Russia, 29 January–1 February 2018; pp. 105–108. [Google Scholar] [CrossRef]
- Giachoudis, N.; Damiris, G.P.; Theodoridis, G.; Spathoulas, G. Collaborative agent-based detection of DDoS IoT botnets. In Proceedings of the 15th Annual International Conference on Distributed Computing in Sensor Systems, DCOSS 2019, Santorini Island, Greece, 29–31 May 2019; p. 8804480. [Google Scholar] [CrossRef]
- Spathoulas, G.; Giachoudis, N.; Damiris, G.P.; Theodoridis, G. Collaborative blockchain-based detection of distributed denial of service attacks based on internet of things botnets. Future Internet 2019, 11, 226. [Google Scholar] [CrossRef] [Green Version]
- Cui, P.; Guin, U. Countering Botnet of Things using Blockchain-Based Authenticity Framework. In Proceedings of the 2019 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Miami, FL, USA, 15–17 July 2019; p. 8839425. [Google Scholar] [CrossRef]
- Zareh, A.; Shahriari, H.R. BotcoinTrap: Detection of Bitcoin Miner Botnet Using Host Based Approach. In Proceedings of the 2018 15th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology, ISCISC 2018, Tehran, Iran, 28–29 August 2018; p. 8546867. [Google Scholar] [CrossRef]
- Zhuang, D.; Chang, J.M. PeerHunter: Detecting peer-to-peer botnets through community behavior analysis. In Proceedings of the 2017 IEEE Conference on Dependable and Secure Computing, Taipei, Taiwan, 7–10 August 2017; p. 8073832. [Google Scholar] [CrossRef] [Green Version]
- Priyanka; Dave, M. PeerFox: Detecting parasite P2P botnets in their waiting stage. In Proceedings of the 2015 International Conference on Signal Processing, Computing and Control, ISPCC 2015, Solan, India, 24–26 September 2015; p. 7375054. [Google Scholar] [CrossRef]
- Obeidat, A.A.; Al-Kofahi, M.M.; Bawaneh, M.J.; Hanandeh, E.S. A novel botnet detection system for P2P networks. J. Comput. Sci. 2017, 13, 329–336. [Google Scholar] [CrossRef] [Green Version]
- Wang, P.; Wang, F.; Lin, F.; Cao, Z. Identifying Peer-to-Peer Botnets Through Periodicity Behavior Analysis. In Proceedings of the 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications and 12th IEEE International Conference on Big Data Science and Engineering, Trustcom/bigdatase 2018, New York, NY, USA, 1–3 August 2018; p. 8455919. [Google Scholar] [CrossRef]
- Barthakur, P.; Dahal, M.; Ghose, M.K. A framework for P2P botnet detection using SVM. In Proceedings of the 2012 International Conference on Cyber-enabled Distributed Computing and Knowledge Discovery, Cyberc 2012, Sanya, China, 10–12 October 2012; p. 6384967. [Google Scholar] [CrossRef]
- Chen, Z.; Yu, X.; Zhang, C.; Zhang, J.; Lin, C.; Song, B.; Gao, J.; Hu, X.; Yang, W.; Yan, E. Fast botnet detection from streaming logs using online lanczos method. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 1408–1417. [Google Scholar] [CrossRef] [Green Version]
- Ersson, J.; Moradian, E. Botnet Detection with Event-Driven Analysis. Procedia Comput. Sci. 2013, 22, 662–671. [Google Scholar] [CrossRef]
- Almutairi, S.; Mahfoudh, S.; Almutairi, S.; Alowibdi, J.S. Hybrid Botnet Detection Based on Host and Network Analysis. J. Comput. Netw. Commun. 2020, 2020, 9024726. [Google Scholar] [CrossRef]
- Lu, W.; Miller, M.; Xue, L. Detecting Command and Control Channel of Botnets in Cloud. In Intelligent, Secure, and Dependable Systems in Distributed and Cloud Environments; Traore, I., Woungang, I., Awad, A., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 55–62. [Google Scholar]
- Zeng, Y.; Yan, G.; Eidenbenz, S.; Shin, K.G. Measuring the effectiveness of infrastructure-level detection of large-scale botnets. In Proceedings of the 2011 IEEE Nineteenth IEEE International Workshop on Quality of Service, San Jose, CA, USA, 6–7 June 2011; p. 5931312. [Google Scholar] [CrossRef]
- François, J.; Wang, S.; Bronzi, W.; State, R.; Engel, T. BotCloud: Detecting botnets using MapReduce. In Proceedings of the 2011 IEEE International Workshop on Information Forensics and Security, Wifs 2011, Iguacu Falls, Brazil, 29 November–2 December 2011; p. 6123125. [Google Scholar] [CrossRef] [Green Version]
- Saraubon, K.; Limthanmaphon, B. Fast Effective Botnet Spam Detection. In Proceedings of the 2009 Fourth International Conference on Computer Sciences and Convergence Information Technology, Seoul, Korea, 24–26 November 2009; pp. 1066–1070. [Google Scholar] [CrossRef]
- Crespo, B.G.; Garwood, A. Fighting Botnets with Cyber-Security Analytics: Dealing with Heterogeneous Cyber-Security Information in New Generation SIEMs. In Proceedings of the 2014 Ninth International Conference on Availability, Reliability and Security, Fribourg, Switzerland, 8–12 September 2014; pp. 192–198. [Google Scholar] [CrossRef]
- Derhab, A.; Bouras, A.; Muhaya, F.B.; Khan, M.K.; Xiang, Y. Spam Trapping System: Novel security framework to fight against spam botnets. In Proceedings of the 2014 21st International Conference on Telecommunications (ICT), Lisbon, Portugal, 4–7 May 2014; pp. 467–471. [Google Scholar] [CrossRef]
- Tang, Y.; Cheng, G.; Yu, J.T.; Zhang, B. Catching modern botnets using active integrated evidential reasoning. J. Internet Serv. Appl. 2013, 4, 1–10. [Google Scholar] [CrossRef] [Green Version]
- Yusof, M.; Saudi, M.M.; Ridzuan, F. A New Android Botnet Classification for GPS Exploitation Based on Permission and API Calls. Lect. Notes Electr. Eng. 2018, 465, 27–37. [Google Scholar] [CrossRef]
- Mongkolluksamee, S.; Visoottiviseth, V.; Fukuda, K. Robust Peer to Peer Mobile Botnet Detection by Using Communication Patterns. In Proceedings of the AINTEC ’18, AINTEC Asian Internet Engineering Conference, Bangkok, Thailand, 12–14 November 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 38–45. [Google Scholar] [CrossRef]
- Karim, A.; Salleh, R.; Khan, K. SMARTbot: A Behavioral Analysis Framework Augmented with Machine Learning to Identify Mobile Botnet Applications. PLoS ONE 2016, 11, e0150077. [Google Scholar] [CrossRef] [PubMed]
- Tidke, S.K.; Karde, P.; Thakare, V. Identification of Botnet hidden behind smartphone applications. In Proceedings of the 2017 International Conference on Energy, Communication, Data Analytics and Soft Computing (ICECDS), Chennai, India, 1–2 August 2017; pp. 420–424. [Google Scholar] [CrossRef]
- Garip, M.T.; Reiher, P.; Gerla, M. RIoT: A Rapid Exploit Delivery Mechanism against IoT Devices Using Vehicular Botnets. In Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall), Honolulu, HI, USA, 22–25 September 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Baltazar, J.; Costoya, J.; Flores, R. Steep rise in Koobface variants is boosted by social networking. Comput. Fraud. Secur. 2009, 2009, 19–20. [Google Scholar] [CrossRef]
- Cybersecurity & Infrastructure Security Agency—“Alert (TA14-150A)—GameOver Zeus P2P Malware”. Available online: https://us-cert.cisa.gov/ncas/alerts/TA14-150A (accessed on 4 August 2016).
- Hatzivasilis, G.; Soultatos, O.; Chatziadam, P.; Fysarakis, K.; Askoxylakis, I.; Ioannidis, S.; Alaxandris, G.; Katos, V.; Spanoudakis, G. WARDOG: Awareness detection watchbog for Botnet infection on the host device. IEEE Trans. Sustain. Comput. 2019, 6, 4–18. [Google Scholar] [CrossRef]
- Ahmed, Z.; Danish, S.M.; Qureshi, H.K.; Lestas, M. Protecting IoTs from mirai botnet attacks using blockchains. In Proceedings of the 2019 IEEE 24th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Limassol, Cyprus, 11–13 September 2019; p. 8858484. [Google Scholar] [CrossRef]
- Yin, D.; Zhang, L.; Yang, K. A DDoS Attack Detection and Mitigation with Software-Defined Internet of Things Framework. IEEE Access 2018, 6, 24694–24705. [Google Scholar] [CrossRef]
- Sadeghian, A.; Zamani, M. Detecting and preventing DDoS attacks in botnets by the help of self triggered black holes. In Proceedings of the 2014 Asia-Pacific Conference on Computer Aided System Engineering (APCASE), Bali, Indonesia, 10–12 February 2014; pp. 38–42. [Google Scholar] [CrossRef]
- De Donno, M.; Donaire Felipe, J.M.; Dragoni, N. ANTIBIOTIC 2.0: A Fog-based Anti-Malware for Internet of Things. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy Workshops (EuroS PW), Stockholm, Sweden, 17–19 June 2019; pp. 11–20. [Google Scholar] [CrossRef]
- Wang, P.; Wu, L.; Cunningham, R.; Zou, C.C. Honeypot Detection in Advanced Botnet Attacks. Int. J. Inf. Comput. Secur. 2010, 4, 30–51. [Google Scholar] [CrossRef] [Green Version]
- Jerkins, J.A. Motivating a market or regulatory solution to IoT insecurity with the Mirai botnet code. In Proceedings of the 2017 IEEE 7th Annual Computing and Communication Workshop and Conference, CCWC 2017, Las Vegas, NV, USA, 9–11 January 2017; p. 7868464. [Google Scholar] [CrossRef]
- Oliveri, A.; Lauria, F. Sagishi: An undercover software agent for infiltrating IoT botnets. Netw. Secur. 2019, 2019, 9–14. [Google Scholar] [CrossRef]
- Tetarave, S.K.; Tripathy, S.; Kalaimannan, E.; John, C.; Srivastava, A. A Routing Table Poisoning Model for Peer-to-Peer (P2P) Botnets. IEEE Access 2019, 7, 67983–67995. [Google Scholar] [CrossRef]
- Davis, C.R.; Fernandez, J.M.; Neville, S. Optimising sybil attacks against P2P-based botnets. In Proceedings of the 2009 4th International Conference on Malicious and Unwanted Software, Malware 2009, Montreal, QC, Canada, 13–14 October 2009; p. 5403016. [Google Scholar] [CrossRef]
- Kelly, C.; Pitropakis, N.; McKeown, S.; Lambrinoudakis, C. Testing and Hardening IoT Devices against the Mirai Botnet. In Proceedings of the 2020 International Conference on Cyber Security and Protection of Digital Services (Cyber Security), Dublin, Ireland, 15–19 June 2020; p. 9138887. [Google Scholar] [CrossRef]
- Hallman, R.; Bryan, J.; Palavicini, G.; Divita, J.; Romero-Mariona, J. IoDDoS—The internet of distributed denial of sevice attacks A case study of the mirai malware and IoT-Based botnets. In Proceedings of the IOTBDS 2017—2nd International Conference on Internet of Things, Big Data and Security, Porto, Portugal, 24–26 April 2017; pp. 47–58. [Google Scholar] [CrossRef]
- Huan, L.; Yu, Y.; Lv, L.; Li, S.; Xia, C. A botnet-oriented collaborative defense scheme description language. In Proceedings of the 9th International Conference on Computational Intelligence and Security, CIS 2013, Emeishan, China, 14–15 December 2013; p. 6746511. [Google Scholar] [CrossRef]
- Bradbury, D. Fighting botnets with sinkholes. Netw. Secur. 2012, 2012, 12–15. [Google Scholar] [CrossRef]
- Kanich, C.; Kreibich, C.; Levchenko, K.; Enright, B.; Voelker, G.M.; Paxson, V.; Savage, S. Spamalytics: An empirical analysis of spam marketing conversion. Commun. ACM 2009, 52, 99–107. [Google Scholar] [CrossRef]
- Watkins, L.; Kawka, C.; Corbett, C.; Robinson, W.H. Fighting banking botnets by exploiting inherent command and control vulnerabilities. In Proceedings of the 9th IEEE International Conference on Malicious and Unwanted Software, Malcon 2014, Fajardo, PR, USA, 28–30 October 2014; p. 6999411. [Google Scholar] [CrossRef]
- Stone-Gross, B.; Cova, M.; Gilbert, B.; Kemmerer, R.; Kruegel, C.; Vigna, G. Analysis of a botnet takeover. IEEE Secur. Priv. 2011, 9, 5560627. [Google Scholar] [CrossRef]
- The Spamhaus Project. Available online: https://www.spamhaus.org/bcl/ (accessed on 23 June 2020).
- IBM X-Force exchange. Available online: https://exchange.xforce.ibmcloud.com/collection/Botnet-Command-and-Control-Servers-7ac6c4578facafa0de50b72e7bf8f8c4 (accessed on 23 June 2020).
- Li, J.; Xue, Z. Distributed Threat Intelligence Sharing System: A New Sight of P2P Botnet Detection. In Proceedings of the 2nd International Conference on Computer Applications and Information Security, ICCAIS 2019, Riyadh, Saudi Arabia, 1–3 May 2019; p. 8769511. [Google Scholar] [CrossRef]
- Dog, S.E.; Tweed, A.; Rouse, L.; Chu, B.; Qi, D.; Hu, Y.; Yang, J.; Al-Shaer, E. Strategic cyber threat intelligence sharing: A case study of IDS logs. In Proceedings of the 2016 25th International Conference on Computer Communications and Networks, ICCCN 2016, Waikoloa, HI, USA, 1–4 August 2016; p. 7568578. [Google Scholar] [CrossRef]
- Eslahi, M.; Rostami, M.R.; Hashim, H.; Tahir, N.M.; Naseri, M.V. A data collection approach for Mobile Botnet analysis and detection. In Proceedings of the 2014 IEEE Symposium on Wireless Technology and Applications (ISWTA), Kota Kinabalu, Malaysia, 28 September–1 October 2014; pp. 199–204. [Google Scholar] [CrossRef]
- Garcia, S.; Erquiaga, M.J.; Shirokova, A.; Garcia Garino, C. Geost Botnet. Operational Security Failures of a New Android Banking Threat. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy Workshops (EuroS PW), Stockholm, Sweden, 17–19 June 2019; pp. 406–409. [Google Scholar] [CrossRef]
- Vidal-González, S.; García-Rodríguez, I.; Aláiz-Moretón, H.; Benavides-Cuéllar, C.; Benítez-Andrades, J.A.; García-Ordás, M.T.; Novais, P. Analyzing IoT-Based Botnet Malware Activity with Distributed Low Interaction Honeypots. In Trends and Innovations in Information Systems and Technologies; Rocha, Á., Adeli, H., Reis, L.P., Costanzo, S., Orovic, I., Moreira, F., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 329–338. [Google Scholar]
- Safaei Pour, M.; Mangino, A.; Friday, K.; Rathbun, M.; Bou-Harb, E.; Iqbal, F.; Samtani, S.; Crichigno, J.; Ghani, N. On data-driven curation, learning, and analysis for inferring evolving internet-of-Things (IoT) botnets in the wild. Comput. Secur. 2020, 91, 101707. [Google Scholar] [CrossRef]
- Borgaonkar, R. An analysis of the asprox botnet. In Proceedings of the 4th International Conference on Emerging Security Information, Systems and Technologies, Securware 2010, Venice, Italy, 18–25 July 2010; p. 5633693. [Google Scholar] [CrossRef] [Green Version]
- Li, X.; Duan, H.; Liu, W.; Wu, J. The growing model of Botnets. In Proceedings of the 2010 International Conference on Green Circuits and Systems, Shanghai, China, 21–23 June 2010; p. 5543027. [Google Scholar] [CrossRef]
- Patsakis, C.; Casino, F.; Katos, V. Encrypted and covert DNS queries for botnets: Challenges and countermeasures. Comput. Secur. 2020, 88, 101614. [Google Scholar] [CrossRef]
- Stone-Gross, B.; Cova, M.; Cavallaro, L.; Gilbert, B.; Szydlowski, M.; Kemmerer, R.; Kruegel, C.; Vigna, G. Your Botnet is My Botnet: Analysis of a Botnet Takeover. In Proceedings of the 16th ACM Conference on Computer and Communications Security, CCS 09, Chicago, IL, USA, 9–13 November 2009; Association for Computing Machinery: New York, NY, USA, 2009; pp. 635–647. [Google Scholar] [CrossRef]
- Barford, P.; Yegneswaran, V. An Inside Look at Botnets. In Malware Detection; Christodorescu, M., Jha, S., Maughan, D., Song, D., Wang, C., Eds.; Springer: Boston, MA, USA, 2007; pp. 171–191. [Google Scholar]
- Shahrestani, A.; Feily, M.; Masood, M.; Muniandy, B. Visualization of invariant bot behavior for effective botnet traffic detection. In Proceedings of the 2012 International Symposium on Telecommunication Technologies, ISTT 2012, Kuala Lumpur, Malaysia, 26–28 November 2012; p. 6481606. [Google Scholar] [CrossRef]
- Rowe, B.; Wood, D.; Reeves, D. How the public views strategies designed to reduce the threat of botnets. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2010; Volume 6101, pp. 337–351. [Google Scholar] [CrossRef]
- Khattak, S.; Ramay, N.R.; Khan, K.R.; Syed, A.A.; Khayam, S.A. A Taxonomy of Botnet Behavior, Detection, and Defense. IEEE Commun. Surv. Tutor. 2014, 16, 898–924. [Google Scholar] [CrossRef]
- Peterson, A. Yes, Terrorists Could Have Hacked Dick Cheneys Heart. Available online: https://www.washingtonpost.com/news/the-switch/wp/2013/10/21/yes-terrorists-could-have-hacked-dick-cheneys-heart/ (accessed on 14 December 2020).



| Paper | Main Contribution and Reference Metrics | This Paper |
|---|---|---|
| [11] | Offers only generalised information about botnets and botnet detection/mitigation strategies. Thirty-nine references from 2007 to 2012. | Describes specific botnet detection mechanisms, advantages, disadvantages, for instance, the Shieldnet framework to detect botnets in vehicular networks [12]. |
| [13,14] | Focuses on describing different kinds of botnet attacks ([13]) and on the threats represented by botnets ([14]), without going into specific mitigation strategies. ([13]—27 references from 2006 to 2016) ([14]—60 references from 2003 to 2018) | Describes both botnet evolution and threats, and offers insight into different detection and mitigation mechanisms. |
| [1,15,16,17] | Offer great insight on botnet research, types of botnets as well as detection and mitigation mechanisms. However, both papers do not include more recent studies and publications (all are pre-2014). ([1]—205 references), ([7]—36), ([15]—49), ([16]—217), ([17]—28). | Covers the same points as aforementioned papers, but also includes more recent research from 2014–2021 such as [18,19] and more. |
| [20] | Presents potential challenges of mobile botnets, but does not include any more recent research (paper from 2012). 40 references from 2002–2012. | Presents more recent papers on mobile botnets such as [18,19] and more. |
| [7,21]. | Covers only generalised botnet types and few specific recent types, such as cloud botnets and social botnets ([7]) or covers P2P botnets only ([21]). ([7]—25 references from 2015–2015) ([7]—36, 2005–2013) | Covers more kinds of botnet types such as IoT botnets, mobile botnets, VANET-based botnets and their related challenges and trends. |
| [10] | Describes botnet evolution, attack threats and actors, but not go into detection and mitigation techniques against botnets. Thirty-one references from 1998–2009. | Covers the same points and also describes different detection categories and specific mitigation mechanisms. |
| [22,23,24,25,26,27] | Limited scope of botnet detection techniques ([22]—34 detection/mitigation references from 1997–2008), ([23]—38, 2004–2011), ([24]—9, 2008–2019), ([25]—7, 2019–2017), ([26]—11, 2008–2015), ([27]—20, 2004–2013). | Includes a larger breadth of more recent detection papers, such as [28,29] and more than 100 more papers compared to [22]. |
| [30] | Focuses specifically on DDoS botnet attacks without covering detection strategies. 145 references from 1993–2015. | Describes potential attack threats of botnets while also covering detection mechanisms. |
| [31,32] | Mentions only IoT-based botnets. ([31]—36 references from 2010 to 2019), ([32]—122, 2004–2021). | Covers IoT-based botnets and also includes other types of botnets, such as mobile botnets, social botnets and VANET-based botnets. |
| [33,34] | Discusses various botnet detection categories in general, but does not highlight the specifics of each technique. ([33]—34 references from 2005 to 2010). | Highlights and describes each detection technique individually including the strengths and novelty of each botnet detection approach. |
| [35,36] | Only compares machine-learning based botnet detection techniques. ([35]—38 references from 1995–2020), ([36]—25, 2001–2017) | Compares machine-learning based detection techniques as well as many more types (IoT, social botnets and more). |
| Motivation | Type of Attack | Target | Vector of Attack | Papers |
|---|---|---|---|---|
| Disruption Denial of service. | DDoS. | Hosting Service Provider. | IoT devices. | [41] |
| Political affiliation Censorship. | DDoS. | Military complex computers. | C&C-based botnet. | [42] |
| Disruption and Destabilisation of national power grids. | DDoS. | Metering infrastructure. | Internet-connected computers and IoT devices. | [43] |
| Sensitive data Password cracking. | Cracking/Brute-forcing. | Common people. | Various. | [44,45,46] |
| Cyber espionage. | (Spear-)phishing and malware | Multiple victims listed. | Various. | [31,47] |
| Security patching Vulnerability scanning (benevolent). | Security patching | Unsecure IoT devices. | Other IoT devices. | [48] |
| Botnet spoofing (fighting other botnets). | Mitigation. | Malicious botnets. | Existing botnets. | [49] |
| Miscellaneous pieces of work detailing motivations. | Various types discussed. | Various targets discussed. | Multiple types discussed. | [10,50] |
| Associated Area of Interest | Vector of Attack | Year | Papers |
|---|---|---|---|
| First recorded appearance. | IRC forums. | Late 1980s | [50] |
| Honeypots is an often employed tool to detect botnets. New botnets have shown a capacity to identify and avoid detection from such measure. | N/A. | 2004 | [55,56] |
| An analysis and discussion of botnets based off of the Darknet. | Darknet. | 2006 | [57] |
| ZeuS botnet and its role as one of the most influential botnets in the world. | Various systems. | 2007 | [9] |
| Botnets have begun showcasing active methods and tools to circumvent detection. | Various means discussed. | 2007 | [7,58,59,60] |
| HTTP-based botnets are explored and discussed along with a multitude of different other botnets. | Browsers and extensions. | 2007 | [61] |
| Description of various botnet characteristics, the latest research and insight into botnets. | N/A. | 2009 | [62,63] |
| New type of botnet capable of impersonating human reaction patterns, a factor otherwise used to identify botnets typically. | Various systems. | 2009 | [64] |
| Smartphones have grown powerful enough to be a potential vector of attack, for a botnet. This is explored in detail. | Smartphones. | 2010 | [65,66,67,68,69,70] |
| Botnets as a service is a newly founded concept, and is explored in details. | Typical SaaS centers. | 2011 | [71] |
| New type of botnet structure, based around a P2P-oriented basis is investigated, discussed and analysed for potential vectors of attack. | None formally disclosed, architecture discussed instead. | 2011 | [72,73,74,75,76,77] |
| Other botnets use obfuscation tactics to hide the true identity/position of the C&C’s location, showcasing a trend of botnets growing more versatile and elusive to researchers. | N/A. | 2013 | [78] |
| More kinds of botnet susceptible hosts become more common, leading to new potential vectors of attack. | Browsers, extensions, smartphones and online clipboards. | 2013 | [79,80] |
| Vehicles can also be a potential vector for botnets, such as GHOST. GHOST seeks out VANETs in cars to utilise the VANET control channel for communication. | Automobiles and other vehicles. | 2016 | [81] |
| IoT devices have become equipped with enough processing power to pose a sizeable threat. The generally poor safety implementations and the scale of IoT networks, makes them a good candidate for attack vectors. | IoT devices. | 2016 | [82,83,84] |
| Proposals for self-evolving botnets. | Unknown vulnerabilities in hosts. | 2016 | [85] |
| Cryptocurrencies have lead to explorations into new areas of potential botnets. Discussion and debate on the architecture. | Blockchain structures. | 2019 | [86] |
| Technique | Advantage(s) | Disadvantage(s) | Detection Rate | Papers |
|---|---|---|---|---|
| Back Propagation (BP). | Can detect botnets with no false positives as well as low expected error rate in higher error environments. | Only tested on a certain types of botnet traffic and characteristics of other botnets. | 99% detection rate, 95.7% accuracy and FP rates of 0.00952 or lower. | [92] |
| PSI-Graph | Much faster than FCGs, better FNR, FPR and accuracy. | N/A. | Accuracy of 98.7%, FNR 1.83% and FPR 0.78%. | [93] |
| Convolutional Neural Network (CNN) | Can automatically extract features of botnets and has higher accuracy than traditional NN. | Reference [94]: Training process requires GPU power. Reference [95] does not yet support transfer learning. | Best accuracy of ResNet is 99.32%. Reference [95] 99.98% accuracy for DenseNet and 83.15% for SVM. Reference [96] achieves up to 98.6% botnet detection accuracy on the self-tests and about 90% on the cross-evaluation test. | [94,95,96,97] |
| Artificial Neural Network (ANN) & MLP-ANN. | Reference [98] has low computational overhead. Reference [99] uses supervised learning approach to obtain high TPR and can further be used in Transfer Learning projects. | Reference [99] does not have hybrid models. | Reference [98] managed to get minimum of 87.56% TPR during testing. Reference [99] got 100% accuracy and TPR. | [98,99] |
| ML & DL. | A combination of multiple ML and DL models including comparisons. | N/A. | N/A. | [97] |
| NN & AIS. | Reference [29] can provide endpoint protection. Reference [100] does not need prior knowledge of botnets. | Reference [29] requires command and control server. | N/A. | [29,100] |
| Machine Learning, Deep Learning, t-distributed stochastic neighbor embedding & Deep Neural Network. | Considers a broad amount of ML and DL techniques. | N/A. | DNN takes a long time to train and also around 1.3 s to execute detection logic where other methods found in this paper is faster or requires less training time. | [101,102,103] |
| Nonnegative Tucker decomposition. | Memory-efficient. | Normally requires too high a computational cost to run in real time. | N/A. | [104] |
| NN with blockchains. | Lightweight: small memory and low-power processors needed for devices. | N/A. | N/A. | [29] |
| Technique | Advantage(s) | Disadvantage(s) | Detection Rate | Papers |
|---|---|---|---|---|
| Network flow analysis | Real-time detection. High detection rate (up to 98%) of known signatures. Can be implemented in current SDN solutions. Supports a wide variety of detection approaches. | Requires training data for unknown attacks. Too many features in selection results in unnecessary overhead. | Varies between 85.34%. Reference [109] to >99% [26]. | [26,28,97,109,110,111,112,113,114,115,116,117,118,119,120,121,122,123,124,125,126,127,128,129] |
| Honeypots | Ability to train model on unknown variants. | Training needs to be supplemented by simulated network traffic. | 99%. | [130,131] |
| DNS-based profiling of Mirai botnets | Uses live datasets based on honeypot infected botnets, low computational time (<0.2 s). | Limited to mirai(-like) botnet variants. | >99%. | [132] |
| Cloud-based detection offload | Linear scaling with number of computational hosts. | Real-time detection not possible. | N/A. | [133] |
| Minimization of ML feature selection | Lower computational cost while keeping high accuracy rate. | Limited to IoT-based botnets ([134]), does not improve weaknesses to unknown signatures. | 98.97% ([134]) and 75–99% ([135]). | [134,135] |
| VM Hypervisor detection agent | Allows OS-level passive detection and monitoring. | Only applicable for VM-based hosts. | N/A. | [5] |
| Self-adaptive system with fuzzy c-means clustering | Can choose security scenarios and adapt mitigation procedures depending on the attack. High resilience. | Dependent on the specific system network used during testing. | High percentage of known and unknown. Multi-vector cyberattacks: 70%. | [136] |
| Network botnet fingerprinting and signature | Large data throughput. High accuracy. Reference [137]: better real-time performance compared to CPU-based approaches (800–1300% speedup) | Specific parameters in the used dataset, which need more features. Reference [137]: requires dedicated GPU hardware. | Very few false positives. Accuracy close to 100%. | [137,138] |
| Network traffic data mining | Allows for detection of botnets inside complex traffic before the attack. Does not require network changes. | Method needs to be deployed by ISPs. Difficulties when using the NAT technology. | Detection: 98% NaiveBayes: 89% BayesNet: 87%. | [139] |
| Multi-phase traffic ranking mechanism | Reduces the false classification rate of normal IP traffic. | Needs further work to detect different kind of HTTP botnets. The experiment data is limited. | N/A. | [140] |
| Multi clusters for classification | Achieve high accuracy and reliability. Outperforms individual clustering algorithms in training time. | Increased algorithm runtime complexity. | N/A. | [141,142] |
| ML on DNS query data | Better than IDS based detection on newer botnets variants. | Takes time to train. | Most ML algorithms score over 85% accuracy on DGA botnets, among which the random forest algorithm gives the best results with an overall classification accuracy of 90.80%. | [143] |
| Technique | Advantage(s) | Disadvantage(s) | Detection Rate | Papers |
|---|---|---|---|---|
| DNS traffic monitoring | Can detect known and unknown botnets by monitoring DNS traffic anomalies. Can detect C&C server migration. | The huge size of traffic occurring in network environments is computationally intensive, and due to this, most DNS traffic monitoring methods are also not real-time. | Positive rate 90% and negative positive rate 5%. Reference [153] managed accuracy of 95% with 0.1% false positives. Reference [154] archived 98.52% True positive as minimum and 0.39% False positive as highest. | [22,23,25,153,154,155,156,157,158] |
| DNS traffic monitoring assisted by mining | Can detect known and unknown bots. Can successfully locate C&C traffic. Most methods have low false positive rates and can detect encrypted communication. | Not real-time. | Random forest can archive up to 99% accuracy. | [22,23,25,132] |
| Network anomalies | Can detect known and unknown bots. | Not useful for detecting C&C traffic. Not real-time viable. | Positive rate of close to 95% and False positive rate lower than 3.5%. | [22,23,25,133,159] |
| Signature-based detection | Can detect most known simple botnets. | Cannot detect unknown or more advanced known botnets. | N/A. | [22,23,25,159] |
| Feature-based detection (CAFE/CSTA) | Can reduce the number of non-active C&C suspected Domain Names by 79.96% with false positive rate of 0.69%. | Can be affected by malformed DNS answers or DNS cache poisoning attacks. | N/A. | [160] |
| Support vector machine SVM | Can detect existence of botnets in small to medium sized networks. | Anti-malware software can increase the false positive rate. | Detection rate of 0.935 and false positive rate of 0.02. | [161] |
| Technique | Advantage(s) | Disadvantage(s) | Detection Rate | Papers |
|---|---|---|---|---|
| Quantum computing to combat Mirai | Fast results. High accuracy. | Only targets botnet with known signatures. | N/A. | [172] |
| Sparse-representation framework on IoT | Faster than compared approaches. | Tested on limited IoT botnet dataset. | 90%. | [173] |
| Logistic regression of traffic | High accuracy. High precision. | Can only detect during propagation phase. | >99%. | [174] |
| Collaborative multi-agent | Can detect large scale DDoS attacks. Lightweight: can be installed on hardware with limited resources. | Needs a minimum level of collaboration across organisations. Training environment does not reflect real-world environments: A percentage of agents may not acting as excepted. | Depends on framework implementation. | [175,176,177] |
| Bitcoin Miners detection | Experiments are showing excellent accuracy. | Only applicable on specific botnet types. | Depending on the variety of techniques that are utilised. | [178] |
| Classification from traffic frequency and behaviour. | No statistical traffic patterns need to be known in advance. Does not rely on payload data. Does not require monitoring of individual host. Effective (very high detection rate). Scalable low false positive rate. | Requires installation at all network boundaries. Unable to detect botnets with low amount of requests. | Up to 100%. | [76,179,180,181,182,183,184,185,186,187] |
| Graph-based approach | Computationally efficient. | Needs a certain amount of training data. Accuracy depends on datasets inspired of the evolving Internet state. | N/A. | [188] |
| PageRank algorithm using clustered cloud computing | Efficient performance (clustering). Scalable and Effective. Easily usable at low costs. | High computational needs. | 99%. | [189] |
| SMTP analysis | Can catch both text and image-based botnet spam mails. | Limited to mail-based botnets. | Detects 96.23% of botnets spam mails with no false positive. | [190,191] |
| Botnet application sandboxing | Computationally cheaper compared to contemporary intrusion detection systems. | Legitimate emails can be flagged wrongly as spam. | Not tested | [192] |
| Evidential reasoning | Can improve botnet detection rates. | Lacks an uncertainty evaluation model. | Up to 90%. | [193] |
| Technique | Advantage(s) | Disadvantage(s) | Detection Rate | Papers |
|---|---|---|---|---|
| Risk factor based on multi-category features | High accuracy in botnet apps.Generates a pattern for Android botnet detection. | Only for static analysis.No response mechanism. | Reference [194]: 93.1%. | [18,194] |
| Dynamic real-time analysis | N/A. | Limited analysis for risk factor. | N/A. | [19] |
| Machine learning | General high detection performance. | Bad detection performance when the bot coexists with other applications that communicate with many hosts. | Achieves 0.93 of the F-measure score by using graphlets of TCP and UDP with 10% of total traffic in 3-minute duration [195]. 99.49% accuracy is achieved [196]. | [195,196] |
| Application monitoring | Mitigation: user warnings if something is suspicious. | SMS and social network applications are not monitored. | N/A. | [197] |
| Mitigation Mechanism | Advantages | Disadvantages | Papers |
|---|---|---|---|
| Best practices for end-users and organisations | Increases overall organisational security, considered best-practice, many well-known standards (i.e., ISO 27001). | Does not specifically target botnets, high user inconvenience cost. | [53,200] |
| Network-level blocking and packet analysis | Very high protection rate, many solutions and detection frameworks. | Very botnet-specific, can introduce additional latency at network edge. | [5,84,98,136,176,201,202,203,204,205] |
| Honeypots and botnet isolation | No effect on internal networks. Low cost. | Lower protection rate compared to network-level blocking, requires additional logically separated network. | [13,22,33,206,207,208] |
| Attacking P2P botnets | Helps mitigate botnet threat for others. Can target specific botnets. Hinders P2P advantages compared to centralised C&C models. | Only targets specific botnets (P2P-based). Low efficiency for organisations. | [209,210] |
| IoT-specific mitigation strategies | Low or offloaded compute resource cost. Some solutions provide general integrity for IoT-based networks. | Specific for IoT-based threats. Still few and untested options compared to network-level blocking. | [2,106,175,211,212] |
| Community-driven approaches | Potentially quicker adaption to newer botnets. Free and Open Source for organisations to use. | Dependent on community development. No de-facto standard decided yet. | [119,213] |
| Botnet mitigation with ethical issues (spreading anti-botnets, attacking suspected hosts) | Mitigates botnets for others. Slows botnet propagation. | Ethically questionable or illegal. Very specific per-botnet. | [49,82,214,215,216,217] |
| Trend | Topics Within Trend | Relative Interest | Papers |
|---|---|---|---|
| Pervasive Computing | Spread of botnets in home appliances | 2 out 18 papers listed. | [31,201] |
| Spread of botnets in mobile phones | 2 out 18 papers listed. | [222,223] | |
| Spread of botnets in (non)-autonomous vehicles. | 2 out 18 papers listed. | [81,198] | |
| Remotely disrupting the controls of an autonomous vehicle. | 1 out of 18 papers listed. | [81] | |
| Smartphones exploited via insufficient app certification process. | 2 out of 18 papers listed. | [37,197] | |
| Lack of restrictions hinders the process of avoiding botnet apps on mobile devices. | 2 out of 18 papers listed. | [207,211] | |
| Various proposals for IoT malware protection, both generalised and specialised. | 4 out of 18 papers listed. | [2,205,207,211] | |
| Usage of honeypots helps make more real-life like data for mitigation strategies. | 1 out of 18 papers listed. | [224] | |
| No standardised way to protect pervasive computing device hurts development of mitigation strategies. | 1 out of 18 papers listed. | [225] | |
| Best-practices in IT security yearns for standardising security in IoT and mobile devices. | 1 out of 18 papers listed. | [2] | |
| Increasing complexityof botnets | Most firewalls and intrusion detection systems are not able to filter IPv6 traffic. | 2 out of 3 papers listed | [226,227] |
| Modern botnets can circumvent traditional detection methods using encrypted channels for traditionally unencrypted traffic. | 1 out of 3 papers listed. | [228] | |
| Social Botnets | Social botnets can be used for multiple purposes, including spam, C&C and falsifying/impersonating user behaviour. | 2 out of 4 papers listed. | [87,199] |
| It is growing increasingly harder for users to discern between true and false information, benefiting botnets. | 1 out of 4 papers listed. | [166] | |
| New and more advanced counter measures are necessary to combat this new development of social botnets. | 1 out of 4 papers listed. | [1] | |
| Machine learning andneural networks forbotnet detection | New research on machine learning based detection schemes shows high rates of true positive detection of botnet behaviour. | 8 out of 9 papers listed. | [24,92,99,109,124,125,127,136] |
| Discussion on the ability to train for zero-day vulnerabilities with custom created datasets. | 1 out of 9 papers listed. | [170] | |
| Proactive botnetmitigation | Proactive botnet mitigation techniques show promising results. | 3 out of 6 papers listed. | [130,207,229] |
| Proactive mitigation strategies and tools need to be developed for both the local and international stage. | 2 out of 6 papers listed. | [230,231] | |
| Users willing to pay for botnet prevention, but lack awareness. | 1 out of 6 papers listed. | [232] | |
| Cloud-based botnets | Cloud services can be used for C&C communications between bots and bot masters, masquerading as benign user traffic. | 1 out of 3 papers listed. | [187] |
| Cloud services offer options for researchers to create botnets without hassle. | 2 out of 3 papers listed. | [87,233] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Thanh Vu, S.N.; Stege, M.; El-Habr, P.I.; Bang, J.; Dragoni, N. A Survey on Botnets: Incentives, Evolution, Detection and Current Trends. Future Internet 2021, 13, 198. https://doi.org/10.3390/fi13080198
Thanh Vu SN, Stege M, El-Habr PI, Bang J, Dragoni N. A Survey on Botnets: Incentives, Evolution, Detection and Current Trends. Future Internet. 2021; 13(8):198. https://doi.org/10.3390/fi13080198
Chicago/Turabian StyleThanh Vu, Simon Nam, Mads Stege, Peter Issam El-Habr, Jesper Bang, and Nicola Dragoni. 2021. "A Survey on Botnets: Incentives, Evolution, Detection and Current Trends" Future Internet 13, no. 8: 198. https://doi.org/10.3390/fi13080198
APA StyleThanh Vu, S. N., Stege, M., El-Habr, P. I., Bang, J., & Dragoni, N. (2021). A Survey on Botnets: Incentives, Evolution, Detection and Current Trends. Future Internet, 13(8), 198. https://doi.org/10.3390/fi13080198









