A Privacy-Preserving KYC-Compliant Identity Scheme for Accounts on All Public Blockchains
Abstract
1. Introduction
2. Preliminaries
2.1. Blockchain
2.2. Smart Contracts
2.3. NFT
2.4. Merkle Tree
2.5. Pedersen Commitment
2.6. Bilinear Mapping
3. System Design
3.1. System Architecture
3.2. Program Flow
- (1)
- The KYC provider deploys the KYCManager contract and the KYCNFT contract to the Ethereum network.
- (2)
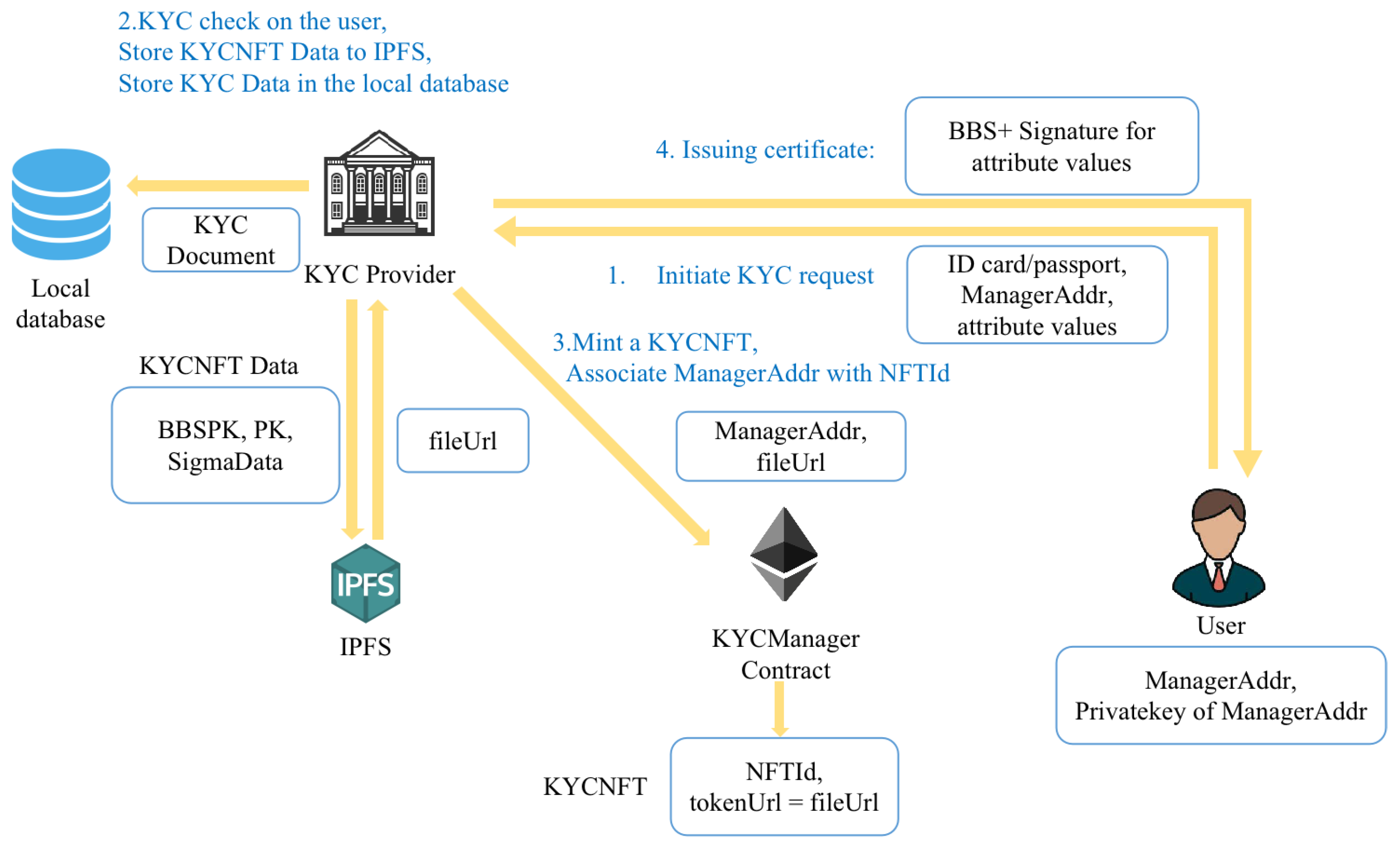
- The user initiates a KYC request to the KYC provider and submits the identity information required for KYC, such as an ID card. Then, the KYC provider checks the user’s identity information. After passing the KYC check, the user generates an Ethereum wallet account, denoted as ManagerAddr. This account will be used as the user’s manager account for the KYC authorization of wallet accounts and will be submitted to the KYC provider.
- (3)
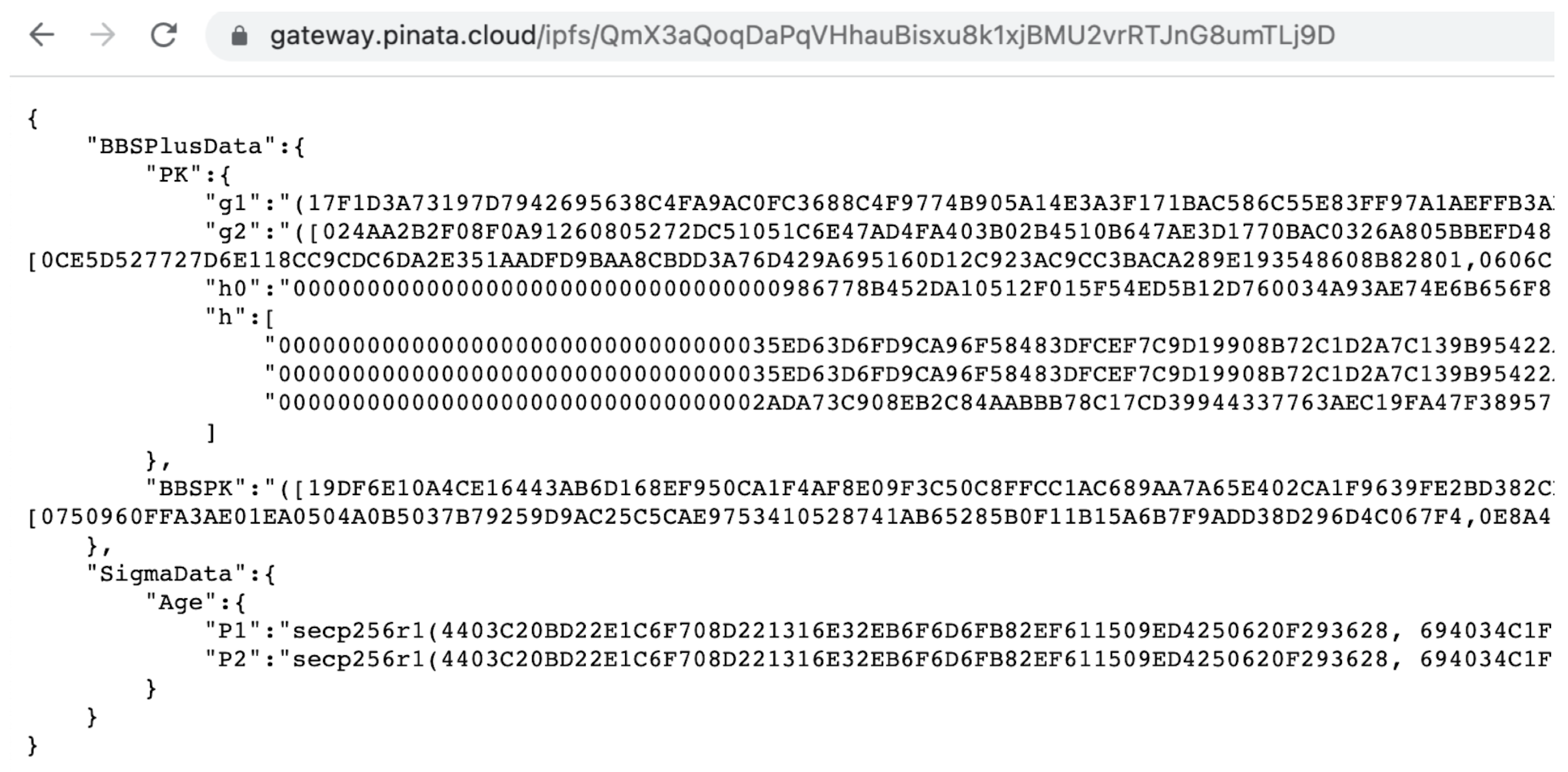
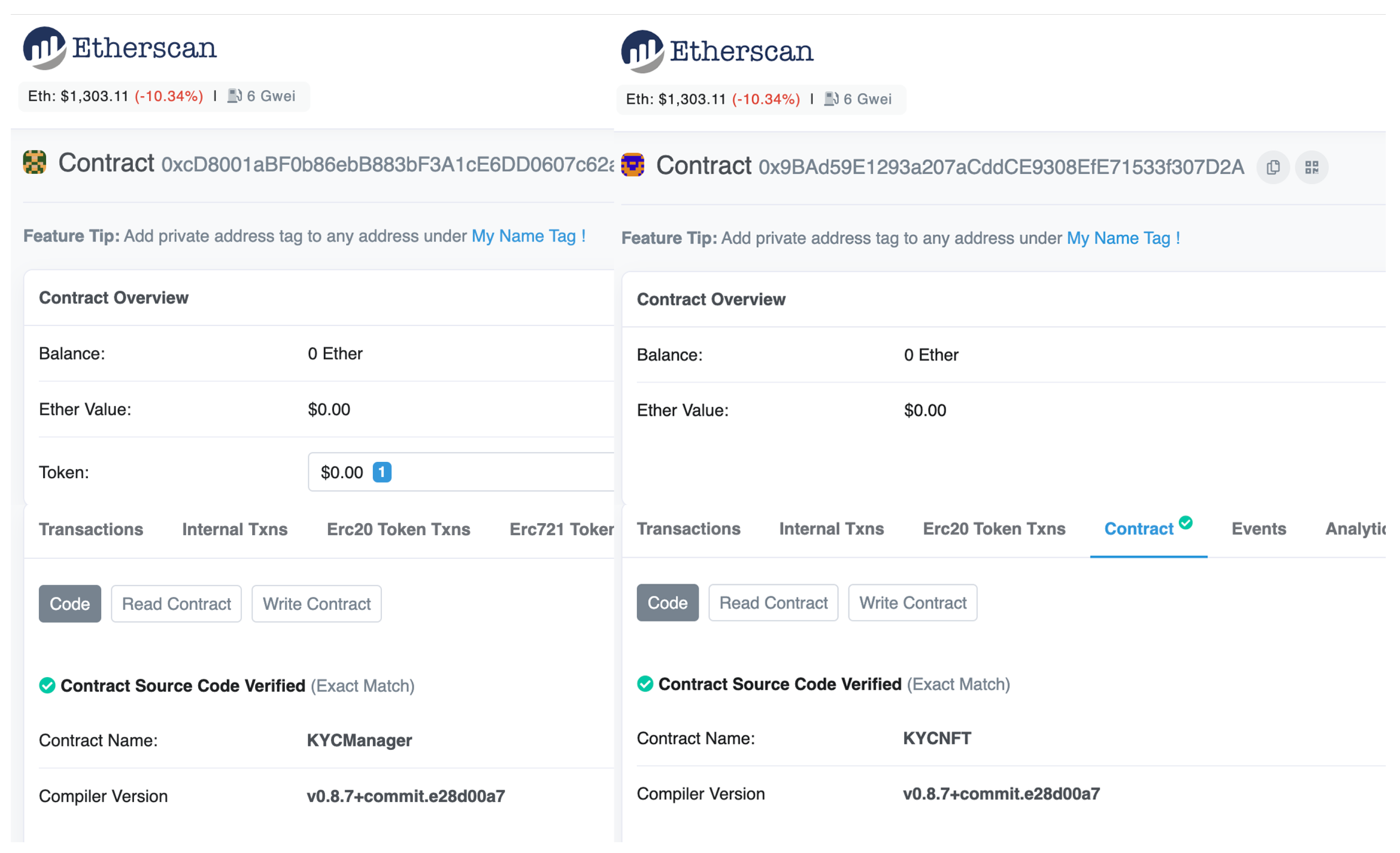
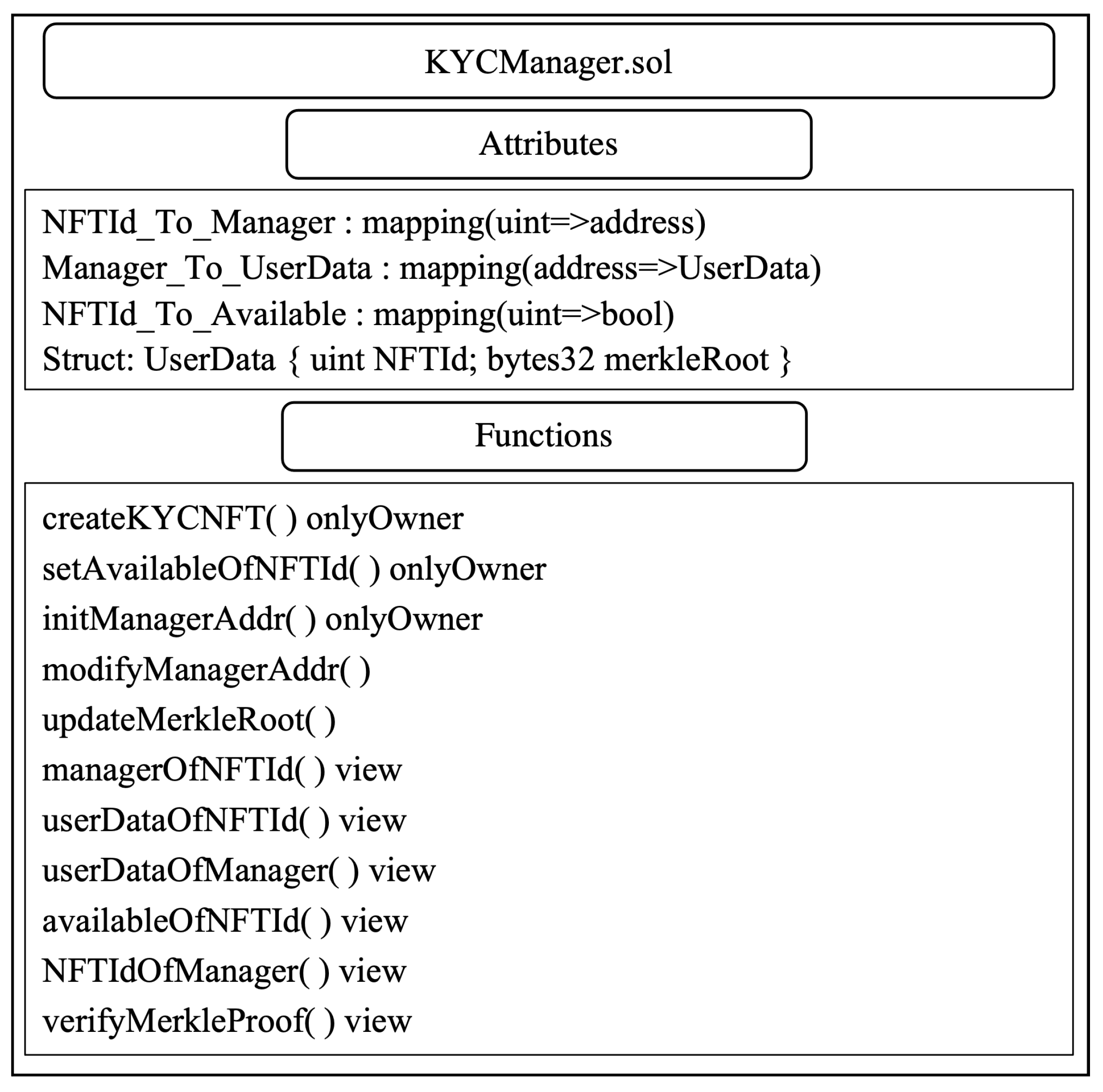
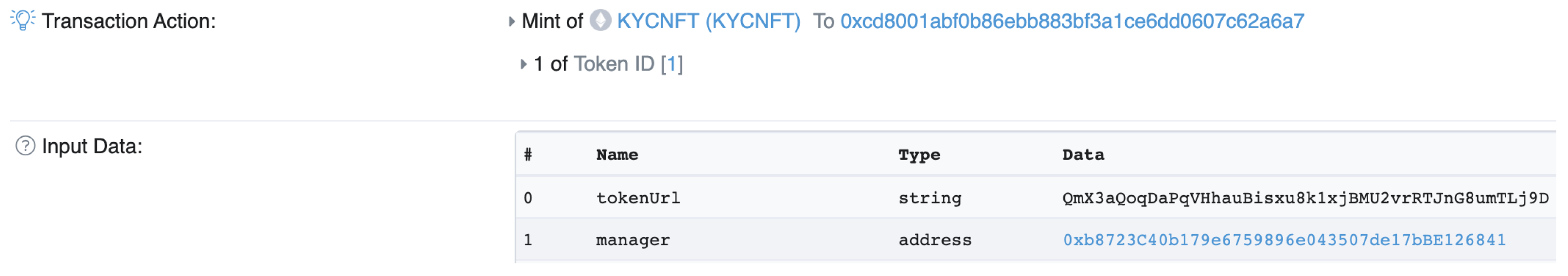
- If the user passes the KYC check, the KYC provider does the following. The KYC provider generates a BBS+ signature for a list of the user’s attribute values, denoted as BBSSig, and sends it to the user. The public keys used for the BBS+ signature are BBSPK and PK.Disjunctive proofs (OR proofs) in the Sigma protocol can be used to construct the obfuscating proofs of the attribute values, proving that the actual attribute value belongs to a specific set without exposing its value. Building an obfuscation proof requires some fake data for obfuscation so the KYC provider generates some fake data for the user, denoted as SigmaData.The KYC provider stores the BBSPK, PK, and SigmaData in the IPFS and obtains the storage path fileUrl, as shown in Figure 2.Then, the KYC provider calls the function createKYCNFT() of the KYCManager contract to mint a KYCNFT, where the tokenURL of the KYCNFT is fileUrl and the owner of the KYCNFT is the KYCManager contract. In addition, the function createKYCNFT() also sets the validity of the user’s identity and binds the user’s manager account ManagerAddr to NFTId.The process of KYC registration is shown in Figure 3.
- (4)
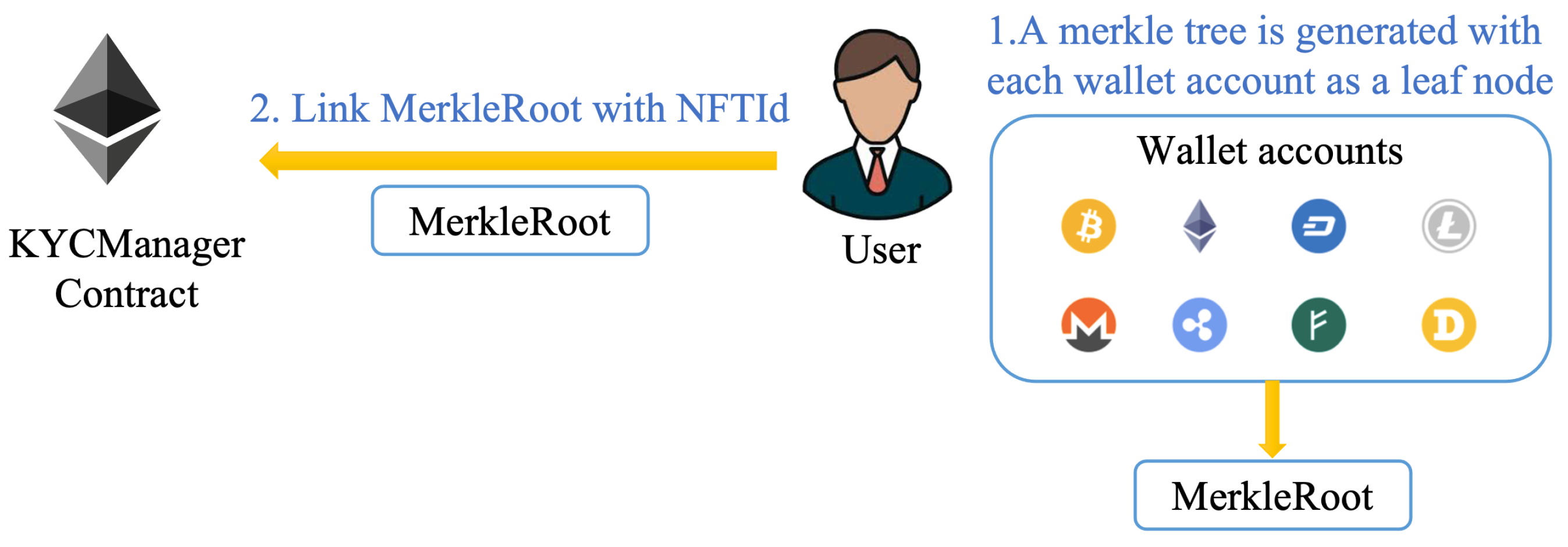
- After obtaining the response from the KYC provider, the user authorizes his wallet accounts with the identity. First, the user adds a blockchain scope to be authorized as a suffix to each wallet account (e.g., 0x123@ETH) and then generates a Merkle tree with each wallet account as a leaf node. The root node value of the Merkle tree is MerkleRoot. The user’s manager account calls the KYCManager contract to link MerkleRoot with NFTId. The KYC authorization process of the wallets is shown in Figure 4.
- (5)
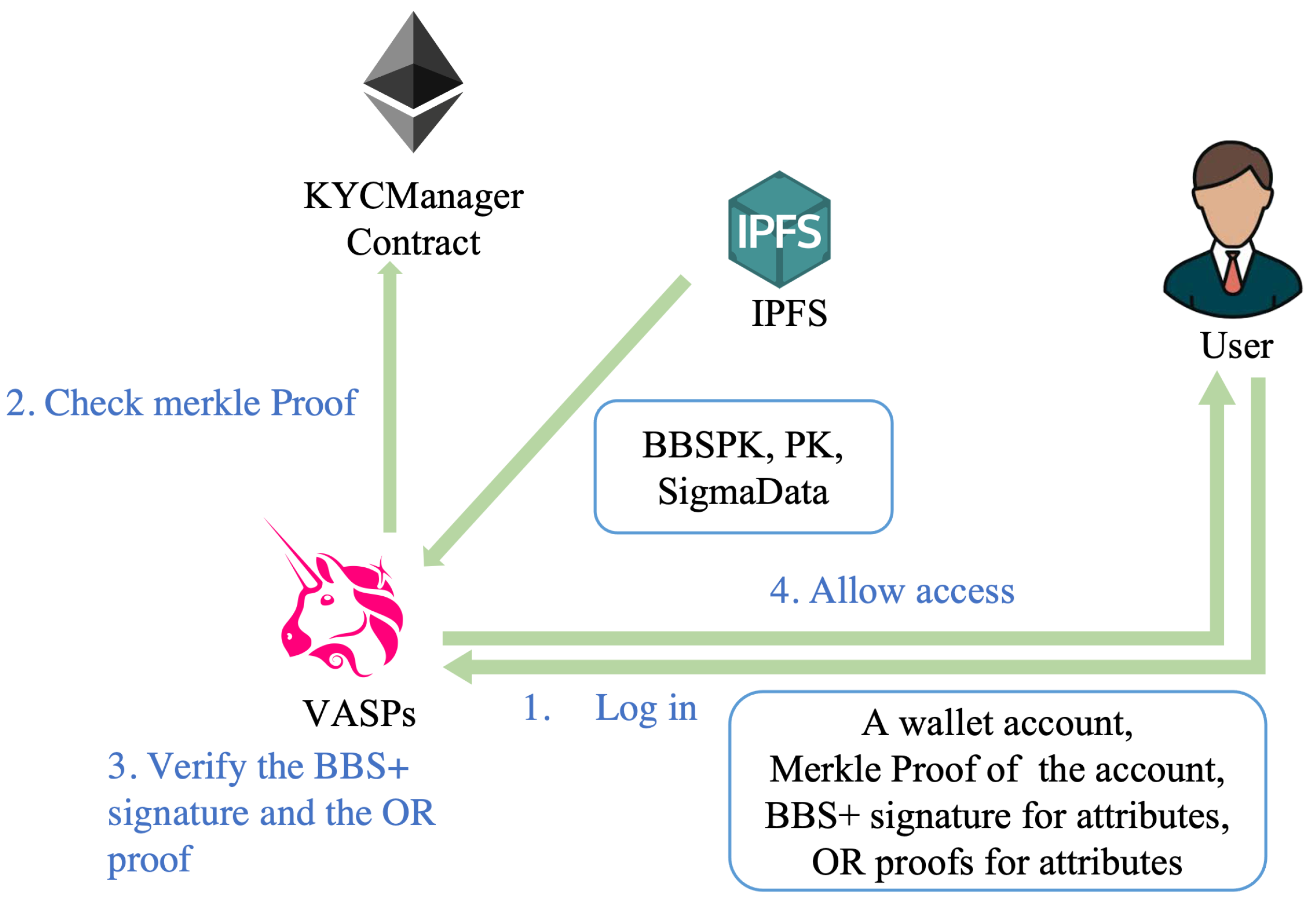
- The user initiates a login request to the VASP using a wallet account and provides a Merkle membership proof MerkleProof that proves the account is in the Merkle tree corresponding to a certain NFTId. According to the attribute requirements announced by the VASP, the user selectively discloses some attributes using the BBS+ signature of all attribute values. According to the SigmaData provided by the KYC provider, the user can generate an obfuscating proof for an attribute to prove that the attribute value belongs to a certain set without revealing which value it is.
- (6)
- By obtaining the user’s real identity data and NFTId from the KYC provider and the user’s wallet account and NFTId from the VASP, the supervisor can associate the wallet account with the real identity.
3.3. BBS+ Signature
- (1)
- Key generation: The public key data include three finite groups, G1, G2, and GT, where the order of G1 and G2 are both prime p. It also includes a bilinear pair . Take generators , . Let the number of signed messages be l, the KYC provider randomly selects and . Then, the KYC provider sets the private key and calculates the public keys and .
- (2)
- Signature: The KYC provider inputs the user-encoded attributes , where each is obtained by mapping the statement of the attribute to using a hash function. For example, mapping the attribute statement “Birthyear = 1970” to will obtain a number m = 2922 …6465. If two users have the same attribute value, they will receive the same m. Therefore, it does not hide the attribute value. Randomly select and calculate A, as shown in Equation (1):Then, the signature is sent to the user.
- (3)
- Verification: The VASP finds the tokenURL of the KYCNFT corresponding to the user’s NFTId. Get BBSPK and PK from tokenURL. Verify the signature using the attribute statements, the attribute-encoded set , and the signature BBSSig, as shown in Equation (2):
- (4)
- Users can only disclose some of the attributes. Suppose the user discloses some attribute values to the verifier; their index is denoted by the set D and the verifier maps these attributes to and obtains the set of messages to be verified, denoted as .The blinded signature is obtained. The following two Equations (6) and (7) need to be proved using any suitable zero-knowledge protocol ZKP.The verifier can compute the left side of the above two equations but not the right side of the equations. If the zero-knowledge proof ZKP passes the verification, the verifier can ensure that is created using the elements of the BBS+ signature, which means that A in the signature before blinding is in the correct form, as shown in Equations (8) and (9).In addition to verifying the ZKP, the verifier also needs to verify and the blinded signature, as shown in Equation (10).
3.4. Extend the OR Proof of the Sigma Protocol
- (1)
- The prover generates a random number r and then computes the commitment , as shown in Equation (11).Choose randomly as the challenges and random values as the responses. Calculate the commitments , as shown in Equation (12).Using as the challenge for the kth proof, calculate the response for the kth proof, as shown in Equation (15).The prover sends the proof to the verifier, as shown in Equation (16).
- (2)
- For the term , the equation holds, as shown in Equation (19).The verifier can only verify the proof and cannot distinguish which secret the verifier possesses.
3.5. Obfuscating Proofs for Discrete Finite Set Attributes
- (1)
- Let g be a generator of the cyclic group G. The user randomly generates a secret key and sends to the KYC provider.
- (2)
- The KYC provider randomly generates as fake data. Each corresponds to an attribute value . The value corresponds to the user’s real attribute value. Write this k tuple to a JSON file as SigmaData; the SigmaData will be stored in the data of the user’s KYCNFT.
- (3)
- According to the intersection of the attribute set published by the VASP and the attribute set in SigmaData, the user creates an OR proof as described in Section 3.4 to prove that his attribute value belongs to the set of attribute values that meets the requirements.
- (4)
- The VASP verifies the proof, checks whether the attribute values in the proof all belong to the required set of attribute values and if so, allows the user to access it.
3.6. KYC Authorization of Wallet Account
3.7. KYC Smart Contracts
| Algorithm 1 createKYCNFT() |
Input:
|
| Algorithm 2 setAvailableOfNFTId() |
Input:
|
| Algorithm 3 modifyManagerAddr() |
Input:
|
| Algorithm 4 updateMerkleRoot(bytes32 MerkleRoot) |
Input:
|
| Algorithm 5 verifyMerkleProof() |
| Input: fordo if then else end if end for ▹Compute the Merkel root from user-submitted proof data. ▹ Get the user data associated with NFTId. Output: |
4. Privacy and Security Analysis
- (1)
- Privacy AnalysisBlockchain digital identity schemes mainly include two aspects of privacy issues—identity privacy and wallet account privacy. The IdP knows both users’ identities and wallet accounts in all existing systems, which poses a threat to privacy. The scheme divides IdPs into supervisors and the KYC provider. Supervisors are responsible for tracing the identities of suspicious accounts, and the KYC provider is responsible for checking the identity of users. The association of identity and wallet accounts is done by the user. Supervisors can investigate the identities corresponding to suspicious wallet accounts through the information held by the KYC provider and VASPs. Therefore, for normal users, their privacy is preserved because no one but themselves knows the association between their wallet account and their real-world identity.
- (2)
- Security AnalysisImpersonation of identity and loss of private keys are the main threats to this type of solution.Due to the collision resistance of the hash function, it is difficult to find two wallet accounts that can generate the same hash value, so the Merkle membership proofs of wallet accounts are difficult to forge or fraudulently use. In addition, if the private key of the manager account is stolen, the attacker needs to initiate a transaction to update the MerkleRoot to authorize his wallet account. When users notice suspicious transactions, they can contact the KYC provider to call the contract to freeze their identity and designate a new manager account. Therefore, the risk of a user’s identity being maliciously linked to other wallet accounts is low.In existing schemes, identities and wallets are generally statically bound, for example, blockchain-based DID schemes use wallet accounts as DIDs, whereas in SBT schemes, identities are bound to wallet accounts by issuing NFTs. Once the wallet’s private key is lost, the identity will also be lost. In the scheme, the KYCManager contract owns each KYCNFT so the KYCNFT is non-transferable and will not be lost. The wallet account and the KYCNFT are dynamically bound so the identity is still available even if the private key of the wallet account is lost. If a user loses the private key of the manager account, he can contact the KYC provider to set up a new manager account. If the private key of an authorized wallet account is leaked or lost, the user can update MerkleRoot to revoke the authorization of this wallet account.
5. Discussion
6. Applications and Socioeconomic Implications
7. Concluding Remarks
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| KYC | know your customer |
| dapps | decentralized applications |
| IdP | identity provider |
| VASP | virtual asset service provider |
| AML | anti-money laundering |
| Defi | decentralized finance |
| FT | fungible token |
| NFT | non-fungible token |
| SPV | simplified payment verification |
| IPFS | Inter-Planetary File System |
| DAO | decentralized autonomous organization |
| W3C | World Wide Web Consortium |
| DID | decentralized identifier |
| SBT | soul-bound token |
| OTC | over-the-counter |
References
- The Chainalysis 2022 Crypto Crime Report. Available online: https://go.chainalysis.com/rs/503-FAP-074/images/Crypto-Crime-Report-2022.pdf (accessed on 7 September 2022).
- Hu, M.; Lee, A.D.; Putniņš, T.J. Evading Capital Controls via Cryptocurrencies: Evidence from the Blockchain. 2021. Available online: https://ssrn.com/abstract=3956933 (accessed on 10 September 2022).
- Li, Y.; Yang, G.; Susilo, W.; Yu, Y.; Au, M.H.; Liu, D. Traceable monero: Anonymous cryptocurrency with enhanced accountability. IEEE Trans. Dependable Secur. Comput. 2019, 18, 679–691. [Google Scholar] [CrossRef]
- Peili, L.I.; Haixia, X.U.; Tianjun, M.A. An efficient identity tracing scheme for blockchain-based systems. Inf. Sci. 2021, 561, 130–140. [Google Scholar]
- Ateniese, G.; Faonio, A.; Magri, B.; Medeiros, B.D. Certified bitcoins. In International Conference on Applied Cryptography and Network Security; Springer: Cham, Switzerland, 2014; pp. 80–96. [Google Scholar]
- Ma, T.; Xu, H.; Li, P. Skyeye: A Traceable Scheme for Blockchain; Cryptology ePrint Archive. 2020. Available online: https://eprint.iacr.org/2020/034 (accessed on 10 September 2022).
- Biryukov, A.; Khovratovich, D.; Tikhomirov, S. Privacy-preserving KYC on Ethereum. In Proceedings of the 1st ERCIM Blockchain Workshop 2018, Amsterdam, The Netherlands, 9 May 2018. [Google Scholar]
- Narayanan, A.; Bonneau, J.; Felten, E.; Miller, A.; Goldfeder, S. Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction; Princeton University Press: Princeton, NJ, USA, 2016; pp. 170–177. [Google Scholar]
- Meiklejohn, S.; Pomarole, M.; Jordan, G.; Levchenko, K.; McCoy, D.; Voelker, G.M.; Savage, S. A fistful of bitcoins: Characterizing payments among men with no names. In Proceedings of the Conference on Internet Measurement Conference, Barcelona, Spain, 23–25 October 2013; pp. 127–140. [Google Scholar]
- Houben, R.; Snyers, A. Cryptocurrencies and Blockchain: Legal Context and Implications for Financial Crime, Money Laundering and Tax Evasion; Publications Office of the European Union: Luxembourg, 2018; pp. 53–56. [Google Scholar]
- Monaco, J.V. Identifying bitcoin users by transaction behavior. In Biometric and Surveillance Technology for Human and Activity Identification XII; SPIE: Bellingham, WA, USA, 2015; pp. 25–39. [Google Scholar]
- Aghaee, A. Identifying blockchain-based cryptocurrency accounts using investment portfolios. arXiv 2021, arXiv:2110.04394. [Google Scholar]
- Civic. Available online: https://www.civic.com/solutions/ (accessed on 24 September 2022).
- Dunphy, P.; Petitcolas, F.A.P. A First Look at Identity Management Schemes on the Blockchain. IEEE Secur. Priv. 2018, 16, 20–29. [Google Scholar] [CrossRef]
- Ethereum Identity Standards. Available online: https://docs.ethhub.io/built-on-ethereum/identity/ERC-EIP/ (accessed on 24 September 2022).
- Origin Protocol. Available online: https://erc725.originprotocol.com/#/ (accessed on 24 September 2022).
- Self-Sovereign Identity Report. Available online: https://en.wikipedia.org/wiki/Self-sovereign_identity (accessed on 24 September 2022).
- W3C. Decentralized Identifiers (DIDs) v1.0. Available online: https://www.w3.org/TR/2021/PR-did-core-20210803/ (accessed on 7 November 2021).
- DID-Methods. Available online: https://w3c.github.io/did-spec-registries/#did-methods (accessed on 24 September 2022).
- Weyl, E.G.; Ohlhaver, P.; Buterin, V. Decentralized Society: Finding Web3’s Soul. 2022. Available online: https://ssrn.com/abstract=4105763 (accessed on 15 September 2022).
- Binance to Launch Binance Account Bound (BAB) Token, the First-Ever Soulbound Token on BNB Chain. Available online: https://www.binance.com/en/support/announcement/0fe1e7c8781844e29f56cb674231dfd7 (accessed on 21 August 2022).
- Reputation DAO. Available online: https://twitter.com/reputationdao (accessed on 24 September 2022).
- Project Galaxy. Available online: https://docs.galaxy.eco/ (accessed on 24 September 2022).
- Sublime. Available online: https://sublime.finance/ (accessed on 24 September 2022).
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260, 1–9. [Google Scholar]
- Fülöp, M.T.; Gubán, M.; Gubán, Á.; Avornicului, M. Application Research of Soft Computing Based on Machine Learning Production Scheduling. Processes 2022, 10, 520. [Google Scholar] [CrossRef]
- Buterin, V. A next-generation smart contract and decentralized application platform. White Pap. 2014, 3, 1–36. [Google Scholar]
- Szabo, N. Formalizing and securing relationships on public networks. First Monday 1997, 2, 1. [Google Scholar] [CrossRef]
- Fabian, V.; Buterin, V. EIP-20: Token Standard. Available online: https://eips.ethereum.org/EIPS/eip-20 (accessed on 20 August 2022).
- Benet, J. Ipfs-Content Addressed, Versioned, p2p File System. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Method of Providing Digital Signatures. Available online: https://patentimages.storage.googleapis.com/69/ab/d9/2ff9f94fada6ea/US4309569.pdf (accessed on 5 November 2021).
- Pedersen T, P. Non-interactive and information-theoretic secure verifiable secret sharing. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2001; pp. 129–140. [Google Scholar]
- Camenisch, J.; Drijvers, M.; Lehmann, A. Anonymous attestation using the strong diffie hellman assumption revisited. In Trust and Trustworthy Computing. Trust 2016; Franz, M., Papadimitratos, P., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2016; Volume 9824. [Google Scholar] [CrossRef]
- Damgård, I. On Σ-Protocols; Lecture Notes; University of Aarhus, Department for Computer Science: Aarhus, Denmark, 2002; p. 84. [Google Scholar]
- Bernhard, D.; Pereira, O.; Warinschi, B. How not to prove yourself: Pitfalls of the fiat-shamir heuristic and applications to helios. In International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 2012; pp. 626–643. [Google Scholar]
- BrightID. Available online: https://www.brightid.org/ (accessed on 19 October 2022).
- Proof of Humanity. Available online: https://www.proofofhumanity.id/ (accessed on 19 October 2022).
- POAP. Available online: https://poap.xyz/ (accessed on 19 October 2022).
- Ethereum Name Service. Available online: https://ens.domains/ (accessed on 19 October 2022).
- Naik, N.; Jenkins, P. Governing principles of self-sovereign identity applied to blockchain enabled privacy preserving identity management systems. In Proceedings of the IEEE International Symposium on Systems Engineering (ISSE), Vienna, Austria, 12 October–12 November 2020; pp. 1–6. [Google Scholar]


| Abbreviation | Description |
|---|---|
| BBSSK | The private key of the BBS + signature. |
| BBSPK, PK | The public key of the BBS + signature. |
| BBSSig | The BBS+ signature. |
| ManagerAddr | The manager account. |
| MerkleProof | A membership proof for a Merkle tree leaf node. |
| MerkleRoot | The root of the Merkle tree. |
| SigmaData | Public data for the Sigma protocol. |
| fileUrl | The storage path of a file in IPFS. |
| NFTId | The id of the user’s identity NFT. |
| 1. Personality Identity | 2. Credential Identity | 3. Reputational Identity | 4. Data Identity | 5. The Scheme | |
|---|---|---|---|---|---|
| Relational Pattern | Personality Verification | Ownership or Social Behaviors | Credit score, contribution value, etc. | Identity data | Identity data |
| Is it in compliance with the regulatory policy? | No | No | Yes for partial solutions | Yes for partial solutions | Yes |
| Is the wallet account anonymous to the IdP? | No | No | No | No | Yes |
| Is the wallet account anonymous to the VASP? | Yes | Yes | Yes | Yes | Yes |
| Does it support multiple blockchains? | No | Some name-service solutions support multi-chain | Only Turing-complete blockchains are supported | DID schemes support all public chains but require IdPs to do extra work | Supports all public blockchains and does not require IdPs to do extra work |
| Will the loss of the wallet’s private key affect the use of the identity? | Partial solutions support social recovery | Partial solutions support social recovery | Partial solutions support social recovery | Partial solutions support social recovery | No |
| Will the theft of the wallet’s private key affect the use of the identity? | Partial solutions support social recovery (only on Turing-complete blockchains) | Partial solutions support social recovery (only on Turing-complete blockchains) | Partial solutions support social recovery (only on Turing-complete blockchains) | Partial solutions support social recovery (only on Turing-complete blockchains) | No |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, N.; Zhang, Y.; Liu, Y. A Privacy-Preserving KYC-Compliant Identity Scheme for Accounts on All Public Blockchains. Sustainability 2022, 14, 14584. https://doi.org/10.3390/su142114584
Sun N, Zhang Y, Liu Y. A Privacy-Preserving KYC-Compliant Identity Scheme for Accounts on All Public Blockchains. Sustainability. 2022; 14(21):14584. https://doi.org/10.3390/su142114584
Chicago/Turabian StyleSun, Nigang, Yuanyi Zhang, and Yining Liu. 2022. "A Privacy-Preserving KYC-Compliant Identity Scheme for Accounts on All Public Blockchains" Sustainability 14, no. 21: 14584. https://doi.org/10.3390/su142114584
APA StyleSun, N., Zhang, Y., & Liu, Y. (2022). A Privacy-Preserving KYC-Compliant Identity Scheme for Accounts on All Public Blockchains. Sustainability, 14(21), 14584. https://doi.org/10.3390/su142114584






