Multi-Source T-S Target Recognition via an Intuitionistic Fuzzy Method
Abstract
:1. Introduction
1.1. Literature Review and Motivation
1.2. Our Contributions
- Improving the robustness of the training process of the model: the features of the aerial targets are classified as inputs to the corresponding T-S target recognition model, so that features are divided into multi-level features with the target properties;
- In the T-S model algorithm, the study of premise and consequence parameter identification has been the key question. We apply an intuitionistic fuzzy C-means method based on the dynamic particle swarm optimization (DPSO) algorithm and the ridge regression model to identify the premise and consequence parameter of the T-S intuitionistic fuzzy model, respectively, which better realizes the parametric identification of the model;
- High classification accuracy can be guaranteed in error-free and error-prone environments. The adaptive weight algorithm reduces the weight corresponding to the model with a low degree of discrimination and increases the weight corresponding to the model with a high degree of discrimination, which is better distinguished from the input features.
1.3. Organization of the Article
2. Preliminaries
2.1. Evidence Theory
2.2. Takagi–Sugeno Intuitionistic Fuzzy Rules Method
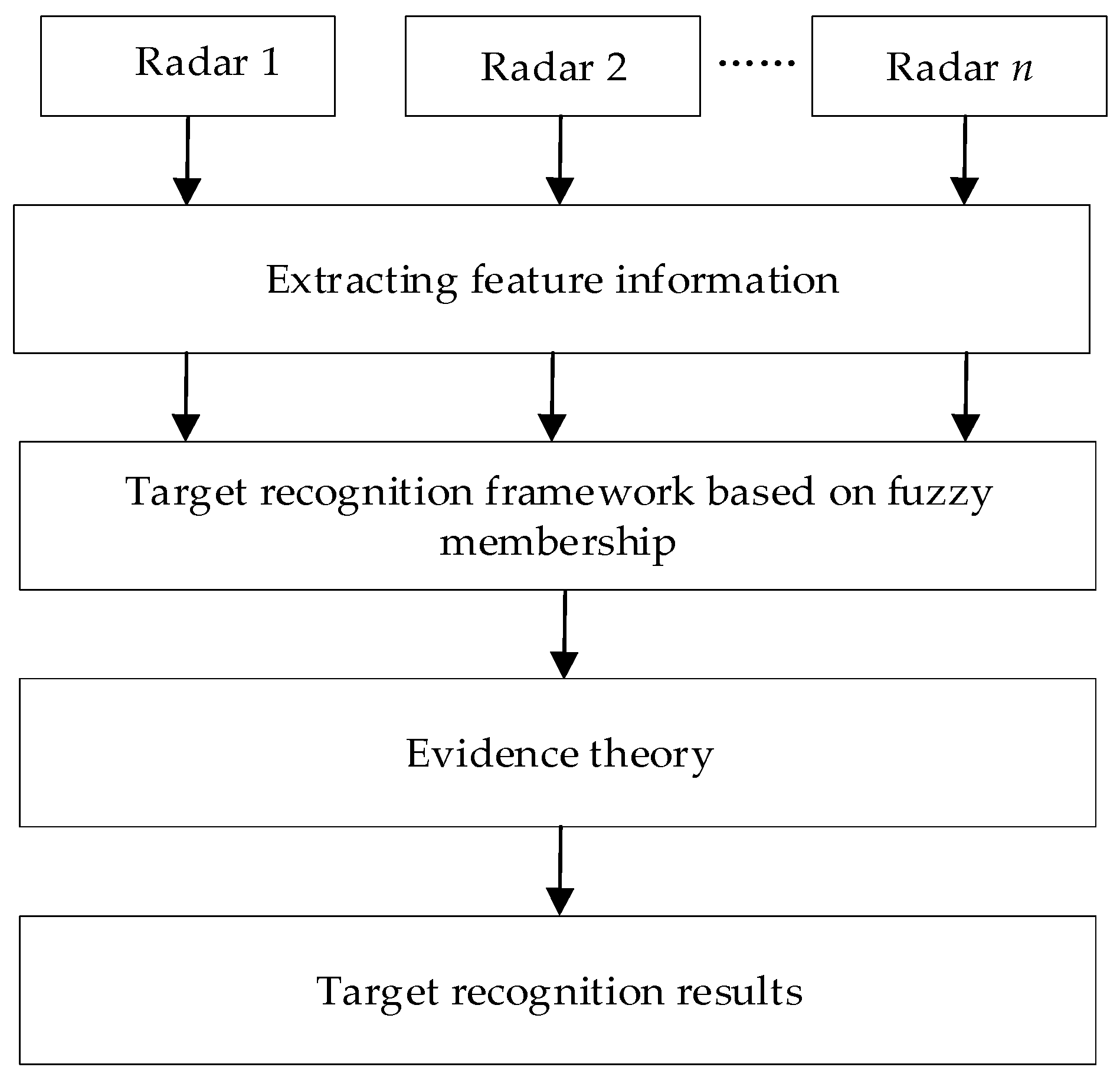
3. Aerial Target Recognition Methods Based on the MTS-IFRM
3.1. Construction of MTS-IFRM
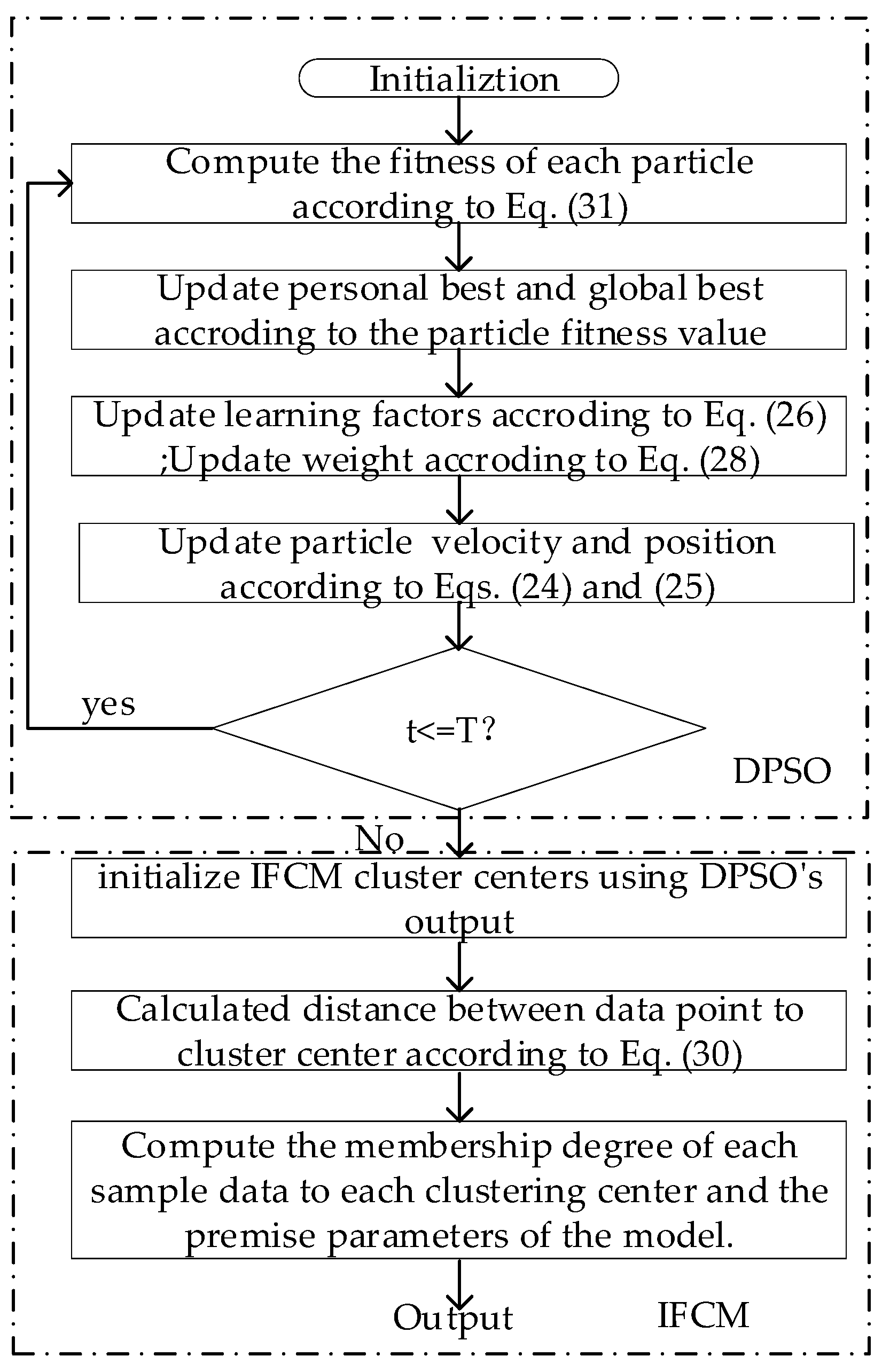
3.2. Premise Identification
- Initialization: Initialize G particles to form G first-generation particles, where each particle randomly generates M clustering centers. The fitness value is calculated by Equation (31) and determines the current optimal position of each particle by the fitness value, and the position of the current particle swarm with the highest fitness is ;
- Compute the velocity and position of each particle in the new particle swarm using Equations (24) and (25);
- Compute the fitness value of each particle in the new particle swarm using Equation (31) and compare it with the previous generation. For the same individual, if the individual fitness in the new population is larger than the corresponding individual in the previous generation, replace the individual of the previous generation and this becomes the optimal position of particle , otherwise, it remains unchanged;
- Compare the fitness value of the optimal individual of the new particle swarm with the optimal individual of the previous generation, if the fitness is greater than the previous generation, update the optimal position of the population to the optimal position of the new particle swarm, otherwise, it remains unchanged, then .
- Repeat Steps 2–4 until a criterion is met that is usually of a sufficiently good fitness or a maximum number of iterations;
- Obtain the individual position with the highest fitness value as the initial clustering center of the IFCM algorithm;
- Compute the membership degree of each sample dataset to each clustering center and the premise parameters of the model. A detailed method can be found in Ref. [36].
3.3. Adaptive Weight Algorithm
- 1.
- For a certain secondary feature, in the output result of the corresponding model, if all the values in the output vector are less than 0.5, the possibility of the feature belonging to the target being classified is too low. Therefore, the secondary feature should be reduced according to the impact of the secondary features on the classification results, the weight corresponding to the secondary features is reduced and assigned to other features. Suppose that the maximum value of the label vector output by the model is , the weight of the corresponding model can be expressed as:
- 2.
- For a certain secondary feature to the corresponding T-S IFM output, if the maximum value in the label vector is greater than 0.5, and the difference between the maximum value and the second large value is less than 0.3, then the classification ability of the secondary features for all of the targets to be classified is weak. However, because the maximum value in the label vector is greater than 0.5, the feature has a certain classification ability for a certain type or several types of targets, but it cannot determine which type the input feature data belongs to. Therefore, the corresponding weight can be appropriately reduced and assigned to other features.
3.4. Computational Complexity Analysis
4. Simulation Results and Analysis
4.1. Example 1: The Data Does Not Contain Fault Features
4.2. Example 2: The Data Contains Fault Features
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Zhao, K.; Sun, R.; Li, L. An improved evidence fusion algorithm in multi-sensor systems. Appl. Intell. 2021, 51, 7614–7624. [Google Scholar] [CrossRef]
- Chen, A.; Tang, X.; Cheng, B.C. Multi-source monitoring information fusion method for dam health diagnosis based on Wasserstein distance. Inform. Sci. 2023, 632, 378–389. [Google Scholar] [CrossRef]
- Liang, Q.; Liu, Z.; Chen, Z. A networked method for multi-evidence-based information fusion. Entropy 2022, 25, 69. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.C.; Wang, J.; Huang, M.J. An evidence combination rule based on a new weight assignment scheme. Soft Comput. 2022, 26, 7123–7137. [Google Scholar] [CrossRef]
- Meng, L.Y.; Li, L.Q. Time-sequential hesitant fuzzy set and its application to multi-attribute decision making. Complex Intell. Syst. 2022, 8, 4319–4338. [Google Scholar] [CrossRef]
- Meng, L.Y.; Li, L.Q.; Xie, W.X. Time-sequential hesitant fuzzy entropy, cross-entropy and correlation coefficient and their application to decision making. Eng. Appl. Artif. Intell. 2023, 123, 106455. [Google Scholar] [CrossRef]
- Jiang, H.; Hu, B.Q. A decision-theoretic fuzzy rough set in hesitant fuzzy information systems and its application in multi-attribute decision-making. Inform. Sci. 2021, 579, 103–127. [Google Scholar] [CrossRef]
- Kaur, M.; Srivastava, A. A new divergence measure for belief functions and its applications. Int. J. Gen. Syst. 2023, 52, 455–472. [Google Scholar] [CrossRef]
- Hu, Z.; Su, Y.; Hou, W. Multi-sensor data fusion method based on divergence measure and probability transformation belief factor. Appl. Soft Comput. 2023, 145, 110603. [Google Scholar] [CrossRef]
- Lv, Y.W.; Yang, G.H. Centralized and distributed adaptive cubature information filters for multi-sensor systems with unknown probability of measurement loss. Inform. Sci. 2023, 630, 173–189. [Google Scholar] [CrossRef]
- Wang, W.; Zhang, Y. A method based on grey theory toward the multi-sensor information fusion of human centered robots. In Proceedings of the 12th International Convention on Rehabilitation Engineering and Assistive Technology, 13 July 2018; pp. 293–296. [Google Scholar]
- Akshaya, T.G.; Sreeja, S. Multi-sensor data fusion for aerodynamically controlled vehicle based on FGPM. IFAC—PapersOnLine 2020, 53, 591–596. [Google Scholar]
- Fu, C.; Qin, K.; Yang, L. Hesitant fuzzy β-covering (T, I) rough set models: An application to multi-attribute decision-making. J. Intell. Fuzzy Syst. 2023. preprint. [Google Scholar] [CrossRef]
- Zhang, L.; Zhan, J.; Xu, Z. Covering-based generalized IF rough sets with applications to multi-attribute decision-making. Inform. Sci. 2019, 478, 275–302. [Google Scholar] [CrossRef]
- Zhang, L.; Zhu, P. Asymmetric models of intuitionistic fuzzy rough sets and their applications in decision-making. Int. J. Mach. Learn. Cyb. 2023, 14, 3353–3380. [Google Scholar] [CrossRef]
- Zhou, Z.; Zhao, C.; Cai, X. Three-dimensional modeling and analysis of fractal characteristics of rupture source combined acoustic emission and fractal theory. Chaos Soliton. Fract. 2022, 160, 112308. [Google Scholar] [CrossRef]
- Lai, Y.; Zhao, K.; He, Z. Fractal characteristics of rocks and mesoscopic fractures at different loading rates. Geomech. Energy Environ. 2023, 33, 100431. [Google Scholar] [CrossRef]
- Wang, H.; Liu, S.V.; Qu, X. Field investigations on rock fragmentation under deep water through fractal theory. Measurement 2022, 199, 111521. [Google Scholar] [CrossRef]
- Dempster, A.P. Upper and lower probabilities induced by a multivalued mapping. In Classic Works of the Dempster-Shafer Theory of Belief Functions; Springer: Berlin/Heidelberg, Germany, 2008; pp. 57–72. [Google Scholar]
- Chen, L.; Deng, Y. A new failure mode and effects analysis model using Dempster–Shafer evidence theory and grey relational projection method. Eng. Appl. Artif. Intell. 2018, 76, 13–20. [Google Scholar] [CrossRef]
- He, Y.; Guo, H.; Li, X. A Collaborative Relay Tracking Method Based on Information Fusion for UAVs. IEEE Trans. Aerosp. Electron. Syst. 2023, 59, 6894–6906. [Google Scholar] [CrossRef]
- Xiao, F. GEJS: A generalized evidential divergence measure for multisource information fusion. IEEE Trans. Syst. Man Cybern. Syst. 2022, 53, 2246–2258. [Google Scholar] [CrossRef]
- Sezer, S.I.; Akyuz, E.; Arslan, O. An extended HEART Dempster–Shafer evidence theory approach to assess human reliability for the gas freeing process on chemical tankers. Reliab. Eng. Syst. Safe 2022, 220, 108275. [Google Scholar] [CrossRef]
- Pan, Y.; Zhang, L.; Li, Z.W. Improved fuzzy Bayesian network-based risk analysis with interval-valued fuzzy sets and D–S evidence theory. IEEE Trans. Fuzzy Syst. 2019, 28, 2063–2077. [Google Scholar] [CrossRef]
- Zhu, C.; Xiao, F. A belief Rényi divergence for multi-source information fusion and its application in pattern recognition. Appl. Intell. 2023, 53, 8941–8958. [Google Scholar] [CrossRef]
- Yin, L.; Deng, X.; Deng, Y. The negation of a basic probability assignment. IEEE Trans. Fuzzy Syst. 2018, 27, 135–143. [Google Scholar] [CrossRef]
- Jiang, W. A correlation coefficient for belief functions. Int. J. Approx. Reason. 2018, 103, 94–106. [Google Scholar] [CrossRef]
- Wang, H.; Deng, X.; Jiang, W. A new belief divergence measure for Dempster–Shafer theory based on belief and plausibility function and its application in multi-source data fusion. Appl. Artif. Intell. 2021, 97, 104030. [Google Scholar] [CrossRef]
- Yager, R.R. On the Dempster-Shafer framework and new combination rules. Inform. Sci. 1987, 41, 93–137. [Google Scholar] [CrossRef]
- Murphy, C.K. Combining belief functions when evidence conflicts. Decis. Support Syst. 2000, 29, 1–9. [Google Scholar] [CrossRef]
- Li, X.; Zhao, Y.; Fan, C. Multi-sensor Data Fusion Algorithm Based on Dempster-Shafer Theory. In Proceedings of the 7th International Conference on Computer and Communications (ICCC), Chengdu, China, 10–13 December 2021; pp. 288–293. [Google Scholar]
- Wang, L.; Yang, H.Y.; Zhang, S.W. Intuitionistic Fuzzy Dynamic Bayesian Network and its application to terminating situation assessment. Procedia Comput. Sci. 2019, 154, 238–248. [Google Scholar] [CrossRef]
- Guo, L.; Yang, R.; Zhong, Z. Target recognition method of small UAV remote sensing image based on fuzzy clustering. Neural Comput. Appl. 2022, 34, 12299–12315. [Google Scholar] [CrossRef]
- Lei, Y.; Kong, W. Technique for target recognition based on intuitionistic fuzzy reasoning. IET Signal Process. 2012, 6, 255–263. [Google Scholar] [CrossRef]
- Dolgiy, A.I.; Kovalev, S.M.; Kolodenkova, A.E. Processing heterogeneous diagnostic information on the basis of a hybrid neural model of Dempster-Shafer. In Proceedings of the Artificial Intelligence: 16th Russian Conference, RCAI 2018, Moscow, Russia, 24–27 September 2018; Proceedings 16. pp. 79–90. [Google Scholar]
- Zhang, C.Y.; Li, L.Q.; Huang, S. Multiple target data-association algorithm based on Takagi-Sugeno intuitionistic fuzzy model. Neurocomputing 2023, 536, 114–124. [Google Scholar] [CrossRef]
- Chen, S.M.; Liu, A.Y. Multiattribute decision making based on nonlinear programming methodology, novel score function of interval-valued intuitionistic fuzzy values, and the standard deviations of the score values in the score matrix. Inform. Sci. 2023, 607, 119381. [Google Scholar] [CrossRef]
- Dhanachandra, N.; Chanu, Y.J. An image segmentation approach based on fuzzy c-means and dynamic particle swarm optimization algorithm. Multimed. Tools Appl. 2020, 79, 18839–18858. [Google Scholar] [CrossRef]



| Notation | Meaning of the Notation | Notation | Meaning of the Notation |
|---|---|---|---|
| Discriminative frame | Scoring function set | ||
| Fuzzy rule l | Number of training samples | ||
| Inputs of CA | Position, velocity, optimal solution of the i-th particle | ||
| Universe of discourses of CA | G | Size of particle swarm | |
| Intuitionistic fuzzy subsets | Current global optimal solution | ||
| Consequent parameter | Minimum, maximum inertia weights | ||
| Membership, non-membership degree | Learning parameter | ||
| Intuitionistic index | T | Number of iterations | |
| Number of fuzzy rules | M | Number of label vector dimensions | |
| Outputs for the model | ,, | Minimum, maximum, and average fitness of the particle swarm |
| Br | Fr | Hr | AGM | TBM | |
|---|---|---|---|---|---|
| Flight height (km) | 25–35 | 7–13 | 1.6–2.5 | 3.8–5.2 | 55–80 |
| Detection distance (km) | 350–450 | 250–350 | 130–180 | 100–140 | 130–180 |
| Flight speed (m/s) | 300–500 | 500–700 | 70–130 | 1000–1500 | 1700–2300 |
| Acceleration (m/s2) | 0–20 | 0–50 | 0–30 | 150–250 | 200–400 |
| Vertical speed (m/s) | 0–50 | 0–300 | 0–50 | 800–1200 | 1600–2300 |
| Cross-section area (m2) | 0.25–0.35 | 0.17–0.23 | 0.08–0.12 | 0.05–0.08 | 0.06–0.11 |
| Aspect ratio | 1.2–2.0 | 2.6–3.6 | 3.2–4.8 | 6.7–9.3 | 8.5–11.5 |
| Serial Number | FH (km) | DD (km) | FS (m/s) | A (m/s2) | VS (m/s) | CA (m2) | AR | Target |
|---|---|---|---|---|---|---|---|---|
| 1 | 58.6 | 135.6 | 1845.5 | 210.4 | 1685.6 | 0.08 | 9.5 | TBM |
| 2 | 4.2 | 125.8 | 1250.7 | 211.9 | 952.2 | 0.06 | 8.4 | AGMM |
| 3 | 8.3 | 344 | 612.3 | 42.6 | 258.4 | 0.22 | 2.7 | Fr |
| 4 | 4.5 | 132.8 | 1252.1 | 158.7 | 958.8 | 0.06 | 6.9 | AGM |
| 5 | 31.6 | 377.4 | 315.3 | 14.6 | 25.3 | 0.31 | 1.6 | Br |
| 6 | 1.7 | 136.6 | 88.6 | 11.3 | 29.3 | 0.09 | 3.8 | Hr |
| 7 | 56.6 | 179.1 | 2200.6 | 365.6 | 1936.7 | 0.10 | 11.5 | TBM |
| Br | Fr | Hr | AGM | TBM | |
|---|---|---|---|---|---|
| FH (km) | (30,7.5) | (10,4.5) | (2,1) | (4.5,1) | (65,15) |
| DD (km) | (400,80) | (300,80) | (200,60) | (120,45) | (150,60) |
| FS (m/s) | (400,150) | (600,150) | (100,50) | (1200,500) | (2000, 500) |
| A(m/s2) | (10,10) | (25,25) | (15,15) | (200,60) | (300,100) |
| VS(m/s) | (25,25) | (150,150) | (25,25) | (1000,300) | (1950,600) |
| CA (m2) | (0.3,0.08) | (0.2,0.06) | (0.1,0.03) | (0.06,0.02) | (0.08,0.03) |
| AR | (1.5,0.5) | (3,0.6) | (4,0.8) | (8,1.3) | (10,1.5) |
| Evidence | Br | Fr | Hr | AGM | TBM | X |
|---|---|---|---|---|---|---|
| 0.4185 | 2.37 × 10−4 | 0 | 0 | 3.93 × 10−4 | 0.5809 | |
| 0.6766 | 0.0297 | 2.88 × 10−4 | 0 | 0 | 0.2936 | |
| 0.8837 | 0.0297 | 0 | 0.0549 | 1.84 × 10−5 | 0 | |
| 0.3857 | 0.0614 | 0.3451 | 1.70 × 10−5 | 8.59 × 10−5 | 0 | |
| 0.3525 | 0.2691 | 0.3525 | 1.80 × 10−5 | 2.01 × 10−5 | 0 | |
| 0.9660 | 0.0340 | 0 | 0 | 0 | 0 | |
| 0.3679 | 1.49 × 10−5 | 7.81 × 10−5 | 0 | 0 | 0.6321 |
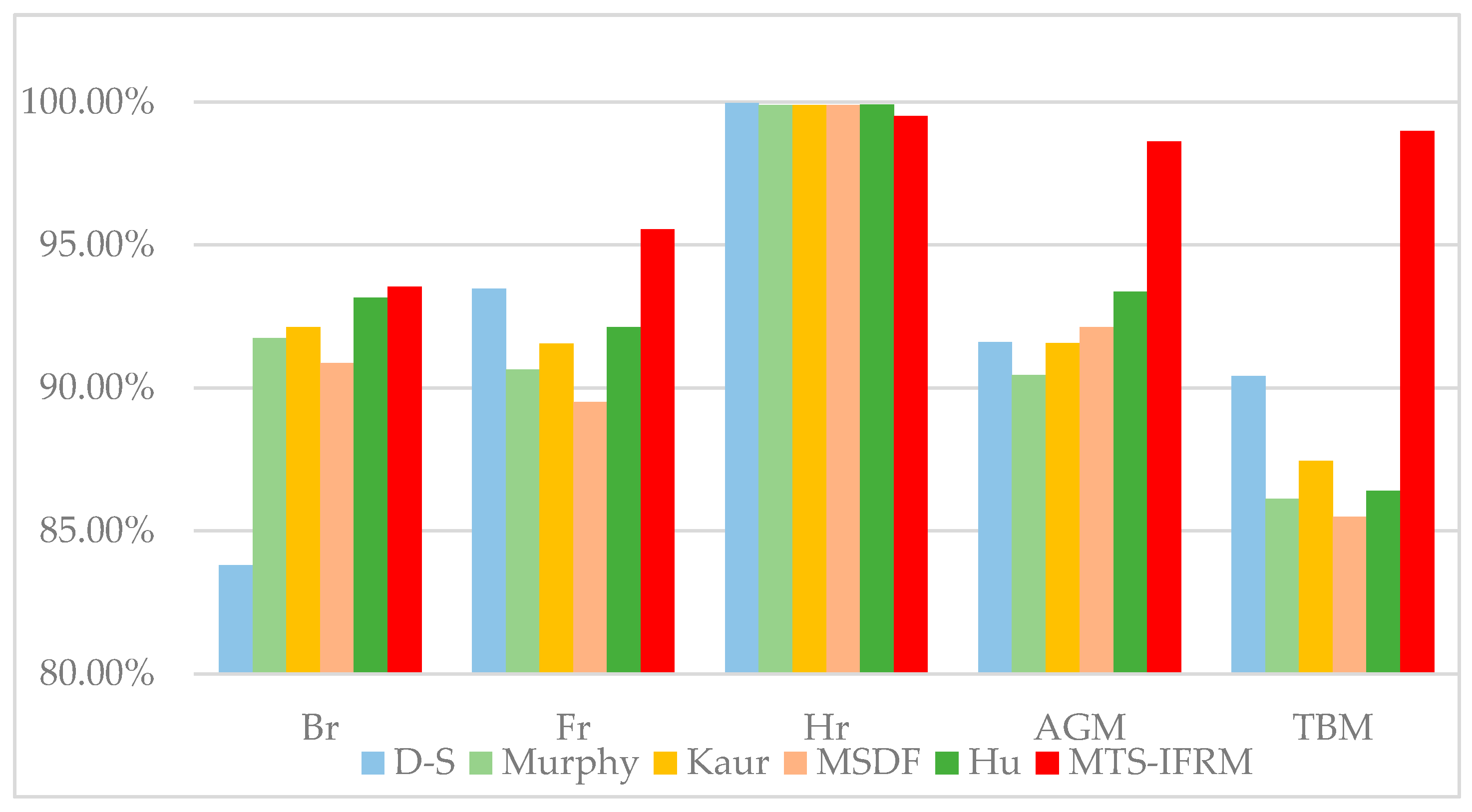
| Method | m(Br) | m(Fr) | m(Hr) | m(AGM) | m(TBM) | m(X) | Target |
|---|---|---|---|---|---|---|---|
| D-S | 0.8095 | 0.0176 | 0 | 0 | 0 | 0.1728 | Br |
| Yager | 0.2832 | 0 | 0 | 0 | 0 | 0.7168 | X |
| Murphy | 0.7905 | 0.0705 | 0.0715 | 0.0047 | 0 | 0.0627 | Br |
| MSDF | 0.7946 | 0.0692 | 0.0694 | 0.0047 | 0 | 0.0621 | Br |
| Kaur | 0.8056 | 0.0862 | 0.0891 | 0.0056 | 0 | 0.0135 | Br |
| Hu | 0.8134 | 0.0923 | 0.0451 | 0.0026 | 0 | 0.0466 | Br |
| MTS-IFRM | 0.9894 | 0.0064 | 0.0042 | 0 | 0 | 0 | Br |
| Method | m(Br) | m(Fr) | m(Hr) | m(AGM) | m(TBM) | m(X) | Target |
|---|---|---|---|---|---|---|---|
| D-S | 0.9610 | 0.0390 | 0 | 0 | 0 | 0 | Br |
| Yager | 0.1201 | 0.0049 | 0 | 0 | 0 | 0.8750 | X |
| Murphy | 0.9020 | 0.0385 | 0.0391 | 0.0021 | 0 | 0.0183 | Br |
| MSDF | 0.9050 | 0.0374 | 0.0375 | 0.0021 | 0 | 0.0180 | Br |
| Kaur | 0.9156 | 0.0395 | 0.0357 | 0.0035 | 0 | 0.0057 | Br |
| Hu | 0.9265 | 0.0402 | 0.0315 | 0.0018 | 0 | 0 | Br |
| MTS-IFRM | 0.9342 | 0.0187 | 0.0472 | 0 | 0 | 0 | Br |
| Method | m(Br) | m(Fr) | m(Hr) | m(AGM) | m(TBM) | m(X) | Target |
|---|---|---|---|---|---|---|---|
| D-S | 0.9782 | 0.0218 | 0 | 0 | 0 | 0 | Br |
| Yager | 0.3554 | 0 | 0 | 0 | 0 | 0.6446 | X |
| Murphy | 0.7905 | 0.0705 | 0.0715 | 0.0047 | 0 | 0.0627 | Br |
| MSDF | 0.7946 | 0.0692 | 0.0694 | 0.0047 | 0 | 0.0621 | Br |
| Kaur | 0.8165 | 0.0712 | 0.0718 | 0.0056 | 0 | 0.0349 | Br |
| Hu | 0.8564 | 0.0522 | 0.0559 | 0.0062 | 0 | 0.0293 | Br |
| MTS-IFRM | 0.9790 | 0.0210 | 0 | 0 | 0 | 0 | Br |
| Method | m(Br) | m(Fr) | m(Hr) | m(AGM) | m(TBM) | m(X) | Target |
|---|---|---|---|---|---|---|---|
| D-S | 0.9998 | 1.75 × 10−4 | 0 | 0 | 0 | 0 | Br |
| Yager | 0.0121 | 0 | 0 | 0 | 0 | 0.9879 | X |
| Murphy | 0.9970 | 0.0014 | 0.0014 | 0 | 0 | 0 | Br |
| MSDF | 0.9973 | 0.0013 | 0.0013 | 0 | 0 | 0 | Br |
| Kaur | 0.9981 | 0.0010 | 9 × 10−4 | 0 | 0 | 0 | Br |
| Hu | 0.9985 | 0.0008 | 0.0011 | 0 | 0 | 0 | Br |
| MTS-IFRM | 0.9813 | 0.0015 | 0.0172 | 0 | 0 | 0 | Br |
| Method | m(Br) | m(Fr) | m(Hr) | m(AGM) | m(TBM) | m(X) | Target |
|---|---|---|---|---|---|---|---|
| D-S | 0 | 1 | 0 | 0 | 0 | 0 | Fr |
| Yager | 0 | 0.0012 | 0 | 0 | 0 | 0.9988 | X |
| Murphy | 0.7060 | 0.0631 | 0.2003 | 0.0035 | 0 | 0.0270 | Br |
| MSDF | 0.7746 | 0.0702 | 0.1257 | 0.0037 | 0 | 0.0258 | Br |
| Kaur | 0.7945 | 0.0642 | 0.1254 | 0.0034 | 0 | 0.0125 | Br |
| Hu | 0.8563 | 0.0281 | 0.1043 | 0.0021 | 0 | 0.0092 | Br |
| MTS-IFRM | 0.9639 | 0.0345 | 1.23 × 10−4 | 0 | 0 | 0 | Br |
| Method | m(Br) | m(Fr) | m(Hr) | m(AGM) | m(TBM) | m(X) | Target |
|---|---|---|---|---|---|---|---|
| D-S | 0 | 1 | 0 | 0 | 0 | 0 | Fr |
| Yager | 0 | 0 | 0 | 0 | 0 | 1 | X |
| Murphy | 0.9830 | 6.31 × 10−4 | 0.0163 | 0 | 0 | 0 | Br |
| MSDF | 0.9965 | 5.89 × 10−4 | 0.0029 | 0 | 0 | 0 | Br |
| Kaur | 0.9905 | 0.0084 | 0.0011 | 0 | 0 | 0 | Br |
| Hu | 0.9942 | 0.0049 | 0.0009 | 0 | 0 | 0 | Br |
| MTS-IFRM | 0.9811 | 0.0184 | 0.0019 | 0 | 0 | 0 | Br |
| Br|δ | Fr|δ | Hr|δ | AGM|δ | TBM|δ | |
|---|---|---|---|---|---|
| FH (km) | 30|15 | 10|5 | 2|1 | 4.5|2 | 70|30 |
| DD (km) | 400|200 | 300|150 | 150|75 | 120|60 | 150|75 |
| FS (m/s) | 400|200 | 600|300 | 100|50 | 1200|600 | 2000|1000 |
| A(m/s2) | 10|10 | 25|25 | 15|15 | 200|100 | 300|150 |
| VS(m/s) | 25|25 | 100|100 | 20|20 | 1000|500 | 2000|1000 |
| CA (m2) | 0.30|0.15 | 0.20|0.1 | 0.10|0.05 | 0.05|0.02 | 0.10|0.05 |
| AR | 1.5|0.75 | 2.5|1.0 | 4.0|2.0 | 8.0|4.0 | 10.0|5.0 |
| D-S | a(Br) = 0.4970 | a(Br) = 0.6085 | a(Br) = 0.7044 | a(Br) = 0.8381 |
| a(Fr) = 0.6394 | a(Fr) = 0.8698 | a(Fr) = 0.3802 | a(Fr) = 0.9347 | |
| a(Hr) = 0.6663 | a(Hr) = 0.9133 | a(Hr) = 0.5227 | a(Hr) = 0.9997 | |
| a(AGM) = 0.6102 | a(AGM) = 0.8389 | a(AGM) = 0.4165 | a(AGM) = 0.9160 | |
| a(TBM) = 0.4207 | a(TBM) = 0.7138 | a(TBM) = 0.2678 | a(TBM) = 0.9041 | |
| Murphy | a(Br) = 0.5976 | a(Br) = 0.7861 | a(Br) = 0.5915 | a(Br) = 0.9174 |
| a(Fr) = 0.7350 | a(Fr) = 0.8473 | a(Fr) = 0.7326 | a(Fr) = 0.9064 | |
| a(Hr) = 0.7956 | a(Hr) = 0.9602 | a(Hr) = 0.7904 | a(Hr) = 0.9990 | |
| a(AGM) = 0.6463 | a(AGM) = 0.7983 | a(AGM) = 0.6228 | a(AGM) = 0.9044 | |
| a(TBM) = 0.4862 | a(TBM) = 0.6907 | a(TBM) = 0.4968 | a(TBM) = 0.8611 | |
| MSDF | a(Br) = 0.6173 | a(Br) = 0.7892 | a(Br) = 0.6141 | a(Br) = 0.9087 |
| a(Fr) = 0.7709 | a(Fr) = 0.8557 | a(Fr) = 0.7776 | a(Fr) = 0.8951 | |
| a(Hr) = 0.8553 | a(Hr) = 0.9749 | a(Hr) = 0.8489 | a(Hr) = 0.9990 | |
| a(AGM) = 0.6977 | a(AGM) = 0.8217 | a(AGM) = 0.7023 | a(AGM) = 0.9212 | |
| a(TBM) = 0.5365 | a(TBM) = 0.7119 | a(TBM) = 0.5362 | a(TBM) = 0.8549 | |
| Kaur | a(Br) = 0.6215 | a(Br) = 0.8021 | a(Br) = 0.6042 | a(Br) = 0.9213 |
| a(Fr) = 0.7821 | a(Fr) = 0.8566 | a(Fr) = 0.7511 | a(Fr) = 0.9155 | |
| a(Hr) = 0.8163 | a(Hr) = 0.9713 | a(Hr) = 0.8224 | a(Hr) = 0.9990 | |
| a(AGM) = 0.7062 | a(AGM) = 0.8078 | a(AGM) = 0.6634 | a(AGM) = 0.9156 | |
| a(TBM) = 0.6035 | a(TBM) = 0.7256 | a(TBM) = 0.5264 | a(TBM) = 0.8744 | |
| Hu | a(Br) = 0.7654 | a(Br) = 0.8156 | a(Br) = 0.6317 | a(Br) = 0.9315 |
| a(Fr) = 0.7905 | a(Fr) = 0.8557 | a(Fr) = 0.7812 | a(Fr) = 0.9213 | |
| a(Hr) = 0.8632 | a(Hr) = 0.9812 | a(Hr) = 0.8497 | a(Hr) = 0.9992 | |
| a(AGM) = 0.7256 | a(AGM) = 0.8247 | a(AGM) = 0.7123 | a(AGM) = 0.9336 | |
| a(TBM) = 0.6636 | a(TBM) = 0.7311 | a(TBM) = 0.5546 | a(TBM) = 0.8639 | |
| MTS-IFRM | a(Br) = 0.8834 | a(Br) = 0.7145 | a(Br) = 0.8345 | a(Br) = 0.9354 |
| a(Fr) = 0.7341 | a(Fr) = 0.8844 | a(Fr) = 0.5341 | a(Fr) = 0.9555 | |
| a(Hr) = 0.7589 | a(Hr) = 0.9253 | a(Hr) = 0.8835 | a(Hr) = 0.9952 | |
| a(AGM) = 0.7954 | a(AGM) = 0.9051 | a(AGM) = 0.4954 | a(AGM) = 0.9862 | |
| a(TBM) = 0.8795 | a(TBM) = 0.9493 | a(TBM) = 0.7101 | a(TBM) = 0.9899 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, C.; Xie, W.; Li, Y.; Liu, Z. Multi-Source T-S Target Recognition via an Intuitionistic Fuzzy Method. Remote Sens. 2023, 15, 5773. https://doi.org/10.3390/rs15245773
Zhang C, Xie W, Li Y, Liu Z. Multi-Source T-S Target Recognition via an Intuitionistic Fuzzy Method. Remote Sensing. 2023; 15(24):5773. https://doi.org/10.3390/rs15245773
Chicago/Turabian StyleZhang, Chuyun, Weixin Xie, Yanshan Li, and Zongxiang Liu. 2023. "Multi-Source T-S Target Recognition via an Intuitionistic Fuzzy Method" Remote Sensing 15, no. 24: 5773. https://doi.org/10.3390/rs15245773
APA StyleZhang, C., Xie, W., Li, Y., & Liu, Z. (2023). Multi-Source T-S Target Recognition via an Intuitionistic Fuzzy Method. Remote Sensing, 15(24), 5773. https://doi.org/10.3390/rs15245773







