Abstract
The usage of the Internet increased dramatically during the start of the twenty-first century, entangling the system with a variety of services, including social media and e-commerce. These systems begin producing a large volume of data that has to be secured and safeguarded from unauthorised users and devices. In order to safeguard the information of the cyber world, this research suggests an expanded form of differential evolution (DE) employing an intelligent mutation operator with an optimisation-based design. It combines a novel mutation technique with DE to increase the diversity of potential solutions. The new intelligent mutation operator improves the security, privacy, integrity, and authenticity of the information system by identifying harmful requests and responses and helping to defend the system against assault. When implemented on an e-commerce application, the performance of the suggested technique is assessed in terms of confidentiality, integrity, authentication, and availability. The experimental findings show that the suggested strategy outperforms the most recent evolutionary algorithm (EA).
1. Introduction
Technology and statistics advance quickly in the contemporary day, where the Internet is everywhere. The Internet is becoming increasingly important to organisations, governments, enterprises, and educational institutions. Although there may be a positive side, some of its negative aspects can not be ignored, which can seriously impact a person or an organisation. Malevolent systems are primarily responsible for tasks such as creating bogus websites, spreading infections, listening in on conversations, modification of data, etc. Some of these operations risk national security and military structure, which might result in significant losses since in IoT-enabled applications data or information mostly are transient and updated by anonymous self-governing devices. With such a large number of devices, terminals, and machines connecting to an Internet of Things (IoT) network, a huge amount of data and security vulnerability makes security a burning issue [1,2].
Confidentiality may be obtained through cryptography, which means “strange texts”. Cryptography has advanced to new levels in the modern world, offering businesses and people privacy to the point that only authorised staff may access the data [3]. With a lengthy history, strong fundamentals, and ongoing development, cryptography is still evolving today. The “secret” hieroglyphics utilised by the Egyptians are one of the first instances of encryption. The most popular method used today, the Caesar cypher, was also employed by the people of Rome in ancient times [4]. Ancient Greeks also used a scytale for cryptographic encryptions. Worldwide, people use cryptography to safeguard their data and information on a daily basis without even recognising that they are doing something so complex. While cryptography offers advantages, it also has certain disadvantages. Because cryptographic systems are so fragile, even a small alteration or mistake can have disastrous effects and result in system breaches [5].
Even though most systems no longer know that they are using it, cryptography is used daily to safeguard information and records by billions of systems worldwide. Although it is extremely advantageous, it is also seen as being rather brittle since cryptographic systems can be broken by a programming or specification error. Different kinds of assaults on information systems that undermine security, integrity, confidentiality, and availability are the work of the hostile system.
Therefore, the security of the system or application cannot be compromised; hence, it requires implementing the optimisation algorithm into the information system to recognise requests from these dangerous nodes and assist systems in warning them before the assault.
Although other classes of optimisation techniques are accessible in the literature, DE is one of the key strategies [6]. Numerous non-deterministic polynomial-time (NP)-complete problems in optimisation methods can be resolved using the population-based meta-heuristic method known as DE. It functions well across a variety of test areas. The optimisation method considers several operations for exploration and exploitation, such as mutation, crossover, and selection. A new vector known as the donor vector is produced during the mutation process. A crossover is then performed on the donor vector to generate a new vector known as the trailing vector. The target, donor, and trail vectors are ultimately picked as the three vectors’ most tasteful solutions. Based on the fitness value, they are then included in the population for the subsequent generations.
1.1. Problem Statement
Highlights of the problem description are as follows.
- The time complexity of the existing evolutionary algorithms [7,8,9,10,11,12,13,14,15,16,17,18] is high. This is because of the several iterations to locate the ideal value. This difficulty worsens with a bigger population and a non-continuous function.
- Security keeps up with the impressive advancements being made in the field of information systems [19]. Intelligent attacks in the IoT environment are viable by sending malicious requests and responses. As a result, it is necessary to safeguard the information by recognising the assaults before they are carried out.
The following is a list of improvements over existing approaches:
- Most existing techniques are based on non-continuous functions, which increases the complexity of optimisation algorithms [10,11,12,13,20,21,22]. In contrast, the proposed method is based on the new automatic adaptation-based strategy, which is incorporated with DE to overcome the searching strategy, which reduces time complexity and provides diversity and convergence rate.
- The methods available in the literature [5,19,23,24,25,26], when applied in the e-commerce application of information systems, are found to be insecure in terms of confidentiality, authenticity, availability, and integrity. In comparison, the proposed method optimises the best fitness function of the different generations of e-commerce applications, achieving better confidentiality, authenticity, availability, and integrity.
The proposed method is incorporated into the security framework to provide security for IoT-enabled applications. These can be any modern IoT applications because in the IoT network devices work independently, hence the possibilities of security attacks increase. This method is specially designed, keeping in the mind the requirements of IoT-enabled e-commerce applications such as supply chain management, banking, retail management, inventory management, etc., rather than general applications. IoT devices exchange data with each other, which helps retail and e-commerce firms to execute their operations smoothly and efficiently. As e-commerce grows in popularity, the possibilities for IoT use in the industry expand. This application can be handy in remote access management, tracking of product in journey, enhanced personalised experience about the customers and products, etc.
With the advancement of technologies such as artificial intelligence (AI), machine learning (ML), and data analytics the possibility of security attacks in IoT-enabled applications is increasing, hence it requires an advanced-level security shield which can cope with the coming challenges. Keeping the security vulnerability of IoT-enabled applications, this work proposed a new AI-based DE method to shield from the security attacks.
1.2. Author’s Contribution
Highlights of the author’s contribution are as follows:
- A novel adaption-based strategy is devised and incorporated with the DE algorithm to identify the request of the malicious node to mitigate security attacks.
- The devised mutation operator considers the environment factor, i.e., an internal environment that maintains the diversity in an initial generation and gives impetus to the convergence speed of the DE algorithm.
- In the performance analysis of confidentiality, integrity, authentication, and availability, the proposed approach is tested on an e-commerce application.
- The observed result shows that the proposed approach obtains a better solution in terms of best, average, and worst fitness functions on a 3-dimension application-based test.
1.3. Article Organisation
The organisation of the rest of the paper is as follows: Section 2 presents a description of existing DE variants and recent approaches devised for information security. Section 3 describes an application for an information security-based evolutionary model. Section 4 outlines a description of the proposed methodology. Section 5 describes the experimental result, in which the obtained results are compared with existing DE, and related standard cost estimation approaches. Finally, Section 6 concludes the study and paves future work paths.
2. Literature Review
The goal of the evolutionary algorithm is to solve the overall optimisation issue. The research makes it quite evident that DE has an issue with stagnation. To deal with these issues, a handful of multi-objective differential evolutionary (MODE) strategies and Pareto-based strategies have been suggested [6,7,8,9,10,11,12,27]. According to the population, the existing MODE-based technique [11] executes mutation and crossover. Additionally, non-dominating sorting was used to reduce the temporal complexity.
The authors of [16] proposed a homeostatic factor-based method to increase the diversity of NASA 93 projects. This method performs better than multi-objective-based software cost-estimating techniques. The authors of [18,19] presented a hybrid technique that controlled two distinct operators and can be applied in many applications. This method performs better than a number of earlier multi-objective algorithms. For multi-objective situations, the authors of [10] created a brand-new Pareto-based (PBDE) differential evolution approach.
Susan et al. [26] stated that computer security is a target that keeps evolving as time goes on. Various mathematical and algorithmic functions are significant concerns in several security tutorials, including hashing techniques and encryption. Othman O. Khalifa et al. [23] illustrated the main components, plans, and characteristics of cryptography are security and privacy. In this era, the age of information communication has played a significant role in the evolution and development of technology. Therefore, the data must be protected and kept secure while transferring through the communication source.
Nitin Jirwan et al. [24] stated that when the data is transmitted, the highest priority is given to data encryption among all the processes present, and an encryption algorithm is applied to data in order to reach the end-user without being interrupted or compromised. Various asymmetric and symmetric cryptographic techniques are used and demonstrated in information transmission.
Callas, J. [25] studied and discussed matters such as privacy enhancement using cryptography, laws related to cryptography, legal changes related to cryptography, reliability of algorithms, and privacy enhancement technologies. He determined and stated that the use of cryptography by society at this time would determine the future of cryptography. This includes the current laws and regulations on cryptography and what the community wants to achieve by using cryptography. He also stated that even with the recent progress of cryptographic algorithms, the field has a lot of things to be improved and new things to be discovered for future generations. He said that the future of cryptography depends on the machines producing strong and secure keys and the rightful owners of the keys to access the information, while others without the keys should not be able to access it. He also tried to explain the view of people on the privacy of messages and security such that any unauthorised person cannot read them.
Cryptography wants to achieve two primary goals: authenticity and privacy, as outlined by different authors [26,28,29,30,31]. The amount of security provided can be expressed in terms of the theoretical secrecy of Shannon and the theoretical authenticity of Simmon.
Schneier [32] stated that topics such as security should not be kept secret as they can be very brittle, and security secrecy is a matter to be made known and not kept secret. If by any means secrecy is lost or inaccessible, then getting it back would be nearly impossible. Schneier cited that encryption and decryption using more minor keys can be transmitted easily and must use a principle. The algorithm used for cryptography must be secure enough to be displayed to the public and still offer such security that no one can crack it. Public scrutiny is the only reliable method to be followed to make more and more improvements in security.
Cloud computing can be used for the secure transmission of cryptography, as cited by Chachapara K. et al. [33,34,35] and illustrated the frameworks such as AES and RSA. AES is, to date, one of the most robust cryptographic algorithms. Users using the cloud have the accessibility to generate various keys for different users and allow different types of permissions to access the files.
As stated in [36], many discussions about cryptography are being developed. The author mentioned that the hash function plays a significant role in cryptography, generating numbers for any piece of data. As the years passed, the weakness of MD5’s algorithm became known, and now a situation arose about how to create secure hash functions.
Gennaro, R. [37,38] cited the role of randomness in cryptography. A random process is one whose outcome or result is unknown and can vary from time to time. He stated that randomness is necessary for cryptography so that the output cannot be predicted, or any user cannot learn the pattern.
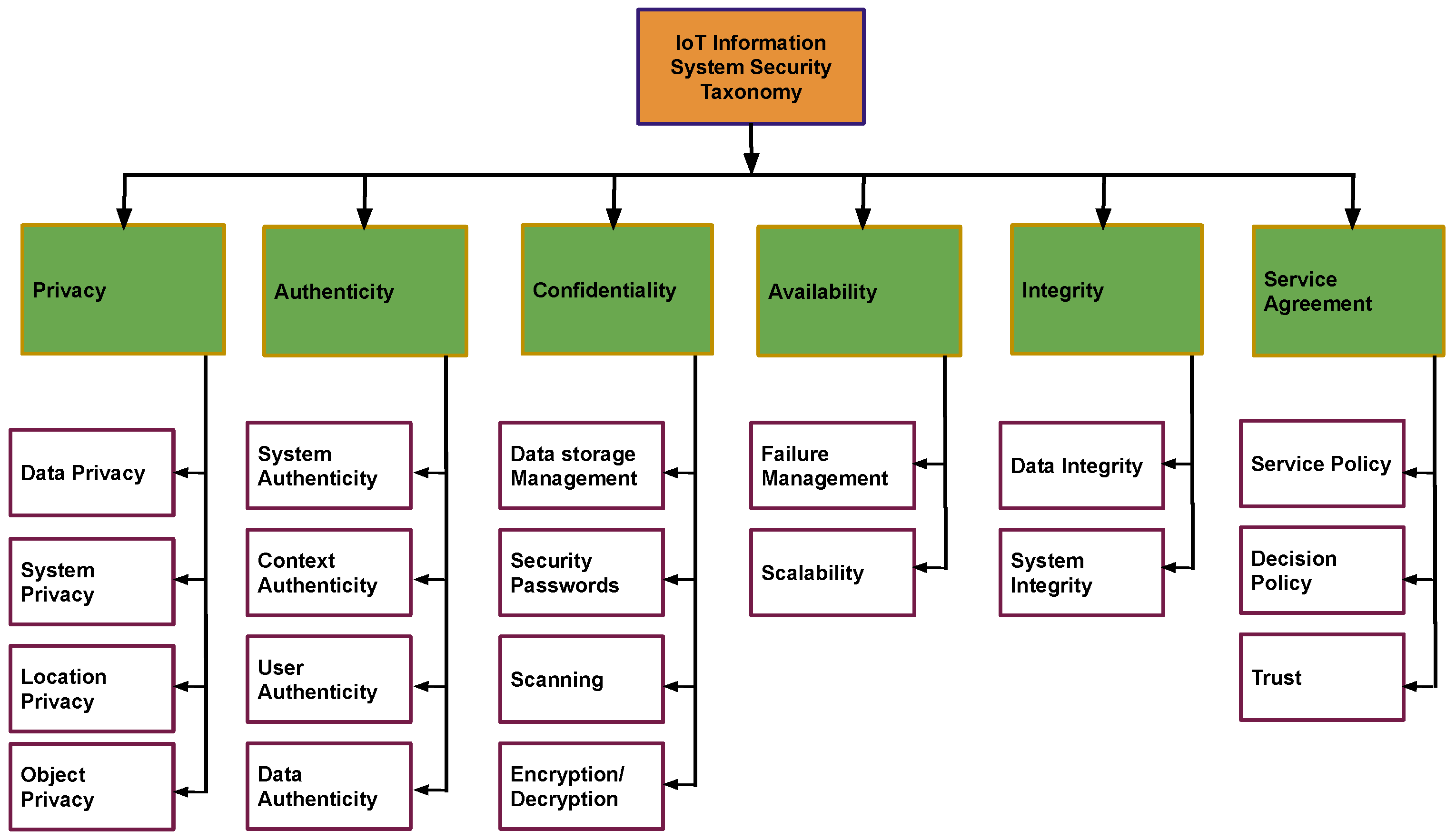
Preneel, B. [39] stated how cryptography was after the Snowden era was over. He discussed practices such as the security of ICT systems, surveillance of systems as a whole, and the methods through which the cryptographic systems could be attacked. From the literature study, various types of security taxonomy have been identified. These security threats can be classified into different groups, as depicted in Figure 1.
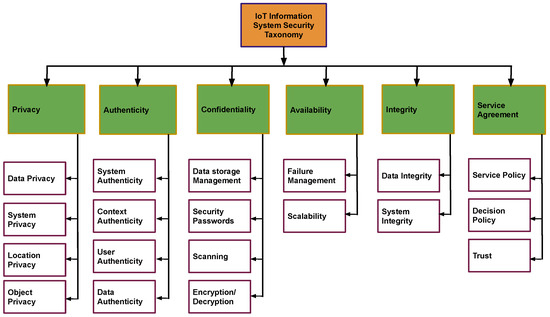
Figure 1.
Information system security taxonomy of smart applications.
From the literature review, the following shortcomings have been identified, as shown in Table 1.

Table 1.
Technical gaps within existing techniques.
- The modern information system not only requires the robust protection of data but also needs to identify the malicious attacks that will breach security.
- The optimisation technique-based threat identification systems are now evolving. This technique can be used in information systems to maintain the integrity, authenticity, confidentiality, and availability of data. However, the existing methods suffer from the diversity issue in finding the optimal solution (threats) to secure the system.
- The second issue with the existing optimisation technique is the non-constraints solution, hence delaying the search capability to identify the optimal solution. It also causes the local optimal problem in finding the optimal solution.
- The tuning of security parameters in optimisation techniques is complex when identifying malicious attacks on data.
3. Related Terminologies of the Proposed Work
This section presents the different terminologies related to the proposed work and IoT-enable applications.
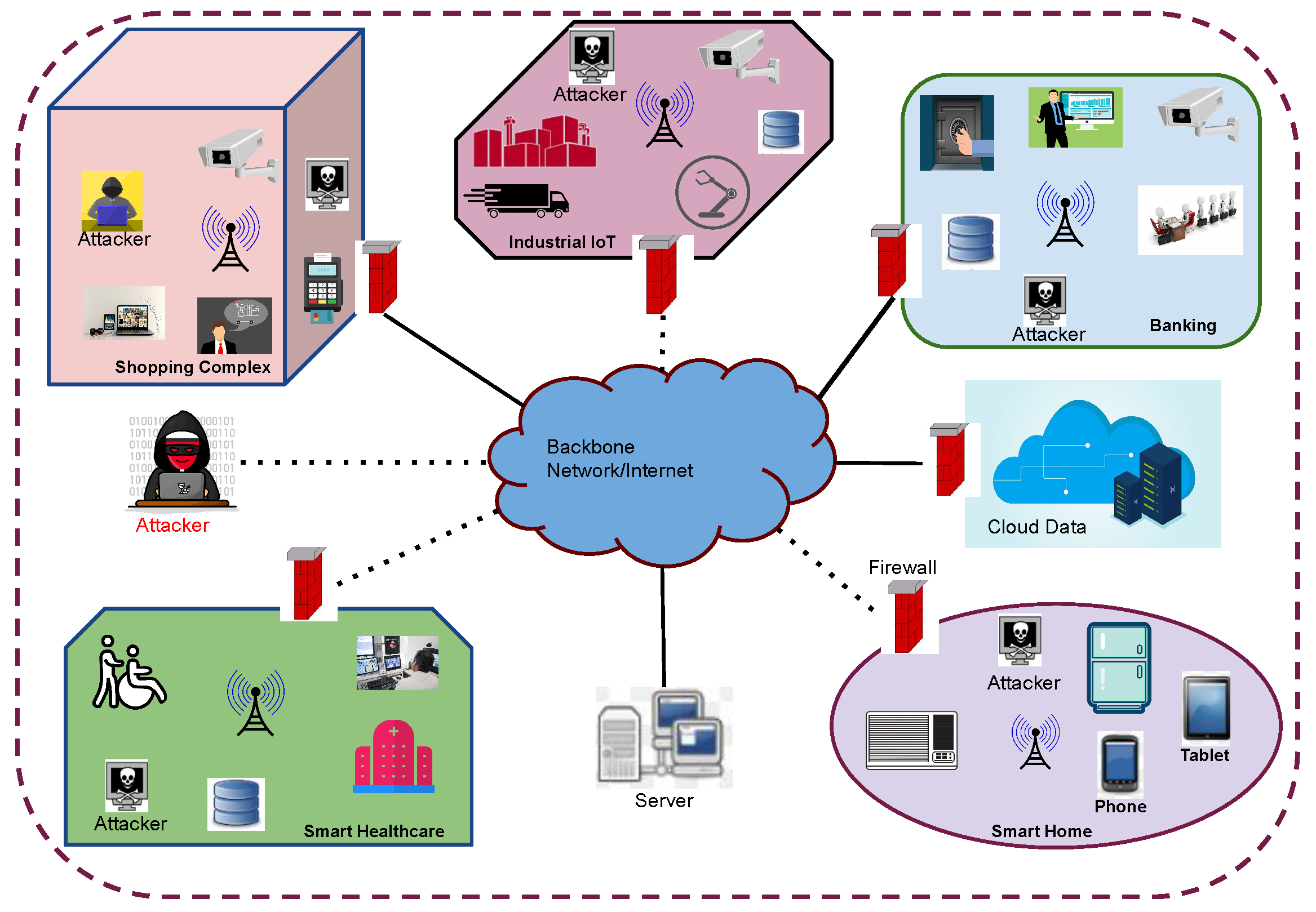
3.1. Deployment Scenario
The proposed method incorporated the security framework to check the validity of data from e-commerce sites. The proposed framework of the security model is designed according to the deployment scenario of different objects, as shown in Figure 2. In this figure, different components (along with attackers) are mounted in different locations and environments to access services. The attackers can disrupt the normal services of a user or devices, hence needs to prevent these attacks. This model represents the confidentiality of data according to the visit to an e-commerce site. Therefore, the optimisation-based security framework checked the confidentiality and integrity of data: these checks, the acceptance rate of different authenticated users and hackers, and the confidentiality and integrity level of requests, and the response of data for different users and malicious systems.
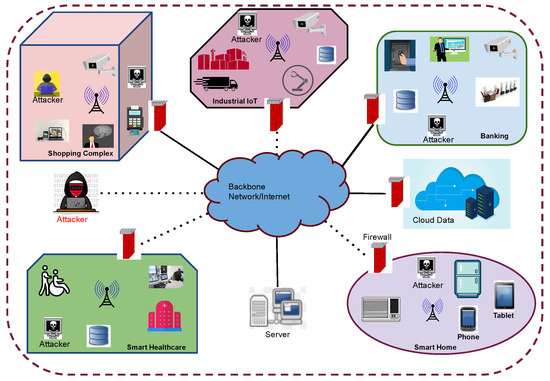
Figure 2.
Proposed model of the security overview of smart applications.
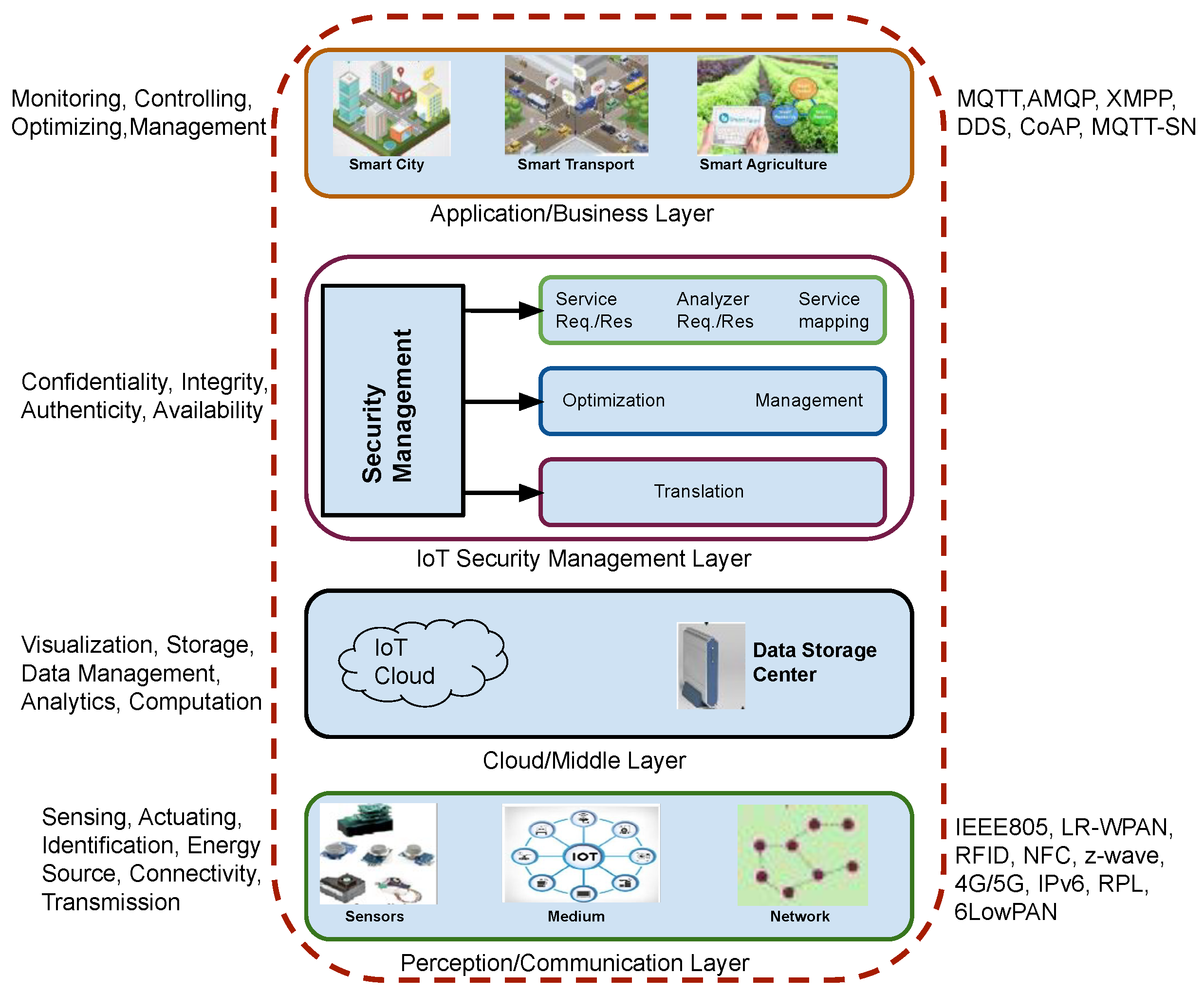
3.2. Layered Stack of Information Security Model
The layered protocol stack of modern IoT-based information security systems is depicted in Figure 3. This layered architecture is proposed keeping in mind the security management requirements of different components. In modern IoT-enabled applications, individual devices request multiple services and need to respond independently without interaction with a human. The top-most layer of this architecture provides smart collaboration and coordination between the different applications and services.
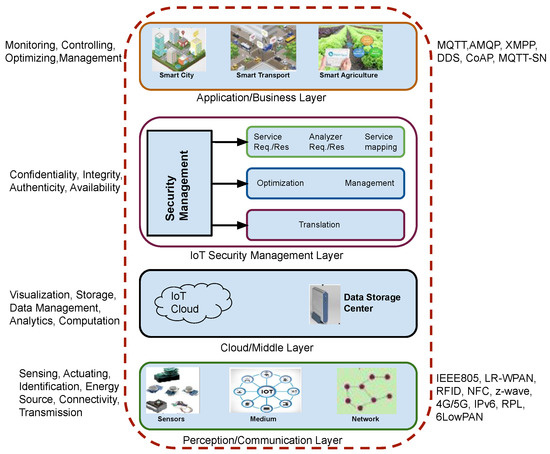
Figure 3.
Proposed model of the security layer architecture.
The confidentiality, integrity, availability, and authenticity of service requests are managed by the security management layer. This layer is in charge of accurately mapping, evaluating, and processing service requests prior to execution in order to achieve the necessary level of security to serve a request. Consequently, this layer handles the generation, administration, and implementation of service requests as well as object virtualisation. The major methods used to ensure security include optimisation, surveillance, translation, coordination, etc. This layer employs a more expressive security policy for use control, which allows event-based authorisations and responsibilities with temporal operators.
The data generated from various sources are stored in the cloud/middle layer. To deliver effective services, this layer manages, purifies, transforms, and analyses data. The communication between the devices is established via the perception and communication layers.
4. Materials and Methods
4.1. Materials
This section describes the data sets used for the experimental evaluation of the proposed work. The data set used for evaluation consists of requests from different sources, including malicious requests to access the information system’s data. An automatic request generator system generates these requests [21,22]. The data sets are taken over a two-month time period. These requests are passed to our proposed optimisation technique to identify malicious requests. These malicious request attacks can be related to authenticity, integrity, confidentiality, or data availability.
4.2. Proposed Method
This section presents the detailed work of the proposed optimisation technique. The DE algorithm is a global optimisation algorithm that tackles constraint and unconstrained issues. However, solving real-world application-based problems with evolutionary algorithms such as DE, particle swarm optimisation (PSO), whale optimisation (WOA) algorithm, and artificial bee (ABCO) colony optimisation is challenging.
Therefore, it is inevitable to design a new evolutionary algorithm that must protect real-world information from malicious attacks. Hence, this work outlines a novel agile adaption-based operator (AABO). This operator automates the adaptation technique to select the best vector from the global search space. It enhances the maintenance of diversity and convergence speeds. This paper presents a better environment for automatically adapting to the environment. The proposed work creates a feasible solution for global search space according to agile adaption-based selection. The process of selection strategy is explained step by step, as given below:
4.2.1. Initialisation
This section outlines random population members of the particular problem or application. This application randomly initialised population members with tuning parameters of problem specification. This problem lies between the lower and upper bound values. Let = , , , , …, be the vector, where individual component values are assigned using Equation (2). After that, the vector can be re-formulated as follows:
The starting population is selected randomly between lower and upper bound
where depicts the variable’s value of the upper bound according to the taken problem area and denotes the lower bound value of the variable according to the taken problem. These vectors are used in application-based problems.
4.2.2. Agile Adaption-Based Operators (AABO)
This section presents the design of a modified version of the original mutation operator of the DE algorithm. This operator modifies the best vector of the standard DE algorithm. This operator incorporates the agile-based adaption techniques according to the feasible search area. The agile adaption-based fitness function to select the best vector and the process is explained in Equation (3):
where denotes the feasible solution of the current environment, and Automatic random vector denotes the selection random best vector according to the lower bound and upper bound.
4.2.3. Generation of New Donor Vector(DV)
The DE method is used to construct a DE/BEST/1 mutation scheme. The scheme incorporates the agile adaption vector for a specific mutation, which provides sufficient diversity. Equations (5) and (6) define the donor vector and the viable environment, respectively.
Update the adaption operator:
where represents the donor vector used in the agile adaption concept for heuristic search and G is iteration or generation. represents the agile adaption-based vector, which is selected according to the best fitness value. is a mutant factor; it selects a random value between 0.1 to 1.8. This value helps the optimum search from the difference vector of the mutation operator. , , , and denote the difference vector of mutation strategy. These mutation strategies (Equations (5) and (6)) provide sufficient diversity for the donor vector and also enhance the convergence rate.
4.3. The Proposed Algorithm
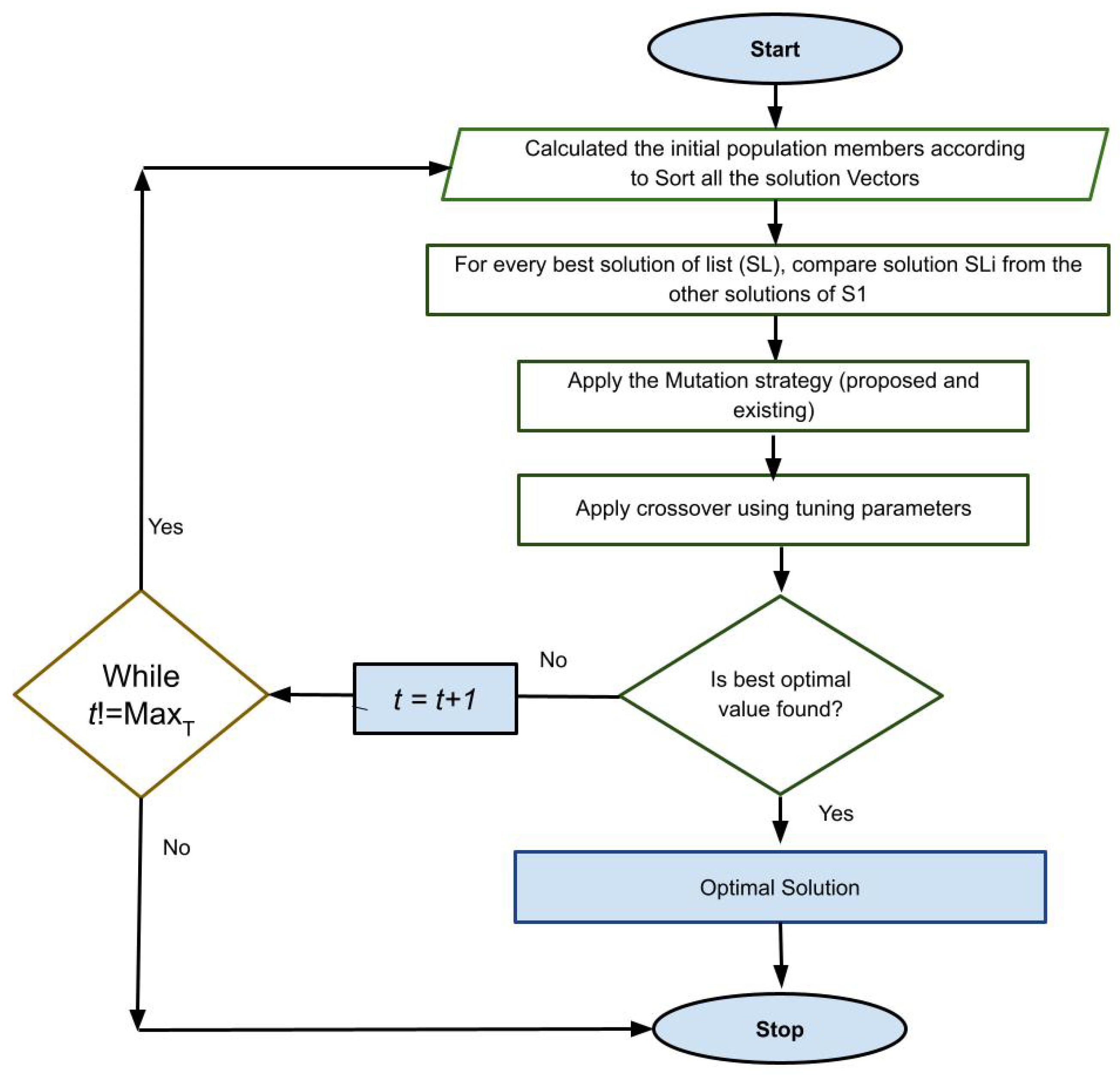
The pseudo-code of the proposed algorithm is shown in the Algorithm 1. This algorithm will be incorporated into the e-commerce-based application to enhance security by considering the set objective functions.
Crossover: It applies the crossover operator after completing the mutation operator. The operator compares the mutant vector to the original vector to find the best adaption value and selects the best ideal value of the search space. It can stop iterating when it finds the best search space value.
Selection: After completing the crossover operator, AAOB applies the selection process of the best optimum vector. This operator compares mutant and offspring vectors. AAOB selects the best optimum vectors or values according to the fitness function. In the operator selection, the concept of the survival of the fittest is generally used. This idea is used in choosing the best optimum value. Still, if it does not produce an optimal value, then this operator finally chooses the original vectors. The whole process is outlined using Algorithm 1 and a flowchart, as shown in Figure 4.
| Algorithm 1: Proposed DE-Based Evolutionary Algorithm |
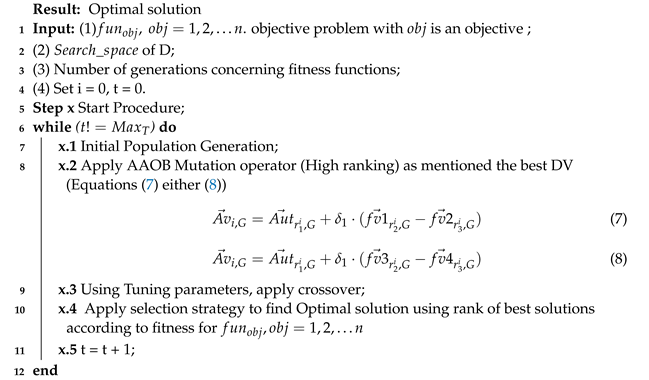 |
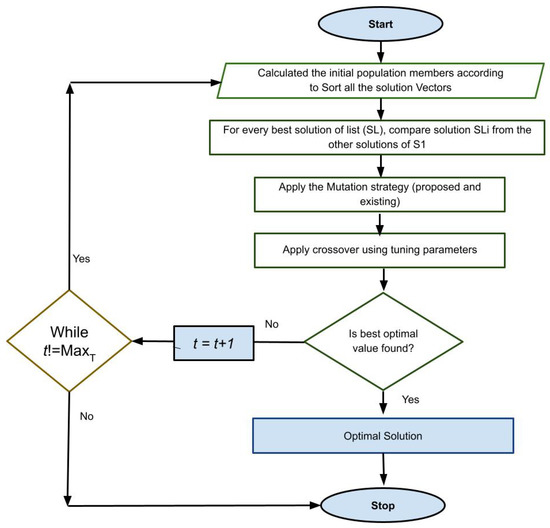
Figure 4.
Flowchart of the proposed algorithm.
4.4. Algorithm of Information Security Model
As shown in Algorithm 1, the proposed method is used in an IoT-enabled e-commerce application to estimate data during data requests and responses to multiple users to improve the system’s security. Various constraint functions, such as secrecy and integrity, were added to this technique. This e-commerce-based technique is discussed step-by-step in Algorithm 2. The objective functions such as and were optimised using this proposed technique. The following is a complete description in the form of pseudo-code of the new algorithm:
- In step 1, the initial input of data requests and data responses of the e-commerce-based application are determined.
- In the second step, the newly obtained vector from various constraint functions is added to the population.
- Afterward, weights assigned to each objective function are done using Equation (13).
- Finally, Step x.1 to Step x.6 are iterated to find optimum solution for , , etc.
| Algorithm 2: Proposed Information Security-Based Evolutionary Algorithm |
 |
4.5. System Model: Objectives Function of Information Security Model
This section presents five different types of objectives function used for the information service framework, i.e., confidentiality (CONF), integrity (INT), authentication (AUTH), and information request and response metrics. These are used to evaluate the proposed algorithm’s effectiveness. The detailed specifications of these objectives are available in [3,8]:
- (I)
- Confidentiality of Data (CONF): The first objective (C1), the confidentiality of the system is represented as CONF(, ). Information requests and data responses are transmitted between requesting and responding nodes. The C1 in terms of cost is obtained by applying Equation (9):where denotes information request and denotes information respond and service cost calculated by CONF(, ) during the data transmission.
- (II)
- Integrity of Data (INT): The second objective (C2) is calculated in terms of modifying data communication per unit time of node using Equation (10):where denotes the integrity or rate of data modification between insecure nodes i and j, denotes the modified transmitted and responded on devices(systems), and CONF(, ) denotes the confidentiality of nodes in the information system.
- (III)
- Availability of Data (AVL): The third objective is the availability of data services within the e-commerce framework. In terms of the availability of data from the server or cloud, the third objective (C3) is computed as follows: Equation (11):where is respond data for to different request information system (). denotes modified data per unit time between different nodes i and j.
- (IV)
- Authentication of Data (AUTH): The third objective is the authenticity of data services within the e-commerce framework. In terms of the authenticity of data from nodes, the third objective (C4) is computed as follows: Equation (12):where is respond data for to different request information systems (). denotes modified data per unit time between different nodes i and j. denotes the number of requests for nodes, and denotes the number of responses (the connection between nodes) for nodes from the system.
4.6. Formulation of Fitness Function of Information System
The fitness functions of the IoT-enabled services obtained by applying Equations (9)–(12) are non-contradictory. Hence, a summation of the weighted approach is applied using Equation (13), for all the objectives ( and ) and these objectives are turned into a single function to evaluate the final performance.
where values of , , , and are the weights assigned to each of the objective functions. The weight factor is crucial to evaluate the performance from one to another objective in multi-objective problems. The proposed IoT-enabled system is compared based on the fitness function with PSO, DE, and the whale optimisation method (WOA).
5. Experimentation and Analysis
5.1. Simulation Framework
The description of the simulation framework considered to execute the proposed and existing algorithms are as follows:
- The test-bed was conducted using a Windows 10 Pro 64-bit operating system, an Intel Core i7-8850H processor, and 8 GB of RAM.
- Every benchmark serves as a test-bed in the specified search space, which is , with D standing for dimension.
- For the comparative analysis, the proposed algorithm is computed 30 times, with the best, average, and worst fitness functions.
- Each test function’s initial population is set at 100. For the maximising the problem, the exploration and exploitation phases are carried out across it.
5.2. Experimental Setup
This section presents a designed simulation framework of the security model based on the line of the optimisation model. This framework works with the proposed method and tests the security function and parameters, as shown in Table 2. It also checks the performance of standard evolutionary optimisation algorithms in the same simulation framework [7,18,40]. The previous section explained the algorithm’s parameters for different scenarios, such as confidentiality, integrity, availability, and authentication functions. The results of the proposed method are compared in several scenarios of information systems (e-commerce) on these parameters. Furthermore, each goal function was performed ten times in succession, and the statistics values were calculated. The proposed method uses 100 generations for testing the confidentiality, data integrity, availability, and authentication indicator, which are shown in Figure 5, Figure 6, Figure 7, Figure 8, Figure 9 and Figure 10.

Table 2.
Parameter of the proposed algorithm.
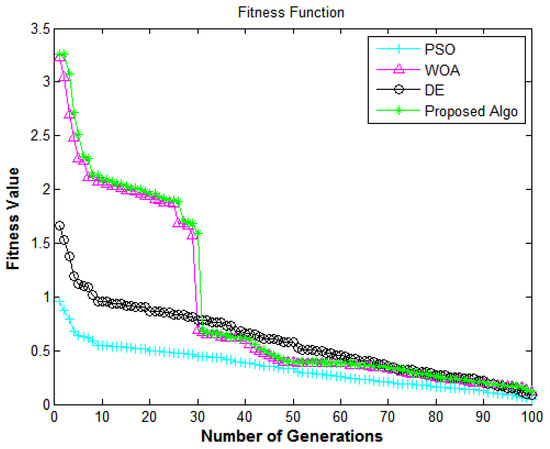
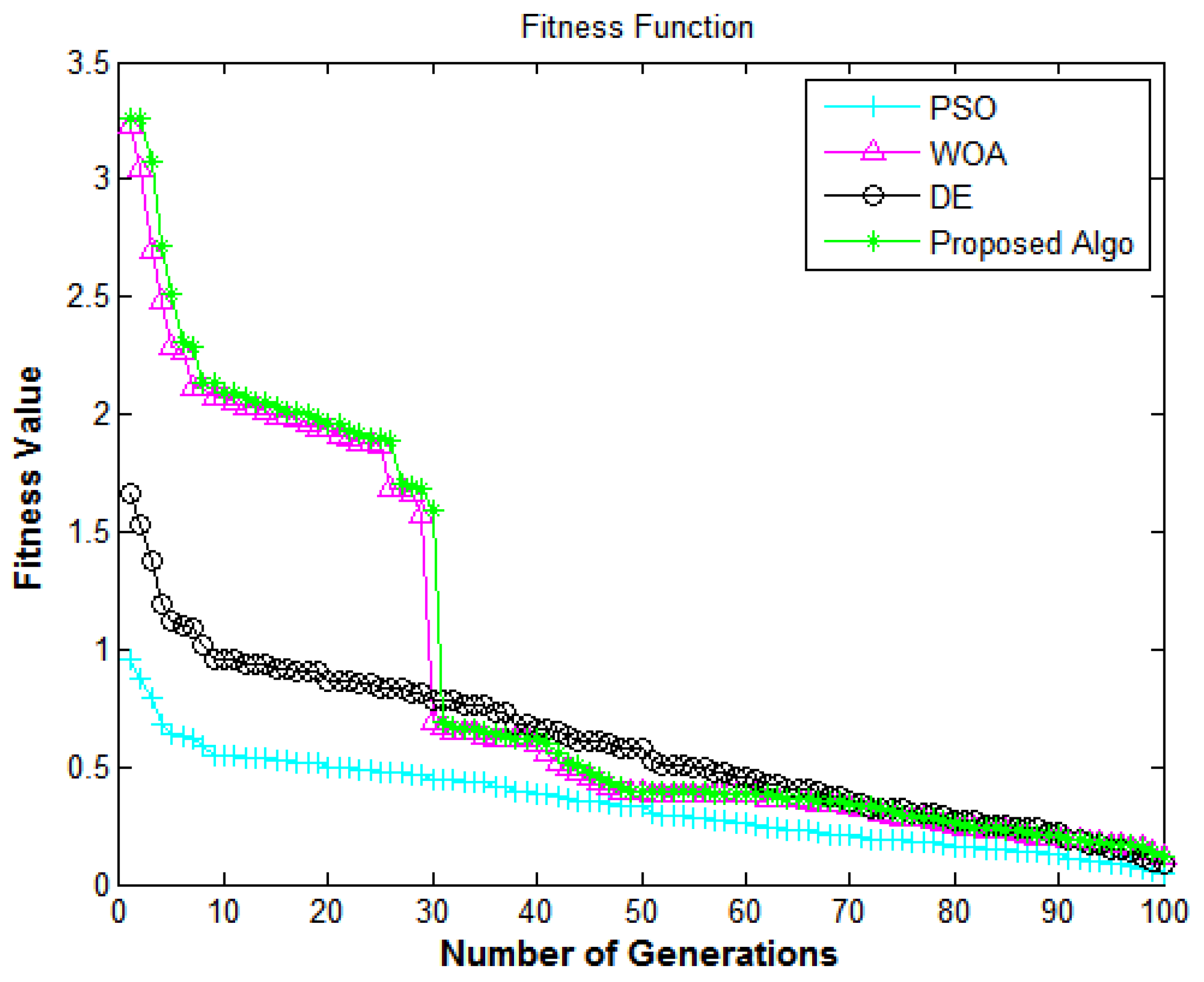
Figure 5.
Information security framework: mumber of generations versus fitness value.
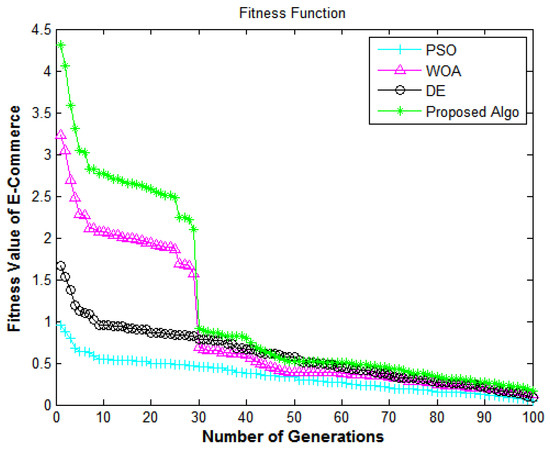
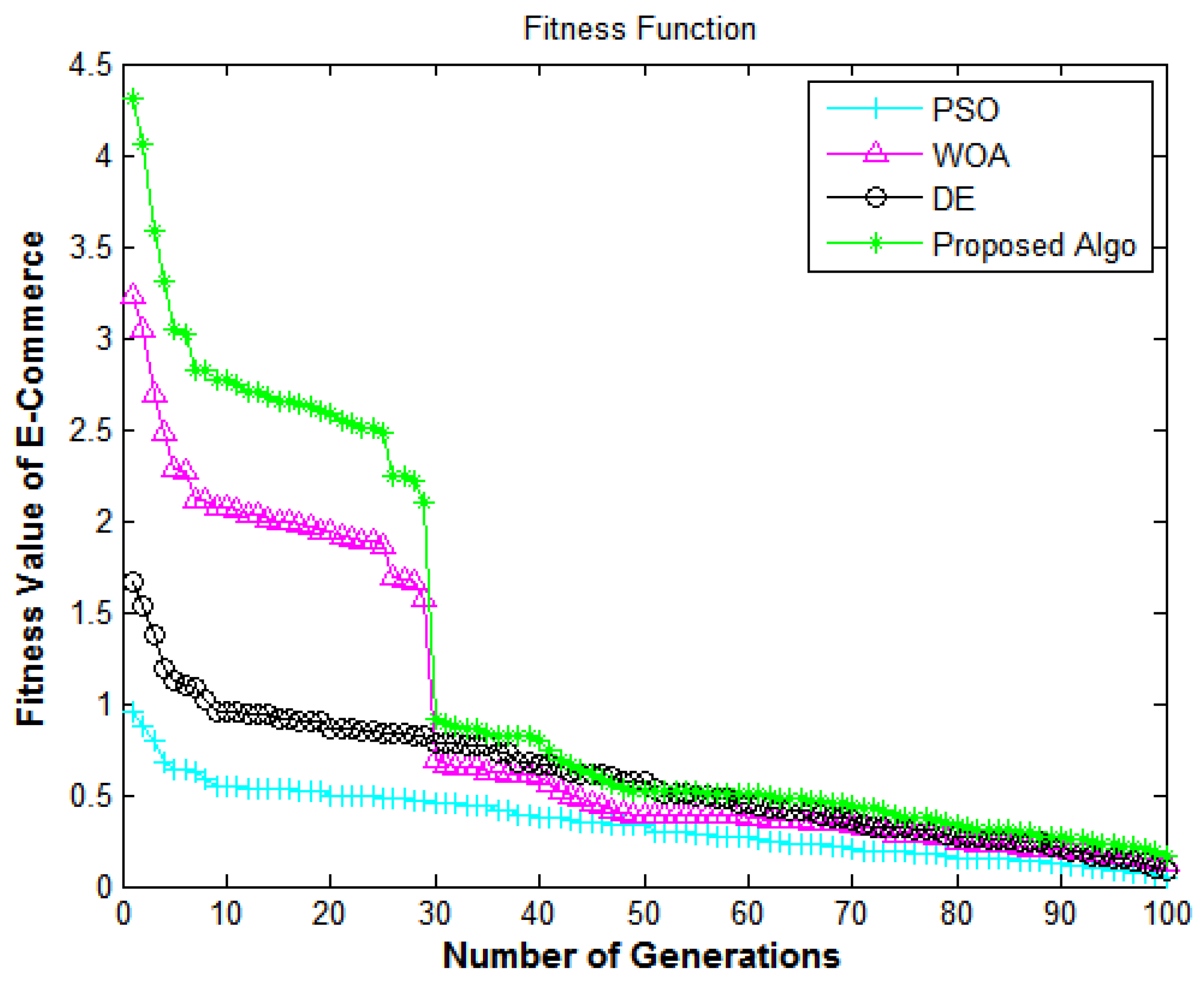
Figure 6.
Information security framework: number of generations versus fitness value of e-commerce.
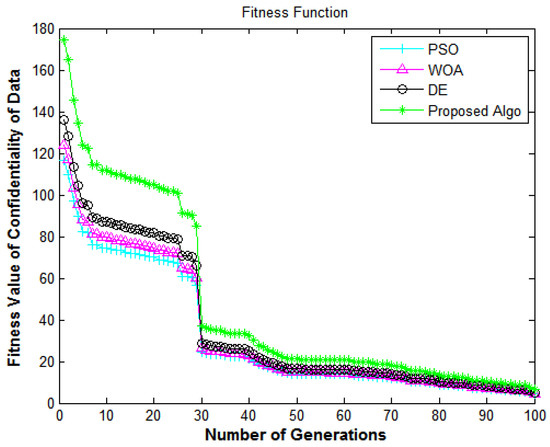
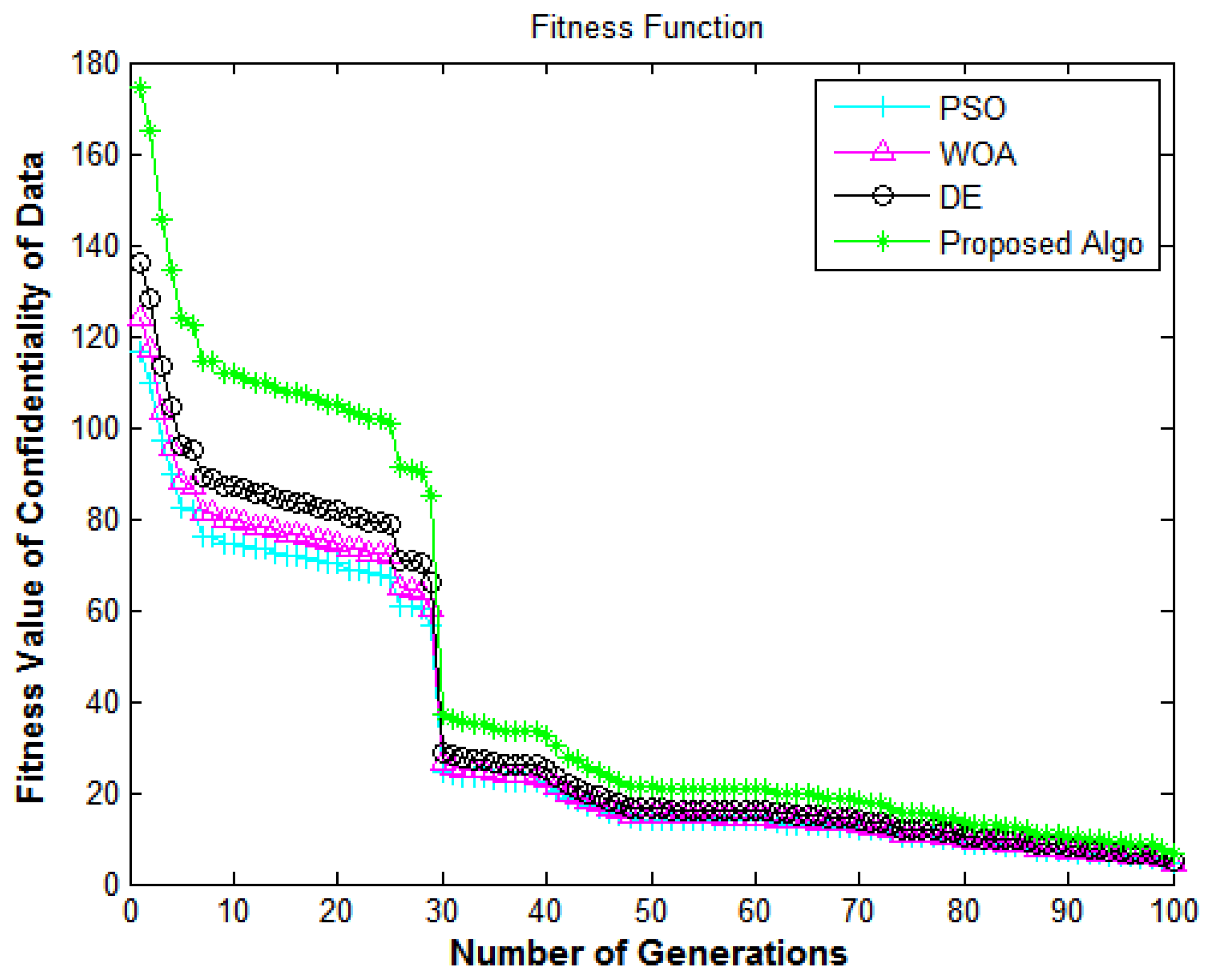
Figure 7.
Information security framework: number of generations versus fitness value of the confidentiality of data.
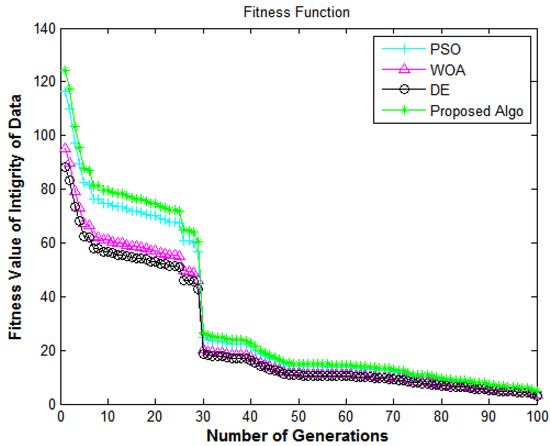
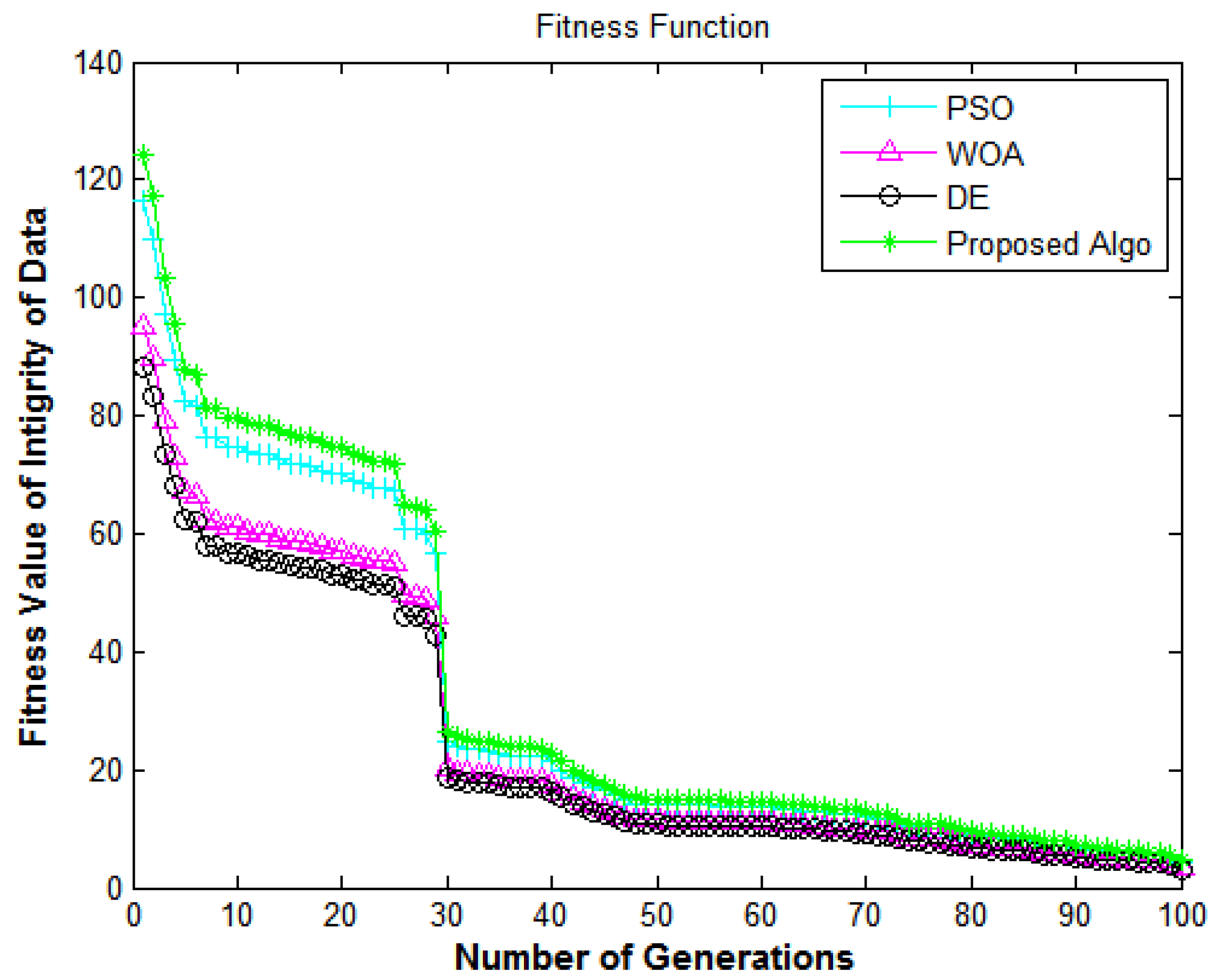
Figure 8.
Information security framework: number of generations versus fitness value of the integrity of data.
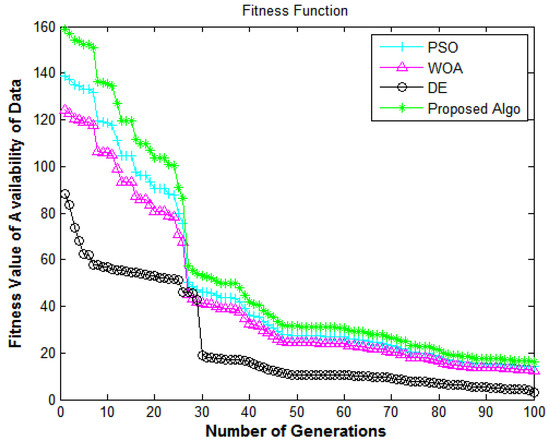
Figure 9.
Information security framework: number of generations versus fitness value of the availability of data.
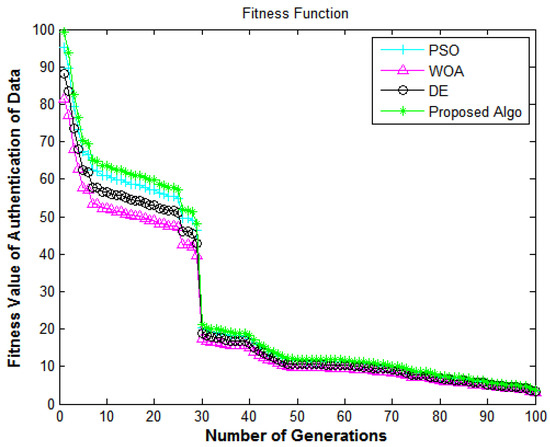
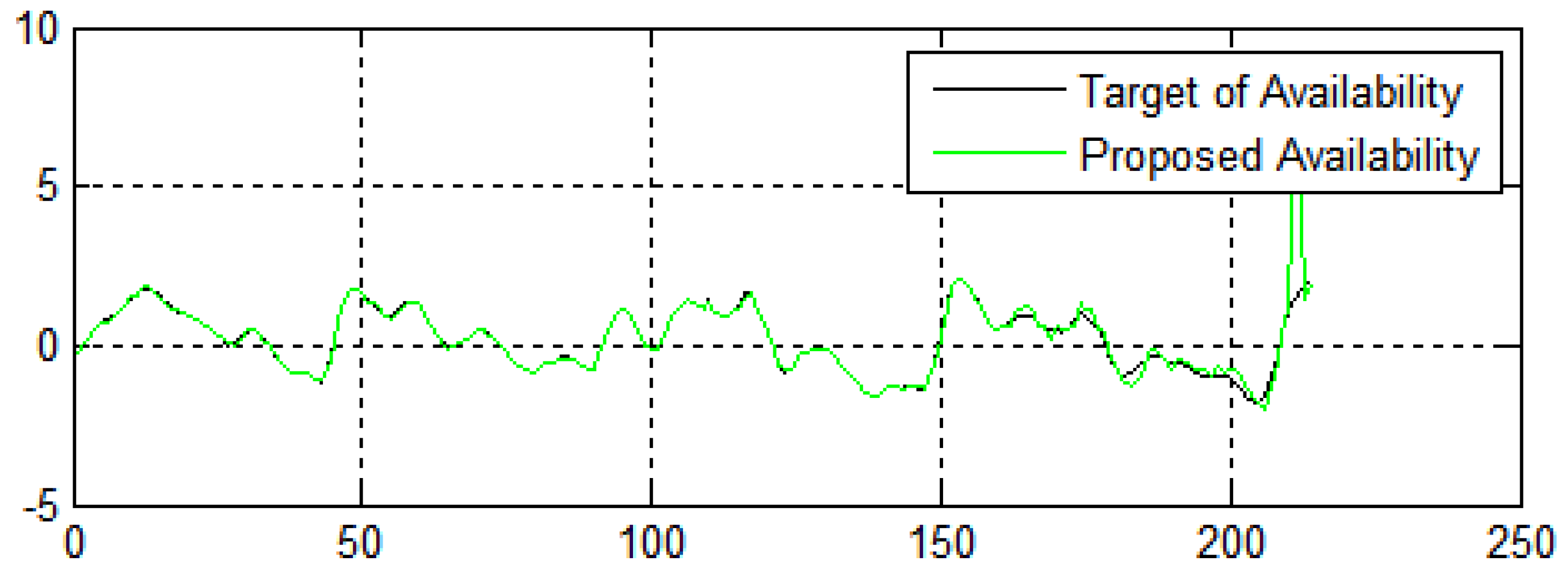
Figure 10.
Information security framework: number of generations versus fitness value of the authentication of data.
In order to compare the best front method with other ones, convergence speed is employed. This method employs an adaptation-based approach to get the most optimal front. The first rank value from the global search area is chosen as the best ideal front indicator. Its vector is a workable optimum solution in the search space because of this. Therefore, the suggested algorithms must identify the best rank in the region of the global search in order to obtain the best optimisation solution. Otherwise, these solutions are not feasible for search purposes.
5.3. Comparison of Fitness Function of the Proposed Work with Referenced Methods
The fitness function of the proposed method is used to compare the performance using Equation (13). When the local optimal problem is evaluated, then it provides sufficient diversity. The reason behind this is that it uses environmental factors to evaluate the convergence speed. The result of the performance is observed in Figure 5.
In Figure 5, the X-axis and Y-axis represent the number of generations and the fitness value, respectively. It shows the performance of algorithms in terms of the security of the data from e-commerce applications. Figure 5 depicts the comparison of all algorithms in terms of the fitness function; it also shows the convergence rate. For all of the security objective issues, the proposed algorithm delivers superior fitness values compared to DE [7], PSO [18], and WOA [40]. The fitness values to enhance the security of the system achieve encouraging performance, which shows that the suggested methodology has a high convergence speed and diversity.
In Figure 6, the X-axis and Y-axis denote the number of generations and the fitness value of the IoT-enabled e-commerce application, respectively. It shows the performance of the algorithms in terms of the security of the data from e-commerce applications. Figure 6 presents the comparative analysis of all algorithms regarding the improved security fitness rate. The proposed algorithm delivers superior fitness values compared to DE [7], PSO [18], and WOA [40]. The fitness values enhance the system’s security and achieve encouraging performance for the fitness value, which shows that the suggested methodology has a high convergence speed and variety.
In Figure 7, the X-axis and Y-axis denote the number of generations and the fitness value of confidentiality of data. This figure shows the performance of the algorithms in terms of the confidentiality of the data from e-commerce applications. The results shown in Figure 7 depict the comparison of all algorithms in terms of the fitness function. The proposed algorithm delivers superior fitness values compared to DE [7], PSO [18], and WOA [40]. The fitness values for enhancing the system’s confidentiality achieve encouraging performance, which shows that the suggested methodology has a high convergence speed and diversity.
In Figure 8, the X-axis and Y-axis denote the number of generations and the fitness value of integrity of data, respectively. This figure shows the performance of the algorithms in terms of the integrity of the data from e-commerce applications. The results in Figure 8 depict the comparison of all algorithms in terms of the fitness function. The proposed algorithm delivers superior fitness values compared to DE [7], PSO [18], and WOA [40]. The fitness values for enhancing the system’s integrity achieve encouraging performance, which shows that the suggested methodology has a high convergence speed and diversity.
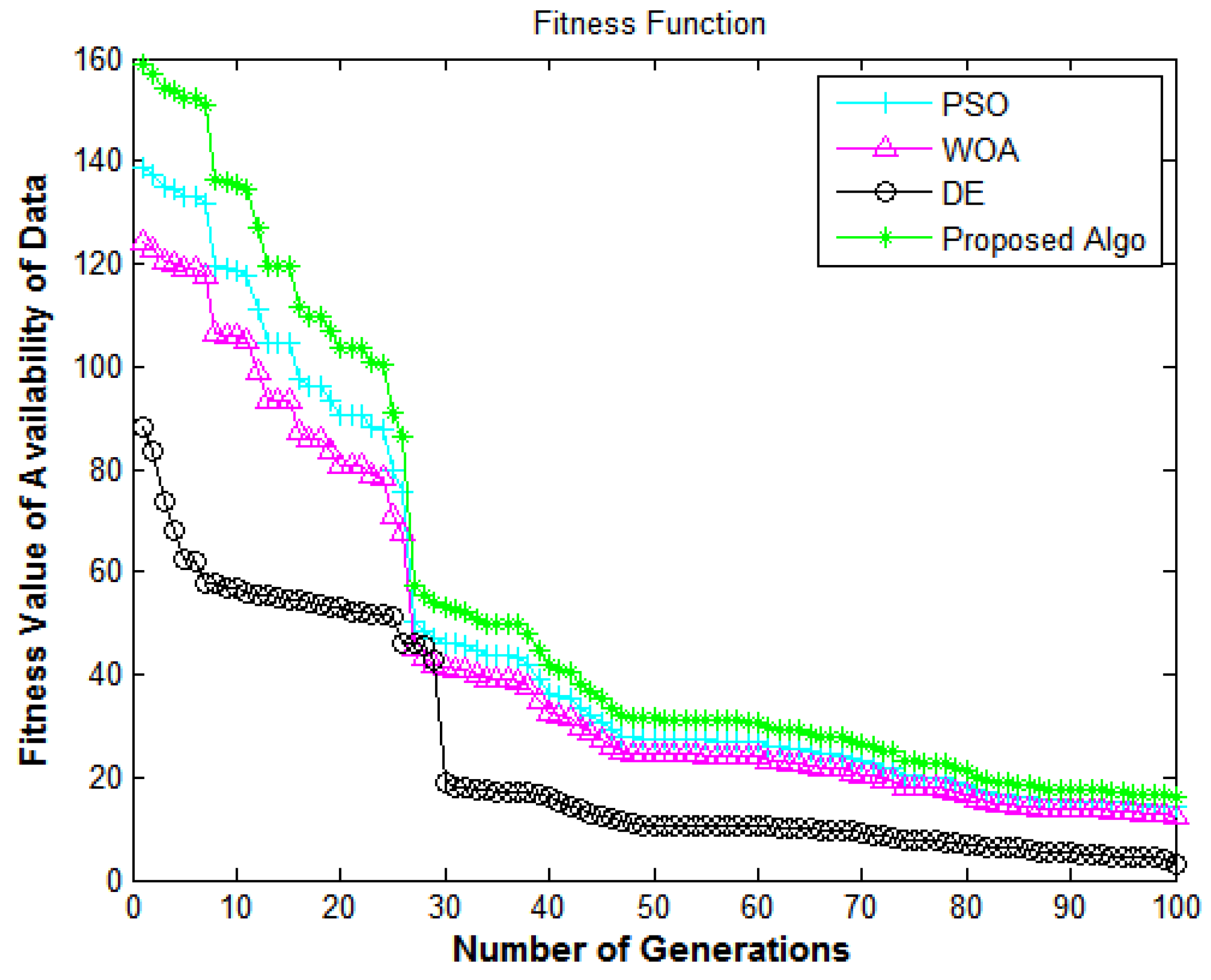
In Figure 9, the X-axis and Y-axis denote the number of generations and the fitness value of data availability, respectively. This shows the performance of the algorithms in terms of the availability of data from e-commerce applications. Figure 9 compares all algorithms in terms of the fitness function. The proposed algorithm delivers superior fitness values compared to DE [7], PSO [18], and WOA [40]. The fitness values for enhancing the system’s service availability achieve encouraging performance, which shows that the suggested methodology has a high convergence speed and diversity.
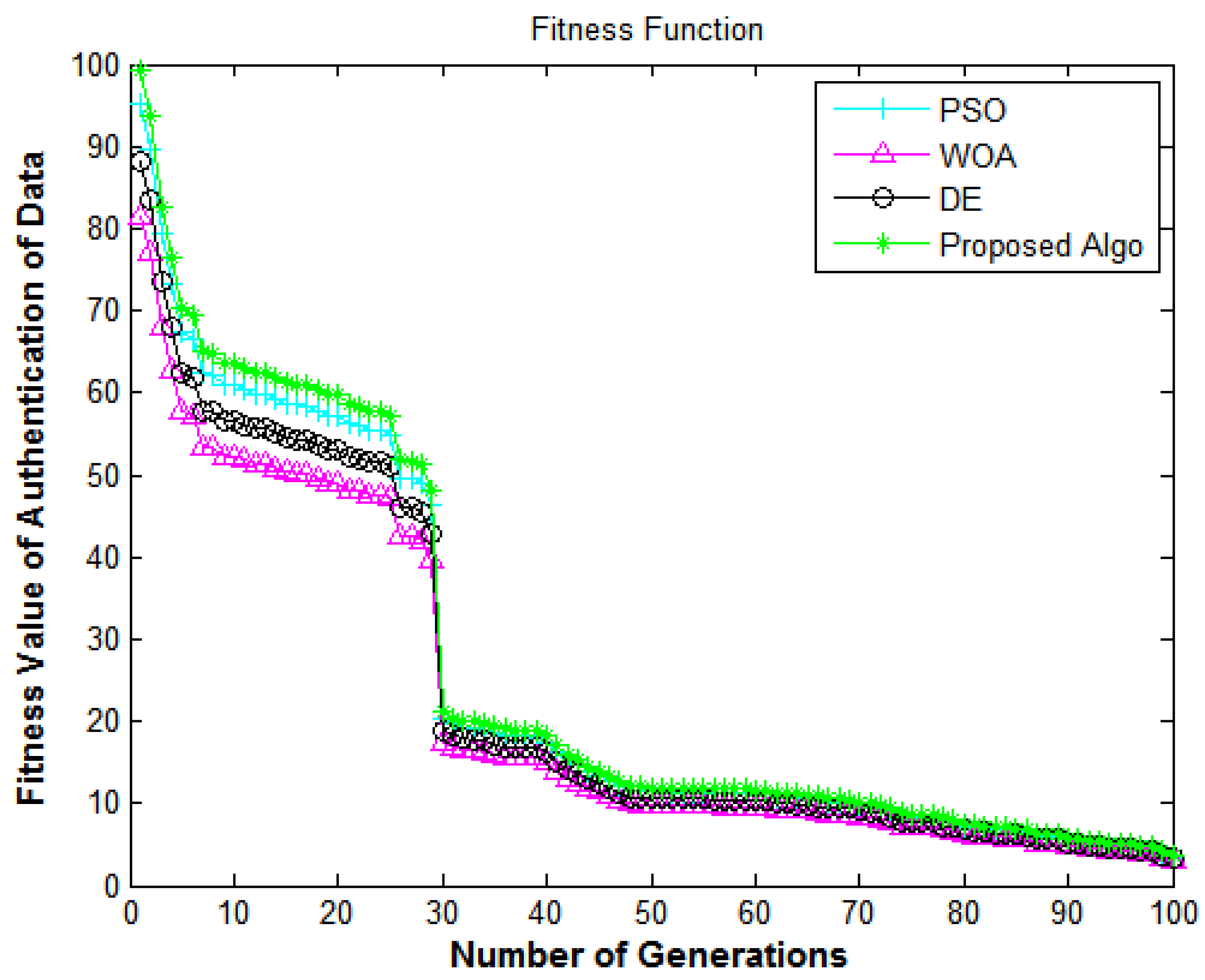
In Figure 10, the X-axis and Y-axis denote the number of generations and the fitness value of data authentication, respectively. Figure 10 shows the performance of the algorithms in terms of the authenticity of the data from e-commerce applications. The results shown in Figure 10 depicted the comparison of all algorithms in terms of the fitness function. The proposed algorithm delivers superior fitness values compared to DE [7], PSO [18], and WOA [40]. The fitness values enhance the authenticity of the system and achieve encouraging performance, which shows that the suggested methodology has a high convergence speed and diversity.
5.4. Result Analysis of IoT-Enabled Application
To ensure the security performance of the proposed optimisation technique, a double-check is done by applying it to the IoT-based e-commerce information system. The performance is checked on all set objectives and control parameters as shown in Table 3.

Table 3.
Control parameters of the proposed algorithm.
5.4.1. Result Analysis of the Confidentiality
The confidentiality is incorporated into the IoT-based network model with Equation (9) to produce the values. These values are available in Table 4 according to the best, average, and worst-case fitness functions. The performance is evaluated in all cases of 50, 100, 150, 200, 250, 300, 350, 400, 450, and 500 generations in three dimensions. From the observed results shown in the table, it is clear that the confidentiality of the proposed method is better than referenced optimisation methods. The best-case scenario represents the high confidentiality of the systems. The average case represents the mean confidentiality of the systems. The worst-case scenario represents the low confidentiality of the systems. Finally, it can be concluded from Table 2 and Table 3 that the proposed method achieves higher confidentiality than existing methods.

Table 4.
Confidentiality in three dimensions. The proposed algorithm compared with the evolutionary algorithm on a security model.
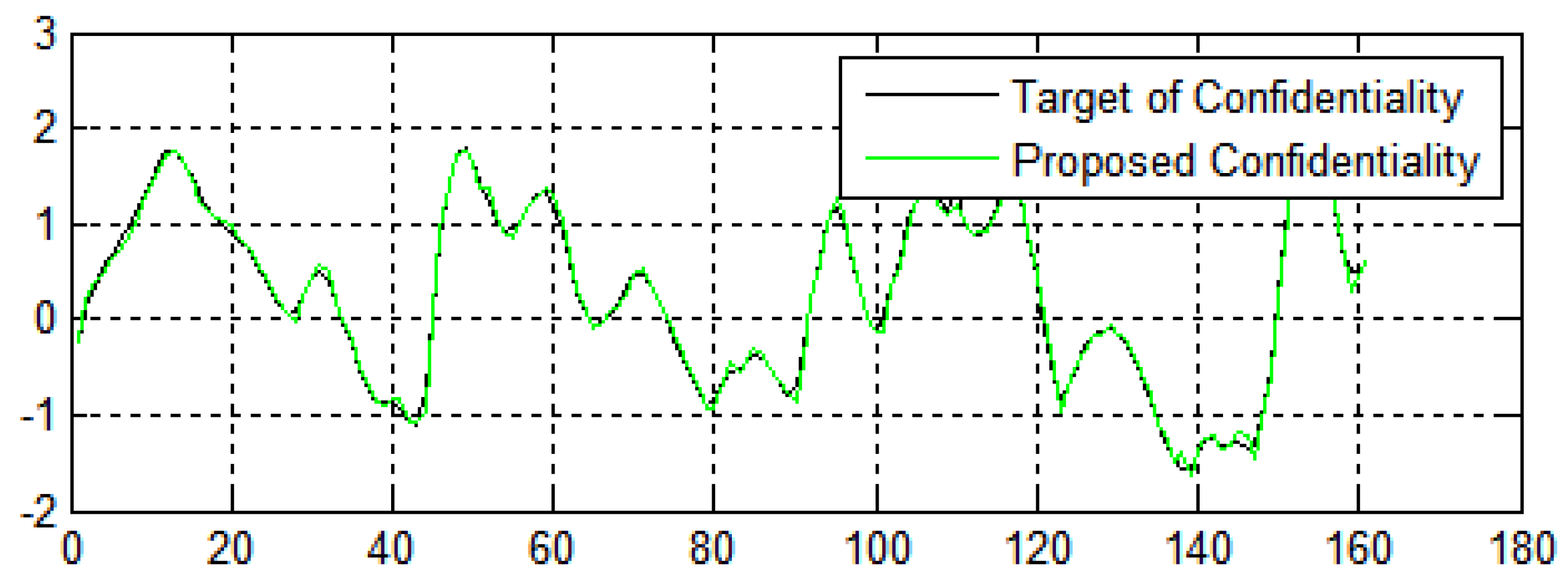
In Figure 11, the X-axis and Y-axis represent the number of generations and fitness value of confidentiality of data, respectively. Figure 11 shows the performance of the algorithms in terms of confidentiality and security of the data from e-commerce applications. The fitness values achieve encouraging performance, which indicates that the proposed method achieves a high convergence speed and diversity.
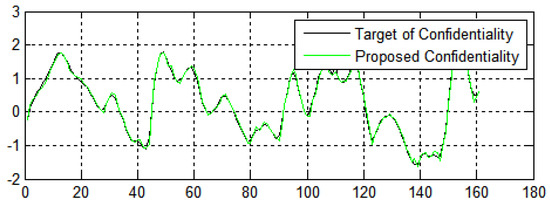
Figure 11.
Data confidentiality in terms of the number of generations in three dimensions.
5.4.2. Result Analysis of the Integrity
This section outlines the application of optimised techniques to check the integrity of the e-commerce system. This method is incorporated into the network model with Equation (10) to generate the value. These values are mentioned in Table 5 according to the best, average, and worst-case fitness functions. The performance is evaluated in all cases of 50, 100, 150, 200, 250, 300, 350, 400, 450, and 500 generations in three dimensions. From this table, it is clear that the best-case scenario represents high integrity, the average case represents mean integrity, and the worst-case scenario represents the low integrity of the systems. The observed values available in Table 5 indicate that the proposed method gives higher performance than other standard optimisation algorithms in terms of integrity.

Table 5.
Integrity in three dimensions. The proposed algorithm compared with the evolutionary algorithm on a security model.
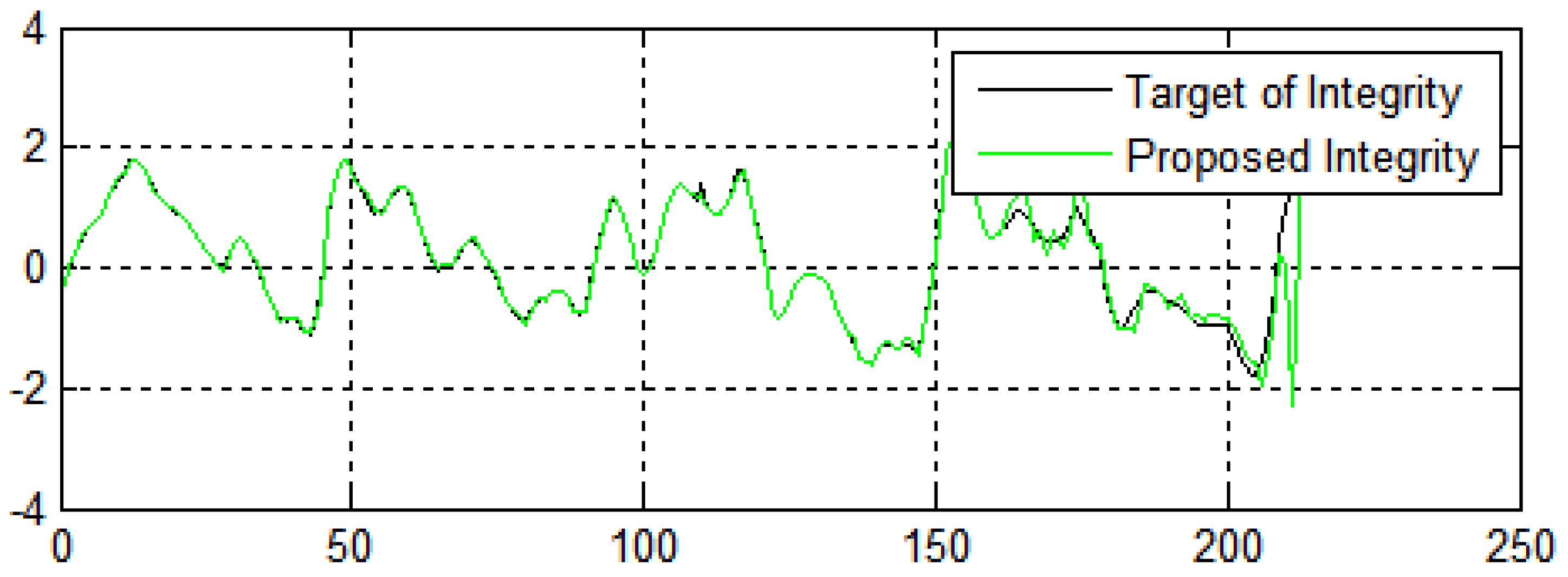
In Figure 12, the X-axis and the Y-axis represents the number of generations and fitness value of the integrity of the data, respectively. Figure 12 shows the performance of the algorithms regarding the integrity and security of the data from e-commerce applications. The fitness values achieve pretty encouraging performance, which indicates the proposed method has high convergence speed and diversity.
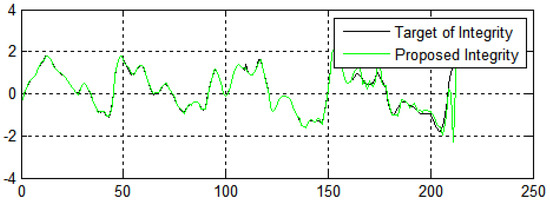
Figure 12.
Data integrity in terms of the number of generations in three dimensions.
5.4.3. Result Analysis of the Availability of Information System
In this section, the method is applied the optimised techniques and we checked the availability of the information system. This method is applied to the IoT-based network model with Equation (11) to produce the values. The values are available in Table 6 according to the best, average, and worst-case fitness functions. The performance is evaluated in all cases of 50, 100, 150, 200, 250, 300, 350, 400, 450, and 500 generations in three dimensions. This table shows the best-case scenario represents the high availability of the systems, the average case represents the mean availability, and The worst-case scenario represents the low availability of the systems. Table 6 shows that the performance of the proposed method is better than that of other standard optimisation algorithms in terms of availability.

Table 6.
Availability in three dimensions. The proposed algorithm compared with the evolutionary algorithm on a security model.
In Figure 13, the X-axis represents the number of generations and the Y-axis represents the fitness value of the availability of the data. Figure 13 shows the performance of the algorithms in terms of the availability and security of the data from e-commerce applications. The fitness values for enhancing the system’s security achieve pretty encouraging performance, which shows that the suggested methodology has high convergence speed and variety.
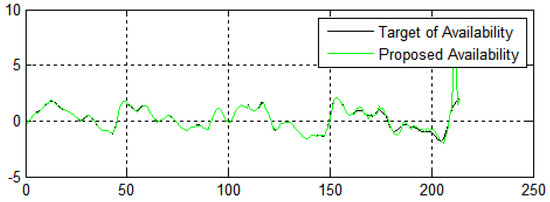
Figure 13.
Data availability in terms of the number of generations in three dimensions.
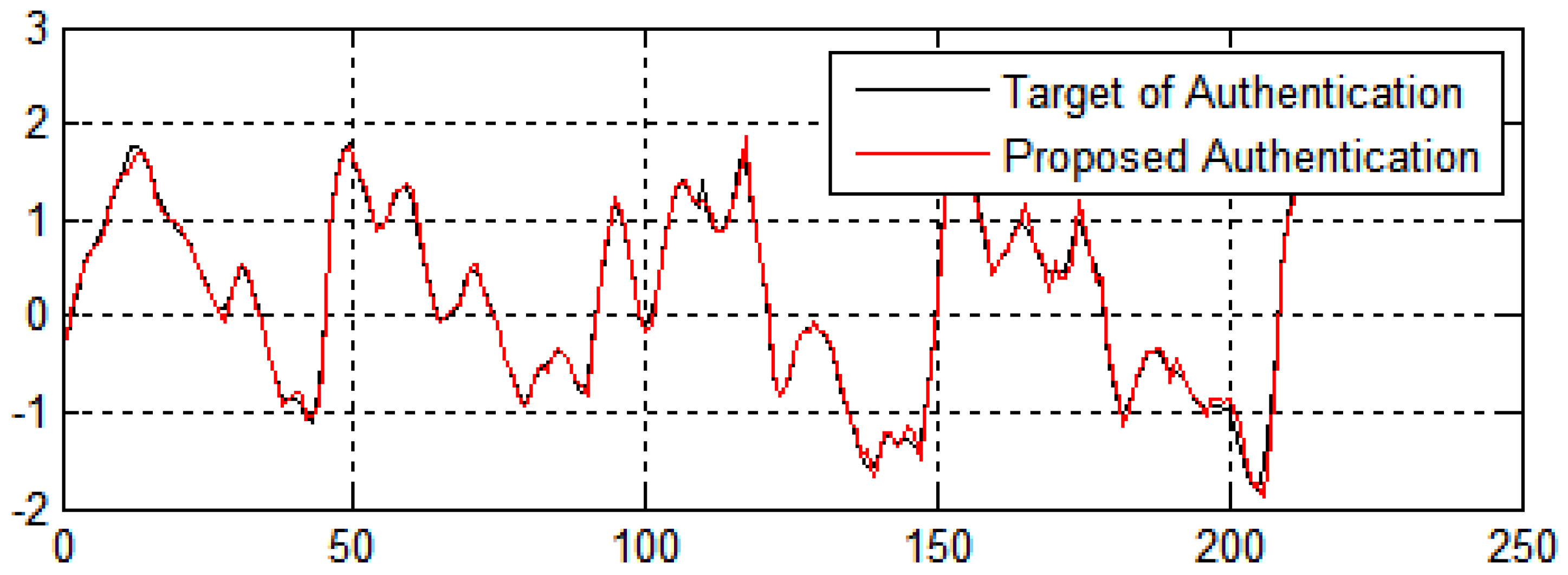
5.4.4. Result Analysis of the Authentication of Information System
This section checks the authenticity of the e-commerce system. This method is incorporated into the network model with Equation (12) to generate the value. These values are mentioned in Table 7 according to the best, average, and worst fitness functions, which check the performance of different generations such as 50, 100, 150, 200, 250, 300, 350, 400, 450, and 500 in three dimensions. This table shows that the performance of the proposed method is better than that of other standard optimisation algorithms in terms of authenticity. The best, average, and worst cases represent the systems’ high, mean, and low authenticity. Table 7 shows that the performance of the proposed method is better than that of other standard optimisation algorithms in terms of authenticity.

Table 7.
Authentication in three dimensions. The proposed algorithm compared with the evolutionary algorithm on a security model.
In Figure 14, the X-axis represents the number of generations and the Y-axis represents the fitness value of the authenticity of the data. Figure 14 shows the performance of the algorithms in terms of authenticity and security of the data from e-commerce applications. The fitness values for enhancing the system’s authenticity show encouraging performance and show that the suggested methodology has a high convergence speed and diversity.
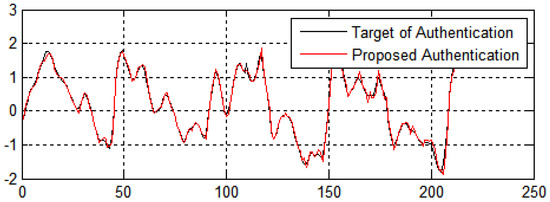
Figure 14.
Data authentication in terms of the number of generations in three dimensions.
6. Conclusions
Nearly all industries have some sort of operation on the Internet and with that arises a need for basic security features such as confidentiality, authenticity, availability, and integrity. Cryptography aims to achieve these features with the help of evolutionary algorithms. This paper introduced a new variant of the mutation operator that provides sufficient diversity for the DE algorithm and enhances the optimal convergence rate for confidentiality, authenticity, availability, and integrity. In addition, the introduced approach is also used to evaluate security problems for enhanced confidentiality, authenticity, availability, and data integrity and accurately predicts the security fitness cost by optimizing the tuning parameters. The findings on several benchmark functions show that the proposed technique performs much better than previous DE algorithm versions on maximal variants, which is very encouraging. The proposed method is applied and tested in IoT-enabled e-commerce applications but in future it can be extended into other applications by incorporating the input parameters according to the requirements.
Author Contributions
Conceptualisation: S.P.S. and S.S.R.; Methodology: S.P.S. and Y.A.; Validation: Y.A. and G.K.; Formal Analysis: Y.A. and G.K.; Investigation: S.S.R. and G.K. Resources: Y.A. and S.S.R.; Data Curation: S.P.S. and G.K.; Writing—Original Draft Preparation: G.K. and S.P.S.; Writing—Review and Editing: Y.A. and S.S.R.; Visualisation: G.K. and S.S.R.; Supervision: Y.A. and S.S.R.; Project Administration: S.P.S., Y.A. and S.S.R.; Funding Acquisition: Y.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research is funded by Deanship of Scientific Research at Umm Al-Qura University, Grant Code: 22UQU4281768DSR07.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data associated with this work will be provided by the corresponding author upon reasonable request.
Acknowledgments
The author would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: (22UQU4281768DSR07).
Conflicts of Interest
We certify that there is no conflict of interest involved in the subject or materials discussed in manuscript.
References
- Feng, B.; Zhou, H.; Li, G.; Zhang, Y.; Sood, K.; Yu, S. Enabling Machine Learning with Service Function Chaining for Security Enhancement at 5G Edges. IEEE Netw. 2021, 35, 196–201. [Google Scholar] [CrossRef]
- Feng, B.; Tian, A.; Yu, S.; Li, J.; Zhou, H.; Zhang, H. Efficient Cache Consistency Management for Transient IoT Data in Content-Centric Networking. IEEE Internet Things J. 2022, 9, 12931–12944. [Google Scholar] [CrossRef]
- Sharma, N.; Prabhjot; Kaur, H. A Review of Information Security using Cryptography Technique. Int. J. Adv. Res. Comput. Sci. 2017, 8, 323–326. [Google Scholar]
- Preneel, B. Understanding Cryptography: A Textbook for Students and Practitioners; Springer: London, UK, 2010. [Google Scholar]
- Katz, J.; Lindell, Y. Introduction t:o Modern Cryptography; Taylor & Francis Group, LLC: London, UK, 2008. [Google Scholar]
- Rainer, S.; Price, K. Differential Evolution—A Simple and Efficient Adaptive Scheme for Global Optimization Over Continuous Spaces; International Computer Science Institute: Berkeley, CA, USA, 1995. [Google Scholar]
- Bili, C.; Lin, Y.; Zeng, W.; Zhang, D.; Si, Y.-W. Modified differential evolution algorithm using a new diversity maintenance strategy for multi-objective optimization problems. Appl. Intell. 2015, 43, 49–73. [Google Scholar]
- Shi, Q.; Chen, W.; Jiang, T.; Shen, D.; Gao, S. Handling Multiobjectives with Adaptive Mutation Based ϵ-Dominance Differential Evolution. ICSI-CCI 2015, 9140, 523–532. [Google Scholar]
- Singh, S.P. Improved based Differential Evolution Algorithm using New Environment Adaption Operator. J. Inst. Eng. India Ser. B 2021, 103, 107–117. [Google Scholar] [CrossRef]
- Singh, P.S.; Kumar, A. Pareto Based Differential Evolution with Homeostasis Based Mutation. J. Intell. Fuzzy Syst. 2017, 32, 3245–3257. [Google Scholar] [CrossRef]
- Chen, X.; Du, W.; Qian, F. Multi-objective differential evolution with ranking-based mutation operator and its application in chemical process optimization. Chemom. Intell. Lab. Syst. 2014, 136, 85–96. [Google Scholar] [CrossRef]
- Zhang, X.; Tian, Y.; Cheng, R.; Jin, Y. An efficient approach to nondominated sorting for evolutionary multiobjective optimization. IEEE Trans. Evol. Comput. 2015, 19, 201–213. [Google Scholar] [CrossRef]
- Deb, K.P.; Agarwal, A.; Meyarivan, T.S. A fast and elitist multi-objective genetic algorithm: NSGA-II. IEEE Trans. Evol. Comput. 2002, 6, 182–197. [Google Scholar] [CrossRef]
- Leandro, L.M.; Xin, Y. Software Effort Estimation as a Multi-objective Learning Problem. Acm Trans. Softw. Eng. Methodol. TOSEM 2013, 22, 1–32. [Google Scholar]
- Singh, S.P.; Kumar, A. Software cost estimation using homeostasis mutation based differential evolution. In Proceedings of the IEEE International Conference on Intelligent Systems and Control (ISCO), Coimbatore, India, 5 January 2017; pp. 173–181. [Google Scholar]
- Singh, S.P.; Singh, V.P.; Mehta, A.K. Differential evolution using homeostasis adaption based mutation operator and its application for software cost estimation. J. King Saud-Univ. Inf. Sci. 2021, 33, 740–752. [Google Scholar] [CrossRef]
- Tan, Y.Y.; Jiao, Y.C.; Li, H.; Wang, X.K. A modification to MOEA/D-DE for multiobjective optimization problems with complicated Pareto sets. Inf. Sci. 2012, 213, 14–38. [Google Scholar] [CrossRef]
- Beed, R.; Roy, A.; Sarkar, S.; Bhattacharya, D. A hybrid multiobjective tourroute optimization algorithm based on particle swarm optimization and artificial bee colony optimization. Comput. Intell. 2020, 36, 884–909. [Google Scholar] [CrossRef]
- Lincke, S.; Hollan, J.A. Network Security: Focus on Security, Skills, and Stability. In Proceedings of the 37th ASEE/IEEE Frontiers in Education Conference, Milwaukee, WI, USA, 10–13 October 2007; p. F1D-10. [Google Scholar]
- Bader, J.; Zitzler, E. HypE: An algorithm for fast hyper volume-based many-objective optimization. Evol. Comput. 2011, 19, 45–76. [Google Scholar] [CrossRef] [PubMed]
- Ganesan, R.; Jajodia, S.; Cam, H. Optimal scheduling of cybersecurity analysts for minimizing risk. ACM Trans. Intell. Syst. Technol. 2017, 8, 1–32. [Google Scholar] [CrossRef]
- Ganesan, R.; Shah, A.; Jajodia, S.; Cam, H. Optimizing alert data management processes at a cyber security operations center. In Adversarial and Uncertain Reasoning for Adaptive Cyber Defense; Springer: Berlin/Heidelberg, Germany, 2019; pp. 206–231. [Google Scholar]
- Khalifa, O.O.; Islam, M.R.; Khan, S.; Shebani, M.S. Communications cryptography. In Proceedings of the RF and Microwave Conference, Selangor, Malaysia, 5–6 October 2004. [Google Scholar]
- Jirwan, N.; Singh, A.; Vijay, S. Review and Analysis of Cryptography Techniques. Int. J. Sci. Eng. Res. 2013, 3, 1–6. [Google Scholar]
- Callas, J. The Future of Cryptography. Inf. Syst. Secur. 2007, 16, 15–22. [Google Scholar] [CrossRef]
- Massey, J.L. Cryptography—A selective survey. Digit. Commun. 1986, 85, 3–25. [Google Scholar]
- Das, S.; Mullick, S.; Suganthan, P.N. Recent advances in differential evolution—An updated survey. Swarm Evol. Comput. 2016, 27, 1–30. [Google Scholar] [CrossRef]
- Rawat, S.S.; Singh, S.; Alotaibi, Y.; Alghamdi, S.; Kumar, G. Infrared Target-Background Separation Based on Weighted Nuclear Norm Minimization and Robust Principal Component Analysis. Mathematics 2022, 10, 2829. [Google Scholar] [CrossRef]
- Anuradha, D.; Subramani, N.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Rajagopal, M. Chaotic Search-and-Rescue-Optimization-Based Multi-Hop Data Transmission Protocol for Underwater Wireless Sensor Networks. Sensors 2022, 22, 2867. [Google Scholar] [CrossRef] [PubMed]
- Ramasamy, V.; Alotaibi, Y.; Khalaf, O.I.; Samui, P.; Jayabalan, J. Prediction of groundwater table for Chennai Region using soft computing techniques. Arab. J. Geosci. 2022, 15, 827. [Google Scholar] [CrossRef]
- Sennan, S.; Kirubasri; Alotaibi, Y.; Pandey, D.; Alghamdi, S. EACR-LEACH: Energy-aware cluster-based routing protocol for WSN based IoT. Comput. Mater. Contin. 2022, 72, 2159–2174. [Google Scholar] [CrossRef]
- Schneier, B. The Non-Security of Secrecy. Commun. ACM 2004, 47, 120. [Google Scholar] [CrossRef]
- Chachapara, K.; Bhadlawala, S. Secure sharing with cryptography in cloud. In Proceedings of the 2013 International Conference on Engineering (NUiCONE), Nirma University, Ahmedabad, India, 28–30 November 2013. [Google Scholar]
- Alotaibi, Y. A New Meta-Heuristics Data Clustering Algorithm Based on Tabu Search and Adaptive Search Memory. Symmetry 2022, 14, 623. [Google Scholar] [CrossRef]
- Kumar, G.; Tomar, P. A Stateless Spatial IPv6 Address Configuration Scheme for Internet of Things. IETE J. Res. 2021, 1–14. [Google Scholar] [CrossRef]
- Orman, H. Recent Parables in Cryptography. IEEE Internet Comput. 2014, 18, 82–86. [Google Scholar] [CrossRef]
- Gennaro, R. Randomness in cryptography. IEEE Secur. Priv. 2006, 4, 64–67. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Badotra, S.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Alassery, F. Energy-Efficient Clustering Scheme for Flying Ad-Hoc Networks Using an Optimized LEACH Protocol. Energies 2021, 14, 6016. [Google Scholar] [CrossRef]
- Preneel, B. Cryptography and Information Security in the Post Snowden Era. In Proceedings of the IEEE/ACM 1st International Workshop on Technical and Legal aspects of data privacy and Security, Florence, Italy, 18 May 2015. [Google Scholar]
- Chen, H.; Duncklee, A.; Jajodia, S.; Liu, R.; Mcnamara, S.; Subrahmanian, V.S. PCAM: A Data-driven Probabilistic Cyber-alert Management Framework. ACM Trans. Internet Technol. 2022, 22, 1–24. [Google Scholar] [CrossRef]
- Wang, Z.; Zhang, Q.; Zhou, A.; Gong, M.; Jiao, L. Adaptive Replacement Strategies for MOEA/D. IEEE Trans. Cybern. 2016, 46, 474–486. [Google Scholar] [CrossRef] [PubMed]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).