An Adaptive Back-Off Mechanism for Wireless Sensor Networks
Abstract
:1. Introduction
2. Review of Related Work
2.1. Critical Technologies of S-MAC Protocol
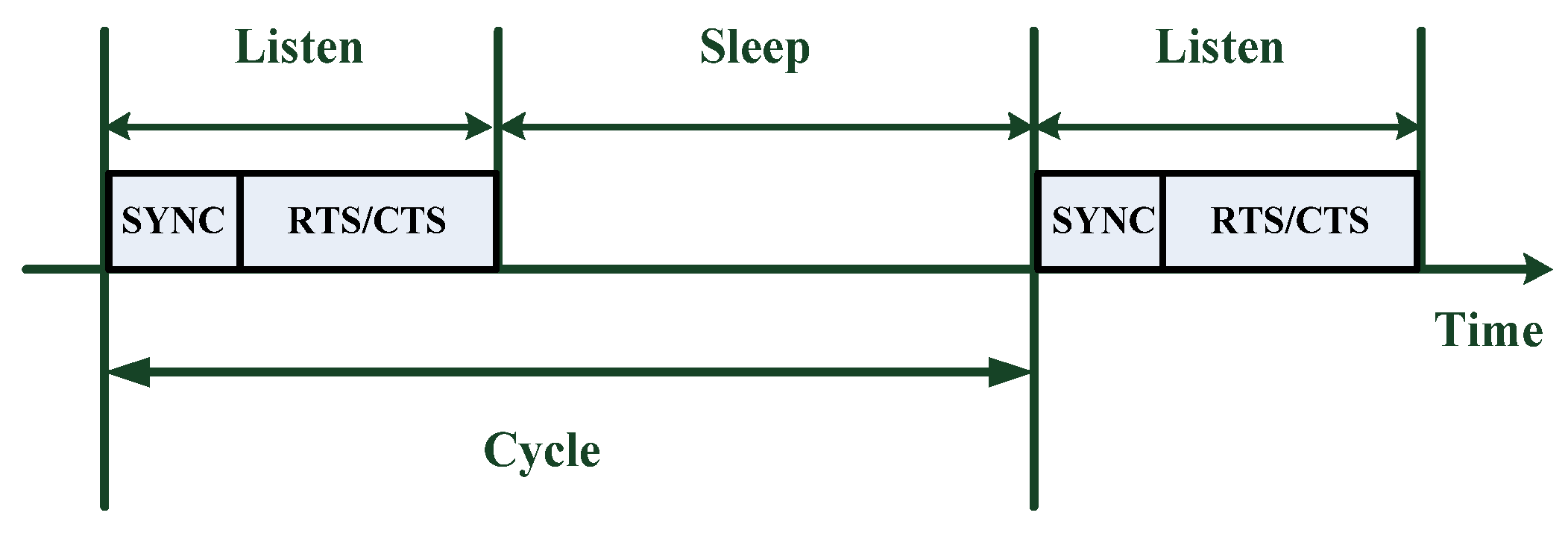
2.1.1. Periodic Listen and Sleep
2.1.2. Collision and Overhearing Avoidance
2.1.3. Message Passing
2.2. Modified Back-Off Mechanisms
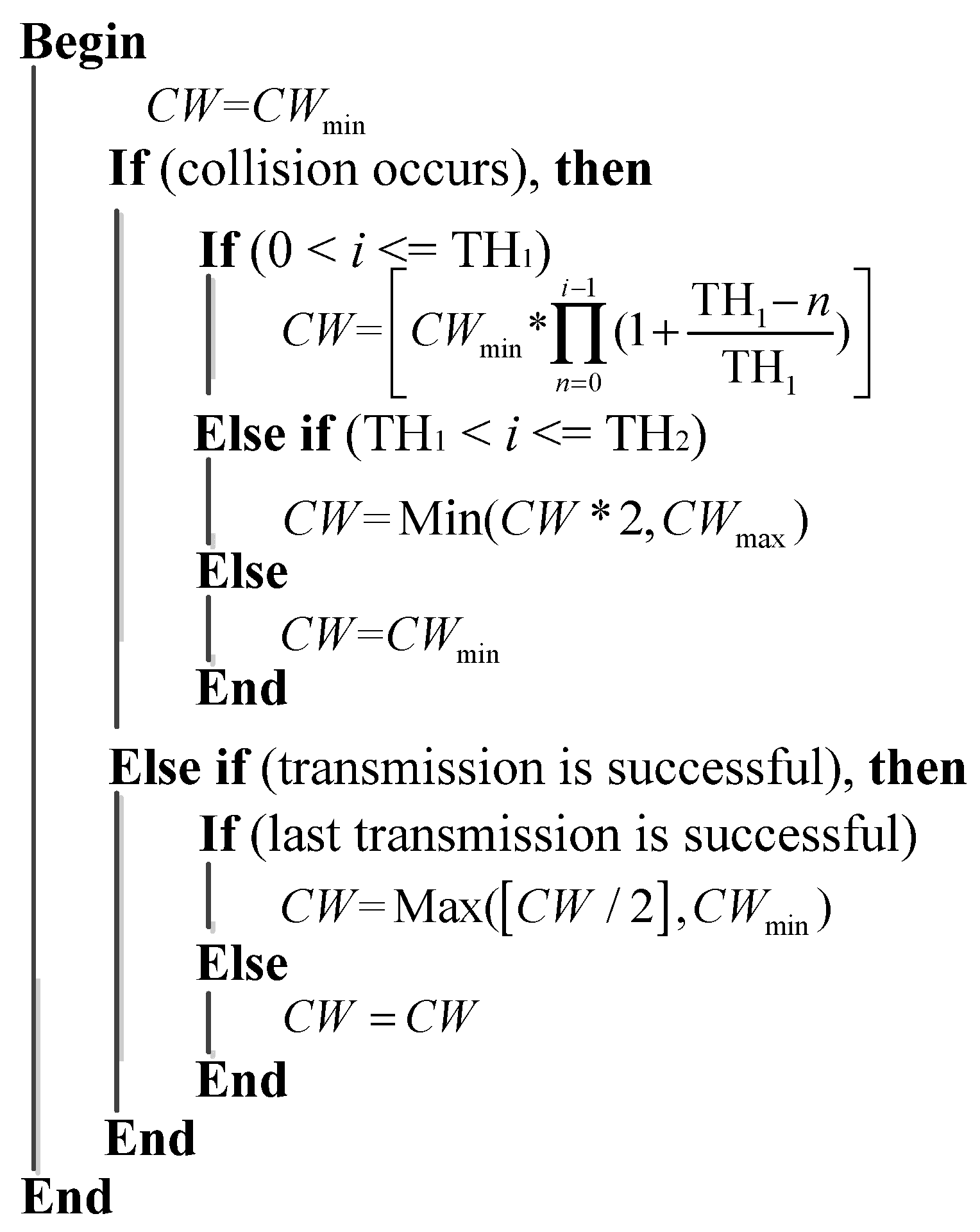
3. Proposed Back-Off Scheme
4. Simulation and Analysis
4.1. Network Topology
4.2. Parameter Setting
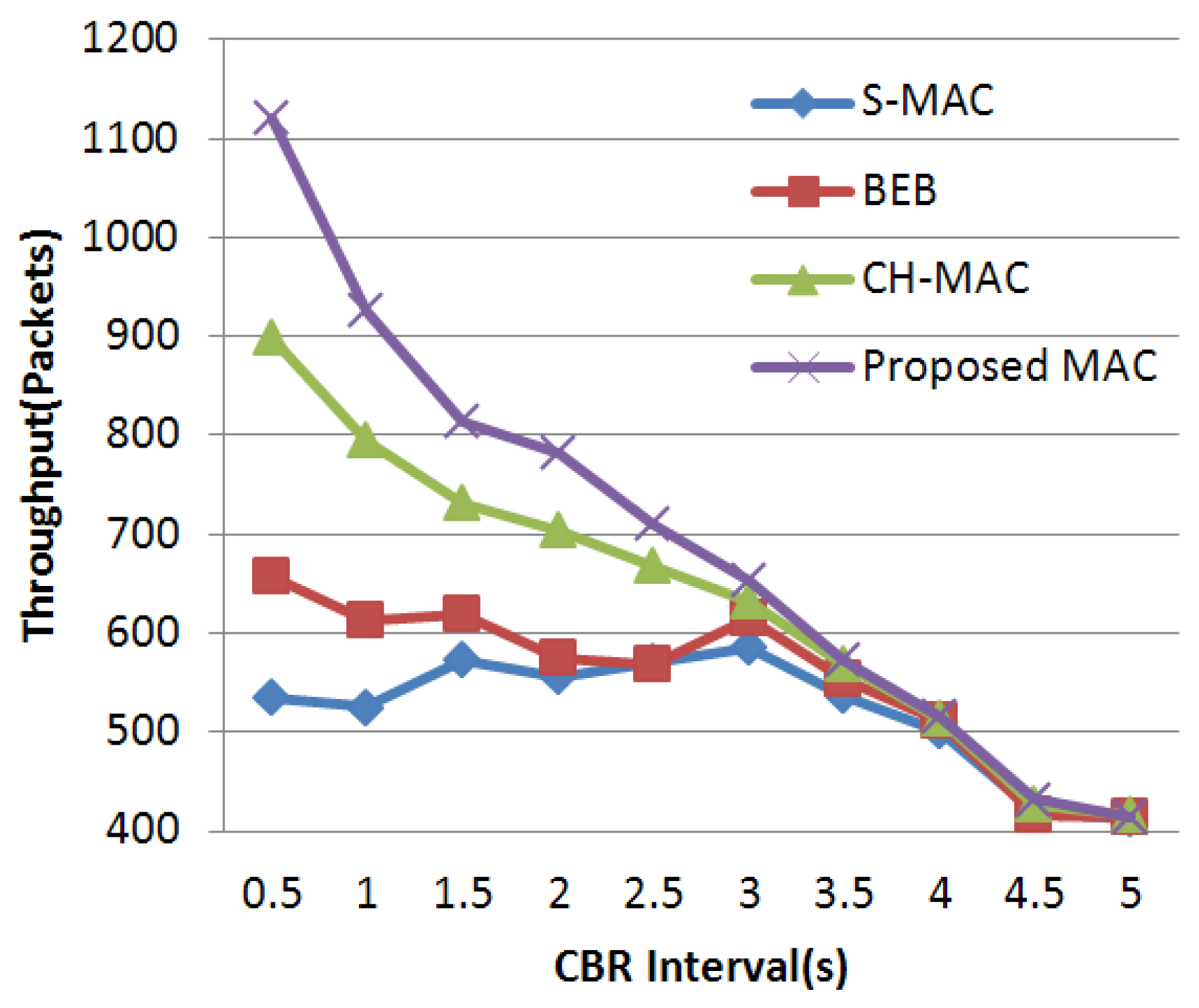
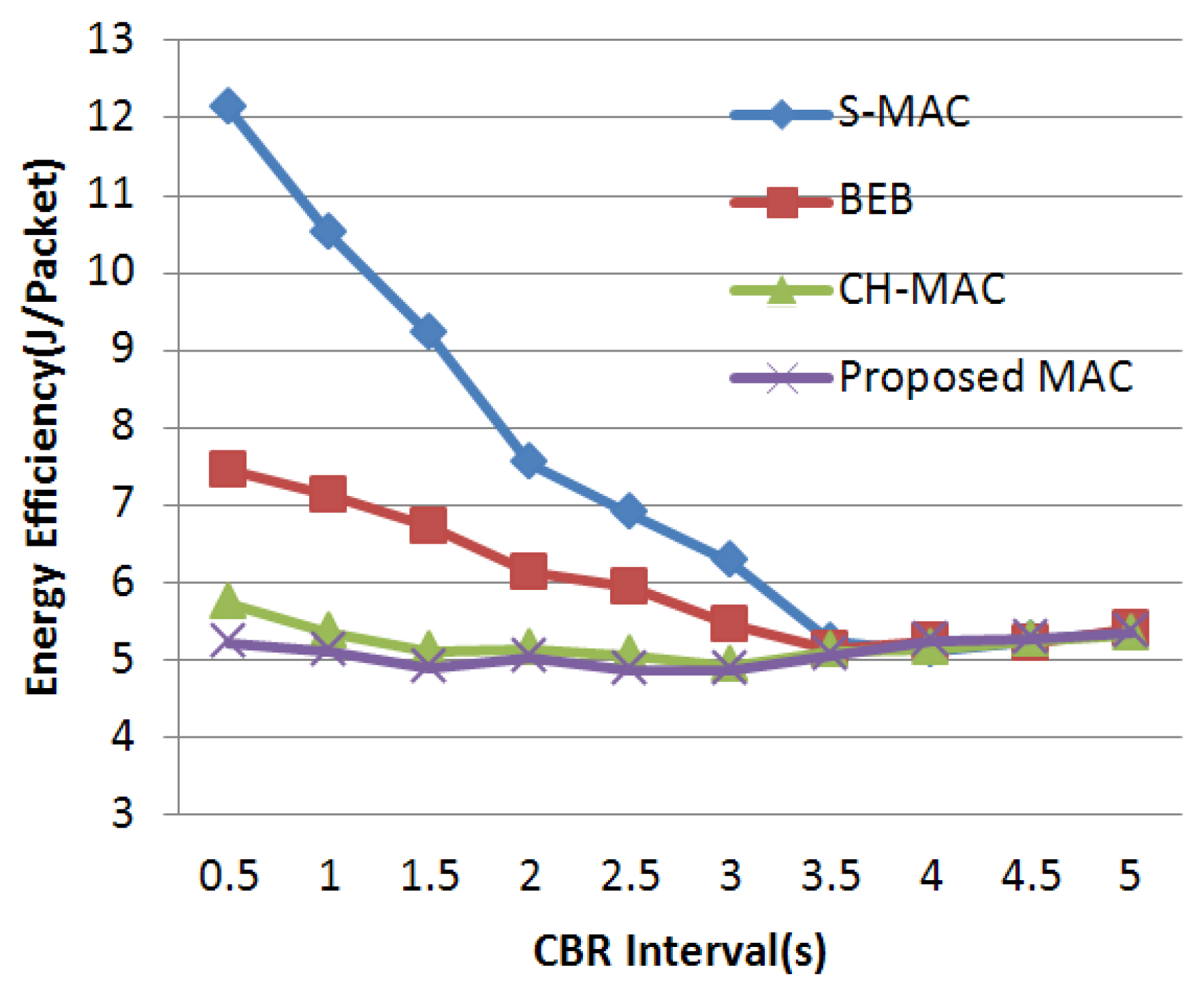
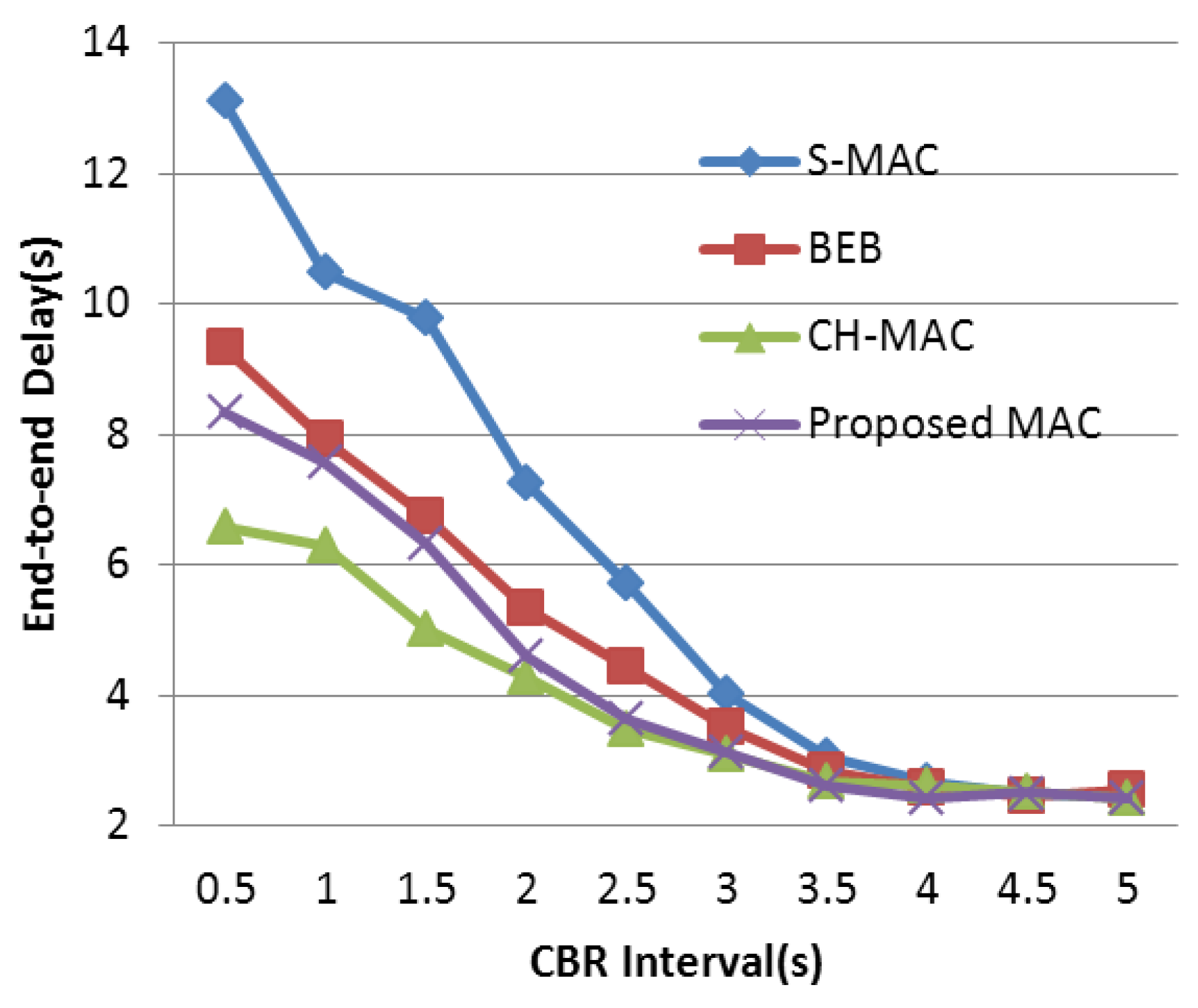
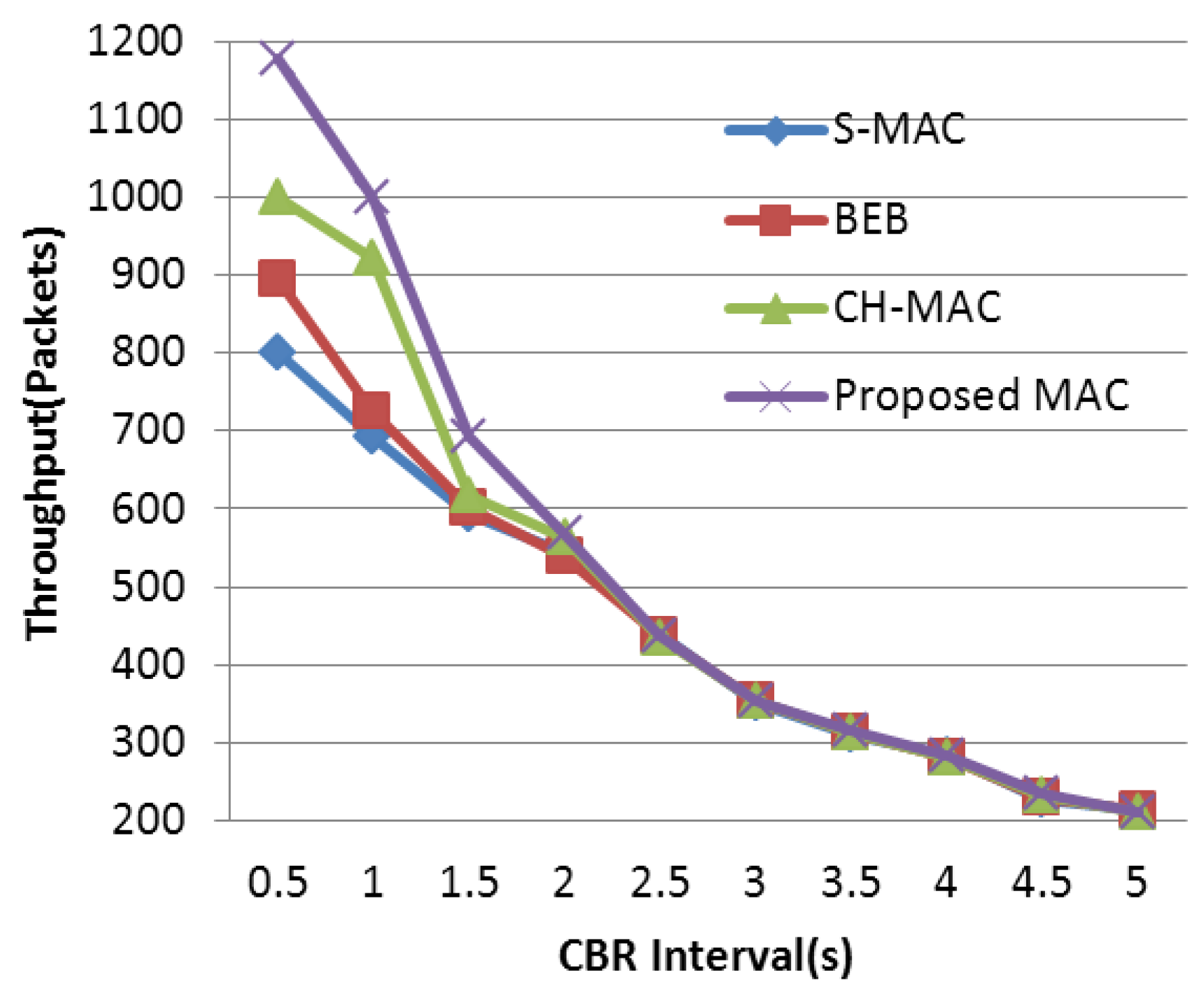
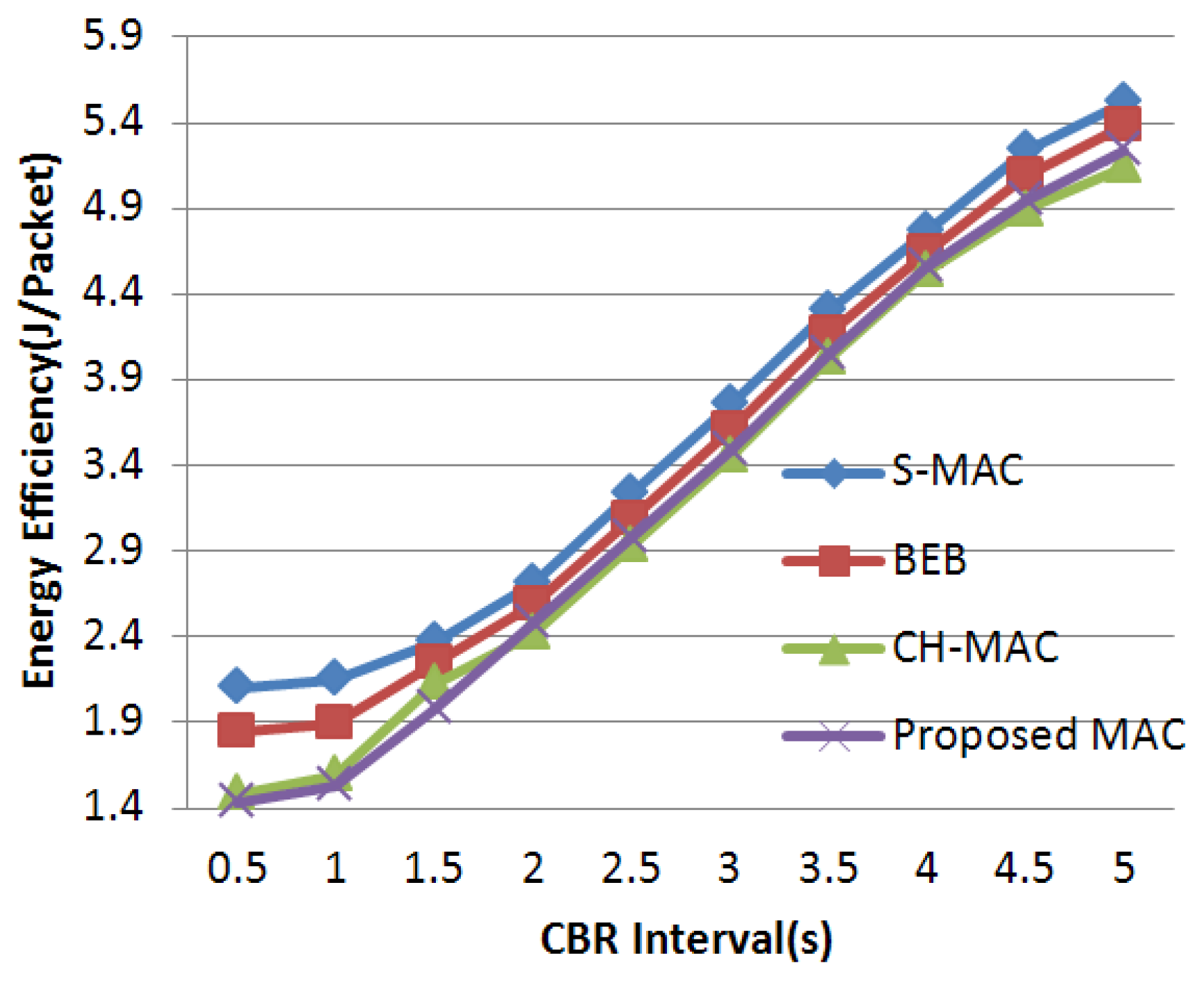
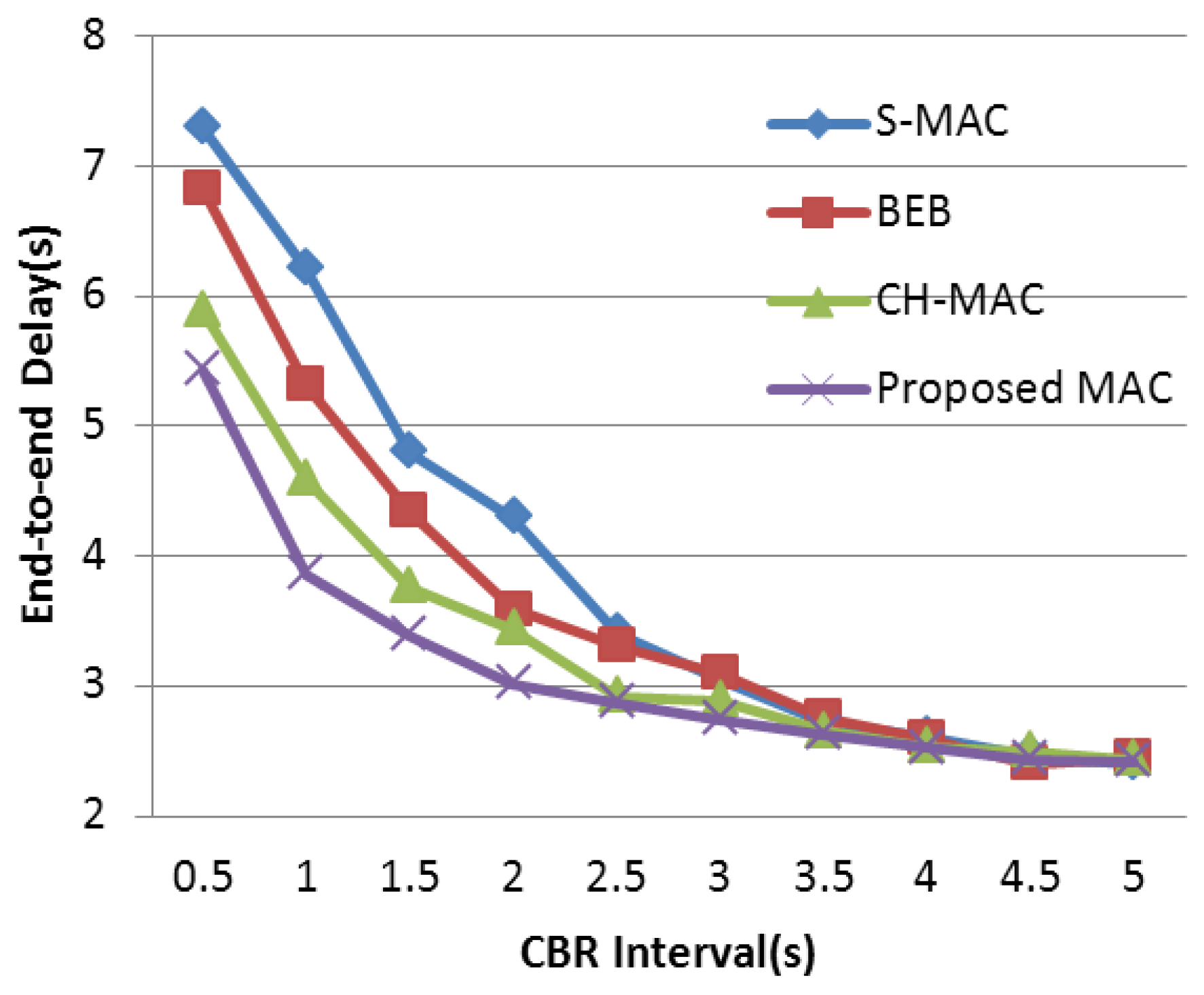
4.3. Experimental Results and Analysis
5. Summaries and Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Razaque, A.; Elleithy, K.M. Automated energy saving (AES) paradigm to support pedagogical activities over wireless sensor networks. In Proceedings of the International Conference on Ubiquitous Computing and Ambient Intelligence, Vitoria-Gasteiz, Spain, 3–5 December 2012. [Google Scholar]
- Razaque, A.; Elleithy, K.M. Low duty cycle, energy-efficient and mobility-based boarder node—MAC hybrid protocol for wireless sensor networks. J. Signal Proc. 2015, 81, 265–284. [Google Scholar] [CrossRef]
- Ray, S. ADV-MAC: Analysis and optimization of energy efficiency through data advertisements for wireless sensor networks. Ad Hoc Netw. 2011, 9, 876–892. [Google Scholar] [CrossRef]
- Ye, W.; Heidemann, J.; Estrin, D. An energy-efficient MAC protocol for wireless sensor networks. In Proceedings of the IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–l2 May 2014. [Google Scholar]
- Xu, D.; Wang, K. An adaptive traffic MAC protocol based on correlation of nodes. EURASIP J. Wirel. Commun. Netw. 2015, 1–13. [Google Scholar] [CrossRef]
- Van Dam, T.; Langendoen, K. An adaptive energy-efficient MAC protocol for wireless sensor networks. Proc. Sen. Sys. 2003, 171–180. [Google Scholar] [CrossRef]
- Ray, S.; Demirkol, I.; Heinzelman, W. ADV-MAC: Advertisement-based MAC protocol for wireless sensor networks. In Proceedings of the IEEE 6th International Conference on Mobile Adhoc and Sensor Systems, Louisville, KY, USA, 12–15 October 2009. [Google Scholar]
- Ray, S.; Demirkol, I.; Heinzelman, W. ATMA: Advertisement-Based TDMA protocol for bursty traffic in wireless sensor networks. In Proceedings of the 2010 IEEE Global Communications Conference, Miami, FL, USA, 6–10 December 2010. [Google Scholar]
- Adnan, M.T.; Datta, S. AdAMAC: A new MAC protocol for high traffic wireless networks. Procedia Comput. Sci. 2013, 19, 313–320. [Google Scholar] [CrossRef]
- Sun, Y.; Du, S.; Gurewitz, O.; Johnson, D.B. DW-MAC: A low latency, energy efficient demand-wakeup MAC protocol for wireless sensor networks. ACM Int. Sym. Mob. Ad Hoc Netw. Comput. 2008, 53–62. [Google Scholar] [CrossRef]
- Li, Z.; Wang, Z.; Zhu, G.; Li, R. A data gathering MAC protocol based on state translation and grouping for WSN. J. Comput. Res. Dev. 2014, 51, 1167–1175. [Google Scholar]
- Chu, Y.; Kosunalp, S.; Mitchell, P.D.; Grace, D.; Clarke, T. Application of reinforcement learning to medium access control for wireless sensor networks. Eng. Appl. Artif. Intell. 2015, 46, 23–32. [Google Scholar] [CrossRef]
- Li, Z.T.; Chen, Q.; Zhu, G.M.; Choi, Y.J.; Sekiya, H. A low latency, energy efficient mac protocol for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2015, 11, 1–9. [Google Scholar] [CrossRef]
- Cheng, L.I.; Wang, K.R.; Zhang, J.L.; Zhao, D.X. Optimization of listening time of S-MAC for wireless sensor networks. J. China Uni. Posts Telecom. 2009, 16, 41–45. [Google Scholar]
- Zou, W.; Wang, E.; Zhou, Z.; Li, W.; Ye, Y. A contention window adaptive MAC protocol for wireless sensor networks. Int. ICST Conf. Commun. Netw. 2012, 566–570. [Google Scholar]
- Andrey, L.; Andrei, G.; Evsey, M. An adaptive back-off protocol with Markovian contention window control. Commun. Stat. Simulate Comput. 2012, 1093–1106. [Google Scholar]
- Liu, Q.; Czylwik, A. A collision-aware back-off mechanism for IEEE 802.15.4 wireless sensor networks. Wirel. Days 2013, 143, 1–3. [Google Scholar]
- Khanafer, M.; Guennoun, M.; Mouftah, H.T. An efficient adaptive back-off algorithm for wireless sensor networks. Glob. Telecom Conf. 2011, 58, 1–6. [Google Scholar]
- Chen, Y.; Li, M.; Shu, L.; Wang, L.; Hara, T. A proportional fairness back-off scheme for funnelling effect in wireless sensor networks. Trans. Emerg. Telecom Technol. 2012, 23, 585–597. [Google Scholar] [CrossRef]
- Zhu, C.; Chen, Y.; Wang, L.; Shu, L.; Yang, Y. SMAC-based proportional fairness back-off scheme in wireless sensor networks. Proceedings of 2010 International Wireless Communications and Mobile Computing Conference, Caen, France, 28 June–2 July 2010. [Google Scholar]
- Yin, K. An effective wireless MAC protocol based on improved binary exponential back-off algorithm. Int. J. Digit. Content Technol. Appl. 2012, 6, 223–229. [Google Scholar]


| Parameter | Value | Parameter | Value |
|---|---|---|---|
| 16 | CBR Packet Size | 512 (bytes) | |
| 1024 | Routing Protocol | AODV | |
| 5 | Initial Energy | 1000 (J) | |
| 9 | Transmit Power | 0.386 (W) | |
| Radio Bandwidth | 20 (kbps) | Receive Power | 0.368 (W) |
| Node Transmission Range | 250 (m) | Idle Power | 0.344 (W) |
| Simulation Time | 1000 (s) | Sleep Power | 5.0e-5 (W) |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, P.; Li, G.; Wang, F. An Adaptive Back-Off Mechanism for Wireless Sensor Networks. Future Internet 2017, 9, 19. https://doi.org/10.3390/fi9020019
Sun P, Li G, Wang F. An Adaptive Back-Off Mechanism for Wireless Sensor Networks. Future Internet. 2017; 9(2):19. https://doi.org/10.3390/fi9020019
Chicago/Turabian StyleSun, Peng, Guangming Li, and Fuqiang Wang. 2017. "An Adaptive Back-Off Mechanism for Wireless Sensor Networks" Future Internet 9, no. 2: 19. https://doi.org/10.3390/fi9020019
APA StyleSun, P., Li, G., & Wang, F. (2017). An Adaptive Back-Off Mechanism for Wireless Sensor Networks. Future Internet, 9(2), 19. https://doi.org/10.3390/fi9020019





