Verification of Privacy Protection Reliability through Mobile Forensic Approach Regarding iOS-Based Instant Messenger
Abstract
:1. Introduction
- It presents a method of investigating the structure of the SQLite database, which stores chat messages in most instant messengers, and the verification of privacy protection reliability from a digital forensic point of view.
- Since this study presents a method of creating backup data for the iPhone without unlocking it, even if the mobile phone is locked, the possibility of leakage of personal information inside the mobile was technically confirmed.
- Since this study includes experimental results on data traces targeting the two messengers with the highest usage rates in the global instant messenger market, it is of practical use in mobile forensics.
2. Related Works
3. Background
3.1. Acquisition Method of Locked iPhone
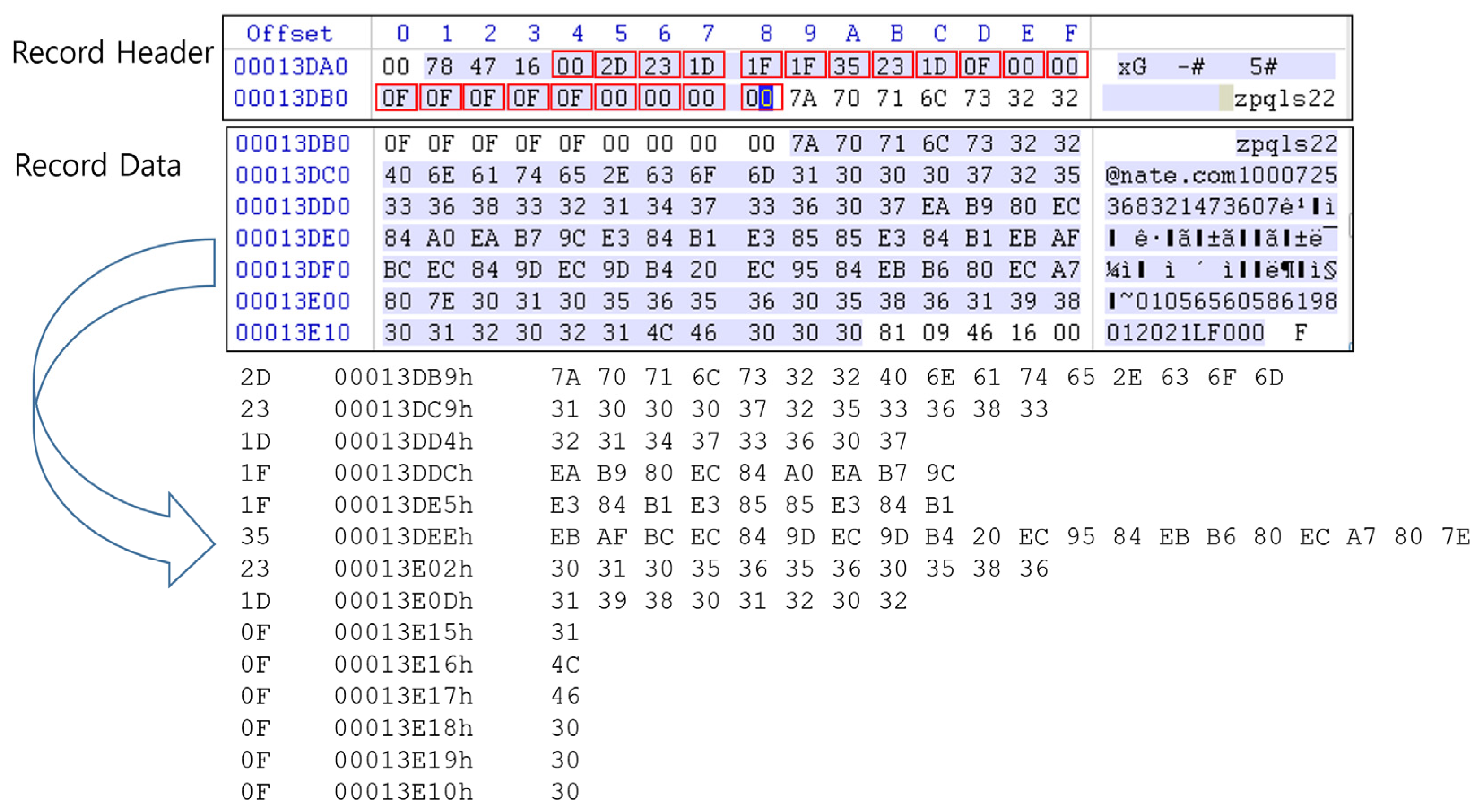
3.2. SQLite Logical Structure
3.3. Cell Structure
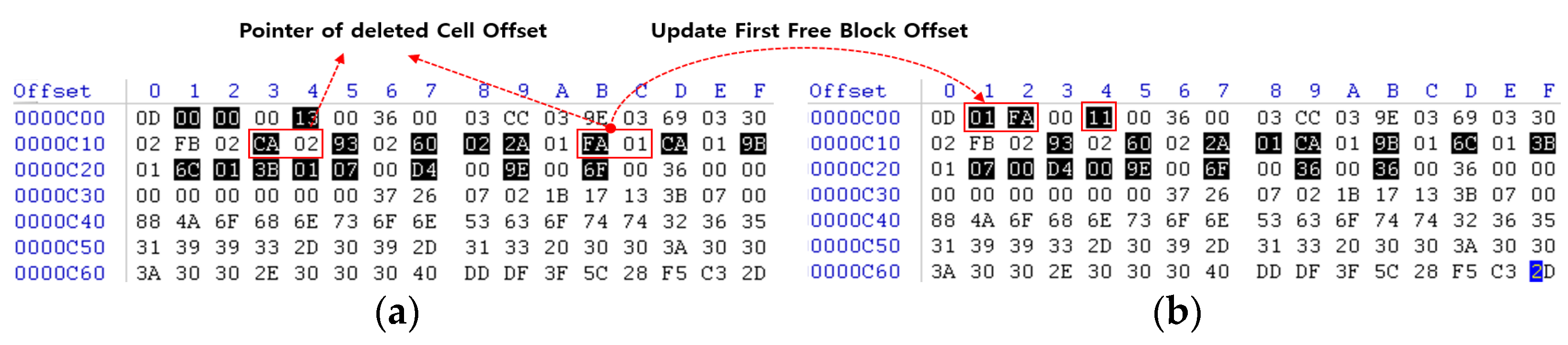
3.4. Existing Method Detection and Recovery of Deleted Cell
3.5. Summary
4. Experimental Environments
4.1. Message Deletion Events of Target Messengers
4.2. Tools and Experiment Environment
4.3. Experimental Method
4.3.1. Delete Part of Chat Message
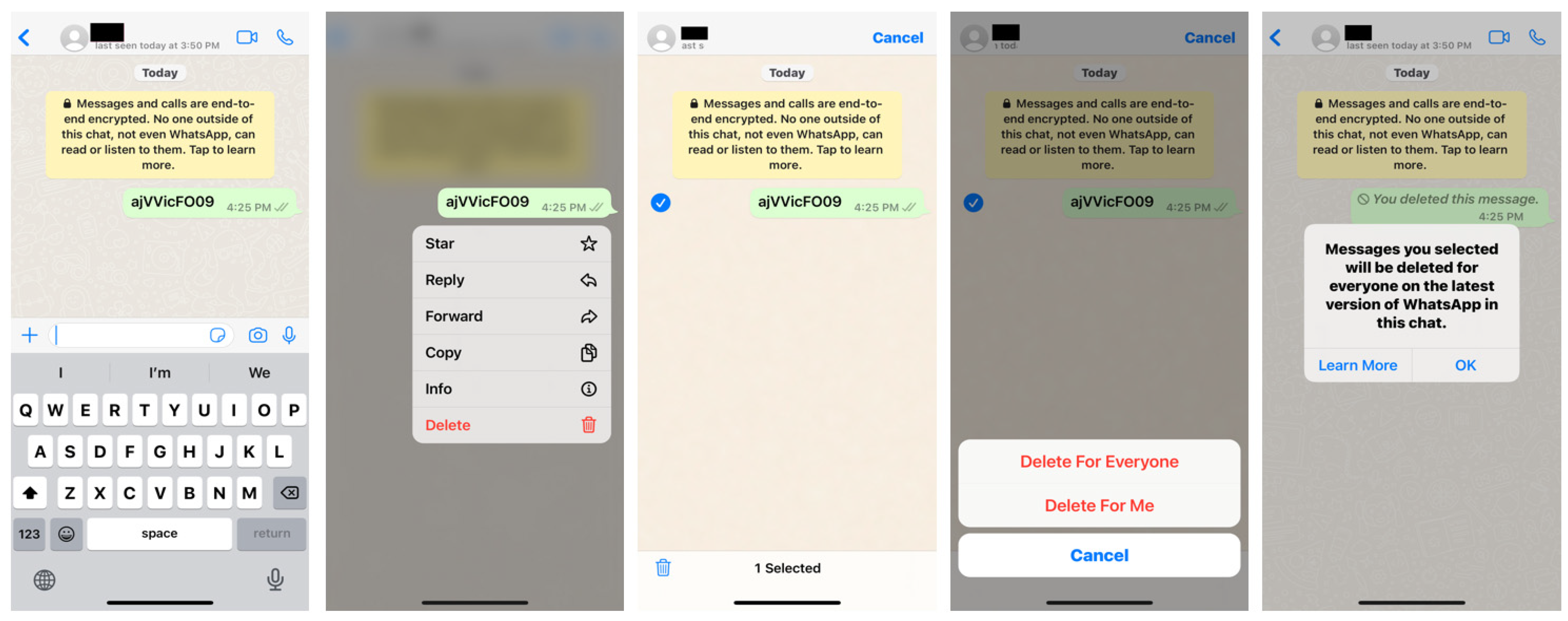
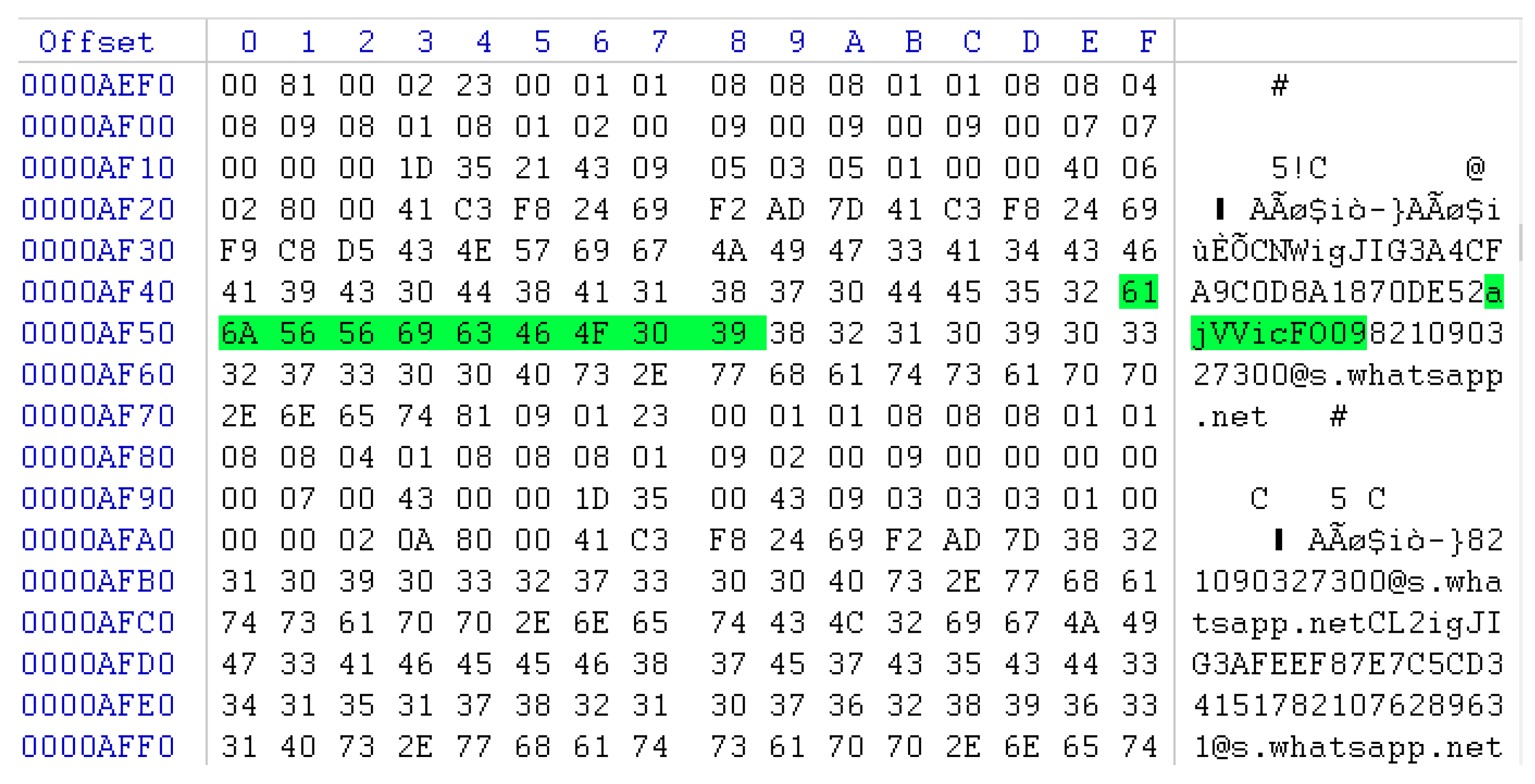
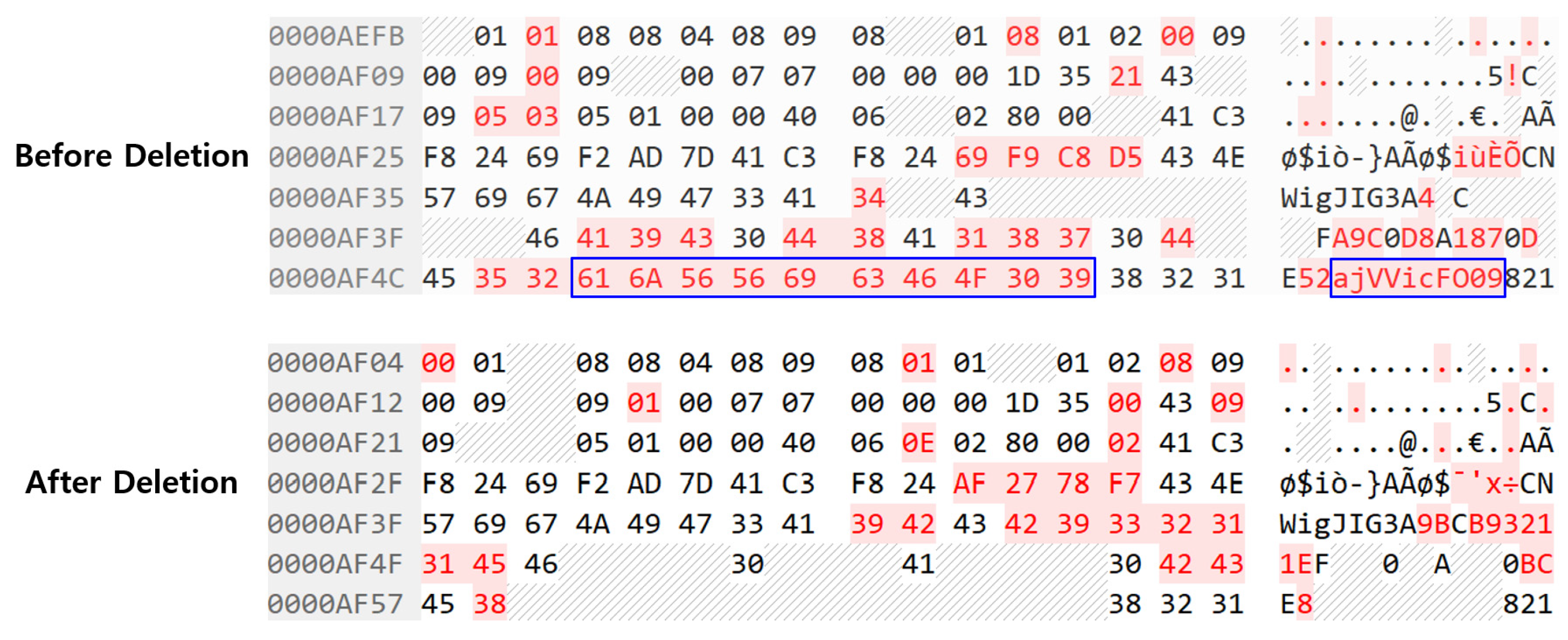
- After launching the instant messenger app (WhatsApp or WeChat) on the iPhone, send a message composed of ajVVicFO09.
- When the receiver confirms the message, delete the ajVVicFO09 message, close the app, and lock the phone.
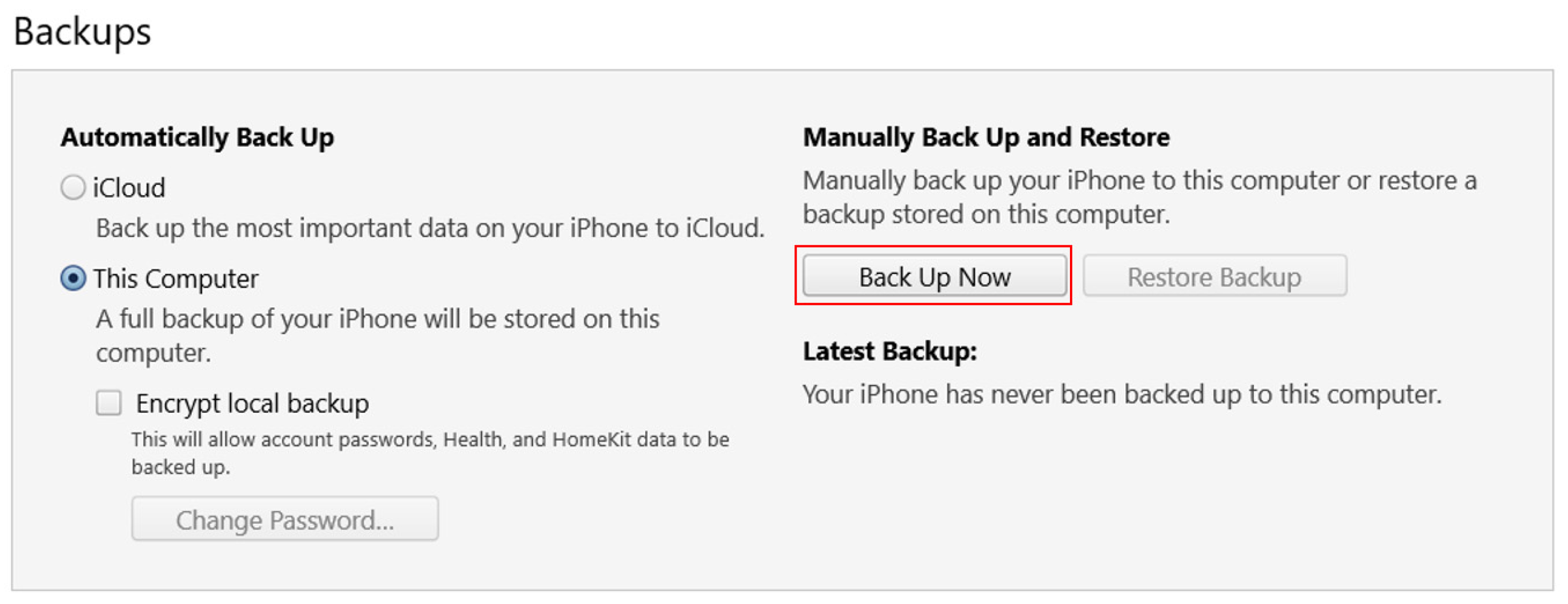
- After copying and saving UDID.plist to the forensic workstation, create a backup file using iTunes.
- Extract the instant messenger app (WhatsApp or WeChat) to be analyzed using iMazing to reconstruct the created backup file.
- Check the SQLite database file where the conversation contents are saved from the extracted app data, and search and analyze the traces of the ajVVicFO09 message.
4.3.2. Delete Chatroom
- After launching the instant messenger app (WhatsApp or WeChat) on the iPhone, send a message composed of qWMLuPMX6h.
- When the receiver confirms the message, delete the chat room, close the app, and lock the phone.
- After copying and saving UDID.plist to the forensic workstation, create a backup file using iTunes.
- Extract the instant messenger app (WhatsApp or WeChat) to be analyzed using iMazing to reconstruct the created backup file.
- Check the SQLite database file where the conversation contents are saved from the extracted app data, and search to analyze the traces of the qWMLuPMX6h message.
5. Verification Results
5.1. WhatsApp
5.1.1. Delete Chat Message
5.1.2. Delete Chatroom
5.2. WeChat
5.2.1. Delete Chat-Log
5.2.2. Delete Chatroom
5.3. Discussion
6. Conclusions and Future Works
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- You, G.; Kim, G.; Cho, S.J.; Han, H. A comparative study on Optimization, Obfuscation, and Deobfuscation tools in Android. J. Internet Serv. Inf. Secur. 2021, 11, 2–15. [Google Scholar]
- Domingues, P.; Nogueira, R.; Francisco, J.C.; Frade, M. Analyzing TikTok from a digital forensics perspective. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2021, 12, 87–115. [Google Scholar]
- Nakashima, E.; Albergotti, R. The FBI Wanted to Unlock the San Bernardino Shooter’s iPhone. It Turned to a Little-Known Australian Firm. Available online: https://www.washingtonpost.com/technology/2021/04/14/azimuth-san-bernardino-apple-iphone-fbi/ (accessed on 21 April 2022).
- Mahalik, H.; Edwards, S.; Murphy, C. iPhone Forensics-Separating the Facts from Fiction. A Technical Autopsy of the Apple/FBI Debate. Available online: https://www.sans.org/webcasts/iphone-forensics-separating-facts-fiction-technical-autopsy-apple-fbi-debate-101890/ (accessed on 25 March 2022).
- Hong, H. The Number of Password Cases Alone Is 56 Billion. iPhone Password That Even the FBI Can’t Solve. Available online: https://www.mk.co.kr/news/society/view/2022/04/321122/ (accessed on 11 May 2022).
- Dixon, S. Most Popular Global Mobile Messenger Apps as of January 2022, Based on Number of Monthly Active Users. Statista. Available online: https://www.statista.com/statistics/258749/most-popular-global-mobile-messenger-apps/ (accessed on 8 May 2022).
- Anglano, C. Forensic analysis of WhatsApp messenger on Android smartphones. Forensic Sci. Int. Digit. Investig. 2014, 11, 201–221. [Google Scholar] [CrossRef] [Green Version]
- Han, J.; Lee, S. A Practical Approach to Analyze Smartphone Backup Data as a Digital Evidence. DFRWS, USA. Available online: https://dfrws.org/presentation/a-practical-approach-to-analyze-smartphone-backup-data-as-a-digital-evidence/ (accessed on 22 May 2022).
- Shimmi, S.S.; Dorai, G.; Karabiyik, U.; Aggarwal, S. Analysis of iOS SQLite schema evolution for updating forensic data extraction tools. In Proceedings of the 8th International Symposium on Digital Forensics and Security (ISDFS), Beirut, Lebanon, 1–2 June 2020; pp. 1–7. [Google Scholar]
- Jeon, S.; Bang, J.; Byun, K.; Lee, G.; Lee, S. The method of recovery for deleted record in the unallocated space of SQLite database. J. Korea Inst. Inf. Secur. Cryptol. 2011, 21, 143–154. [Google Scholar]
- Jung, B.; Han, J.; Choi, H.; Lee, S. A study on the possibility of recovering deleted data through analysis of SQLite Journal in messenger application. J. Digit. Forensic 2018, 12, 11–20. [Google Scholar]
- Property List. Available online: https://en.wikipedia.org/wiki/Property_list (accessed on 17 May 2022).
- Satish, B. Forensic Analysis of iPhone Backups. Available online: https://www.exploit-db.com/docs/english/19767-forensic-analysis-of-ios5-iphone-backups.pdf (accessed on 2 June 2022).
- Apple Platform Security. Available online: https://support.apple.com/ko-kr/guide/security/welcome/web (accessed on 2 June 2022).
- About the ‘Trust This Computer’ Alert on Your iPhone, iPad, or iPod Touch. Available online: https://support.apple.com/en-us/HT202778 (accessed on 2 June 2022).
- The Database Header. Available online: https://sqlite.org/fileformat.html#the_database_header (accessed on 18 May 2022).
- B-Tree Pages. Available online: https://sqlite.org/fileformat.html#b_tree_pages (accessed on 18 May 2022).
- Jeon, S.; Bang, J.; Byun, K.; Lee, S. A recovery method of deleted record for SQLite database. Pers. Ubiquitous Comput. 2011, 16, 707–715. [Google Scholar] [CrossRef]
- Khalid, Y. Extracting WhatsApp Messages from an iOS Backup. Available online: https://yasoob.me/posts/extracting-whatsapp-messages-from-ios-backup/ (accessed on 6 March 2022).
- Qu, Y.; Yu, S.; Zhou, W.; Chen, S.; Wu, J. Customizable Reliable Privacy-Preserving Data Sharing in Cyber-Physical Social Networks. IEEE Trans. Netw. Sci. Eng. 2021, 8, 269–281. [Google Scholar] [CrossRef]
- Feng, J.; Rong, C.; Sun, F.; Guo, D.; Li, Y. PMF: A Privacy-preserving Human Mobility Prediction Framework via Federated Learning. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2020, 4, 1–21. [Google Scholar] [CrossRef]








| Offset | Size | Description |
|---|---|---|
| 0 | 1 | A flag indicating the b-tree page type 0 × 02: interior index B-tree page (Internal) 0 × 05: interior table B-tree page (Internal) 0 × 0A: leaf index B-tree page (Leaf) 0 × 0D: leaf table B-tree page (Leaf) Any other value for the b-tree page type is an error. |
| 1 | 2 | Byte offset into the page of the first freeblock |
| 3 | 2 | Number of cells on this page |
| 5 | 2 | Offset to the first byte of the cell content area. A zero value is used to represent an offset of 65,536, which occurs on an empty root page when using a 65,536-byte page size. |
| 7 | 1 | Number of fragmented free bytes within the cell content area |
| 8 | 4 | The right-most pointer (interior b-tree pages only) |
| Category | Property | Value |
|---|---|---|
| Forensic Workstation | OS | Microsoft Windows 11 |
| Platform | INTEL X64 | |
| File system | NTFS | |
| Target Device (Evidence) | Model | Apple iPhone XS |
| Capacity | 64 GB | |
| Software Version | iOS 15.4.1 | |
| File system | APFS | |
| Instant Messenger | WhatsApp Version | v2.22.6.74 |
| WeChat Version | v8.0.18 | |
| Data Acquisition | Method | Logical (Backup File) |
| Tool | iTunes v12.12.3.5 | |
| Experiment Keyword | For deleting part of the chat Message | ajVVicFO09 |
| For deleting chatroom | qWMLuPMX6h | |
| Forensics Tools for Analysis | SQLite DB Browser | DB Browser for SQLite v3.12.2 |
| Backup Reconstructor | iMazing v2.14.8 | |
| Hexadecimal Comparison | Beyond Compare4 v4.4.2 | |
| Keyword Search | dnGrep v3.0.42.0 |
| No | Column Name | Declared Type | Default Value | Not Null |
|---|---|---|---|---|
| 1 | Z_PK | INTEGER | 0 | FALSE |
| 2 | Z_ENT | INTEGER | 0 | FALSE |
| 3 | Z_OPT | INTEGER | 0 | FALSE |
| 4 | ZCHILDMESSAGESDELIVEREDCOUNT | INTEGER | 0 | FALSE |
| (skip 26 columns) | ||||
| 31 | ZPUSHNAME | VARCHAR | 0 | FALSE |
| 32 | ZSTANZAID | VARCHAR | 0 | FALSE |
| 33 | ZTEXT | VARCHAR | 0 | FALSE |
| 34 | ZTOJID | VARCHAR | 0 | FALSE |
| No | Column Name | Declared Type | Default Value | Not Null |
|---|---|---|---|---|
| 1 | CreateTime | INTEGER | 0 | FALSE |
| 2 | Des | INTEGER | FALSE | |
| 3 | ImgStatus | INTEGER | 0 | FALSE |
| 4 | MesLocalID | INTEGER | FALSE | |
| 5 | Message | TEXT | FALSE | |
| 6 | MesSvrID | INTEGER | 0 | FALSE |
| 7 | Status | INTEGER | 0 | FALSE |
| 8 | TableVer | INTEGER | 1 | FALSE |
| 9 | Type | INTEGER | FALSE |
| Category | SQLite File | Deletion Subject | The Deleted Area on Page | Message Privacy | |
|---|---|---|---|---|---|
| Column Data | Cell | ||||
| ChatStorage.sqlite | Part of message | Update with NULL (shrink) | Exists | Protected | |
| Chat room | Message not found | ||||
| Message_2.sqlite | Part of message | Updated whole cell area with 0 × 00 | Protected | ||
| Chat room | Message not found | ||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shin, J.; Seo, J.-T. Verification of Privacy Protection Reliability through Mobile Forensic Approach Regarding iOS-Based Instant Messenger. Sustainability 2022, 14, 13281. https://doi.org/10.3390/su142013281
Shin J, Seo J-T. Verification of Privacy Protection Reliability through Mobile Forensic Approach Regarding iOS-Based Instant Messenger. Sustainability. 2022; 14(20):13281. https://doi.org/10.3390/su142013281
Chicago/Turabian StyleShin, Jiho, and Jung-Taek Seo. 2022. "Verification of Privacy Protection Reliability through Mobile Forensic Approach Regarding iOS-Based Instant Messenger" Sustainability 14, no. 20: 13281. https://doi.org/10.3390/su142013281
APA StyleShin, J., & Seo, J.-T. (2022). Verification of Privacy Protection Reliability through Mobile Forensic Approach Regarding iOS-Based Instant Messenger. Sustainability, 14(20), 13281. https://doi.org/10.3390/su142013281







