Effective Energy Management via False Data Detection Scheme for the Interconnected Smart Energy Hub–Microgrid System under Stochastic Framework
Abstract
:1. Introduction
1.1. Energy Management in Distribution Systems
1.2. Energy Hub Systems
1.3. False Data Injection Attack (FDIA)
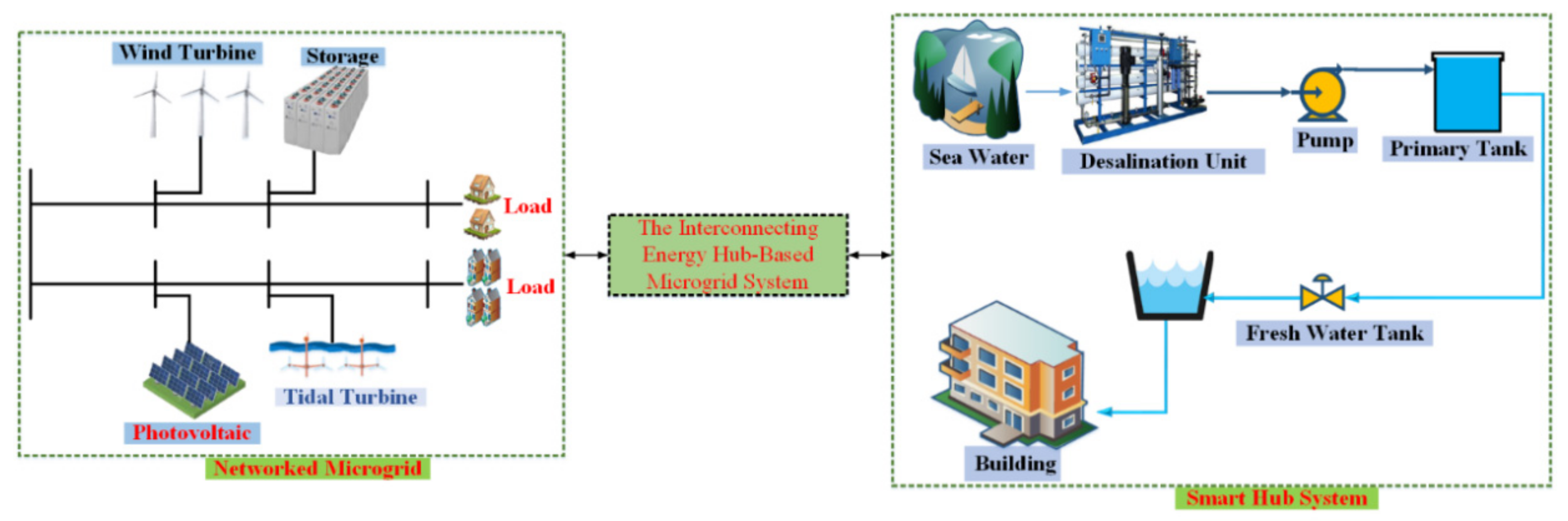
- Providing an efficient and comprehensive framework based on the interconnected energy hub-based microgrid system to improve the simultaneous management of energy different carriers.
- Developing an appropriate and strong IPS-RL scheme aimed at detecting all types of attacks and guarantee the minimum detection delay.
- Validating and assessing the proposed detection method by implementing and modeling the FDI attack.
- The uncertainties of the studied system, including the electrical, thermal, and water loads, the tidal current, wind speed. and sunlight, are formulated by the UT method, which can model the correlation among uncertain parameters.
2. Formulation Definition of the Proposed Framework
2.1. Electrical Part
2.2. Heat Part
2.3. Water Part
3. Proposed Cyber Attack Detection Approach
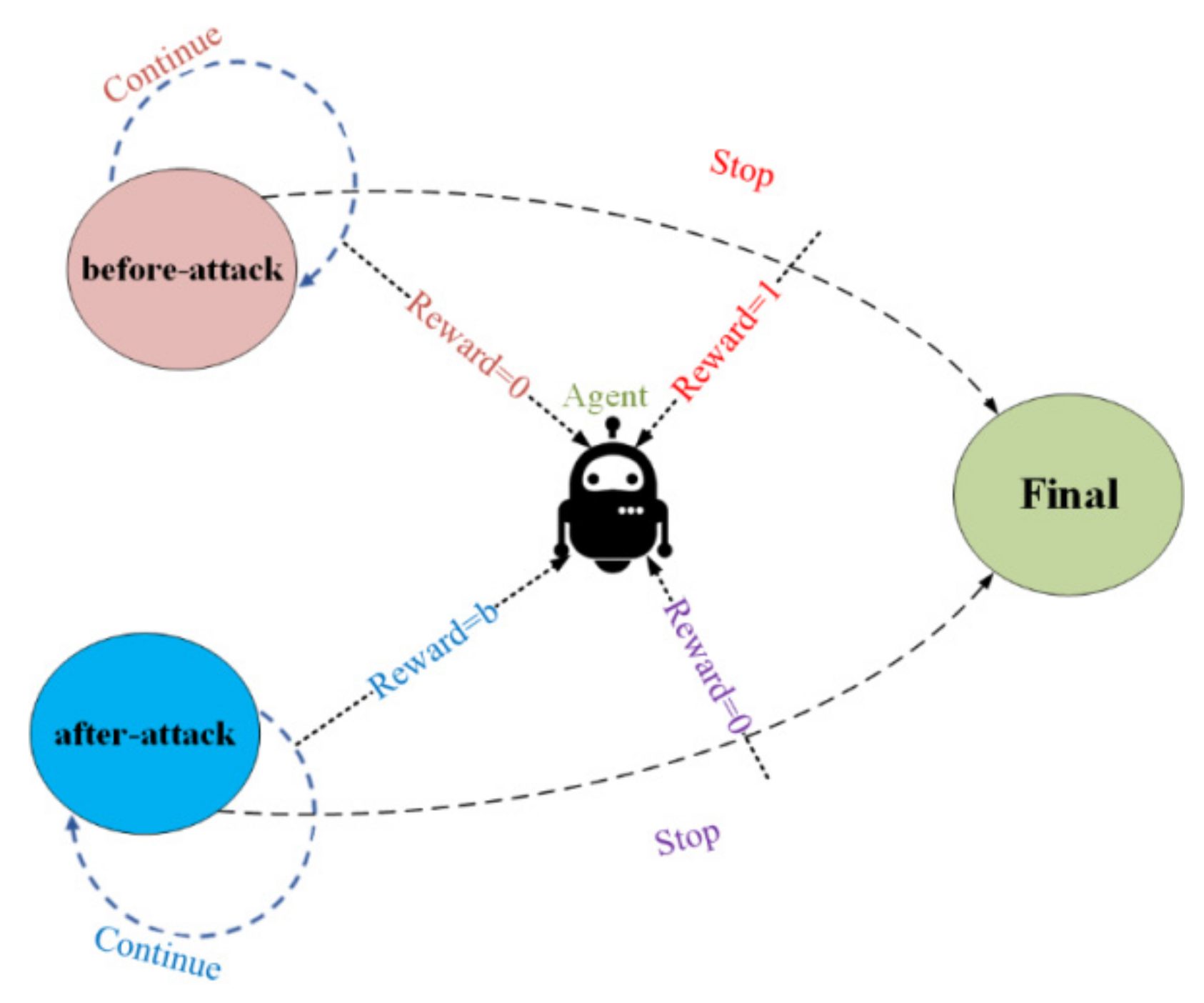
3.1. FDIA Model
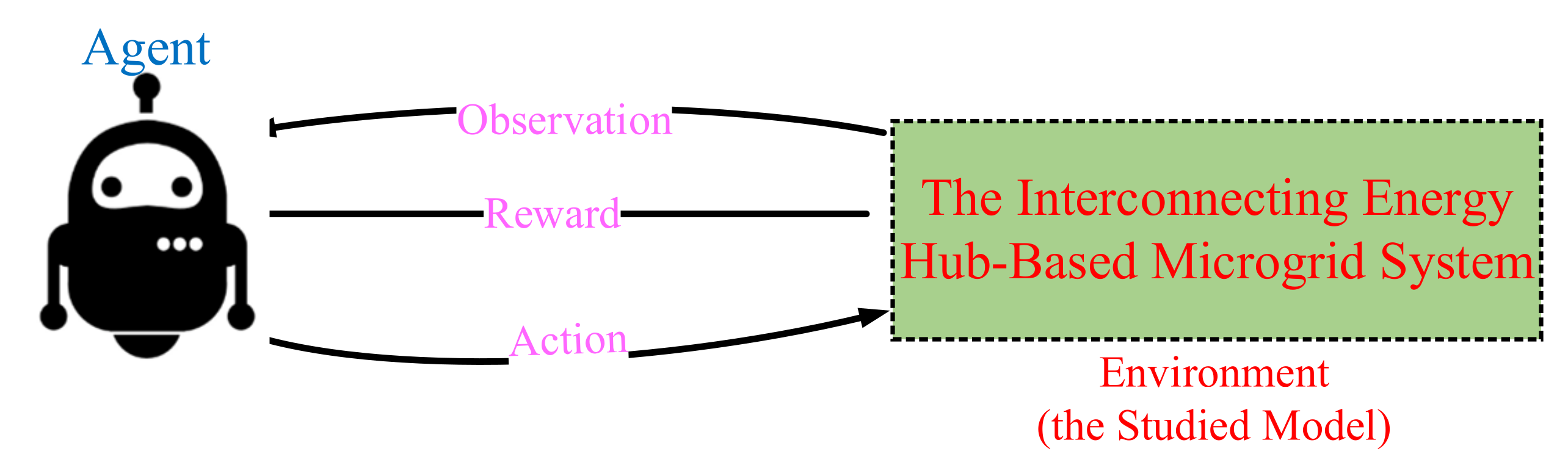
3.2. The Structure Definition of the Proposed IPS-RL Approach
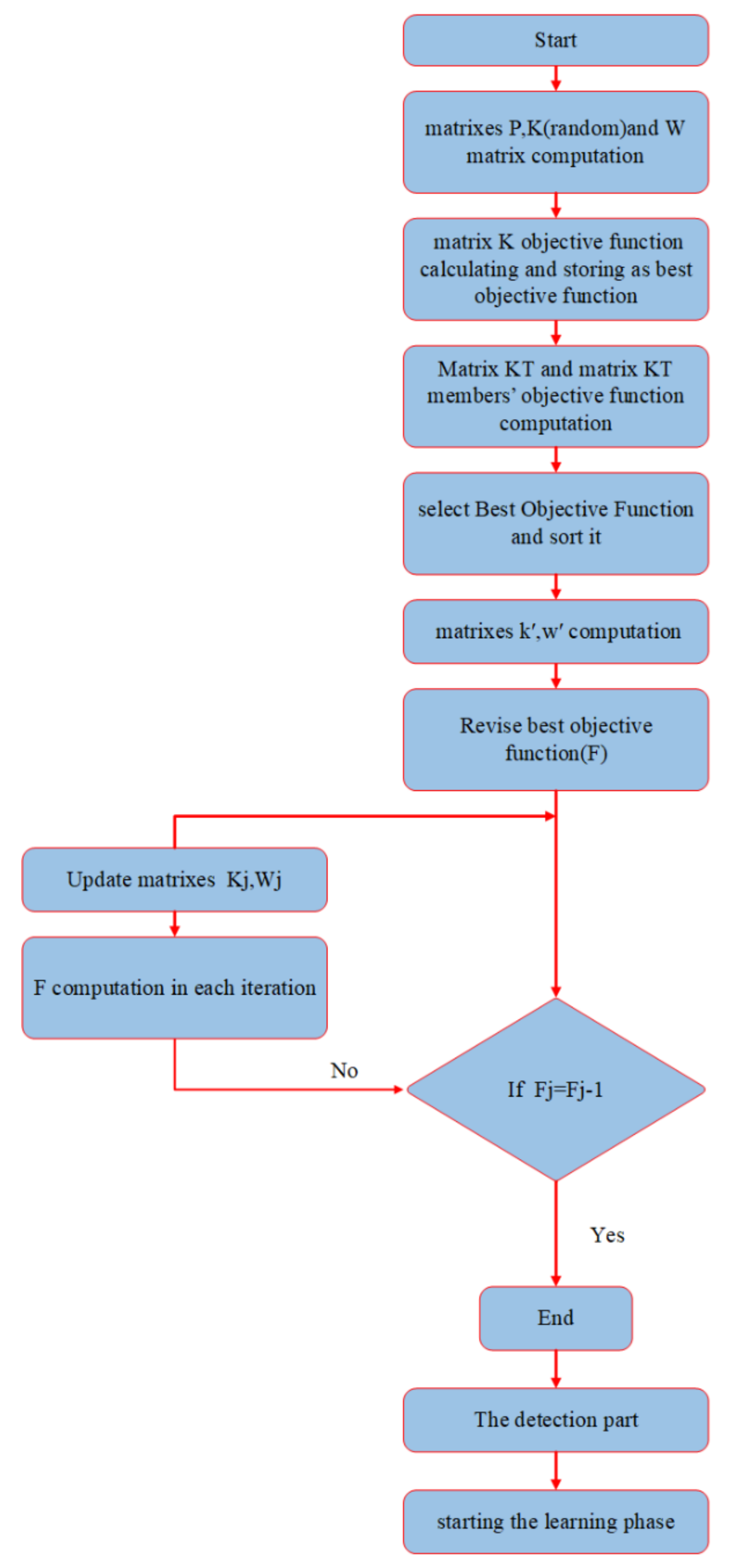
3.3. Intelligent Priority Selection Algorithm
4. Salp Swarm Optimization Algorithm
5. Stochastic Modeling Based on Ut Method
6. Simulation Results
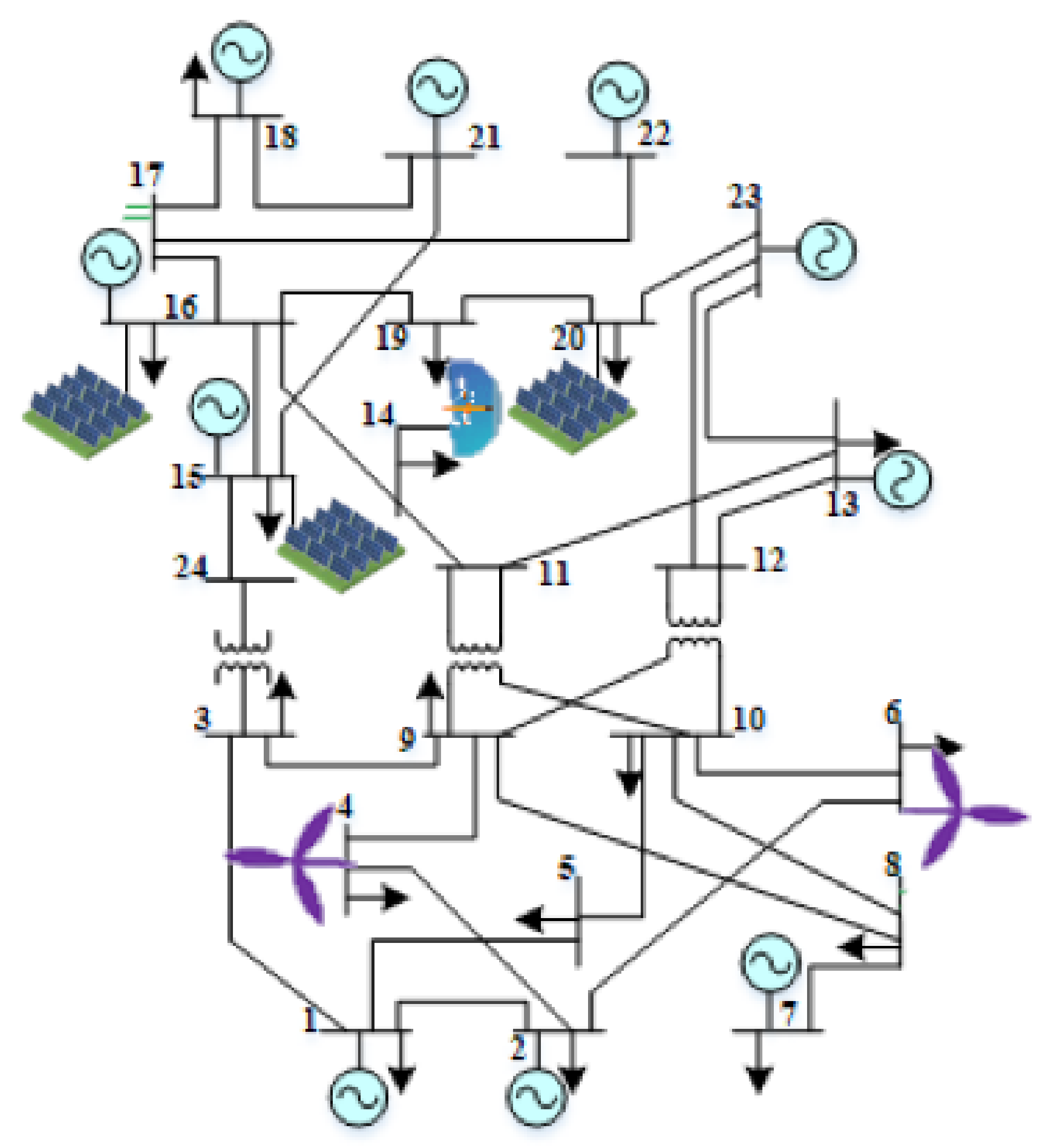
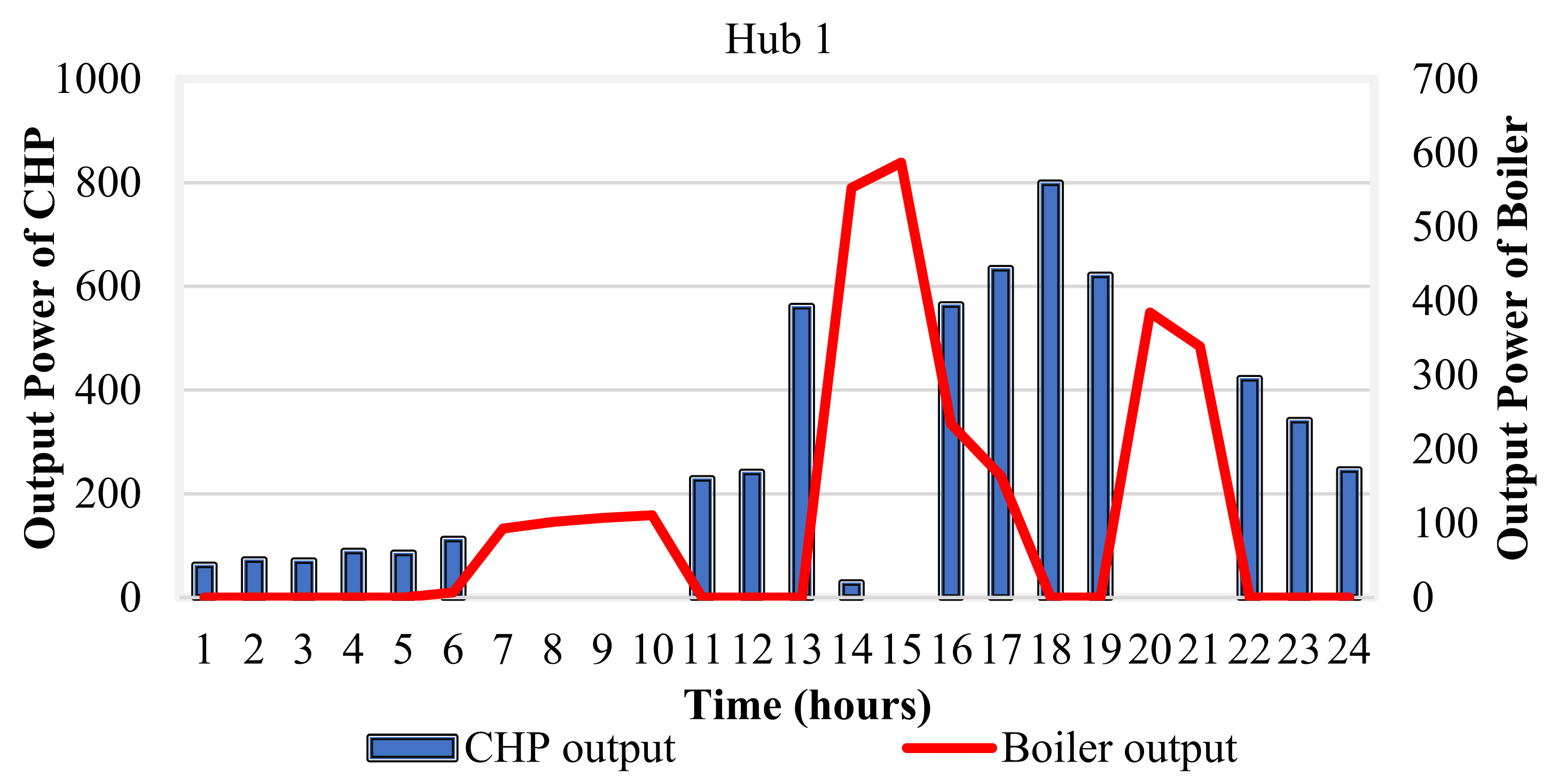
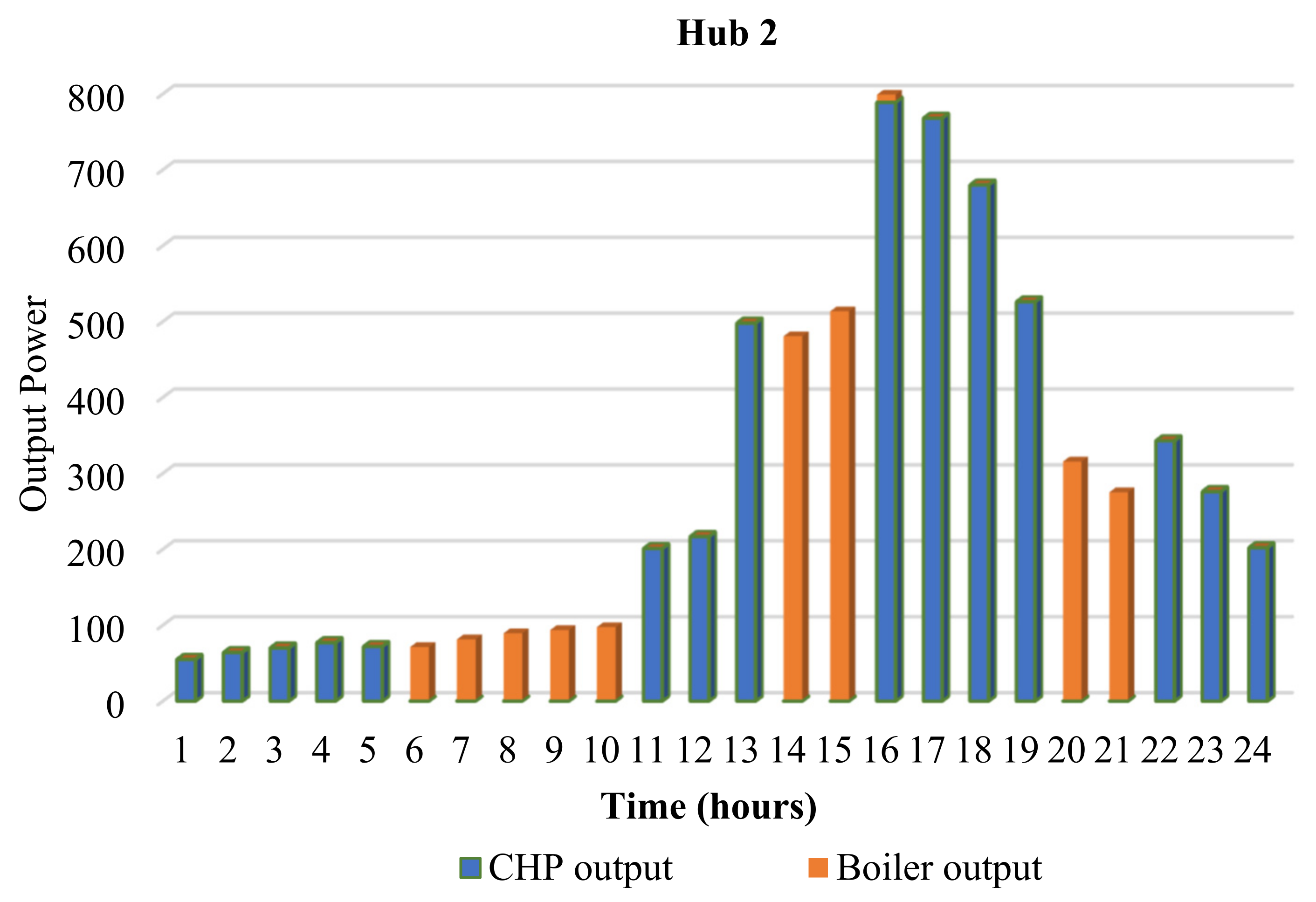
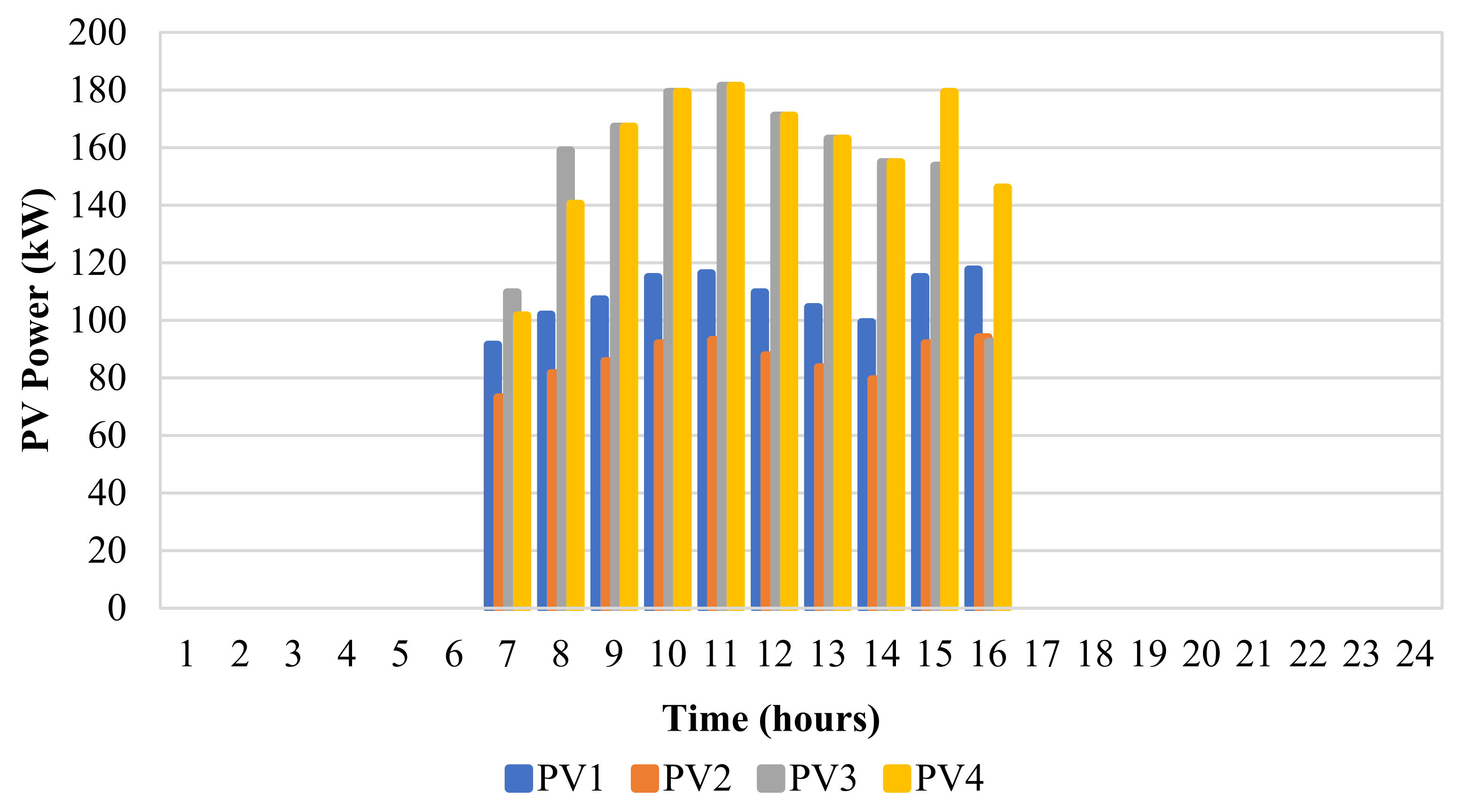
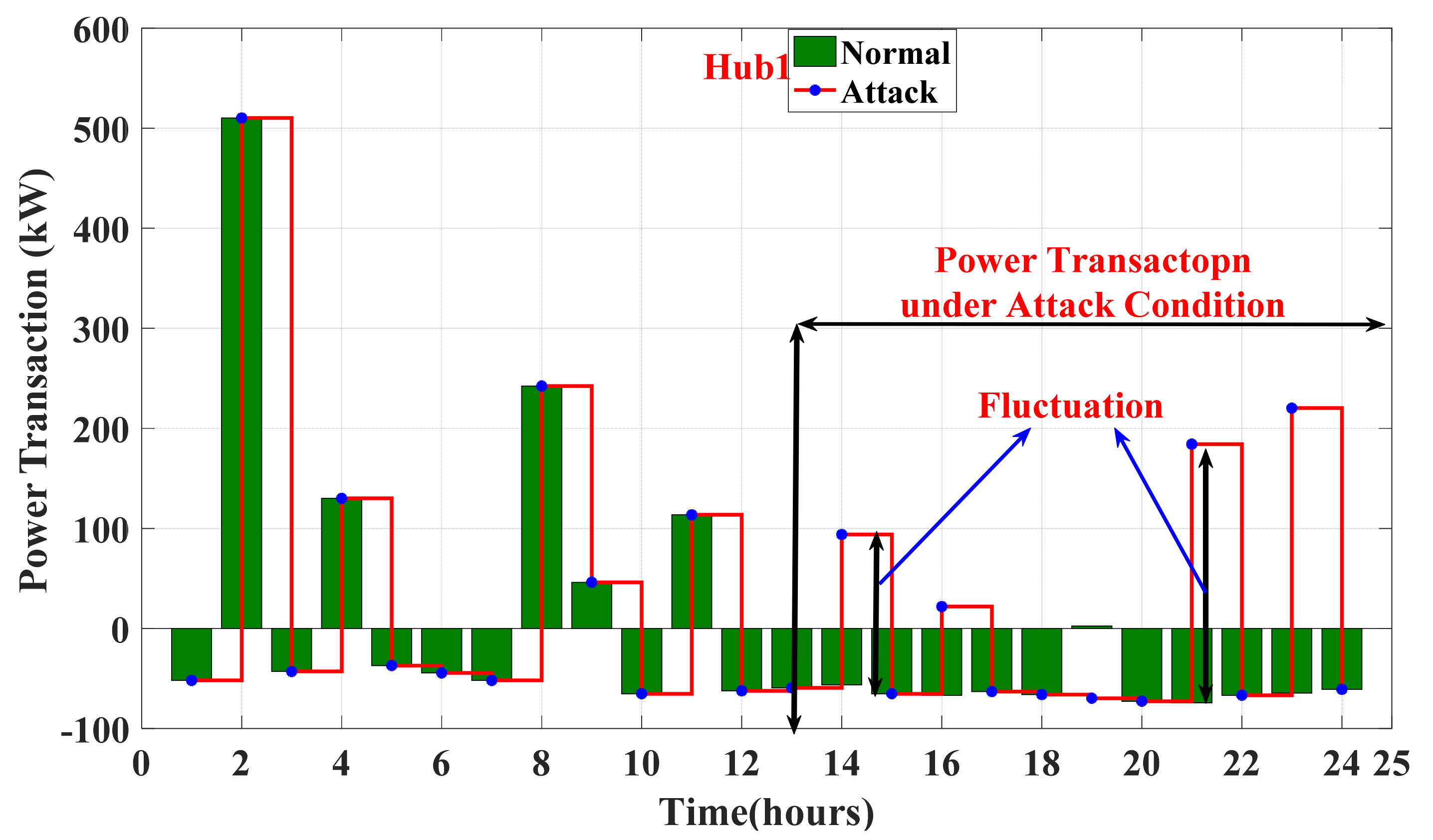
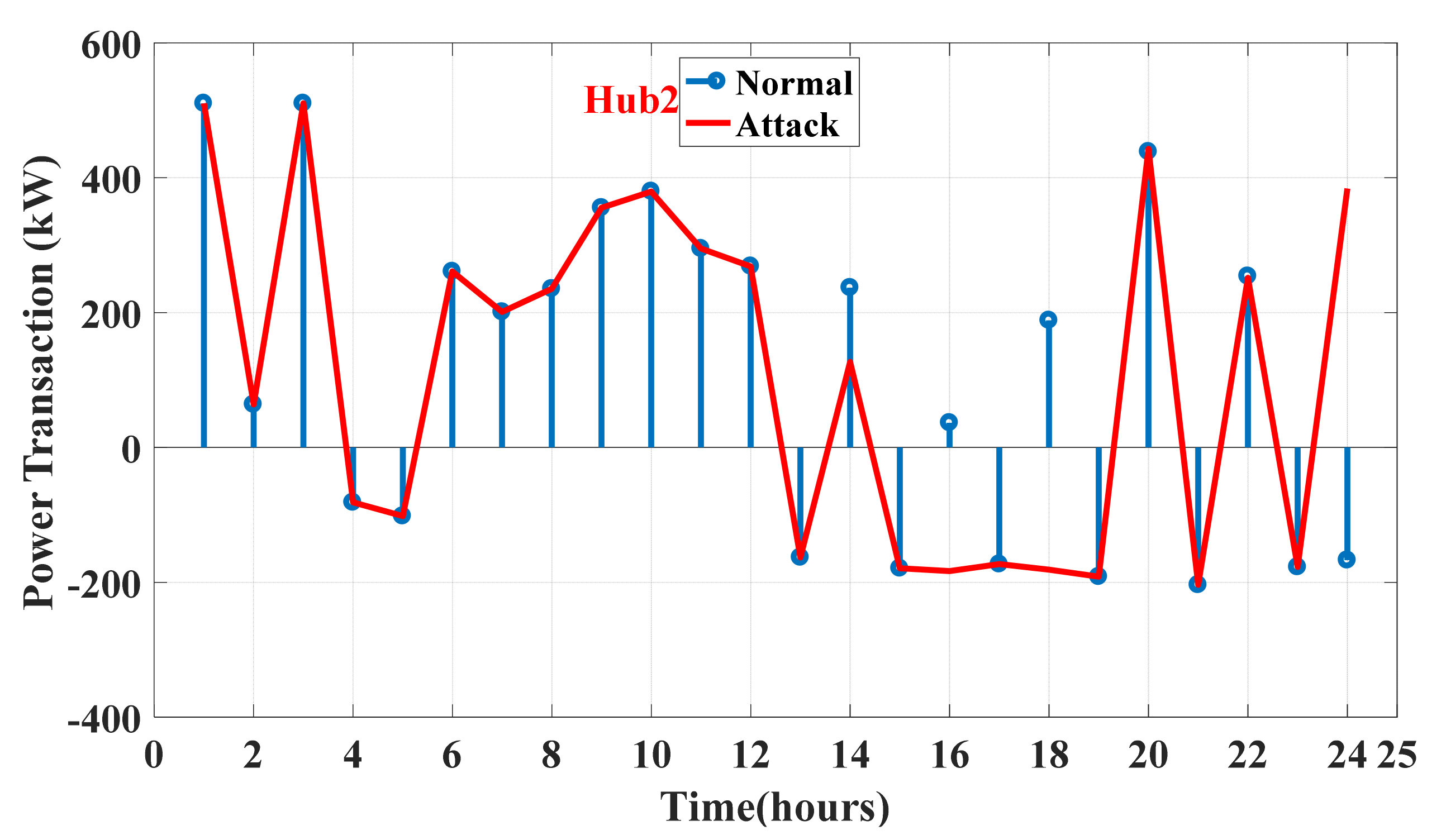
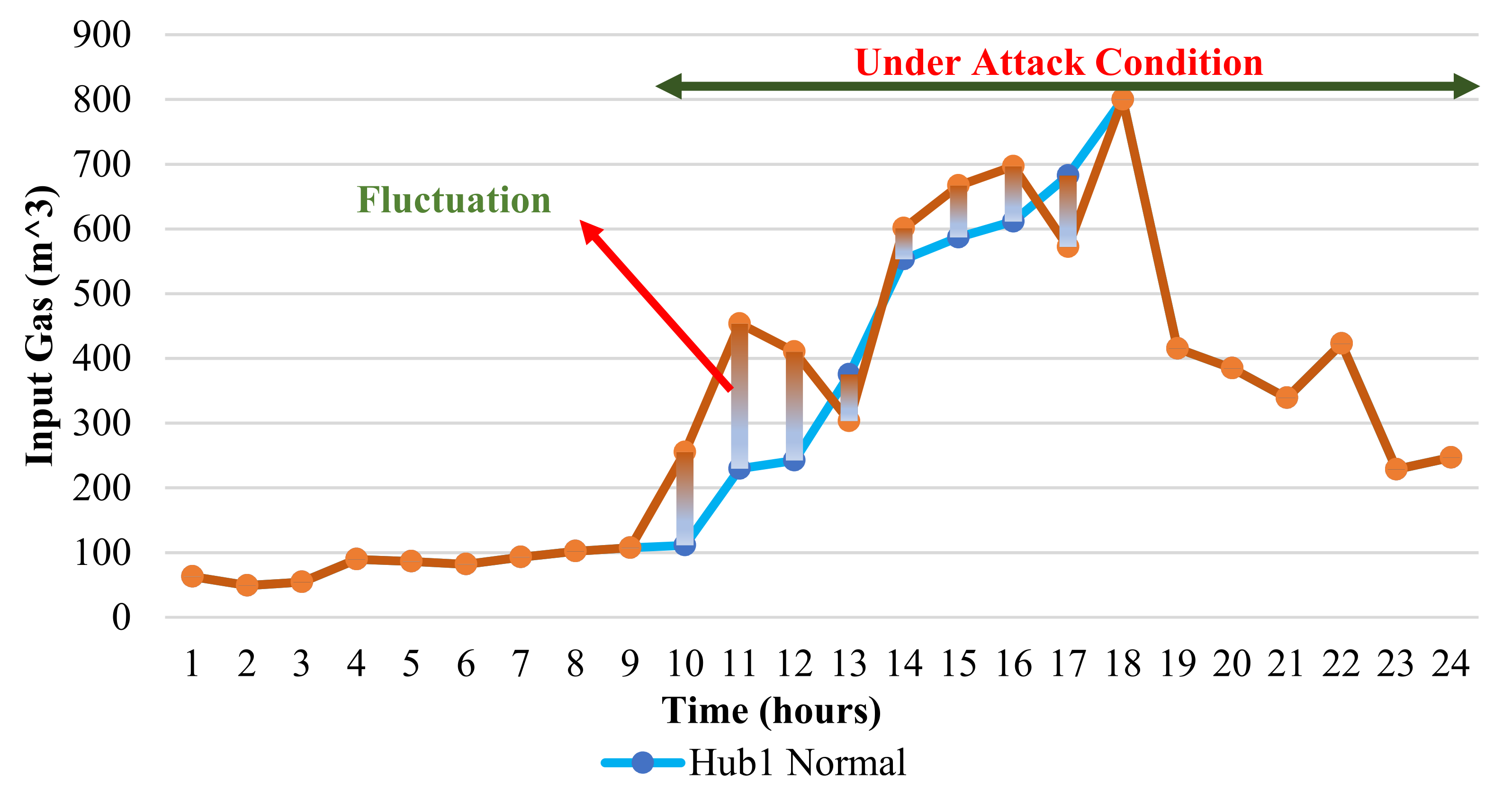
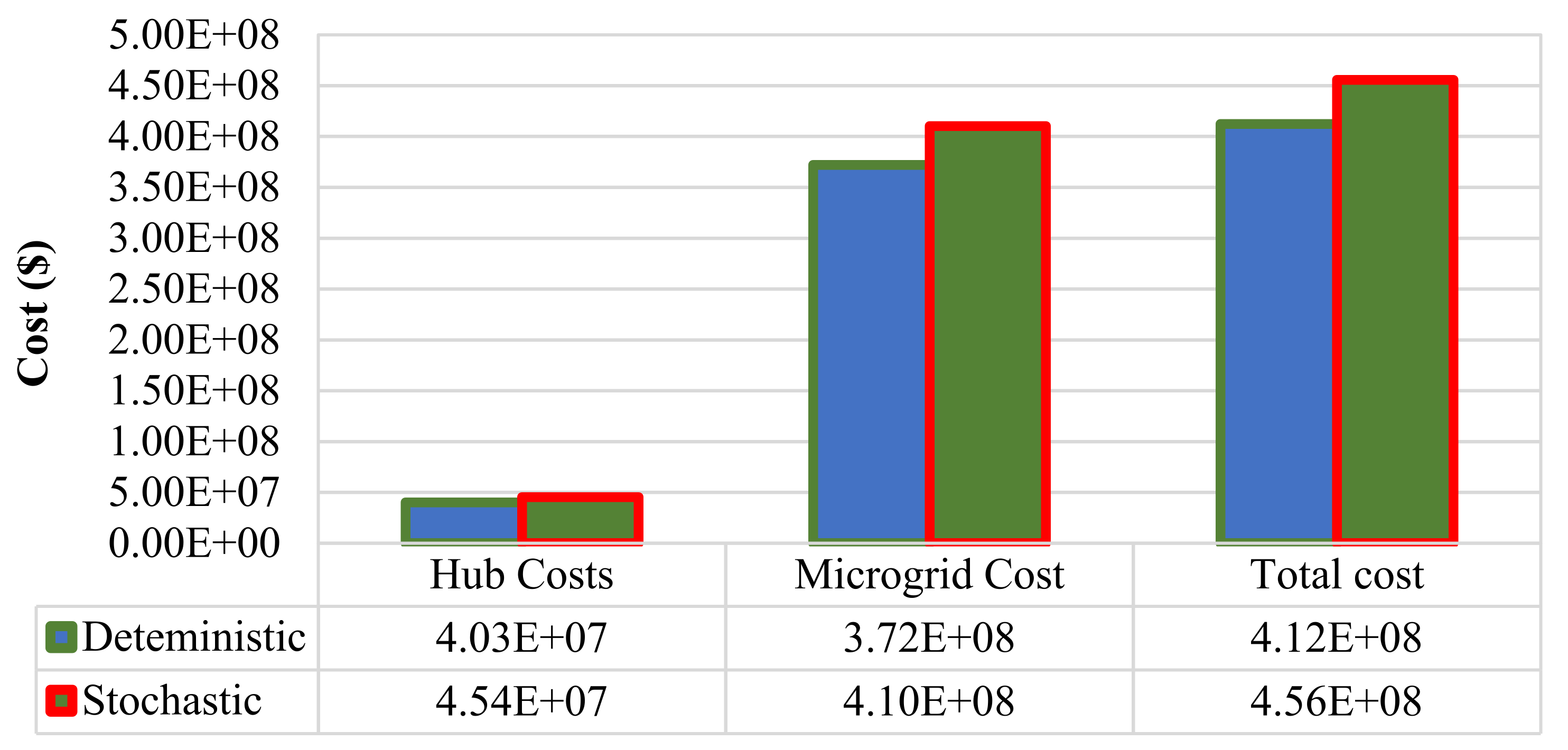
6.1. Energy Management of The Energy Hub-Based Networked Microgrid System
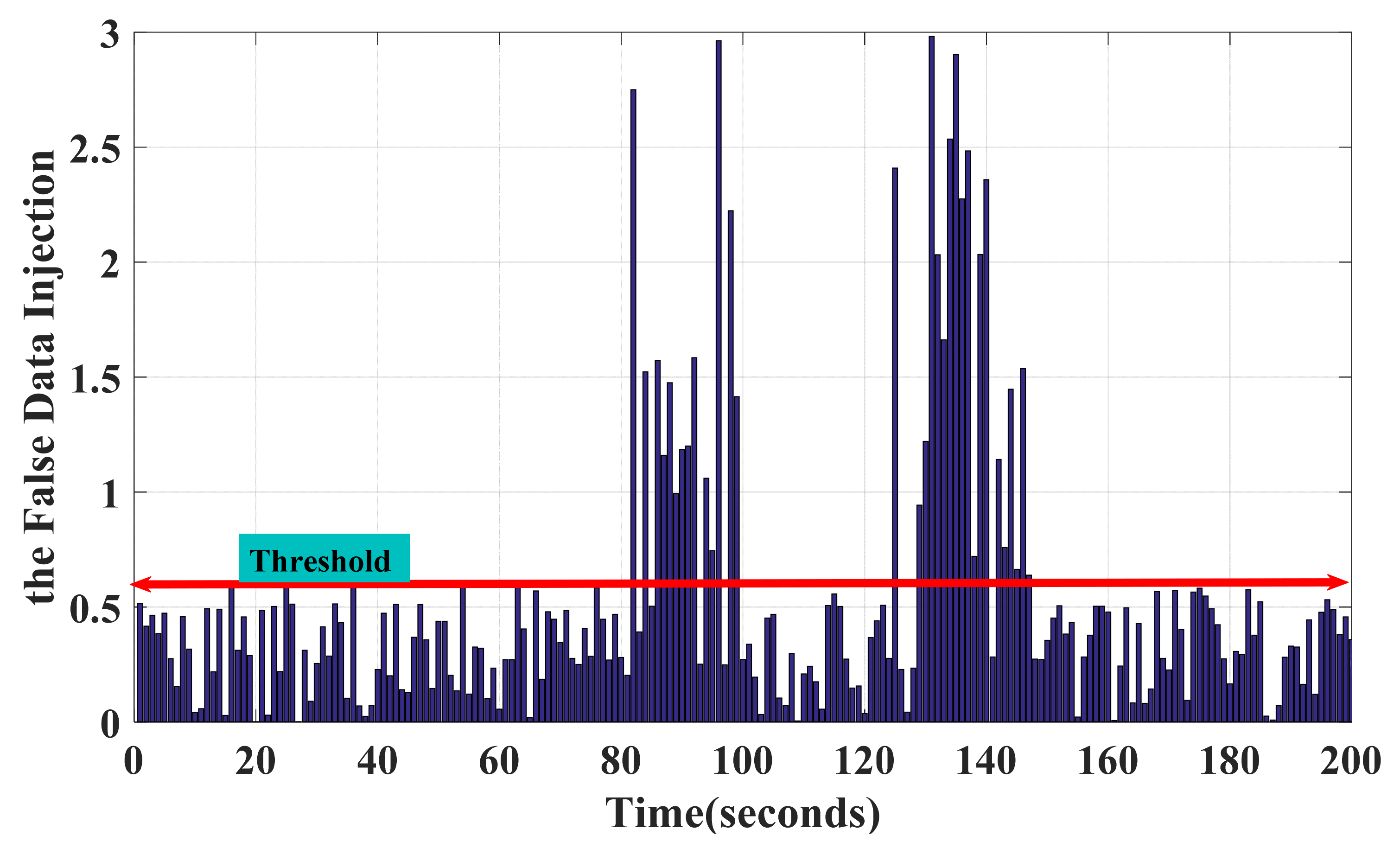
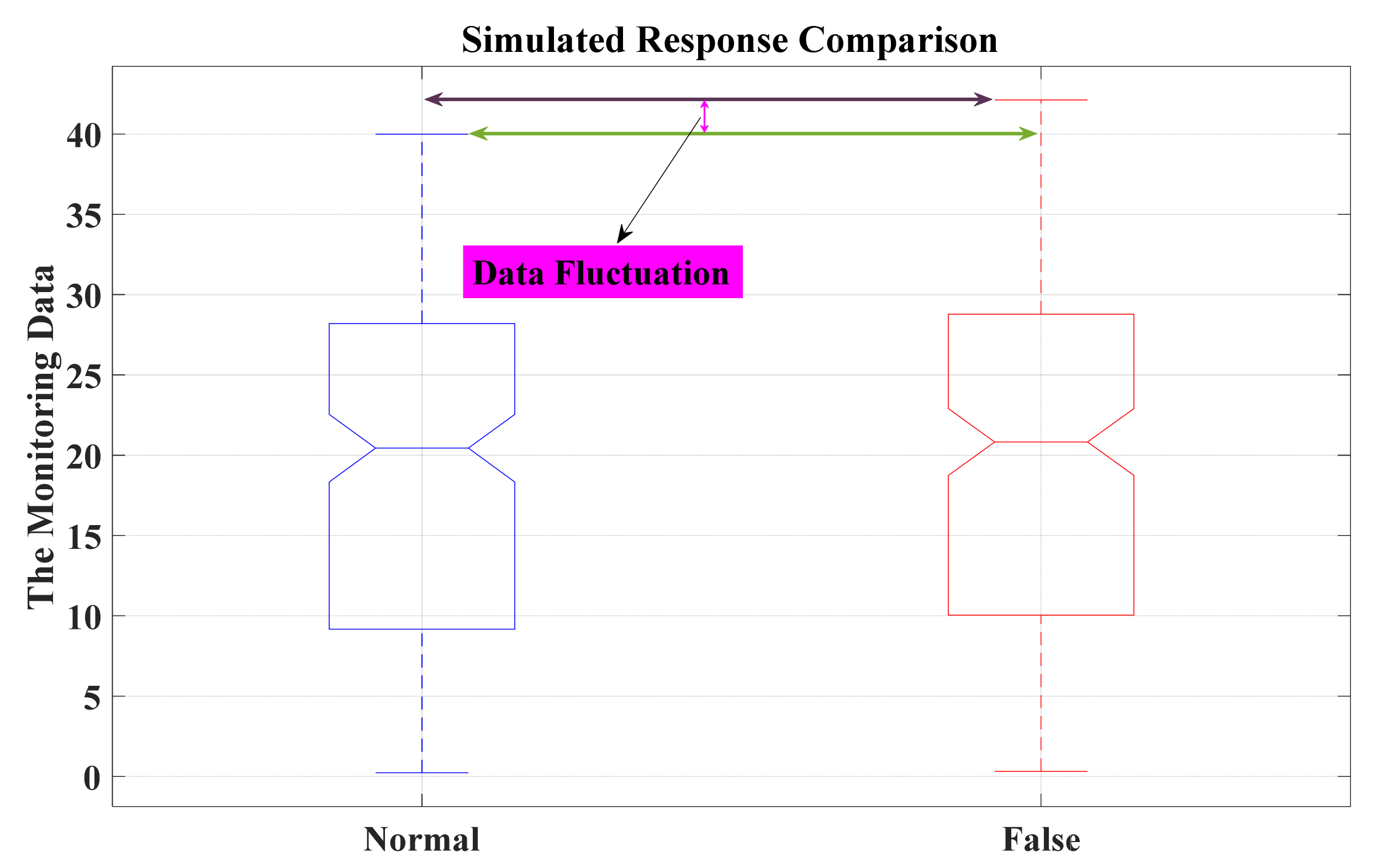
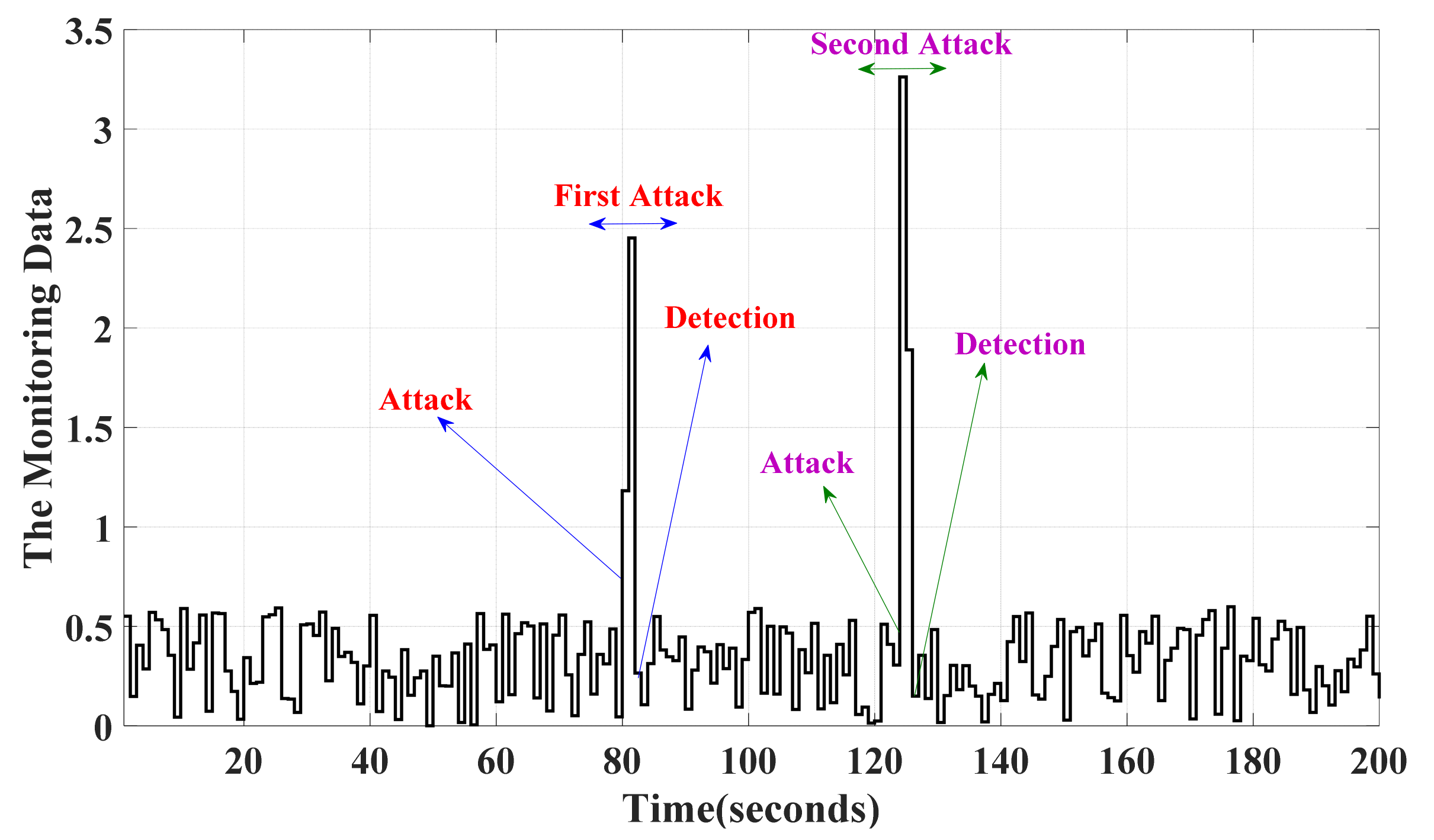
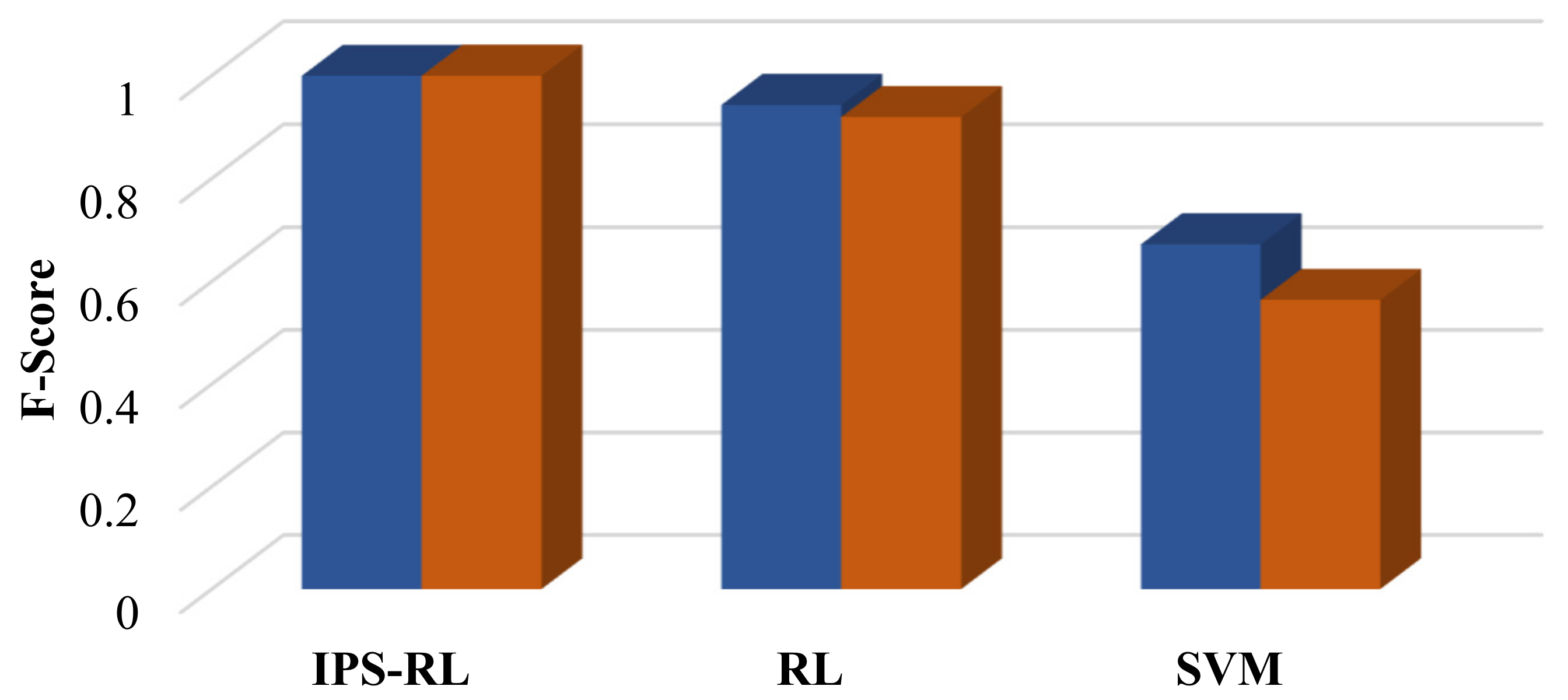
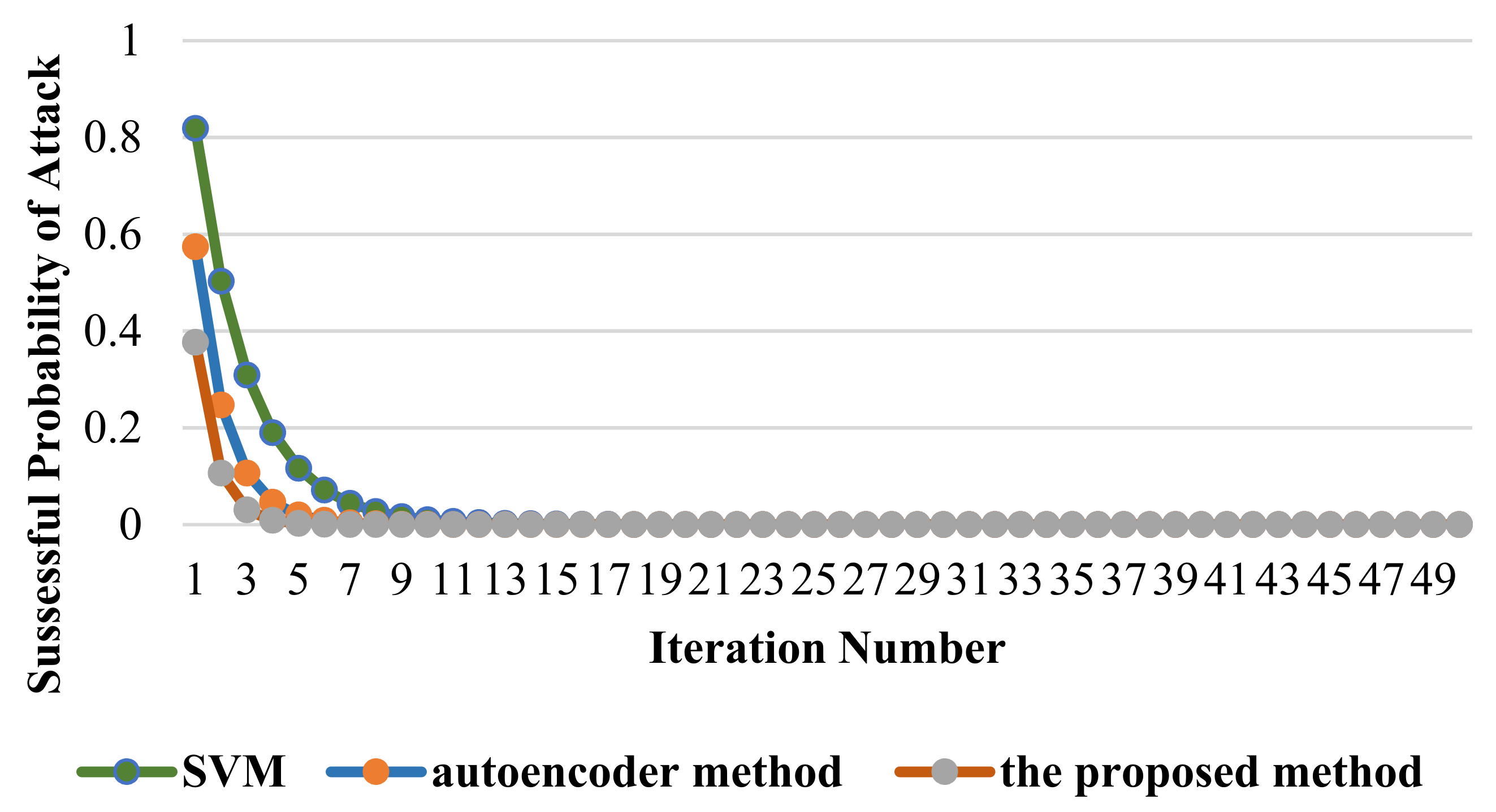
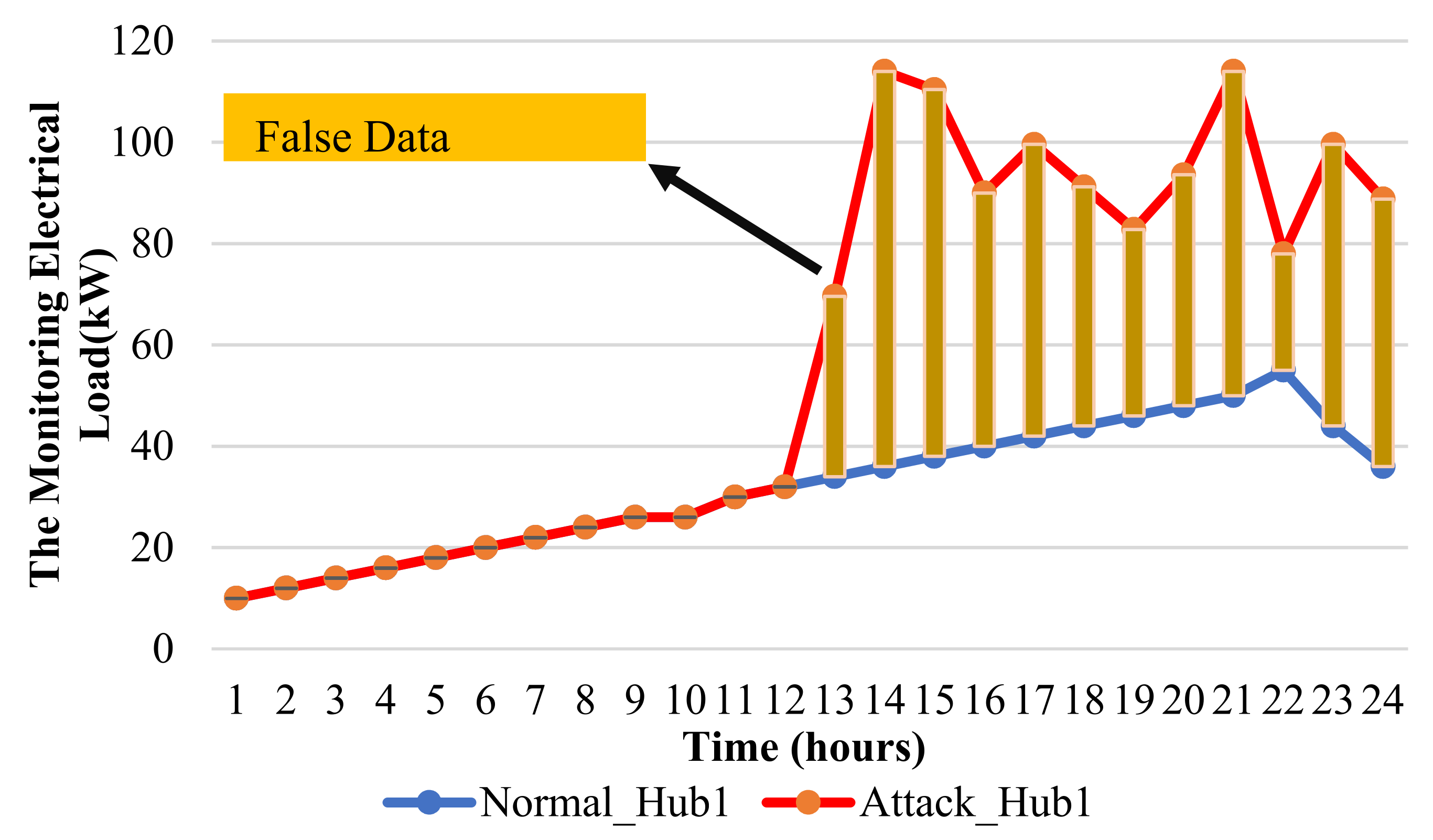
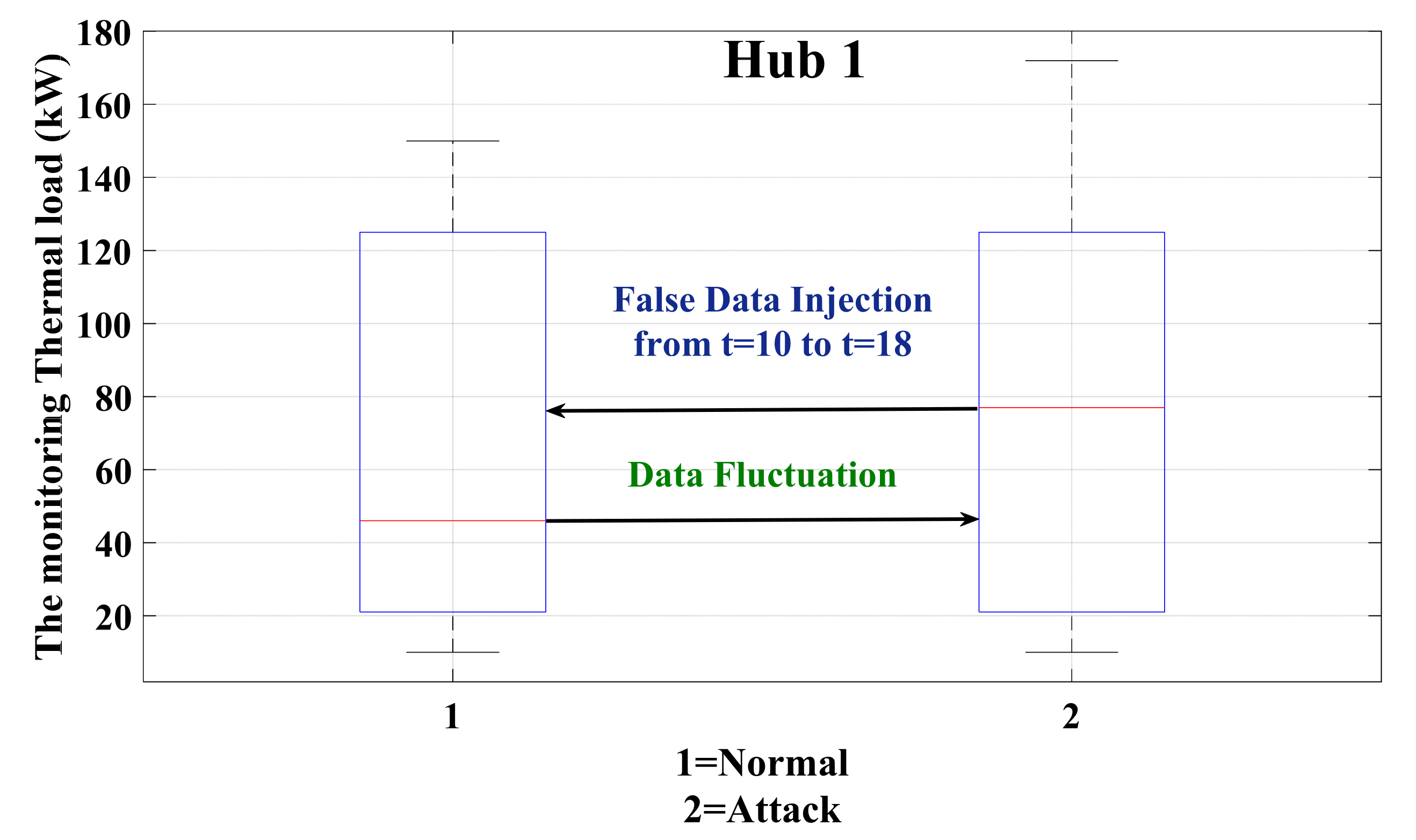
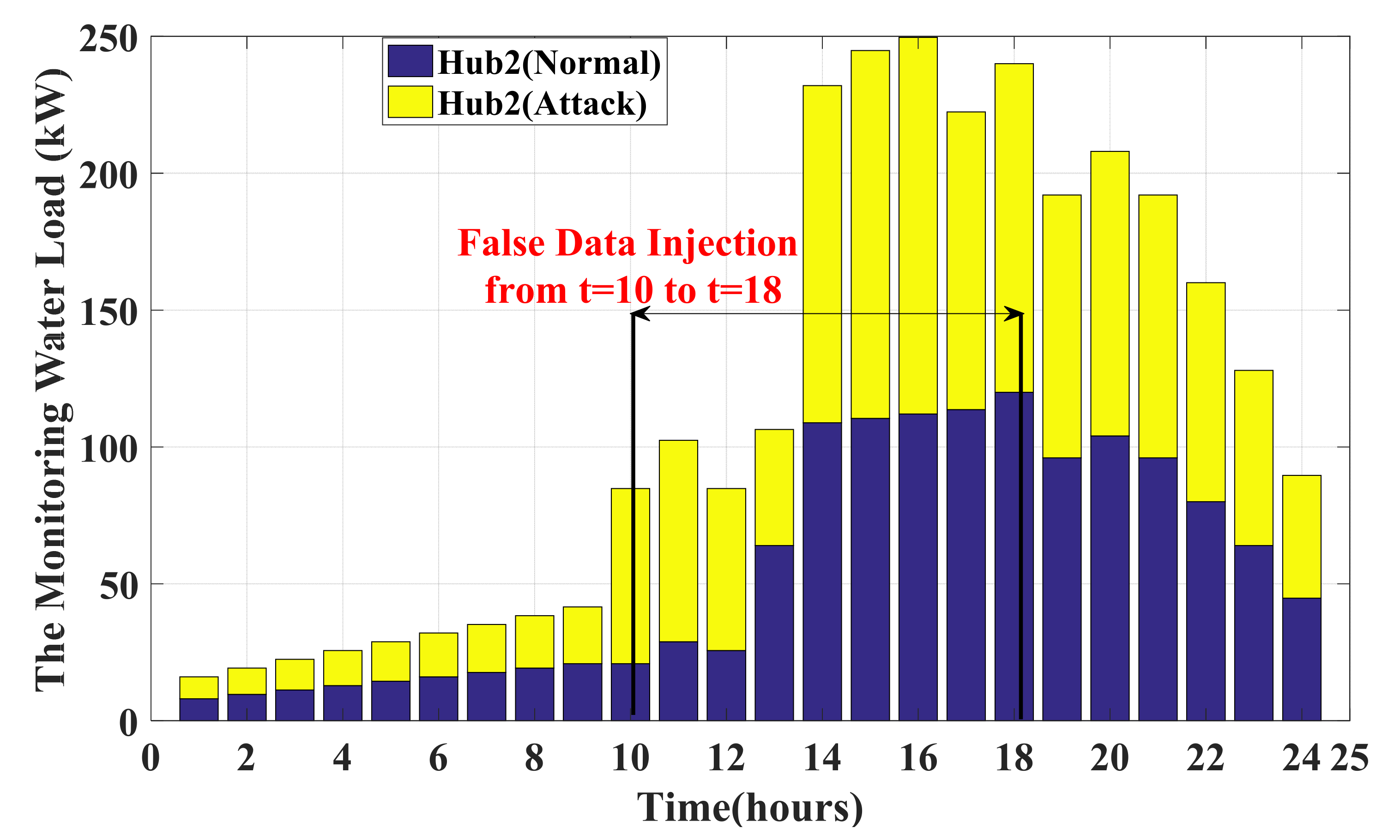
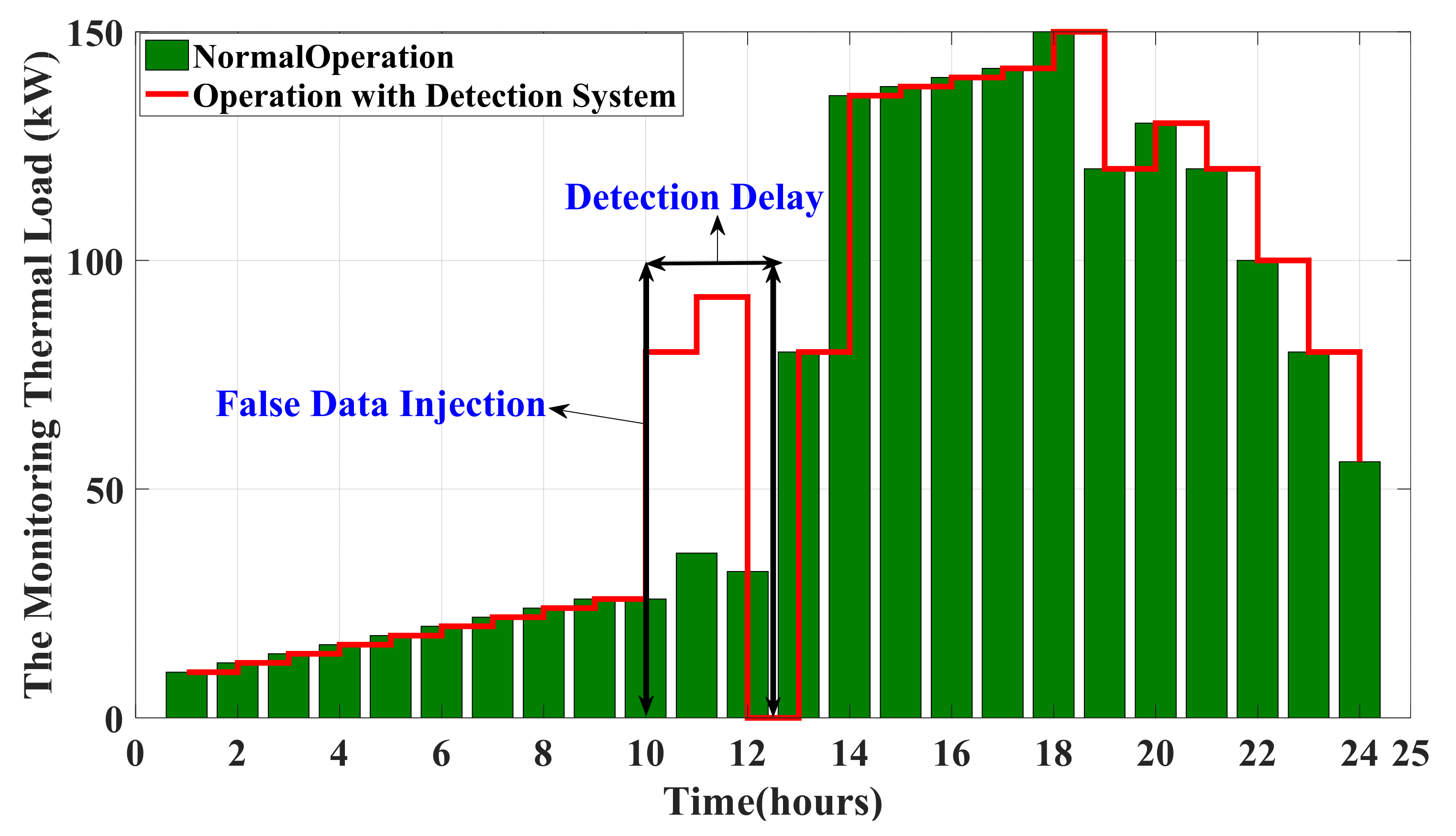
6.2. Assessing and Validating the IPS-RL Method Based Detection Scheme against Malicious Attacks
6.3. Effects of Uncertainties on the Performance of the Studied System
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Nomenclature
| Set/Indices of bats, = {1,…, r}. | |
| Set/Indices of time, = {1,…, 24}. | |
| Set/Indices of units, = {1,…, i}. | |
| , , , , , | Efficiencies of electrical transformer, gas-electricity conversion of CHP, gas-electricity conversion of the boiler, gas to heat conversion of CHP, gas-heat conversion of boiler, battery energy exchange, respectively. |
| , | The max/min of multi-EH power transaction, respectively. |
| , | The max/min of energy level of the battery, respectively. |
| , | The max/min of power exchange of the battery, respectively. |
| , | Electrical demand of the multi-EH system, thermal demand of the multi-EH, respectively. |
| , | The max/min of input water of the desalination unit, respectively. |
| , , | Nominal capacities of the transformer, CHP, and boiler units, respectively. |
| , , | Direct normal irradiation, solar radiation, and power loss of PV, respectively. |
| , , | Wind density, area of rotor blades, and wind speed, respectively. |
| , , | The power capture coefficient, seawater density and swept area of the turbine blades, respectively. |
| The loss efficiency of energy storage system. | |
| The energy coefficient of desalination system (KW/Lit). | |
| Random value between [0, 1]. | |
| The attack time | |
| False data | |
| ,, , , | Operation costs of the networked microgrid system, PVs, WTs, tidal units, and cost of power transaction from multi-EH system to the networked microgrid, respectively. |
| , , , , , | Multi-EH system, CHP, boiler, energy storage system, water supply system, power transaction from networked microgrid to the multi-EH system, respectively. |
| , , , , , | Power generation of PVs, WTs, tidal units, power transaction to/from multi-EH system to/from networked microgrid, power injection through the lines, and electrical demands of the networked microgrid, respectively. |
| , , , , | CHP input gas power, boiler input gas power, power exchange of the energy storage system, the power consumption of desalination unit and gas demand of the multi-EH, respectively. |
| , , , , , , | Secondary tank water volume, desalination unit output water, consumed water from the grid, secondary tank output water, desalination unit water volume, desalination unit input water, binary variable, respectively. |
| The Energy level of the battery. | |
| Reward binary variable. | |
| Receiving reward at t | |
| Estimation of likelihood | |
| Energy of PV | |
| Tidal current speed |
References
- Mohamed, M.A.; Jin, T.; Su, W. Multi-agent energy management of smart islands using primal-dual method of multipliers. Energy 2020, 208, 118306. [Google Scholar] [CrossRef]
- Lan, T.; Liu, X.; Wang, S.; Jermsittiparsert, K.; Alrashood, S.T.; Rezaei, M.; Al-Ghussain, L.; Mohamed, M.A. An advanced machine learning based energy management of renewable microgrids considering hybrid electric vehicles’ charging demand. Energies 2021, 14, 569. [Google Scholar] [CrossRef]
- Al-Ghussain, L.; Ahmad, A.D.; Abubaker, A.M.; Mohamed, M.A. An integrated photovoltaic/wind/biomass and hybrid energy storage systems towards 100% renewable energy microgrids in university campuses. Sustain. Energy Technol. Assess. 2021, 46, 101273. [Google Scholar]
- Xia, T.; Rezaei, M.; Dampage, U.; Alharbi, S.A.; Nasif, O.; Borowski, P.F.; Mohamed, M.A. Techno-Economic Assessment of a Grid-Independent Hybrid Power Plant for Co-Supplying a Remote Micro-Community with Electricity and Hydrogen. Processes 2021, 9, 1375. [Google Scholar] [CrossRef]
- Al-Ghussain, L.; Ahmad, A.D.; Abubaker, A.M.; Abujubbeh, M.; Almalaq, A.; Mohamed, M.A. A Demand-Supply Matching-Based Approach for Mapping Renewable Resources Towards 100% Renewable Grids in 2050. IEEE Access 2021, 9, 58634–58651. [Google Scholar] [CrossRef]
- Mohamed, M.A.; Almalaq, A.; Abdullah, H.M.; Alnowibet, K.A.; Alrasheedi, A.F.; Zaindin, M.S.A. A Distributed Stochastic Energy Management Framework Based-Fuzzy-PDMM for Smart Grids Considering Wind Park and Energy Storage Systems. IEEE Access 2021, 9, 46674–46685. [Google Scholar] [CrossRef]
- Mostafa, M.H.; Ali, S.G.; Ćalasan, M.; Abdelaziz, A.Y.; Aleem, S.H.A. Scenario-Based Approach for Efficient Energy Management in Microgrids Considering Parameters Uncertainty. In Proceedings of the 25th International Conference on Information Technology IT, Zabljak, Montenegro, 16–20 February 2021; pp. 1–7. [Google Scholar]
- Tan, H.; Ren, Z.; Yan, W.; Wang, Q.; Mohamed, M.A. Wind Power Accommodation Capability Assessment Method for Multi-Energy Microgrids. IEEE Trans. Sustain. Energy 2021, 12, 2482–2492. [Google Scholar] [CrossRef]
- Yin, F.; Hajjiah, A.; Jermsittiparsert, K.; Al-Sumaiti, A.S.; Elsayed, S.K.; Ghoneim, S.S.M.; Mohamed, M.A. A secured social-economic framework based on PEM-blockchain for optimal scheduling of reconfigurable interconnected microgrids. IEEE Access 2021, 9, 40797–40810. [Google Scholar] [CrossRef]
- Wang, P.; Wang, D.; Zhu, C.; Yang, Y.; Abdullah, H.M.; Mohamed, M.A. Stochastic management of hybrid AC/DC microgrids considering electric vehicles charging demands. Energy Rep. 2020, 6, 1338–1352. [Google Scholar] [CrossRef]
- Javanmard, B.; Tabrizian, M.; Ansarian, M.; Ahmarinejad, A. Energy management of multi-microgrids based on game theory approach in the presence of demand response programs, energy storage systems and renewable energy resources. J. Energy Storage 2021, 42, 102971. [Google Scholar] [CrossRef]
- Divshali, P.H.; Choi, B.J.; Liang, H. Multi-agent transactive energy management system considering high levels of renewable energy source and electric vehicles. IET Gener. Transmiss. Distrib. 2017, 11, 3713–3721. [Google Scholar] [CrossRef] [Green Version]
- İnci, M.; Büyük, M.; Demir, M.H.; İlbey, G. A review and research on fuel cell electric vehicles: Topologies, power electronic converters, energy management methods, technical challenges, marketing and future aspects. Renew. Sustain. Energy Rev. 2021, 137, 110648. [Google Scholar] [CrossRef]
- Espín-Sarzosa, D.; Palma-Behnke, R.; Núñez-Mata, O. Energy management systems for microgrids: Main existing trends in centralized control architectures. Energies 2020, 13, 547. [Google Scholar] [CrossRef] [Green Version]
- Zhou, B.; Zou, J.; Chung, C.Y.; Wang, H.; Liu, N.; Voropai, N.; Xu, D. Multi-microgrid Energy Management Systems: Architecture, Communication, and Scheduling Strategies. J. Mod. Power Syst. Clean Energy 2021, 9, 463–476. [Google Scholar] [CrossRef]
- Rocha, H.R.; Honorato, I.H.; Fiorotti, R.; Celeste, W.C.; Silvestre, L.J.; Silva, J.A. An Artificial Intelligence based scheduling algorithm for demand-side energy management in Smart Homes. Appl. Energy 2021, 282, 116145. [Google Scholar] [CrossRef]
- Miglani, A.; Kumar, N.; Chamola, V.; Zeadally, S. Blockchain for Internet of Energy management: Review, solutions, and challenges. Comput. Commun. 2020, 151, 395–418. [Google Scholar] [CrossRef]
- Ranjan, S.; Moin, S.; Vashist, P.; Uddin, A.S.M. Role of Cyber-Security in Smart Energy Management Systems. Sustain. Energy Technol. Assess. 2021, 10, 1–18. [Google Scholar]
- Najafi, A.; Tavakoli, A.; Pourakbari-Kasmaei, M.; Lehtonen, M. A risk-based optimal self-scheduling of smart energy hub in the day-ahead and regulation markets. J. Clean. Prod. 2021, 279, 123631. [Google Scholar] [CrossRef]
- Wang, F.; Xu, H.; Xu, T.; Li, K.; Shafie-Khah, M.; Catalão, J.P. The values of market-based demand response on improving power system reliability under extreme circumstances. Appl. Energy 2017, 193, 220–231. [Google Scholar] [CrossRef]
- Tan, H.; Yan, W.; Ren, Z.; Wang, Q.; Mohamed, M.A. A robust dispatch model for integrated electricity and heat networks considering price-based integrated demand response. Energy 2022, 239, 121875. [Google Scholar] [CrossRef]
- Jadidbonab, M.; Mohammadi-Ivatloo, B.; Marzband, M.; Siano, P. Short-term self-scheduling of virtual energy hub plant within thermal energy market. IEEE Trans. Ind. Electron. 2020, 68, 3124–3136. [Google Scholar] [CrossRef] [Green Version]
- Chassin, D.P.; Behboodi, S.; Shi, Y.; Djilali, N. H2-optimal transactive control of electric power regulation from fast-acting demand response in the presence of high renewables. Appl. Energy 2017, 205, 304–315. [Google Scholar] [CrossRef]
- Cesena, E.A.M.; Good, N.; Syrri, A.L.; Mancarella, P. Techno-economic and business case assessment of multi-energy microgrids with co-optimization of energy, reserve and reliability services. Appl. Energy 2018, 210, 896–913. [Google Scholar] [CrossRef]
- Behboodi, S.; Chassin, D.P.; Djilali, N.; Crawford, C. Transactive control of fast-acting demand response based on thermostatic loads in realtime retail electricity markets. Appl. Energy 2018, 210, 1310–1320. [Google Scholar] [CrossRef]
- Wu, J.; Guan, X. Coordinated multi-microgrids optimal control algorithm for smart distribution management system. IEEE Trans. Smart Grid 2013, 4, 2174–2181. [Google Scholar] [CrossRef]
- Zeng, C.; Jiang, Y.; Liu, Y.; Tan, Z.; He, Z.; Wu, S. Optimal Dispatch of Integrated Energy System Considering Energy Hub Technology and Multi-Agent Interest Balance. Energies 2019, 12, 3112. [Google Scholar] [CrossRef] [Green Version]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 ukraine blackout: Implications for false data injection attacks. IEEE Trans. Power Syst. 2017, 32, 3317–3318. [Google Scholar] [CrossRef]
- Liu, Y.; Ning, P.; Reiter, M.K. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. 2011, 14, 1–33. [Google Scholar] [CrossRef]
- Liu, X.; Li, Z.; Liu, X.; Li, Z. Masking transmission line outages via false data injection attacks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1592–1602. [Google Scholar] [CrossRef]
- Deng, R.; Xiao, G.; Lu, R.; Liang, H.; Vasilakos, A.V. False data injection on state estimation in power Systems—Attacks, impacts, and defense: A survey. IEEE Trans. Ind. Informat. 2017, 13, 411–423. [Google Scholar] [CrossRef]
- Rahman, M.A.; Mohsenian-Rad, H. False data injection attacks with incomplete information against smart power grids. In Proceedings of the IEEE Global Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; pp. 3153–3158. [Google Scholar]
- Dehghani, M.; Niknam, T.; Ghiasi, M.; Siano, P.; Alhelou, H.H.; Al-Hinai, A. Fourier Singular Values-Based False Data Injection Attack Detection in AC Smart-Grids. Appl. Sci. 2021, 11, 5706. [Google Scholar] [CrossRef]
- Julier, S.J. The scaled unscented transformation. In Proceedings of the of the 2002 American Control Conference (IEEE Cat. No. CH37301), Anchorage, AK, USA, 8–10 May 2002; IEEE. Volume 6. [Google Scholar]
- Wang, S.; Gao, W.; Meliopoulos, A.P.S. An alternative method for power system dynamic state estimation based on unscented transform. IEEE Trans. Power Syst. 2011, 27, 942–950. [Google Scholar] [CrossRef]
- Xiao, L.; Li, Y.; Han, G.; Liu, G.; Zhuang, W. PHY-layer spoofing detection with reinforcement learning in wireless networks. IEEE Trans. Veh. Technol. 2016, 65, 10037–10047. [Google Scholar] [CrossRef]
- Zou, H.; Tao, J.; Elsayed, S.K.; Elattar, E.E.; Almalaq, A.; Mohamed, M.A. Stochastic multi-carrier energy management in the smart islands using reinforcement learning and unscented transform. Int. J. Electr. Power Energy Syst. 2021, 130, 106988. [Google Scholar] [CrossRef]
- Mirjalili, S.; Gandomi, A.; Mirjalili, S.Z.; Saremi, S.; Faris, H.; Mirjalili, S.M. Salp Swarm Algorithm: A bio-inspired optimizer for engineering design problems. Adv. Eng. Softw. 2017, 114, 163–191. [Google Scholar] [CrossRef]
- Abualigah, L.; Shehab, M.; Alshinwan, M.; Alabool, H. Salp swarm algorithm: A comprehensive survey. Neural Comput. Appl. 2020, 32, 11195–11215. [Google Scholar] [CrossRef]
- Mohamed, M.A.; Hajjiah, A.; Khalid Alnowibet, A.; Alrasheedi, A.F.; Awwad, E.M.; Muyeen, S.M. A Secured Advanced Management Architecture in Peer-to-Peer Energy Trading for Multi-Microgrid in the Stochastic Environment. IEEE Access 2021, 9, 92083–92100. [Google Scholar] [CrossRef]
- Kiros, S.; Khan, B.; Padmanaban, S.; Haes Alhelou, H.; Leonowicz, Z.; Mahela, O.P.; Holm-Nielsen, J.B. Development of Stand-Alone Green Hybrid System for Rural Areas. Sustainability 2020, 12, 3808. [Google Scholar] [CrossRef]
- Gong, X.; Dong, F.; Mohamed, M.A.; Abdalla, O.M.; Ali, Z.M. A secured energy management architecture for smart hybrid microgrids considering PEM-fuel cell and electric vehicles. IEEE Access 2020, 8, 47807–47823. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, X.; Gao, L.; Chen, W.; Li, P. Intelligent fault diagnosis of rotating machinery using a new ensemble deep auto-encoder method. Measurement 2020, 151, 107232. [Google Scholar] [CrossRef]
- Ahmed, I.; Aftab, S.; Ullah, I.; Saeed, M.A.; Husen, A. A Classification Framework to Detect DoS Attacks. Int. J. Comput. Netw. Inf. Secur. 2019, 11, 40–47. [Google Scholar]
- Israr, U.; Fayaz, M.; DoHyeun, K. Analytical modeling for underground risk assessment in smart cities. Appl. Sci. 2018, 8, 921. [Google Scholar]
- Hossain, M.A.; Chakrabortty, R.K.; Ryan, M.J.; Pota, H.R. Energy management of community energy storage in grid-connected microgrid under uncertain real-time prices. Sustain. Cities Soc. 2021, 66, 102658. [Google Scholar] [CrossRef]
- Masrur, H.; Sharifi, A.; Islam, M.R.; Hossain, M.A.; Senjyu, T. Optimal and economic operation of microgrids to leverage resilience benefits during grid outages. Int. J. Electr. Power Energy Syst. 2021, 132, 107137. [Google Scholar] [CrossRef]


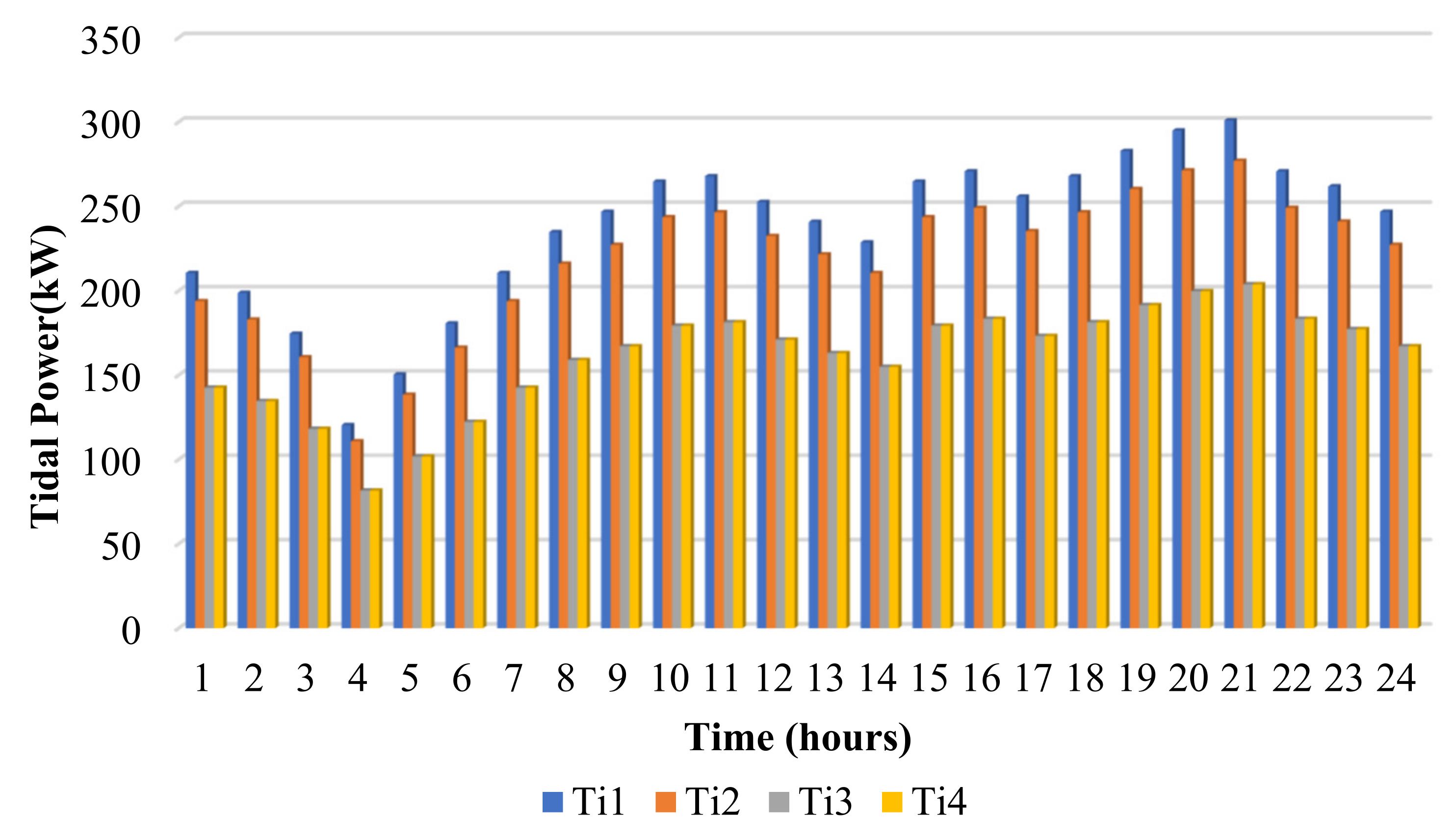
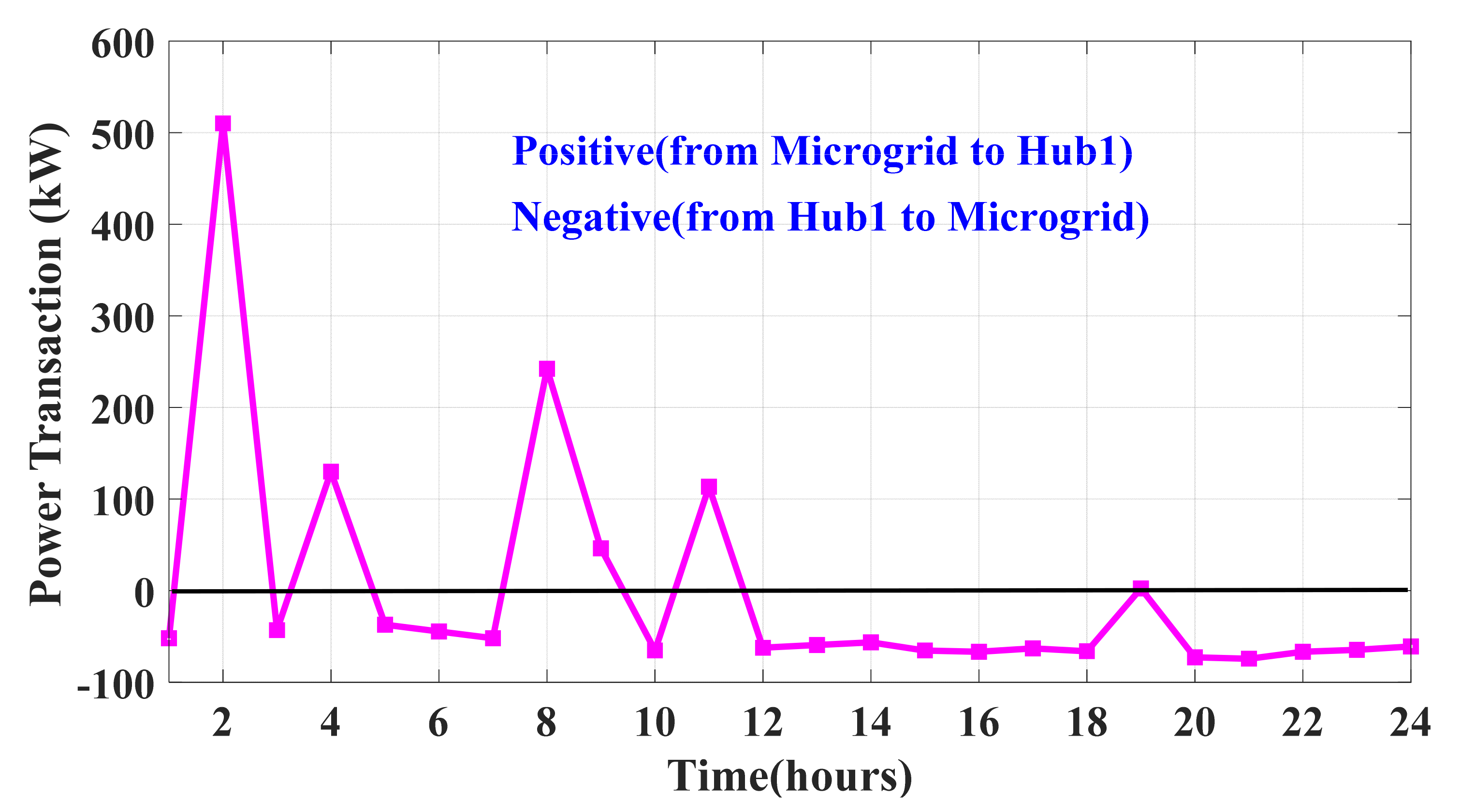
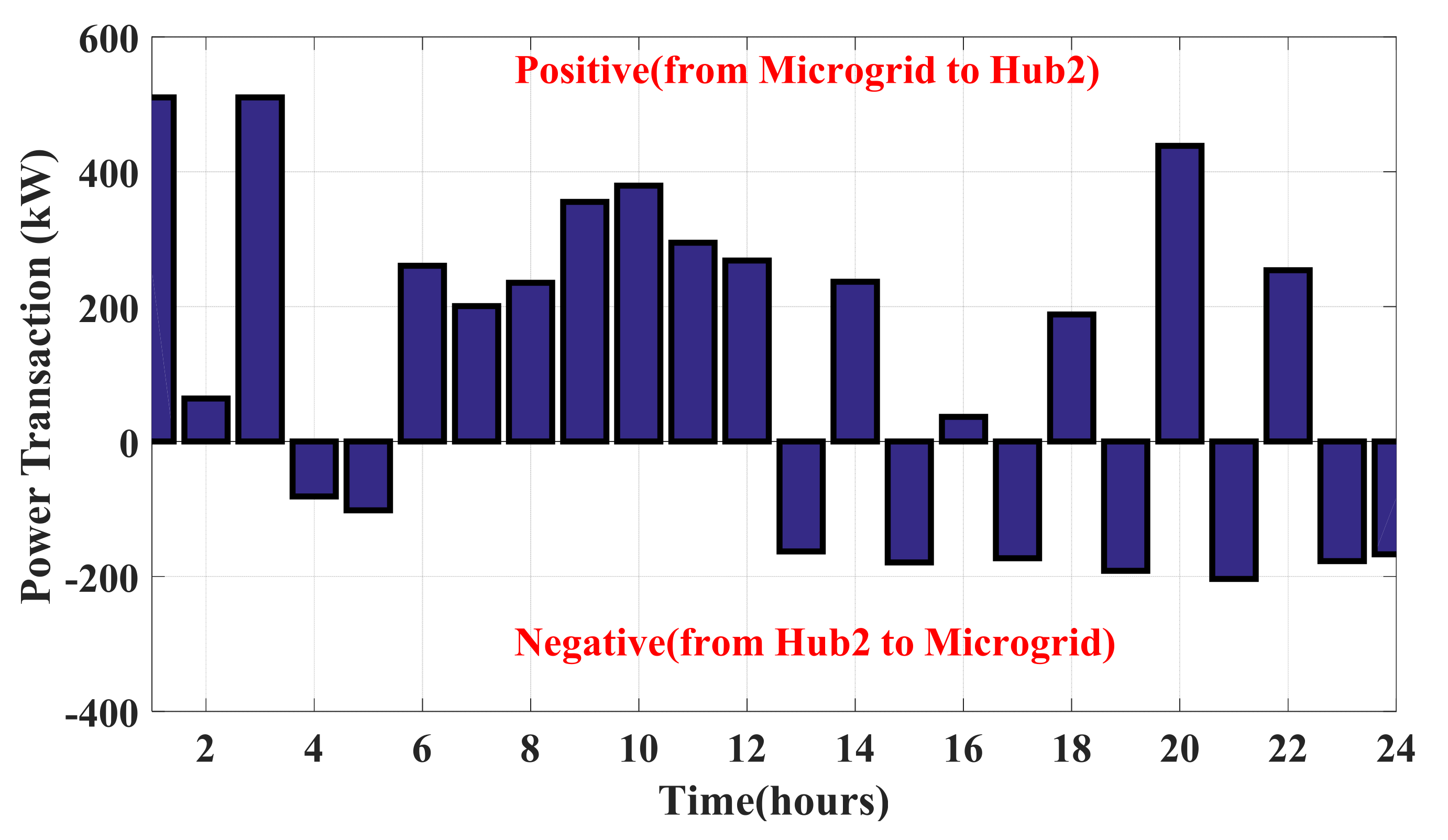
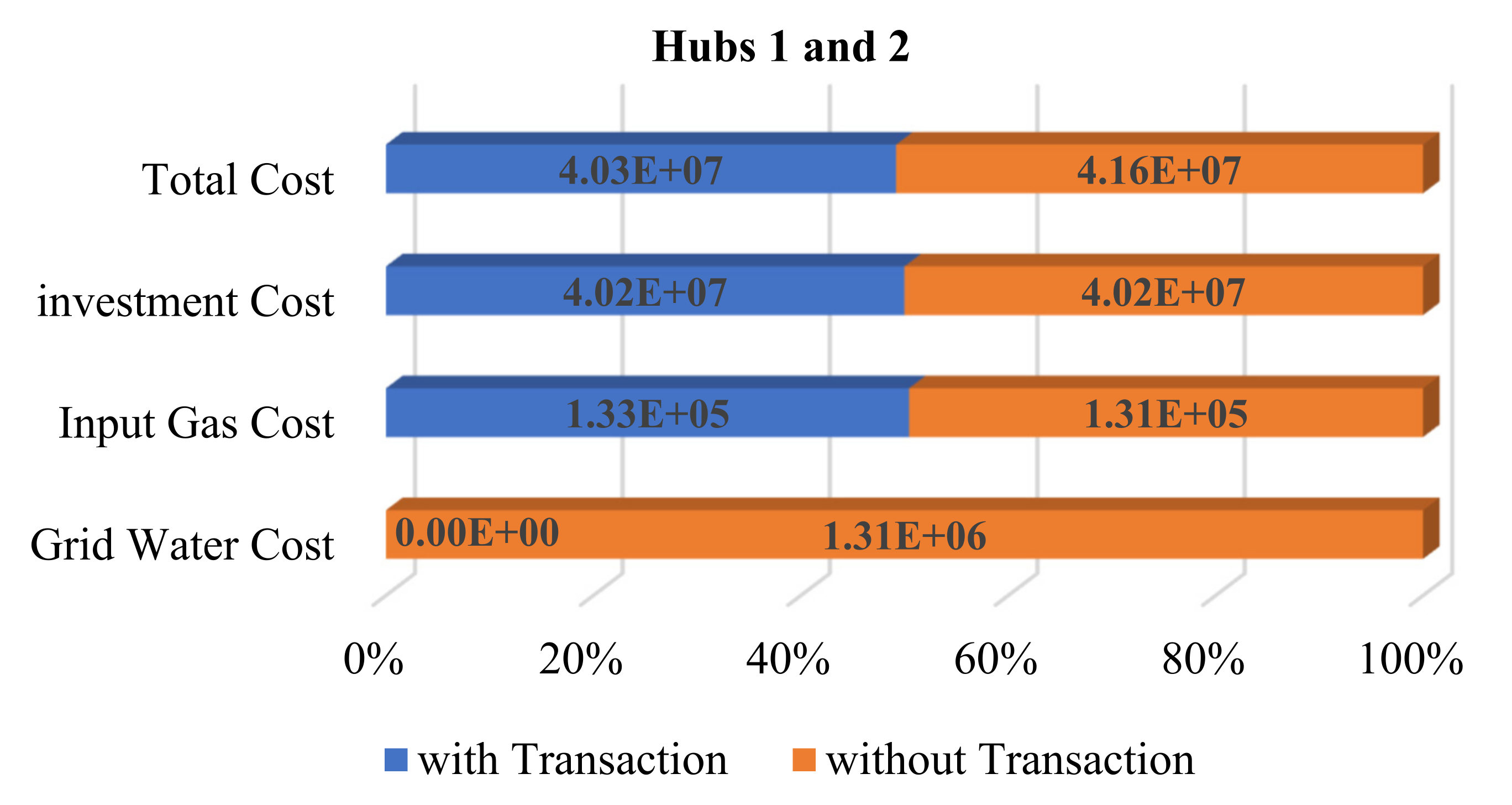


| Reinforcement Learning | Hub Energy | Microgrid | Uncertainty | Attack Detection | |
|---|---|---|---|---|---|
| [19] | ✓ | ||||
| [29,32] | ✓ | ||||
| [35] | ✓ | ✓ | |||
| [36] | ✓ | ✓ | ✓ | ||
| [37] | ✓ | ✓ | ✓ | ||
| Proposed Model | ✓ | ✓ | ✓ | ✓ | ✓ |
| Bus Number | Vmin | Vmax | Pd (MW) | Qd (MVAR) |
|---|---|---|---|---|
| 1 | 0.95 | 1.05 | 108 | 22 |
| 2 | 0.95 | 1.05 | 97 | 20 |
| 3 | 0.95 | 1.05 | 180 | 37 |
| 4 | 0.95 | 1.05 | 74 | 15 |
| 5 | 0.95 | 1.05 | 71 | 14 |
| 6 | 0.95 | 1.05 | 136 | 28 |
| 7 | 0.95 | 1.05 | 125 | 25 |
| 8 | 0.95 | 1.05 | 171 | 35 |
| 9 | 0.95 | 1.05 | 175 | 36 |
| 10 | 0.95 | 1.05 | 195 | 40 |
| 11 | 0.95 | 1.05 | 0 | 0 |
| 12 | 0.95 | 1.05 | 0 | 0 |
| 13 | 0.95 | 1.05 | 265 | 54 |
| 14 | 0.95 | 1.05 | 194 | 39 |
| 15 | 0.95 | 1.05 | 317 | 64 |
| 16 | 0.95 | 1.05 | 100 | 20 |
| 17 | 0.95 | 1.05 | 0 | 0 |
| 18 | 0.95 | 1.05 | 333 | 68 |
| 19 | 0.95 | 1.05 | 181 | 37 |
| 20 | 0.95 | 1.05 | 128 | 26 |
| 21 | 0.95 | 1.05 | 0 | 0 |
| 22 | 0.95 | 1.05 | 0 | 0 |
| 23 | 0.95 | 1.05 | 0 | 0 |
| 24 | 0.95 | 1.05 | 0 | 0 |
| Operation Conditions | Input Gas Cost | Grid Water Cost | Microgrid Cost |
|---|---|---|---|
| Normal | 1.3307^105 | 0 | 3.7196^108 |
| Attack (water & thermal) | 1.6795^105 | 2.7479^107 | 3.937^108 |
| Operation Conditions | Attack without IPS-RL | Attack with IPS-RL |
|---|---|---|
| Grid Water Cost | 2.7479^107 | 436 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alnowibet, K.; Annuk, A.; Dampage, U.; Mohamed, M.A. Effective Energy Management via False Data Detection Scheme for the Interconnected Smart Energy Hub–Microgrid System under Stochastic Framework. Sustainability 2021, 13, 11836. https://doi.org/10.3390/su132111836
Alnowibet K, Annuk A, Dampage U, Mohamed MA. Effective Energy Management via False Data Detection Scheme for the Interconnected Smart Energy Hub–Microgrid System under Stochastic Framework. Sustainability. 2021; 13(21):11836. https://doi.org/10.3390/su132111836
Chicago/Turabian StyleAlnowibet, Khalid, Andres Annuk, Udaya Dampage, and Mohamed A. Mohamed. 2021. "Effective Energy Management via False Data Detection Scheme for the Interconnected Smart Energy Hub–Microgrid System under Stochastic Framework" Sustainability 13, no. 21: 11836. https://doi.org/10.3390/su132111836
APA StyleAlnowibet, K., Annuk, A., Dampage, U., & Mohamed, M. A. (2021). Effective Energy Management via False Data Detection Scheme for the Interconnected Smart Energy Hub–Microgrid System under Stochastic Framework. Sustainability, 13(21), 11836. https://doi.org/10.3390/su132111836








