Global and Local Real-Time Anomaly Detectors for Hyperspectral Remote Sensing Imagery
Abstract
:1. Introduction
2. Commonly Used Global and Local Anomaly Detectors
2.1. Global RX Detector
2.2. Local RX Detector

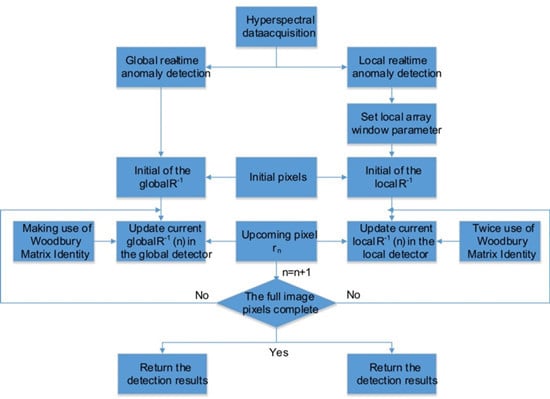
3. Real-Time Anomaly Detectors
3.1. Global Real-Time Detector
3.2. Local Real-Time Detector



4. Experiments
4.1. Data Set Descriptions



| Sensor | AVIRIS |
|---|---|
| Wavelength | 400–1800 nm |
| Bands | 158 |
| Spectral resolution | 10 nm |
| Spatial resolution | 20 m |
| Image size | 200 × 200 |
| Gray range | 0–10,000 |
| Location | Northern Nye County, NV |
4.2. Global Real-Time Processing Experiments







4.3. Local Real-Time Processing Experiments



| Measures | Alunite (A) | Buddingtonite (B) | Calcite (C) | Kaolinite (K) | Muscovite (M) |
|---|---|---|---|---|---|
| SAM | 0.1821 | 0.0656 | 0.0441 | 0.1923 | 0.0924 |
| SID | 0.0405 | 0.0046 | 0.0025 | 0.0522 | 0.0103 |

4.4. Computational Analysis
| K-RXD (seconds) | R-RXD (seconds) | CRXD (seconds) | GRTCRXD (seconds) | LRXD (seconds) | LRTCARXD (seconds) | |
|---|---|---|---|---|---|---|
| Scenario TI | 1.7067 | 1.1825 | 2178.97 | 24.1223 | 332.8399 | 47.8953 |
| ScenarioTE | 1.4789 | 1.1045 | 1984.92 | 22.4953 | 294.2294 | 43.1142 |
| AVIRIS LCVF | 1.2293 | 0.7925 | 1471.51 | 14.9151 | 183.2476 | 28.1530 |


5. Conclusions
- The proposed real-time algorithm has two main features: (1) it is a causal procedure, in the sense that the data samples used for data processing should be only those up to the data sample vector currently being processed; (2) the processing time of the algorithm is negligible, and the proposed method could meet the efficiency requirement by updating the inverse of the correlation matrix without repeated recalculation. Taking advantage of these two features, we gain the benefit of saving data storage since it only needs to store two types of information, about the previous moment and pixel the currently being processed; this is also much easier in terms of hardware implementation because it uses an update equation instead of matrix inversion calculation.
- As demonstrated in anomaly detection results for both synthetic and real hyperspectral images, real-time processing offers the significant advantage of seeing time-varying changes in background information. As time moves along, various levels of background suppression produce false alarms, thus producing a tremendous effect on visual assessment. This issue is worth pursuing and beyond the scope of this paper. It would be interesting to investigate this issue since background suppression provides users with a better understanding of what the detected anomalies really are. Specifically, some weak anomalies detected earlier may be overwhelmed by strong anomalies detected later, as the experimental results show. However, this phenomenon is very important in anomaly detection but cannot be observed using commonly used anomaly detectors, which perform one-shot operation to show the final detected anomalies.
- Despite the fact that local anomaly detection for hyperspectral imagery is not new and has been widely discussed in the literature, the concept of a causal matrix local window (CMLW) and a causal array local window (CALW) for real-time implementation is new.
- The Woodbury matrix identity has been known for a long time but is newly used to derive a recursive equation in this paper, avoiding computing reversion of covariance/correlation matrix. This will greatly shorten the processing time. Computational complexity analysis is very important for anomaly detection because some targets, especially moving targets, provoke immediate decision-making because they may show up suddenly and then disappear quickly afterwards. As a result, for this kind of detection, the processing time must be very short. This paper gives a comparative discussion of the computing time of different algorithms, showing the advantages of time-saving through the Woodbury matrix identity theory.
- The proposed real-time detection methods have the additional benefit of being portable. Other detection algorithms, such as CEM, TCIMF, etc., could also be conducted as real-time detectors using the same methodology.
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Chang, C.-I. Hyperspectral Imaging: Techniques for Spectral Detection and Classification; Kluwer Academic/Plenum Publishers: New York, NY, USA, 2003. [Google Scholar]
- Chang, C.-I. Hyperspectral Data Processing: Algorithm Design and Analysis; Wiley: Hoboken, NJ, USA, 2013. [Google Scholar]
- Rosario, D.S. Algorithm Development for Hyperspectral Anomaly Detection. PhD Thesis, University of Maryland, College Park, MD, USA, 2008. [Google Scholar]
- Reed, I.S.; Yu, X. Adaptive multiple-band CFAR detection of an optical pattern with unknown spectral distribution. IEEE Trans. Signal. Process. 1990, 38, 1760–1770. [Google Scholar] [CrossRef]
- Plaza, A.; Martinez, P.; Plaza, J. A new method for target detection in hyperspectral imagery based on extended morphological profiles. In Proceedings of the 2003 IEEE International Conference on Geoscience and Remote Sensing Symposium, Toulouse, France, 21–25 July, 2003; pp. 3772–3774.
- Kwon, H.; Nasrabadi, N.M. Kernel RX-algorithm: A nonlinear anomaly detector for hyperspectral imagery. IEEE Trans. Geosci. Remote Sens. 2005, 43, 388–397. [Google Scholar] [CrossRef]
- Foy, B.R.; Theiler, J.; Fraser, A. M. Decision boundaries in two dimensions for target detection in hyperspectral imagery. Opt. Express. 2014, 22, 608–617. [Google Scholar] [CrossRef] [PubMed]
- Guo, Q.; Zhang, B.; Ran, Q.; Gao, L.; Li, J.; Plaza, A. Weighted-RXD and linear filter-based RXD: Improving background statistics estimation for anomaly detection in hyperspectral imagery. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2014, 7, 2351–2366. [Google Scholar] [CrossRef]
- Kwon, H.; Der, S.Z.; Nasrabadi, N.M. Projection-based adaptive anomaly detection for hyperspectral imagery. In Proceedings of the 2003 IEEE International Conference on Image Processing, Barcelona, Spain, 14–17 September, 2003; pp. 1001–1004.
- Ranney, K.I.; Soumekh, M. Hyperspectral anomaly detection within the signal subspace. IEEE Geosci. Remote Sens. Lett. 2006, 3, 312–316. [Google Scholar] [CrossRef]
- Ma, L.; Crawford, M.M.; Tian, J. Anomaly detection for hyperspectral images using local tangent space alignment. In Proceedings of the 2010 IEEE International Conference on Geoscience and Remote Sensing Symposium, Honolulu, HI, USA, 25–30 July, 2010; pp. 824–827.
- Taitano, Y.P.; Geier, B.A.; Bauer, K.W., Jr. A locally adaptable iterative RX detector. Eurasip. J. Adv. Sign. Process. 2010. [Google Scholar] [CrossRef]
- Matteoli, S.; Diani, M.; Corsini, G. A kurtosis-based test to efficiently detect targets placed in close proximity by means of local covariance-based hyperspectral anomaly detectors. In Proceedings of the 3rd Workshop on Hyperspectral Image and Signal Processing: Evolution in Remote Sensing, Lisbon, Portugal, 6–9 June, 2011.
- Molero, J.M.; Garzon, E.M.; Garcia, I.; Plaza, A. Analysis and optimizations of global and local versions of the RX algorithm for anomaly detection in hyperspectral data. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2013, 6, 801–814. [Google Scholar] [CrossRef]
- Kwon, H.; Der, S.Z.; Nasrabadi, N.M. Adaptive anomaly detection using subspace separation for hyperspectral imagery. Opt. Eng. 2003, 42, 3342–3351. [Google Scholar] [CrossRef]
- Matteoli, S.; Veracini, T.; Diani, M.; Corsini, G. A locally adaptive background density estimator: An evolution for RX-based anomaly detectors. IEEE Geosci. Remote Sens. Lett. 2014, 11, 323–327. [Google Scholar] [CrossRef]
- Scholkopf; Smola, A.J. Learning with Kernels; MIT Press: Cambridge, MA, USA, 2002. [Google Scholar]
- Chang, C.-I.; Chiang, S.-S. Anomaly detection and classification for hyperspectral imagery. IEEE Trans. Geosci. Remote Sens. 2002, 40, 1314–1325. [Google Scholar] [CrossRef]
- Ren, H.; Chang, C.-I. Target-constrained interference-minimized approach to subpixel target detection for hyperspectral images. Opt. Eng. 2000, 39, 3138–3145. [Google Scholar] [CrossRef]
- Wang, Y.; Schultz, R.; Chen, S.; Liu, C.; Chang, C.-I. Progressive constrained energy minimization for subpixel detection. Proc. SPIE 2013, 8743, 874321. [Google Scholar]
- Liu, W.; Chang, C.-I. A nested Spatial window-based approach to target detection for hyperspectral imagery. In Proceedings of 2004 IEEE International Conference on Geoscience and Remote Sensing Symposium, Anchorage, AK, USA, 20–24 September, 2004; pp. 266–268.
- Liu, W.; Chang, C.-I. Multiple-window anomaly detection for hyperspectral imagery. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2013, 6, 644–658. [Google Scholar] [CrossRef]
- Stellman, C.M.; Hazel, G.G.; Bucholtz, F.; Michalowicz, J.V.; Stocker, A.; Scaaf, W. Real-time hyperspectral detection and cuing. Opt. Eng. 2009, 17, 17391–17411. [Google Scholar]
- Zhao, C.; Wang, Y. Design and analysis of hyperspectral anomaly detection based on Kalman filter theory. Chin. J. Electron. 2013, 22, 849–854. [Google Scholar]
- Molero, J.M.; Garzon, E.M.; Garcia, I.; Quintana-Orti, E.S.; Plaza, A. Efficient implementation of hyperspectral anomaly detection techniques on GPUs and multicore processors. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2014, 7, 2256–2266. [Google Scholar] [CrossRef]
- Rossi, A.; Acito, N.; Diani, M.; Corsini, G. RX architectures for real-time anomaly detection in hyperspectral images. J. Real-Time Image Process. 2012. [Google Scholar] [CrossRef]
- Ensafi, E.; Stocker, A. D. An adaptive CFAR algorithm for real-time hyperspectral target detection. Proc. SPIE 2008. [Google Scholar] [CrossRef]
- Hager, W.W. Updating the inverse of a matrix. SIAM Rev. 1989, 31, 221–239. [Google Scholar] [CrossRef]
- Press, W.H.; Teukolsky, S.A.; Vetterling, W.T.; Flannery, B.P. Numerical Recipes: The Art of Scientific Computing, 3rd revised ed.; Cambridge University Press: Cambridge, UK, 2007. [Google Scholar]
- Chen, S.; Wang, Y.; Wu, C.; Liu, C.; Chang, C.-I. “Real-time causal processing of anomaly detection for hyperspectral imagery. IEEE Trans. Aerosp. Electron. Syst. 2014, 50, 1511–1534. [Google Scholar] [CrossRef]
- USGS Website. Available online: http://speclab.cr.usgs.gov/cuprite.html (accessed on 27 July 2014).
- Chang, C.-I.; Hsueh, M. Characterization of anomaly detection for hyperspectral imagery. Sens. Rev. 2006, 26, 137–146. [Google Scholar] [CrossRef]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, C.; Wang, Y.; Qi, B.; Wang, J. Global and Local Real-Time Anomaly Detectors for Hyperspectral Remote Sensing Imagery. Remote Sens. 2015, 7, 3966-3985. https://doi.org/10.3390/rs70403966
Zhao C, Wang Y, Qi B, Wang J. Global and Local Real-Time Anomaly Detectors for Hyperspectral Remote Sensing Imagery. Remote Sensing. 2015; 7(4):3966-3985. https://doi.org/10.3390/rs70403966
Chicago/Turabian StyleZhao, Chunhui, Yulei Wang, Bin Qi, and Jia Wang. 2015. "Global and Local Real-Time Anomaly Detectors for Hyperspectral Remote Sensing Imagery" Remote Sensing 7, no. 4: 3966-3985. https://doi.org/10.3390/rs70403966
APA StyleZhao, C., Wang, Y., Qi, B., & Wang, J. (2015). Global and Local Real-Time Anomaly Detectors for Hyperspectral Remote Sensing Imagery. Remote Sensing, 7(4), 3966-3985. https://doi.org/10.3390/rs70403966