Underpinning Quality Assurance: Identifying Core Testing Strategies for Multiple Layers of Internet-of-Things-Based Applications
Abstract
:1. Introduction
2. Literature Review
3. Framework for IoT Testing
3.1. Device-Level Testing
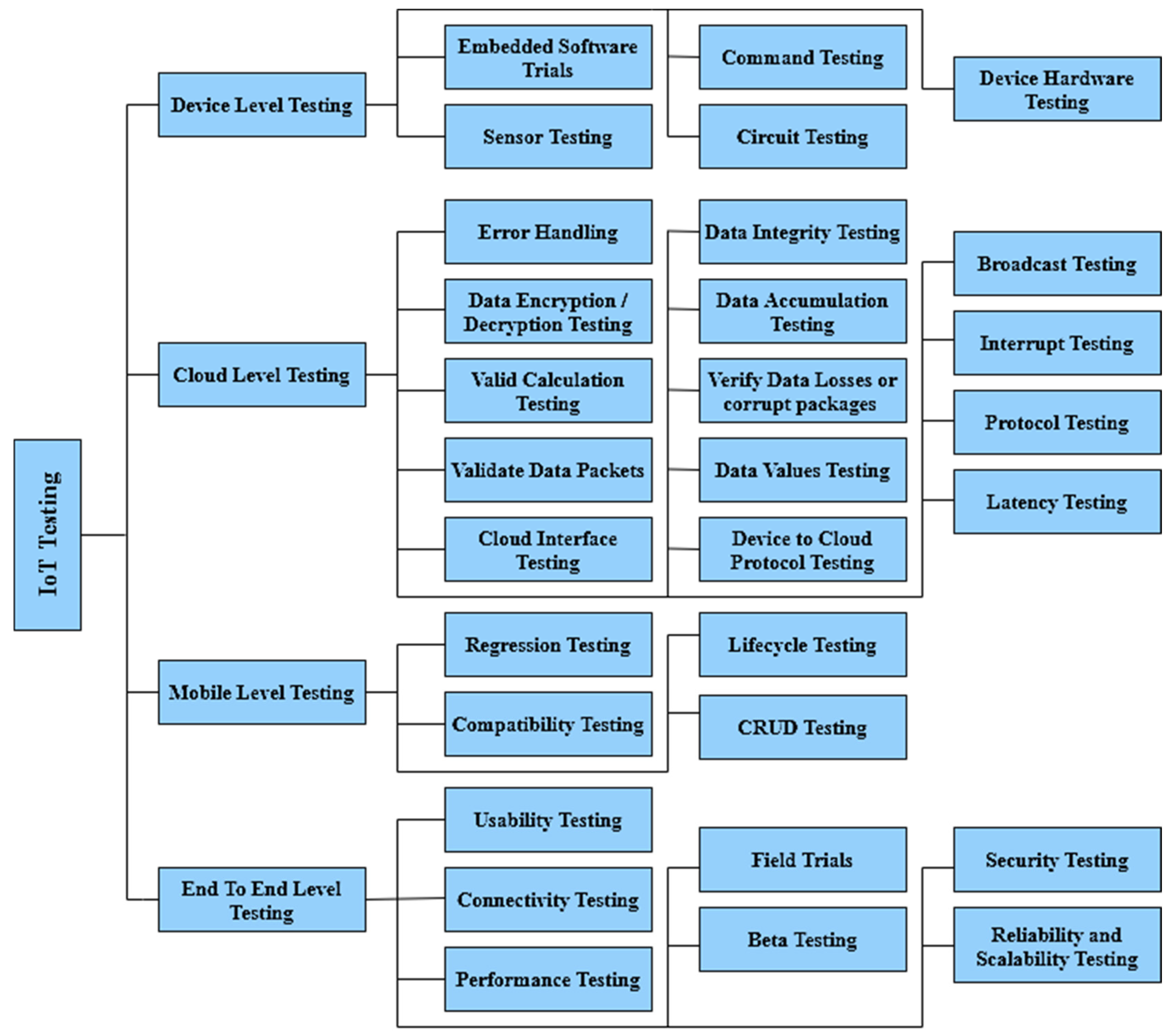
3.2. Cloud-Level Testing
3.3. Mobile-Level Testing
3.4. End-to-End Testing
4. Mapping of Important Testing Domains at each Layer of the IoT’s Layered Architecture
4.1. Collaboration and Process Layer
- Security Testing: Physical and logical threats to the security of an IoT-embedded system are analyzed. One of the best practices for maintaining the security of an IoT device is to train employees on the importance of security on an IoT device. In the case of an outside service provider, their capability of maintaining security should be validated before obtaining any services from them. The software part must be well-protected with login identification and a strong password, keeping it protected from unauthorized access to personal information or manipulation of device usage [41,42,43,44,45,46,47,48].
- Performance Testing: Performance testing deals with testing the overall performance of an IoT device. It includes checking the number of users that can be handled by the device at a time and how it reacts to the situation of excess users. It also deals with the recovery of a system in case of any issue or even if the number of users exceeds the response time of the device being tested at peak loads, as well as during normal working.
- Usability Testing: Usability testing deals with how easy a system is to use by people of every age, culture, and physical or mental capability level. This includes people, contexts, activities, and technologies to be used. Usability testing can be performed on parameters like navigation, affordability, flexibility, consistency, control, recovery, constraints, conviviality, style, and visibility.
- CRUD Testing: This means Creating, Reading, Updating, and Deleting. The response of a system is tested after performing these steps on the system to determine whether it allows new data to be added, created, accessed, and easily read by the user. A matrix is made for easy evaluation of the system. This is also a type of black box testing.
- Beta Testing: Beta testing refers to testing in which a group of people test the product and give their feedback. These people can be any external testing party. This is basically acceptance testing by the user.
- Field Trials: In field trials, the product is given to the user so that they can test it in a real environment rather than through some automation technique or artificial method.
4.2. Application Layer
- Regression Testing: Regression testing is performed after adding new functionality to an application of the IoT device by testing the whole system again, validating its results, and checking how changes in the system affected the whole IoT device.
- Reliability and Scalability Testing: Reliability and scalability testing deals with testing the system in terms of ’abilities’, i.e., the non-functional attributes of the system.
- Compatibility Testing: In compatibility testing, the compatibility of a software application is checked with other components and software in an IoT device. The compatibility of the operating system is also checked, and the type of database that is compatible with the current system type is kept in mind.
- Life-Cycle Testing: Life-cycle testing includes the validation of every step of the system development life-cycle. It checks whether every step is properly followed or not.
4.3. Data Abstraction Layer
- Error Handling: This deals with the detection, resolution, and anticipation of errors in an application and how it reacts in case of these errors, e.g., does it safely shut down and terminate the preprocess?
- Encryption and Decryption: In the case of encryption and decryption, both the data sent and received should be the same; if they are not, then how will the system deal with the error and recovery of information?
- Valid Calculation: The calculations are observed, and their validity is very important. If there is some mistake in the calculations, then the whole encryption and decryption process will be full of errors.
4.4. Data Accumulation Layer
- Validate Data Packets: The data packets sent to the communication media and received on the other end should be the same with no error or noise.
- Data Integrity Testing: Integrity of data means the quality of data. The data should be accurate, consistent, and complete.
- Data Accumulation: Data accumulation deals with collecting the data and then validating their quality.
- Verify Data Loses or Corrupt Packets: Every packet is observed and checked for the eradication of corrupt or lost data packets. There are few methods and techniques available to extract corrupted information or estimate its values.
- Data Values: The data values must be correctly sent and received.
4.5. Connectivity Layer
- Broadcast Testing: Broadcast testing ensures the quality of transmission and broadcasting of data. It is also known as a test pattern, test card, close-down, or start-up testing.
- Cloud Interface Testing: The web traffic on the cloud being used for the IoT device and the function’s validity are checked. The scalability, redundancy, and performance are also observed.
- Device-to-Cloud Protocol Testing: The requirements for compatibility of the application of the IoT device are validated, and the compatibility of the application being used to interact with the cloud is also checked. There should not be any defects arising during connection of the cloud and the application.
- Latency Testing: Latency testing checks the amount of time that the system takes to send and receive data. It should be kept to a minimum in order to provide the best-quality interface and services to the user.
- Interruption Testing: In interruption testing, the response of the system in case of all possible interrupts is observed. The system should return to a normal working state in case of any interruption.
4.6. Physical Devices and Controller Layers
- Sensor Testing: All the sensors of the IoT device are validated by checking their outputs separately. Every sensor should work properly. If any sensor does not give the correct output, then the whole calculation can go wrong. This is crucial in the case of critical systems.
- Command Testing: The commands given to the processor are validated in command testing. These commands should give the expected output.
- Circuit Connectivity: The proper connectivity of the circuit is very important. If a single wire is detached accidentally or has a wrong connection, there can be a loss of any other component, like actuators, which affects the cost of the project. The connections should be tight and validated by different devices.
- Device Testing: The proper functioning of every device separately attached, for providing services or assisting in them, must be verified.
- Embedded Software: Embedded software testing deals with the testing of the operating system of the processor being used.
5. Results and Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Townsend, J. Gradual Transformation to Secure Cloud Operations. 2016. Available online: https://www.ctl.io/blog/post/qawith-the-iot/ (accessed on 1 January 2023).
- Al-Fagih, A.E.; Al-Turjman, F.M.; Alsalih, W.M.; Hassanein, H.S. A Priced Public Sensing Framework for Heterogeneous IoT Architectures. IEEE Trans. Emerg. Top. Comput. 2013, 1, 133–147. [Google Scholar] [CrossRef]
- Kiljander, J.; D’Elia, A.; Morandi, F.; Hyttinen, P.; Takalo-Mattila, J.; Ylisaukko-Oja, A.; Soininen, J.-P.; Cinotti, T.S. Semantic Interoperability Architecture for Pervasive Computing and Internet of Things. IEEE Access 2014, 2, 856–873. [Google Scholar] [CrossRef]
- Zhou, J.; Hu, L.; Wang, F.; Lu, H.; Zhao, K. An efficient multidimensional fusion algorithm for IoT data based on partitioning. Tsinghua Sci. Technol. 2013, 18, 369–378. [Google Scholar] [CrossRef]
- Leal, A.G.; Santiago, A.; Miyake, M.Y.; Noda, M.K.; Pereira, M.J.; Avanço, L. Integrated environment for testing IoT and RFID technologies applied on the intelligent transportation system in Brazilian scenarios. In Proceedings of the 2014 IEEE Brasil RFID, Sao Paulo, Brasil, 25 September 2014; pp. 22–24. [Google Scholar]
- Li, F.; Xiong, P. Practical Secure Communication for Integrating Wireless Sensor Networks into the Internet of Things. IEEE Sens. J. 2013, 13, 3677–3684. [Google Scholar] [CrossRef]
- Mao, X.; Zhou, C.; He, Y.; Yang, Z.; Tang, S.; Wang, W. Guest editorial: Special issue on wireless sensor networks, cyber-physical systems, and internet of things. Tsinghua Sci. Technol. 2011, 16, 559–560. [Google Scholar] [CrossRef]
- Reetz, E.S.; Kuemper, D.; Moessner, K.; Tönjes, R. How to Test IoT-based Services before Deploying them into Real World. In Proceedings of the European Wireless 2013; 19th European Wireless Conference, Guildford, UK, 16–18 April 2013; pp. 1–6. [Google Scholar]
- Kuemper, D.; Reetz, E.S.; Tönjes, R. Test derivation for semantically described IoT services. In Proceedings of the 2013 Future Network & Mobile Summit, Lisboa, Portugal, 3–5 July 2013; p. 13851815. [Google Scholar]
- Gimenez, P.; Molina, B.; Palau, C.E.; Esteve, M. SWE Simulation and Testing for the IoT. In Proceedings of the 2013 IEEE International Conference on Systems, Man, and Cybernetics, Manchester, UK, 13–16 October 2013; pp. 356–361. [Google Scholar]
- Fernandes, J.; Nati, M.; Loumis, N.S.; Nikoletseas, S.; Raptis, T.P.; Krco, S.; Rankov, A.; Jokic, S.; Angelopoulos, C.M.; Ziegler, S. IoT Lab: Towards co-design and IoT solution testusing the crowd. In Proceedings of the 2015 International Conference on Recent Advances in Internet of Things (RIoT), Singapore, 7–9 April 2015; pp. 1–6. [Google Scholar]
- Desnitsky, V.A.; Kotenko, I.V.; Nogin, S.B. Detection of anomalies in data for monitoring of security components in the Internet of Things. In Proceedings of the 2015 XVIII International Conference on Soft Computing and Measurements (SCM), St. Petersburg, Russia, 19–21 May 2015; pp. 189–192. [Google Scholar] [CrossRef]
- Chuang, C.; Cheng, W.; Hsu, K. A comprehensive composite digital services quality assurance application on the intelligent transportation system. In Proceedings of the 2015 17th Asia-Pacific Network Operations and Management Symposium (APNOMS), Busan, Republic of Korea, 19–21 August 2015; pp. 368–371. [Google Scholar]
- Masirap, M.; Amaran, M.H.; Yussoff, Y.M.; Rahman, R.A.; Hashim, H. Evaluation of reliable UDP-based transport protocols for the Internet of Things (IoT). In Proceedings of the 2016 IEEE Symposium on Computer Applications and Industrial Electronics (ISCAIE), Batu Feringghi, Malaysia, 30–31 May 2016; pp. 200–205. [Google Scholar]
- Sankaran, S. Lightweight security framework for IoTs using identity based cryptography. In Proceedings of the 2016 International Conference on Advances in Computing, Communications, and Informatics (ICACCI), Communications, Jaipur, India, 21–24 September 2016; pp. 880–886. [Google Scholar] [CrossRef]
- Chandan, A.R.; Khairnar, V.D. Security Testing Methodology of IoT. In Proceedings of the 2018 International Conference on Inventive Research in Computing Applications (ICIRCA), Coimbatore, India, 11–12 July 2018; pp. 1431–1435. [Google Scholar]
- Kim, D.; Lee, E.; Kang, S. IJPoster: Expediting IoT Application Testing. In Proceedings of the International Conference on Mobile Systems, Applications, and Services, Seoul, Republic of Korea, 17–21 June 2019; pp. 572–573. [Google Scholar]
- Kaiser, A.; Hackel, S. Standards-Based IoT Testing with Open-Source Test Equipment. In Proceedings of the 2019 IEEE 19th International Conference on Software Quality, Reliability and Security Companion (QRS-C), Sofia, Bulgaria, 22–26 July 2019; pp. 435–441. [Google Scholar] [CrossRef]
- Abdallah, M.; Jaber, T.; Alabwaini, N.; Alnabi, A.A. A Proposed Quality Model for the Internet of Things Systems. In Proceedings of the 2019 IEEE Jordan International Joint Conference on Electrical Engineering and Information Technology (JEEIT), Amman, Jordan, 9–11 April 2019; pp. 23–27. [Google Scholar]
- Popereshnyak, S.; Suprun, O.; Suprun, O.; Wieckowski, T. IoT application testing features based on the modeling network. In Proceedings of the 2018 XIVth International Conference on Perspective Technologies and Methods in MEMS Design (MEMSTECH), Lviv, Ukraine, 18–22 April 2018; pp. 127–131. [Google Scholar]
- Kim, H.; Ahmad, A.; Hwang, J.; Baqa, H.; Le Gall, F.; Ortega, M.A.R.; Song, J. IoT-TaaS: Towards a Prospective IoT Testing Framework. IEEE Access 2018, 6, 15480–15493. [Google Scholar] [CrossRef]
- Papachristou, K.; Theodorou, T.; Papadopoulos, S.; Protogerou, A.; Drosou, A.; Tzovaras, D. Runtime and Routing Security Policy Verification for Enhanced Quality of Service of IoT Networks. In Proceedings of the 2019 Global IoT Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019; p. 18833635. [Google Scholar]
- Temkar, R.; Chakrabarti, P.; Jena, O.P.; Elngar, A.A.; Margala, M.; Ravi, V. Multi-attribute quality score computation for Internet of Things (IoT) based applications. Res. Sq. 2022. [Google Scholar] [CrossRef]
- Julio, Y.R.; Contreras, B.H.; Rivera, S.C.; López, C.C.; Mangonez, A.D.P.; Herazo, H.B. Framework to Manage Software Quality on IIoT Apps. IOP Conf. Ser. Mater. Sci. Eng. 2021, 1154, 012006. [Google Scholar] [CrossRef]
- Medhat, N.; Moussa, S.; Badr, N.; Tolba, M.F. Testing Techniques in IoT-based Systems. In Proceedings of the 2019 Ninth International Conference on Intelligent Computing and Information Systems (ICICIS), Cairo, Egypt, 8–10 December 2019; pp. 394–401. [Google Scholar] [CrossRef]
- Sharma, A.; Sarje, A.K. Testing Techniques for IoT Systems: A Review. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2020. [Google Scholar]
- Kumari, R.; Soni, M.K. A Comprehensive Study of Quality Assurance Techniques in the Internet of Things. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2020. [Google Scholar]
- Chen, S.; Xu, H.; Liu, D.; Hu, B.; Wang, H. A Vision of IoT: Applications, Challenges, and Opportunities with China Perspective. IEEE Internet Things J. 2014, 1, 349–359. [Google Scholar] [CrossRef]
- Lanzisera, S.; Weber, A.; Liao, A.; Pajak, D.; Meier, A. Communicating Power Supplies: Bringing the Internet to the Ubiquitous Energy Gateways of Electronic Devices. IEEE Internet Things J. 2014, 1, 153–160. [Google Scholar] [CrossRef]
- Kypus, L.; Vojtech, L.; Hrad, J. Security of ONS service for applications of the Internet of Things and their pilot implementation in academic network. In Proceedings of the 2015 16th International Carpathian Control Conference (ICCC), Szilvasvarad, Hungary, 27–30 May 2015; pp. 271–276. [Google Scholar] [CrossRef]
- Marinissen, E.J.; Zorian, Y.; Konijnenburg, M.; Huang, C.T.; Hsieh, P.H.; Cockburn, P.; Delvaux, J.; Rožić, V.; Yang, B.; Singelée, D.; et al. IoT: Source of test challenges. In Proceedings of the 2016 21st IEEE European Test Symposium (ETS), Amsterdam, The Netherlands, 23–27 May 2016; p. 16159898. [Google Scholar]
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of Things for Smart Cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Power, D.; Curry, D.; Pierson, R.; Lawrence, C. Petnet’sfailure Is a Warning to IoT developers. Available online: http://readwrite.com/2016/08/01/petnet-shows-happens-iot-fails-dl1/ (accessed on 1 January 2023).
- Naveed, M.; Usman, S.M.; Satti, M.I.; Aleshaiker, S.; Anwar, A. Intrusion Detection in Smart IoT Devices for People with Disabilities. In Proceedings of the 2022 IEEE International Smart Cities Conference (ISC2), Pafos, Cyprus, 26–29 September 2022; p. 22187135. [Google Scholar] [CrossRef]
- Allerin.com. IoT Solutions Failure Points that You Should Be Aware of. 2016. Available online: https://www.allerin.com/blog/6-iotfailure-points-that-you-should-be-aware-of (accessed on 1 January 2023).
- Training an Artificial Neural Network—Intro, solver. 2016. Available online: http://www.solver.com/training-artificial-neural-networkintro (accessed on 1 September 2023).
- Irshad, A.; Mallah, G.A.; Bilal, M.; Chaudhry, S.A.; Shafiq, M.; Song, H. SUSIC: A Secure User Access Control Mechanism for SDN-Enabled IIoT and Cyber–Physical Systems. IEEE Internet Things J. 2023, 10, 16504–16515. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Irshad, A.; Khan, M.A.; Khan, S.A.; Nosheen, S.; AlZubi, A.A.; Zikria, Y.B. A lightweight authentication scheme for 6G-IoT enabled maritime transport system. IEEE Trans. Intell. Transp. Syst. 2021, 24, 2401–2410. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Irshad, A.; Yahya, K.; Kumar, N.; Alazab, M.; Bin Zikria, Y. Rotating behind Privacy: An Improved Lightweight Authentication Scheme for Cloud-based IoT Environment. ACM Trans. Internet Technol. 2021, 21, 1–19. [Google Scholar] [CrossRef]
- Said, G.; Ghani, A.; Ullah, A.; Azeem, M.; Bilal, M.; Kwak, K.S. Light-weight secure aggregated data sharing in IoT-enabled wireless sensor networks. IEEE Access 2022, 10, 33571–33585. [Google Scholar] [CrossRef]
- Hasan, S.S.U.; Ghani, A.; Din, I.U.; Almogren, A.; Altameem, A. IoT Devices Authentication Using Artificial Neural Network. Comput. Mater. Contin. 2022, 70, 3701–3716. [Google Scholar] [CrossRef]
- Haq, M.I.U.; Khalil, R.A.; Almutiry, M.; Sawalmeh, A.; Ahmad, T.; Saeed, N. Robust graph-based localization for industrial Internet of things in the presence of flipping ambiguities. CAAI Trans. Intell. Technol. 2023; early view. [Google Scholar]
- Irshad, A.; Usman, M.; Chaudhry, S.A.; Naqvi, H.; Shafiq, M. A provably secure and efficient authenticated key agreement schemefor energy internet-based vehicle-to-grid technology framework. IEEE Trans. Ind. Appl. 2020, 56, 4425–4435. [Google Scholar]
- Kipongo, J.; Esenegho, E.; Swart, T.G. Efficient topology discovery protocol using IT-SDN for software-defined wireless sensor network. Bull. Electr. Eng. Inform. 2022, 11, 256–269. [Google Scholar] [CrossRef]
- Esenogho, E.; Djouani, K.; Kurien, A.M. Integrating Artificial Intelligence Internet of Things and 5G for Next-Generation Smart grid: A Survey of Trends Challenges and Prospect. IEEE Access 2022, 10, 4794–4831. [Google Scholar] [CrossRef]
- Alzahrani, B.A.; Irshad, A.; Alsubhi, K.; Albeshri, A. A secure and efficient remote patient-monitoring authentication protocol for cloud-IoT. Int. J. Commun. Syst. 2020, 33, e4423. [Google Scholar] [CrossRef]
- Kantarci, B.; Mouftah, H. Trustworthy Sensing for Public Safety in Cloud-Centric Internet of Things. IEEE Internet Things J. 2014, 1, 360–368. [Google Scholar] [CrossRef]












| Reference | Research Gaps | Proposed Solutions |
|---|---|---|
| A. E. Al-Fagih et al. [2] | Challenges related to pricing, resource management, and inter-operability in wireless sensors | Priced PS framework for architectures of IoT for applica tions related to services in cities to make them smart and the use of utility function of pricing for acquisition of data |
| J. Kiljander et al. [3] | The devices heterogeneity, for representing their functionality in form of a platform for virtual computing | Architectures for interoperability of semantic level architecture for pervasive IoTs and its computing |
| J. Zhou et al. [4] | Large amount of data which is sparse, dynamic, hetero geneous, and multi-source in IoT | Use of data fusion for manipulation and management of such kind of data for improvement of efficiency of data and system and for providing advanced level of intelligence |
| Leal et al. [5] | Sensing which is trustworthy and safe for general public in IoTs which are cloud-centric | Sensing-as-a-Service (S2aaS) enhances safety from public by using sensing services with help of crowd management which is provided by various smartphones having different sensors |
| F. Li et al. [6] | Integration of secured network for integration of wireless sensors of network into IoT | Heterogeneous signcryption scheme which are offline and online as well, for securing of the communication between an internet boot and sensor node |
| X. Mao et al. [7] | Issue of systems which are cyber-physical and networks which are wireless sensor in IoT | Not Defined |
| E. S. Reetz et al. [8] | Testing of services which are based on IoT before their deployment into the world | Emulation of resources of IoT interface from the architectural, implementation and semantic perspective |
| D. Kuemper et al. [9] | Derivation of test for services of IoT which are semantic based | Methodology for enriching of service related to descriptions for derivation of testing which is semi-automated and is required for the adaptions of IoT |
| P. Gimenez et al. [10] | Faster tests with reduced cost of operation and low risk | using simulator of high quality sensor, SWE simulation and web standards for sensors |
| J. Fernandes et al. [11] | So-designing issues in IOT | Platform of loT lab for the design framework of loT reference architecture model for creation of an initial design including test-bed components, crowd-sourcing, ability to do federation with other test-beds and virtualization |
| V. A. Desnitsky et al. [12] | Monitor security components for anomaly detection in components and data in IoT | Use of expert knowledge and elicitation approach and for detecting data anomalies and giving them as an input for automated systems for monitoring of IoT components of security |
| C. Chuang et al. [13] | Application on quality assurance of composite digital services on Intelligent Transportation System | Framework for integration of end-to-end testing for quality assurance which works on DSRA (Digital Service Refer ence Architecture) supported by forum of TM |
| M. Masirap et al. [14] | In-adaptability of protocol like TCP | Transport protocols based on UDP which are UDT, PA UDP and RUBDP for use in application of IoT |
| S. Sankaran et al. [15] | Increased sensitivity of securing IoTs related to data of user and consumption of high power which is the nature of IoTs | Using cryptography which is identity based and develop ment of security framework which is light in weight for IoTs |
| A. R. Chandan et al. [16] | Maintaining authenticity, confidentiality and integrity for securing the network of the IoT network | Framework for testing of IoT |
| D. Kim et al. [17] | Verification and execution of applications of IOT | TITAN is designed in such a way for allowing developers to verify and execute IoT applications preventing from being constrained by the environment, in a development environment |
| A. Kaiser et al. [18] | Growing of probability and complexity of vulnerabilities and malfunctions in IOT | IoT-Test ware Eclipse for ensuring conformance and ro bustness of protocol and secured implementations |
| M. Abdallah et al. [19] | Model for quality measurement, making the measurement process of quality less applicable, less accurate, and more challengeable | Model for the quality of IoT which consists the character istics of IoT systems, by introduction of quality factors for measuring them |
| S. Popereshnyak et al. [20] | Difficulties related to the phase of testing of applications and systems of IoT | Features related to testing, based on network of modeling of IoT Application |
| Kim et al. [21] | Increased complexity and cost of testing because of the large number of variables heterogeneity and scalability of conventional testing of IoT devices | Testing of IoT as a Service called IoT-TaaS, which is a service oriented approach for automation of testing of IoT |
| K. Papachristou et al. [22] | Routing and runtime verification of the policies for security to enhance quality of networks in IoT | Framework for number of information security policies’ verification at run-time, of the network and dynamic routing paths flow |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aljaedi, A.; Siddique, S.; Satti, M.I.; Alharbi, A.R.; Alotaibi, M.; Usman, M. Underpinning Quality Assurance: Identifying Core Testing Strategies for Multiple Layers of Internet-of-Things-Based Applications. Sustainability 2023, 15, 15683. https://doi.org/10.3390/su152215683
Aljaedi A, Siddique S, Satti MI, Alharbi AR, Alotaibi M, Usman M. Underpinning Quality Assurance: Identifying Core Testing Strategies for Multiple Layers of Internet-of-Things-Based Applications. Sustainability. 2023; 15(22):15683. https://doi.org/10.3390/su152215683
Chicago/Turabian StyleAljaedi, Amer, Saba Siddique, Muhammad Islam Satti, Adel R. Alharbi, Mohammed Alotaibi, and Muhammad Usman. 2023. "Underpinning Quality Assurance: Identifying Core Testing Strategies for Multiple Layers of Internet-of-Things-Based Applications" Sustainability 15, no. 22: 15683. https://doi.org/10.3390/su152215683
APA StyleAljaedi, A., Siddique, S., Satti, M. I., Alharbi, A. R., Alotaibi, M., & Usman, M. (2023). Underpinning Quality Assurance: Identifying Core Testing Strategies for Multiple Layers of Internet-of-Things-Based Applications. Sustainability, 15(22), 15683. https://doi.org/10.3390/su152215683


_Lu.png)



