HealthBlock: A Framework for a Collaborative Sharing of Electronic Health Records Based on Blockchain
Abstract
1. Introduction
- The EHRs are appropriately protected (Integrity + Confidentiality) and available anytime from any country.
- The patients have full control of their EHRs, and they can temporarily delegate access to any person or organization at any time.
- The patients can obtain anonymous healthcare services, when needed, to better protect their privacy.
- The patients’ attributes can be proved remotely, making telemedicine more efficient.
- The solution takes into consideration that in an emergency, the patients may not have their full capacity to grant access to their EHRs.
2. Related Work
- Patients have full control over their EHRs: Patients keep their EHRs in their wallets or saved in some store in an encrypted form, and they control who can access which selected attributes and when.
- Anonymous Healthcare Service: It will be nice if the solution gives patients the possibility to obtain an anonymous service when they want. Patients hold a set of attributes related to their identity, including EHRs, and show only what it is required. For instance, to obtain a COVID-19 vaccine, patients may need only to show that they are older than a certain age; they are citizens of the city where they ask for the vaccine and have not received the vaccine yet.
- Availability: It is very important that the EHRs are available anytime from any location, even if some equipment is down or attacked.
- Integrity: We should ensure that EHRs have not been accidentally or maliciously changed. Without integrity, EHRs are useless.
- Confidentiality: EHRs contain very sensitive information, and if disclosed, some serious damages can take place for their owners, including loss of jobs and increasing insurance fees.
- Access Control Delegation: Any solution that aims to manage EHRs should give the patient an easy way to delegate some access to any attributes related to their EHRs.
- Zero-Knowledge Proof (ZKP): It could be useful for patients to prove some properties related to their attributes without revealing their values. For example, they can prove that they are more than 18 years old without revealing their exact age. Commonly, some blockchain used ZKP protocols to provide this kind of property.
- Emergency Access to EHRs: In the case of an emergency when the patient is not in his full capacity to provide, by himself, his EHRs, a secure alternative solution should be provided.
- Scalability: When blockchain is used, we should carefully evaluate the volume of data added every day and be sure that the solution stays scalable, even when billions of clients are involved.
- Interoperability: To maximize its interoperability, any solution should use standards and, when needed, blockchain should be public and available worldwide.
- Remote Health Service: EHRs management solutions should provide the possibility of remote consultations, a growing need, particularly in the COVID-19 context. This could be possible, particularly when patients can remotely prove their attributes.
3. Preliminaries
3.1. Blockchain Technology
3.1.1. Key Characteristics of Blockchain
- Ledger: Unlike traditional databases, transactions in a blockchain could not be modified or deleted.
- Secure: Blockchain intrinsically provides integrity, traceability, and availability.
- Absence of trust: A blockchain can fulfill its security properties, even if its nodes are operated by players that do not trust each other and have antagonist goals.
3.1.2. Blockchain Types
3.2. Smart Contracts
3.3. Hyperledger Indy
3.4. Hyperledger Fabric
3.5. InterPlanetary File System (IPFS)
4. Proposed Framework
4.1. Preliminaries
4.1.1. Roles
- Patients: Patients play a crucial role, and the whole system aims to appropriately protect their EHRs and make them available to authorized participants when needed. Each document (a part of an EHRs, insurance, identity, etc.) contains a set of attributes (name, address, blood type, etc.) and a unique DID (decentralized identifier). Each DID is also associated with a public key and stored in the Hyperledger Indy. A patient proves that he is the owner of a document by showing he is the owner of the private key associated with the public correlated to the document referred by DID. The patients have full control of their EHRs. The system allows them to create and modify the access control policies related to their EHRs. This policy could be stored in Hyperledger Fabric or Ethereum. EHRs are varied and produced by different health service providers. To simplify the presentation, we assume that Bob is our patient.
- Healthcare providers: They are the producers and the consumers of healthcare attributes related to patients. They include individuals (doctors, nurses, etc.) and institutions (hospitals, labs, research centers, etc.). Once a healthcare attribute is produced or updated, any future access, inside or outside the same institution, should be consistent with the patient access control policy. To simplify the framework’s presentation, we assume that the provider is a laboratory L and the doctor Alice is the consumer.
- Healthcare card provider or insurance issuers: Using their healthcare cards or insurance, patients can receive services from different healthcare providers without directly paying them when they are appropriately covered.
4.1.2. Notations
- (Hashed message): A message m hashed by a hash function H, such as SHA-256, SHA3, RIPMD, Merkle-tree, etc.
- (Symmetric-key encryption): A message m encrypted by the key k using a symmetric cryptographic system, such as AES, 3-DES, etc.
- (Message encrypted with a public key): A message m encrypted with the public key using an asymmetric cryptographic system, such as RSA, El-Gamal, etc.
- (A signed message): A message m signed with the private key using an asymmetric cryptographic system, such as RSA, DSA, El-Gamal, etc.
4.1.3. Hyperledger Indy
- The agent B sends the credential containing the DID to A.
- A reads from Hyperledger Indy, the public key associated with the DID .
- A asks B to prove that he owns the private key associated with using a challenge–response protocol such as the example of Table 4.At the first step, A sends to B a fresh random number (called a nonce and used as a challenge). At the second step, B returns the nonce signed using the appropriate private key .To verify if the challenge was answered correctly, A checks if the message was signed using the private key associated with .
4.2. Ehrs Management Based on Indy
- After visiting any EHRs attribute provider, such as a laboratory, the patient can ask any time, even remotely, for his attributes. He sends a request containing a DID and a public key kb. The laboratory verifies the identity of the patient and asks him to prove that he is the owner of the public key Kb using the challenge–response protocol shown in Table 4.
- Once the patient’s identity and ownership of the public key Kb have been proven, the laboratory creates a certificate attesting that DID belongs to the owner of Kb and saves it in Hyperledger Indy as shown in Table 5.
- The laboratory creates a signed document containing the DID, the requested attributes, their values and sends it to the patient.
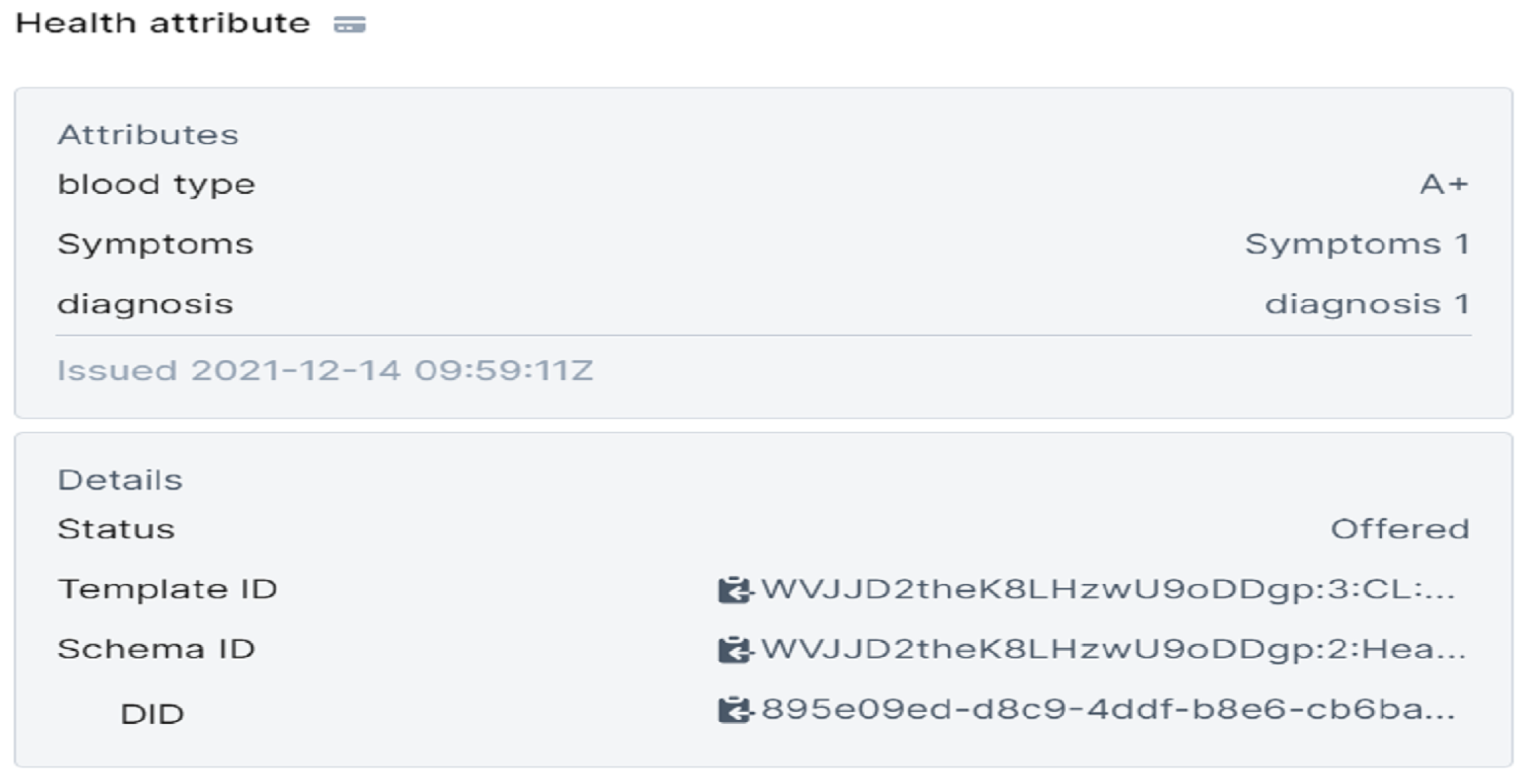
- The patient saves these attributes in his wallet as shown in Table 5 and can provide them for any future need. For example, suppose that a doctor requests these attributes, then the patient uses his wallet and provides them.
- The doctor Alice gets the public key Kb associated with DID from Indy.
- Alice asks the patient Bob to prove that he is the owner of the Kb by using a challenge–response protocol shown in Table 4.
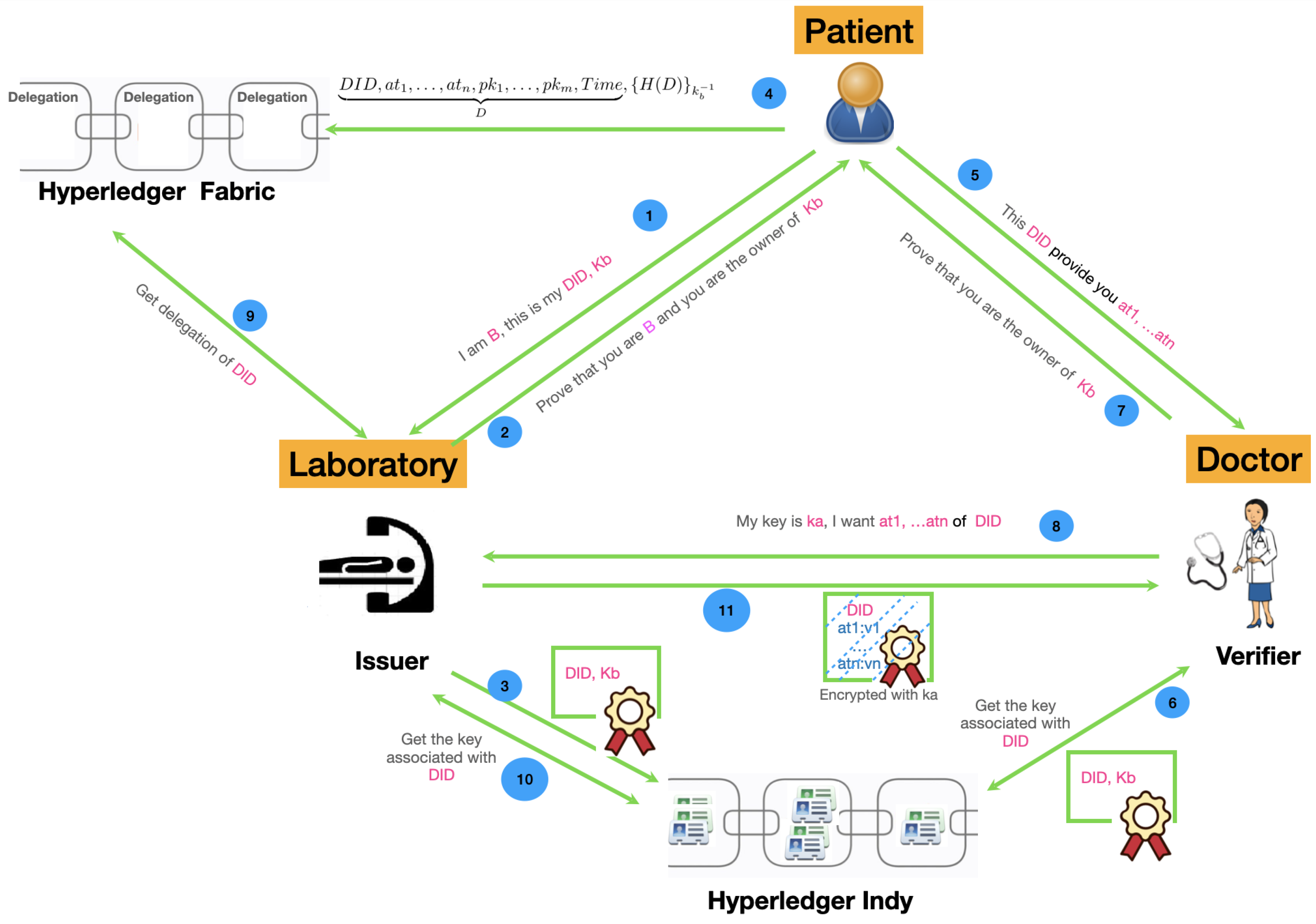
4.3. Module I: Access Control Delegation
- The patient does not necessarily need to carry his attributes in a wallet. He can obtain them any time by contacting their providers.
- The patient can delegate his access control rights to any trusted third party as shown in Table 7. A delegation is a kind of certificate that associates a DID with a set of attributes and a set of public keys. More precisely, a delegation has the form shown by Equation (1) and states that the attributes of the patient known by can be accessed by anyone having a key in until a deadline :The hole delegation policy is specified by a list of rules given in the format of Equation (1) which corresponds to the ABAC model [29]. In fact, each rule specifies the subjects by their public keys (), the objects by their names (), the action (read) is implicit, and the context by (). Of course, we can enrich the rule to take into account other contexts attributes (location, etc.). Additionally, instead of fixing the public keys of the subjects, we can fix some of their attributes (role, department, and hospital). In this case, the subjects need to prove their attributes before getting access to the specified objects. The subject attributes and the proof of their ownership could be handled using Indy in the same manner as proving the ownership of other medical attributes.
- The patient asks the laboratory to attest that he is the owner of the pair (, ). Additionally, he provides the identity that allows the laboratory to identify him; this could be another DID.
- The laboratory asks the patient to prove that he is B and he is the owner of . B can use any DID related to his public key, by which the laboratory can know him.
- The laboratory certifies the link between and and saves it in Indy as shown in Table 5. At the same time, it certifies and keeps secret the link between and B (i.e., ). This link can be saved locally by the laboratory or encrypted using its public key and returned to the patient. Later, when the doctor asks for attributes related to , the link between and B (i.e., ) should be provided or recovered.
- The patient can add the delegation related to any subset of his attributes using Hyperledger Fabric.
- The patient visits the doctor and provides him with the and the list of attributes that he can obtain from the laboratory.
- The doctor obtains the public key associated with from Indy as well as the service endpoint of the trusted provider that certifies this link.
- Using the public key , the doctor asks the patient to prove that he is its owner using the challenge–response protocol given by Table 4.
- Using the service endpoint of the laboratory, the doctor sends a request to obtain attributes associated with and provides his public key .
- The laboratory obtains the delegation from Hyperledger Fabric.
- The laboratory obtains the public key associated with from Indy and checks that the delegation obtained in the previous step is valid (signed using the private key associated with ) and appropriate (it contains the key ).
- The laboratory obtains the identity B of the patient associated with , searches for his attributes, and provides them to the doctor encrypted by his public key as shown in Table 8. Please notice that, for efficiency reasons, public keys are not usually used to encrypt data except keys and hashes. So, encrypting EHR record R with a public key implicitly means that where k is a random private key.
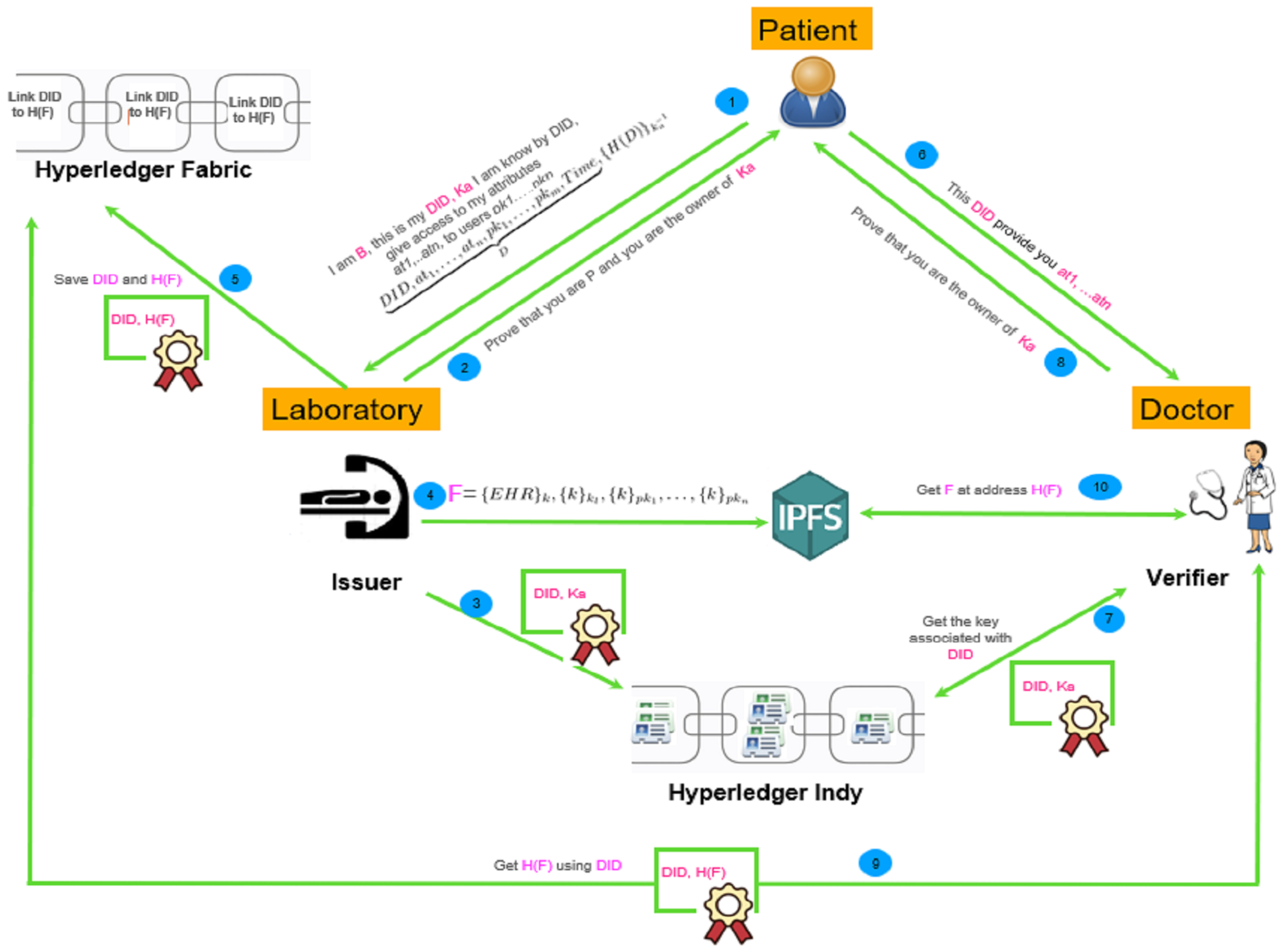
4.4. Module I: Increase Integrity, Availability and Confidentiality by Using IPFS and Fabric
- First, the patient visits a laboratory and receives some service that creates new healthcare attributes, . At any moment later, he can send a request to associate a to any parts of his attributes. He can also, at the same time or any moment later, send a delegation to the laboratory. If the patient wants to give new principal access in the future, he can send a new delegation to the laboratory, and a new entry will be added in the IPFS, or we update the previous one.Notice also that we can handle the delegation as in the previous architecture, but with IPFS, we can immediately concretize it by giving access to the keys protecting the EHRs to all the authorized principals.
- The laboratory checks the patient’s identity and verifies that he owns the public key associated with the .
- The laboratory adds to Indy a certificate linking to .
- The laboratory creates the file F containing the requested attributes encrypted with its key and all the keys given within the delegation and saves it in the IPFS.
- The laboratory adds to Fabric a certificate linking to ( is the address of F in the IPFS).
- The patient contacts the doctor Alice and asks for a healthcare service and provides the associated with his attributes that he wants to share with her.
- Alice obtains the public key associated with from Hyperledger Indy.
- The doctor asks the patient to prove that he owns the public key .
- The doctor obtains associated with from Hyperledger Fabric.
- The doctor obtians the file F with the address from IPFS.
- The doctor uses her public key to decrypt the EHRs of the patient.
4.5. Handling Emergency Access
- The decentralized identifier (DID) used in Indy is a W3C standard [30]. The main information in a DID record is the DID number and its owner’s public key. However, it may contain many other information useful for different contexts. For example, we find the authentication protocols that the owner can use with verifiers. Additionally, the DID record may contain delegation information giving other public keys of other subjects that can act on behalf of the owner and can be used for emergency access. In addition, the DID record is designed to be extensible so that we can add other fields useful for our specific contexts. In particular, we can add fields for the contact information related to delegated people for emergency; we gave their public keys in the delegation field. Another interesting feature provided by the DID is the ability to specify different verification and authentication methods. We can, for example, use a threshold signature. In this case, we can specify n keys in the delegation part, and require that at least k of them need to sign a challenge to able to behave on behalf of the owner. Using this mechanism, it is even possible to revoke a key according to the owner requirement.
- We can simply use the secret splinting technique to achieve this goal. The idea is as follows: To be able to act on behalf of Bob during an emergency, trustees need to know the DID of the vital attributes and the private key associated to it. However, Bob does not want to give to a particular trustee, but he allows any subgroup of trustees, with a predefined size, to reveal this private key. To this end, we can use the threshold cryptography (also called secret splitting) like [31]: the key is encrypted by a random secret key k that can be revealed only by a group of trustees with the appropriate size. A common way to achieve this goal is to generate a random polynomial of degree , where , then we generate n points in the polynomial. Every trustee receives only one point on the polynomial. In this case, we are sure that at least l users are needed to rebuild the polynomial and find the value of using the famous Lagrange equations [32].Of course, hospitals should know the contact of the trustees of Bob. For this reason, Bob needs to register them somewhere (e.g., hospital information systems) so that they will be found and contacted quickly. It will also be a good idea that hospitals are one of the trustees. Obviously, the emergency procedure (finding trustees, contacting them, recovering the key, and revealing vital attributes) should be automated so as to not waste a precious second.
4.6. Module II: Webauthn for More Security
5. Prototype: A Proof of Concepts
5.1. EHR Based on the Hyper-Ledger Indy
| PUBLIC-KEY | Date | Attribute | … | Attribute |
| ⋮ | ⋮ | ⋮ | ⋮ | ⋮ |
| 1 January 2023 | … |
| Healthcare-Provider | PUBLIC-KEY | PRIVATE-KEY | Date | Attributes |
| ⋮ | ⋮ | ⋮ | ⋮ | ⋮ |
| L | 1 January 2023 |
- Bob sends a request to the laboratory to ask for a subset of attributes in that are associated with . This request should contain the name of the attributes, his owner (), a fresh public key , and fresh random DID as shown in Figure 5. First, the laboratory checks the identity of Bob by asking him to prove that he owns public key using the protocol of Table 4. Then, the laboratory asks Bob to prove that he is also the owner of public key using the protocol of Table 4.
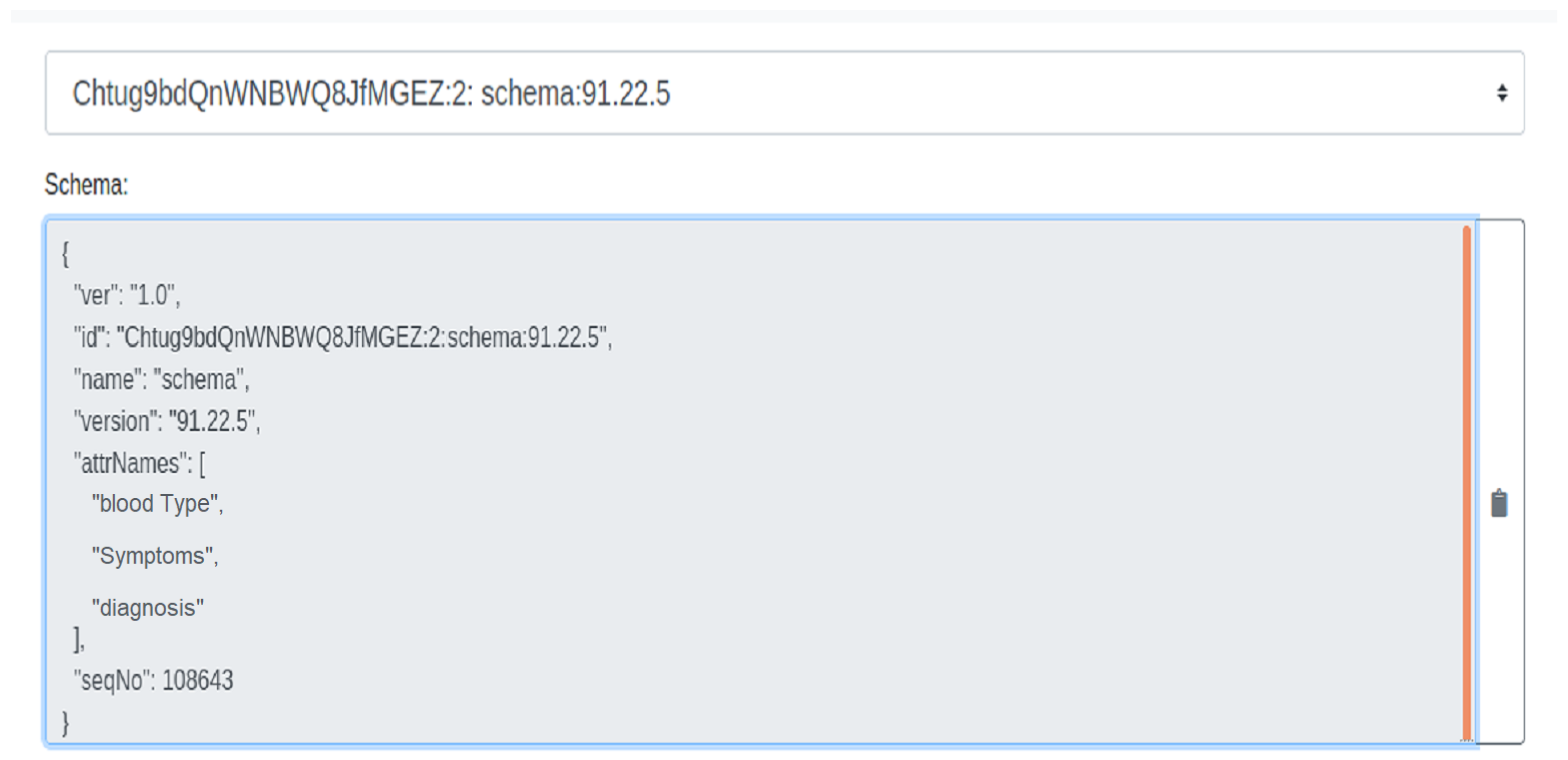
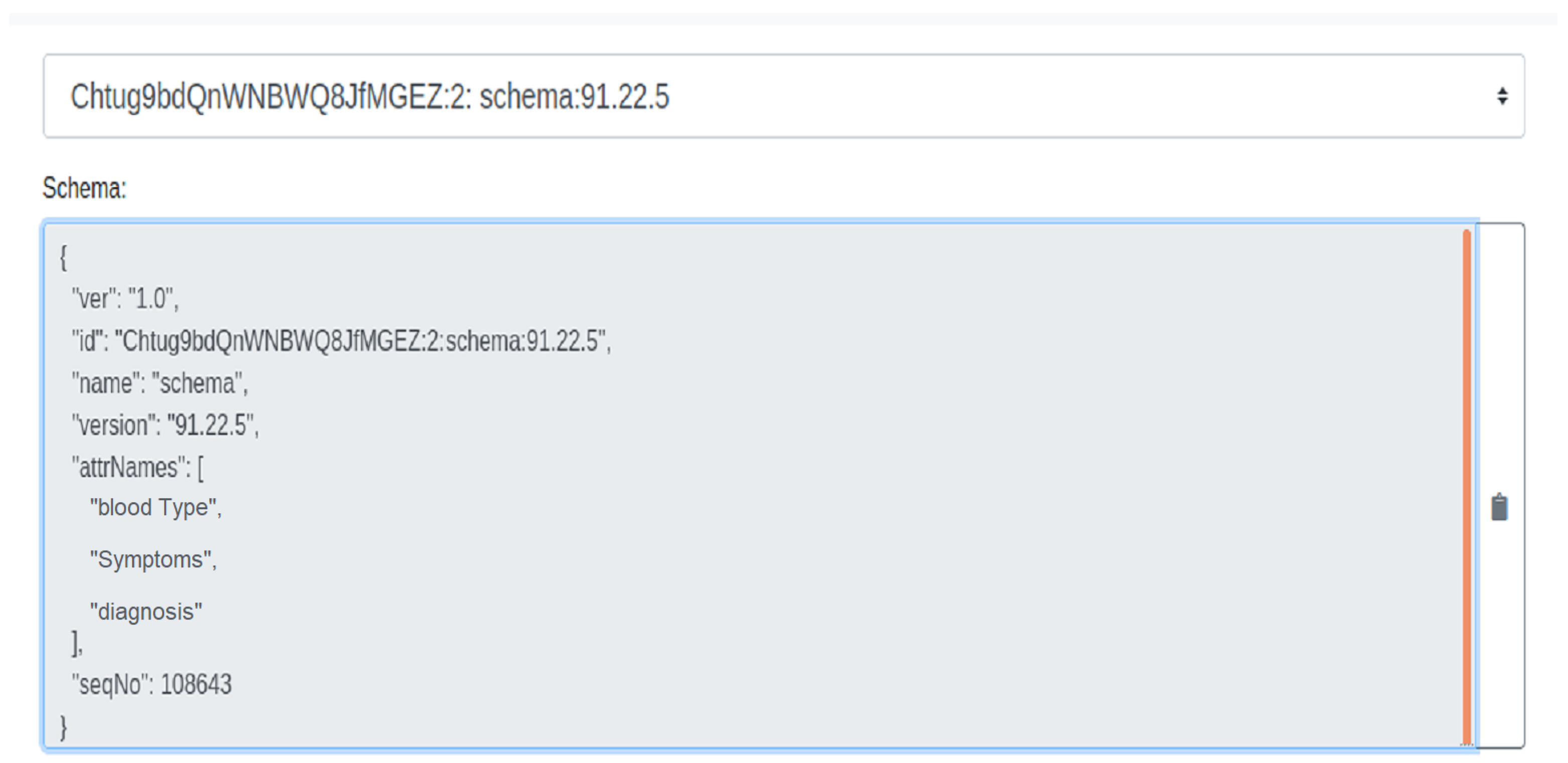
- The laboratory creates a certificate attesting that DID belongs to the owner of and saves it in the hyper-ledger Indy as shown in Figure 6.
- Then, the laboratory creates a signed document (patient credentials) for Bob containing the DID and the requested attributes with their values. After that, the laboratory sends these credentials to Bob, who saves them in his wallet as shown in Figure 7.
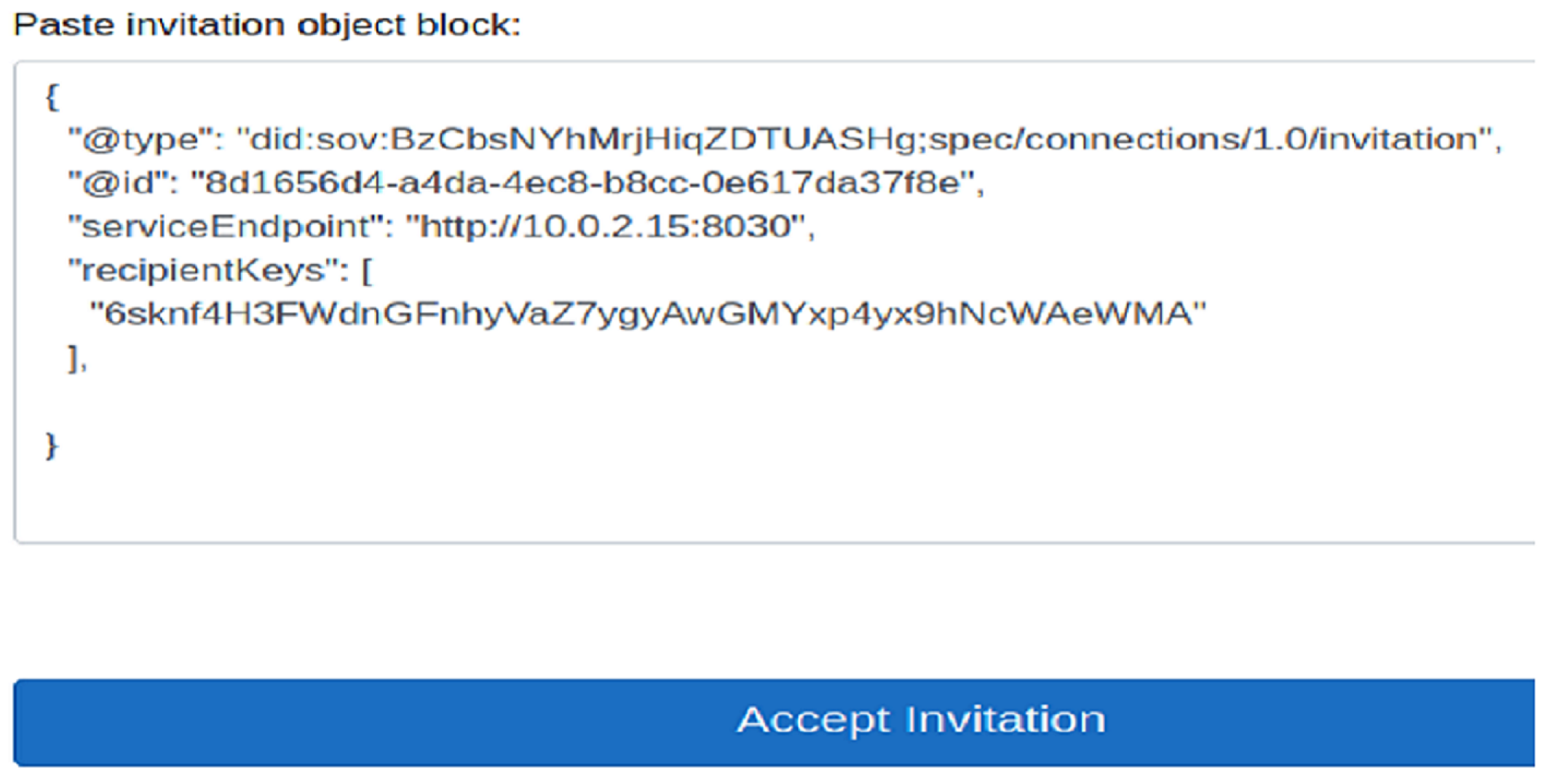
- Patient Bob forwards the credential containing the attributes and their value to Alice.
- Then, doctor Alice accepts Bob’s invitation as shown in Figure 8 and obtains the public key Kb associated with DID from the hyper-ledger Indy.
5.2. EHR Based on Indy and Fabric
- The laboratory certifies the link between and and saves it in Hyperledger Indy as shown in Figure 6.
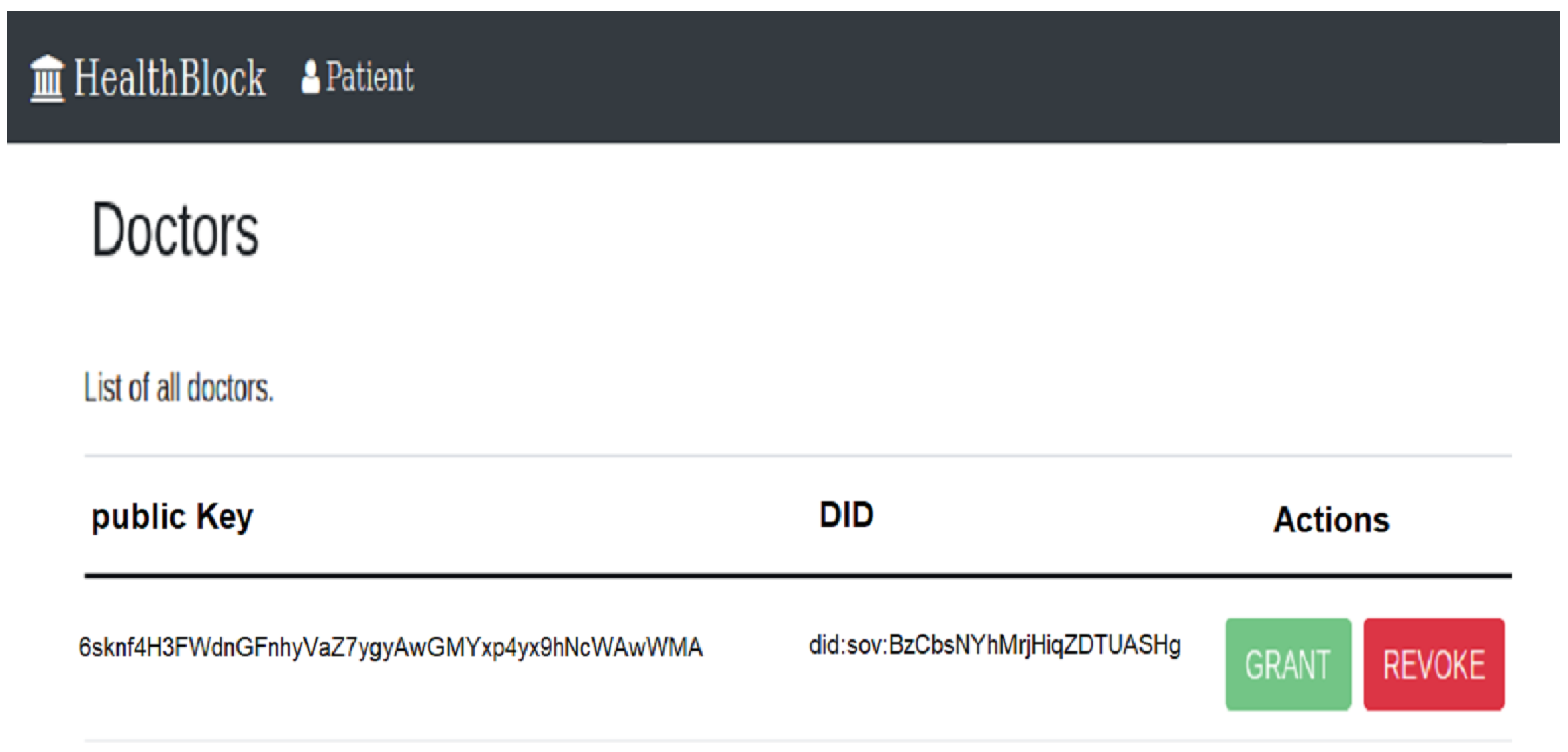
- Bob can add the delegation related to his attributes provided by the laboratory to Hyperledger Fabric as shown in Figure 10.
- Bob visits doctor Alice and provides her with the and the list of attributes that she can obtain from the laboratory as shown in Figure 11.
- Alice obtains the public key associated with from Indy as well as the service endpoint of the trusted provider that certifies this link.
- Using the public key , Alice asks Bob to prove that he is its owner using the challenge–response protocol given by Table 4.
- Using the service endpoint of the laboratory, Bob sends a request to obtain the attributes associated with and provides his public key .
- The laboratory obtains the delegation from Hyperledger Fabric as shown in Figure 10.
- The laboratory obtains the public key associated with from Indy as shown in Figure 6 and checks that the delegation obtained in the previous step is valid (it is signed using the private key associated with ) and appropriate (it contains the key ).
- The laboratory obtains the identity kb0 of the patient associated with , searches for his attributes, and provides them to the doctor encrypted by his public key .
6. Discussion
- No one can access to healthcare attributes without the consent of their owners.
- Patients can remotely prove that they are the owners of their EHRs.
- Patients can remotely prove, using zero-knowledge proof (ZKP), that a part of their healthcare attributes respects some properties without revealing their values (e.g., blood pressure is less than 130 mm Hg).
- Patients can hide some attributes in an EHR while revealing others.
- Full patient control over their EHRs: Any access to any EHR attribute by the doctor at step 10 of Figure 4 requires prior patient delegation in step 5.
- Anonymous Healthcare Service: Patients can register anonymously using DIDs and later prove ownership of any DID attached to their EHR.
- EHR-Availability: EHRs are stored in IPFS which inherently ensures availability since data are duplicated and decentralized.
- EHR-Confidentiality: EHRs are encrypted in step 4 of Figure 4 using public keys of authorized third parties only.
- EHR-Integrity: Since EHRs are stored in IPFS which addresses files by their hashes, any modification in a file renders the hash invalid.
- EHR-Access Control Delegation: Step 2 in Figure 4 allows patients to delegate any attribute of their EHRs to any third party
- EHR-Zero-Knowledge Proof: This feature is inherently provided by the Hyperledger Indy. Doctors cannot reveal any other information relating to the patients, except for the attributes that have been deliberately provided to them.
- EHR-Emergency Access: Examples of techniques that can be used to manage access to EHRs in an emergency were discussed in Section 4.5.
- Scalability: The most important characteristics affecting the scalability of the proposed architecture are storage and transaction speed.Transaction speed is usually addressed by selecting a Hyperledger using a fast consensus algorithm. Fabric uses the KAFKA-consensus algorithm [34] while Indy uses Byzantine Redundant Fault Tolerance (RBFT) [35]. As noted in [36], both are based on authorized voting and offer good speed. For example, according to the Fabric official website [25], the supported transaction speed is 3000 transactions per second. It is a fast blockchain compared to Bitcoin (maximum of 7 transactions per second) or Ethereum (45 transactions per second). For comparison, according to [37], Visa handles 1700 transactions per second. Regarding Indy, the supported transaction speed, according to [38], is 100 transactions per second.To address the storage scalability issue, most blockchain and Hyperledger use both online and offline storage. Transactions are stored offline, where their hashes are stored online and shared among peers. Other techniques, including vertical and horizontal scaling, are also used. For IPFS, for example, more nodes (servers) are added (vertical scaling) to give more storage to the overall file system before reaching its limit. The same idea applies to nodes used for offline storage with Hyperledgers. Another possible expansion can be achieved by adding more power and memory to existing nodes, which is also useful for improving the storage scalability of IPFS, Indy, and Fabric.
- Interoperability: Using an open, planetary file system, such as IPFS and a public Hyperledger such as Indy makes the solution more interoperable. Fabric could also be made public.
- Remote Health Service: The proposed solution allows patients to remotely prove their attributes, thanks to Indy, which is essential to open the door to remote healthcare services.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| EHRs | Electronic Health Records |
| EMRs | Electronic Medical Records |
| P2P | Peer-to-Peer |
| DID | Decentralize Identifier |
| IPFS | InterPlanetary File System |
| SSI | Self-Sovereign Identity |
| SFS | Self-Certifying File System |
| ZKP | Zero-Knowledge Proof |
| ABAC | Attribute based Access Control |
| ABE | Attribute based Encryption |
| W3C | World Wide Web Consortium |
| URI | Uniform Resource Identifier |
| RBFT | Redundant Byzantine Fault Tolerance |
References
- IPFS. IPFS Powers the Distributed Web. Available online: https://ipfs.io (accessed on 7 January 2023).
- IPFS. Bitswap. Web. Available online: https://docs.ipfs.io/concepts/bitswap/ (accessed on 11 May 2022).
- GIT. Distributed Is the New Centralized. Web. Available online: https://git-scm.com (accessed on 11 May 2022).
- Maziéres, D.; Kaminsky, M.; Kaashoek, M.F.; Witchel, E. Separating key management from file system security. In Proceedings of the 7th ACM Symposium on Operating System Principles (SOSP ’99), Kiawah Island, SC, USA, 12–15 December 1999. [Google Scholar]
- Sun, J.; Yao, X.; Wang, S.; Wu, Y. Blockchain-based secure storage and access scheme for electronic medical records in IPFS. IEEE Access 2020, 8, 59389–59401. [Google Scholar] [CrossRef]
- Kumar, R.; Marchang, N.; Tripathi, R. Distributed off-chain storage of patient diagnostic reports in healthcare system using IPFS and blockchain. In Proceedings of the 2020 INTERNATIONAL Conference on Communication Systems & Networks (COMSNETS), Bengaluru, India, 7–11 January 2020; pp. 1–5. [Google Scholar]
- Khatoon, A. A blockchain-based smart contract system for healthcare management. Electronics 2020, 9, 94. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Blockchain for Secure EHRs Sharing of Mobile Cloud Based e-Health Systems. IEEE Access 2019, 7, 66792–66806. [Google Scholar] [CrossRef]
- Shen, B.; Guo, J.; Yang, Y. MedChain: Efficient healthcare data sharing via blockchain. Appl. Sci. 2019, 9, 1207. [Google Scholar] [CrossRef]
- Niu, S.; Chen, L.; Wang, J.; Yu, F. Electronic health record sharing scheme with searchable attribute-based encryption on blockchain. IEEE Access 2019, 8, 7195–7204. [Google Scholar] [CrossRef]
- Shahnaz, A.; Qamar, U.; Khalid, A. Using blockchain for electronic health records. IEEE Access 2019, 7, 147782–147795. [Google Scholar] [CrossRef]
- Kim, M.G.; Lee, A.R.; Kwon, H.J.; Kim, J.W.; Kim, I.K. Sharing medical questionnaries based on blockchain. In Proceedings of the 2018 IEEE International Conference on Bioinformatics and Biomedicine (BIBM), Madrid, Spain, 3–6 December 2018; pp. 2767–2769. [Google Scholar]
- Dagher, G.G.; Mohler, J.; Milojkovic, M.; Marella, P.B. Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology. Sustain. Cities Soc. 2018, 39, 283–297. [Google Scholar] [CrossRef]
- Fan, K.; Wang, S.; Ren, Y.; Li, H.; Yang, Y. Medblock: Efficient and Secure Medical Data Sharing via Blockchain. J. Med. Syst. 2018, 42, 136. [Google Scholar] [CrossRef] [PubMed]
- Liu, J.; Li, X.; Ye, L.; Zhang, H.; Du, X.; Guizani, M. BPDS: A blockchain based privacy-preserving data sharing for electronic medical records. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Omar, A.A.; Rahman, M.S.; Basu, A.; Kiyomoto, S. Medibchain: A blockchain based privacy preserving platform for healthcare data. In Proceedings of the International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, Guangzhou, China, 12–15 December 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 534–543. [Google Scholar]
- Dubovitskaya, A.; Xu, Z.; Ryu, S.; Schumacher, M.; Wang, F. Secure and Trustable Electronic Medical Records Sharing using Blockchain. AMIA Annu. Symp. Proc. 2017, 2017, 650. [Google Scholar] [PubMed]
- Liang, X.; Zhao, J.; Shetty, S.; Liu, J.; Li, D. Integrating Blockchain for Data Sharing and Collaboration in Mobile Healthcare Applications. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–5. [Google Scholar]
- Xia, Q.I.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-less Medical Data Sharing Among Cloud Service Providers via Blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. Medrec: Using blockchain for medical data access and permission management. In Proceedings of the 2016 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016; pp. 25–30. [Google Scholar]
- Yue, X.; Wang, H.; Jin, D.; Li, M.; Jiang, W. Healthcare Data Gateways: Found Healthcare Intelligence on Blockchain with Novel Privacy Risk Control. J. Med. Syst. 2016, 40, 218. [Google Scholar] [CrossRef] [PubMed]
- SandIkkaya, M.T.; Decker, B.D.; Naessens, V.; Szomszor, M.; Kostkova, P. Privacy in commercial medical storage systems. In Proceedings of the Electronic Healthcare. Third International Conference, eHealth 2010, Casablanca, Morocco, 13–15 December 2010; Lecture Notes of the Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering. Springer Verlag: Berlin/Heidelberg, Germany, 2011; Volume 69, pp. 247–258. [Google Scholar]
- Masi, M.; Maurer, R. On the Usage of SAML Delegate Assertions in an Healthcare Scenario with Federated Communities. In Proceedings of the Electronic Healthcare. Third International Conference, eHealth 2010, Casablanca, Morocco, 13–15 December 2010; Lecture Notes of the Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering. Springer Verlag: Berlin/Heidelberg, Germany, 2011; Volume 69, pp. 212–218. [Google Scholar]
- Indy. Hyperledger Indy. Available online: https://www.hyperledger.org/use/hyperledger-indy (accessed on 27 November 2022).
- Linux Foundation. Hyperledgre Fabric. Available online: https://www.hyperledger.org/use/fabric (accessed on 7 March 2021).
- FIDO Alliance. Simpler, Stronger Authentication. Available online: https://fidoalliance.org (accessed on 2 December 2021).
- Sovrin Foundation. Sovrin. Available online: https://sovrin.org (accessed on 23 December 2020).
- Sovrin Foundation. Use Case Spotlight: The Government of British Columbia Uses the SovrinNetwork to Take Strides towards a Fully Digital Economy. Available online: https://sovrin.org/usecase-spotlight-the-government-of-british-columbia-uses-the-sovrin-networkto-take-strides-towards-a-fully-digital-economy/ (accessed on 23 December 2020).
- Hu, V.C.; Ferraiolo, D.; Kuhn, R.; Schnitzer, A.; Sandlin, K.; Miller, R.; Scarfone, K. Guide to Attribute Based Access Control (ABAC) Definition and Considerations. NIST Special Publication 800-162. 2014. Available online: https://nvlpubs.nist.gov/nistpubs/specialpublications/NIST.SP.800-162.pdf (accessed on 10 January 2023).
- World Wide Web Consortium (W3C). Decentralized Identifiers (DIDs) v1.0 Core Architecture, Data Model, and Representations. W3C Standard 2021. Available online: https://www.w3.org/TR/did-core/#authentication (accessed on 12 April 2022).
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Berrut, J.P.; Trefethen, L.N. Barycentric Lagrange Interpolation (PDF). Siam Rev. 2004, 46, 501–517. [Google Scholar] [CrossRef]
- Webauthn. Using WebAuthn. Available online: https://webauthn.io (accessed on 2 January 2021).
- Kreps, J.; Narkhede, N.; Rao, J. Kafka: A distributed messaging system for log processing. Proc. NetDB 2011, 11, 1–7. [Google Scholar]
- Aublin, P.L.; Mokhtar, S.B.; Quéma, V. RBFT: Redundant Byzantine Fault Tolerance. In Proceedings of the IEEE 33rd International Conference on Distributed Computing Systems, Philadelphia, PA, USA, 8–11 July 2013. [Google Scholar]
- The Linux Foundation. Hyperledger Architecture, Volume 1: Introduction to Hyperledger Business Blockchain Design Philosophy and Consensus. 2017. Available online: https://www.hyperledger.org/wp-content/uploads/2017/08/Hyperledger_Arch_WG_Paper_1_Consensus.pdf (accessed on 20 March 2022).
- Sedgwick, K. No, Visa Doesn’t Handle 24,000 TPS and Neither Does Your Pet Blockchain. Available online: https://news.bitcoin.com/no-visa-doesnt-handle-24000-tps-and-neither-does-your-pet-blockchain/ (accessed on 20 March 2022).
- Edx. Introduction to Hyperledger Sovereign Identity Blockchain Solutions: Indy, Aries & Urs. Available online: https://learnthings.online/other/2020/03/05/introduction-to-hyperledger-sovereign-identity-blockchain-solutions-indy-aries-ursa (accessed on 10 April 2022).


| Blockchain Type | Blockchain Name | Smart Contract | Blockchain Role | EHRs Access Control | EHRs Privacy | EHRs Storage | Authors |
|---|---|---|---|---|---|---|---|
| Public | Ethereum | Yes | Save Address of EHRs | Attribute Based Encryption (ABE) | ABE | IPFS | Sun et al. [5] |
| Save Addresses of Patients | Cloud EHR Manager | EHR Manager’s Public Key | Nguyenet al. [8] | ||||
| Off-chain Storage | Shahnaz et al. [11] | ||||||
| Dagher et al. [13] | |||||||
| Provider Local Database + Patient Database | Azaria et al. [20] | ||||||
| Not fixed | No | Save hash value of EHRs | bread crumbs | Encryption technology | Local Database or Cloud | Fan et al. [14] | |
| Store data digest in Blockchain | Database | Shen et al. [9] | |||||
| Consortium | Save keywords of EHRs | Attribute-Based Encryption | Cloud Storage | Niu et al. [10] | |||
| Save hash of medical data | membership service component | Liang et al. [18] | |||||
| Save medical data | Not specified | Blockchain | Al Omar et al. [16] | ||||
| metadata + access control policy | Role-based | Local Database + Cloud | Dubovitskaya et al. [17] | ||||
| Stored hash of medical records | Not specified | Hash based data storage | IPFS | Kumar et al. [6] | |||
| Yes | Reserve indexes of EMRs | Content extraction signature | Encryption technology | Cloud | Liu et al. [15] | ||
| Questionnaire result data | According to medical policy | Blockchain | Kim et al. [12] | ||||
| save immutable database | Not specified | Database | Xia et al. [19] | ||||
| Private | No | data stored in private blockchain | Access control model | Blockchain + Cloud | Yue et al. [21] | ||
| No Blockchain | No Blockchain | No Blockchain | Encryption technology + Cryptographic Protocols | Database | Sandıkkaya et al. [22] |
| Without Permission | With Permission | |
|---|---|---|
| read and write | limited read or write | |
| Public (access to everyone) | Bitcoin, Ethereum, IOATA, etc. | Hyperledger Indy (sovereign), IODB, etc. |
| Private (access to a limited group) | Hyperledger Sawtooth (permissionless mode) | Hyperledger Fabric, Iroha, Sawtooth, etc. |
| DID | PUBLIC-KEY | DID- | {Hash(DID, PUBLIC-KEY, DID-)} |
|---|---|---|---|
| ⋮ | ⋮ | ⋮ | ⋮ |
| 1. | A | → | B | : | |
| 2. | B | → | A | : |
| Data Location | Patient Wallet | Indy | IPFS |
|---|---|---|---|
| EHRs | ✓ | ✓ | |
| DID-Key certification | ✓ |
| Features | Patient Controls Access to his EHRs | Anonymous Healthcare Service | EHR-Availability | EHR-Confidentiality | EHR-Integrity | EHR-Access Control Delegation | EHR-Zero-Knowledge Proof | EHR-Emergency Access | Scalability | Interoperability | Remote Health Service | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Approach | ||||||||||||
| Indy EHRs | ✓ | ✓ | +- | +- | +- | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| Roles | Patient | EHR Provider | EHR Consumer | |
|---|---|---|---|---|
| Action on EHRs | ||||
| Creation | ✓ | |||
| Encryption | ✓ | |||
| Upload | ✓ | |||
| Access | ✓ | ✓ | after patient’s permission | |
| Delegate permission | ✓ | |||
| Modify | ✓ | |||
| During transmission (Provider to Patient) | Wallet | During transmission (Patient to Consumer) | |
| EHR protection | public key of Patient | public key of Patient | public key of Consumer |
| Features | Patient Controls Access to His EHR | Anonymous Healthcare Service | EHR-Availability | EHR-Confidentiality | EHR-Integrity | EHR-Access Control Delegation | EHR-Zero-Knowledge Proof | EHR-Emergency Access | Scalability | Interoperability | Remote Health Service | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Approach | ||||||||||||
| Indy + Fabric EHRs | ✓ | ✓ | +- | +- | +- | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| Features | Patient Controls Access to His EHR | Anonymous Healthcare Service | EHR-Availability | EHR-Confidentiality | EHR-Integrity | EHR-Access Control Delegation | EHR-Zero-Knowledge Proof | EHR-Emergency Access | Scalability | Interoperability | Remote Health Service | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Approach | ||||||||||||
| Indy + Fabric + IPFS EHRs | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| Features | EHR-Availability | EHR-Confidentiality | EHR-Integrity | Delegation | EHRs-Location | Delegation Location | |
|---|---|---|---|---|---|---|---|
| Approach | |||||||
| Indy | +- | +- | +- | Patient’s wallet | |||
| Indy + Fabric | +- | +- | +- | ✓ | Patient’s wallet | Fabric | |
| Indy + Fabric + IPFS | ✓ | ✓ | ✓ | ✓ | IPFS | Fabric | |
| Step | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Computation | |||||||||||||
| Patient | Hash | 0,0,1 | 1,1,1 | 0,1,0 | 0,1,0 | 1,0,0 | 0,1,0 | 0,0,1 | |||||
| Signature or Private Key Encryption | 0,0,1 | 0,1,1 | 0,1,0 | 1,1,0 | 0,0,1 | ||||||||
| Signature Verification or Public key Encryption | 1,0,0 | ||||||||||||
| Symmetric Key Encryption/ Decryption | |||||||||||||
| Key Generation | 1,1,0 | ||||||||||||
| Random Number Generation | 1,1,0 | ||||||||||||
| Laboratory | Hash | 1,0,1 | 1,1,1 | 1,1,1 | 0,0,1 | ||||||||
| Signature or Private Key Encryption | 1,0,0 | 0,1,1 | 0,0,1 | 0,1,0 | |||||||||
| Signature Verification or Public key Encryption | 1,0,1 | 0,0,1 | 0,0,n | 0,1,0 | |||||||||
| Symmetric Key Encryption/ Decryption | 0,0,1 | ||||||||||||
| Key Generation | |||||||||||||
| Random Number Generation | 1,1,0 | ||||||||||||
| Doctor | Hash | 1,0,0 | 1,0,0 | 1,1,0 | 0,1,1 | 0,0,1 | 0,0,1 | 0,1,1 | |||||
| Signature or Private Key Encryption | 0,0,1 | ||||||||||||
| Signature Verification or Public key Encryption | 1,0,0 | 1,0,0 | 1,1,0 | 0,1,1 | 0,0,1 | 0,0,1 | 0,1,0 | ||||||
| Symmetric Key Encryption/ Decryption | 0,0,1 | ||||||||||||
| Key Generation | |||||||||||||
| Random Number Generation | 1,0,0 | 0,1,0 | 0,0,1 | ||||||||||
| Features | Full Patient Control over Their EHRs | Anonymous Healthcare Service | EHR-Availability | EHR-Confidentiality | EHR-Integrity | EHR-Access Control Delegation | EHR-Zero-Knowledge Proof | EHR-Emergency Access | Scalability | Interoperability | Remote Health Service | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Approach | ||||||||||||
| Sun et al. [5] | ✓ | ✓ | ✓ | |||||||||
| Kumarn et al. [6] | ✓ | ✓ | ✓ | |||||||||
| Khatoo [7] | +- | +- | +- | |||||||||
| Nguyen et al. [8] | ✓ | ✓ | ✓ | |||||||||
| Shen et al. [9] | +- | +- | ✓ | |||||||||
| Niu et al. [10] | +- | ✓ | ✓ | |||||||||
| Shahnaz et al. [11] | ✓ | ✓ | ✓ | ✓ | ||||||||
| Kim et al. [12] | ✓ | ✓ | ✓ | |||||||||
| Dagher et al. [13] | +- | +- | ✓ | ✓ | ||||||||
| Liu et al. [15] | +- | +- | ✓ | |||||||||
| Al Omar et al. [16] | ✓ | ✓ | ✓ | |||||||||
| Dubovitskaya et al. [17] | ✓ | +- | +- | |||||||||
| Liang et al. [18] | +- | +- | ✓ | ✓ | ||||||||
| Xia et al. [19] | +- | +- | ✓ | |||||||||
| Azaria et al. [20] | +- | ✓ | ✓ | ✓ | ||||||||
| Yue et al. [21] | ✓ | ✓ | ✓ | |||||||||
| Fan et al. [14] | +- | +- | +- | |||||||||
| Proposed Approach (Indy +Fabric + IPFS) | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abdelgalil, L.; Mejri, M. HealthBlock: A Framework for a Collaborative Sharing of Electronic Health Records Based on Blockchain. Future Internet 2023, 15, 87. https://doi.org/10.3390/fi15030087
Abdelgalil L, Mejri M. HealthBlock: A Framework for a Collaborative Sharing of Electronic Health Records Based on Blockchain. Future Internet. 2023; 15(3):87. https://doi.org/10.3390/fi15030087
Chicago/Turabian StyleAbdelgalil, Leina, and Mohamed Mejri. 2023. "HealthBlock: A Framework for a Collaborative Sharing of Electronic Health Records Based on Blockchain" Future Internet 15, no. 3: 87. https://doi.org/10.3390/fi15030087
APA StyleAbdelgalil, L., & Mejri, M. (2023). HealthBlock: A Framework for a Collaborative Sharing of Electronic Health Records Based on Blockchain. Future Internet, 15(3), 87. https://doi.org/10.3390/fi15030087






