1. Introduction
Like other environments, Internet-of-Thing (IoT) technology has had a major impact on agriculture. The world population is increasing, so we need maximum production in the country, and modern technology is helping to increase it [
1]. If we are using old methods, it’s difficult to fulfill the need of the world population [
2]. IoT is used in agriculture in many ways, protecting lives, safety, monitoring, controlling access to water and urea, and many other things. There are some sub-sectors of IoT-based agriculture such as smart farming and smart cattle farms.
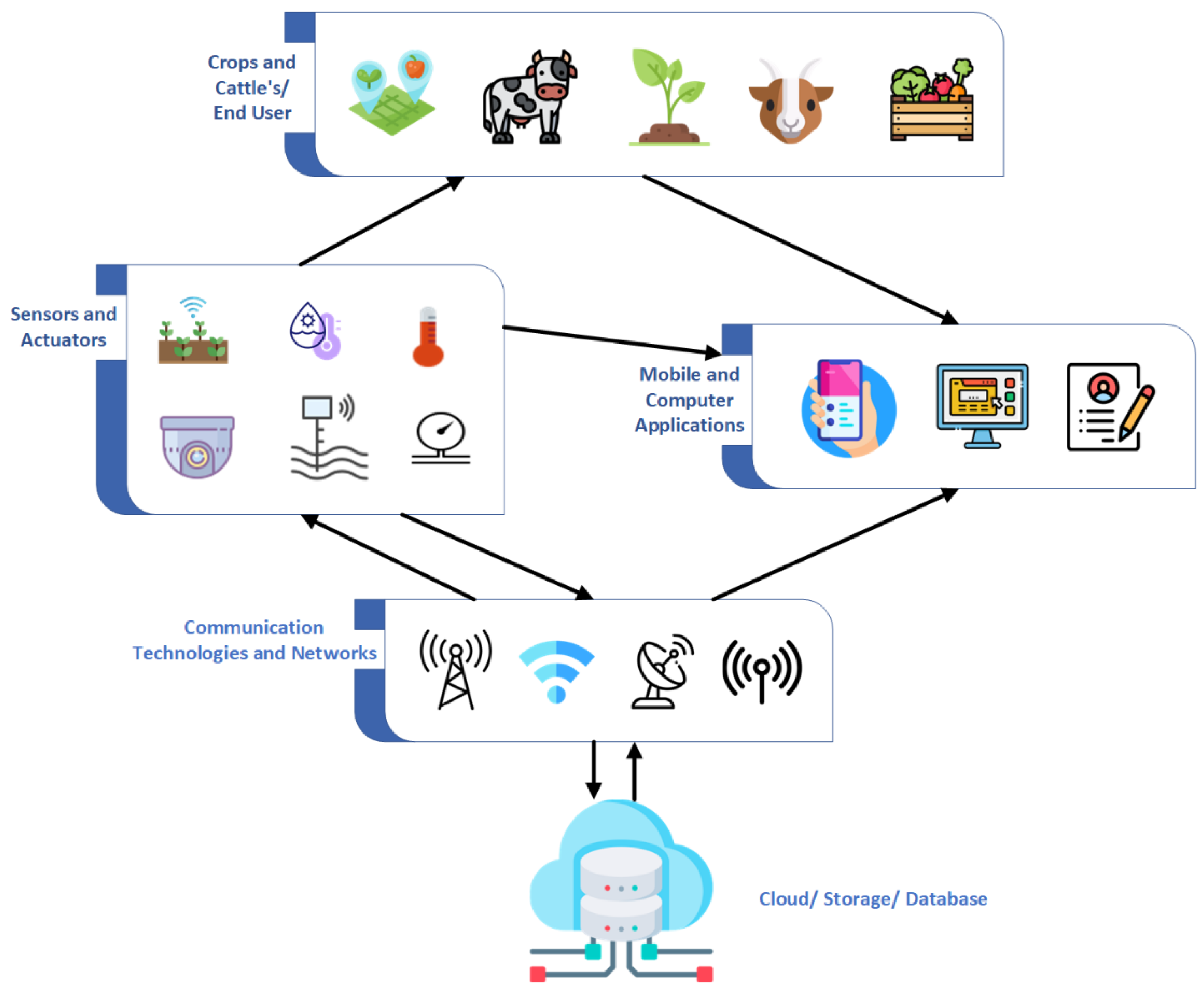
Figure 1 shows a multi-level schematic of smart agriculture. Despite its virtues, technological developments have brought new challenges. One of the biggest challenges facing IoT is security due to loose network connections [
3]. Sometimes wild animals enter farmland and destroy crops, similar to how they disrupt IoT or technological devices such as sensors and actuators [
4]. As of today, IoT devices will alert or notify farmers in such situations. The problem, however, is that farmers are not always ready to deal with such attacks. Security concerns are a giant hurdle in the versatile use of IoT [
5]. Therefore, farmers need a security measure that can act on its own.
One network security technique is adaptive security, which addresses runtime security [
6]. Like other industries, IoT is very popular in agriculture because it creates new opportunities for farmers, but also some challenges. In smart farming and smart cattle farms, there are many safety concerns related to wildlife or weather conditions. Smart farming becomes more cost-effective by addressing safety concerns related to wildlife and weather conditions. Traditional scarecrow sculptures with sensors and IoT devices are used to enhance security [
7]. The scope of cyberattacks in Modern Agriculture 4.0 is broad. Improving security is always a matter of increasing the potential of a system. Smart sensors have four layers: (a) perception layer; (b) network layer; (c) surface layer; (d) application layer; each layer has its own security issues [
8].
As the population increases, more food is needed, so the production of food is increased through the use of technology [
9]. IoT is one of the emerging technologies today. Towards this end, smart farming (like IoT-based farming) is an effective step towards achieving good crop growth. IoT is having a major impact on agriculture and related things like smart farming and smart livestock production. A detailed review of smart agriculture is discussed in [
5], and issues related to sensors, IoT devices, and security issues are identified. In smart farming, different devices use many algorithms that serve different purposes, such as security, image processing, and climate control. These algorithms can be compared, and an algorithm hat works well in all of them is of interest. In the modern era, technology is developing, and things are becoming automated and digital. We can make technology more powerful and make our lives easier.
IoT is beneficial in all fields: e-health, smart home, smart car, smart agriculture, and smart appliances. IoT-based devices contain sensors and actuators that can sense and react to the environment [
10]. According to a 2020 study, there are 34 billion IoT devices worldwide [
7]. A recent IBM study suggests that by 2025, basic IoT devices will account for
$1 trillion in healthcare alone [
11]. In the field of patient health monitoring, this is done using multiple sensors. The sensor can collect data from the patient every time and share it with the doctor as needed [
12]. Similarly, in the smart home space, users can control home equipment such as lights, fans, air conditioners, etc. If someone wants to enter the home camera, verify that the person is allowed in. Companies can check the movement of their vehicles. Vehicles that hold food also have the ability to maintain temperature, so food stays fresh until it reaches the user.
In smart farming, IoT devices need to monitor climate conditions and alert farmers. IoT sensors analyze plant production and issue alerts in the event of an attack [
13]. It is the third wave of information technology, and all fields that will develop are moving in the direction of artificial intelligence and the IoTs. However, security is a challenge for IoT because it is not mature enough and there are no standards for security and privacy [
14]. Whenever anything is connected to the Internet, there is always the potential for a security breach. For the security of the network, a systematic intrusion prevention system called IPS is used. The directives and rules in this system focus on cleaning the network from threats [
15]. It does not contain instructions on risk analysis and quality of service security. Likewise, intrusion detection systems cannot have instructions for new threats and their analysis and defense [
16].
There are two types of security in IoT, one is static and the other is dynamic [
17]. Static safety only works under defined conditions and cannot prepare for unknown situations. Because IoT operates in a real-time environment and the types of threats to systems are so numerous, static security is not enough. To eliminate these security risks, using dynamic security operations, we need to make the system more sophisticated as the level of risk increases. In a dynamic security system, it identifies threats and vulnerabilities by itself, and the system analyzes the situation and makes decisions based on this situation [
18].
In the dynamic/autonomous security discipline, a cybersecurity approach used to prevent threats from occurring is adaptive security [
19]. It is an automated technology that continuously assesses risks and threats while trying to protect the system. The security of networks, especially ones like the Internet of Things, is a major concern these days. In IoT, devices are loosely connected and there are many risks and opportunities to compromise security. In the IoT framework, static security is too weak to effectively address security risks. Therefore, in this case, an advanced security system that can dynamically protect the system is required. Adaptive security protects systems in a number of ways, such as protecting systems from cyber-attacks, discovering risks and threats, and another approach is retrospective, where risks are discovered in greater detail, and some adaptive systems predict future risks.
A risk-free environment is one of the most predictable practices in information technology (IT) [
20]. It is necessary to analyze the possibility of project failure in order to exclude it from consideration. The most important thing to make a system risk-free and secure is that you understand your risks and threats. Users/developers know exactly what they are trying to avoid and mitigate. Risk identification and mitigation is the biggest challenge in the Internet of Things (IoT) environment [
21]. To analyze risk, we need to focus on several things, such as: determine the risk analysis method for the area; examine the environment′s response to risk analysis practices; analyze the answers; and assess the level of risk. Risk factors can be reduced through rigorous safety and assessment. The risk analysis model should be intelligent and adaptable to any type of environment [
22]. There is the potential for risk in adaptive security operations, and this is how we introduce risk analysis to them.
The key contributions of this research are as follows. We develop an assessment framework for implementation in scenarios. These scenarios are based on smart farming, and they can feature storylines and cases that help shape our framework. Our framework focuses on safety factors, risk factors and costs. We also found security and risk factors for graphs on adaptive security. Different basic agricultural environments are integrated into an adaptive security model and evaluation framework. In this research, we first identify the issues that constitute IoT security concerns and then conduct an adaptive security risk analysis.
Figure 2 shows the research question that we have formulated to set the goals based on our problem and proposed solution. After choosing the most appropriate security model, we implement it and conduct experiments. Experiments are carried out in real scenarios such as smart agriculture. After the experiment, we calculate the results and compare them. In the final step, we analyze the results and show how the results can be improved.
2. Materials and Methods
We have applied adaptive security technology to smart agriculture and adopted it as a case study. Our focus is on applying adaptive security technology in smart farming and saving farmers′ information from competitors. Farmers′ data protects our technology from hackers. Tools are used to get results and check them beforehand. Finally, we will compare our results, validate them and show improved results.
After creating an adaptive security model, we validate it using simulation tools or a real sensor-based environment and implement the model using some case studies. The use and implementation of adaptive security is not common in smart farming, so we selected smart farming and smart farming as case studies.
Figure 3 shows that first we need to find the basic smart agriculture threats and vulnerabilities that compromise farmland security, and then we implement an adaptive security approach to address the threats and monitor the vulnerabilities. We also describe the security risks to our assets and how these risks make our assets vulnerable. Adaptive security also tells us what our security needs and goals are, and how we can reduce risk by using this adaptive security. The main purpose of this adaptive security-based research effort is to secure the underlying IoT environment.
In the initial stage, an adaptive security model is selected and then applied to the simulated environment. These models can be applied on testbeds or in real environments. Adaptive security models are typically validated against four parameters. These parameters are defined as follows:
Adaptive optimization: It is the system’s ability to adapt or adjust itself at runtime. For example, if a hacker tries to enter the system with a password, the adaptive system changes the encryption technology;
Adaptive configuration: The system can change itself according to the situation. For example, using a verification code when logging in can prevent system restarts or fake logins;
Adaptive healing: If something goes wrong in the system, it can correct and normalize it;
Adaptive protection: Systems can protect themselves by analyzing threats. The system can dynamically react and neutralize threats.
After implementation, we collect results for each model and perform a risk analysis on each model, which helps to improve it. Three basic parameters are applied to an adaptive security model for risk analysis: (a) the ability to monitor the risk, (b) the risk analysis, and (c) the response to that risk. We consider the state-of-the-art risk management frameworks to discuss these types of risk management steps during the study, such as the NIST (National Institute of Science and Technology) Risk Management Framework (RMF) and the ISO-IEC 27005:2018 Information Technology-Security Techniques-Information Security Risk Management.
Additional parameters are used for adaptive risk management for a comprehensive analysis of the adaptive model.
What threats and risks does this approach handle well?
What types of algorithms and functions are used in the model?
How is context awareness used and manipulated in models?
Performing risk analysis and using adaptive security context awareness in IoT is essential. Context awareness uses the word “WH” to represent objects. “WH” words include what, why, where, who and when.
Scenes represent very frequent interactions between users and smart devices, and there are different types of scenes, such as scenario library, story library, simulation library, and sequence structure library. Two important questions need to be answered when creating a scenario: (A) What scenario should be defined? (B) How helpful is the scenario in finding the research solution under consideration? We conduct scenario-based assessments to identify threats and risks in IoT-based environments. Our scenarios demonstrate what smart farming really is and also help to find solutions to threats and risks. These scenarios demonstrate basic IoT environments in farmland, gardens, and smart ranches.
The proposed scenario covers two basic factors:
Security factors: Covering all security factors is challenging because there are several things in network and data communications that create security risks. We create scenarios globally so that they can cover most security factors in that area. These security factors are related to data flow, data storage, and instruction-set violations in sensors in smart IoT environments.
Risks assessment factors: When security is good, risk is less likely and vice versa. Adaptive security attempts to mitigate all security threats, which is why the system is less risky. Adaptation can improve risks and threats. When a system is able to handle risk, it provides quality service to users. Our scenarios discuss what types of risks arise and how to deal with them.
In a scenario-based framework, different parameters are considered, which are:
The number of threats affecting the security of a scenario;
The number of security actions to minimize security threats and risks;
Several agricultural states where adaptive security should be applied.
2.1. States of an Environment
In
Figure 4, we have shown the Quantitative Assessment Framework (ASIA) of the proposed system. Suppose that we have a sufficiently secure intelligent environment, denoted by S. This smart environment is also risk-free and works well. Risk is represented by R. Using a simple notion of sets; we intersect between a safe S and a risk-free environment R. From the intersection we get an equilibrium space B. This is the ideal condition as shown in
Figure 4a. Suppose we have an intelligent system with sufficient security and a risk-free environment. Therein, a threat appears which is denoted by T. This threat brings about a state of equilibrium in the environment. Due to this equilibrium state, the minimization is shown in
Figure 4b. When a threat occurs in a system, adaptive security attempts to mitigate that threat. This threat can be mitigated by the proposed threat mitigation process with adaptive security to make the system risk-free. Threat mitigation requires some processing cost, marked C. This processing cost minimizes the steady-state range, and at this stage; the working principle of the real environment is shown in
Figure 4c.
2.2. Quantitative Assessment Framework
A system′s safety and ability to deal with risk can be measured against the data provided by people or the environment. We are trying to build an estimator that takes data as the input and helps to check the quality of adaptive security. After creating the estimation function, the expert needs to input the data into the function. In this regard, we can find the method to calculate the quality of video streams in [
23]. In the following equations, we show how the environment can be evaluated using human data.
To make our framework quantifiable, we define “q”. It is a true function 0 ≤ q ≤ 1 that should address the satisfaction of requirements and how well they cover the environment. If the value of q is close to zero, it has a poor value and the minimum requirement is met, and a high value of q means the maximum requirement is met.
The function q is divided into three parts: (a) the function q
S represents the security requirement to be satisfied; (b) the risk assessment requirement to be satisfied is represented by the function q
R; (c) during the threat and risk analysis, the occurred cost is denoted as C. Now the function q is the sum of all subfunctions denoted as,
where ∏ presents the factorial notation, q
i is partial function; w
i is weight. The weights can be anything from real numbers 0 ≤ w
i < ∞. Smaller weight values are less important, whereas larger weight values are important. It is natural if the weight is 1.
For the full definition of the above equation, the factor k that affects q
i is missing. To make the equation complete we exchange the weights by
then we find the equation
. Finally, the value of q is elaborated as,
(1) Security Factors: Define G
S = (S\I) ∪ M as representing a state where the environment is secure and the requirements regarding security are fulfilled, and the environment has no threat. Suppose a state in the environment x which is not falling in the environment for the fulfillment of its requirements, a normalized distance d
Sx: 0 ≤ d
Sx ≤ 1 is required and this state has ideal requirements. When the d
Sx = 1, its deviations cannot be tolerated.
Hence the function is defined as:
(2) Risk Assessment Factors: Define GR = R\C is representing a state where all risk related requirements are satisfied and the effect of these are mitigated. There is a state x that is outside of the risk-free environment as it is not in an ideal risk-free environment, so we define the distance d
Rx: 0 ≤ d
Rx ≤ 1. When the value of d
Rx = 1, risk assessment factors are inadequately fulfilled. Risk assessment may be affected by the environment or also due to adaptation. This could impact the data availability.
Hence the function is defined as:
(3) Mitigation Costs: When performing safety operations and environmental risk assessments, there are costs such as: environmental changes, cost of providing quality monitoring, etc. This unpredictable cost is C. If the cost is outside the region, we define the distance as d
C: 0 ≤ d
C ≤ 1. We define the following function as,
2.3. Assessment to Define the qi Values
Finding the value of qi requires human evaluation to tell us to what extent the requirements are met. Likert scales were used to assess these requirements. The Likert scale is a psychometric scale commonly used for research purposes. It contains a series of questions that can be answered by experts in that particular field. These questions have five (5) or seven (7) values, from best to worst or top to bottom.
When a questionnaire was filled by the expert, for each question of qi on the Likert scale, we propose a function e that takes the response of each question, which is represented as q˜i ∈ N for 0 ≤ q˜i ≤ n − 1, as an argument. For expressing the value of qi, multiple approaches are used, and here we used two (2) of them:
- (2)
Logarithmic Method
- (3)
Other Methods
The Likert scale, which is used with many types of data, is a psychometric scale. Data can be subjective or objective, and data can be qualitative or quantitative. The ranking of questionnaires used in Likert scales depends on ratings, such as Consistency Basis, Frequency Basis, Importance Basis, Quality Basis, and Probability Basis. Assessments on this scale are as common as other assessments, such as tools used to measure software quality.
The input here uses objective data, the output of the measured data from 0 ≤ qi ≤ 1, and is applied to Equation (2). The value of is substituted into Equations (2) or (3), and is not hard-coded to only substitute into Equation (2). For evaluation, many people want to participate in the evaluation. Experts evaluate them one by one, and the result is the sum of all.
2.4. Scenarios Base Evaluation
To discuss scenarios and the storyline of the scenario, let us first discuss some scenario components that are helpful in understanding adaptive security.
Figure 5 shows the components of the scenario as it is divided into 4 levels.
Here, we divide the smart farming environment into four component base levels from 1 to 4. Level 1 is the land, level 2 is the adaptive security infrastructure network, level 3 is the environment, and level 4 is the agricultural management system. (1) Country: This is the country where adaptive security is applied. (2) Adaptive Security Infrastructure Network: Adaptive Security Infrastructure Network monitors the land and agricultural environments and collects their data. The sensors in the network are randomly connected, with some sensors specific to parts of the country, whereas others collect data in general. (3a) Smart Garden: It is a garden area security where the garden is covered by multiple sensors and cameras. It is to collect data and send all the information to farmers via a mobile app or management system. (3b) Smart cattle farm: The smart environment of the cattle farm, now the sensors are the same as the cattle and the cattle farm. The system is mobile connected. (3c) Smart fields: In smart fields, sensors are placed together with crops, and some sensors are placed in the corners of the land. These sensors collect data related to crops, weather, and external factors affecting farmland. (4) Farmer management system: This is the background of the whole system. It is a trusted system connected to the entire environment through a network. It can collect and store all data. Farmers have only one person access to the system.
- (A)
Garden Area Security
Many fruits and vegetables are grown in the garden. These fruits and vegetables are expensive and require some protection from intruders, as well as protection from climate change and water supply. In the first scenario, we have a garden and deploy a drone that can monitor its safety. This is a training drone with a camera. If someone who doesn′t exist in the drone′s camera database enters the garden, they can trigger an alarm that can activate the former. The drone employs adaptive safety operations that can react to the situation. Sensors monitoring climate change and soil moisture are also hooked up. In IoT, devices and sensors are connected through a network, which is also an IoT environment. All sensors check their neighbors over the network. The farmer will also notify it if one of the sensors stops working, as shown in
Figure 6.
There are also some sub-scenarios for campus security, which are created according to the situation:
- (1)
Gardner is in the garden
When the gardener is in the garden, he has a separate room to check the activity of the garden. He can also change the value. The server room records the decisions the sensors make and how they protect the system.
- (2)
Gardner is out
Gardner is going for work or any task for his home. He is connected with the system through the mobile application. He checks the sensors and also monitors their decisions.
- (3)
Sensor is damage by some natural disaster
Sensors can be damaged due to natural disasters such as heavy rain, thunderstorms and high temperatures. They can disrupt the functionality of the system. Gardner couldn′t get the right answer, and the system′s protection against threats was weak.
- (B)
Field area security
Fields are under threat from wildlife that can invade fields and destroy crops, as shown in
Figure 7. These animals also disrupt sensors in smart farming environments. When a field uses IoT devices and sensors, all data on the network flows through the sensors. These sensors are loosely connected to each other. These sensors contain all the settings for the plant, such as how much water B needs, what temperature is good, and any information on insects and other diseases in the plant. All data flows over the network and there are threats associated with hacking into this system. If an intruder hacks into this system and changes all of the settings, crops will be destroyed. Often, farmers are not proficient in this technique, so it is easy to catch them. System settings are connected to the mobile app or controller. The live area has some sub-scenarios, which are described according to the on-site situation.
- (1)
Farmer monitor from home
The farmer uses the farmer management system and he can monitor all the activities of the system. Farmers also have the option to connect to the system via video. The number of working sensors and the number of idle sensors can be controlled by the management system.
- (2)
Animal damages the sensor
Crops and fields are in an open environment with many opportunities for wildlife invasion. These animals can damage any sensors and disrupt the adaptive functioning of the system. If a farmer is connected to a management or mobile application, he can understand the losses.
- (3)
Impact of season
Seasons work very well for plants because different seasons have different plants. Insufficient sunlight in winter has affected the solar base equipment. Just like in winter, the summer sun is very strong and can melt the sensor.
- (C)
Cattle Farm Area Security
There are many expensive animals in the cattle farm. There is no paper document for the animals indicating that the animal is related to this person. When an animal is lost or stolen, it can be difficult to find it. On a cattle farm, the farmer or caretaker cannot be on the farm all the time. For this reason, there needs to be security around the ranch where independent decisions can be made in the farmer′s absence.
Figure 8 shows a smart cattle farm.
Other threats are related to animal safety. Animals may move to locations where cables or electrical systems have been laid. In this case, the farmer must be notified or adaptively addressed. When the weather is hot, the cattle farm must be cooled and heated. Since animals cannot express how they feel about the weather, temperature sensors are used to perform actions. In today′s smart cattle farms, a new term called “aquaculture” is used for smart fish farming. Aquaculture will be discussed in future work.
What happens in the cattle station is described in the following sub-scenarios:
On a cattle farm, the need for safety is different day and night. During the day, cattle are most likely to be in the open and on the move. At night, cows are in the shade. The security parameters are different both times.
- (2)
Monitoring of farm
Monitoring on farms is mostly mobile, as it is nearly impossible for farmers to monitor every animal. The owner uses the mobile app along with the monitor in the server room.
- (3)
Animal changing
A new animal enters the farm or an animal leaves the farm, in which case safety sensors are attached to the animal. In the case of animal elimination, remove the sensor from the animal so it does not distract the entire system with false location information or false information.
- (4)
Monitoring of food process
Sensors are used to check the feed when the farmer is not on the farm and the animals are eating it. Is this feed fresh or stale? The water system works perfectly. When the tank is one level lower, the tank is full again. The system should be secure enough to protect the water sensor settings.
3. Scenarios in the Storyline
In the previous section, we created some scenes and sub-scenarios that can be used to create storylines that can be used in our framework. Here, we show the plot of all the scenes about gardens, fields and pastures. Storylines are used to analyze scenarios.
- (A)
Storyline for garden area
Tom has an orchard, and his garden is equipped with smart IoT devices. The garden has a basic IoT drone that monitors the garden area, tracks the location via GPS and optimizes the security of the garden. There are also some electrochemical and mechanical sensors in the garden. All sensors are connected and communicate with each other. When Tom is on the farm, he can monitor the garden surroundings from the server room. Tom sees what the sensors are doing and collects their responses. When Tom is not in the garden, he connects to his garden via a mobile app. He sees all of his notifications on his phone. Tom wants other gardeners and farmers to keep his details private. Basic IoT drones need to be waterproof to function properly in the rain. When one sensor stops working, the other sensors communicate and generate a notification of this failure. Other sensors can connect to Tom and alert him to garden conditions.
- (B)
Storyline for Field area
Mike is a landowner and grows crops on a large scale. He uses smart farming and has deployed some IoT-based sensors. His area of expertise uses optical sensors, position sensors and soil moisture sensors. When Mike is at home, he monitors his fields through the Farmer Management System. His family has a server room where all the data collected from the fields is stored on the server. Suppose that Mike is gone and an animal such as a pig or another wild animal enters the field and tries to damage the sensor. Smart statues in the corners of the fields try to scare the animals. Other sensors connected to the statue will be alerted if the animals are able to enter the crops. The entire situation was captured on camera, from which Mike saw the entire scene. In this case, the alarm is also activated. The angle of the sun changes as the seasons change from winter to summer. Due to seasonal changes, the values of temperature and humidity are completely different. The harvests also vary between seasons. Because of all these seasonal variations, Mike trains his sensors accordingly. Crops are outdoors and therefore have a big impact on the seasons.
- (C)
Storyline for Cattle Farm
We develop the cattle farm storyline while Adam manages the cattle farm. He has several animals such as buffalo, goat, chicken and horse. During the day, all the animals are in the clearing of the pasture. Adam took his animals to the sanctuary at night. Surveillance cameras are installed on the cattle farm. Location-based sensors connect to the animal and they are connected to GPS and monitor the animal′s location. Electrochemical sensors are used to test the pH levels of the feed and water for the animals. It also checks the diet for iron, sodium, potassium and calcium. All sensors are connected via GPS and Wi-Fi, so Adam checks for updates via his phone. The sensors in the smart cattle farm are interconnected. Adam bought some new animals and brought them to the farm. If the sensors are connected to the new animals, they must be connected to the other sensors. If the animal has been fighting or the sensor is broken, it alerts other animals around and collects data from those animals. Adam wants to back up his farm data. If the data is lost, there is a risk of animal theft.
4. Results and Evaluation
For evaluation, we extract parts from the proposed scenarios and use them in our framework. We describe and comment on the use of the framework through the scene. Note that these values are from the hit-and-trail method and are for illustration purposes only. These are rough values for evaluation, with few conservative values. Several evaluation methods have been described in the framework evaluation section, but here we only apply linear and logarithmic methods.
- A.
Confidentiality and Observability
In our scenario plot, garden, yard, and field data should be kept secret from other characters and their rivals. Assume that in the first case of the framework in S, confidentiality and observability of data are important.
When we talk about data observability, it means that third parties observe the data stream and signal that they can also observe the presence of the device. For environmental countermeasures, corners can be shielded, or the signal can be designed to be in the environment every week. The process of shielding the surroundings is an expensive task, so low signal strength is applied in most cases, but this has an impact on data availability. Signals cannot reach every corner of the environment. There are also cases where the signal flow comes from outside the environment because there are jammers in some corners of the environment.
Data confidentiality is used when we try to hide data from unauthenticated users. Data encryption and authentication are used for data confidentiality. Various encryption techniques and authentication methods are used to protect the system when a threat arises or when a hacker attempts to gain access to the system. System protection has a negative impact; it drains the battery and minimizes performance.
Evaluation of Field Area: To evaluate scenarios, we found numerical values. In the first example, we have live area security. The quantitative values of the first example are shown in
Table 1, and the corresponding graph is shown in
Figure 9. The variables for the first example are: (a) q
S1 is the value for on-site observability; (b) q
S2 is the value for off-site observability; (c) q
S3 is the value for confidentiality; (d) q
S4 is the value for availability; (e) q
R1 is the value for natural disasters; (f) q
R2 is the intruder risk value; (g) q
C is the other abatement cost. Recall that the value of q
i represents the distance of a given requirement from ideal satisfaction, where 1 means that the requirement is fully satisfied. We use the following cases: (I) base case, i.e., environment without jammers, using a fairly simple encryption algorithm and authentication protocol, sensors transmitting at normal power; (II) add jammers in the environment; (III) minimize signal strength; (IV) use different encryption algorithms; (V) use different authentication protocol.
As mentioned in the previous section, we discussed the Likert scale, which uses n parameters, ranging from the best value to the worst value on the scale. For example, in q
S1, we prepare a series of requirements from 0 to 5, as shown in
Table 2. Again, the requirements for q
R1 are shown in
Table 3. 0 is an unacceptable minimum value. When q
S1 is 0, the value of q is also 0. When the value of q
S1 is 5, it is the ideal situation to meet all requirements.
For doing the experiment, we have q˜Si = 1…4, q˜Qi = 1…2, and q˜QC for the assessment. We find the values of these by some rough estimation, but more accurate results are calculated in the future work. The weights wi assigned values are also from rough estimation. After an assessment of all the values, the results are evaluated for qˆi and qtotal using logarithmic approach.
Cattle Farm Evaluation: In our second scenario for the security of cattle farms, we have the following variables: q
S1 has a value for the observability inside the cattle farm; q
S2 is the value for confidentiality; q
S3 is the value for availability; q
R1 is the value from the animals; q
Q2 is the value for risk from the intruders; and q
C are other mitigation costs. The same process that was described for the field area security was repeated for the cattle farm.
Table 4 presents the assessment values of the cattle farm example and
Figure 10 shows its graph.
The cases used for the environment of cattle are: (I) first is base case in which all things are working fine, sensor are collecting right value and moderate power consumption, (II) control power of signals as per time (high at day time low at night time); (III) using different encryption algorithm; and (IV) using different authentication protocol. Then we create the scale for each of our variable as per Likert scale. Initially we set the value of scale from 0 to 5. For doing the experiment, we have q˜Si = 1…3, q˜Qi = 1…2, and q˜QC for the assessment. After doing the assessment we shown the results in table.
Evaluation of Garden Area: In our third scenario for the security of garden area we have the valuables: q
S1 has a value for the observability inside the garden, q
S2 has a value for the observability outside the garden, (c) q
S2 is the value for confidentiality; q
S3 is the value for availability; q
R1 is the value for from the animals; q
Q2 is the value for risk from the intruders; and q
C are other mitigation costs. The process describes for the field area security we repeated the same process for the garden area. For the example of garden area assessment values shown in
Table 5 and
Figure 11 show its respected graph.
Cases for cattle environments are: (I) firstly, a base case where everything works under normal conditions, sensors collect values and have moderate power consumption; (II) jammers are added to the environment; (III) signal strength is minimized; (IV) different encryption algorithms are used; (V) different authentication protocols are used. Then, we create scales for each variable based on the Likert scale. First, we set the value of the scale from 0 to 5. For doing the experiment, we have q˜Si = 1…4, q˜Qi = 1…2, and q˜QC for the assessment. After doing the assessment, we show the results in the table.
We apply numerical values to logarithmic and linear equations. Check that both equations have the same data, and their total result is shown in the figure. Logarithmic and linear methods have the same working and processing behavior. However, the results of the logarithmic method have higher values than the results of the linear method.
5. Discussion
Adaptive security is defined as a security system that learns from the environment and reacts according to the situation and can handle threats with very little computation and energy consumption. This security makes IoT systems more secure and reliable. Adaptive security using learning loops and system analysis is described in [
24].
The implementation and functions of adaptive security are shown in
Figure 12. The basic steps of adaptive security are:
- (a)
System startup: In this step, the new system is built and has basic knowledge of the environment;
- (b)
Monitor: Here, the system goes to work and observes the environment. This is an ongoing process where the system can monitor the environment without threats;
- (c)
Analyze: When a situation arises, the system can analyze it. This occurs in the database checked in this step;
- (d)
Execute: Once you′ve selected a specific threat response, it′s time to run.
It′s a learning cycle that applies to each new situation. All new and old situations are stored in the database. The database relies on adaptive security and has all operations related to security. All these things are connected to the basic IoT environment. Adaptive security monitors the IoT underlying the environment and remediates and deploys into the IoT when threats arise. Learning loops are a key feature of adaptive systems.
- A.
Integrating the Estimation Function to Adaptive Security
As detailed in the previous section, the key concept of adaptive security. Data is monitored by sensors, analyzed by analyzers, and then sent for execution after validation by an adaptive database. This is an ongoing process and adaptive database learning as the learning loop works every time.
Figure 13 shows the integration framework.
We now return to the plot we outlined in the previous section. In the storyline evaluation, the value of qi is evaluated for the sub-scene, and we find the weighted value of q. The sensor in adaptive safety monitors the measurement of k and writes its measurement as sk. We design a function u(sk) in which the value as u(sk) = q as q is defined in the previous section that was used for scenarios. Although using the function u can generate the same value, the sensors are taken as an input. Similarly, as q for qi, we drive the function ui(sk) for the scenarios. The function qi is also generating the same value as it takes input from the sensors.
At the initial stage, the functions u(sk) and ui(sk) are in the learning stage. With the passage of time, these functions are learnt and the adaptive database is updated. The value of u(sk) and ui(sk) change over time. Then, these functions are evaluated in the analyzer phase. For the evaluation context awareness, game theory and some others are used.
On the basis of our scenarios, the values of q, qSi, qRi and qC are assessed from experts and specialists in the field. These values help to check the accuracy of the model. This data can also be used to validate the estimator by comparing it with the estimator after it has been created. Data from sensors and adapters are retrieved from the monitor component and applied to a set of measurement parameters. The analyzer uses the estimated model to do its work and sends the results to the adapter component.
- B.
Evaluation Methods
To evaluate the behavior of the adaptive security techniques and methods, we used some of the environment-based scenarios and storylines introduced in the previous section. We make a number of situations in the scene, and after creating the plot for these situations, after performing the evaluation, we find and calculate the values of q, qSi, qQi, qC, u(sk), and ui(sk).
In order to perform this computation in real time, it is necessary to build a test bench with all functions. The evaluation method states that for calculations in a test bench or simulation, all necessary situations and scenarios must be run, and the framework must be evaluated. If adaptive security algorithms are used, they will process the new state and evaluate and compute a score. For checking the behavior of the adaptive algorithm, the values of u(sk) and ui(sk) are compared, and the values of q, qSi, qQi, and qC are also required for the assessment. The final goal of an adaptive algorithm is to ensure its behaviour is near to the right decision of the assessment.
6. Conclusions
This study proposes an evaluation framework applied to IoT-based smart agriculture. We describe the importance of scenario-based assessments. Threats and risks emerge from smart farming and speak to the importance of security in IoT-based farming. We have created a framework that can assess safety factors, risk factors and costs. We build basic farming scenarios for field areas, garden areas and cattle farms. Additionally, sub-scenarios and cases are created for use in the framework. The framework assesses compliance with safety factor and risk factor requirements. We have created a storyline for all three farming environments. These storylines are used with different evaluation methods to calculate the results. All storylines are analyzed and evaluated. In future work, we will create a simulation of these scenarios. These are also applied on some testbeds to implement the framework in real time.