A Lightweight Authentication and Authorization Framework for Blockchain-Enabled IoT Network in Health-Informatics
Abstract
1. Introduction
2. Literature Review
3. Materials and Methods
3.1. Random Number Generation
3.1.1. Homogenous IoT Devices
3.1.2. Heterogeneous IoT Devices
3.2. Proposed Authentication Framework
3.3. Experimental Setup
4. Results and Discussion
4.1. Mutual Authentication Robustness
4.2. Security Strength
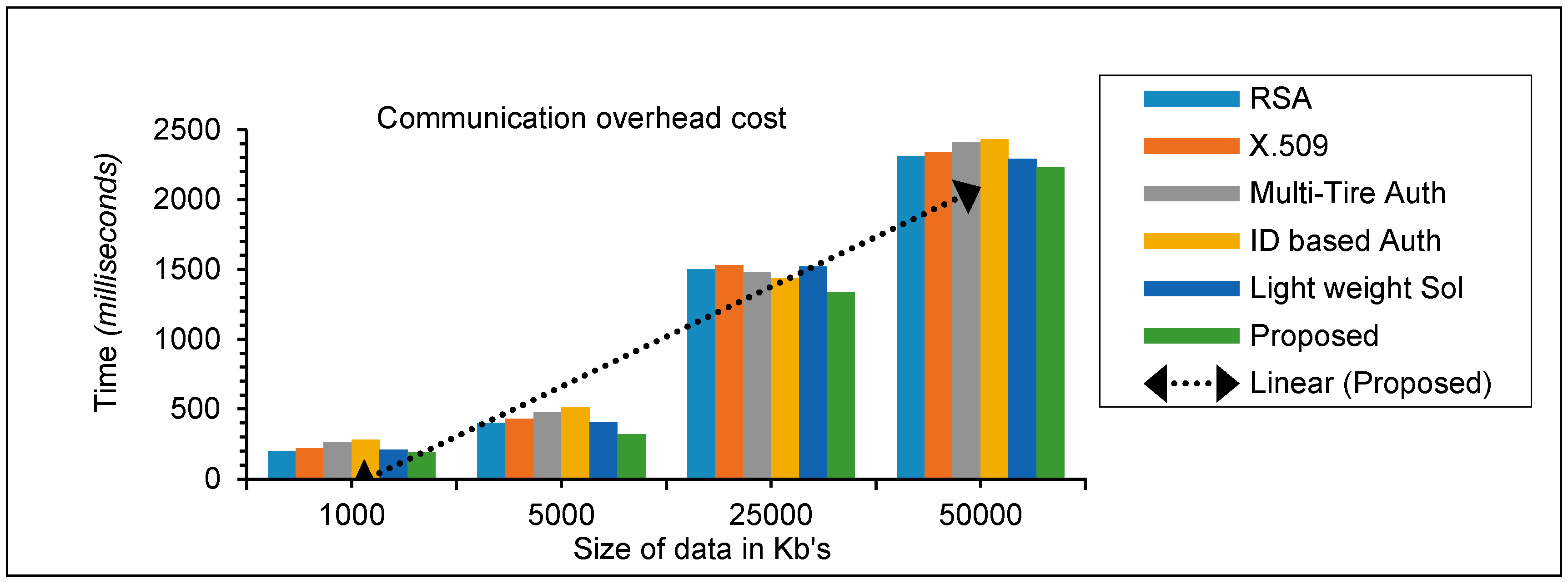
4.3. Communication Overhead
4.4. Computational Overhead
4.5. Resistance against Attacks
4.6. No Clock Synchronization and Independence of Session Key
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Udokwu, C.; Kormiltsyn, A.; Thangalimodzi, K.; Norta, A. The state of the art for blockchain-enabled smart-contract applications in the organization. In Proceedings of the 2018 Ivannikov Ispras Open Conference (ISPRAS), Tokyo, Japan, 22–23 November 2018; pp. 137–144. [Google Scholar]
- Bennett, B. Blockchain HIE Overview: A Framework for Healthcare Interoperability. Telehealth Med. Today 2017, 2, 1–6. [Google Scholar] [CrossRef]
- Casino, F.; Patsakis, C.; Batista, E.; Borràs, F.; Martínez-Ballesté, A. Healthy routes in the smart city: A context-aware mobile recommender. IEEE Softw. 2017, 34, 42–47. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.-N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Siyal, A.A.; Junejo, A.Z.; Zawish, M.; Ahmed, K.; Khalil, A.; Soursou, G. Applications of blockchain technology in medicine and healthcare: Challenges and future perspectives. Cryptography 2019, 3, 3. [Google Scholar] [CrossRef]
- Yang, Y.; Zheng, X.; Tang, C. Lightweight distributed secure data management system for health internet of things. J. Netw. Comput. Appl. 2017, 89, 26–37. [Google Scholar] [CrossRef]
- Patranabis, S.; Shrivastava, Y.; Mukhopadhyay, D. Provably secure key-aggregate cryptosystems with broadcast aggregate keys for online data sharing on the cloud. IEEE Trans. Comput. 2017, 66, 891–904. [Google Scholar] [CrossRef]
- Huang, H.; Gong, T.; Ye, N.; Wang, R.; Dou, Y. Private and secured medical data transmission and analysis for wireless sensing healthcare system. IEEE Trans. Ind. Inform. 2017, 13, 1227–1237. [Google Scholar] [CrossRef]
- Ara, A.; Al-Rodhaan, M.; Tian, Y.; Al-Dhelaan, A. A secure privacy-preserving data aggregation scheme based on bilinear ElGamal cryptosystem for remote health monitoring systems. IEEE Access 2017, 5, 12601–12617. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. BSN-Care: A secure IoT-based modern healthcare system using body sensor network. IEEE Sens. J. 2016, 16, 1368–1376. [Google Scholar] [CrossRef]
- Li, M.; Yu, S.; Zheng, Y.; Ren, K.; Lou, W. Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 131–143. [Google Scholar] [CrossRef]
- Li, S.; Da Xu, L.; Zhao, S. The internet of things: A survey. Inf. Syst. Front. 2015, 17, 243–259. [Google Scholar] [CrossRef]
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future internet: The internet of things architecture, possible applications and key challenges. In Proceedings of the 10th International Conference on Frontiers of Information Technology, Islamabad, Pakistan, 17–19 December 2012; pp. 257–260. [Google Scholar]
- Sardaraz, M.; Tahir, M. A Hybrid Algorithm for Scheduling Scientific Workflows in Cloud Computing. IEEE Access 2019, 7, 186137–186146. [Google Scholar] [CrossRef]
- AVSystem. Available online: https://www.avsystem.com/blog/what-is-iot-architecture/ (accessed on 13 June 2020).
- Aijaz, A.; Aghvami, A.H. Cognitive machine-to-machine communications for Internet-of-Things: A protocol stack perspective. IEEE Internet Things J. 2015, 2, 103–112. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Zheng, L.; Chen, S.; Xiang, S.; Hu, Y. Research of architecture and application of Internet of Things for smart grid. In Proceedings of the 2012 International Conference on Computer Science and Service System, Nanjing, China, 11–13 August 2012; pp. 938–941. [Google Scholar]
- Rubí, J.N.S.; Gondim, P.R.d.L. Interoperable Internet of Medical Things platform for e-Health applications. Int. J. Distrib. Sens. Netw. 2020. [Google Scholar] [CrossRef]
- Ma, Z.; Shang, X.; Fu, X.; Luo, F. The architecture and key technologies of Internet of Things in logistics. In Proceedings of the International Conference on Cyberspace Technology, Beijing, China, 23 November 2013; pp. 464–468. [Google Scholar]
- Schulz, P.; Matthe, M.; Klessig, H.; Simsek, M.; Fettweis, G.; Ansari, J.; Ashraf, S.A.; Almeroth, B.; Voigt, J.; Riedel, I. Latency critical iot applications in 5g: Perspective on the design of radio interface and network architecture. IEEE Commun. Mag. 2017, 55, 70–78. [Google Scholar] [CrossRef]
- Wu, J.; Feng, Y.; Sun, P. Sensor fusion for recognition of activities of daily living. Sensors 2018, 18, 4029. [Google Scholar] [CrossRef]
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed internet of things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Weber, R.H. Internet of Things–New security and privacy challenges. Comput. Law Secur. Rev. 2010, 26, 23–30. [Google Scholar] [CrossRef]
- Bai, G.; Yan, L.; Gu, L.; Guo, Y.; Chen, X. Context-aware usage control for web of things. Secur. Commun. Netw. 2014, 7, 2696–2712. [Google Scholar] [CrossRef]
- Haller, S.; Karnouskos, S.; Schroth, C. The internet of things in an enterprise context. In Future Internet Symposium; Springer: Berlin/Heidelberg, Germany, 2008; pp. 14–28. [Google Scholar]
- Whitmore, A.; Agarwal, A.; Da Xu, L. The Internet of Things—A survey of topics and trends. Inf. Syst. Front. 2015, 17, 261–274. [Google Scholar] [CrossRef]
- Lu, R.; Li, X.; Liang, X.; Shen, X.; Lin, X. GRS: The green, reliability, and security of emerging machine to machine communications. IEEE Commun. Mag. 2011, 49, 28–35. [Google Scholar]
- Kothmayr, T.; Schmitt, C.; Hu, W.; Brünig, M.; Carle, G. DTLS based security and two-way authentication for the Internet of Things. Ad Hoc Netw. 2013, 11, 2710–2723. [Google Scholar] [CrossRef]
- Kotzanikolaou, P.; Magkos, E. Hybrid key establishment for multiphase self-organized sensor networks. In Proceedings of the Sixth IEEE International Symposium on a World of Wireless Mobile and Multimedia Networks, Taormina, Italy, 16 June 2005; pp. 581–587. [Google Scholar]
- Moghaddam, F.F.; Moghaddam, S.G.; Rouzbeh, S.; Araghi, S.K.; Alibeigi, N.M.; Varnosfaderani, S.D. A scalable and efficient user authentication scheme for cloud computing environments. In Proceedings of the 2014 IEEE Region 10 Symposium, Kuala Lumpur, Malaysiam, 14–16 April 2014; pp. 508–513. [Google Scholar]
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. Authentication protocols for Internet of Things: A comprehensive survey. Secur. Commun. Netw. 2017, 2017. [Google Scholar] [CrossRef]
- Saadeh, M.; Sleit, A.; Qatawneh, M.; Almobaideen, W. Authentication techniques for the internet of things: A survey. In Proceedings of the Cybersecurity and Cyberforensics Conference (CCC), Amman, Jordan, 2–4 August 2016; pp. 28–34. [Google Scholar]
- Yue, X.; Wang, H.; Jin, D.; Li, M.; Jiang, W. Healthcare data gateways: Found healthcare intelligence on blockchain with novel privacy risk control. J. Med. Syst. 2016, 40, 218. [Google Scholar] [CrossRef]
- Dai, H.-N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Trnka, M.; Cerny, T.; Stickney, N. Survey of Authentication and Authorization for the Internet of Things. Secur. Commun. Netw. 2018, 2018. [Google Scholar] [CrossRef]
- Mukherjee, A.; Ghosh, S.; Behere, A.; Ghosh, S.K.; Buyya, R. Internet of Health Things (IoHT) for Personalized Health Care using Integrated Edge-Fog-Cloud Network. J. Ambient Intell. Humaniz. Comput. 2020. [Google Scholar] [CrossRef]
- Alam, T. mHealth Communication Framework using blockchain and IoT Technologies. Int. J. Sci. Technol. Res. 2020. [Google Scholar] [CrossRef]
- Rathee, G.; Sharma, A.; Saini, H.; Kumar, R.; Iqbal, R. A hybrid framework for multimedia data processing in IoT-healthcare using blockchain technology. Multimed. Tools Appl. 2020, 79, 9711–9733. [Google Scholar] [CrossRef]
- Patel, V. A framework for secure and decentralized sharing of medical imaging data via blockchain consensus. Health Inform. J. 2019, 25, 1398–1411. [Google Scholar] [CrossRef] [PubMed]
- Chen, Y.; Ding, S.; Xu, Z.; Zheng, H.; Yang, S. Blockchain-based medical records secure storage and medical service framework. J. Med. Syst. 2019, 43, 5. [Google Scholar] [CrossRef] [PubMed]
- Chakraborty, S.; Aich, S.; Kim, H.-C. A secure healthcare system design framework using blockchain technology. In Proceedings of the 2019 21st International Conference on Advanced Communication Technology (ICACT), PyeongChang, Korea, 17–20 February 2019; pp. 260–264. [Google Scholar]
- Zhang, A.; Lin, X. Towards secure and privacy-preserving data sharing in e-health systems via consortium blockchain. J. Med. Syst. 2018, 42, 140. [Google Scholar] [CrossRef]
- Rahmadika, S.; Rhee, K.-H. Blockchain technology for providing an architecture model of decentralized personal health information. Int. J. Eng. Bus. Manag. 2018. [Google Scholar] [CrossRef]
- Zhang, J.; Xue, N.; Huang, X. A secure system for pervasive social network-based healthcare. IEEE Access 2016, 4, 9239–9250. [Google Scholar] [CrossRef]
- Hasselgren, A.; Kralevska, K.; Gligoroski, D.; Pedersen, S.A.; Faxvaag, A. Blockchain in healthcare and health sciences—A scoping review. Int. J. Med. Inform. 2020, 134, 104040. [Google Scholar] [CrossRef]
- Agbo, C.C.; Mahmoud, Q.H.; Eklund, J.M. Blockchain technology in healthcare: A systematic review. In Healthcare; Multidisciplinary Digital Publishing Institute: Basel, Switzerland, 2019; p. 56. [Google Scholar]
- Ferrag, M.A.; Maglaras, L.; Derhab, A. Authentication and authorization for mobile IoT devices using biofeatures: Recent advances and future trends. Secur. Commun. Netw. 2019. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Meddeb, A. Internet of things standards: Who stands out from the crowd? IEEE Commun. Mag. 2016, 54, 40–47. [Google Scholar] [CrossRef]
- Weyrich, M.; Ebert, C. Reference architectures for the internet of things. IEEE Softw. 2016, 33, 112–116. [Google Scholar] [CrossRef]
- Zhang, M.; Sun, F.; Cheng, X. Architecture of internet of things and its key technology integration based-on RFID. In Proceedings of the 2012 Fifth International Symposium on Computational Intelligence and Design, Nanjing, China, 18–20 October 2012; pp. 294–297. [Google Scholar]
- Gou, Q.; Yan, L.; Liu, Y.; Li, Y. Construction and strategies in IoT security system. In Proceedings of the 2013 IEEE International Conference on Green Computing and Communications and IEEE Internet of Things and IEEE Cyber, Physical and Social Computing, Beijing, China, 20–23 August 2013; pp. 1129–1132. [Google Scholar]
- Zhao, K.; Ge, L. A survey on the internet of things security. In Proceedings of the 2013 Ninth International Conference on Computational Intelligence and Security, Emeishan, China, 14–15 December 2013; pp. 663–667. [Google Scholar]
- Castellani, A.P.; Bui, N.; Casari, P.; Rossi, M.; Shelby, Z.; Zorzi, M. Architecture and protocols for the internet of things: A case study. In Proceedings of the 2010 8th IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops), Mannheim, Germany, 29 March–2 April 2010; pp. 678–683. [Google Scholar]
- Anshel, I.; Anshel, M.; Goldfeld, D.; Lemieux, S. Key agreement, the Algebraic EraserTM, and lightweight cryptography. Contemp. Math. 2007, 418, 1–34. [Google Scholar]
- Artin, E. Theory of braids. Ann. Math. 1947, 48, 101–126. [Google Scholar] [CrossRef]
- Hong, D.; Sung, J.; Hong, S.; Lim, J.; Lee, S.; Koo, B.; Lee, C.; Chang, D.; Lee, J.; Jeong, K. HIGHT: A new block cipher suitable for low-resource device. In Proceedings of the CHES 2016, Barbara, CA, USA, 17–19 August 2016; pp. 46–59. [Google Scholar]
- Li, N.; Liu, D.; Nepal, S. Lightweight Mutual Authentication for IoT and Its Applications. IEEE Trans. Sustain. Comput. 2017, 2, 359–370. [Google Scholar] [CrossRef]
- Hoffstein, J.; Pipher, J.; Silverman, J.H. International Algorithmic Number Theory Symposium; Springer: Berlin, Germany, 1998; pp. 267–288. [Google Scholar]
- Perlner, R.A.; Cooper, D.A. Quantum resistant public key cryptography: A survey. In Proceedings of the 8th Symposium on Identity and Trust on the Internet, Gaithersburg, MD, USA, 14–16 April 2009; pp. 85–93. [Google Scholar]
- Gura, N.; Patel, A.; Wander, A.; Eberle, H.; Shantz, S.C. Comparing elliptic curve cryptography and RSA on 8-bit CPUs. In Proceedings of the CHES 2004, Cambridge, MA, USA, 11–13 August 2004; pp. 119–132. [Google Scholar]
- Hankerson, D.; Menezes, A.J.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer Science & Business Media: New York, NY, USA, 2006. [Google Scholar]
- Liu, A.; Ning, P. TinyECC: A configurable library for elliptic curve cryptography in wireless sensor networks. In Proceedings of the 7th International Conference on Information Processing in Sensor Networks, St. Louis, MO, USA, 10–13 August 2008; pp. 245–256. [Google Scholar]
- Hermans, J.; Peeters, R.; Preneel, B. Proper RFID privacy: Model and protocols. IEEE Trans. Mob. Comput. 2014, 13, 2888–2902. [Google Scholar] [CrossRef]
- Lee, Y.K.; Batina, L.; Singelée, D.; Verbauwhede, I. Low-cost untraceable authentication protocols for RFID. In Proceedings of the Third ACM Conference on Wireless Network Security, Hoboken, NJ, USA, 22–24 March 2010; pp. 55–64. [Google Scholar]
- Lee, Y.K.; Batina, L.; Verbauwhede, I. EC-RAC (ECDLP based randomized access control): Provably secure RFID authentication protocol. In Proceedings of the 2008 IEEE International Conference on RFID, Las Vegas, NV, USA, 3–10 March 2008; pp. 97–104. [Google Scholar]
- Lee, Y.K.; Batina, L.; Verbauwhede, I. Untraceable RFID authentication protocols: Revision of EC-RAC. In Proceedings of the 2009 IEEE International Conference on RFID, Orlando, FL, USA, 27–28 April 2009; pp. 178–185. [Google Scholar]
- Ko, K.; Lee, S.; Cheon, J.; Han, J.; Kang, J.-S.; Park, C. New public-key cryptosystem using braid groups. In Proceedings of the Advances in Cryptology—CRYPTO 2000, Santa Barbara, CA, USA, 20–24 August 2000; pp. 166–183. [Google Scholar]
- Anshel, I.; Anshel, M.; Fisher, B.; Goldfeld, D. New key agreement protocols in braid group cryptography. In Cryptographers’ Track at the RSA Conference; Springer: Berlin/Heidelberg, Germany, 2001; pp. 13–27. [Google Scholar]
- Ko, K.H.; Choi, D.-H.; Cho, M.S.; Lee, J.-W. New Signature Scheme Using Conjugacy Problem. IACR Cryptol. ePrint Arch. 2002, 2002, 168. [Google Scholar]
- Lee, E.; Lee, S.; Hahn, S. Pseudorandomness from braid groups. In Proceedings of the Advances in Cryptology—CRYPTO 2001, Santa Barbara, CA, USA, 19–23 August 2001; pp. 486–502. [Google Scholar]
- Hofheinz, D.; Steinwandt, R. A practical attack on some braid group based cryptographic primitives. In Proceedings of the Public Key Cryptography 2003, Miami, FL, USA, 6–8 January 2003; pp. 187–198. [Google Scholar]
- Lee, S.; Lee, E. Potential weaknesses of the commutator key agreement protocol based on braid groups. In Proceedings of the Advances in Cryptology—EUROCRYPT 2002, Amsterdam, The Netherlands, 28 April–2 May 2002; pp. 14–28. [Google Scholar]
- Ben-Zvi, A.; Blackburn, S.R.; Tsaban, B. A practical cryptanalysis of the Algebraic Eraser. In Proceedings of the Annual Cryptology Conference, 2016, Santa Barbara, CA, USA, 14–18 August 2016; pp. 179–189. [Google Scholar]
- Blackburn, S.R.; Robshaw, M.J. On the security of the Algebraic Eraser tag authentication protocol. In Proceedings of the International Conference on Applied Cryptography and Network Security 2016, London, UK, 19–22 June 2016; pp. 3–17. [Google Scholar]
- Kalka, A.; Teicher, M.; Tsaban, B. Short expressions of permutations as products and cryptanalysis of the Algebraic Eraser. Adv. Appl. Math. 2012, 49, 57–76. [Google Scholar] [CrossRef][Green Version]
- Peeters, R.; Hermans, J.; Fan, J. IBIHOP: Proper Privacy Preserving Mutual RFID Authentication. RFIDSec Asia 2013, 11, 45–56. [Google Scholar]
- Vaudenay, S. On privacy models for RFID. In Proceedings of the Advances in Cryptology–ASIACRYPT 2007, Kuching, Malaysia, 2–6 December 2007; pp. 68–87. [Google Scholar]
- Zhu, H.; Lin, X.; Zhang, Y.; Lu, R. Duth: A user-friendly dual-factor authentication for Android smartphone devices. Secur. Commun. Netw. 2015, 8, 1213–1222. [Google Scholar] [CrossRef]
- Chen, D.; Zhang, N.; Qin, Z.; Mao, X.; Qin, Z.; Shen, X.; Li, X.-Y. S2M: A lightweight acoustic fingerprints-based wireless device authentication protocol. IEEE Internet Things J. 2017, 4, 88–100. [Google Scholar] [CrossRef]
- Katz, J.; Lindell, A.Y. Aggregate message authentication codes. In Topics in Cryptology–CT-RSA 2008; Springer: Berlin, Germany, 2008; pp. 155–169. [Google Scholar]
- Lai, C.; Li, H.; Lu, R.; Jiang, R.; Shen, X. LGTH: A lightweight group authentication protocol for machine-type communication in LTE networks. In Proceedings of the Global Communications Conference (GLOBECOM) 2013, Atlanta, GA, USA, 9–13 December 2013; pp. 832–837. [Google Scholar]
- Lai, C.; Lu, R.; Zheng, D.; Li, H.; Shen, X.S. GLARM: Group-based lightweight authentication scheme for resource-constrained machine to machine communications. Comput. Netw. 2016, 99, 66–81. [Google Scholar] [CrossRef]
- Lee, S.-H.; Jeong, Y.-S. Information authentication selection scheme of IoT devices using conditional probability. Indian J. Sci. Technol. 2016. [Google Scholar] [CrossRef]
- Endler, M.; Briot, J.-P.; De Almeida, V.; Dos Reis, R.; Silva, F.S.E. Stream-based Reasoning for IoT Applications–Proposal of Architecture and Analysis of Challenges. Int. J. Semant. Comput. 2017, 11, 325–344. [Google Scholar] [CrossRef]
- Borgohain, T.; Borgohain, A.; Kumar, U.; Sanyal, S. Authentication systems in internet of things. arXiv 2015, arXiv:1502.00870. [Google Scholar]
- Alonso, Á.; Fernández, F.; Marco, L.; Salvachúa, J. Iaacaas: Iot application-scoped access control as a service. Future Internet 2017, 9, 64. [Google Scholar] [CrossRef]
- Cirani, S.; Picone, M.; Gonizzi, P.; Veltri, L.; Ferrari, G. Iot-oas: An oauth-based authorization service architecture for secure services in iot scenarios. IEEE Sens. J. 2014, 15, 1224–1234. [Google Scholar] [CrossRef]
- Kumari, A.; Gupta, R.; Tanwar, S.; Kumar, N. Blockchain and AI amalgamation for energy cloud management: Challenges, solutions, and future directions. J. Parallel Distrib. Comput. 2020, 143, 148–166. [Google Scholar] [CrossRef]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.-N.; Chen, W.; Chen, X.; Weng, J.; Imran, M. An overview on smart contracts: Challenges, advances and platforms. Future Gener. Comput. Syst. 2020, 105, 475–491. [Google Scholar] [CrossRef]
- Fan, K.; Wang, S.; Ren, Y.; Li, H.; Yang, Y. Medblock: Efficient and secure medical data sharing via blockchain. J. Med. Syst. 2018, 42, 136. [Google Scholar] [CrossRef]
- Li, H.; Zhu, L.; Shen, M.; Gao, F.; Tao, X.; Liu, S. Blockchain-based data preservation system for medical data. J. Med. Syst. 2018, 42, 141. [Google Scholar] [CrossRef]
- Zubaydi, H.D.; Chong, Y.-W.; Ko, K.; Hanshi, S.M.; Karuppayah, S. A review on the role of blockchain technology in the healthcare domain. Electronics 2019, 8, 679. [Google Scholar] [CrossRef]
- Automated Validation of Internet Security Protocols and Applications (AVISPA) Tool. Available online: http://www.avispa-project.org/ (accessed on 15 March 2020).
- Chicxurug. SolMet-Solidity-Parser. Available online: https://github.com/chicxurug/SolMet-Solidity-parser (accessed on 20 February 2020).
- Singh, A.; Chatterjee, K. A secure multi-tier authentication scheme in cloud computing environment. In Proceedings of the 2015 International Conference on Circuit, Power and Computing Technologies (ICCPCT), Nagercoil, India, 19–20 March 2015; pp. 1–7. [Google Scholar]
- Yang, J.H.; Lin, P.Y. An ID-based user authentication scheme for cloud computing. In Proceedings of the 2014 Tenth International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), Kitakyushu, Japan, 27–29 August 2014; pp. 98–101. [Google Scholar]
- Raza, S. Lightweight Security Solutions for the Internet of Things; Mälardalen University: Västerås, Sweden, 2013. [Google Scholar]











| S.No | Parameter | Descriptions |
|---|---|---|
| 1. | SLOC | Source lines of code |
| 2. | LLOC | Logical lines of code |
| 3. | NF | Number of functions |
| 4. | NL | Nesting level |
| 5. | NLE | Nesting level else if |
| 6. | NUMPAR | Number of parameters |
| 7. | DIT | Depth of inheritance tree |
| 8. | NOA | Number of ancestors |
| 9. | NOD | Number of descendants |
| 10. | NA | Number of attributes (i.e., states) |
| 11. | Read Latency | The time interval between reading request and response |
| 12. | Read Throughput | Measurement of read operations completed in a defined timeframe |
| 13. | Transaction Latency | The time from the submission of a transaction until the generation of results in the network |
| 14. | Transaction Throughput | The frequency of transactions submission over the Blockchain network. |
| S. No | Parameter | Configuration |
|---|---|---|
| 1. | Radio Medium | Unit Disk Graph Medium (UDGM) |
| 2. | Mote Startup Delays | 1000 ms |
| 3. | Random Speed | 123,456 |
| 4. | New Random seed on reload | ON |
| 5. | Simulation area | 550 m × 550 m |
| 6. | Number of thresholds | Fixed i.e., 3000, 6000, 12,000, 24,000, 48,000 |
| 7. | Number of IoT devices | 15, 30, 60, 120 and 10, 35, 75, 100 and Random |
| 8. | Data generation interval | 0.1 ms |
| 9. | Transmission of IoT device | 25 m |
| 10. | Initial dataset time | 2.0 h |
| Parameters | Migration Solidity Metric Value | User Solidity Metric Value |
|---|---|---|
| SLOC | 13 | 140 |
| LLOC | 5 | 80 |
| NF | 3 | 2 |
| NL | 0 | 1 |
| NLE | 0 | 0 |
| NUMPER | 1 | 12 |
| DIT | 0 | 1 |
| NOA | 0 | 1 |
| NOD | 3 | 0 |
| NA | 0 | 5 |
| Attacks | RSA | X.509 | Multi-Tire Auth | ID-Based Auth | Lightweight Sol | Proposed |
|---|---|---|---|---|---|---|
| DoS | Yes | No | Yes | No | No | Yes |
| Eavesdropping | Yes | Yes | No | Yes | No | No |
| Forgery | Yes | No | Yes | No | Yes | Yes |
| Impersonation | Yes | Yes | No | Yes | Yes | Yes |
| Insider | No | No | Yes | No | Yes | No |
| Man-in-middle | Yes | Yes | Yes | Yes | Yes | Yes |
| Replay | Yes | Yes | Yes | No | No | Yes |
| Timing | No | Yes | No | Yes | No | Yes |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tahir, M.; Sardaraz, M.; Muhammad, S.; Saud Khan, M. A Lightweight Authentication and Authorization Framework for Blockchain-Enabled IoT Network in Health-Informatics. Sustainability 2020, 12, 6960. https://doi.org/10.3390/su12176960
Tahir M, Sardaraz M, Muhammad S, Saud Khan M. A Lightweight Authentication and Authorization Framework for Blockchain-Enabled IoT Network in Health-Informatics. Sustainability. 2020; 12(17):6960. https://doi.org/10.3390/su12176960
Chicago/Turabian StyleTahir, Muhammad, Muhammad Sardaraz, Shakoor Muhammad, and Muhammad Saud Khan. 2020. "A Lightweight Authentication and Authorization Framework for Blockchain-Enabled IoT Network in Health-Informatics" Sustainability 12, no. 17: 6960. https://doi.org/10.3390/su12176960
APA StyleTahir, M., Sardaraz, M., Muhammad, S., & Saud Khan, M. (2020). A Lightweight Authentication and Authorization Framework for Blockchain-Enabled IoT Network in Health-Informatics. Sustainability, 12(17), 6960. https://doi.org/10.3390/su12176960






