Abstract
In order to develop a Supercomputing Cloud Platform (SCP) prototype system using Service-Oriented Architecture (SOA) and Petri nets, we researched some technologies for Web service composition. Specifically, in this paper, we propose a reliability calculation method for Web service compositions, which uses Fuzzy Reasoning Colored Petri Net (FRCPN) to verify the Web service compositions. We put forward a definition of semantic threshold similarity for Web services and a formal definition of FRCPN. We analyzed five kinds of production rules in FRCPN, and applied our method to the SCP prototype. We obtained the reliability value of the end Web service as an indicator of the overall reliability of the FRCPN. The method can test the activity of FRCPN. Experimental results show that the reliability of the Web service composition has a correlation with the number of Web services and the range of reliability transition values.
1. Introduction
The Supercomputing Cloud Platform (SCP) integrates many different kinds of software including ANSYS, ABAQUS, LS-DYNA, SLURM, LSF, etc. SCP provides a simple Web interactive way for large-scale and parallel CAE simulation tasks. Our research team develops a SCP prototype of supercomputing. Specifically, we use Service-Oriented Architecture (SOA) architecture to develop the prototype. We use Petri nets to describe Web service compositions, and realized the prototype using a workflow system.
For automatic composition for Web services based on semantic technology, we introduce Ontology Web language for Services (OWL-S) to describe Web services. In order to verify the Web Service Compositions, we proposed a reliability calculation method for Web Service Composition Using Fuzzy Reasoning Colored Petri Nets (FRCPN), then we judged whether the Web service composition could meet the reliability requirements.
At present, the applications of OWL-S are well established in the engineering field. The study on web service composition has many theoretical researches and engineering practices, and the study on CPN, FRCPN has also been making progress. However, the reliability of Web service composition needs to be strengthened and studied further.
2. Related Work
Many researchers use SOA architecture, semantic technology, and workflow technology to build Colored Petri Nets (CPN) or composition system for Web services. In [1], the authors developed a platform prototype for cloud simulation named COSIM-CSP using some Web services, discovery technology, and so on. In [2,3,4,5,6,7,8], the authors also proposed models for cloud platform and designed system prototypes. In [9], the authors developed a composition system for Web services named OntoPipeliner based on semantics. At present, there are some studies underway on a cloud platform based on OWL-S semantic technology, such as [9,10,11].
It is one of the main possible directions for studying on Web service compositions base on Petri. Many researchers are dedicated to applying the improvement of Petri nets to combined Web services [12,13,14,15,16,17]. In [18], the authors proposed a CPN model. In the model, the authors added the transaction features of Web services, considered Quality of Service (QoS) and transaction, and then formed a credible composition for Web services.
In [19], the authors used CPN to design a deterministic analysis method that is used to measure the reliability and the performance. CPN can display the routing structure and apply probability theory. In addition, the authors developed a software tool called WSET, which is used for supporting QoS sensor modeling. In [20], the authors used Petri nets for orchestration with the OWL-S service, which is treated as an ontology engine to support reasoning. In [21], the authors used Hierarchical Colored Petri Net (HCPN) to formally describe Web service compositions, converted the structure of data flow information described by OWL-S, and used the CPN tool to verify the model. In [22], the authors proposed an improved HCPN namely EHCPN to describe Web service compositions. In [23], the authors proposed a method based on translation to convert the process model of OWL-S services into Petri nets. In [24], the authors proposed a method based on stochastic Petri nets for the performance analysis of OWL-S process, and used non-Markov Stochastic Petri Nets as an intermediate representation.
Some scholars have done research on the reliability of Web service compositions using Petri, CPN, or FRCPN [25,26,27,28,29]. In order to improve the reliability value of Web service compositions, [18] and [30] proposed using CPN to formalize the various properties of Web service compositions. In [16], non-Markov Stochastic Petri Nets are proposed based on a probabilistic method of reliability analysis of OWL-S Web service compositions. The authors introduce the normal completion probability of the process to calculate the reliability. In [31], the authors proposed a method to use Petri nets to build reliable Web service compositions. This method verifies the behavior of service compositions and repairs the design errors at design time or run time.
Kim, Y. et al. [32] proposed a trust model expressed by a graph. In the graph, the weights of the edges denote the weights of trust. According to the evaluated trust value, the model can choose a more suitable Web service or Web service composition. In [33], based on the analysis of the data for past services, the authors used the K-mean clustering algorithm to predict the reliability of atomic Web services. Xu, J. et al. [34] developed a model to select the most appropriate service composition. The model uses stochastic Petri nets for service compositions to create a qualitative model, which performs a quantitative analysis of the failure rate and repair rate. In [35], a method called is proposed to quantify the reliability of a repairable system. The main parameters in the method are failure rate, time, and Petri nets. Many methods generate a reachable tree according to the graph, and then calculate the reliability of the tree according to the various parameters of the reachable tree as the reliability of FRCPN graph [36].
In summary, there has been some progress in terms of the reliability calculation method for Web service compositions. However, there is not yet an exact definition of semantic similarity threshold relations in the literature, nor is there a reliability calculation method for Petri nets based on the relations of semantic threshold similarity. The main contributions of this paper are as follows.
- We gradually define the concepts of reliability calculation. Based on the definition of formalized description for Web services, we define the semantic threshold similarity and semantic threshold equality for Web services. We first give the definition of FRCPN and the definition of FRCPN activity. Then, we propose the conditions of the activity. We analyze the reliability calculation of some elements in five kinds of production rules in FRCPN. According to the requirements of reliability calculation for FRCPN, we redefine the formalized definition of transition and the formalized definition of Web services.
- A reliability calculation method for FRCPN is proposed. Firstly, the method calculates the reliability values of the transitions in FRCPN, and uses an algorithm to generate a Sequential Linked List for Filling Reliability Value (SLLFRV) linked list. According to the SLLFRV linked list, we propose an algorithm to calculate the reliability values of all Web services. Finally, we use the reliability value of the end Web service in FRCPN as the reliability value of FRCPN.
- We apply and analyze the reliability calculation method. The reliability value of a FRCPN graph is calculated as an example. We analyze the execution process of the method. We analyze the implementation effect of the method for different size FRCPNs and obtain some rules. We give the application description for the method in SCP.
3. Related Definition
3.1. Definition of Semantic Threshold Similarity and Definition of Semantic Threshold Equality
Definition 1.
Formal description of Web services [9]. A Web service can be formally described as
where is the input parameter set of Web service is the output parameter set of Web service is the precondition set of Web service is the QoS set of Web service .
Definition 2.
Semantic threshold similarity for two ontologies and semantic threshold equality for two ontologies. There are two ontology concepts, and . By calculating their semantic similarity, we can obtain the value of . We set a semantic similarity threshold, . If , then the relation of semantic threshold similarity is built between and , denoted as . If , and , then the relation of semantic threshold equality is built between and , denoted as .
Definition 3.
Semantic threshold similarity for two ontology sets and semantic threshold equality for two ontology sets. There are two concept sets and . We set a semantic similarity threshold, . If any concept in exists corresponding in to satisfy , then the relation of semantic threshold similarity is built between and , denoted as . If , and , then the relation of semantic threshold equality is built between and , denoted as .
Definition 4.
Semantic threshold similarity for Web service preconditions and semantic threshold similarity for Web services QoS. There are two Web services, and ; if any logical expression in exists corresponding in , and is true, then is true, the relation of semantic threshold similarity is built between , denoted as . If any logical expression of QoS in exists corresponding in , and is true, then is true, the relation of semantic threshold similarity is built between and , denoted as .
Definition 5.
Semantic threshold similarity for two Web services and semantic threshold equality for two Web services. There are two Web services, and . We set a semantic similarity threshold , if , , and , then the relation of semantic threshold similarity is built between , denoted as . If and , then the relation of semantic threshold equality is built between , denoted as .
3.2. Definition of FRCPN and Definition of FRCPN Activity
Definition 6.
Formal definition of FRCPN based on semantic similarity for Web service composition [16]:
- (1)
- represents the place set, and each place represents a Web service.
- (2)
- represents the transition set, and each transition represents the matching relationships among Web services.
- (3)
- F is a dependence relation set, represented as an If-Then form.
- (4)
- is a function of , and the function’s value is in the range of [0,1], which is the triggered threshold of the transition. The function is also the semantic similarity threshold for Web services, and we can control the minimum triggered threshold using the function.
- (5)
- is the precondition set defined on the , which represents all preconditions being satisfied before the transitions are triggered.
- (6)
- is the QoS set defined on the ; it indicates all QoS of the Web services that need to be satisfied before the transitions are triggered.
We can measure the matching degree using semantic similarity between the interfaces of two Web services, and then establish the dependence relation. There are five kinds of dependence relations in FRCPN. The semantic similarity calculation considers some factors, including I/O interfaces P, Q, etc., so we adopt semantic similarity as reliability. It is necessary that the reliability value of the transition achieve semantic threshold as a trigger.
Definition 7.
FRCPN activity. In FRCPN, if , and a transition sequence exists, the transition sequence is triggered in sequence, and in semantic threshold , the reliability value Γ of each transition t is satisfied with , then transition t is triggered, we consider that transition t is active in semantic threshold k. According to the dependence relations in FRCPN, we can calculate the reliability values of the Web services and the transitions. We use the reliability value of the end Web service in FRCPN as the reliability value ω of FRCPN. In the reliability threshold , all of the transitions in FRCPN are active in semantic threshold k, and the reliability value ω of FRCPN satisfies , so FRCPN is activity in semantic threshold k and reliability threshold a.
3.3. Production Rule of FRCPN
Next, we discuss five production rules of FRCPN. According to the reliability values of Web services, we can verify the FRCPN activity, and obtain better quality FRCPN.
3.3.1. The First Production Rule
(The semantic similarity threshold k)
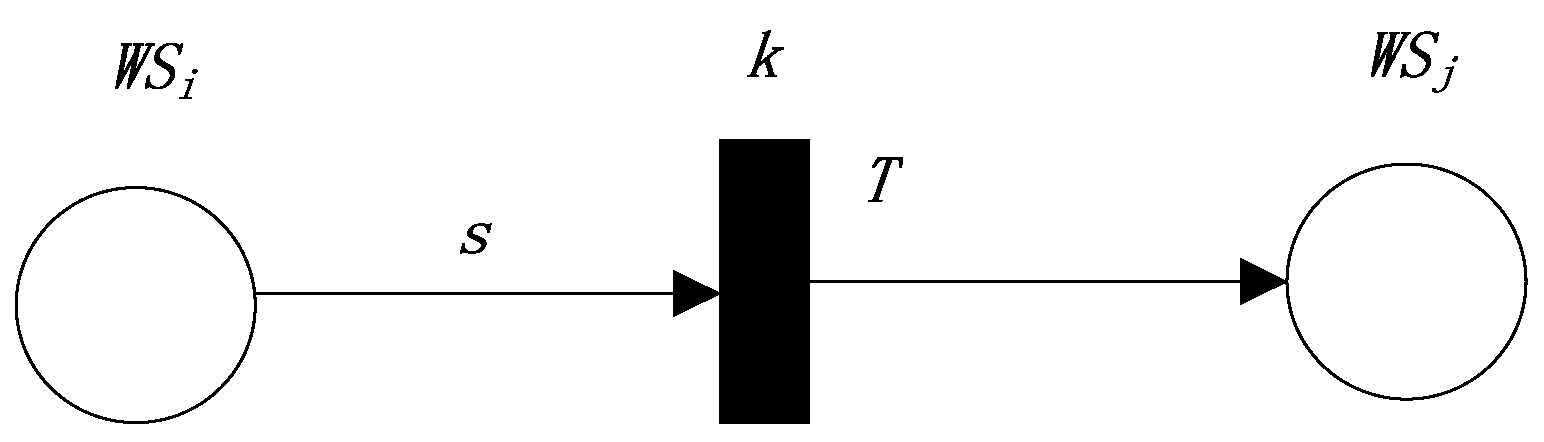
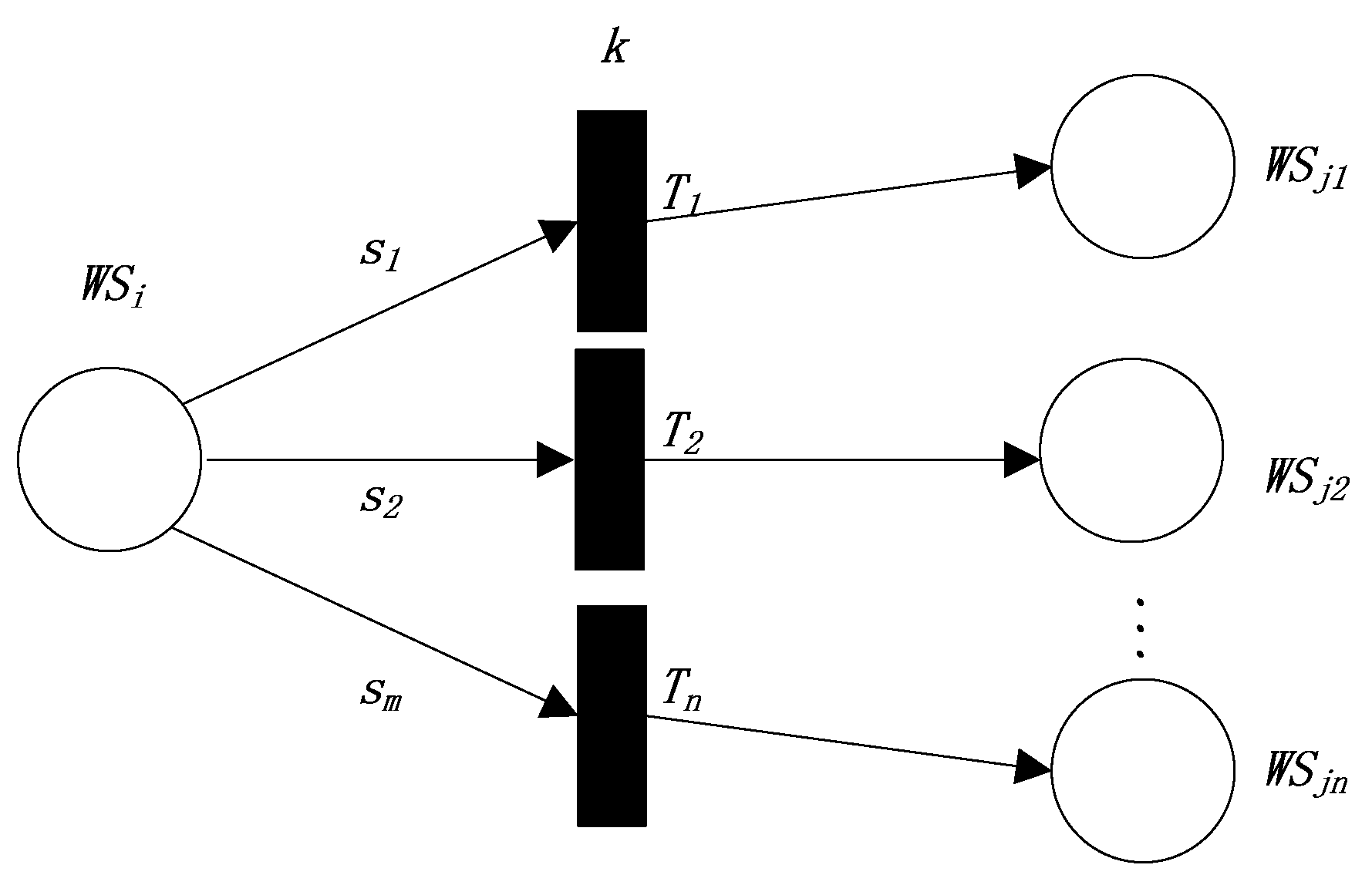
The first production rule represents a dependence relation (the semantic similarity threshold k). The FRCPN based on semantic similarity for Web service compositions is shown in Figure 1.
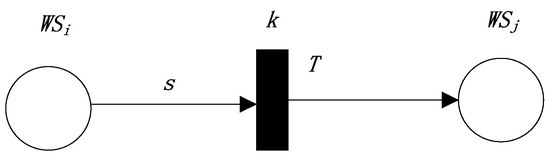
Figure 1.
The FRCPN (Fuzzy Reasoning Colored Petri Net) expression of the first production rule.
The above rule indicates the dependence relationship . Here, s is the semantic similarity value between the outputs of and the inputs of . The above rule needs to satisfy some conditions including , , and all of the conditions in . Therefore,
In Equation (1), represents the semantic similarity between the outputs of and the inputs of . is the weight that represents the attention degree of matching between the outputs of and the inputs of . is the weight that represents the attention degree of satisfying all conditions in and .
According to the above definition, we define the reliability value of the transition T by the semantic similarity between the interfaces of and the interfaces of , as follows:
We can define the reliability value of in this dependence relation as follows:
3.3.2. The Second Production Rule
(The semantic similarity threshold k)
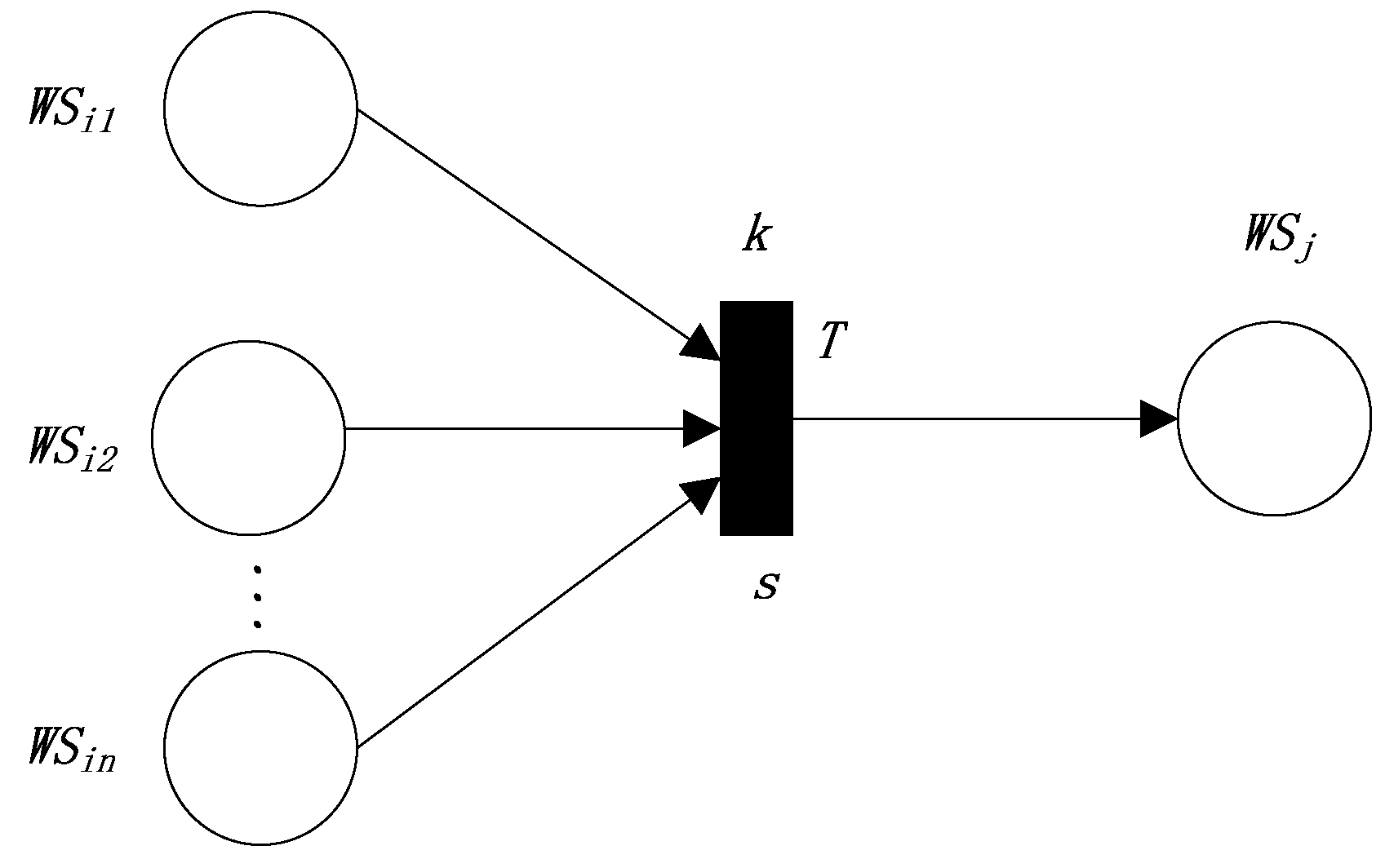
The second production rule represents a dependence relation “” (the semantic similarity threshold k). The FRCPN based on semantic similarity for Web service compositions is shown in Figure 2.
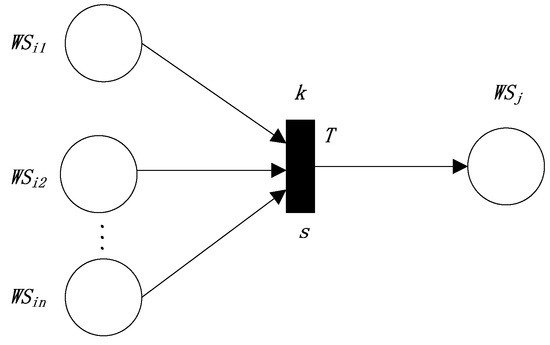
Figure 2.
The FRCPN expression of the second production rule.
s is the semantic similarity between (the union of the outputs of “”) and the inputs of . The above rule needs to satisfy some conditions, including , , all of the conditions in “”, and all of the conditions in “”. Therefore,
In Equation (4), represents the semantic similarity between and the inputs of . is the weight that represents the attention degree of matching between and the inputs of . is the weight that represents the attention degree of satisfying all the conditions in “” and “”.
According to the above definition, we define the reliability value of the transition T in terms of the semantic similarity between the interfaces of “” and the interfaces of as follows:
We can define the reliability value of as follows:
3.3.3. The Third Production Rule
(The semantic similarity threshold k)
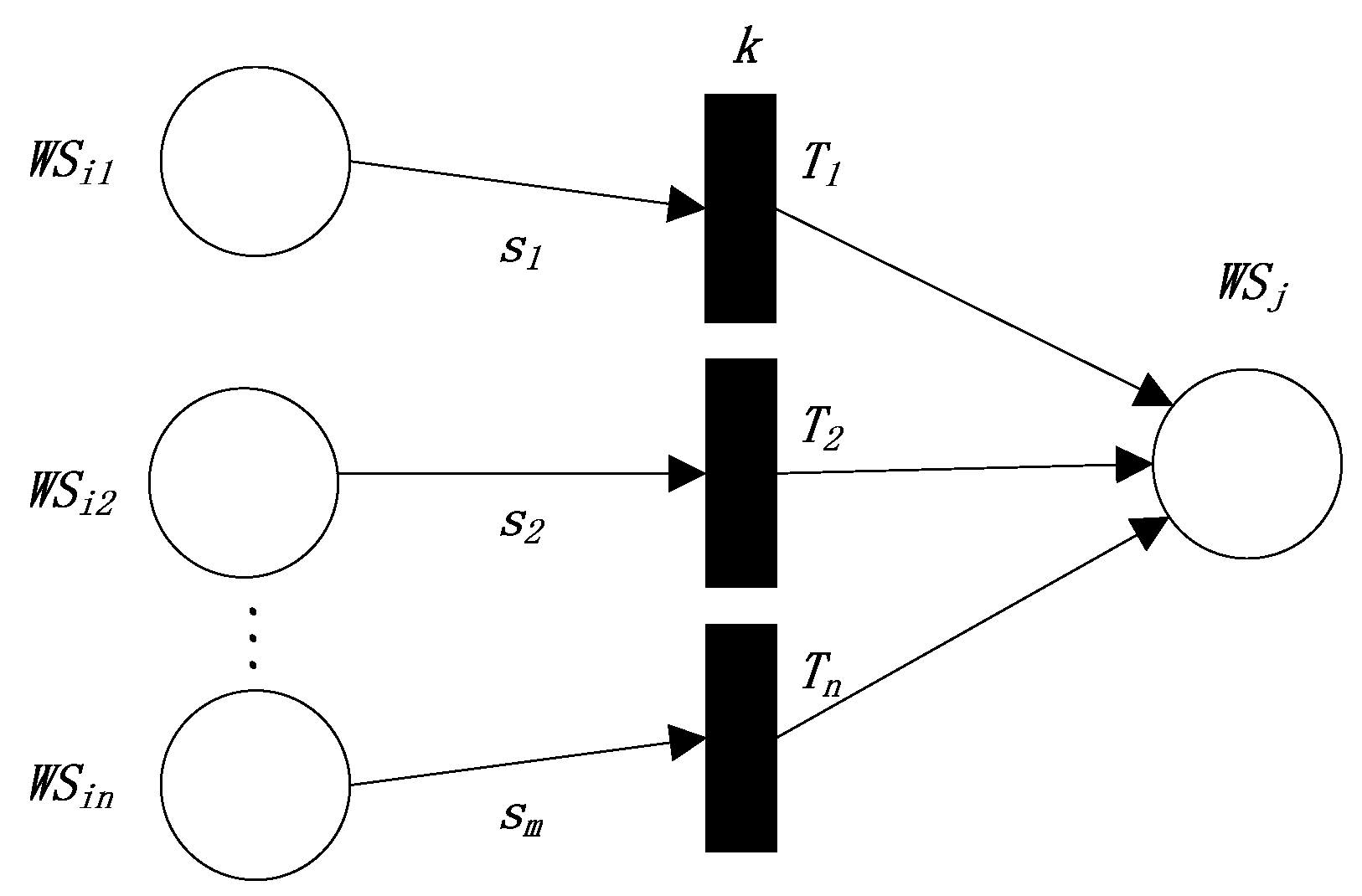
This production rule represents a dependence relation “” (the semantic similarity threshold k). The FRCPN based on semantic similarity for Web service compositions is shown in Figure 3.
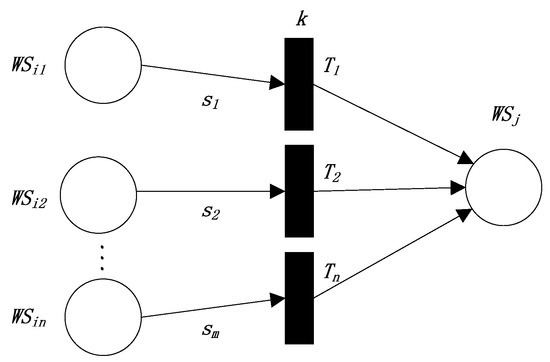
Figure 3.
The FRCPN expression of the third production rule.
“, , , ” are the values of the semantic similarity between the outputs of “,” respectively, and the inputs of . The above rule needs to satisfy some conditions, including , , all of the conditions in “”, and those in “”.
In Equation (7), represents the semantic similarity between the outputs of and the inputs of ; represents the semantic similarity between the outputs of and the inputs of , and so on. is the weight that represents the attention degree of matching between the outputs of and the inputs of ; is the weight that represents the attention degree of matching between the outputs of and the inputs of , and so on. is the weight that represents the attention degree of satisfying all the conditions in and ; is the weight that represents the attention degree of satisfying all the conditions in and , and so on.
According to the above definition, we define the reliability values “” of the transitions “” as the semantic similarities between the interfaces of “” respectively, and the interfaces of , as follows:
We can define the reliability of as follow,
3.3.4. The Fourth Production Rule
(The semantic similarity threshold k)
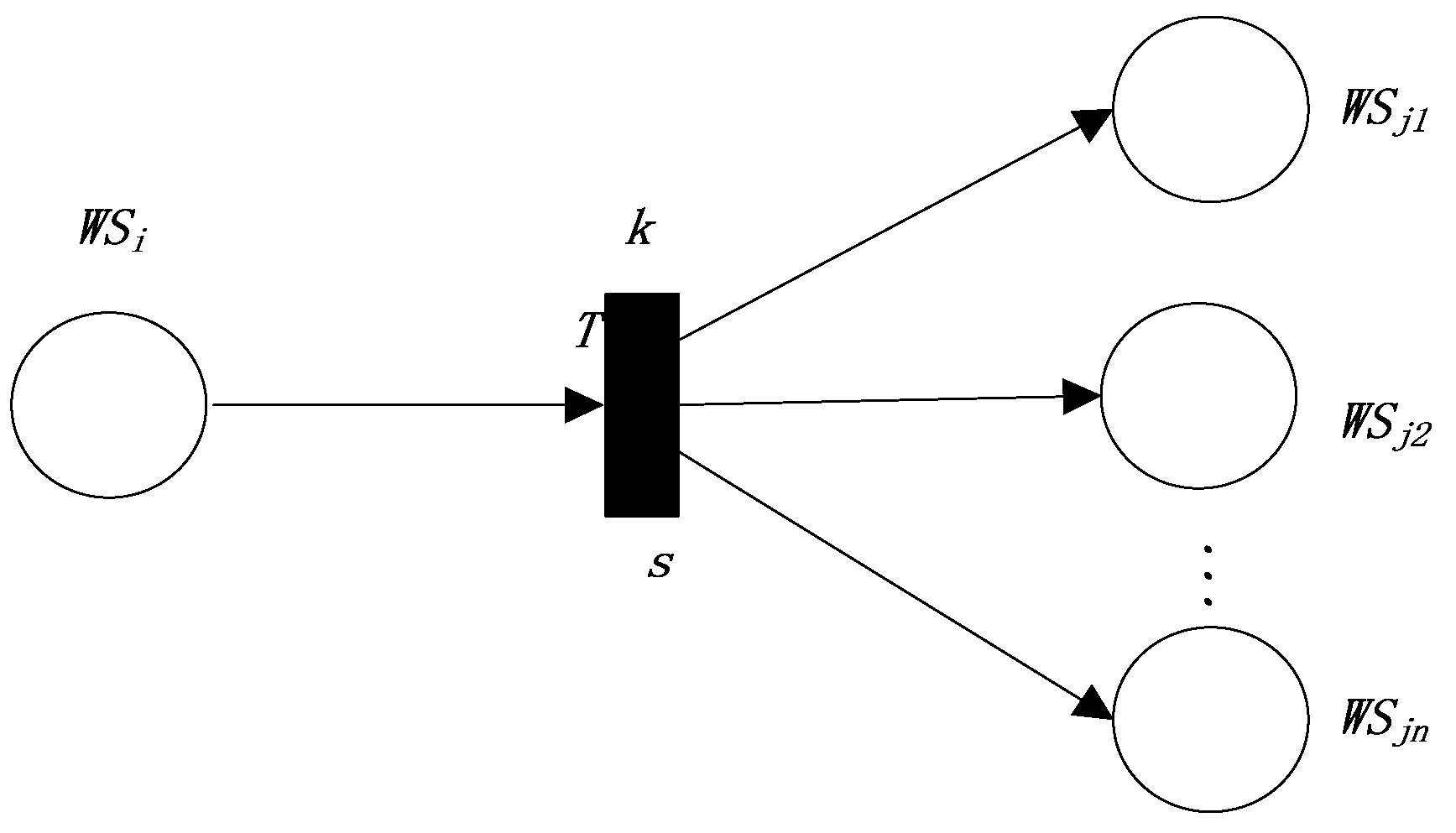
This fourth production rule represents a dependence relation “” (the semantic similarity threshold k). The FRCPN based on semantic similarity for Web service compositions is shown in Figure 4.
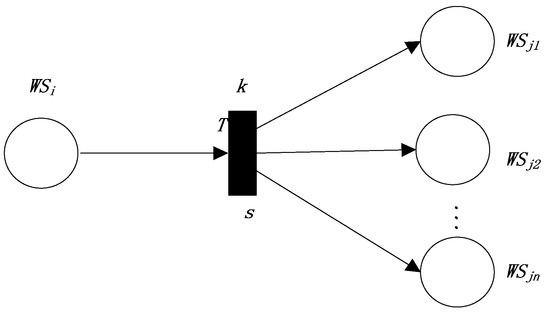
Figure 4.
The FRCPN expression of the fourth production rule.
s is the semantic similarity between the outputs of and (union of inputs of “”). The above rule needs to satisfy some conditions, including , , and all of the conditions in . Therefore,
In Equation (10), represents the semantic similarity between the outputs of and . is the weight that represents the attention degree of matching between the outputs of and . is the weight that represents the attention degree of matching meeting all the conditions in and .
According to the above definition, we define the reliability value of the transition in terms of the semantic similarity between the interfaces of and the interfaces of , as follows:
We can define the reliability values of “” in this dependence relation as follows:
3.3.5. The Fifth Production Rule
(The semantic similarity threshold k)
This fifth production rule represents a dependence relation “” (the semantic similarity threshold k). The FRCPN based on semantic similarity for Web service compositions is shown in Figure 5.
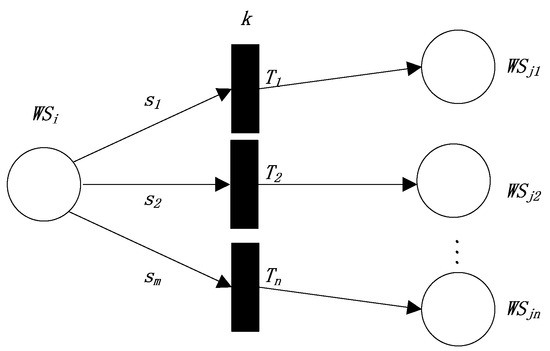
Figure 5.
The FRCPN expression of the fifth production rule.
, , , are the semantic similarity between the outputs of and the inputs of “,” respectively. The above rule needs to satisfy some conditions, including , , and all of the conditions in , . Therefore,
In Equation (13), represents the semantic similarity between the outputs of and the inputs of ; represents the semantic similarity between the outputs of and the inputs of , and so on. is the weight that represents the attention degree of matching between the outputs of and the inputs of ; is the weight that represents the attention degree of matching between the outputs of and the inputs of , and so on. is the weight that represents the attention degree of satisfying all the conditions in , in , is the weight that represents the attention degree of satisfying all the conditions in , in , and so on.
According to the above definition, we define the reliability values “” of the transitions “” to equal the semantic similarities between the interfaces of and the interfaces of “”, respectively, as follows:
We can further define the reliability values of . This production rule needs only one Web service , we can trigger “”, so,
The five kinds of production rule, above have some common points; the points can be summed up with some general rules:
- (1)
- In the first, fourth, and fifth production rules, the reliability value of the postpositional Web service of the transition equals the product of the reliability of the prepositional Web service of the transition and the reliability value of the transition.
- (2)
- In the second production rule, the reliability value of the postpositional Web service of the transition equals the minimum reliability value of all the prepositional Web services multiplied by the reliability value of the transition.
- (3)
- In the third production rule, the reliability value of the postpositional Web service of the transitions equals the maximum value of the reliability values of the respective prepositional Web services multiplied by the reliability values of the transitions.
In order to calculate the reliability of Web services and the reliability values of transitions, we make formal definitions of Web services and transitions in FRCPN.
Definition 8.
Formal definition of Web service in FRCPN.
- (1)
- WS, Web Service represents a Web service in FRCPN.
- (2)
- IRS, Immediate Reachability Set. For a current Web service WS, if there exists a transition t satisfying some conditions, including and , then we call the immediate reachability Web service of WS. All of the immediate reachability Web services of WS are called an immediate reachability set of WS, denoted as IRS.
- (3)
- PRTS, PRepositional Transition Set. For a current Web service WS, if there exists a transition t satisfying , we call t the prepositional transition of WS. All of the prepositional transitions of WS are called a prepositional transition set of WS, denoted as PRTS.
- (4)
- POTS, POstpositional Transition Set. For a current Web service WS, if there exists a transition t satisfying , we call t the postpositional transition of WS. All of the postpositional transitions of WS are called a postpositional transition set of WS, denoted as POTS.
- (5)
- PIRS, Prepositional Immediate Reachability Set. For a current Web service WS, if there exists a transition t satisfying some conditions, including and , we call the prepositional immediate reachability Web service of WS. All of the prepositional immediate reachability Web services of WS are called a prepositional immediate reachability Web service set, denoted as PIRS.
- (6)
- , the reliability value of the current Web service. Before calculating the reliability value of all Web services in the graph, we set the initial Web service’s reliability to 1, and the reliability value of other Web services to 0.
Definition 9.
Formal definition of transition in FRCPN.
- (1)
- T, Transition, represents a transition in FRCPN.
- (2)
- PRWSS, PRepositional Web Service Set. For a current transition t, if there exists a Web service WS satisfying , we call WS the prepositional Web service of t. All of the prepositional Web services of t are called the prepositional Web service set of t, denoted as PRWSS.
- (3)
- POWSS, POstpositional Web Service Set. For a current transition t, if there exists a Web service WS satisfying , we call WS s the postpositional Web Service of t. All of the postpositional Web Services of t are called the postpositional Web Service set of t, denoted as POWSS.
- (4)
- Type, the type of current transition. There are five types of transition. The first type of transition is shown in Figure 1, the second type of transition is shown in Figure 2, the third type of transition is shown in Figure 3, the fourth type of transition is shown in Figure 4, and the fifth type of transition is shown in Figure 5.
- (5)
- , the reliability value of the current transition.
4. Reliability Calculation Method for FRCPN
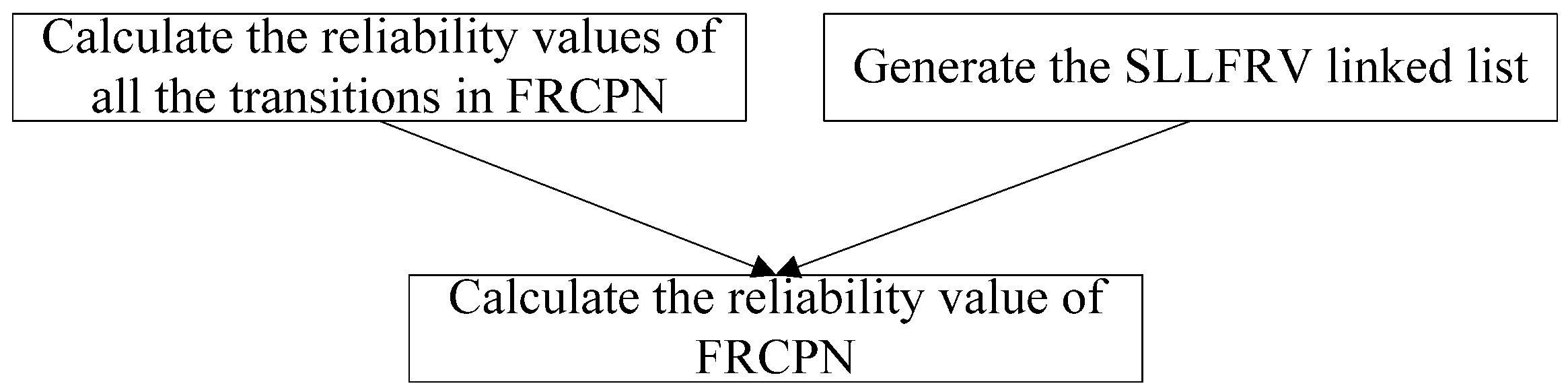
Here we propose a reliability calculation method for Web service compositions in FRCPN, as shown in Figure 6. Firstly, we calculated the reliability values of all the transitions in FRCPN, then we generated the SLLFRV linked list. Finally, according to the reliability values of all the transitions and the SLLFRV linked list, we calculated the reliability value of FRCPN.
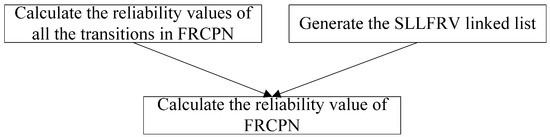
Figure 6.
The procedure of the reliability calculation method.
4.1. Reliability Calculation Algorithm for All the Transitions in FRCPN
The time complexity of Algorithm 1 is O(n). After getting the transition set of the graph, the algorithm uses a cycle “for” to set the reliability values of the transitions. The reliability values of the transitions are related to the type of transition. If the type of the current transition is the first type, the third type, or the fifth type, and the PRWSS of the current transition and the POWSS of the current transition have only a Web service, the reliability value of the current transition is . If the type of the current transition is the second type, then the PRWSS has many Web services, but the POWSS of the current transition only has a Web service, so the reliability value of the current transition is . If the type of the current transition is the fourth type, then the POWSS of the current transition has many Web services, but the PRWSS only has a Web service, so the reliability value of the current transition is .
| Algorithm 1 TSet fillTransitionValue(FRCPN frcpn) |
| Algorithm’s name: The reliability calculation algorithm for all the transitions in FRCPN |
| Input parameter: FRCPN graph frcpn |
| Output parameter: TSet, The transition set filled with reliability values in FRCPN |
| //Get the transition set of FRCPN graph frcpn |
| 1 TSet tSet = frcpn.getTransitionSet() |
| //Set successively the reliability values of all the transitions in frcpn using a loop |
| 2 for int k = 0 to |tSet| − 1 step 1 |
| 3 Transition t = tSet.get(k) |
| //Get the type of the transition |
| 4 int type = t.getType() |
| //Set the reliability value of the transition according to the type of the transition |
| //If the type of the transition is the first type, the third type or the fifth type |
| 5 if type = 1 or type = 3 or type = 5 then |
| //The PRWSS has only a Web service |
| 6 WS wsi = t.getPRWSS.get(0) |
| //The POWSS has only a Web service |
| 7 WS wsj = t.getPOWSS.get(0) |
| //Set the reliability value of the transition. In the expression, |
| 8 t.setReliablityValue() |
| 9 end if |
| //If the type of the transition is the second type |
| 10 if type = 2 then |
| //Get the PRWSS of current transition |
| 11 WSSet preWSS = t.getPRWSS() |
| //The POWSS has only a Web service |
| 12 WS wsj = t.getPOWSS.get(0) |
| //Set the reliability value of the transition. In the expression, |
| //|preWSS| = n |
| //The elements in preWSS are represented as preWSS1, preWSS2,…, preWSSn |
| 13 t.setReliablityValue() |
| 14 end if |
| // If the type of the transition is the fourth type |
| 15 if type = 4 then |
| //The PRWSS has only a Web service |
| 16 WS wsi = t.getPRWSS.get(0) |
| //Get the POWSS of current transition |
| 17 WSSet postWSS = t.getPOWSS () |
| // Set the reliability value of the transition. In the expression, |
| //|postWSS| = n |
| //The elements in postWSS are represented as postWSS1, postWSS2,…, postWSSn |
| 18 t.set Reliablity Value() |
| 19 end if |
| 20 end for |
| 21 return tSet |
4.2. Generation Algorithm for SLLFRV Linked List
We set the reliability value of the starting Web service in FRCPN as 1. The call to the Web service is always backward, and a FRCPN is a directed acyclic graph, so we can successively calculate the reliability values of the Web services in FRCPN according to the transitions. When we calculate the last Web service, the reliability value of the last Web service is used as the reliability value of FRCPN. There are the following problems when we set the reliability values of Web services.
- (1)
- If the reliability values of some Web services in the PIRS of current Web service are not set, this situation will lead to non-generation of the reliability value for the current Web service.
- (2)
- A transition has several possible postpositional Web Services, and different transitions may have the same postpositional Web Service, so we need to consider the situation for setting the reliability value of Web service many times.
Regarding the first problem, we propose a SLLFRV linked list. According to the sequence of transitions in SLLFRV, we can successively set the reliability values in the POWSS of the current transition. Certainly, this solves the first problem, because the reliability values in PIRS of the current transition have not been generated.
Regarding the second problem, we propose a reliability calculation algorithm for Web services in FRCPN. In the algorithm, we consider the situation for setting the reliability value of Web service many times. If we arrive at the current Web service from multiple different paths, we select a higher reliability value among multiple paths as the reliability value of the current Web service.
The data structure of SLLFRV is a simple Singly Linked List, denoted as LinkT. The algorithm for generating SLLFRV is given below.
Algorithm 2 uses the recursive idea. Each time, the algorithm performs a double cycle “for” and continues recursion, so the time complexity of the algorithm is O(n3).
| Algorithm 2 LinkT generateLinkT(FRCPN frcpn, Transition t, LinkT linkT) |
| Algorithm’s name: The generation algorithm for SLLFRV |
| Input parameters: FRCPN graph frcpn, current transition t, SLLFRV linked list linkT. When the algorithm is called first, we set the input parameter t is ∅, and set the input parameter linkT is ∅. |
| Output parameter: the SLLFRV linked list generated |
| //If t is ∅ and linkT is ∅, then it is the first time to call this algorithm |
| 1 if t is ∅ and linkT is ∅ then |
| 2 linkT = newLinkT() |
| //Get starting Web service of frcpn |
| 3 WS ws = frcpn.getStartWebService() |
| //Get the POTS of starting Web service |
| 4 TSet postTSet = ws.getPOTS() |
| 5 for int i = 0 to|postTSet| − 1 step 1 |
| 6 if i = 0 then |
| 7 linkT = postTSet.get(0) |
| 8 linkT.top = postTSet.get(0) |
| 9 linkT.last = postTSet.get(0) |
| 10 else |
| 11 linkT.last.next = postTSet.get(i) |
| 12 linkT.last = postTSet.get(i) |
| 13 end if |
| 14 end for |
| //Continue to iterative generate linkT |
| 15 for int i = 0 to|postTSet| − 1 step 1 |
| 16 generateLinkT(fcpn,postTSet.get(i),linkT) |
| 17 end for |
| 18 else //It is not first time to call generateLinkT() |
| // Generate linkT and return to the superior function |
| 19 if t is ∅ then |
| 20 return linkT |
| 21 end if |
| //Get the POWSS of the current transition |
| 22 WSSet wsSet = t.getPOWSS () |
| 23 for int i = 0 to |wsSet| − 1 step 1 |
| 24 WS ws = wsSet.get(i) |
| //Get the POTS of the current Web service |
| 25 TSet postTSet = ws.getPOTS() |
| //Get the PRTS of the current Web service |
| 26 TSet preTSet = ws.getPRTS() |
| //If PRTS of the current Web service is not in linkT |
| 27 if preTSet not in linkT then |
| 28 break |
| 29 end if |
| //If the current Web service does not have a postpositional transition |
| 30 if postTSet is ∅ then |
| 31 break |
| 32 end if |
| 33 for int j = 0 to |postTSet| − 1 step 1 |
| 34 Transition ct = postTSet.get(j) |
| //Get the union of POWSS of all the transitions in linkT |
| 35 WSSet linkTPreWSSet = |
| //Set the initial value of the judgment flag to false |
| /*The judgment flag indicates whether the PRWSS of the current transition is included in preWSSet*/ |
| 36 boolean flag = false |
| 37 WSSet tPreWSSet = ct.getPRWSS() |
| // If tPreWSSet is a subset of linkTPreWSSet, then set the flag to true |
| 38 if tPreWSSet in linkTPreWSSet then |
| 39 flag = true |
| 40 end if |
| /*If the current transition is not included in linkT, and the judgment flag is |
| true*/ |
| 41 if ct not in linkT and flag is true then |
| 42 linkT.last.next = ct |
| 43 linkT.last = ct |
| 44 end if |
| 45 end for |
| // Continue to iterative generate linkT |
| 46 for int i = 0 to |postTSet| − 1 step 1 |
| 47 generateLinkT(fcpn,postTSet.get(i),linkT) |
| 48 end for |
| 49 end for |
| 50 end if |
| 51 return linkT |
When the algorithm is first time to be called, t and linkT are ∅, so the algorithm creates a new linkT, and begins to inspect from the starting Web service of the graph. The algorithm puts the POTS of the starting Web service into linkT, and then continues the recursion.
If the algorithm is not first time to be called, then the algorithm must judge some things. If the current transition t is ∅, then it indicates that recursion is completed and the algorithm can return to the superior function. If the transition t is not empty, then the algorithm gets the POWSS of the current transition and uses a cycle “for” to inspect the elements in POWSS.
Next, the algorithm gets the POTS postTSet of the current Web service and the PRTS preTSet of the current Web service. If preTSet is not in linkT, it shows that the reliability values of the prepositional transitions of the current Web service and the reliability values of the postpositional transitions of the current Web service have not all been generated, so the algorithm does not continue to inspect the candidate transitions, and uses “break” to exit inspection. If the current Web service does not have an immediate postpositional transition, postTSet is empty and the algorithm does not continue to follow the transition in the future, so also uses “break” to exit inspection.
Next, the algorithm uses a cycle “for” to traverse the transitions in postTSet. In the ideas of the algorithm, if the transitions are already in linkT, then the reliability values of all the immediate postpositional web services of the transitions can be calculated. The algorithm first gets the union of POWSS of all the transitions in linkT, and then executes set operations. If the PRWSS of the current transition is a subset of linkTPreWSSet, then it indicates that the reliability values of all the immediate postpositional Web services of the current transition can be calculated. If the current transition is not in linkT, the algorithm puts the current transition into linkT and then continues recursion.
In summary, if the transition is in linkT, the reliability values of all the prepositional Web services of the transition can be calculated according to the order in linkT before the reliability values of the postpositional Web services of the transition are calculated. Therefore, the algorithm can confirm that the reliability values of the immediate postpositional Web services of the transition can be calculated.
4.3. Reliability Calculation Algorithm for All the Web Services in FRCPN
Algorithm 3 was used to calculate the reliability values of Web Services according to SLLFRV linkT in sequence. According to the content of the algorithm, the time complexity of the algorithm is O(n2).
| Algorithm 3 FRCPN fillWSValue(FRCPN frcpn, LinkT linkT) |
| Algorithm’s name: the reliability calculation algorithm for FRCPN frcpn |
| Input parameters: FRCPN graph frcpn, SLLFRV linked list linkT |
| Output parameter: FRCPN graph frcpn that the graph has generated the reliability values of Web services |
| //According to SLLFRV linkT, generate successively the reliability values of Web services |
| 1 for Transition t = linkT.top to t = null step t = t.next |
| //If the current transition is of the first, fourth, or fifth type |
| 2 if t.getType() = 1 or t.getType() = 4 or t.getType() = 5 then |
| /*Get the reliability value of the prepositional Web service of the current transition*/ |
| 3 float trustValue = t.getPRWSS().get(0).getTrustValue() × t.getTrustValue() |
| //Get the POWSS of the transition t |
| 4 WSSet postWSSet = t. |
| //Set the reliability values of the Web services in POWSS of transition t |
| 5 for int i = 0 to |postWSSet| − 1 step 1 |
| 6 WS ws = postWSSet.get(i) |
| 7 ws.setTrustValue( Max{ ws.getTrustValue, trustValue} ) |
| 8 end for |
| 9 end if |
| //If the current transition is of the second type |
| 10 if t.getType() = 2 then |
| //Get the PRWSS of the current transition |
| 11 WSSet preWSSet = t.getPRWSS() |
| /*The reliability value of the postpositional Web service of the transition equals the minimum value of reliability values of all the prepositional Web services of the transition*/ |
| //|preWSSet| = |
| 12 float trustValue = Min( preWSSet.get(0).getTrustValue(), |
| preWSSet.get(1).getTrustValue(), …,preWSSet.get(n).getTrustValue()) |
| ×t.getTrustValue() |
| //The POWSS of the current transition has only one Web service |
| 13 WS ws = t.getPOWSS.get(0) |
| 14 ws.setTrustValue( Max{ ws.getTrustValue, trustValue} ); |
| 15 end if |
| // If the current transition is of the third type |
| 16 if t.getType() = 3 then |
| //The POWSS of the current transition only has one Web service |
| 17 WS ws = t.getPOWSS().get(0) |
| //Get the PRTS of the current transition |
| 18 TSet tSet = ws.getPRTS() |
| //Get the reliability value of ws, |tSet| = n |
| 19 float trustValue = Max( |
| tSet.get(0).getPRWSS().get(0).getTrustValue()×tSet.get(0).getTrustVale(), |
| tSet.get(1).getPRWSS().get(0).getTrustValue()×tSet.get(1).getTrustVale(), |
| …, |
| tSet.get(n).getPRWSS().get(0).getTrustValue()×tSet.get(n).getTrustVale()); |
| 20 ws.setTrustValue( Max{ ws.getTrustValue, trustValue} ); |
| 21 end if |
| 22 end for |
| 23 return frcpn |
The algorithm traverses the transitions in SLLFRV linkT, in order to calculate the reliability values of the direct subsequent Web services of the transitions in SLLFRV linkT according to the type of transition. If the current transition t is of the first, fourth, or fifth type, it only has one immediate prepositional Web service, and the reliability values of immediate postpositional Web services are t.getPRWSS().get(0).getTrustValue()×t.getTrustValue(). In order to prevent conflict between the reliability values of multiple transitions, the algorithm executes the operation “Max”, so as to always get the highest reliability value as the final reliability value of a Web service.
If the current transition t is of the second type, the current transition has multiple immediate prepositional Web services, so the algorithm must take the minimum reliability value of the immediate prepositional Web services as the basis for calculating the reliability values of the postpositional Web services of the current transition. The calculation formula is Min(preWSSet.get(0).getTrustValue(),preWSSet.get(1).getTrustValue(),…,preWSSet.get(n).getTrustValue())×t.getTrustValue().
If the current transition t is of the third type, the current transition has only one immediate postpositional Web service, so the algorithm must take the operation “Max” after the reliability values of the immediate prepositional Web Services and the reliability value of the current transition are multiplied. The algorithm can obtain the reliability value of the immediate postpositional Web service. The calculation formula is
Max(tSet.get(0).getPRWSS().get(0).getTrustValue() × tSet.get(0).getTrustValue(),_
tSet.get(1).getPRWSS().get(0).getTrustValue() × tSet.get(1).getTrustValue(),…,_
tSet.get(n).getPRWSS().get(0).getTrustValue() × tSet.get(n).getTrustValue(),).
5. An Example of the Application of the Method
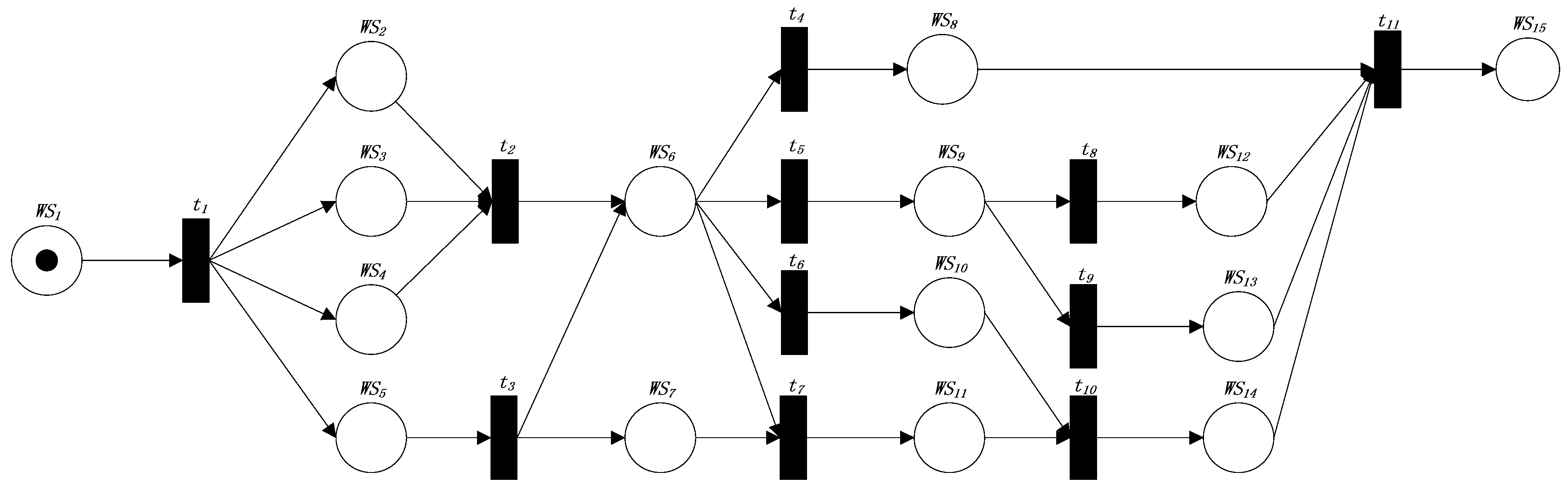
Assume that we have generated a service composition expressed by FRCPN for the calculation process for CAE simulation in SCP prototype, as shown in Figure 7. According to the reliability calculation method, we will calculate the reliability value of the FRCPN.
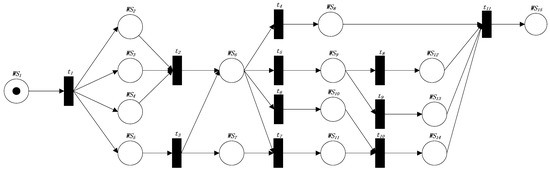
Figure 7.
The FRCPN generated.
We get all kinds of parameters of Web services, as shown in Table 1. The reliability value ReliabilityValue is required for the calculation, so we use the method in this paper to calculate the reliability value.

Table 1.
The parameters of Web services in FRCPN (Fuzzy Reasoning Colored Petri Net).
Firstly, we use Algorithm 1 to get the reliability values of the transitions in the FRCPN. We use frcpn.getTransitionSet() to get the transition sequence, which is {t4,t7,t5,t6,t8,t11,t9,t10,t3,t2,t1}. We set the semantic similarity threshold k = 0.8, m1 = 0.8, and m2 = 0.2 in all the formulas. All of the conditions in P, Q are satisfied. All the transitions in the FRCPN are shown in Table 2.

Table 2.
The parameters of the transitions in the FRCPN.
According to the sequence {t4,t7,t5,t6,t8,t11,t9,t10,t3,t2,t1} and Algorithm 1, we calculate the reliability values of the transitions. Let us start with a look at the calculation of t4’s reliability value. We know from Table 2 that t4 is of the fifth type. According to Algorithm 1, wsi and wsj are WS6 and WS8, respectively, and we can calculate the reliability value of t4 as follows:
According to Algorithm 1, we can calculate the reliability value of each transition in order as follows:
We continue to use Algorithm 2 to generate the SLLFRV linked list. When the algorithm is first time to be called, we can use generateLinkT(frcpn,). Therefore, we get , and the algorithm puts in the to SLLFRV linked list linkT. Next, the algorithm calls recursively generateLinkT(frcpn,).
When the algorithm is called by generateLinkT(frcpn,), we get . Next, according to the cycle “for” to wsSet in the algorithm, we get , , and know that the value of “pretest not in linkT” is false. In the cycle “for” to postTSet in the algorithm, we can get and the following results:
According to the above analysis, tPreWSSet is a subset of linkTPreWSSet, the value of flag is true. “ct not in linkT” indicates that the current transition is not in linkT, and the value of flag is true, so the algorithm puts into the tail of linkT.
Next, the algorithm is called recursively generateLinkT(frcpn,). Through continuous recursive calls, the algorithm produces the SLLFRV linkT as follows:
According to the sequence in the SLLFRV linkT, we use Algorithm 3 to get the reliability values of all the Web services as follows:
The last Web service is in the FRCPN graph, so the reliability of the FRCPN graph is the reliability value of . The reliability value of the FRCPN graph is 0.717.
6. Simulated Experiments
In order to analyze the effect of the method proposed in this paper, we used the SCP prototype to conduct simulated experiments. Due to the uncertainty of the Web services, under the premise of the validity of experiment, we made the following settings for the experimental conditions and related parameters.
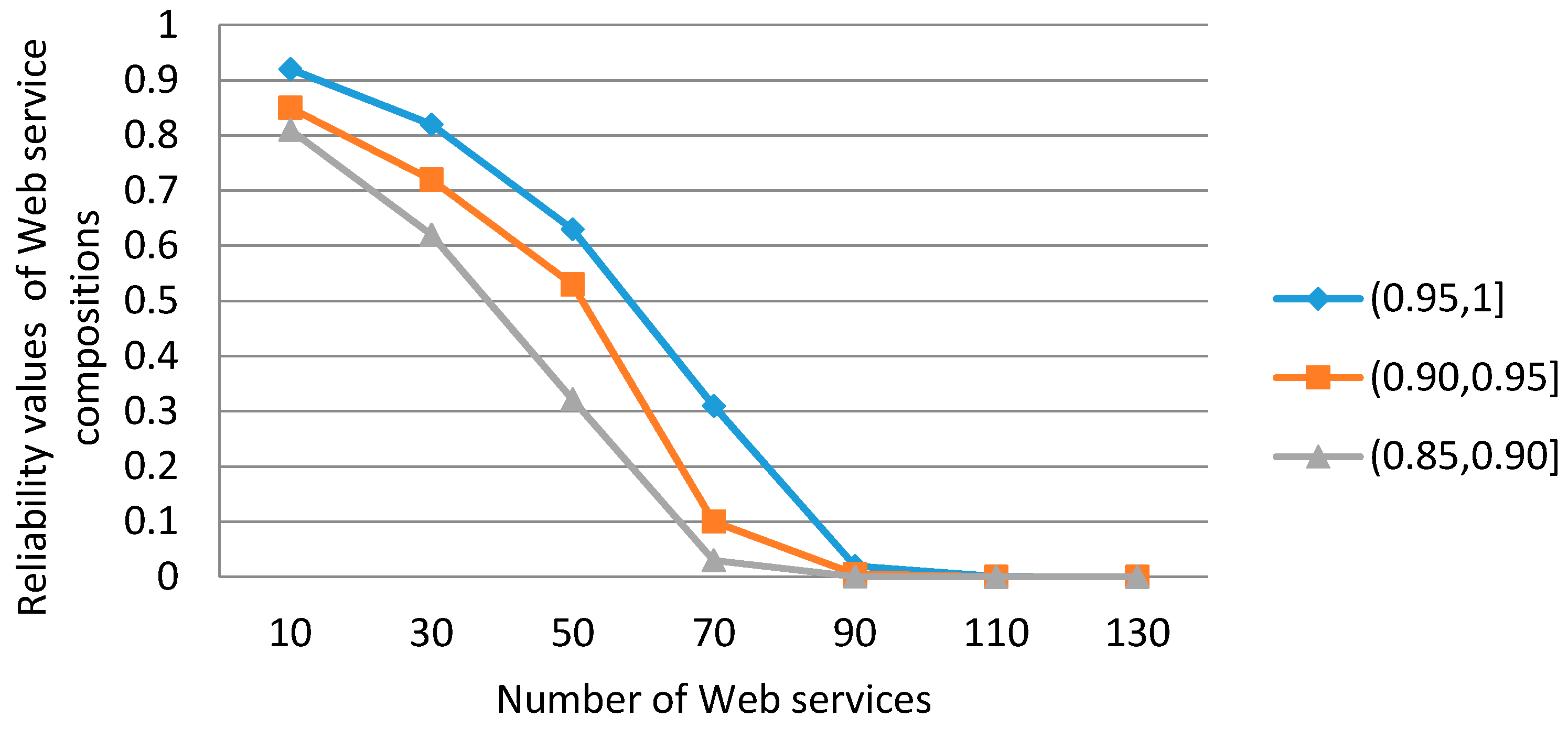
We used seven FRCPN graphs to simulate the Web service compositions; the number of Web services in the FRCPN graphs is 10, 30, 50, 70, 90, 110, and 130, respectively. We used five kinds of production rules to represent FRCPN, but kept the ratio between Web services and transitions is 1:5, so the length of SLLFRV is respectively 2, 6, 10, 14, 18, 22. The similarity threshold of all the transitions is set to the same value. After Algorithm 1 is finished, we assumed that the reliability values of transitions are divided into three ranges, i.e., . According to the three ranges, we can get three sets of data; the similarity thresholds of the three sets are 0.95, 0.90, and 0.85, respectively.
The purpose of the experiment was to simulate the reliability values of FRCPN in different reliability ranges of transitions. The reliability values of Web service compositions were unlimited. The experimental results are shown in Figure 8. In the figure, the horizontal axis represents the number of Web services in FRCPN; the vertical axis represents the reliability values of Web service compositions.
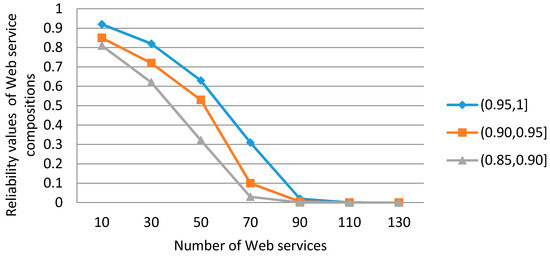
Figure 8.
The results of the simulated experiment.
According to Figure 8, we can know the relationships among the reliability values of Web service compositions, the number of Web services, and the reliability ranges of transitions. The following relationships can be obtained:
- (1)
- Under the same reliability range of transitions, if the number of Web services is greater, then the length of SLLFRV is longer and the reliability values of the Web service compositions are smaller.
- (2)
- Under different reliability ranges of transitions, if the minimum range is smaller, then as the number of Web services increases, the reliability values of the service compositions decrease more rapidly.
- (3)
- We should proper control the scale of Web services in FRCPN. For example, if we set the reliability threshold of Web service compositions as 0.6, then in the reliability range (0.95, 1.0] of transitions, the number of Web services should be controlled below 30 and the length of SLLFRV is below 6.
7. Application in SCP
The SCP prototype uses Eclipse as a development tool, Java as a development language, OWL-S as a Web service description language, Tuscany as the Web services’ container, WSDL2OWLS as conversion tool, and OWL-S API as an interface tool.
The Web services in the SCP prototype are implemented by POJO Java class, and we use Web Service Description Language (WSDL) to describe the Web services. The software of the SCP prototype generates semantic Web service descriptions after filling QoS content according to WSDL, and then gets OWL documents.
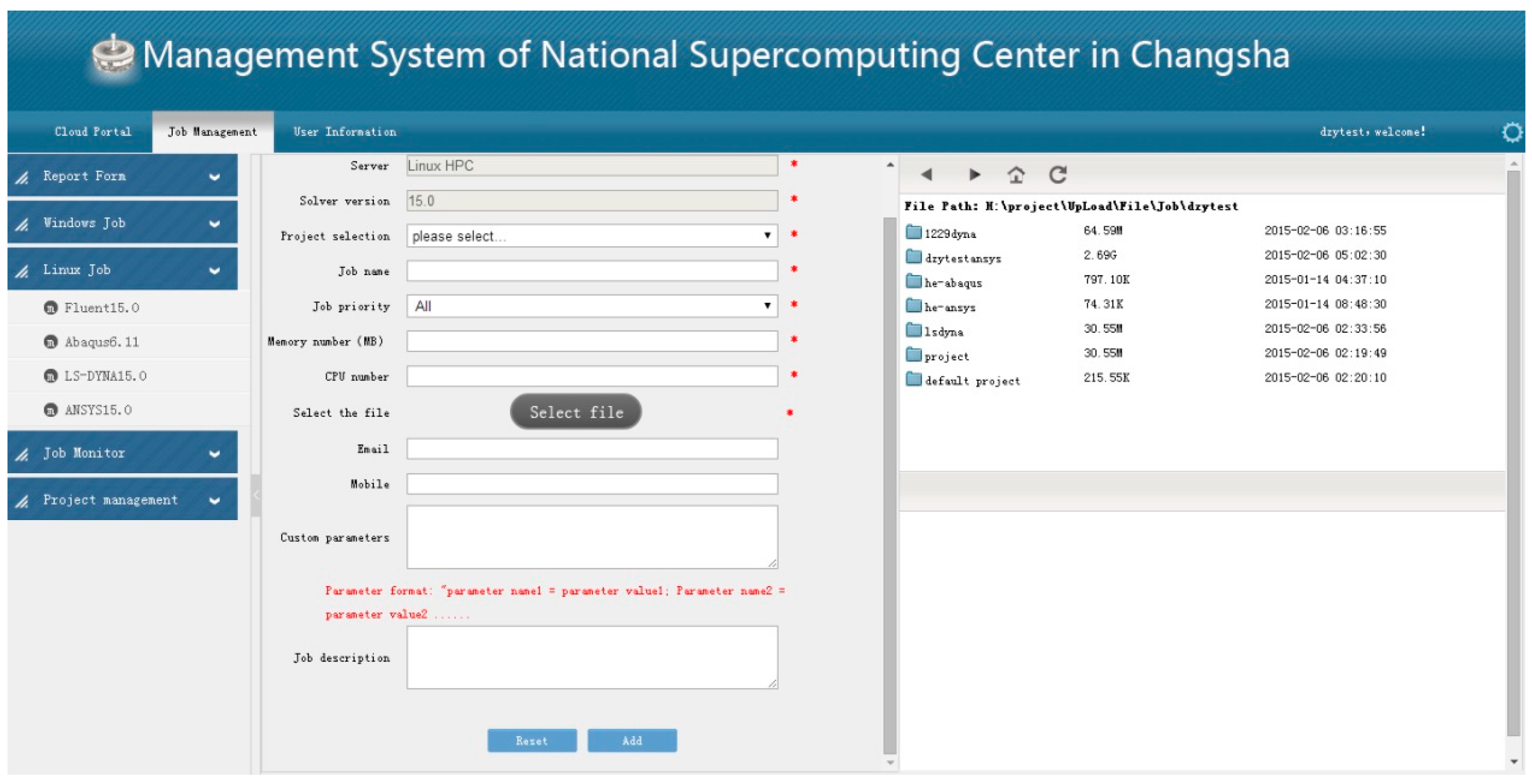
The users of the SCP prototype submit their computing requirements for CAE simulation through the Web system, as shown in Figure 9. After the SCP prototype receives the user’s request, the SCP prototype generates the request ontology, and then generates FRCPN. Therefore, we used the method in this paper to calculate the reliability value, then screen and get the best FRCPN.
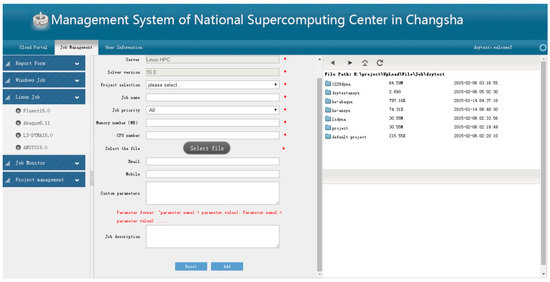
Figure 9.
The interface for submitting a job in the SCP (Supercomputing Cloud Platform) prototype.
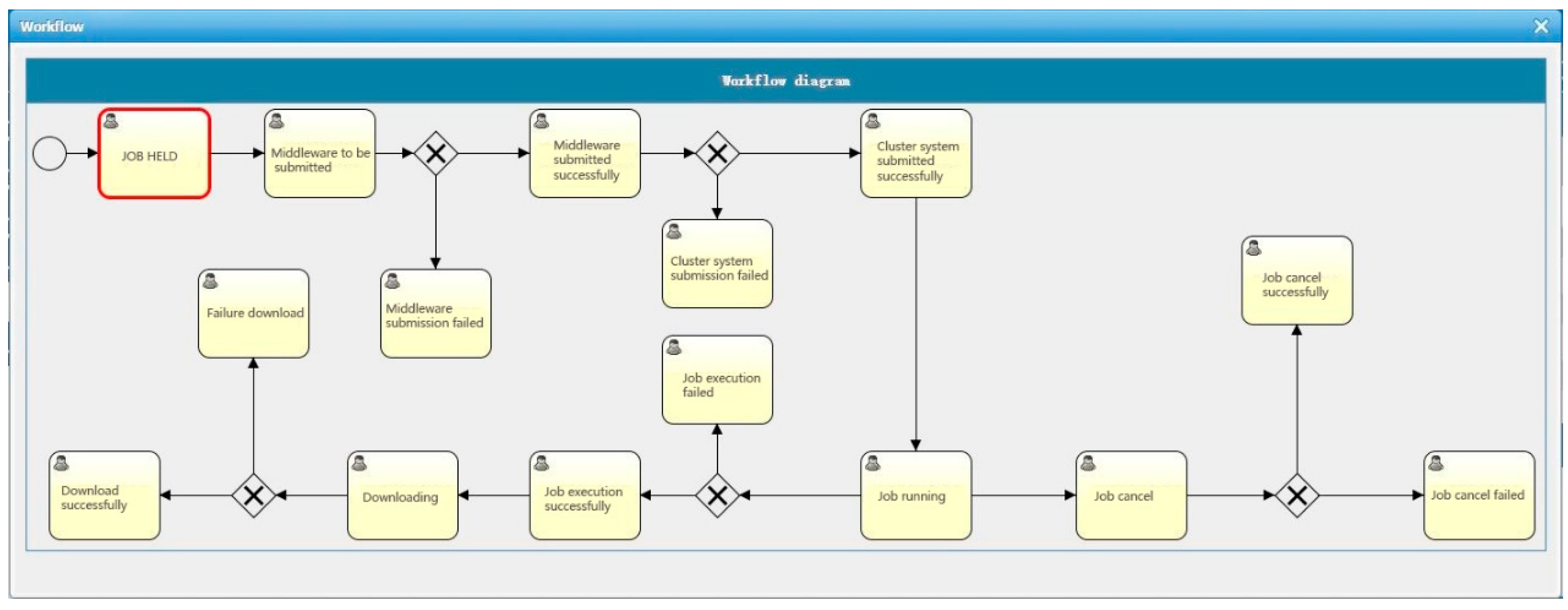
After the SCP prototype generates FRCPN graphs for CAE simulation, many FRCPN graphs are selected. The SCP prototype then calculates the reliability value of FRCPN graphs. We set k = 0.95, a = 0.9, and the number of Web services as not more than 30. We chose the highest reliability of FRCPN as the final business flow chart. Then we used Activiti to implement FRCPN. An example Activiti workflow for a computing job is shown in Figure 10.
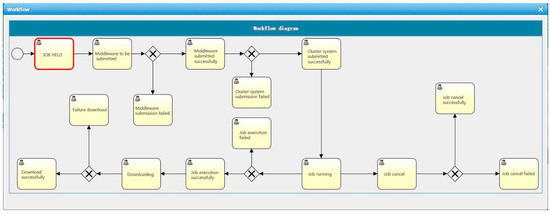
Figure 10.
An example Activiti workflow for a computing job in the SCP prototype.
8. Conclusions and Further Work
When we use SOA architecture to develop an SCP prototype, we need to verify FRCPN after the prototype automatically generates FRCPN, and calculate the reliability value of FRCPN for further screening. We proposed a series of definitions, including semantic threshold similarity for Web services, formal definition of transition in FRCPN, etc. We proposed a reliability calculation method for Web service compositions using FRCPN. Firstly, the method calculates the reliability values of all the transitions in FRCPN. Then, the method generates the SLLFRV linked list. Finally, according to the reliability values of all the transitions and SLLFRV linked list, the method calculates the reliability value of FRCPN.
The experiment shows that the reliability values of Web service compositions have some regularity with the number of Web services and the reliability range of transitions. If the FRCPN scale is larger and the minimum value of the reliability range of transitions is smaller, then the reliability value of FRCPN is smaller, so we need to proper control the scale of Web services in FRCPN, and improve the reliability of a single transition. Next, we can carry out further research in the following areas:
- (1)
- Study the transaction model of Web service compositions and the exception recovery mechanism of Web service compositions, to facilitate the fallback handling for the jobs in the SCP prototype.
- (2)
- Carry out research into the structural verification algorithm of FRCPN to verify the validity of the structure.
- (3)
- Create a comprehensive summary of existing research works to form the theory and application system behind service compositions in the cloud platform, including modeling, searching, matching, automatic composition, validation, transaction handling, exception handling, etc.
Acknowledgments
This work was supported by the National Natural Science Foundation of China (61174140, 61472127, 61272395); National Key Technology Support Program of China Grant No.2012BAH09B02.
Author Contributions
Ziyun Deng put forward the ideas of research work and algorithm design; Lei Chen and Tingqing He performed the experiments; Tao Meng analyzed the data; Lei Chen and Tingqing He contributed tools; Ziyun Deng and Tingqing He wrote the paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Li, B.; Chai, X.; Zhang, L.; Hou, B.; Lin, T.Y.; Yang, C.; Xiao, Y.; Xing, C.; Zhang, Z.; Zhang, Y.; et al. New advances of the research on cloud simulation. In Advanced Methods, Techniques, and Applications in Modeling and Simulation; Springer: New York, NY, USA, 2014; Volume 4, pp. 1597–1606. [Google Scholar]
- Juan, Y.; Gang, G. Design a new manufacturing model: Cloud manufacturing. In Proceedings of the 2012 International Conference on Cybernetics and Informatics; Springer: New York, NY, USA, 2014; Volume 14, pp. 1597–1606. [Google Scholar]
- Zhang, L.; Luo, Y.; Tao, F.; Li, B.; Ren, L.; Zhang, X.; Guo, H.; Cheng, Y.; Hu, A.; Liu, Y. Cloud manufacturing: A new manufacturing paradigm. Enterp. Inf. Syst. 2014, 8, 167–187. [Google Scholar] [CrossRef]
- Ren, L.; Zhang, L.; Tao, F.; Zhao, C.; Chai, X.; Zhao, X. Cloud manufacturing: From concept to practice. Enterp. Inf. Syst. 2015, 9, 186–209. [Google Scholar] [CrossRef]
- Lu, Y.; Xu, X.; Xu, J. Development of a hybrid manufacturing cloud. J. Manuf. Syst. 2014, 33, 551–566. [Google Scholar] [CrossRef]
- Cho, S.-H. CAE services on cloud computing platform in South Korea. In AsiaSim 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 440–446. [Google Scholar]
- Yu, J.; Cha, J.; Lu, Y.; Xu, W.; Sobolewski, M. A CAE-integrated distributed collaborative design system for finite element analysis of complex product based on SOOA. Adv. Eng. Softw. 2010, 41, 590–603. [Google Scholar] [CrossRef]
- Wahab, O.A.; Bentahar, J.; Otrok, H.; Mourad, A. Towards trustworthy multi-cloud services communities: A trust-based hedonic coalitional game. IEEE Trans. Serv. Comput. 2016. [Google Scholar] [CrossRef]
- Lee, S.; Kim, H.-G.; Jung, H.; Lee, M.; Song, S.; You, B.-J. OntoPipeliner: An ontology-based automatic semantic service pipeline generator. Expert Syst. Appl. 2011, 38, 9472–9482. [Google Scholar] [CrossRef]
- Angelo, F.; Eugenio, Z. Context-aware composition of semantic web services. Mob. Netw. Appl. 2014, 19, 235–248. [Google Scholar]
- Lin, S. Research on Semantic Similarity Computation and Applications. Ph.D. Thesis, Shangdong University, Shangdong, China, October 2009. [Google Scholar]
- Xia, Y.; Liu, Y.; Liu, J.; Zhu, Q. Modeling and performance evaluation of BPEL processes: A stochastic-petri-net-based approach. IEEE Trans. Syst. Man Cybern. Part A Syst. Hum. 2012, 42, 503–510. [Google Scholar] [CrossRef]
- Du, Y.; Li, X.; Xiong, P. A petri net approach to mediation-aided composition of web services. IEEE Trans. Autom. Sci. Eng. 2012, 9, 429–435. [Google Scholar] [CrossRef]
- Du, Y.; Tan, W.; Zhou, M. Timed compatibility analysis of web service composition: A modular approach based on petri nets. IEEE Trans. Autom. Sci. Eng. 2014, 11, 594–606. [Google Scholar] [CrossRef]
- Yu, W.; Yan, C.; Ding, Z.; Jiang, C.; Zhou, M. Modeling and validating e-commerce business process based on petri nets. IEEE Trans. Syst. Man Cybern. Syst. 2014, 44, 327–341. [Google Scholar] [CrossRef]
- Xia, Y.; Luo, X.; Li, J.; Zhu, Q. A petri-net-based approach to reliability determination of ontology-based service compositions. IEEE Trans. Syst. Man Cybern. Syst. 2013, 43, 1240–1247. [Google Scholar]
- Feng, L.; Masanao, O.; Takashi, K.; Kobayashi, K. A learning fuzzy petri net model. IEEE Trans. Electr. Electron. Eng. 2012, 7, 274–282. [Google Scholar] [CrossRef]
- Chen, L.; Zhang, G. A petri net approach to reliable execution for web service composition. In Proceedings of the 2013 9th International Conference on Computational Intelligence and Security (CIS), Sichuan, China, 14–15 December 2013; pp. 105–109.
- Nematzadeh, H.; Motameni, H.; Mohamad, R.; Nematzadeh, Z. QoS Measurement of workflow-based web service compositions using colored petri net. Sci. World J. 2014, 2014, 1–15. [Google Scholar] [CrossRef] [PubMed]
- Vidal, J.C.; Lama, M.; Bugarín, A. Toward the use of petri nets for the formalization of OWL-S choreographies. Knowl. Inf. Syst. 2012, 32, 629–665. [Google Scholar] [CrossRef]
- Zhu, L.; Sun, L. Hierarchical colored petri nets based modeling and analyzing for web service composition. Key Eng. Mater. 2011, 467, 1206–1211. [Google Scholar] [CrossRef]
- Li, B.; Ji, S.; Qiu, D.; Cai, J. Generating test cases of composite services based on owl-s and eh-cpn. Int. J. Softw. Eng. Knowl. Eng. 2010, 20, 921–941. [Google Scholar] [CrossRef]
- Xia, Y.; Zhang, X.; Luo, X.; Zhu, Q. Modelling of ontology-based service compositions using petri net. Elektron. Elektrotech. 2013, 19, 75–78. [Google Scholar] [CrossRef]
- Xia, Y.; Wan, N.; Dai, G.; Luo, X.; Sun, T. A non-markovian stochastic petri net-based approach to performance evaluation of ontology-based service composition. Concurr. Comput. Pract. Exp. 2012, 24, 2255–2267. [Google Scholar] [CrossRef]
- Wahab, O.A.; Bentahar, J.; Otrok, H.; Mourad, A. A survey on trust and reputation models for Web services: Single, composite, and communities. Decis. Support Syst. 2015, 74, 121–134. [Google Scholar] [CrossRef]
- Hang, C.-W.; Kalia, A.K.; Singh, M.P. Behind the curtain: Service selection via trust in composite services. In Proceedings of the 2012 IEEE 19th International Conference on Web Services (ICWS), Honolulu, HI, USA, 24–29 June 2012; pp. 9–16.
- Stantchev, V. Effects of Replication on Web Service Performance in WebSphere; International Computer Science Institute: Berkeley, CA, USA, 2008. [Google Scholar]
- Stantchev, V.; Malek, M. Translucent replication for service level assurance. In High Assurance Services Computing; Springer: New York, NY, USA, 2009; pp. 1–18. [Google Scholar]
- Werner, M.; Richling, J.; Milanovic, N.; Stantchev, V. Composability concept for dependable embedded systems. In Proceedings of the International Workshop on Dependable Embedded Systems at the 22nd Symposium on Reliable Distributed Systems (SRDS 2003), Florence, Italy, 5 October 2003; pp. 20–25.
- Haddad, J.E.I.; Manouvrier, M.; Rukoz, M. TQoS: Transactional and QoS-aware selection algorithm for automatic web service composition. IEEE Trans. Serv. Comput. 2010, 3, 73–85. [Google Scholar] [CrossRef]
- Fan, G.; Yu, H.; Chen, L.; Liu, D. Petri net based techniques for constructing reliable service composition. J. Syst. Softw. 2013, 86, 1089–1106. [Google Scholar] [CrossRef]
- Kim, Y.; Choi, J.-S.; Shin, Y. Trustworthy service discovery for dynamic web service composition. KSII Trans. Internet Inf. Syst. 2015, 9, 1260–1281. [Google Scholar]
- Silic, M.; Delac, G.; Srbljic, S. Prediction of atomic web services reliability for QoS-aware recommendation. IEEE Trans. Serv. Comput. 2015, 8, 425–438. [Google Scholar] [CrossRef]
- Xu, J.; Yao, S. Reliability of SOA systems using SPN and GA. In Proceedings of the IEEE 10th World Congress on Services, Anchorage, AK, USA, 27 June–2 July 2014; pp. 370–377.
- Garg, H. Reliability analysis of repairable systems using petri nets and vague Lambda—Tau methodology. ISA Trans. 2013, 52, 6–18. [Google Scholar] [CrossRef] [PubMed]
- Gan, M.; Wang, S.; Zhou, M.; Li, J.; Li, Y. A survey of reachability trees of unbounded petri nets. Acta Autom. Sin. 2015, 41, 686–693. [Google Scholar]
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).