1. Introduction
Great importance is attached to the security management of buildings. With the increasing scale and more complex internal structure and function of buildings, the theory and equipment of building security management are also progressing. Building security management comprises personnel protection, entity prevention, and technical prevention, and is accomplished with several different security systems, such as video surveillance systems, smoke control systems, and automatic fire alarm systems. It is also an essential part of building operation and maintenance. Efficient security management can ensure the safety of the building itself and the people in it, reduce the loss of the building when danger occurs, and ensure the sustainable operation of the building.
Stadiums can be used for various public activities such as sports competitions or large public events. Their ability to hold large volumes of people and their high construction standards and complex internal structures mean they require high security standards. Because of this, security management personnel usually face more complex building facility systems, more complex and irregular architectural layouts, and a more intensive flow of people compared to regular buildings, which makes managing the security large stadiums more challenging.
The intelligent building combines automated programs for sensing and control, using intelligent equipment and analysis software to monitor building operation and maintenance processes [
1]. Applications for intelligent buildings include, but are not limited to, safety control, fire detection, energy management, intelligent lighting systems, intelligent monitoring, and the control of heating, ventilation, and air conditioning systems (HVAC) [
2]. Peixian et al. [
3] state that the research on intelligent buildings mainly includes decision support, integration and interoperation, control algorithms, energy and comfort management, and occupancy detection. The general working mode of the intelligent building is to obtain parameters about the operation state of the building from monitors in the building. After analysis, building equipment systems will be automatically controlled to achieve the safety, comfort, and energy saving goals. Eini et al. [
4] analyzed the performance requirements of the intelligent building management system and used machine learning and model-based control methods to control the indicators of the indoor environment, comfort, and safety of the building. Building security management also involves various systems for intelligent buildings, such as fire alarms, water sprinklers, and smoke detection devices [
2].
The indoor security of buildings is threatened by many factors that make facility management challenging. The indoor hazards of buildings have various sources, such as fire, harmful gas leakage, electrical hazards, and illegal intrusion [
5]. These disasters can cause significant loss of life and property. Faraji et al. [
6] studied the critical factors of large-scale stadium security and proposed measures to improve stadium security. The main types of indoor hazards were summarized by Wehbe et al. [
5]. Monitoring the occurrence of hazards is essential. Dong et al. [
7] reviewed the application of indoor sensors and summarized different types of sensors used in the intelligent operation and maintenance of buildings. Regarding the danger of excessive crowding, Peixiao et al. [
8] developed an algorithm to identify whether there is crowd aggregation by analyzing the temporal and spatial changes in people’s positions. For the detection of illegal intrusion, there are active intrusion detection methods and passive intrusion detection methods. Although the intruder does not carry any equipment, passive intrusion detection methods can still detect the intrusion. Passive intrusion detection methods have received more attention [
9]. For hazards such as harmful gas leakage, toxic gas sensors are installed in the building, and an alarm is issued when the harmful gas concentration reaches the safety limit [
10].
Emergency management methods need to be developed for hazardous situations in buildings to reduce loss of life and property. When dangerous situations occur, the first thing to do is quickly evacuate the people in the building to a safe area. Indoor positioning is a technology that allows one to obtain the location of indoor people and movable objects, which is essential for emergency evacuation. Using tools such as Wi-Fi signals and micro-electro-mechanical systems, appropriate fusion positioning methods can be developed to measure the exact location of people in buildings [
11]. The BIM model contains the geometric information and attributes of the building. Building layout information is available for indoor positioning and navigation with the building information model (BIM) [
12]. For large public places such as large stadiums, both indoor and outdoor parts have complex plans. In the evacuation process of such places, multiple positioning technologies must be combined to achieve a seamless indoor and outdoor location information service. For example, the combination of positioning technologies such as the global navigation satellite system (GNSS), inertial navigation unit, and ultra-wideband (UWB) provides a seamless indoor and outdoor positioning service through the conversion of different positioning modes in the indoor/outdoor transition zone [
13]. The evacuation simulation algorithm can be used to calculate the time and path of emergency evacuation of the crowd [
14] and simulate the evacuation process in certain initial conditions. Some studies have considered the behavioral characteristics of people during evacuation. For example, Young et al. [
15] analyzed the behavioral characteristics of stadium evacuation under normal conditions, high motivation conditions, and emergency conditions. The evacuation algorithm can guide the actual crowd evacuation. For example, by connecting the pedestrian evacuation algorithm with the direction the exit sign indicates to achieve dynamic evacuation instructions [
16]. Saini et al. [
17] combined the actual position of people in the building and the pedestrian evacuation algorithm to provide evacuation path guidance for people trapped in buildings. Timely rescue is vital when danger occurs. Fire dynamics simulators (FDS) and BIM are combined to simulate fire development in the building to enable rescuers to understand the situation inside the dangerous building quickly [
18]. FDS simulates and predicts changes at the fire site, and the results are visualized with BIM. The Internet of Things is also integrated to monitor the indoor environment to provide helpful information for firefighters [
18]. To allow rescuers to check whether there are victims in the building quickly, a path planning algorithm can be used to design a path for rescuers to inspect the building [
19].
By integrating multiple security systems, the automation of the security system can be improved. Integrating the BIM model, evacuation simulation, visual display, and the maintenance of firefighting equipment in the fire management system, the functions of evacuation assessment, safety education, and equipment maintenance are realized on the same platform [
20]. The integration of sensing and control systems enabled automatic hazard perception and mitigation. For example, with the integration of combustible gas sensors and control equipment, the gas valve and exhaust fan are automatically controlled for risk mitigation when the concentration of combustible gas is too high [
21].
The introduction of digital twins provided new solutions to problems in many fields. The digital twin establishes a dynamic digital model of the physical entity and monitors, simulates and controls the physical system’s state with a multi-faceted and multi-level description of the physical system in the real world [
22]. The digital twin was initially applied to the maintenance of aircraft [
23]. With the introduction of intelligent manufacturing, digital twins are widely used in workshop management. Workshop scheduling [
24], equipment control, and equipment operation status monitoring [
25] is realized in the digital twin framework. Digital twin connects physical and virtual manufacturing processes, reproduces physical manufacturing processes in virtual models, simulates and optimizes physical manufacturing processes, and dynamically adjusts manufacturing processes [
24]. Regarding workshop production process control, some scholars have introduced digital twins into the manufacturing execution system (MES) to collect data in the production process and control production quality [
26,
27]. The automatic control of manufacturing equipment is also an important research direction of digital twins. By installing the network control devices on the physical machine, the digital twin model can send information such as manufacturing process parameters to the physical machine and then realize intelligent control of the manufacturing machine based on the production plan [
28].
Digital twins are applied to building construction and facility management in the construction industry. In the construction process, Pan et al. [
29] integrated BIM, the Internet of Things, and data mining to build a data-driven project management framework based on digital twin for predicting and optimizing construction progress. Toni et al. [
30] established a digital twin model for silos of bulk building materials to monitor the remaining materials and arrange replenishment logistics. In the field of facility management, the application of digital twins is focused on the monitoring of buildings. The virtual model can monitor and analyze the indicators of the physical building and simulate the change in the building’s performance during operation. Dang et al. [
31] established a virtual model, including a finite element model and a deep learning model, for the bridge structure, and connected it with the sensing device installed on the physical bridge to monitor and identify the structural damage to the bridge. Combining the modeling methods of the simulation-based and data-based virtual model, Kang et al. [
32] established a digital twin model of a reinforced concrete bridge and used sensors for bridge health monitoring and predictive maintenance. Combining digital twins and intelligent algorithms, Lu et al. [
33] conducted a contextual analysis of the operational data of building facilities and warned about abnormal operations. Agostinelli et al. [
34] used BIM, the Internet of Things, and artificial intelligence to develop an intelligent optimization system for energy management in residential areas to reduce the energy consumption of buildings. Hosamo et al. [
35] proposed a predictive maintenance framework based on digital twin for heating, ventilation and air conditioning systems. Combined with BIM, the Internet of Things (IoT), machine learning, and other technologies, the operation status of the air handling unit is monitored, and a predictive maintenance plan is developed.
There are research gaps in the application of digital twins in building security. Building security management involves multiple subsystems and types of data gathered from various resources. However, there is currently a lack of methods for integrated security information analysis. It is not easy to achieve data exchange between different subsystems, so many data islands exist. Although many kinds of simulation models related to building security have been developed, such as indoor environment [
34], pedestrian evacuation [
14], and fire development models [
36], they are mainly used in the simulation in specific conditions; they cannot reflect an actual emergency in the building.
The application of digital twins in building security can use the analysis and prediction capabilities of virtual simulation models to conduct real-time analysis of the status of physical buildings. The digital twin model combines virtual simulation models and sensing data to perform real-time analysis, predict and optimize the indoor environment, judge the existence of danger, and provide emergency treatment plans when the emergency happens.
The rest of the paper is organized as follows: The digital twin modeling method of intelligent security is presented in
Section 2, and the application mode of the digital twin model is presented in
Section 3.
Section 4 takes a building in the National Sliding Center as an example and the application process of the digital twin model is analyzed with several normal and abnormal situations.
The contribution of this paper can be concluded as follows: (1) A security management method based on digital twin is proposed. Multiple building security systems are integrated into the digital twin framework, and a digital twin model of intelligent security management for large-scale stadiums and its application mode is developed. (2) Integrating technologies such as BIM, the Internet of Things, and data about various aspects, to link and integrate multiple security subsystems. (3) Based on the digital twin model, the security conditions in the stadium are analyzed through virtual simulation and other ways. The facility system in the physical stadium is automatically controlled. The whole process formed a closed loop of “perception-analysis-control”.
2. Modeling Method of the Digital Twin Model for Intelligent Security in Large Stadiums
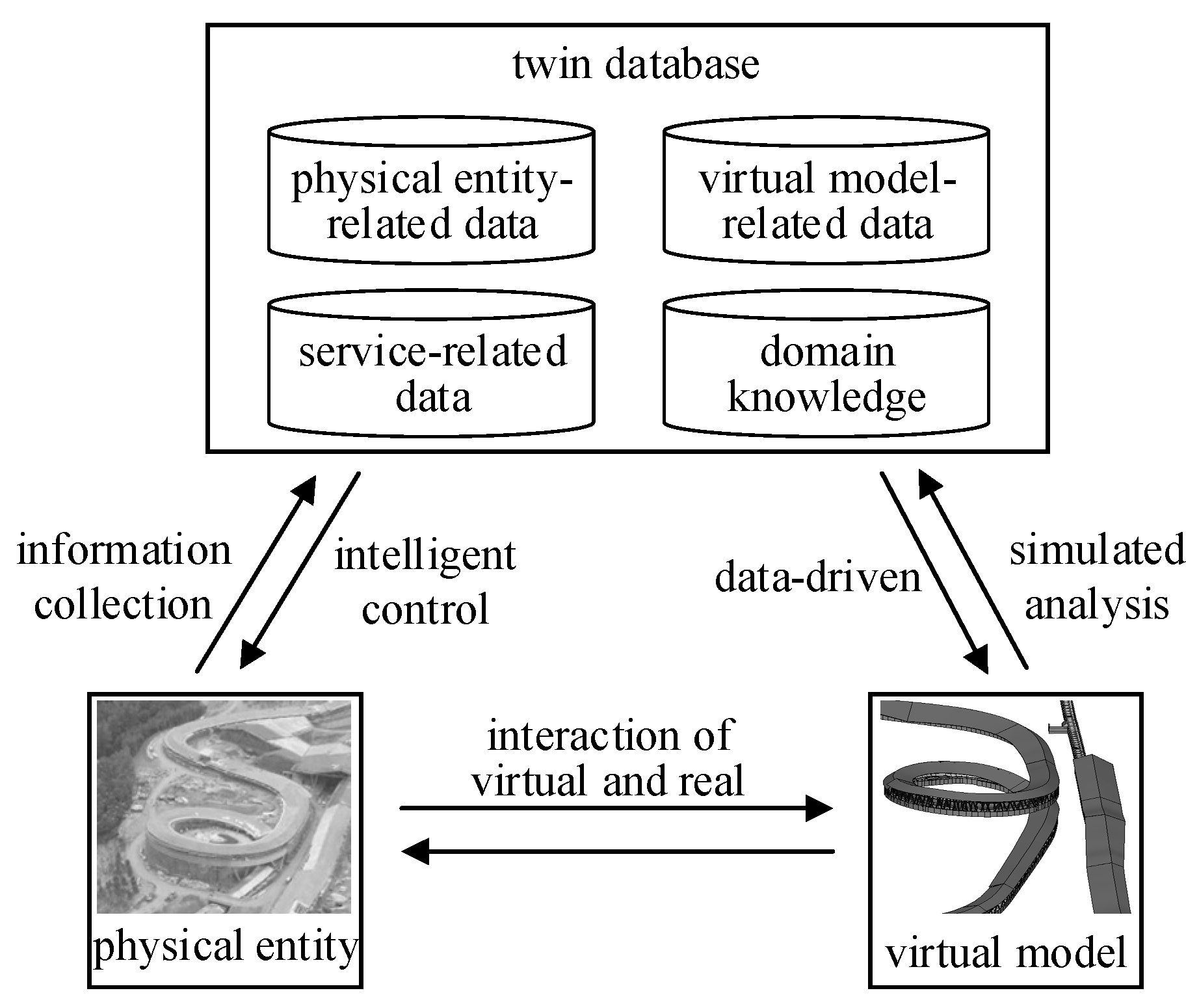
The intelligent security digital twin model includes a physical model, a virtual model, and a twin database, as shown in
Figure 1. The physical model is the basis of the digital twin model. With sensing devices in the stadium, the security data of the building are collected and uploaded to the twin database. With the network control module on the building facilities, the facilities can receive the commands generated by the virtual model. The virtual model includes models such as hazard identification, environment simulation, crowd simulation, equipment system simulation, and automatic control of facilities. The virtual model interacts with the physical stadium through interfaces. Driven by simulation models and intelligent algorithms, the virtual model analyzes data such as the location of people, the indoor environment, and the operating status of facilities, and controls the facilities automatically. In this process, GNSS provides consistent spatio-temporal data. The twin database stores physical and virtual model data, security service-related data, and domain knowledge of security management. The twin database supports the analysis of the virtual model and the automatic control of the physical stadium with data. The digital twin model for intelligent security can automatically analyze, predict, and control the security situation in the stadium by detecting the occurrence of danger, analyzing and predicting the trend of hazards, and controlling building facilities in the risk mitigation process.
The digital twin model includes a variety of virtual models for building security. While recording the security data, the current data drive the virtual model and simulate the current and future security situation. In the digital twin framework, the security data in different subsystems can be integrated into the twin database, and the data can be shared among different subsystems to realize the integrated application of multiple security subsystems.
2.1. Modeling Method of Physical Security Management Model
The physical security management model is a description of the process of security management in the real world. The model includes information about the building structure and security facilities in the physical building, as shown in
Figure 2. Security facilities include sensors and execution equipment in the stadium, which can detect and adjust the security condition in the stadium. The stadium building includes structural components such as beams, slabs, columns, walls, and other building components such as doors, windows, and pipelines, which provide environmental information for security management.
2.1.1. Modeling Method of Security Facilities
Many security facilities detect the security condition in the building, such as perimeter protection, access control, video surveillance, and smoke detection. There are also facility systems in the building to adjust the conditions in the building, which act as actuators in intelligent security systems, such as ventilation systems, smoke prevention and exhaust systems, and automatic fire extinguishing systems.
The model of the intelligent security equipment is shown in Equation (1):
In the equation, MSEQ represents the physical model of building intelligent security equipment; ID is the identification code of the intelligent security device, corresponding to the intelligent security device individually; type is the type and model of the device; prod is the manufacturer of the device; date is the data that the device has installed; loc is the location of the device; set is the parameter set of the device, which is a set containing several parameters. Different devices have different parameter sets. The symbol state is the device’s current state, including shutdown, running, and abnormal.
2.1.2. Modeling Method of the Physical Building
The components in the BIM model have a unique
ID number, which can be used to map the physical building and virtual building models. The information on components and devices can be queried in the database through
ID. The model of the building entity is shown in Equation (2):
In the equation, MSBU represents the physical entity model of building components; ID is the ID identifier of the component; type is the type of component; loc is the component’s location; material is the component’s material; and size is the size of the component. The building entity model contains the attributed information of building components, mapped to the virtual building model through component ID.
There is a kind of virtual entity that does not have a physical form and exerts its functions through the interaction of sensors and computer programs in the building, such as the electronic fence around the building. For such physical entities, corresponding virtual models need to be developed, and ID numbers are assigned for indexing.
2.2. Modeling Method of Virtual Model
According to the theory of the digital twin five-dimensional model [
22], the virtual model of the digital twin model describes the geometry, physical, behavior, and rules of physical entities. Considering the particularity of security management, the environment is added as the fifth aspect to describe the environment of security management. The composition of the virtual model is shown in Equation (3):
In the equation, MSVE is the virtual model of the digital twin model for building intelligent security, including geometry, physical, behavior, rules, and environment models. MSG is the geometric model, which describes the geometric characteristics of the building, including the plane and spatial layout of the building and facilities. In particular, geometric models of facilities closely related to security, such as security equipment, and fire hoses, should be included. MSP is the physical model, which describes the physical properties of the building, such as equipment parameters. MSB is the behavior model, which describes the behavior of the building, facilities, and people. MSR is the rule model, which describes the operation rules of the building and its ancillary facilities and the behavior patterns of the people in the building. MSE is the environmental model, which describes the environment of the entire building security system, that is, the environment inside and outside the building.
The modeling process of the virtual model is shown in
Figure 3. In the modeling process of the virtual model, a geometric model is developed based on the geometric information in the BIM model. Based on the parametric non-geometric information in the BIM model, the physical model of the building and facilities is developed with parameters. Based on the emergency management theory, the behavior patterns of people in the building are obtained as the physical model of personnel. The behavior model converts the security data generated in the security management process into parameters and analyzes the behavior in the security management process. The rule model limited the changes in parameters according to the security rules. The information on the internal and external environment of the building is expressed as parameters, and the change rule of the environmental parameters is described by the building environment analysis model, and the environmental model is developed. Based on the BIM model, security parameters and the parameter changes, the building security situation is monitored, simulated, and predicted from the five aspects of geometry, physical attributes, behavior, rules, and environment under the unified spatio-temporal reference data provided by GNSS.
2.2.1. The Modeling Method of Geometric Model
The geometric information of the stadium is included in the geometric model MSG, which provides the building information for the digital twin model, including the layout and the building facilities. The BIM model contains all the geometric details of the building, which can be used as the basis for the geometric model in the digital twin. The geometric model is based on a LOD500 BIM model. The BIM model is appropriately simplified. Only necessary information is retained to obtain the geometric model, such as building geometric information.
2.2.2. The Modeling Method of the Physical Model
The physical model is used to describe the physical attributes of the stadium, including the physical attributes of the building structure, the parameters of the building facilities, and the characteristics of people in the stadium.
The high-precision BIM model contains all geometric and non-geometric information about the building structures. Attributes such as the building components’ size and material required for security management can be extracted from the BIM model. Then, the physical properties of the building structure, such as the components’ fire resistance grade and the fire door’s maximum passing capacity, can be obtained.
For building facilities, the physical parameters can be extracted from the high-precision BIM model of the stadium. Then, the model of the building facilities’ physical properties can be developed. The physical model of security equipment should include information about the devices’ working performance. Concerning the physical model of the building, the ability of the building to meet the needs of the users in normal conditions and its ability to respond to emergencies in abnormal conditions can be calculated. The physical model of building facilities can be developed from individual components and the entire building facility system. The physical model of the component level describes the physical characteristics of a single device, such as the power and flow rate of a single fan. The physical model of the system level describes the physical characteristics of the entire building facility system, such as the ventilation volume of the complete smoke control and extraction system.
For people in the stadium, the physical model describes the characteristics and patterns of people in building security management. For example, the patterns of crowd movement in emergency evacuation and the behavior characteristics of people in an emergency.
2.2.3. The Modeling Method of the Behavior Model
The behavior model describes the behavior of elements such as equipment and personnel in building security management. Based on other virtual models and the data collected in the physical entity with the automated analysis program, the changes in parameters in the physical building are simulated, and the changes in the security situation of the building are evaluated and predicted.
For building facilities, based on the physical model of facilities and sensors installed on the devices, the operation state and process of the devices and system can be collected and simulated, and the impact of the operation of the devices on the security situation can be obtained. The behavior model of building facilities also includes the control model of equipment. Based on the control model and the system’s calculation result, the facilities’ instructions can be formed.
For the people in the building, the behavior model mainly describes the location information. To solve the positioning problems in and around the stadiums, technologies such as GNSS and UWB are integrated to provide seamless location information services in and around stadiums. Based on the location information service covering the inside and surrounding areas of the stadium, the monitoring of the intensity of people and evacuation simulation can be carried out to study the distribution of people in the building and provide location guidance for people in the emergency evacuation process.
2.2.4. The Modeling Method of the Rule Model
The rule model MSR depicts the principles and laws of security management. It includes daily security management, rules for judging dangerous states, and emergency response.
Regarding daily security management, the procedures and regulations are set up based on security standards and regulations to process data generated by intelligent security equipment, such as identifying abnormal signals.
Regarding the judgment of hazards, the criteria for the judgment of hazards generally exist in security regulations and emergency plans. These criteria are converted into regulations, and the dangerous state and the level of danger are judged by checking the security data collected from physical entities with logical judgments. For example, when the data output by the smoke detector reaches a particular value, it is determined that a fire has occurred. Artificial intelligence algorithms can be used to analyze the collected data and judge the dangerous state intelligently.
In an event requiring an emergency response, it is necessary to establish rules for dealing with hazards in and around the stadium. The sources of the rules include two aspects: the regulations about emergency response in the security code and the emergency plan made by the stadium’s manager. The rules are converted into security codes and emergency plans are converted into structured programs. Then, control strategies are set up for building facilities and the measures to be taken by security personnel in different hazardous conditions.
2.2.5. The Development of the Environmental Model
Unlike the workshop production process, the scope of building security management includes the building itself and the environment inside and around the building. There is no corresponding entity of the environment, and it is not easy to distinguish the physical and behavioral models of the environment. Adding an environmental model MSE to describe the environment involved in building security management is necessary.
The internal environment of the building mainly includes indoor environmental elements involved in building security management, such as temperature, harmful gas concentration, wind, and light. The environmental model also consists of the building environment analysis model established by the environmental analysis program, which reflects the changing pattern of the indoor environment. Based on the actual environmental data, the change in the indoor environment of the building can be simulated and predicted by running the building environment analysis model.
The building’s external environment includes the environment outside the building and its perimeter, reflecting things around the building and their relationship with the building. It mainly consists of the topography and essential public facilities around the building related to security management. The fineness of the virtual model of the external environment is determined by the requirements of building security management. GNSS and other remote sensing technologies are applied to draw geographical information, including landforms and facilities around buildings. Moreover, regular or continuous monitoring of the changes in the surrounding environment is carried out. Thus, a virtual model consistent with the environment around the building in the real world can be built.
2.3. The Structure of the Twin Database
2.3.1. Components of the Twin Database
The twin data of the digital twin model is stored in the twin database. The twin database consists of four parts: physical entity-related data, virtual model-related data, service-related data, and domain knowledge [
37].
Physical entity-related data include static data and dynamic data. Static data are data that do not change with time, such as the stadium’s geometric parameters, physical properties, and equipment properties. Dynamic data are obtained from the physical building and updated over time to reflect the security condition of the stadium. Dynamic data can also be divided into historical and real-time data according to the time the data are obtained [
38]. Historical data were collected 30 days prior, which can be used to trace and analyze the historical status of building security. Real-time data were collected within 30 days, reflecting the building’s current and recent security condition, and are one of the bases for intelligent analysis and decision-making.
The virtual model-related data include the data of geometry, physical attributes, behavior, rules, and the environment in the virtual model, forming a virtual image of the physical entity. One of the important capabilities of the digital twin virtual model is its ability to simulate the security condition of the stadium, such as the indoor environment and personnel evacuation. The virtual model-related data also include data about the simulation model, such as conditions and results.
The functions of the digital twin model in stadium security management are realized with services, including the services required for the operation of the digital twin model and the application services of security management [
37]. The data needed for the service are service-related data. The services provided by the building intelligent security digital twin model include monitoring building security conditions, the identification of hazards, and the emergency response to hazards. The data required include hazard assessment data, and control command data of the building facilities, etc.
Domain knowledge includes management experience, rules and regulations, standards, and emergency plans, etc., in the security management of large stadiums, generally expressed as regulations. Domain knowledge transforms knowledge and experience into structured procedures and can intelligently propose emergency measures in dangerous conditions.
2.3.2. Collection of Digital Twin Data
The intelligent security system based on digital twin needs to be supported by static data that reflect the basic information of the physical entity. Static data are generally obtained by data input during the modeling process, and can also be collected manually or automatically in the stadium with data collection technologies such as radio frequency identification (RFID). The static data in the twin database generally do not change with time during the stadium’s operation. During the stadium operation, static data are read from the twin database, and no changes are made to the data. When the stadium is renovated, the static data can be re-collected similarly, and the original static data can be overwritten to update the digital twin model.
The dynamic data collected from the physical model are used to drive the changes in parameters in the virtual model and reconstruct the state of the physical entity in the virtual model. The dynamic data set obtained by data collection devices is shown in Equation (4):
In the equation, DSEQ represents a collection of data collected by a data collection device, which includes one or more kinds of data collected by a particular device at a specific time. ID represents the ID number of the data collection device. The time represents the time of data collection. The name is a set of parameter names, including one or more parameter names. The value is the set of data values corresponding to the names of the parameters in name in turn.
With the sensors in the stadium, dynamic data is automatically collected and transmitted to the twin database through a unified communication protocol. An IoT system can realize this process. The transmission of the data can be wired or wireless based on the type and importance of the data.
4. Case Study
Taking a building in the National Sliding Center as an example, the application mode of the digital twin model for intelligent security management of large-scale stadiums is illustrated. The National Sliding Center (
Figure 5) is one of the newly built venues for the 2022 Beijing Winter Olympic Games. It is located in Xiaohaituo Mountain, Yanqing District, Beijing, and it will host the bobsleigh, skeleton, and luge events during the Beijing Winter Olympic Games. The National Sliding Center has a unique architectural form, posing high risks during the competition. The National Sliding Center has a 2000-meter-long track built on the mountain with five starting areas. During the competition, the top speed the athletes can reach is 134.4 km/h, which is a high risk. The large flow of people during the operation of the National Sliding Center increases the complexity of the stadium’s security management. The high-security management requirements of Winter Olympics venues require a better security management system. The digital twin model for intelligent security management can integrate multiple building security subsystems, intelligently analyze and predict the condition in the building according to sensing data, and meets the security management requirements of the stadium.
In the modeling process of the digital twin model of the National Sliding Center, a high-precision BIM model of the venue building is developed, which includes the accurate 3D model and attributes of the components and equipment in the building. Geographic information system (GIS) technology is used to establish the terrain model of the mountain. Then BIM and GIS data are integrated to describe the building and its surrounding environment.
4.1. Normal Operation
During the operation of the National Sliding Center, the stadium will be in normal condition mode most of the time due to the high-security level. In the normal operation stage, the intelligent security system based on digital twin collects the security data in the building and monitors the occurrence of hazards.
The modeling and operation mode of data acquisition equipment is illustrated with harmful gas sensing equipment. The harmful gas sensor is modeled as follows: M1 = {SH2L2XC01, CO sensor, a fire equipment factory, 2020, SH2-L2, {system name, data update frequency}, {Other fire systems, 30 s}, normal}. It means that the ID number of the device is SH2L2XC01, and the type of the device is a CO sensor, produced by a fire equipment factory and installed in 2020. It is on the second floor of a building in the National Sliding Center. The sensor belongs to the “other fire system”. The sensor’s measurement data are uploaded every 30 s, and the sensor works normally. In normal conditions, the sensor automatically collects data on harmful gas concentration. It uploads the data to the intelligent security system through the communication network in the specified update frequency to continuously monitor the harmful gas concentration at the sensor’s location. The uploaded information includes the sensor ID, current time, parameter name, and the value of the CO concentration. The intelligent security system preprocesses the received data and stores them in the twin database. The rules in the digital twin model contain the criteria for the occurrence of hazards. These criteria are expressed as critical values of various indicators or their combinations, including the criteria for concentrations of hazardous gases. During the stadium operation, the rule model continuously compares the critical value of the concentration of harmful gas (ppm) with the real-time value of the concentration of harmful gas and determines whether there is a dangerous condition. When the real-time harmful gas concentration exceeds the critical value, the system determines that there is a hazardous event and turns into an abnormal state.
Spatio-temporal information is important in security management. GNSS can provide unified spatio-temporal information for the security management of the stadium, ensure that the security systems run in the same spatio-temporal benchmark, and promote the cooperation of the security subsystems. The National Sliding Center consists of several multistorey buildings, and many building components are outdoors, providing a good condition for the reception of the GNSS signal. GNSS is used to quickly obtain the three-dimensional coordinates of important places inside and outside the stadium. It is also used to monitor the building and the surrounding mountains continuously. It captures changes in the environment in time when danger may occur, and alerts the danger with the rule model.
The people in the building are an important part of security management and also the purpose of security management. During the stadium’s operation, the location of building users’ needs be collected, and location-based services are provided to the building users. By integrating UWB and GNSS, a seamless navigation and positioning system can be built, covering the interior and exterior of the building and providing location-based services to building users. Through location-based services, while providing navigation services in complex built environments, information about the location of people inside the building is collected. Indicators such as population density can be calculated to prevent dangerous situations such as overcrowding. Considering that the speed of crowd movement is not very fast, the data refresh frequency is reduced in the process of population density estimation to reduce the burden on the system’s operation.
The data are classified in the twin database according to the time that the data are collected. Data collected within 30 days are classified into real-time data. Data collected for more than 30 days are transferred to the historical database.
4.2. Illegal Intrusion
The National Sliding Center has many facilities to maintain the venue’s operation, and many necessary equipment for competitions are stored in the stadium. The occurrence of illegal intrusions may affect the venue’s operation, such as the destruction or loss of facilities in the building, and threats to the safety of personnel in the venue. Therefore, it is necessary to focus on the prevention of illegal intrusion. The intelligent security system based on digital twin can timely perceive the occurrence of illegal intrusion and locate it. Other systems can be invoked when necessary to evacuate the people in the stadium or stop intruders.
Many accesses to control and perimeter protection equipment are arranged in the sled venues to detect whether the building has been intruded. Corresponding virtual models are developed for access control and perimeter protection equipment, including BIM models and parameters consistent with the actual devices. The data of the virtual model are stored in the twin database. The perimeter protection system without a physical fence realizes the function of intrusion detection with sensing data and logical rules, and the existence of perimeter protection is represented by the virtual fence in the geometric model.
When intruders break the access control or perimeter protection to enter the venue, the access control equipment and perimeter protection equipment will detect abnormalities and alarm, and the intelligent security system will enter an abnormal state. When the doors and windows are opened normally, the rules in the rule model will be used to determine whether the doors and windows are legally opened. Then, the occurrence of illegal intrusion will be determined. If the door that should not be opened out of service hours is opened, the rule model determines that there is an illegal intrusion and the system enters an abnormal state. The virtual model responds to intrusion events based on management regulations and emergency plans in the rule model. The area that illegal intruders may reach is calculated in the geometric model and classified as dangerous, and the access control around the dangerous area is locked to stop intruders. Path planning algorithms are used to design an optimized route for security personnel to reach the location of intruders, and location-based services are used to direct the security personnel to the scene for processing. When illegal intrusion occurs during the service hours of the stadium, the evacuation simulation algorithm is used to simulate the evacuation according to the distribution of people in the stadium. According to the simulation results, the people in the stadium can be guided to avoid dangerous areas while leaving the stadium. In the emergency response process, the intelligent security system continuously monitors intruders’ positions and dynamically adjusts the dangerous area and the evacuation path. When the illegal intrusion event is successfully disposed of, the intelligent security system removes the alarm according to the instruction issued by the building management personnel. The application process in the intrusion scenario is shown in
Figure 6.
4.3. Fire
Fire is one of the most dangerous disasters that can occur in large public buildings. Fire can develop rapidly and cause significant harm to people’s lives and property; therefore, it has been the focus of attention in the design and maintenance of buildings. In the emergency management of fire, it is necessary to use many building facilities. However, traditional fire protection systems usually lack the ability to control building facilities automatically. The evacuation and the emergency start of equipment rely on manual operation. The intelligent security system based on digital twin has the ability to integrate systems, simulate them, and predict the situation in the building, and can carry out a dynamic update of emergency strategies and intelligent equipment control in fire scenarios.
Intelligent sensors for fire prevention, such as smoke detectors, carbon monoxide detectors, temperature sensors, and fire extinguishing systems such as fire pumps, automatic sprinkler systems, and smoke control systems, are installed in the venues. The BIM model consistent with the physical devices is developed to form the geometric model, and is attaches the devices’ properties including ID, type, location, performance parameters, and working state to the BIM model to develop the non-geometric model. The simulation model of the indoor environment of the stadium is developed based on indoor environment simulation technology. The evacuation simulation model is based on the evacuation algorithm and building layout. They are included in the stadium’s environmental and behavioral models.
During the stadium operation, the twin database receives the environmental data obtained by indoor environment sensors, and the virtual model judges whether the parameters are within the normal range. When the data exceed the safety range, the intelligent security system alarms and turns into an abnormal state. In the abnormal state, the system reconstructs the conditions of the physical building in the virtual model with the data obtained in the stadium. The static information of the building is provided by the geometric and physical models, and the change in environmental parameters in the stadium is simulated with the behavior, rule, and environmental models, and the predictive emergency management strategy is given. According to the detected location of the fire, the dangerous area is marked in the geometric model and shown to managers and users. The dangerous area is set to be unreachable in the evacuation model. The spray system and fire pumps at the corresponding position are started based on the logical rules in the rule model. The environmental model can simulate the changes in the environmental parameters inside the building, such as temperature, harmful gas concentration, and airflow direction. Based on the simulation model of airflow and location of the fire, the ventilators in the emergency ventilation system need to start and the flow rate that needs to be reached is given. Then, the control signal is sent to the corresponding devices. Building managers take emergency measures according to the tips given by the digital twin model. At the same time, the virtual model simulates the development of the fire, the change in dangerous areas and the state of the building facility system, and take preventive control measures based on the simulation results. The development trend of the fire after the control measures are applied is simulated based on the changed simulation parameters, and the control measures are optimized based on the simulation results. Then, the optimized control strategy is converted into parameters to form the control instructions. Before the fire is extinguished, the sensor continuously obtains data, judges whether the fire is extinguished, and updates the simulation parameters. The process is shown in
Figure 7.
In the process of emergency evacuation, the evacuation model dynamically avoids the dangerous area and optimizes the evacuation path according to the location of people. Based on the optimized evacuation path, the direction of evacuation indicators in the building is adjusted automatically and guides people in the building to escape along the optimized route. Under the simulation condition, the emergency evacuation guidance function of the digital twin model is tested in the scene of a fire in a building of the stadium. The simulated fire occurred in a stairwell on one floor of the building. The indoor environment index data during the fire were simulated by computer, including indoor temperature and the concentration of harmful gas. When a fire occurs in the room, the indoor environment indicators in the room where the fire occurs change. When either of the two indices of indoor temperature and harmful gas concentration exceed the normal range, it is determined that a fire occurs in the building. At this time, the intelligent security system enters the abnormal operation mode. The system obtains the location of the fire based on the location that the abnormal data came from, and defines the burning room and the affected area near it as dangerous area. Then, the dangerous area is made inaccessible in the geometric model to avoid directing people in the building to the danger area. The points inside the room and the crossing points on passages in the architectural plan are taken as nodes. Then, the nodes are connected with straight lines to form a topology diagram that describes the connectivity among the rooms. The topology diagram is used as the input of the path planning algorithm. Particularly, the dangerous area is made unreachable by setting the distance between the nodes in the danger area and the surrounding nodes to infinity. In the intelligent security system, the location of people is determined by the positioning system set up in the building. With the path planning algorithm, taking the location of people as the starting point and the exit as the end point, the optimal route of emergency evacuation is calculated, and evacuation guidance is realized by changing the direction of evacuation indicators. People in the room may be evacuated to the nearest stairwell if no intelligent security system is applied for evacuation guidance. However, when the nearest stairwell is a dangerous area, people turn back there, increasing the evacuation distance. However, if the intelligent security system is applied for evacuation guidance, the dangerous areas in the real world are mapped to the virtual model of the building, thus obtaining an optimized route that does not pass through the dangerous areas. Based on the evacuation route given by the twin model, the intelligent security system changes the directions of the evacuation indicators in the building to guide the people to evacuate along the optimized route. The evacuation route with evacuation guidance is shorter than that without guidance. The intelligent security system based on digital twin can effectively avoid extending the evacuation path caused by blind evacuation due to a lack of understanding of the building layout and the dangerous locations in the evacuation process and effectively shorten the evacuation time.
5. Conclusions
This research applied digital twin to the field of security management of large stadiums, developed a digital twin model for intelligent security, and proposed the operation mechanism of the security management system driven by the digital twin model. The model described a variety of information about the security of the stadium. By describing the geometric shape and physical characteristics of building structures and facilities, the behavior of the elements in security management, the rules of security management, and the features of the internal and external environment of the building, the security condition in the physical stadium can be accurately reconstructed in the virtual world. Simulation models and intelligent algorithms are applied in the virtual model to simulate and predict the development of danger. In the digital twin framework, GNSS and multiple security subsystems are integrated. The building facilities are automatically controlled with the virtual model to adjust the building’s security condition automatically. The proposed method improved the efficiency and intelligence of security management in large stadiums.
The following conclusions can be drawn from the research:
A modeling method and application framework for intelligent security based on digital twin are proposed. Digital twin technology is used to solve the problem in the security management of large stadiums.
Simulation models and intelligent algorithms are introduced to the intelligent security system. They simulate and predict the security condition based on sensing data, and optimize the emergency strategies in hazardous situations. The functions of automatic identification of the type of danger, auxiliary processing in emergencies, and automatic control of the emergency equipment in the building were realized, reducing the labor intensity of security management personnel.
The modeling method and application framework for intelligent security based on digital twin proposed in this paper is universal. However, the specific implementation methods may need to be modified because the security management in different buildings faces different operation scenarios and types of danger. However, the intelligent security digital twin modeling method and application mode are similar.
Large-scale buildings such as stadiums have complex internal structures and various types of building facility systems. In the operation process of large stadiums, it is necessary to employ an extensive workforce to check the security situation of the whole building, and to operate multiple building facility systems. Particularly in an emergency, security managers find it difficult to quickly determine the occurrence of danger. Handling an emergency requires security managers to operate multiple building facility systems simultaneously to mitigate the emergency’s damage to the building. Based on the BIM model and the virtual simulation model of the facility system and indoor environment formed in the design phase of the building, the geometric, physical, behavioral, rule and environmental information required by the digital twin model for intelligent security are obtained. Various building facilities and their systems provide a way to perceive and control the security situation in the building. The intelligent security system based on digital twinning combines the two aspects. In the process of security management, the simulation ability of the virtual model is applied to analyze and forecast the collected information on the security situation, and the development trend of danger is predicted during an emergency and the decision is made. The building facility system is integrated into the intelligent security system to control danger through the automatic control of the facility system. The proposed method can be applied to large stadiums and similar buildings to carry out intelligent perception, analysis, and prediction of the security situation in the building. The security situation is controlled with facility systems in the building, and the danger is analyzed and dealt with intelligently when an emergency occurs. The proposed method can improve the efficiency of building security management.
This method provides an automatic process for the security management of large stadiums, and can improve its efficiency and automation. However, the method has limitations. The amount of attributed information in large stadiums is huge, and the data are usually provided in different formats. It is challenging to integrate such a large amount of complex building information. Integrating the control systems of multiple building facility systems within a building is also challenging because they often use different control systems. The case study in this paper integrated part of the data and facility systems of the building to verify the feasibility of the method. In addition, realizing the complete digital twin of building security requires the cooperation of theory, equipment, software, and the management system. Based on the theoretical discussion of the modeling method and the application process of the digital twin model for intelligent security management, the developing method of the intelligent security system based on digital twin will be further studied, focusing on aspects of software and equipment, in future research.