Blockchain-Based Decentralized Storage Systems for Sustainable Data Self-Sovereignty: A Comparative Study
Abstract
1. Introduction
1.1. Contributions
1.2. Methodology
- Data Collection: A comprehensive review of the existing literature, technical documents, whitepapers, and user forums related to decentralized storage platforms was conducted. This diversity of data sources provided a robust foundation for understanding the current state of these systems and their real-world applications.
- Comparison of Key Features: The key features of the selected decentralized storage platforms were systematically compared, focusing on the underlying technology, primary use cases, data redundancy, security, privacy, incentivization, payment models, data control, versioning, and community adoption. Particular emphasis was placed on assessing the support for DSS and integrating blockchain technology to enhance user control and data integrity.
- Analysis of Performance Metrics: Performance metrics, including upload/download speed, latency, throughput, data redundancy, resource efficiency, and scalability, were analyzed. This analysis evaluated each platform’s operational efficiency and practical viability in supporting sustainable DSS.
2. Research Background
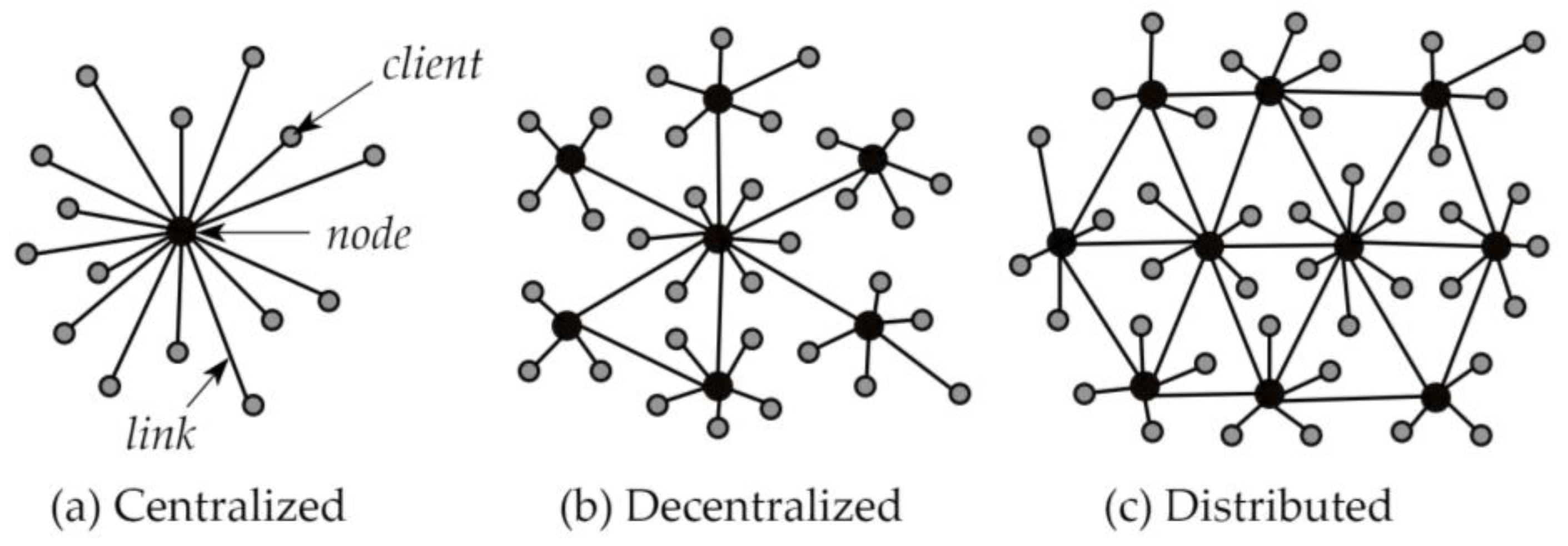
2.1. Centralized, Decentralized, and Distributed Storage Systems
2.1.1. Centralized Architectures
2.1.2. Decentralized Architectures
2.1.3. Distributed Architectures
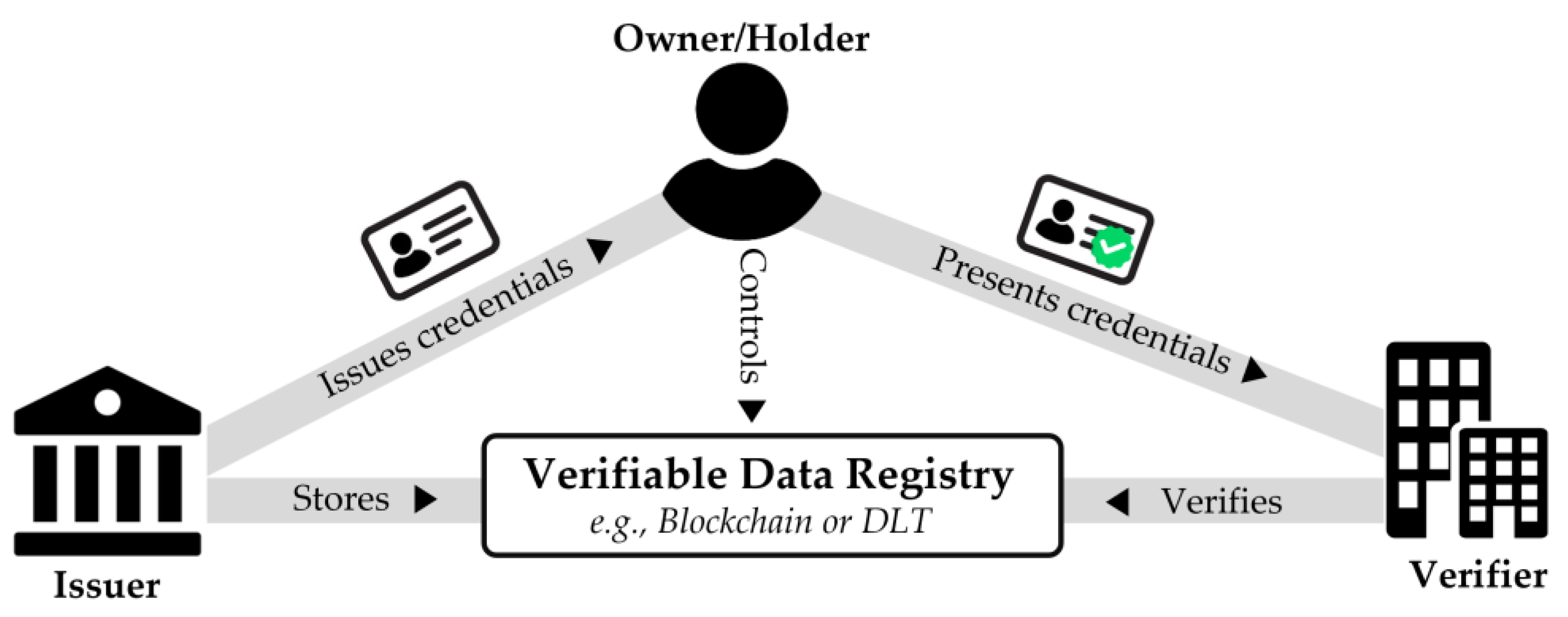
2.2. Data Sovereignty, Data Self-Sovereignty, and Self-Sovereign Identity
2.2.1. Data Sovereignty
2.2.2. Data Self-Sovereignty
2.2.3. Self-Sovereign Identity
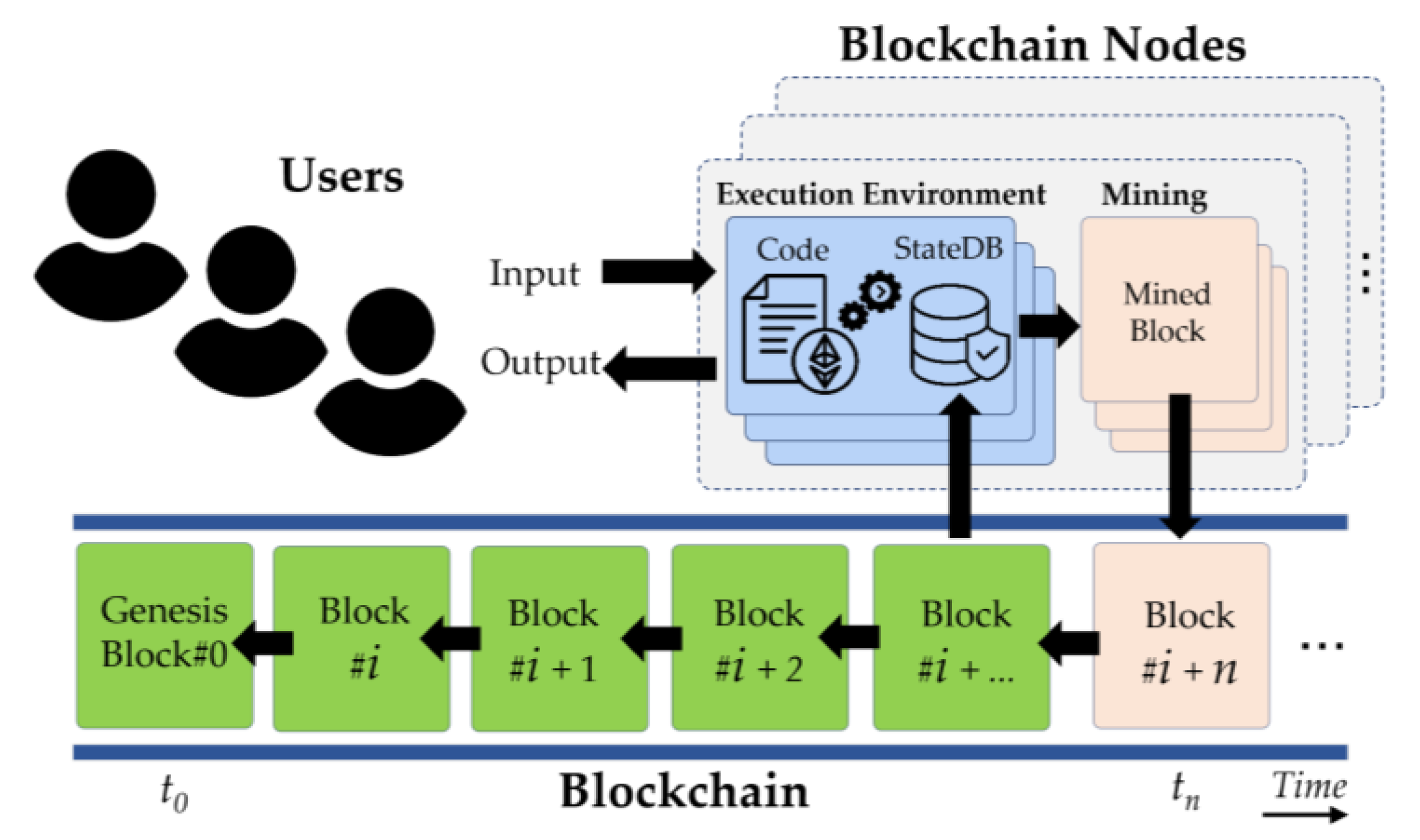
2.3. Blockchain, Consensus, and Smart Contracts
2.3.1. Blockchain Definition
2.3.2. Blockchain Classification
- Public blockchains are permissionless networks where participants can securely engage in transactions without intermediaries [47,48,49]. These networks operate in a trustless environment, meaning transactions are validated and recorded without requiring trust between the parties involved. Notable examples include Bitcoin [47] and Ethereum [48], widely recognized for their open and decentralized nature. In these public blockchains, participants can join the network anonymously, and any node with the requisite software can create, verify, and validate transactions. The key advantages of public blockchains include independence, decentralization, transparency, and trust. However, due to the computational demands of consensus mechanisms such as PoW, these networks often face problems related to performance, scalability, and high energy and resource consumption [47,48,49].
- Private blockchains are closed, permissioned networks managed by a single organization or a select group of entities [50,51,52,53,54]. Access is restricted to authorized participants, allowing greater control over the network and its operations. Hyperledger Fabric [50,51], R3 Corda [51,52], and Ripple [53] are prominent examples of private blockchains. While private blockchains offer improved performance, scalability, and privacy compared to public blockchains, they sacrifice some of the core principles of decentralization, although some private blockchains may be controlled by a small group rather than a single entity [50,51,53]. The centralized control in private blockchains may limit transparency and trust because the managing organization strongly influences the network’s operations.
- Consortium blockchains represent a hybrid model that combines elements of both public and private blockchains [50,51,52,53,54,55,56]. These networks are managed by a group of organizations that share a common ledger, with governance distributed among the consortium members [50,51,54]. Consortium blockchains balance the openness of public blockchains and the control of private blockchains, offering enhanced security and decentralization compared to private networks. However, establishing and maintaining a consortium blockchain can be complex, requiring coordination and collaboration among multiple entities. Examples of consortium blockchain platforms include Hyperledger Fabric [50,51], R3 Corda [52,53], Hyperledger Sawtooth [55], and Quorum [56]. These networks are particularly well-suited for industries where multiple organizations must collaborate while maintaining control over their data and transactions.
2.3.3. Consensus Protocols
2.3.4. Smart Contracts
2.4. Decentralized Storage Systems
2.4.1. Decentralized Storage Architecture
2.4.2. Decentralized Storage Characteristics
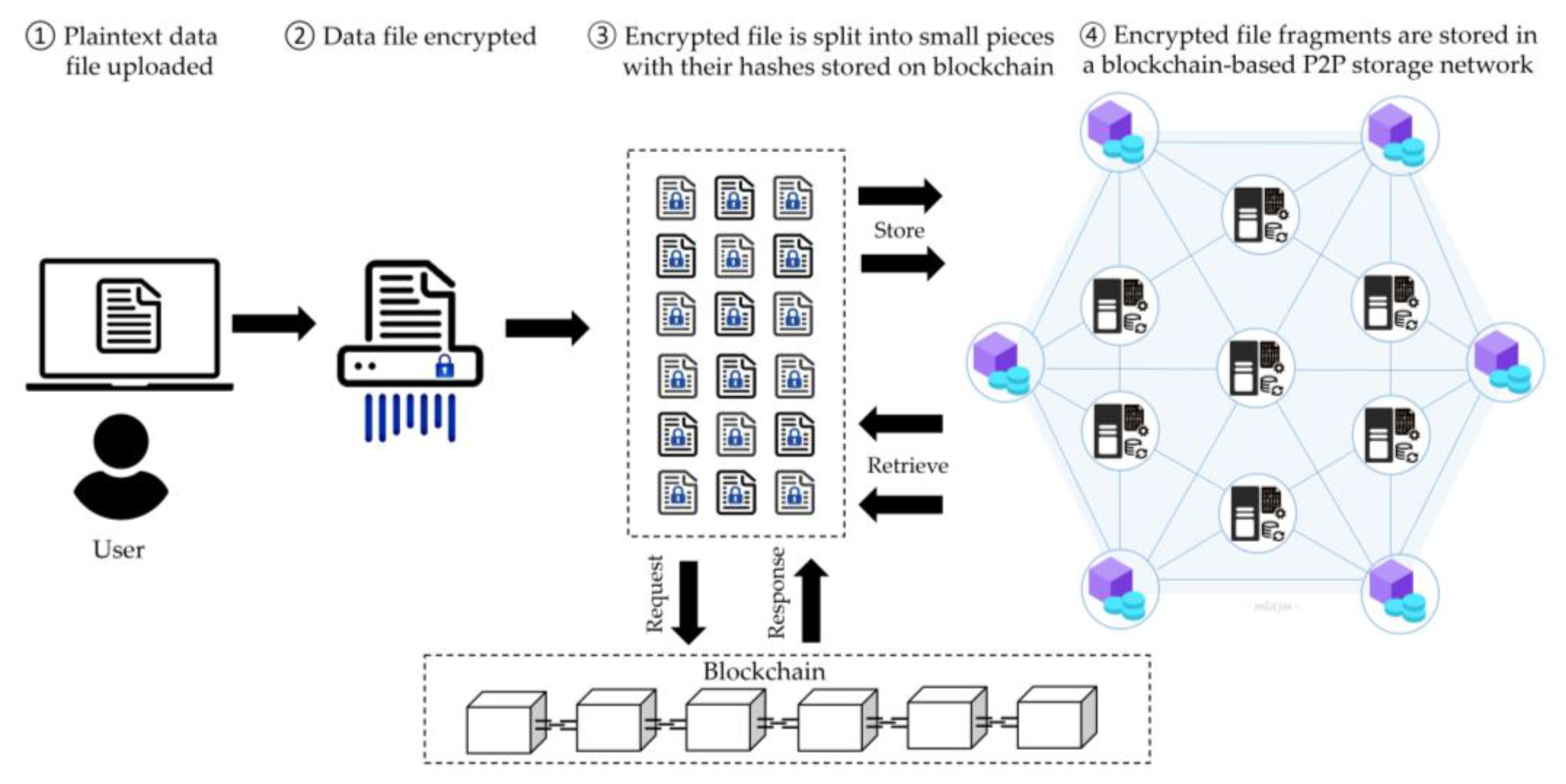
- Decentralization: Unlike traditional storage solutions that store data on centralized servers controlled by a single entity, decentralized storage systems distribute data across a network of nodes governed by consensus protocols [31,32,33,34,35,36,37,38,39,40,41]. This distribution is enabled by blockchain or other DLTs, which ensure that no single point of control exists within the system [47,48,49,50,51,52,53,54]. This decentralization enhances system resilience and reduces the risk of data tampering or loss due to central server failures.
- User Control and Censorship Resistance: One of the fundamental principles of decentralized storage systems is that users have full ownership and control over their data. These systems inherently resist censorship because no central authority can enforce data removal [32,33,34,35,36,37,38,39,40,41]. Users retain the ability to determine how their data are shared and used, ensuring that they maintain sovereignty over their digital assets. User control is essential in environments where freedom of information and privacy are vital.
- Enhanced Security and Privacy: Decentralized storage systems significantly enhance security and privacy by spreading data across multiple nodes in the network [34,35,36,37,38,39,40]. This dispersion makes it more difficult for attackers to compromise the entire system because gaining control of a single node does not provide access to the complete dataset. Additionally, these systems employ advanced encryption and cryptographic techniques to protect data from unauthorized access [32,33,34,35,36,37,38,39,40,41]. This ensures the data remain secure and unreadable even if a node is compromised without the proper decryption keys.
- Redundancy and Reliability: One of the key advantages of decentralized storage systems is their inherent redundancy. Data are replicated across various nodes within the network, ensuring that they remain accessible even if some nodes fail or go offline [35,36]. This redundancy enhances the system’s overall reliability, giving users confidence that their data will be available when needed.
- Data Portability: Decentralized storage systems offer greater data portability, allowing users to move their data easily from one service provider to another [10,18,20]. This is possible because no single provider has a lock-in over the user’s data. Users can migrate their data without the restrictions often imposed by centralized storage providers, thus avoiding vendor lock-in and enhancing user autonomy.
- Interoperability and Scalability: Decentralized storage systems are designed to be highly interoperable and scalable [32,33,34,35,36,37,38,39,40]. They can be easily integrated with different systems and services, accommodating various use cases and applications [18,19,20]. As the network of nodes grows, the system’s storage capacity and processing power can scale accordingly, allowing it to handle increasing amounts of data without compromising performance. This scalability supports large-scale applications and ensures the system remains efficient as demand grows [32,33,35].
3. Existing Decentralized Storage Solutions
3.1. Key Feature Comparison
- Arweave [32] is a decentralized platform that provides permanent data storage, focusing primarily on privacy, censorship resistance, and long-term data durability. It employs a blockchain-like structure called Blockweave, which ensures that data are retained indefinitely once stored [31,32]. This permanence is achieved through high redundancy, where copies of the data are distributed across the network and stored forever. The platform employs advanced encryption techniques to ensure high security and privacy. Transactions within the Arweave network are facilitated by its native cryptocurrency AR tokens [32], which users use to pay for storage services. Despite its strong focus on data permanence and security, Arweave does not support file versioning, which might be a limitation for users requiring historical data tracking [31,32]. Arweave has been particularly appealing for use in projects that must store critical data permanently, such as archives, academic records, and web content requiring tamper-proof preservation [25,32,34,54].
- BitTorrent [33], one of the most well-known P2P file-sharing protocols, is known for efficiently distributing large amounts of data over the internet. Due to its robust scalability and widespread adoption, it is especially effective for sharing popular files that many users want to access simultaneously. Despite its basic security, which largely depends on the file source, BitTorrent remains widely used due to its ease of use and scalability [31,33]. The platform does not integrate blockchain technology and lacks file versioning functionality. BitTorrent has evolved into a suite of commercial products, including the BitTorrent File System (BTFS) [64], a scalable decentralized storage system that aims to reduce storage costs, improve fault tolerance, and avoid censorship. BTFS leverages the large user base of the BitTorrent protocol to create a distributed file storage network that supports dApps [64]. However, BitTorrent and BTFS do not integrate blockchain technology directly and lack file versioning capabilities, which may limit their use cases in scenarios that require blockchain’s trustless features.
- Dat [34] is an open-source, decentralized data-sharing protocol specifically tailored to the needs of the scientific and academic communities. It enables a secure, versioned, and distributed data storage network that allows researchers to share datasets using a P2P protocol [31,34]. Dat is designed to foster collaboration among researchers via the efficient sharing of large datasets with built-in version control, which allows users to access previous versions of the data [31,34]. This makes it an invaluable tool for collaborative scientific research, which relies on the integrity and reproducibility of data. The focus on privacy and user control is essential for its niche community, which values the ability to maintain autonomy over shared data without relying on centralized authorities [31,34]. Dat is backed by a community of developers and researchers dedicated to improving the transparency and accessibility of scientific data.
- Filecoin [35] is a decentralized storage network that transforms cloud storage into an algorithmic market. Built on IPFS [37], Filecoin allows users to rent out their unused storage space in a decentralized storage marketplace; users can choose from various storage providers based on price, redundancy, and geographical location. The platform operates on a blockchain foundation, ensuring transaction transparency and security [31,35,65]. Filecoin uses strong encryption and file contracts to guarantee data integrity and privacy, making it a highly scalable solution for decentralized storage needs. Although Filecoin offers robust privacy protections, it does not support file versioning, which is a limitation for users who require access to historical versions of their data [31,35]. The Filecoin network is powered by its native cryptocurrency, also named Filecoin [35], which incentivizes users to provide and maintain storage capacity on the network. Filecoin is widely regarded as one of the most promising decentralized storage solutions, hosting a growing ecosystem of applications and services.
- Hypercore Protocol [36] is an open-source P2P protocol for fast, scalable, secure, and real-time data sharing. It is built on Hypercore logs [36], signed append-only logs similar to lightweight blockchains without a consensus algorithm. Hypercore Protocol is optimized for efficiently sharing large datasets and streaming data, which makes it suitable for various applications, such as collaborative environments and real-time data streams [31,36]. The protocol provides high redundancy and scalability, ensuring data remain accessible and consistent across the network. Hypercore also supports file versioning, allowing users to track changes and access previous versions of their data [31,36]. The platform is backed by an emerging community of developers and users exploring its potential use in various applications.
- IPFS [37] is a decentralized and P2P file-sharing network designed for securely storing and sharing data in a distributed file system. IPFS uses a content-addressing scheme that uniquely identifies each file based on its content rather than its location, creating a more efficient and resilient internet [31,37]. The system employs a distributed hash table (DHT) and Merkle-directed acyclic graph data structure to ensure data integrity and availability across the network [37]. IPFS is particularly well suited for applications that require decentralized web hosting, distributed data sharing, and content distribution [31,37]. The platform balances privacy with user control, offering high scalability and file versioning support. IPFS has been widely adopted and has a large and active community of users and developers, expanding its capabilities. Other decentralized storage solutions, such as Filecoin [35,65], use IPFS as their underlying technology, demonstrating its versatility and importance.
- MaidSafe [38] is a decentralized file system operating on the Secure Access For Everyone (SAFE) network [31,70,71] without centralized control or indexing. The SAFE network is designed for secure and decentralized data management services with support for file versioning, thus ensuring data privacy, security, and user autonomy [38,70,71]. It employs a distributed locking mechanism to ensure data integrity, even when multiple users access the same file simultaneously [70,71]. While its scalability is moderate, MaidSafe benefits from an established community of supporters and contributors. Safecoin [31,72] is the native cryptocurrency of the SAFE Network, which is used to incentivize users to contribute resources. Safecoin enables secure, private transactions and facilitates micropayments within the network without intermediaries [31,72]. MaidSafe’s focus on privacy and security makes it a popular choice for users who prioritize these features in their data storage solutions.
- Sia [39] is a blockchain-based decentralized cloud storage platform that splits, encrypts, and distributes files across a decentralized network. This platform ensures high redundancy and security, allowing users to maintain control over their data [39,65]. The storage model of Sia enables users to rent out unused storage space to others, creating a decentralized storage marketplace. The platform uses strong encryption to protect data and offers high redundancy by storing multiple copies of each file across the network [39]. Sia’s scalability is moderate, and its storage and retrieval services are powered by its native cryptocurrency, Siacoin [39,65]. Siacoin facilitates transactions within the network, incentivizing storage providers and ensuring the continued availability of storage resources. Sia is particularly well suited for users who require a secure and decentralized alternative to traditional cloud storage services.
- Storj [40] is a decentralized cloud storage platform that leverages blockchain technology to provide secure, efficient, and cost-effective data storage services. All data stored on Storj are encrypted, fragmented into small pieces, and distributed across a global cloud network [31,40,65]. The platform ensures enhanced privacy and security through encryption and sharding, restricting data access to owners or authorized users. The platform supports file versioning, allowing users to track changes and access previous versions of their data [40]. Storj has gained widespread community adoption due to its high scalability, ease of use, and support for various applications, including web hosting, data archiving, and content distribution [40,65,73]. The platform uses STORJ tokens as its payment model [73] to incentivize storage providers and facilitate transactions within the network.
- Swarm [41] is a distributed storage platform and content distribution service that is part of the Ethereum Web3 Stack [48]. It provides decentralized public record storage with high redundancy and security, ensuring that data remain accessible and tamper-proof [31,41]. Swarm’s integration with the Ethereum network allows it to use smart contracts and other blockchain-based features to enhance data management and distribution [41,48]. Despite its moderate scalability, Swarm has a growing community behind it. The platform uses a token-based model (BZZ) to incentivize participants and support its operations, making it a vital component of the Ethereum ecosystem’s decentralized infrastructure [41,48].
3.2. Comparison of Performance Metrics
3.2.1. Speed and Latency
3.2.2. Throughput and Scalability
3.2.3. Data Redundancy and Availability
3.2.4. Resource Efficiency and Network Dependence
3.2.5. Consistency, Reliability, and Security
3.2.6. Cost Efficiency, Complexity, and Ease of Integration
4. Conclusions and Directions for Future Research
4.1. Conclusions
4.2. Directions for Future Research
- Interoperability and Standardization: Future research should focus on developing protocols and standards that facilitate interoperability across decentralized storage solutions. Achieving seamless integration between various platforms will be crucial for fostering a cohesive decentralized storage ecosystem.
- Data Migration and Portability: As the adoption of decentralized storage systems grows, there will be an increasing need for methods and tools that enable seamless data migration across platforms. Ensuring data portability without compromising security, privacy, and performance will be critical for future innovation.
- Security and Privacy Enhancements: Continued development of advanced post-quantum encryption techniques, privacy-preserving algorithms, and robust security mechanisms is essential for maintaining the confidentiality and integrity of data stored in decentralized systems. Research should also explore new approaches such as quantum-resistant algorithms, zero-knowledge proofs, homomorphic encryption, and AI-driven threat detection to mitigate emerging threats in this space.
- Usability and User Experience: Improving the usability and accessibility of decentralized storage platforms is vital for broader adoption. Future work should include user studies and usability testing to refine user interfaces and experiences, making these systems more accessible to technical and non-technical users.
- Environmental Impact and Sustainability: As blockchain-based storage solutions become more widespread, it is essential to assess their environmental impact. Research should explore eco-friendly approaches to reduce energy consumption and carbon emissions, ensuring that these technologies are sustainable in the long term.
- Community and Governance Structures: The decentralized nature of these systems calls for innovative community-driven governance models. Future research should examine decentralized incentives, decision-making mechanisms, and governance structures that promote inclusivity, transparency, and democratic participation within decentralized storage networks.
- Regulatory and Legal Implications: As decentralized storage systems challenge traditional data management paradigms, there is a pressing need to explore the regulatory and legal implications of data sovereignty and privacy in these environments. Future studies should address how these systems can comply with existing regulations while preserving their decentralized nature.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- De Mooy, M. Rethinking Privacy Self-Management and Data Sovereignty in the Age of Big Data: Considerations for Future Policy Regimes in the United States and the European Union; Bertelsmann Stiftung; Springer: Berlin/Heidelberg, Germany, 2017; Available online: https://cdt.org/insights/rethinking-privacy-self-management-and-data-sovereignty-in-the-age-of-big-data/ (accessed on 20 July 2024).
- Hummel, P.; Braun, M.; Tretter, M.; Dabrock, P. Data sovereignty: A review. Big Data Soc. 2021, 8, 1. [Google Scholar] [CrossRef]
- Duisberg, A. Legal Aspects of IDS: Data Sovereignty—What Does It Imply? In Designing Data Spaces; Springer: Cham, Switzerland, 2022; pp. 61–90. [Google Scholar]
- De Filippi, P.; McCarthy, S. Cloud computing: Centralisation and data sovereignty. Eur. J. Law Technol. 2012, 3, 1–18. [Google Scholar]
- Irion, K. Government cloud computing and national data sovereignty. Policy Internet 2012, 4, 40–71. [Google Scholar] [CrossRef]
- Hummel, P.; Braun, M.; Augsberg, S.; Dabrock, P. Sovereignty and data sharing. ITU J. ICT Discov. Spec. Issue 2018, 25, 1–10. [Google Scholar]
- Vaile, D. The cloud and data sovereignty after Snowden. Aust. J. Telecommun. Digit. Econ. 2014, 2, 31–41. [Google Scholar] [CrossRef]
- Sun, Y.; Zhang, J.; Xiong, Y.; Zhu, G. Data Security and Privacy in Cloud Computing. Int. J. Distrib. Sens. Netw. 2014, 10, 190903. [Google Scholar] [CrossRef]
- Yang, P.; Xiong, N.; Ren, J. Data security and privacy protection for cloud storage: A survey. IEEE Access 2020, 8, 131723–131740. [Google Scholar] [CrossRef]
- Pasupulati, R.P.; Shropshire, J. Analysis of centralized and decentralized cloud architectures. In Proceedings of the SoutheastCon 2016, Norfolk, VA, USA, 30 March–3 April 2016; pp. 1–7. [Google Scholar]
- Park, D.B.; Li, X.; Shahhosseini, A.M.; Tsay, L.S. Data ownership in cloud: Legal issues. Int. J. Forensic Eng. Manag. 2021, 1, 125–148. [Google Scholar] [CrossRef]
- Alboaie, S.; Cosovan, D. Private Data System Enabling Self-Sovereign Storage Managed by Executable Choreographies. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Neuchâtel, Switzerland, 2017; Volume 10320, pp. 83–98. [Google Scholar]
- Liang, X.; Shetty, S.; Zhao, J.; Bowden, D.; Li, D.; Liu, J. Towards decentralized accountability and self-sovereignty in healthcare systems. In Proceedings of the 19th International Conference on Information and Communications Security, Beijing, China, 6–8 December 2017; pp. 387–398. [Google Scholar]
- Yan, Z.; Gan, G.; Riad, K. BC-PDS: Protecting Privacy and Self-Sovereignty through BlockChains for OpenPDS. In Proceedings of the IEEE Symposium on Service-Oriented System Engineering (SOSE), San Francisco, CA, USA, 6–9 April 2017; pp. 138–144. [Google Scholar]
- Kim, G.-H. A Design of Self-Sovereign Data Distribution Platform for a Reliable Data Economy. J. Digit. Contents Soc. 2021, 22, 483–490. [Google Scholar] [CrossRef]
- Fallatah, K.U.; Barhamgi, M.; Perera, C. Personal Data Stores (PDS): A Review. Sensors 2023, 23, 1477. [Google Scholar] [CrossRef]
- Abbas, A.E.; van Velzen, T.; Ofe, H.; van de Kaa, G.; de Reuver, M. Beyond control over data: Conceptualizing data sovereignty from a social contract perspective. Electron. Mark. 2024, 34, 20. [Google Scholar] [CrossRef]
- Merlec, M.M.; In, H.P. DataMesh+: A Blockchain-Powered Peer-to-Peer Data Exchange Model for Self-Sovereign Data Marketplaces. Sensors 2024, 24, 1896. [Google Scholar] [CrossRef] [PubMed]
- Sharma, P.; Jindal, R.; Borah, M.D. Blockchain-based decentralized architecture for cloud storage system. J. Inf. Secur. Appl. 2021, 62, 102970. [Google Scholar] [CrossRef]
- Khalid, M.I.; Ehsan, I.; Al-Ani, A.K.; Iqbal, J.; Hussain, S.; Ullah, S.S.; Nayab. Department of Information Technology, The University of Haripur, Haripur, Pakistan. A comprehensive survey on blockchain-based decentralized storage networks. IEEE Access 2023, 11, 10995–11015. [Google Scholar] [CrossRef]
- Zang, H.; Kim, H.; Kim, J. Blockchain-Based Decentralized Storage Design for Data Confidence Over Cloud-Native Edge Infrastructure. IEEE Access 2024, 12, 50083–50099. [Google Scholar] [CrossRef]
- Ali, S.; Wang, G.; White, B.; Cottrell, R.L. A Blockchain-Based Decentralized Data Storage and Access Framework for PingER. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 1303–1308. [Google Scholar]
- Jariwala, M.P.; Obaidat, M.S.; Wazid, M.; Mishra, A.K.; Singh, D.P. Designing Blockchain-Based Decentralized Scheme for Secure File Storage System. In Proceedings of the 2024 International Conference on Computer, Information and Telecommunication Systems (CITS), Girona, Spain, 17–19 July 2024. [Google Scholar]
- Wang, S.; Zhang, Y.; Zhang, Y. A blockchain-based framework for data sharing with fine-grained access control in decentralized storage systems. IEEE Access 2018, 6, 38437–38450. [Google Scholar] [CrossRef]
- Li, G.; Sato, H. A privacy-preserving and fully decentralized storage and sharing system on blockchain. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; Volume 2, pp. 694–699. [Google Scholar]
- Merlec, M.M.; Lee, Y.K.; Hong, S.-P.; In, H.P. A smart contract-based dynamic consent management system for personal data usage under GDPR. Sensors 2021, 21, 7994. [Google Scholar] [CrossRef]
- Albrecht, J.P. How the GDPR will change the world. Eur. Data Prot. Law Rev. 2016, 2, 287. [Google Scholar] [CrossRef]
- Voigt, P.; Von dem Bussche, A. The eu general data protection regulation (gdpr). In A Practical Guide, 1st ed.; Springer International Publishing: Cham, Switzerland, 2017; Volume 10, pp. 10–5555. [Google Scholar]
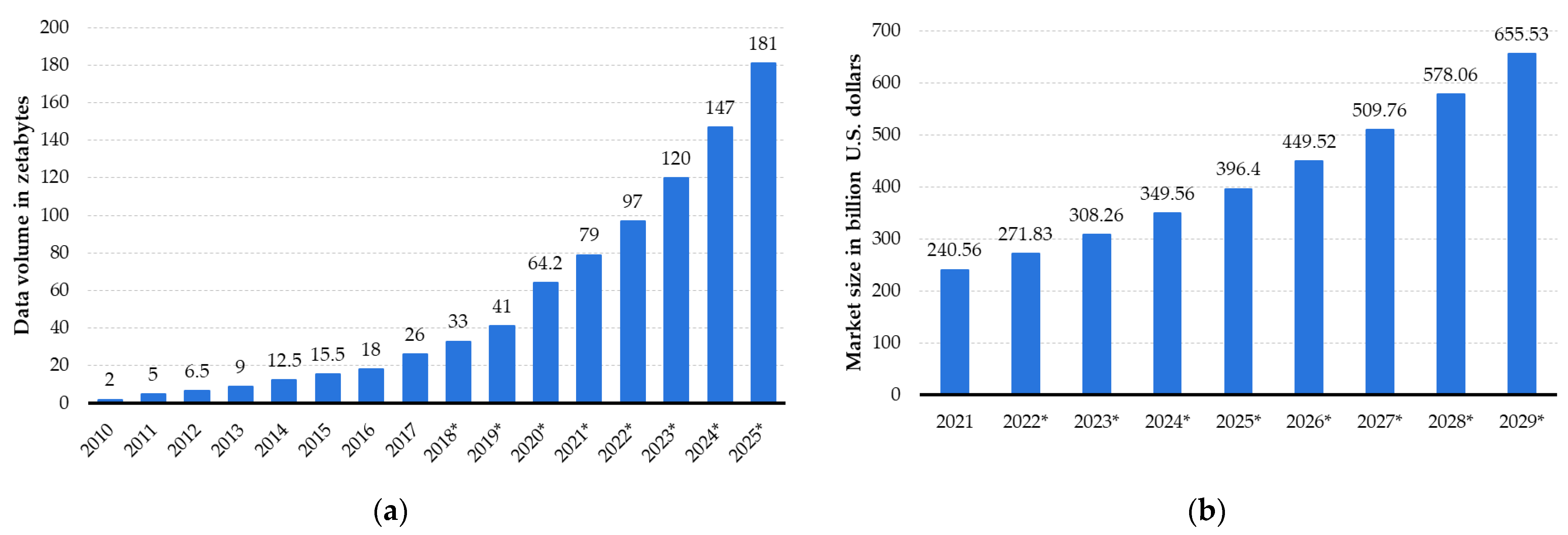
- IDC & Statista. Volume of Data/Information Created, Captured, Copied, and Consumed Worldwide from 2010 to 2020, with Forecasts from 2021 to 2025 (in Zettabytes). Statista, Statista Inc. 7 June 2021. Available online: https://www.statista.com/statistics/871513/worldwide-data-created/ (accessed on 20 July 2024).
- Fortune Business Insights. Size of The Big Data Analytics Market Worldwide from 2021 to 2029 (in Billion U.S. Dollars); Statista ID 1336002; Statista Inc.: New York, NY, USA, 2022. [Google Scholar]
- Daniel, E.; Tschorsch, F. IPFS and friends: A qualitative comparison of next generation peer-to-peer data networks. IEEE Commun. Surv. Tutor. 2022, 24, 31–52. [Google Scholar] [CrossRef]
- Williams, S.; Diordiiev, V.; Berman, L.; Uemlianin, I. Arweave: A Protocol for Economically Sustainable Information Permanence. Arweave Yellow Paper. 2019. Available online: https://arweave.org/yellow-paper.pdf (accessed on 20 January 2024).
- Pouwelse, J.; Garbacki, P.; Epema, D.; Sips, H. The bittorrent p2p file-sharing system: Measurements and analysis. In International Workshop on Peer-to-Peer Systems; Springer: Berlin/Heidelberg, Germany, 2005; pp. 205–216. [Google Scholar]
- Ogden, M.; McKelvey, K.; Madsen, M.B. Dat—Distributed dataset synchronization and versioning. Open Science Framework, 10(2.2). 2017. Available online: http://slides.kevinmarks.com/dat-paper.pdf (accessed on 20 July 2024).
- Protocol Labs. Filecoin: A decentralized storage network. Protocol Labs. July 2017. Available online: https://filecoin.io/filecoin.pdf (accessed on 20 July 2024).
- Hypercore Protocol—Github., Nov. 2023. Available online: https://github.com/hypercore-protocol (accessed on 20 July 2024).
- Benet, J. IPFS—Content addressed versioned P2P file system (DRAFT 3). arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Irvine, D. Maidsafe Distributed File System. 2010. Available online: https://docs.maidsafe.net/Whitepapers/pdf/MaidSafeDistributedFileSystem.pdf (accessed on 20 July 2024).
- Vorick, D.; Champine, L. Sia: Simple Decentralized Storage. 2014. Available online: https://sia.tech/sia.pdf (accessed on 20 July 2024).
- Wilkinson, S.; Boshevski, T.; Brandoff, J.; Prestwich, J.; Hall, G.; Gerbes, P.; Hutchins, P.; Pollard, C. Storj: A Decentralized Cloud Storage Network Framework v3.0. White Paper. 2018. Available online: https://www.storj.io/storjv3.pdf (accessed on 20 July 2024).
- Swarm. SWARM: Storage and Communication Infrastructure for a Self-Sovereign Digital Society. 2021. Available online: https://www.ethswarm.org/swarm-whitepaper.pdf (accessed on 20 July 2024).
- Raval, S. Decentralized Applications: Harnessing Bitcoin’s Blockchain Technology, 1st ed.; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2016. [Google Scholar]
- Pincheira, M.; Donini, E.; Vecchio, M.; Kanhere, S. A Decentralized Architecture for Trusted Dataset Sharing Using Smart Contracts and Distributed Storage. Sensors 2022, 22, 9118. [Google Scholar] [CrossRef] [PubMed]
- Mühle, A.; Grüner, A.; Gayvoronskaya, T.; Meinel, C. A survey on essential components of a self-sovereign identity. Comput. Sci. Rev. 2018, 30, 80–86. [Google Scholar] [CrossRef]
- Schardong, F.; Custódio, R. Self-Sovereign Identity: A Systematic Review, Mapping and Taxonomy. Sensors 2022, 22, 5641. [Google Scholar] [CrossRef]
- Ding, Y.; Sato, H. Self-sovereign identity as a service: Architecture in practice. In Proceedings of the 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC), Los Alamitos, CA, USA, 27 June–1 July 2022; pp. 1536–1543. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System; BN Publishing: La Vergne, TN, USA, 2008. [Google Scholar]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Alzhrani, F.E.; Saeedi, K.A.; Zhao, L. A Taxonomy for Characterizing Blockchain Systems. IEEE Access 2022, 10, 110568–110589. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the Thirteenth EuroSys Conference.,EuroSys ’18; Association for Computing Machinery: New York, NY, USA, 2018; pp. 30:1–30:15. [Google Scholar]
- Valenta, M.; Sandner, P. Comparison of Ethereum, Hyperledger Fabric and Corda; Frankfurt School Blockchain Center: Hessen, Germany, 2017; Volume 8, pp. 1–8. [Google Scholar]
- Brown, R.G.; Carlyle, J.; Grigg, I.; Hearn, M. Corda: An Introduction. Available online: https://www.smallake.kr/wp-content/uploads/2016/10/corda-introductory-whitepaper-final.pdf (accessed on 20 July 2024).
- Benji, M.; Sindhu, M. A study on the Corda and Ripple blockchain platforms. In Advances in Big Data and Cloud Computing; Springer: Berlin/Heidelberg, Germany, 2019; pp. 179–187. [Google Scholar]
- Merlec, M.M.; Islam, M.M.; Lee, Y.K.; In, H.P. A Consortium Blockchain-Based Secure and Trusted Electronic Portfolio Management Scheme. Sensors 2022, 22, 1271. [Google Scholar] [CrossRef]
- Ampel, B.; Patton, M.; Chen, H. Performance modeling of hyperledger sawtooth blockchain. In Proceedings of the 2019 IEEE International Conference on Intelligence and Security Informatics (ISI), Shenzhen, China, 1–3 July 2019; pp. 59–61. [Google Scholar]
- Mazzoni, M.; Corradi, A.; Nicola, V.D. Performance evaluation of permissioned blockchains for financial applications: The ConsenSys Quorum case study. Blockchain Res. Appl. 2021, 3, 100026. [Google Scholar] [CrossRef]
- Lashkari, B.; Musilek, P. A Comprehensive Review of Blockchain Consensus Mechanisms. IEEE Access 2021, 9, 43620–43652. [Google Scholar] [CrossRef]
- Pan, J.; Song, Z.; Hao, W. Development in Consensus Protocols: From PoW to PoS to DPoS. In Proceedings of the 2021 2nd International Conference on Computer Communication and Network Security (CCNS), Xining, China, 30 July–1 August 2021; pp. 59–64. [Google Scholar]
- Islam, M.M.; Merlec, M.M.; In, H.P. A comparative analysis of proof-of-authority consensus algorithms: Aura vs. Clique. In Proceedings of the 2022 IEEE International Conference on Services Computing (SCC), Barcelona, Spain, 10–16 July 2022; pp. 327–332. [Google Scholar]
- Hewa, T.; Ylianttila, M.; Liyanage, M. Survey on blockchain based smart contracts: Applications, opportunities and challenges. J. Netw. Comput. Appl. 2021, 177, 102857. [Google Scholar] [CrossRef]
- Rouhani, S.; Deters, R. Security, performance, and applications of smart contracts: A systematic survey. IEEE Access 2019, 7, 50759–50779. [Google Scholar] [CrossRef]
- Wang, S.; Ding, W.; Li, J.; Yuan, Y.; Ouyang, L.; Wang, F.Y. Decentralized Autonomous Organizations: Concept, Model, and Applications. IEEE Trans. Comput. Soc. Syst. 2019, 6, 870–878. [Google Scholar] [CrossRef]
- Chishti, M.S.; Sufyan, F.; Banerjee, A. Decentralized On-Chain Data Access via Smart Contracts in Ethereum Blockchain. IEEE Trans. Netw. Serv. Manag. 2021, 174–187. [Google Scholar] [CrossRef]
- Assawamekin, N.; Kijsipongse, E. Design and implementation of BitTorrent file system for distributed animation rendering. In Proceedings of the 2013 International Computer Science and Engineering Conference (ICSEC), Nakhonpathom, Thailand, 4–6 September 2013; pp. 68–72. [Google Scholar]
- Zhu, Y.; Lv, C.; Zeng, Z.; Wang, J.; Pei, B. Blockchain-based Decentralized Storage Scheme. J. Phys. Conf. Ser. 2019, 1237, 042008. [Google Scholar] [CrossRef]
- Benisi, N.Z.; Aminian, M.; Javadi, B. Blockchain-based decentralized storage networks: A survey. J. Netw. Comput. Appl. 2020, 102656. [Google Scholar] [CrossRef]
- Bacis, E.; di Vimercati, S.D.C.; Foresti, S.; Paraboschi, S.; Rosa, M.; Samarati, P. Securing Resources in Decentralized Cloud Storage. IEEE Trans. Inf. Forensics Secur. 2020, 15, 286–298. [Google Scholar] [CrossRef]
- Shah, M.; Shaikh, M.; Mishra, V.; Tuscano, G. Decentralized Cloud Storage Using Blockchain. In Proceedings of the 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI) (48184), Tirunelveli, India, 16–18 April 2020; pp. 384–389. [Google Scholar]
- Zhu, Z.; Qi, G.; Zheng, M.; Sun, J.; Chai, Y. Blockchain based consensus checking in decentralized cloud storage. Simul. Model. Pract. Theory 2020, 102, 101987. [Google Scholar] [CrossRef]
- Lambert, N.; Bollen, B. The SAFE Network—A New Decentralised Internet. 2014. Available online: http://docs.maidsafe.net/Whitepapers/pdf/TheSafeNetwork.pdf (accessed on 20 July 2024).
- Irvine, D. MaidSafe Distributed Hash Table. 2010. Available online: https://docs.maidsafe.net/Whitepapers/pdf/MaidSafeDistributedHashTable.pdf (accessed on 20 July 2024).
- Nick, L.; Ma, Q.; Irvine, D. Safecoin: The Decentralised Network Token. Maidsafe Tech. Rep. 2015. Available online: https://docs.maidsafe.net/Whitepapers/pdf/Safecoin.pdf (accessed on 20 July 2024).
- Bush, R.; Choi, S. Forecasting Ethereum STORJ Token Prices: Comparative Analyses of Applied Bitcoin Models. In Proceedings of the 2019 International Conference on Data Mining Workshops (ICDMW), Beijing, China, 8–11 November 2019; pp. 216–223. [Google Scholar]
- Gong, F.; Kong, L.; Lu, Y.; Qian, J.; Min, X. An Overview of Blockchain Scalability for Storage. In Proceedings of the 2023 26th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Rio de Janeiro, Brazil, 24–26 May 2023; pp. 516–521. [Google Scholar] [CrossRef]
- Liu, W.; Huang, H.; Yin, H.; Min, G.; Yuan, Y.; Wu, D. Scalable Blockchain-Based Data Storage in Internet of Things. IEEE Commun. Mag. 2024, 62, 40–45. [Google Scholar] [CrossRef]
- Pinheiro, E.; Bianchini, R.; Dubnicki, C. Exploiting redundancy to conserve energy in storage systems. In Proceedings of the Joint Intl. Conference on Measurement and Modeling of Computer Systems, New York, NY, USA, 15–26 June 2006. [Google Scholar]
- Brinkmann, A.; Effert, S. Redundant data placement strategies for cluster storage environments. In International Conference On Principles of Distributed Systems; Springer: Berlin/Heidelberg, Germany, 2008; pp. 551–554. [Google Scholar]
- Kermarrec, A.-M.; Le Merrer, E.; Straub, G.; van Kempen, A. Availability-Based Methods for Distributed Storage Systems. In Proceedings of the 2012 IEEE 31st Symposium on Reliable Distributed Systems, Irvine, CA, USA, 8–11 October 2012; pp. 151–160. [Google Scholar]
- Povyshev, A.A.; Sokolov, A.N. Ensuring the Integrity and Availability of Information in the Model of Decentralized Data Storage System. In Proceedings of the 2024 International Russian Smart Industry Conference (SmartIndustryCon), Sochi, Russia, 25–29 March 2024; pp. 517–521. [Google Scholar]
- Ismail, A.; Toohey, M.; Lee, Y.C.; Dong, Z.; Zomaya, A.Y. Cost and Performance Analysis on Decentralized File Systems for Blockchain-Based Applications: State-of-the-Art Report. In Proceedings of the 2022 IEEE International Conference on Blockchain (Blockchain), Espoo, Finland, 22–25 August 2022; pp. 230–237. [Google Scholar]
- Shah, S.C. An Energy-Efficient Resource Management System for a Mobile Ad Hoc Cloud. IEEE Access 2018, 6, 62898–62914. [Google Scholar] [CrossRef]
- Li, J.; Wu, J.; Chen, L.; Li, J. Blockchain-based secure and reliable distributed deduplication scheme. In Proceedings of the Algorithms and Architectures for Parallel Processing: 18th International Conference, ICA3PP 2018, Guangzhou, China, 15–17 November 2018; Proceedings, Part I 18. Springer: Cham, Switzerland; Newark, NJ, USA, 2018; pp. 393–405. [Google Scholar]
- Schweiger, P. Improving Usability of Blockchain-Based Decentralized Applications. Master’s Thesis, University of Applied Sciences Technikum Wien, Wien, Austria, 2021. [Google Scholar]

| Public Blockchain | Private Blockchain | Consortium Blockchain | |
|---|---|---|---|
| Network Topology | 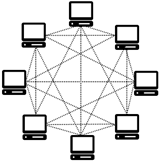 | 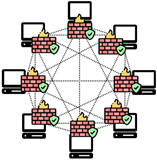 | 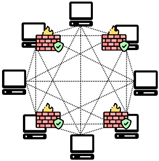 |
| Key Features |
|
|
|
| Advantages | + Independence + Decentralization + Transparency + Trust | + Access control | + Access control |
| + Performance | + Performance | ||
| + Scalability | + Scalability | ||
| + Privacy | + Privacy | ||
| Drawbacks | - Performance and scalability - Security at high cost - Resource consumption - Transaction cost | - Trust and transparency (limited) - No public auditability - (Centralized) governance | - Transparency (limited) - High complexity |
| Platform | Underlying Technology | Use Case | Security Features | Privacy | Blockchain Utilization | Payment Model | Data Control | Versioning Support | Community/Adoption |
|---|---|---|---|---|---|---|---|---|---|
| Arweave [32] | Blockweave | Permanent data storage | Encryption, permanence | High | Yes | Cryptocurrency (AR tokens) | User | No | Growing |
| BitTorrent [33] | P2P file sharing | File sharing | Basic (depends on file source) | Moderate | No | Free (Ad-supported) | User | No | Very Wide |
| Dat [34] | P2P data sharing | Scientific data sharing | Encryption, version control | High | No | Free (Open-source) | User | Yes | Niche |
| Filecoin [35] | Blockchain | Decentralized storage | Encryption, file contracts | High | Yes | Cryptocurrency (Filecoin) | User | No | Growing |
| Hypercore Protocol [36] | Distributed ledger | Secure, real-time data sharing | Encryption, real-time updates | High | No | Free (Open-source) | User | Yes | Emerging |
| IPFS [37] | P2P network | Decentralized file sharing | Content addressing, file identifiers | Moderate | No | Free (Open-source) | User | Yes | Wide |
| MaidSafe [38] | Decentralized network | Secure data management | Encryption, secure network | High | No | Free (Open-source) | User | Yes | Established |
| Sia [39] | Blockchain | Decentralized storage | File splitting, encryption | High | Yes | Cryptocurrency (Siacoin) | User | Yes | Niche |
| Storj [40] | Decentralized cloud storage | Decentralized storage | Encryption, sharding | High | No | Cryptocurrency (STORJ token) | User | Yes | Wide |
| Swarm [41] | Ethereum Web3 stack | Decentralized record storage | Encryption, redundancy | High | Yes | Token-based (BZZ) | User | Yes | Emerging |
| Platform | Speed (Upload/Download) | Latency | Throughput | Data Redundancy | Security | Scalability | User Interface | Data Reliability | Cost Efficiency |
|---|---|---|---|---|---|---|---|---|---|
| Arweave [32] | Moderate | Moderate | High | Very High | High | High | Moderate | Very High | Moderate |
| BitTorrent [33] | High (for popular files) | Low | High | High | Moderate | High (for popular files) | Easy | High | High |
| Dat Protocol [34] | Moderate | Moderate | Moderate | High | High | Moderate | Moderate | High | High |
| Filecoin [35] | High | Low | High | High | High | High | Moderate | High | Variable |
| Hypercore Protocol [36] | High | Low | High | High | High | High | Moderate | High | High |
| IPFS [37] | Moderate | Moderate | High | High | High | High | Moderate | High | High |
| MaidSafe [38] | Moderate | Moderate | Moderate | High | High | Moderate | Moderate | High | High |
| Sia [39] | High | Moderate | High | High | High | Moderate | Moderate | High | Variable |
| Storj [40] | High | Low | High | High | High | High | Moderate | High | Variable |
| Swarm [41] | Moderate | Moderate | Moderate | High | High | Moderate | Moderate | High | Variable |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Merlec, M.M.; In, H.P. Blockchain-Based Decentralized Storage Systems for Sustainable Data Self-Sovereignty: A Comparative Study. Sustainability 2024, 16, 7671. https://doi.org/10.3390/su16177671
Merlec MM, In HP. Blockchain-Based Decentralized Storage Systems for Sustainable Data Self-Sovereignty: A Comparative Study. Sustainability. 2024; 16(17):7671. https://doi.org/10.3390/su16177671
Chicago/Turabian StyleMerlec, Mpyana Mwamba, and Hoh Peter In. 2024. "Blockchain-Based Decentralized Storage Systems for Sustainable Data Self-Sovereignty: A Comparative Study" Sustainability 16, no. 17: 7671. https://doi.org/10.3390/su16177671
APA StyleMerlec, M. M., & In, H. P. (2024). Blockchain-Based Decentralized Storage Systems for Sustainable Data Self-Sovereignty: A Comparative Study. Sustainability, 16(17), 7671. https://doi.org/10.3390/su16177671


_Lu.png)




