Abstract
In higher education, especially in programming-intensive fields like computer science, safeguarding students’ source code is crucial to prevent theft that could impact learning and future careers. Traditional storage solutions like Google Drive are vulnerable to hacking and alterations, highlighting the need for stronger protection. This work explores digital technologies that enhance source code security, with a focus on Blockchain and NFTs. Due to Blockchain’s decentralized and immutable nature, NFTs can be used to control code ownership, improving security, traceability, and preventing unauthorized access. This approach effectively addresses existing gaps in protecting academic intellectual property. However, as Bennett et al. highlight, while these technologies have significant potential, challenges remain in large-scale implementation and user acceptance. Despite these hurdles, integrating Blockchain and NFTs presents a promising opportunity to enhance academic integrity. Successful adoption in educational settings may require a more inclusive and innovative strategy.
1. Introduction
In an era marked by rapid technological advancements and increasing concerns over intellectual property rights, protecting digital assets has become a critical challenge. For students in Computer Science and Software Engineering (CSSE), ensuring the integrity and ownership of their source code is essential, as it represents not only their academic effort but also potential intellectual property. Despite existing submission protocols and security measures, issues related to originality, authorship, and unauthorized use of student-developed code remain prevalent.
This paper explores how Blockchain and Non-Fungible Tokens (NFTs) can enhance the security and traceability of student projects. Specifically, it examines the submission and evaluation processes in universities, with a particular focus on the Massachusetts Institute of Technology (MIT). Additionally, it discusses the importance of source code protection through licensing and copyright regulations across different regions, including Europe, Asia, and Colombia.
Furthermore, this study delves into the role of digital assets, Blockchain, and NFTs in safeguarding intellectual property within academic environments. These emerging technologies provide innovative solutions to long-standing concerns regarding ownership verification and tamper-proof record-keeping. By integrating these decentralized technologies, universities can strengthen the security of student projects while fostering a more transparent and reliable academic ecosystem.
The implementation of blockchain, NFTs, and digital certificates for securing intellectual property, particularly academic source code, presents several advantages and disadvantages:
Advantages:
- Immutability and Security: Blockchain ensures that once a transaction is recorded, it cannot be altered, providing strong protection against plagiarism or unauthorized modifications.
- Decentralization: Eliminates the reliance on a single authority, reducing the risk of data manipulation or institutional biases in ownership claims.
- Transparent Ownership Records: NFTs allow for the creation of unique digital signatures, providing indisputable proof of authorship and ownership.
- Automated Smart Contracts: These enable streamlined licensing agreements and automatic enforcement of intellectual property rights without intermediaries.
Disadvantages:
- High Energy Consumption: Many blockchain networks require substantial computational power, raising concerns about sustainability and efficiency.
- Regulatory Uncertainty: The legal framework for blockchain-based intellectual property protection is still evolving, with varying acceptance across jurisdictions.
- Complexity and Cost: Implementing blockchain and NFTs requires technical expertise and may involve high transaction fees, making it less accessible for smaller institutions or individual students.
- Irreversible Transactions: While immutability is a strength, errors in ownership attribution or smart contracts can be difficult to correct.
By analyzing these advantages and disadvantages, it becomes evident that while blockchain and NFTs offer unprecedented security and authenticity, their adoption in academia requires careful consideration of legal and technical factors.
- Code submission processes:
This is more so in the systems and computer engineering career, whereby final exercises like software and system development are perceived as the last milestones in the training process [1]. In such projects, a student will post his/her source code, and the posted material will be analyzed based on both how well it works, as well as other program guidelines. In most universities, code is shared on other internal digital platforms such as OneDrive and Google Drive. They include replication, such as in Git repositories or Learning Management Systems (LMS) such as Moodle®, which offer security and guarantee the integrity of the content. Still, the issue of source code protection remains critical, with concerns about possible manipulation or theft of work before final evaluation [2]. It should be considered that this aspect is critical, as changes to the code pose a risk of compromising the academic integrity of the project and the student, as well as the reputation of the academic institution [3].
- b.
- Thesaurus in Systems Engineering:
MIT has created fine-grained and specific thesauri that are aimed at improving the reusability of technical terms in systems engineering. For example, one of the major resources of MIT is the Thesaurus of Engineering Terminology (TET), containing a defined and extensively approved set of Global Standards in systems engineering. Dialogues created by this thesaurus are used in software development tools, thus ensuring conformity and compliance in the language used in projects [4].
Moreover, Stanford, Harvard, and other universities have adopted and have further developed their own technical thesauri. These thesauri contain not only the words and phrases potentially used when searching for information, but also the precise definitions of the concepts being searched, and their interrelations, which makes search results understandable for researchers and students who employ commonly accepted terms and definitions. Such actions help in improving the quality of communication within such a project, as well as safeguarding the intellectual property of students [5].
All in all, regarding the thesauri and policies used in the institution, these are meant for a fair and transparent evaluation process, as well as correct attribution of authorship and retention of academic knowledge [6].
- c.
- Definition of Source Code:
Source code is defined as a sequential collection of coded statements written in a programming language that is intelligible to the programmer and is in a form that can be compiled/interpreted and run on the machine [7]. As a matter of fact, at MIT, the source code is important in any software project as it embodies the thinking and the answers that a programmer uses to achieve solutions. Thus, it becomes critical to protect this fundamental foundation for the creation of all the applications and systems and to preserve the author’s intellectual integrity [8].
- d.
- Definition and Copyright of Source Code
Source code is a structured collection of coded statements written in a programming language that can be compiled or interpreted to execute on a machine [9]. At MIT, source code is considered a fundamental component of software projects, encapsulating the problem-solving approaches and intellectual contributions of the developer. Therefore, protecting source code is essential to preserving academic integrity and the intellectual rights of its authors [10].
Legal protections for source code vary significantly across jurisdictions. In Europe, the Directive 2009/24/EC classifies source code as a literary work, granting authors exclusive rights to use and distribute their code. Similarly, Japan and South Korea have adopted legal frameworks to safeguard software copyrights, albeit with regional differences in implementation [11]. In Colombia, the National Copyright Office recognizes source code as a form of software work, granting its author economic and moral rights [12]. To combat piracy and unauthorized use, various measures have been implemented, including open licenses that specify usage conditions and digital protection technologies that restrict unauthorized access [13].
- e.
- Digital Assets and Blockchain for Academic Protection
Digital assets encompass a broad range of resources in digital form, including documents, multimedia files, cryptocurrencies, and NFTs [14]. Protecting these assets is critical in an environment where data can be easily stolen or manipulated. Security measures such as encryption, private keys, and multi-factor authentication are commonly used to safeguard digital resources [15].
Blockchain technology has emerged as a robust solution for ensuring the integrity of digital assets by providing a decentralized and tamper-proof ledger [16]. Unlike traditional databases, blockchain operates through Distributed Ledger Technology (DLT), which disperses records across multiple nodes, eliminating a single point of control and reducing the risk of unauthorized alterations [17]. The cryptographic nature of blockchain ensures that each record remains immutable and secure, making it a viable option for intellectual property management in academia [18].
- f.
- NFTs as a Mechanism for Intellectual Property Protection
Non-fungible tokens are unique digital assets stored on a blockchain, capable of representing a variety of intellectual properties, including academic source code [19]. By tokenizing student projects as NFTs, institutions can generate a unique and verifiable digital signature that certifies the authenticity and ownership of each work [20]. This approach not only enhances security but also provides an immutable record of authorship. Additionally, the implementation of multi-chain blockchain technology could improve interoperability between different blockchain networks, offering more flexible and scalable solutions for managing NFTs in academic settings [21,22].
1.1. Discussion of Challenges and Limitations in the Study
While leveraging the tamper-proof provenance offered by Blockchain and NFTs for student source code verification holds immense promise, this study acknowledges several hurdles that must be addressed for widespread adoption [23]. These challenges include technical integration, scalability, performance, user adoption, security concerns, and regulatory compliance, all of which impact the feasibility of large-scale implementation in academic settings.
- Technical Integration: The integration of Blockchain-based solutions with existing university IT infrastructures presents a significant challenge. Academic institutions rely on legacy systems that may not be fully compatible with newer blockchain-based applications, requiring a migration strategy that minimizes workflow disruptions. Furthermore, interoperability between different blockchain protocols and existing digital credentialing platforms must be ensured to facilitate seamless adoption. Recent studies suggest that hybrid architectures combining on-chain and off-chain storage can help address compatibility issues and improve performance in academic environments [24].
- Scalability and Performance: Blockchain networks face significant scalability limitations due to increasing transaction loads, particularly in environments with high volumes of student submissions and academic records. As the number of users and projects grows, transaction throughput and processing times may become bottlenecks, leading to inefficiencies [25]. Several approaches, such as sharing, off-chain computation (e.g., Layer 2 solutions), and Directed Acyclic Graphs (DAGs), have been proposed to enhance blockchain scalability in educational applications. Now, emerging technologies like rollups and sidechains also offer potential improvements by offloading computational tasks while maintaining security guarantees.As the number of users and projects increases, the scalability of the blockchain network is affected. The latency and processing issues can compromise system efficiency. Solutions such as sharding and off-chain computation have been proposed to mitigate these issues. Recent studies have shown that optimizing resource allocation in Internet of Things (IoT) networks through deep reinforcement learning techniques, such as the Deep Reinforcement Learning-based resource allocation approach, can significantly reduce latency and improve overall system performance [26]. This approach has been validated in wireless networks considering the network slicing paradigm, achieving minimization of information update times, and optimizing resource efficiency in decentralized networks.
- Security and Privacy Concerns: Ensuring the security and privacy of academic records is critical. While blockchain offers immutability and transparency, it also raises concerns regarding unauthorized data exposure and potential attacks on smart contracts. Zero-knowledge Proofs (ZKPs) and Trusted Execution Environments (TEEs) have been explored as viable methods to enhance security and privacy in blockchain-based academic credentialing. Additionally, quantum resistance remains a long-term concern, as advancements in quantum computing could compromise existing cryptographic schemes used in blockchain networks [27].
- User Adoption and Training: The technical nature of blockchain systems presents a steep learning curve for faculty and students unfamiliar with decentralized technologies. A lack of blockchain literacy could hinder adoption and effective utilization [28]. Therefore, user-friendly interfaces, comprehensive training programs, and educational resources are essential to facilitate widespread acceptance. Research has shown that gamified learning approaches and interactive tutorials can enhance blockchain adoption in academic settings [29].
At the same time, when outlining the research advantages and prospects for application, the members of the research team see great hopes for the development of this solution in the sphere of academic integrity and intellectual property rights. They have addressed these challenges in advance in their effort in designing and implementing the system to ensure a better and more efficient system in the future.
1.2. Study Objectives and Motivation Behind Them
The objective of the research is to ensure a systematic search of the literature on the security of digital assets and intellectual property in academic settings with the help of Blockchain and NFTs. The purpose of this study is to define and reveal the measures and approaches taken to protect the software, digital data, and other relevant items in universities. To this end, the PRISMA methodology for searching, screening, and sorting the papers is used on the selected key databases. In addition, four databases, including IEEE Xplore, ScienceDirect, ACM Digital Library, and SpringerLink, have been selected because they contain numerous related research papers and articles.
Therefore, based on the overarching objective, this investigation seeks to address specific research questions (RQ):
- RQ1: What is the distribution of papers across different years, focusing on Final Project, Degree, Copyright, Software, Digital Content, and University Internal Protection?
- RQ2: How are the chosen papers related to the proposed keywords concerning these topics?
- RQ3: Which of the papers explore Blockchain-based tokens and Cross-Chain (Smart Contract) as a review related to the academic setting?
- RQ4: Which papers explore non-fungible tokens, copyright, integrity, and software within academic and university contexts?
- RQ5: In the current landscape of Unique Assets of Digital Content, what constitutes the primary challenges that universities face regarding their internal protection processes?
- RQ6: What global standards are employed to safeguard the integrity and assets of digital content and media, especially in the context of educational institutions?
- RQ7: What types of NFTs are used to generate digital assets for content software and applications, and what methods and techniques are currently being utilized?
1.3. Contributions
This work aims to explore the application of blockchain and NFTs in the university context to secure the contents of academic theses. Most attention will be paid to choosing resources related only to this application. The key objective is then to offer an effective solution for protecting the conceptual information that should be included in the students’ theses.
The primary contributions can be summarized as follows:
- Synthesis of Existing Knowledge: To achieve this, we will perform a systematic review of the literature to provide a synthesis of the research studies in the field. Making this synthesis will give a clear connection on how both blockchain and NFTs can be applied to protect academic content. Further, we will describe the technical aspects and some of the ethical issues of their application in an academic context [30,31,32].
- Recommendations for Future Applications: From the identification of the project, recommendations on the future trend for the use of blockchain and NFTs in issues of intellectual property will be developed. This investigation will go outside the ivory tower’s research confines as a means of providing valuable information for other aspects of intellectual property management strategies [33,34].
- Identification of Emerging Trends: This study will reveal contemporary and fresh ideas for utilizing blockchain and NFTs to address the issue of copyright and intellectual property rights. This will help in the ongoing debate of emerging technologies in the field of intellectual property [35,36].
- Practical Validation and Case Studies: We will look at examples of the adoption of blockchain and NFTs in academic institutions, including current use cases and pilots. This analysis would reveal the experiences of practical difficulties or achievements in the implementation of these technologies in the context of this study [37,38].
2. Materials and Methods
The integration of blockchain technology with groundbreaking digital assets has been extensively examined in previous literature, particularly concerning information security, intellectual property protection, and blockchain’s core function: ensuring the authenticity of digital content in educational environments. One of the key aspects analyzed is how blockchain-based solutions, particularly NFTs, can help guarantee the authenticity of student-generated software. Additionally, studies highlight the benefits of using NFT technology to create immutable archives, securing ownership records and the history of digital assets [39].
Furthermore, the application of decentralized storage solutions alongside blockchain technology has been a central topic in recent discussions. These approaches aim to enhance security and accessibility for digital content by leveraging blockchain’s permanent and transparent nature [40]. For instance, research has demonstrated that hybrid blockchain solutions can enable the secure storage and retrieval of academic assets, reducing the risks of hacking and data loss [41].
In addition to these benefits, blockchain adoption in educational contexts presents technological, scalability, and performance challenges. A primary concern is the scalability of blockchain networks, especially as the demand for digital asset protection and ownership authentication continues to grow. Several solutions have been proposed, such as layer-two scaling techniques and off-chain computation, designed to improve performance without compromising security [42].
Moreover, integrating blockchain into academic environments raises concerns about usability and accessibility. To ensure widespread adoption, it is crucial that faculty members and students can seamlessly incorporate these technologies into their work so that they remain relevant in the long term. Research suggests that user-centered design and extensive training programs are essential to overcoming adoption barriers and facilitating a smooth transition to blockchain-based systems [43].
Finally, current global efforts to establish international standards for the application of blockchain and NFTs in intellectual property management remain ongoing. Ensuring compliance with institutional policies is crucial for creating a secure and legally sound framework for handling digital assets [44]. Overall, this line of research underscores the transformative potential of blockchain technology and NFTs in safeguarding academic intellectual property, advocating for their broader implementation not only in educational institutions but also in content management across the information society.
2.1. PRISMA
This section introduces the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) methodology as a useful framework for searching and selecting relevant articles on blockchain technology in educational environments. This methodology is based on a series of systematic and reproducible steps that allow for a comprehensive and exhaustive review of the literature. The aim is to leverage the benefits of this methodology, which include:
- Conducting a comprehensive and exhaustive review of the literature.
- Reducing bias in study selection.
- Increasing the transparency and reproducibility of the review.
- Facilitating the synthesis of available evidence.
The PRISMA methodology steps that will be implemented are as follows:
- Define the research question: What are the best practices for software project management in the post-production phase?
- Identify relevant studies: Articles will be searched for in the following databases: IEEE Xplore, ACM Digital Library, ScienceDirect, and Scopus. The search terms will be: “Authenticity”, “Blockchain”, “Copyright”, “Data protection”, “Degree Works”, “Digital certificates”, “Digital Rights Management”, “Intellectual Property”, “Non-Fungible Tokens (NFTs)”, “Source code”, “Technological innovation”.
- Study selection: Studies that meet the following criteria will be selected:
- Published in a Q1 or Q2 journal
- Published in the last 10 years (2014–2024) to include recent advancements in blockchain and digital security.
- Written in English or Spanish to ensure accessibility and broad applicability.
- Directly relevant to the research question, specifically discussing blockchain, NFTs, and digital certificates in educational and intellectual property contexts.
- Data extraction: The following data will be extracted from the selected studies: Authors, Year of publication, Study title, Abstract, Methodology, Results, and Conclusions
- Data analysis: The data extracted from the different articles will be analyzed to identify the best practices for blockchain technology in educational environments.
- Presentation of results: The results of the review will be presented in an informative table and its respective analysis.
- Why PRISMA: The PRISMA methodology, designed for systematic reviews and meta-analyses, offers core principles that resonate strongly within this project’s context:
- Structured Literature Review: While this project involves system development, a PRISMA-inspired approach to the literature review would ensure a comprehensive and unbiased exploration of existing research. This includes using well-defined search terms in relevant databases, clear inclusion and exclusion criteria for studies, and a thorough analysis focused on security, intellectual property protection mechanisms, and educational applications of blockchain.
- Transparent Process: Documenting the literature search strategy, system design choices, and evaluation methods aligns with PRISMA’s emphasis on transparency. This allows others to understand the research process, assess its rigor, and potentially replicate the work.
- Focus on Evidence: PRISMA helps researchers move beyond subjective opinions and design a project that aims to generate concrete evidence. This can include data from security tests, insights from usability studies, and thematic analysis of feedback related to the system’s impact on academic integrity.
- Addressing Bias: Even in a single-institution project, biases can creep in when designing or choosing technological components. A PRISMA mindset encourages the researcher to actively consider potential biases in the literature they review, the architecture they propose, and their evaluation criteria.
By incorporating these elements, the project gains the following benefits:
- Credibility and Trustworthiness: A well-documented, evidence-based, and bias-aware approach strengthens the research findings. This is crucial when recommending potentially disruptive technology to a university’s stakeholders.
- Synthesis and Insights: PRISMA encourages researchers to move beyond just summarizing existing studies. It guides them toward identifying patterns, gaps, and areas ripe for innovation, making this project more likely to yield novel and useful solutions.
- Foundation for Future Research: A solid research foundation lays the groundwork for further exploration. The structured literature review can inform future meta-analyses, while the findings of this project might inspire replication studies at other universities.
By clearly articulating PRISMA’s role in this study, the methodology’s relevance becomes more apparent, bridging the gap between the literature review and the implementation of blockchain, NFTs, and digital certificates in academic settings.
2.2. Incorporation and Exclusion Parameters
To ensure a comprehensive and focused exploration of relevant research, the following parameters guide the literature selection process:
Incorporation Parameters
- Direct Relevance to Education: Studies explicitly investigating blockchain and NFT applications for intellectual property protection within academic settings are prioritized. This focus on the educational context ensures the review captures research directly applicable to the project’s specific challenge.
- Technical Depth: Papers detailing technical implementations, architectural choices, NFT designs, and security mechanisms relevant to similar use cases are actively sought. These provide insight into the feasibility and potential design considerations for the proposed source code protection system.
- Usability and Adoption Analysis: Studies addressing the usability of blockchain-based systems for students and faculty, as well as potential integration challenges within university workflows, are considered vital. Practical insights into adoption barriers and facilitators contribute to the design of a solution tailored to the specific needs of the academic environment.
- Empirical Data and Case Studies: Papers presenting quantitative or qualitative evidence from pilot projects or implementations of similar systems are highly valued. Such data enable an assessment of the technology’s potential impact on deterring plagiarism and safeguarding intellectual property.
Exclusion Parameters
- Outdated Technologies: Studies primarily focused on superseded blockchain platforms or earlier NFT standards are excluded to maintain focus on cutting-edge and actively maintained technologies.
- Cryptocurrency Emphasis: Papers with a central emphasis on cryptocurrency applications are excluded, even while acknowledging their reliance on blockchain. This refinement concentrates research on the application of blockchain specifically for intellectual property protection.
- Focus on Relevant Educational Applications: While some studies may offer valuable insights, those focusing on the application of blockchain in areas unrelated to intellectual property and higher education, such as healthcare or supply chain management, are excluded unless they directly contribute transferable knowledge to the educational domain.
- Non-Academic Focus: Priority is placed on studies conducted within academic institutions or contexts. Papers primarily exploring commercial applications are excluded to ensure the review reflects the specific challenges and regulations of the university setting.
- Lack of Empirical Basis: Purely conceptual or speculative discussions without data-driven analysis are excluded. The review favors studies grounded in concrete system designs, experimental results, or reasoned arguments.
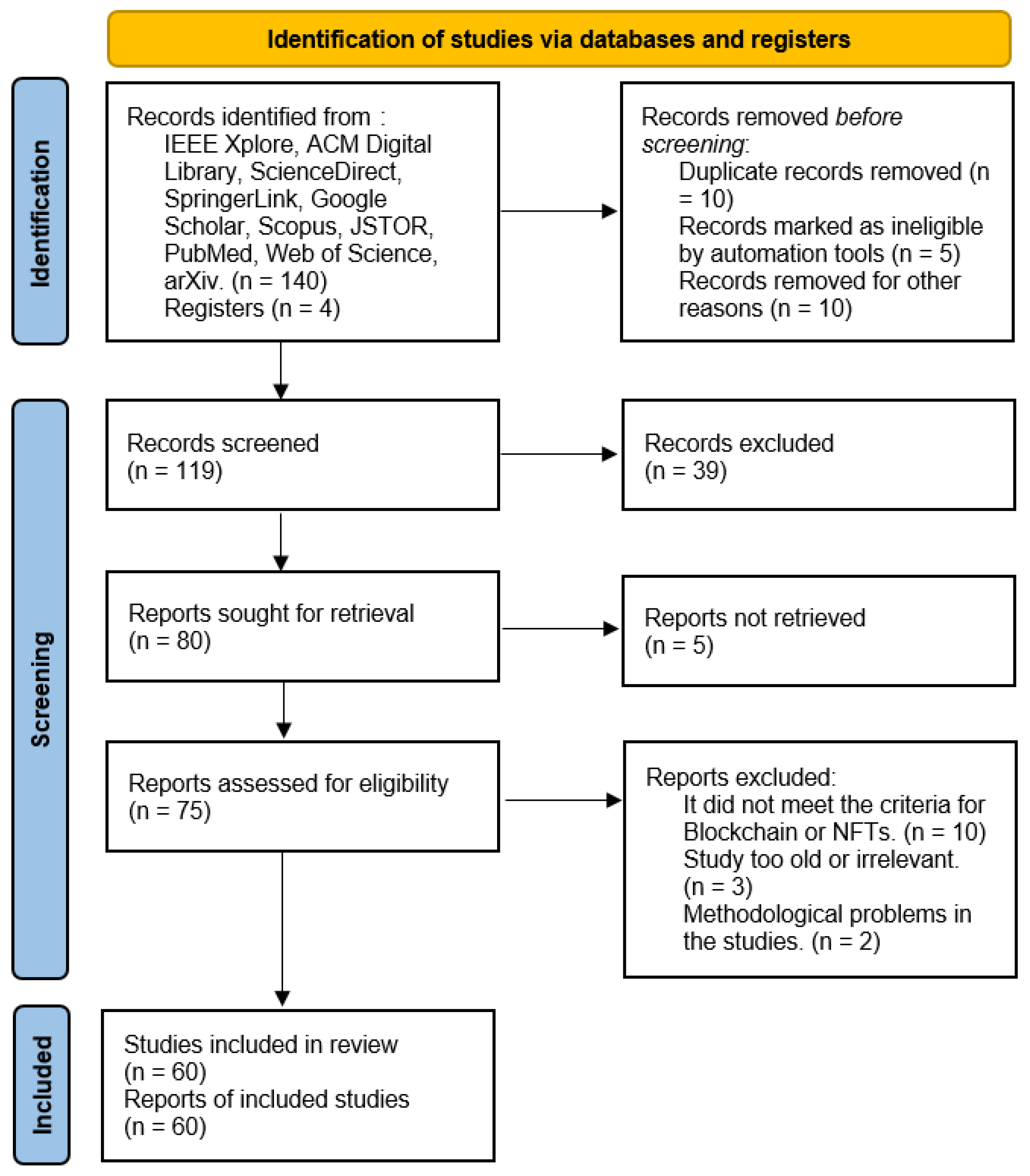
The generalized PRISMA method used is shown in Figure 1:
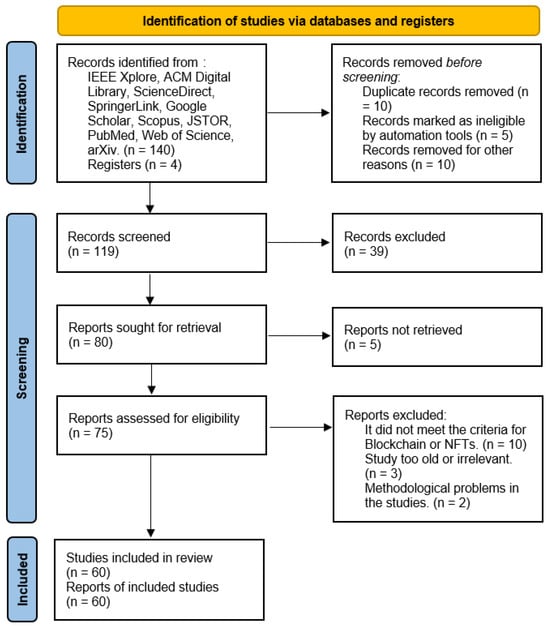
Figure 1.
The generalized PRISMA method used.
3. Results
In this section, we present the findings of our detailed review focused on the application of blockchain and NFT technologies in relation to intellectual property security in academic papers.
The analysis aimed to identify patterns, trends, and insights related to the current secure integration of blockchain and NFTs in the protection and authentication of source code in academic papers, covering the detailed evaluation of more than 100 selected studies. The obtained results are presented in a concise manner with meticulously produced concise tables and graphs. These visual representations make it easier to sort and analyze the wide range of papers reviewed, offering insights into key issues, methodologies, and emerging areas of interest at the crossroads between blockchain, NFTs technology, and higher education.
Results Based on the Proposed Research Questions
- RQ1: What is the distribution of papers across different years?
As shown in Table 1, there are no papers from 2020 and earlier that align with the theme of blockchain integration and intellectual authenticity. This is because most papers from those years primarily focused on the introduction and potential of blockchain in other contexts, without specifically addressing its application for the protection of intellectual property or the authenticity of source code, which are key areas in our proposal.

Table 1.
Distribution of papers by years.
The lack of papers during this period can be explained by the fact that the technology was still in its infancy during this period and has not been widely discussed in academic circles for such uses. Furthermore, the few papers available before 2021 may present data that could already be obsolete or solutions that, in the current environment, would no longer be feasible or helpful because of fast evolution, important for the technological context, and the need for improvements in the system of intellectual property.
Starting in 2020, there is a significant increase in publications, peaking in 2021 and 2022, with 31 articles published each year. This increase reflects growing interest and greater attention toward the integration of blockchain and NFT technologies in the protection of intellectual property and code authenticity. This coincides with the consolidation of these technologies and their recognition as effective tools to address challenges related to intellectual property in the academic environment.
The upward trend in publications during these recent years underscores the increasing importance and recognition of blockchain and NFTs as viable and necessary solutions for protecting intellectual property and authenticity in academia.
This recent focus also indicates a shift towards broader adoption of these technologies, driven by their ability to offer immutable and transparent records that secure authorship and the integrity of digital assets.
- RQ2: How are the chosen papers related to the proposed keywords?
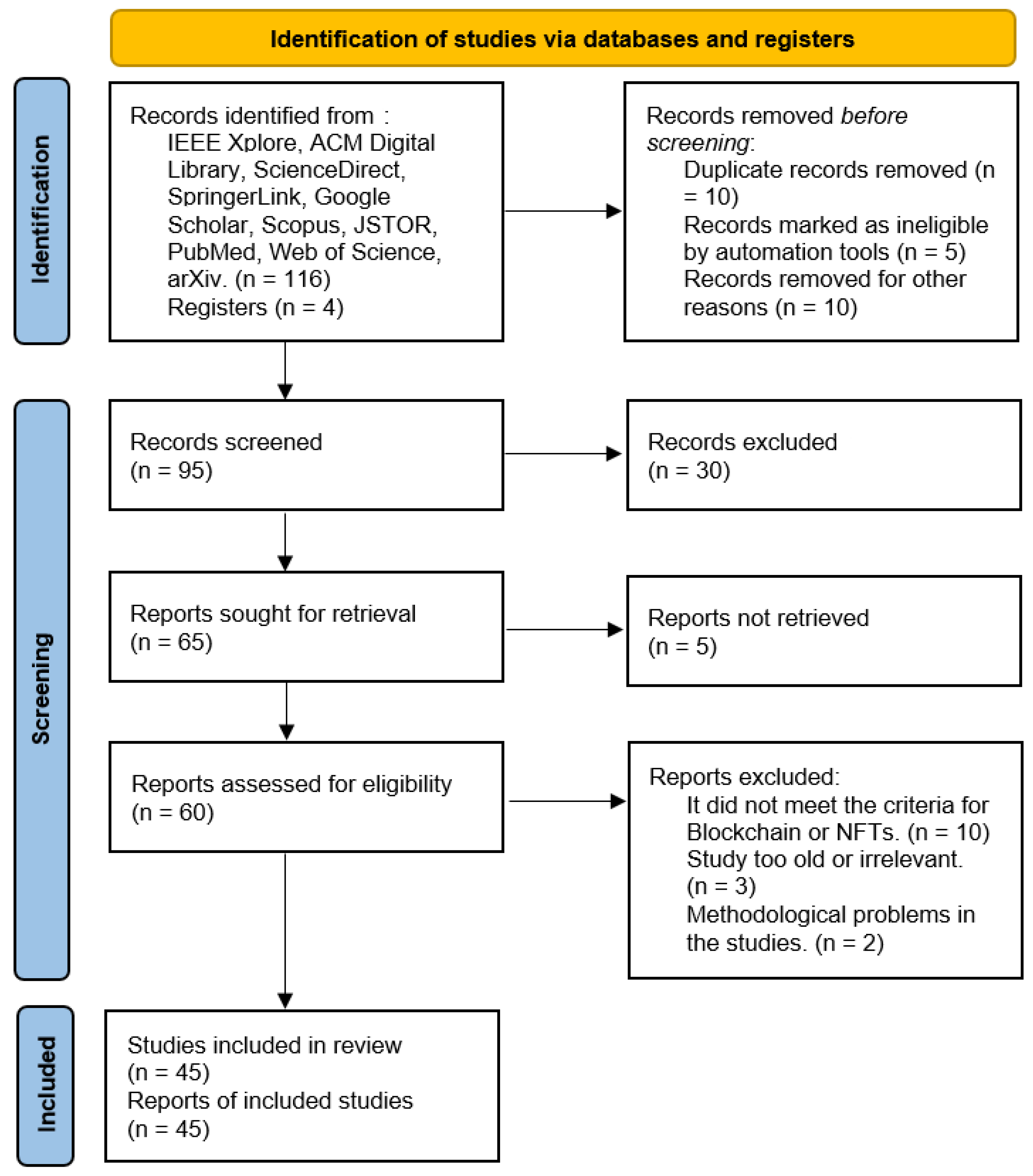
The PRISMA method applied to answer question 2 is shown in Figure 2:
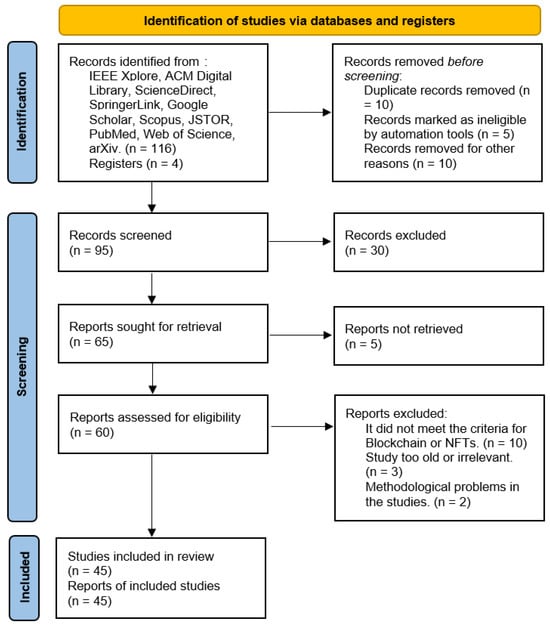
Figure 2.
PRISMA method applied to answer: How are the chosen papers related to the proposed keywords?
During the review of the articles, we observed that many of them not only focused on establishing a relationship between blockchain and various domains but also on exploring how to ensure this connection to maintain the integrity and security of the chain. Table 2 categorizes these articles according to keywords such as integrity, copyright, software, digital content/asset, and NFTs. It was evident that a significant number of studies emphasized the intersection of blockchain with copyright and software applications. For example, considerable attention to the integrity and protection of digital content was noted, suggesting a robust focus on information security.

Table 2.
Classification of research papers on blockchain based on given keywords.
In addition, many studies addressed both integrity and copyright, highlighting the importance of protecting digital assets in the blockchain environment. A particular interest in NFTs was also observed, with several papers exploring their specific applications and challenges. The distribution of different fields reveals a notable concentration on copyright and digital assets, indicating a thorough exploration of blockchain’s potential in various sectors.
This detailed analysis highlights the diverse but interconnected nature of blockchain research, emphasizing both its technological advances and practical implementations. The review highlights that most studies focus on issues related to security and integrity, rather than on the blockchain integration framework, which is crucial for the future development of this technology.
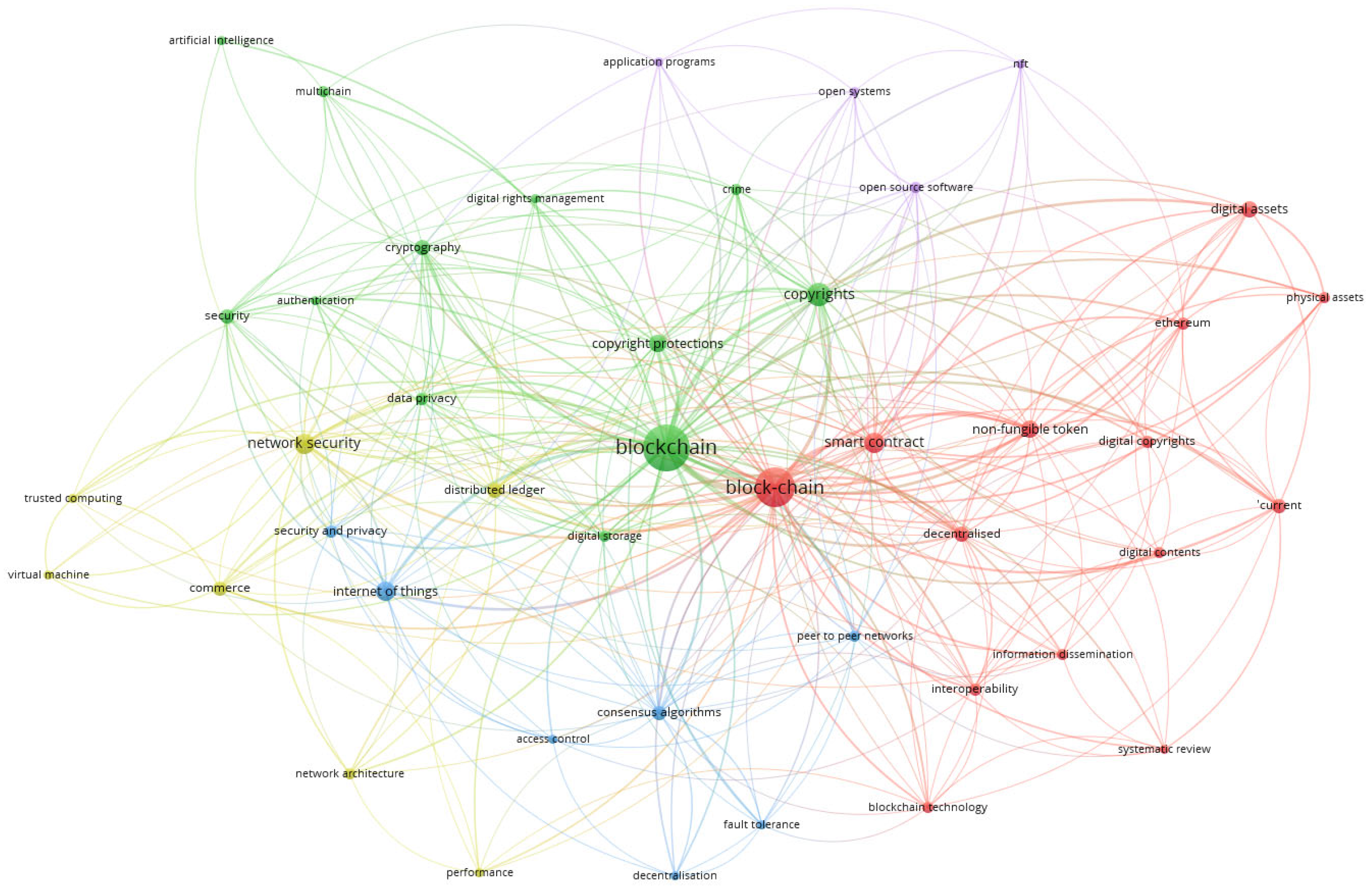
The VOSviewer-generated graph illustrates a co-occurrence analysis of keywords related to blockchain and its associated concepts (See Figure 3). In this visualization, larger nodes represent terms that appear more frequently in the dataset, indicating their prominence in the analyzed literature. The most significant keywords include “blockchain”, “block-chain”, “network security”, and “internet of things”.
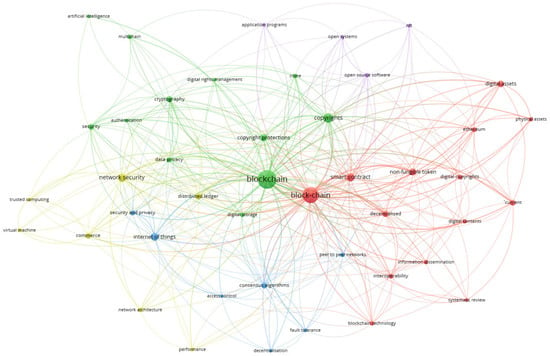
Figure 3.
Co-occurrence analysis of keywords.
The colors in the network graph represent different thematic clusters, grouping related terms based on their conceptual associations:
- Green Cluster: This cluster primarily includes terms such as network security, privacy, encryption, and authentication, which are fundamental to the secure implementation of blockchain in business and cybersecurity applications.
- Red Cluster: This group encompasses terms like digital assets, smart contracts, Ethereum, and NFTs, reflecting blockchain’s role in the digital economy, asset tokenization, and decentralized systems.
- Blue Cluster: This category focuses on the Internet of Things (IoT), consensus algorithms, and access control, highlighting the interplay between blockchain and automated digital ecosystems.
- Purple Cluster: This cluster includes open-source software and open systems, emphasizing collaboration and transparency in blockchain development.
Additionally, the graph reveals a strong emphasis on integrity and copyright protection, underlining the importance of securing digital assets within blockchain environments. Notably, there is significant interest in NFTs, with multiple studies exploring their applications and challenges. The distribution of thematic clusters indicates a strong research focus on copyright protection and digital assets, demonstrating blockchain’s expanding role across various sectors.
- RQ3: Which papers explore non-fungible tokens, copyright, integrity, software, and multichain?
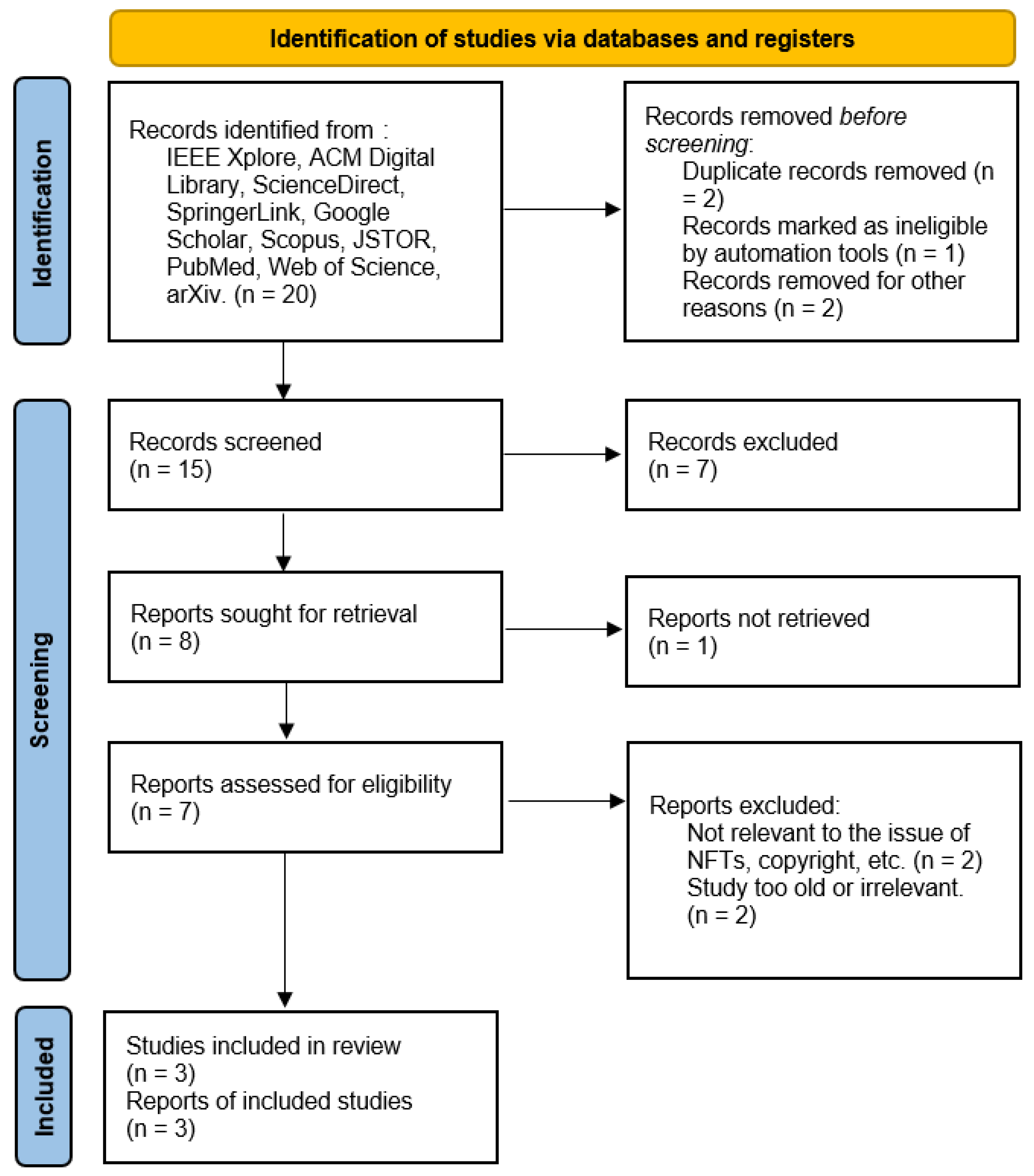
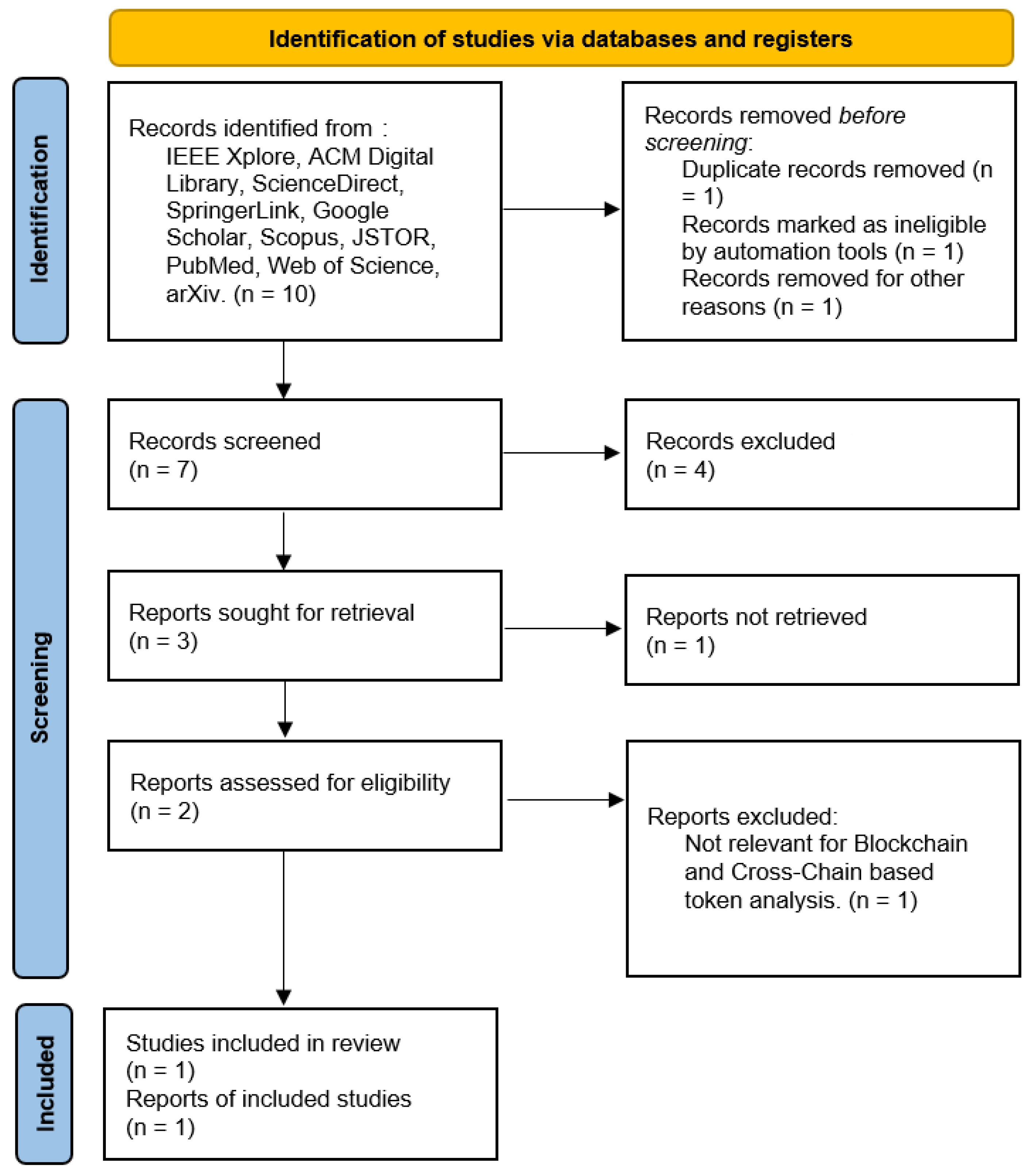
The PRISMA method applied to answer question 3 is shown in Figure 4:
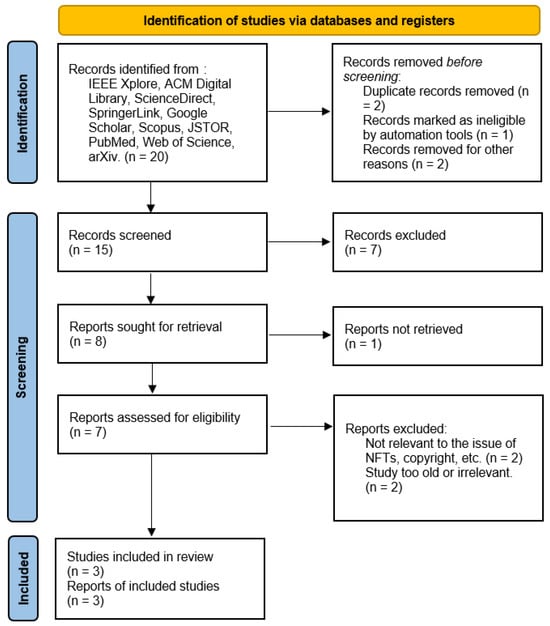
Figure 4.
PRISMA method applied to answer: Which papers explore non-fungible tokens, copyright, integrity, software, and mul-tichain?
In conducting the search for different articles that could be related to the subject matter, five articles were found that are reviews and share a similar approach in their research on the integration of Non-Fungible Tokens, copyright, integrity, software, and multichain, providing a detailed overview of how these technologies are being applied to ensure the protection and authenticity of software works. As shown in Table 3.

Table 3.
Papers that explore non-fungible tokens, copyright, integrity, software, and multichain.
- RQ4: Which of the papers explores Blockchain-based tokens and Cross-Chain (Smart Contract) as a review related?
The PRISMA method applied to answer question 4 is shown in Figure 5:
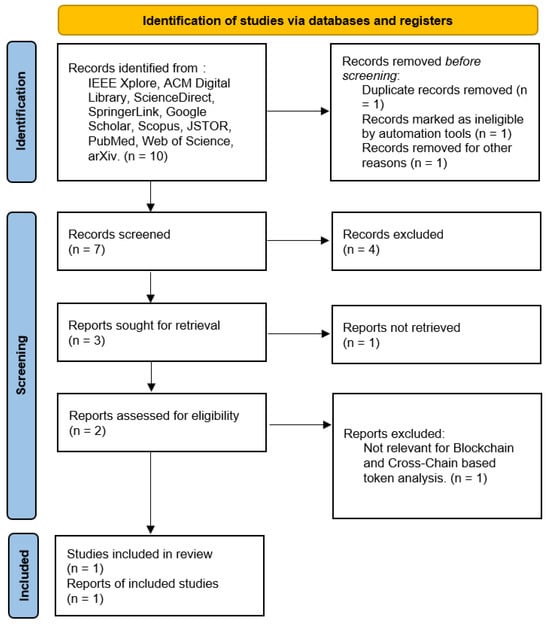
Figure 5.
PRISMA method applied to answer: Which of the papers explores Blockchain-based tokens and Cross-Chain (Smart Contract) as a review related?
The review of the articles reveals that several papers explore the use of Blockchain-based tokens and Cross-Chain solutions in the context of smart contracts. These studies focus on how these technologies can improve security, efficiency, and data management in various sectors, especially education and real estate. For example, one of the articles proposes a decentralized education system based on smart contracts that uses the Ethereum Virtual Machine (EVM) to manage academic certificates, eliminating bureaucracy and reducing costs. This system ensures compliance with regulations such as GDPR, providing a more secure and efficient solution for managing educational documents.
Another paper presents a conceptual framework for the adoption of Blockchain-based smart contracts in the smart city real estate sector. This study identifies key aspects and details the use of the EVM to develop these contracts, improving the user experience and benefiting property owners and real estate agents by aligning with Industry 4.0. In addition, solutions for Domain Name System (DNS) centralization using Blockchain are addressed, optimizing domain management and speeding up transactions.
As shown in Table 4, these papers highlight how the integration of Blockchain and Cross-Chain solutions can transform traditional sectors by implementing advanced technologies that improve transparency, security, and operational efficiency while complying with regulatory standards and offering new, more robust, and reliable business models.

Table 4.
Analysis of Blockchain-based tokens and Cross-Chain.
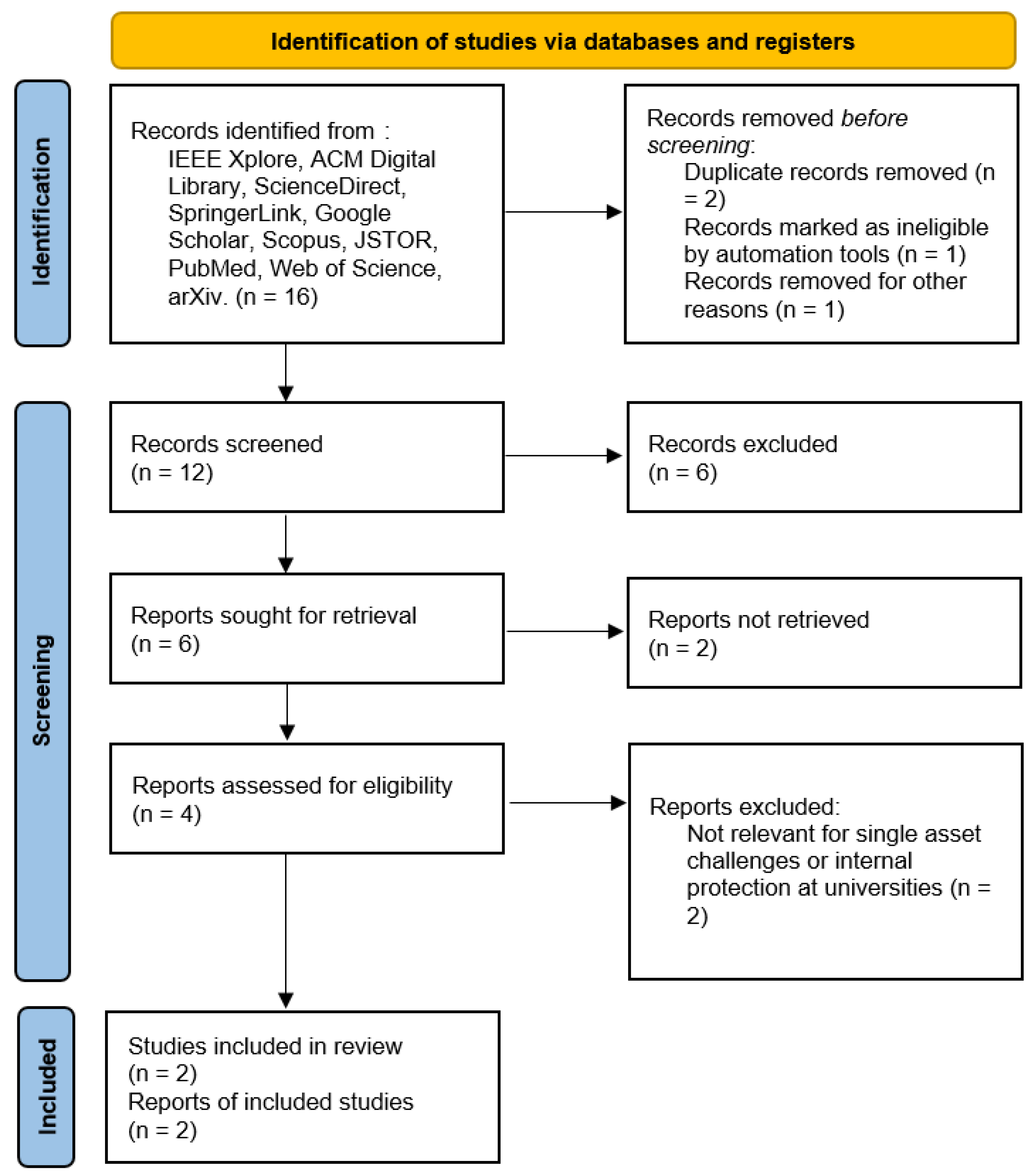
- RQ5: In the current landscape of Unique Asset of Digital content, what constitutes the primary challenges that Universities face regarding their internal protection processes?
The PRISMA method applied to answer question 5 is shown in Figure 6:
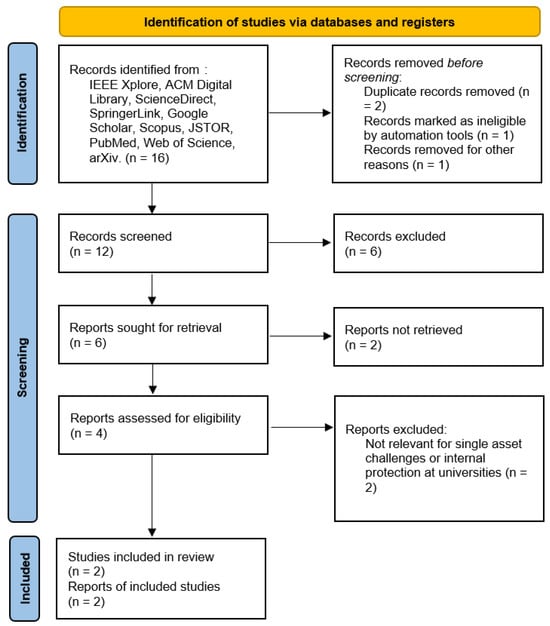
Figure 6.
PRISMA method applied to answer the question five.
While analyzing the articles, we noticed that they not only demonstrate the existence of a link between blockchain and various domains but also the possibility of how this relationship would ensure cohesion to protect the chain’s sanctity. The studies considered a range of issues related to the management of a university’s internal processes of information security for specific digital content. Among the challenges include data security and privacy, particularly where large chunks of information are involved and flow across devices, creating problems in the protection of privacy. However, blockchain technology is accompanied by performance and scalability problems, which include transactions per second, block size, and many others.
Another crucial factor is multichain, where there is a combination of more than one blockchain, and handling multiple blockchains comes with other complications, including the integration of blockchains. This also brings out the issue of social control and regulation since decentralization can create problems with governance and regulation. At long last, the future consequences of integrating blockchain into IoT are unknown, as they involve complex issues related to security, privacy, and coordination.
However, there exists a stark lack of strong protocols for the decentralized storage and authentication of patents, such as NFTs, and simple solutions on how the authenticity and ownership of these patents will be verified. As blockchain rises as a more crucial focus in handling digital assets, it is important to solve these challenges. The results are presented in Table 5.

Table 5.
Main challenges in the current landscape of unique assets or digital content and universities’ internal protection.
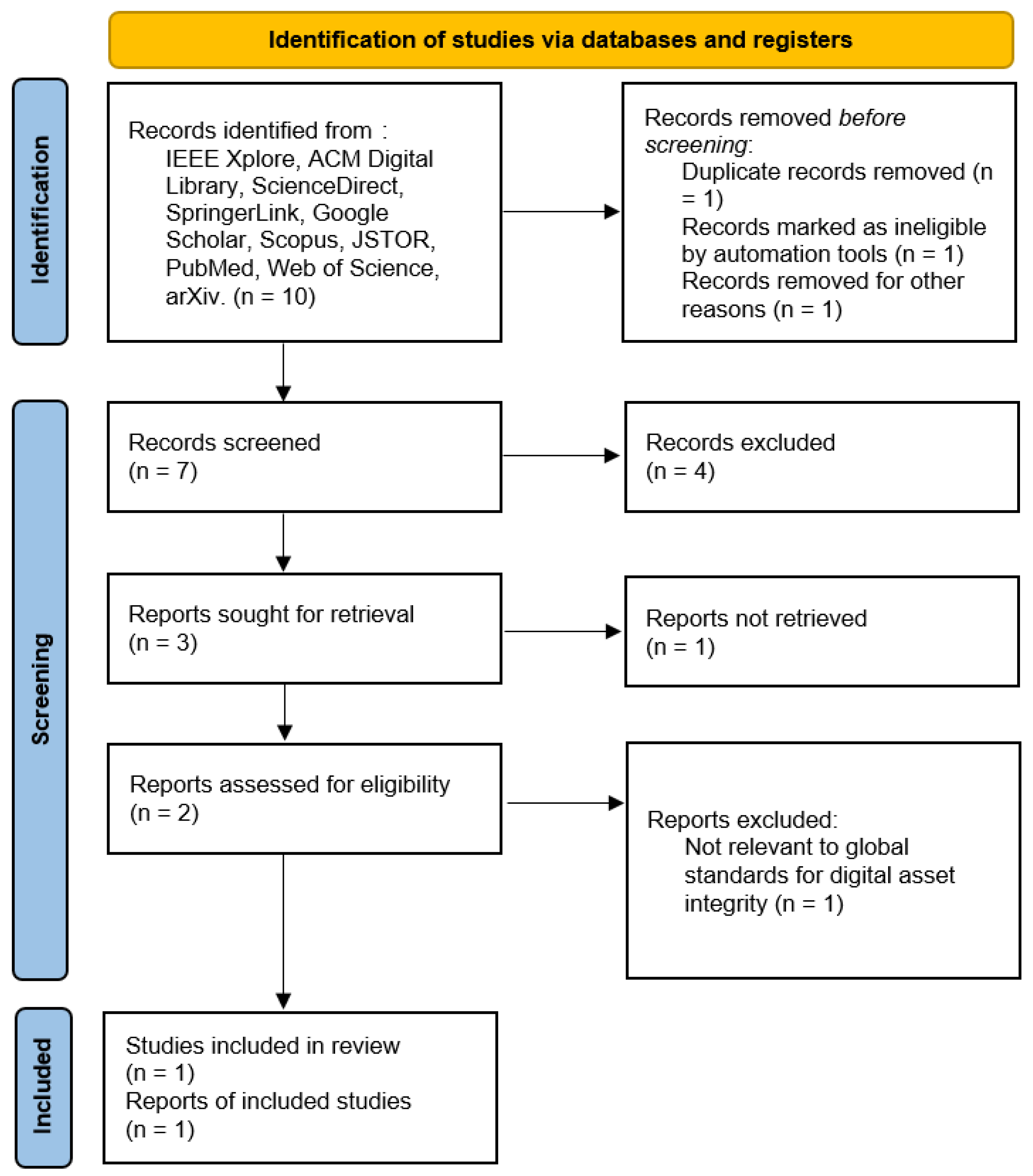
- RQ6: What global standards are used to safeguard the integrity and assets of digital content and media?
Thus, in the relatively short existence of digital culture, the issues of text and media integrity and protection appeared to be one of the key concerns. With the increased use of digital assets, there are also increased risks, such as hacking into the database, piracy, data loss, and theft of intellectual property. In response to these challenges, several international standards have been put in place to protect digital content and media. The PRISMA method applied to answer question 6 is shown in Figure 7:
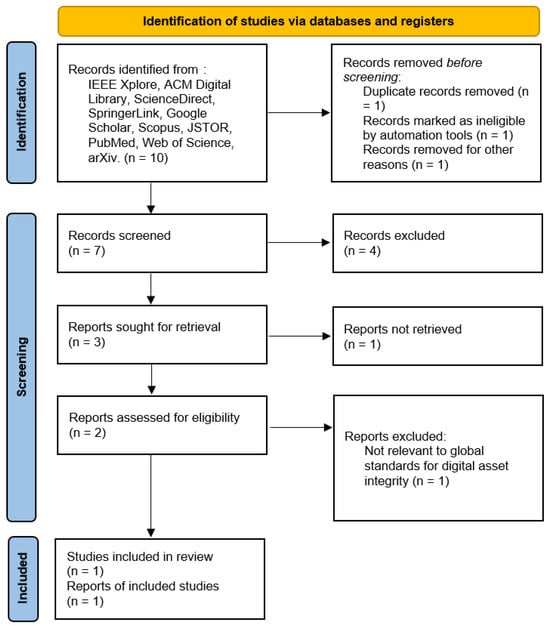
Figure 7.
PRISMA method applied to answer the question six.
These standards, developed by different international organizations, define frameworks and policies that assist organizations in protecting their digital resources, content, and intellectual property.
While reviewing the content of related works, it was found that, in addition to identifying the link between blockchain technology and various domains, attempts have also been made to identify ways to sustain this connection with the help of effective algorithms for the integrity and security of the blockchain. Some of the issues that these studies raise include data security and privacy, especially when using data on different devices. More specifically, there are concerns regarding performance and relative scalability, such as raw computing capacity and block size. When there are two or more blockchains, referred to as ‘multichain’, additionally issues arise, including coordination and communication between the blockchains, as well as social controls and regulation due to decentralization. In addition, the future usage of blockchain with the Internet of Things needs further assessment of its long-term effects on security, privacy, and efficiency.
Furthermore, the enhancement of proper solutions for the decentralized management and verification of virtual properties, for example, patents in the form of NFTs is increasing. A perfect match of geographically decentralized procedures of patent authenticity and propriety checking is also needed. Hence, given the role of digital asset protection in the modern blockchain landscape, these challenges need to be addressed properly. The following article aims to discuss some of the most common sets of standards globally found within this field with regard to their duties, application, and with special concern to the digital content and media industry. The details and results are presented in Table 6.

Table 6.
Global standards used to safeguard the integrity and assets of digital content and media.
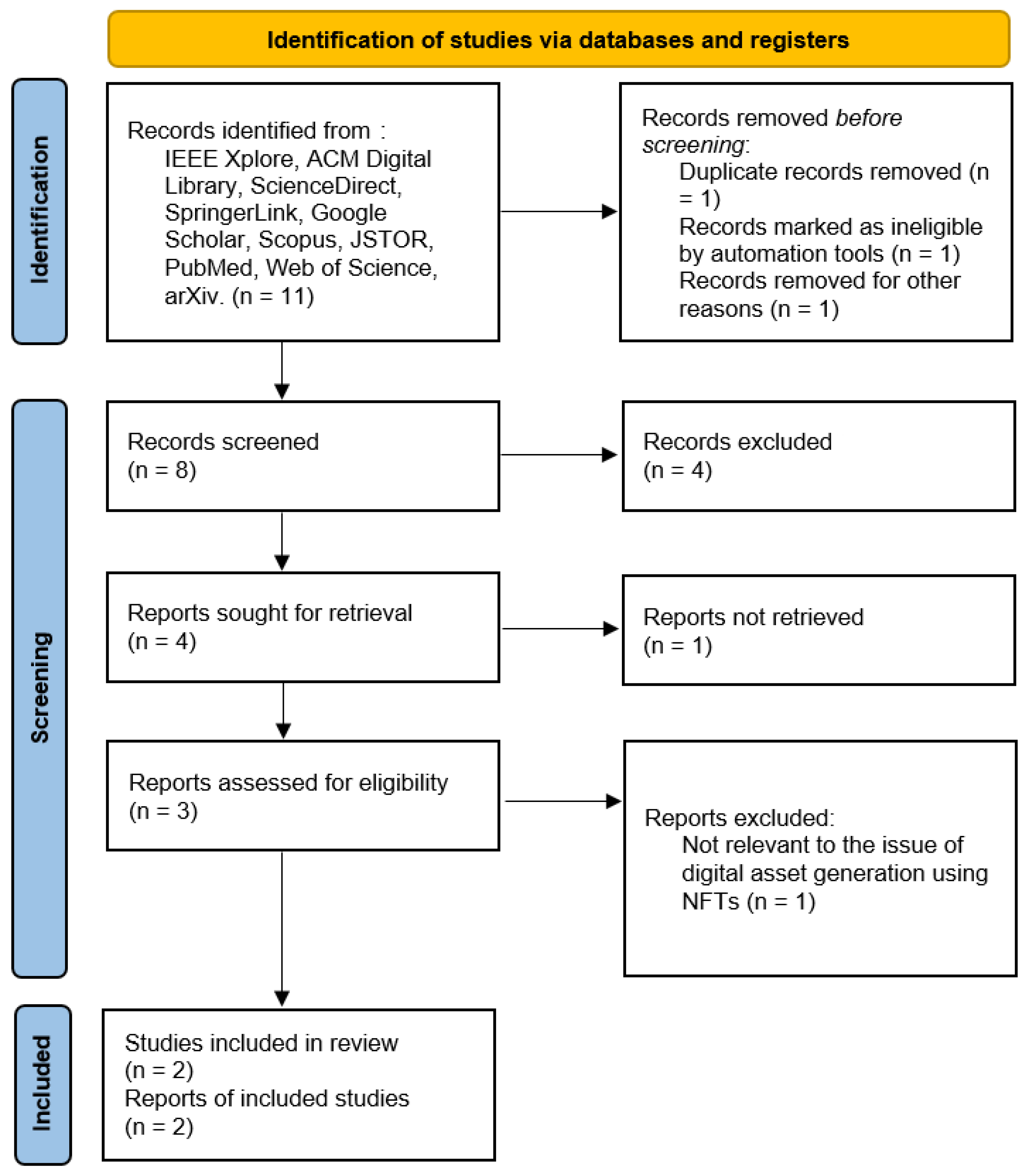
- RQ7: What types of NFTs are used to generate digital assets for content software and applications, and what methods and techniques are currently being utilized?
The PRISMA method applied to answer question 7 is shown in Figure 8:
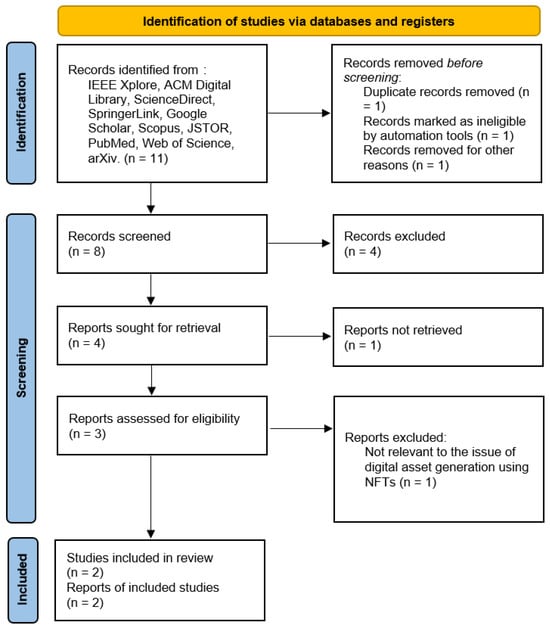
Figure 8.
PRISMA method applied to answer the question seven.
NFTs have become a significant change on the digital spectrum as it has presented an innovative method of attesting to the ownership and uniqueness of digital entities. Automatically and artificially, as exclusive cryptographic tokens, NFTs have been employed to provide provenance of digital assets and content, software, and applications. In doing so, original owners and creators are now able to monetize their work in breakthrough ways. NFTs’ rapidly increasing popularity concerns various fields in the sphere of digital assets, such as art, music, virtual land, and in-game items. This evolution has been caused by the need for secure and verifiable ownership in a digital environment, which is captured by NFTs using blockchain technology.
While analyzing articles identified in the previous stage, it was found that different kinds of NFTs are used to create digital assets regarding content software and applications. Some of them include utility NFTs, which grant the holder certain privileges in a digital ecosystem; collectible NFTs, which are widely used in gaming and virtual worlds; and functional NFTs, which are essential and embedded into the operational features of the software application. The studies also discussed the ways and means adopted in generating and developing these NFTs, along with focusing on the smart contracts that play an essential part in facilitating transactions and ownership regimes. Moreover, Ethereum and Binance Smart Chain are the most popular platforms for developing, trading, and storing NFTs, as they ensure safety and prevent tampering.
The constant creation and implementation of new NFTs for digital assets in content software and applications require that proper methods and appropriate techniques be developed to harness this technology. This article will strive to explore the current use of NFT types and the techniques applied in creating and handling them in the current market, with insights on future advancements of this progressive and innovative segment. Table 7 compiles the various methods and techniques used in the generation of digital assets.

Table 7.
Methods and techniques used in the generation of digital assets for content software and applications using NFTs.
4. Discussion
In analyzing the presented articles, several key contributions and areas of interest for future research in the field of digital content protection and data integrity using emerging technologies like blockchain were identified. The following discussion covers the results and challenges posed by the selected articles:
4.1. Integration of Hardware Security Modules (HSM) and Blockchain
This development in the Industrial-IoT domain from a security point of view is remarkable when HSM, along with blockchain technology, is integrated. This hardware-based root-of-trust is vital to protect against physical tampering and unauthorized access to critical systems, rendering an HSM essential for any organization currently [82]. When it comes to blockchain, HSMs are key management elements that enable the best encryption processes possible, improving the overall security architecture. This combination is particularly attractive in situations where the safekeeping of sensitive data is paramount, such as academic records management and certification processes in educational institutions [83]. However, interoperability and standard decryption require extensive overhead for multiple HSMs, as do hundreds of different blockchains. Future research should explore how standardized HSM-enabled blockchain solutions could enhance the integrity of academic credentials and digital rights in education.
4.2. Blockchain-Based Digital Rights Management (DRM)
The main advantages of using blockchain technology in DRM can be understood if one examines the shortcomings of traditional DRM systems, which can indeed be centralized and nontransparent [139]. The presented solution of utilizing blockchain ensures the possibility of effectively providing information on copyrights and transactions in an unchangeable and transparent manner to all parties interested in the process. The use of smart contracts makes the process of enforcing the rights concerning the copyright terms, as well as the issue of licenses, more efficient by eliminating the need for a central server and control and the associated issues with hacking and unauthorized access [128]. Despite such benefits, there are certain problems that arise during the shift to blockchain-based DRM systems: compliance with existing models of DRM, the problem of the blockchain’s ability to perform at varying scales, and the problem of developing an intuitive interaction with the system. However, a crucial gap exits in the definition of new legal concepts and subsequent regulation, adequate for blockchain applications in DRM. Further research should be focused on evaluating the feasibility of employing such methods, identifying the scalability solutions for implementing blockchain DRM systems on a large scale, and determining the legal requirements that would enable large-scale implementation of such systems in the global market [107].
4.3. Information-Sharing Platforms in the Scientific Community
Introducing the blockchain into the scientific community aligns with the solution to secure data sharing [37]. Conventional processes of exchanging data typically involve the help of a third party, and this can negatively affect the levels of trust, openness, and data quality. Blockchain, alongside such technologies as InterPlanetary File System (IPFS), forms a decentralized structure that increases data protection and makes record updates irreversible [68]. This is especially the case in the published literature, especially in the scientific literature, where the data generated must be accurate and reproducible. The proposed blockchain-based platforms enhance the security of data sharing, where smart contracts are used for the management of access control and data sharing agreement [100]. They are as follows: the scalability of the data, the expensive cost of storage on the blockchain, and questions on how to incorporate these technologies in research. It is recommended that future studies investigate the main methods of addressing such challenges, such as efficient data management, low transaction costs, and improved application of blockchain technology and systems to researchers.
4.4. Use of Non-Fungible Tokens (NFTs) in the Art Market
The application of NFTs in the art market is a new way of establishing the identity and ownership of digital art [115]. Through the incorporation of blockchain, NFTs confirm that a certain piece of content is original and unique. It could significantly disrupt the conventional art market since it will create new income sources for artists and the collectors will have more revenue to ensure that the works they are purchasing are original. Various challenges persist with the market for NFTs, including floppiness of the current market, effects on blockchains’ energy use, and little research on the economic effects of NFTs in the art market [47]. Thirdly, to achieve better and more efficient regulations of NFTs, there must be certain practices and legislation that could guarantee more safety for the artists, collectors, and investors. More studies should be conducted as to the future viability of NFTs, standard guidelines for their application, and the social and ecological impacts of blockchain in the art economy, as well as environmental and regulatory concerns related to blockchain and NFTs [110].
4.5. Education and Digital Competencies
This can be attributed to the fact that there seems to have been an increased rate of digitization across industries, including those in higher learning institutions’ areas of interest such as accounting and finance [34]. Since digital technologies such as blockchain are gradually integrating into these fields, the graduates need to be ready to operate in this environment. This comprises skills in the management of content in digital environments, distributed records in the blockchain, and autonomous decentralized systems of P2P nodes. Nonetheless, the current curricula offer a mismatch between the skills students are prepared for and the real-world expectations today [64]. Furthermore, many educators who are directly involved with teaching their students may not possess the know-how to teach the new technologies. To fill these gaps, future research should aim at designing more extensive teacher training programs, designing segmented and flexible curriculum models, and incorporating the processes by which learners engage with technologies in their curricular learning activities. This will not only equip students with knowledge on how to handle situations in an economy with prominent applications of the internet and technology but also enable educational institutions to remain relevant in a fast-changing world [90].
4.6. Addressing Implementation Challenges in Blockchain and NFTs for Academic Integrity
Despite the transformative potential of Blockchain and NFTs in securing academic intellectual property, several challenges hinder large-scale adoption in university environments. To overcome these barriers, targeted mitigation strategies must be developed to ensure seamless integration, usability, and regulatory compliance.
- Institutional Integration and Scalability Solutions: One of the primary concerns is the technical complexity involved in integrating Blockchain with existing LMS and institutional repositories. To facilitate this process, hybrid architectures combining off-chain storage (e.g., IPFS) with on-chain verification can optimize performance while maintaining decentralization. Additionally, permissioned blockchains offer a scalable alternative, allowing universities to control access while benefiting from Blockchain’s security features.
- Enhancing Adoption through User-Centered Design: For Blockchain and NFTs to gain traction in academia, ease of use is critical. Implementing intuitive user interfaces within university portals will lower the barrier for faculty and students. Moreover, comprehensive training programs should be introduced to familiarize users with Blockchain-based certification systems. Gamification strategies, such as rewarding students with NFT-based certifications for academic achievements, can also boost engagement and drive widespread adoption.
5. Conclusions
This review aimed to analyze the status and implementation of Blockchain and NFTs technologies in protecting the authenticity and intellectual property of source code within academic environments. Through a systematic examination of over 100 recent articles, this study has identified key advancements, persistent challenges, and future directions in the integration of these technologies. Over the past five years, academic interest in Blockchain and NFTs has increased steadily, particularly in areas related to security, digital certification methods, and code integrity.
The growing relevance of Blockchain and NFTs in ensuring the authenticity and ownership of software developments in academia is evident in the reviewed literature. The number of related publications has risen consistently since 2018, with notable peaks in 2021 and 2023. Most studies emphasize the need for enhanced security measures, highlighting Blockchain’s potential to ensure software traceability and integrity, while NFTs offer a unique capability to create immutable digital certificates for intellectual property protection.
However, several unresolved challenges remain, including scalability, efficiency, cost, integration complexity, quantum resistance, and the balance between centralization and decentralization. Addressing these issues is essential for fully unlocking the potential of Blockchain and NFTs in academic applications. Nevertheless, the reviewed studies propose various techniques and architectural improvements to mitigate these limitations, including advances in cryptographic methods, the integration of both on-chain and off-chain solutions, the use of Trusted Execution Environments (TEEs), and decentralized file storage solutions. Further research is required to optimize the trade-offs between scalability, efficiency, security, and privacy in Blockchain-based academic systems.
This review serves as a foundation for academics and practitioners seeking to advance the secure adoption of Blockchain and NFTs in educational environments. By summarizing both the progress made and the existing gaps, this study provides a basis for future research efforts in this evolving field. While these technologies present promising opportunities, additional studies are needed to develop practical solutions for secure, decentralized, and efficient systems that protect the intellectual property of software developments in academia. In this regard, this review establishes a reference point for further exploration, guiding future efforts toward meaningful integration and advancement in intellectual property protection and digital content integrity within academic institutions.
In conclusion, these technologies have promising possibilities in integration but there is still potential for further studies, which will make possible the formation of practical solutions for providing secure decentralized and efficient systems for managing and protecting the intellectual property of the software developments in academia. In this way, this review establishes the base and a starting point to proceed in this new field. In this paper, the current situation on the integration of Blockchain and NFTs has been described based on the literature available in the current world. Thus, in these conclusions, we have identified the most significant emerging limitations, gaps, and significant progress by analyzing relevant articles, as highlighted above. These conclusions are not meant to suggest specific solutions to the problems that have been identified; rather, these conclusions are meant to serve as a roadmap to help progress toward change and meaningful integration into the practices of intellectual property protection and authenticity of software developments in academic organizations.
Author Contributions
This review study includes the following individual contributions: Methodology, L.J.R.L.; Software, L.J.R.L. and G.G.M.L.; Validation, L.J.R.L.; Resources, L.J.R.L.; Formal analysis, G.G.M.L.; Data curation, G.G.M.L.; Writing—review and editing, L.J.R.L. and G.G.M.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The data that support the findings of this study are available from the corresponding author upon reasonable request.
Acknowledgments
The authors acknowledge Universidad El Bosque for supporting research project code AUX-2024-01-04 and for providing access to scientific databases.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Chiba, K.; Ito, H. Sublinear Computation Paradigm: Constant-Time Algorithms and Sublinear Progressive Algorithms. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2022, 105, 131–141. [Google Scholar] [CrossRef]
- Saimon, M.; Lavicza, Z.; Dana-Picard, T. Enhancing the 4Cs among College Students of a Communication Skills Course in Tanzania through a Project-Based Learning Model. Educ. Inf. Technol. 2023, 28, 6269–6285. [Google Scholar] [CrossRef] [PubMed]
- Han, S.; Nikou, S.; Ayele, W.Y. Digital Proctoring in Higher Education: A Systematic Literature Review. Int. J. Educ. Manag. 2024, 38, 265–285. [Google Scholar] [CrossRef]
- MIT. MIT Libraries: Copyright and Licensing. Available online: https://libraries.mit.edu/copyright/ (accessed on 14 August 2024).
- Stanford University. Software Intellectual Property. Available online: https://fairuse.stanford.edu/overview/faqs/software/ (accessed on 14 August 2024).
- Harvard University. Research Data Security & Safety. Available online: https://researchsupport.harvard.edu/research-data-security-and-safety (accessed on 14 August 2024).
- Cormen, T.H.; Leiserson, C.E.; Rivest, R.L.; Stein, C. Introduction to Algorithms, 3rd ed.; MIT Press: Cambridge, MA, USA, 2009. [Google Scholar]
- Massachusetts Institute of Technology. MIT License. Available online: https://memgraph.com/blog/what-is-mit-license (accessed on 14 August 2024).
- European Parliament and of the Council. Directive 2009/24/EC on the Legal Protection of Computer Programs and Their Licenses. Official Journal of the European Union, 23 April 2009. [Google Scholar]
- Lee, K.; Park, H. Copyright and Intellectual Property Law in East Asia. J. East Asian Stud. 2021, 15, 123–135. [Google Scholar]
- Direccion Nacional de Derechos de Autor. Guía Sobre Derechos de Autor en Colombia. Available online: https://www.derechodeautor.gov.co/es/guia-de-derecho-de-autor-para-creadores-y-usuarios (accessed on 14 August 2024).
- Stallman, R. Open Source Licensing: Ensuring Freedom in Digital Work. J. Softw. Freedom 2021, 7, 85–97. [Google Scholar]
- Kshetri, N.I. Digital Assets: Definition and Protection Strategies. J. Digit. Econ. 2023, 14, 25–35. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 14 August 2024).
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain Technology: Beyond Bitcoin. Appl. Innov. Rev. 2016, 2, 6–19. [Google Scholar]
- Tapscott, A.; Tapscott, D. Blockchain Revolution: How the Technology Behind Bitcoin and Other Cryptocurrencies Is Changing the World; Penguin Random House: New York, NY, USA, 2018. [Google Scholar]
- Mougayar, K. The Business Blockchain: Promise, Practice, and the Application of the Next Internet Technology; John Wiley & Sons: Hoboken, NJ, USA, 2016. [Google Scholar]
- Garay, J.A.; Kiayias, A. The Blockchain Model of Cryptography and Security. In Advances in Cryptology—CRYPTO 2015; Springer: Berlin/Heidelberg, Germany, 2015; Volume 9216, pp. 116–140. [Google Scholar]
- Hackett, R.A. The Future of Digital Assets: Blockchain and Beyond. Harv. Bus. Rev. 2022, 94, 45–53. [Google Scholar]
- O’Reilly, D. NFTs and Intellectual Property. J. Blockchain Res. 2022, 9, 97–108. [Google Scholar]
- Alizadeh, A. Tokenizing Intellectual Property: The Case for NFTs in Academia. J. Digit. Asset Manag. 2023, 18, 67–79. [Google Scholar]
- Buterin, V. Proof of Stake: The Making of Ethereum and the Philosophy of Blockchains; Seven Stories: New York, NY, USA, 2022; Available online: https://books.google.com/books?hl=es&lr=&id=hWpVEAAAQBAJ&oi=fnd&pg=PT7&ots=DWhtVvvJmA&sig=pCWL1yOdYtmC4X0H4PqC3fk0CqA (accessed on 14 August 2024).
- Han, H.; Shiwakoti, R.K.; Jarvis, R.; Mordi, C.; Botchie, D. Accounting and Auditing with Blockchain Technology and Artificial Intelligence: A Literature Review. Int. J. Account. Inf. Syst. 2023, 48, 100598. [Google Scholar] [CrossRef]
- Guo, H.; Yu, X. A Survey on Blockchain Technology and Its Security. Blockchain Res. Appl. 2022, 3, 100067. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. Proc. IEEE 2021, 106, 667–684. [Google Scholar]
- Lopes, H.S.; Rocha, F.; Vieira, F.H. Deep Reinforcement Learning Based Resource Allocation Approach for Wireless Networks Considering Network Slicing Paradigm. J. Commun. Inf. Syst. 2023, 38, 21–33. [Google Scholar]
- Basu, S.; Karmakar, S.; Bera, D. Blockchain-based Secured Virtual Machine Image Monitor. In Proceedings of the 7th International Conference on Information Systems Security and Privacy (ICISSP 2021), Online, 11–13 February 2021. [Google Scholar]
- Mishra, A.; Karmakar, S.; Dutta, A.; Bose, A.; Mohapatro, M. Design and Deployment of IoT Enabled Blockchain-Based Resilient Supply-Chain Management System using Ethereum. Int. J. Comput. Digit. Syst. 2022, 12, 1029–1050. [Google Scholar] [CrossRef]
- Tanwar, V.; Ramkumar, K.R. An Analysis of Blockchain and NFT Technologies and Their Drawbacks. In Proceedings of the 2023 2nd International Conference on Applied Artificial Intelligence and Computing (ICAAIC), Salem, India, 4–6 May 2023; IEEE: Piscataway, NJ, USA; pp. 1251–1259. [Google Scholar] [CrossRef]
- Wu, L.; Lu, W.; Peng, Z.; Webster, C. A Blockchain Non-Fungible Token-Enabled ‘Passport’ for Construction Waste Material Cross-Jurisdictional Trading. Autom. Constr. 2023, 149, 104783. [Google Scholar] [CrossRef]
- Ismail, S.; Reza, H.; Zadeh, H.K.; Vasefi, F. A Blockchain-Based IoT Security Solution Using Multichain. In Proceedings of the 2023 IEEE 13th Annual Computing and Communication Workshop and Conference (CCWC 2023), Las Vegas, NV, USA, 8–11 March 2023. [Google Scholar] [CrossRef]
- Ismailisufi, A.; Popovic, T.; Gligoric, N.; Radonjic, S.; Sandi, S. A Private Blockchain Implementation Using Multichain Open Source Platform. In Proceedings of the 2020 24th International Conference on Information Technology (IT 2020), Zabljak, Montenegro, 18–22 February 2020. [Google Scholar] [CrossRef]
- Koussema, R.A.; Haga, H. Highly Secure Residents Life Event Management System Based on Blockchain by Hyperledger Fabric. J. Comput. Commun. 2021, 9, 38–55. [Google Scholar] [CrossRef]
- Chen, Z.; Ding, W.; Xu, Y.; Tian, M.; Zhong, H. Fair Auctioning and Trading Framework for Cloud Virtual Machines Based on Blockchain. Comput. Commun. 2021, 171, 89–98. [Google Scholar] [CrossRef]
- Fekete, D.L.; Kiss, A. Toward Building Smart Contract-Based Higher Education Systems Using Zero-Knowledge Ethereum Virtual Machine. Electronics 2023, 12, 664. [Google Scholar] [CrossRef]
- Zichichi, M.; D’Angelo, G.; Ferretti, S.; Marzolla, M. Accountable Clouds Through Blockchain. IEEE Access 2023, 11, 48358–48374. [Google Scholar] [CrossRef]
- Ullah, F.; Al-Turjman, F. A Conceptual Framework for Blockchain Smart Contract Adoption to Manage Real Estate Deals in Smart Cities. Neural Comput. Appl. 2023, 35, 5033–5054. [Google Scholar] [CrossRef]
- Kumar, N.; Goel, V.; Ranjan, R.; Altuwairiqi, M.; Alyami, H.; Asakipaam, S.A. A Blockchain-Oriented Framework for Cloud-Assisted System to Countermeasure Phishing for Establishing Secure Smart City. Secur. Commun. Netw. 2023, 2023, 8168075. [Google Scholar] [CrossRef]
- Karagwal, S.; Tanwar, S.; Badotra, S.; Rana, A.; Jain, V. Blockchain for Internet of Things (IoT): Research Issues, Challenges, and Future Directions. In EAI/Springer Innovations in Communication and Computing; Springer: Cham, Switzerland, 2023; pp. 15–34. [Google Scholar] [CrossRef]
- Panduro-Ramirez, J.; Lourens, M.; Gehlot, A.; Singh, D.P.; Singh, Y.; Salunke, D.J. Blockchain Approach for Implementing Access Control in IoT. In Proceedings of the 2023 International Conference on Artificial Intelligence and Smart Communication (AISC), Greater Noida, India, 27–29 January 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 596–599. [Google Scholar] [CrossRef]
- Xu, H.; Liu, W.; Liu, X. Blockchain-Based Trust Auction for Dynamic Virtual Machine Provisioning and Allocation in Clouds. Wirel. Commun. Mob. Comput. 2021, 2021, 6639107. [Google Scholar] [CrossRef]
- Wang, S.; Wang, K.; Jia, L.; Yu, L.; Li, Z.; Sun, Y.; Li, J.; Zhou, J. Blockchain Smart Contract Virtual Machine Optimization Technology for Domain Name Systems. In Proceedings of the 2021 IEEE International Conference on Industrial Application of Artificial Intelligence (IAAI), Harbin, China, 24–26 December 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 445–451. [Google Scholar] [CrossRef]
- El Koshiry, A.; Eliwa, E.; El-Hafeez, T.A.; Shams, M.Y. Unlocking the power of blockchain in education: An overview of innovations and outcomes. Blockchain Res. Appl. 2023, 2023, 100165. [Google Scholar] [CrossRef]
- Kuznetsov, O.; Frontoni, E.; Kuznetsova, K.; Shevchuk, R.; Karpinski, M. NFT Technology for Enhanced Global Digital Registers: A Novel Approach to Tokenization. Future Internet 2024, 16, 252. [Google Scholar] [CrossRef]
- Wen, X. Application of Blockchain Technology in Copyright Protection of Digital Music Information. Int. J. Grid Util. Comput. 2023, 14, 136. [Google Scholar] [CrossRef]
- Amirta, R.; Deepika, M.S.; Franklin, R.G. Decentralized Access Control with Anonymous Authentication of Data Stored Using Blockchain. Res. J. Eng. Technol. 2020, 11, 10–14. [Google Scholar] [CrossRef]
- Yi, Y. Application of Blockchain Technology Based on Privacy Data Protection in RMB Internationalization Path. Mob. Inf. Syst. 2022, 2022, 1904593. [Google Scholar] [CrossRef]
- Riabi, I.; ben Ayed, H.K.; Zaghdoudi, B.; George, L. Blockchain-Based OAuth for IoT. In Proceedings of the 2021 10th IFIP International Conference on Performance Evaluation and Modeling in Wireless and Wired Networks (PEMWN 2021), Ottawa, ON, Canada, 23–25 November 2021. [Google Scholar] [CrossRef]
- Riaz, S.; Mushtaq, A.; Ibrar, H. Content Generation in Web 3.0 and Blockchain-Based Decentralized Social Networks: A Theoretical Adoption Framework. In Proceedings of the IEEE Region 10 Annual International Conference, Proceedings/TENCON, Hong Kong, China, 1–4 November 2022. [Google Scholar] [CrossRef]
- Kimura, K.; Imamura, M.; Omote, K. Cross-Referencing Scheme to Ensure NFT and Platform Linkage Unaffected by Forking. In Proceedings of the 2023 IEEE International Conference on Blockchain and Cryptocurrency (ICBC 2023), Dubai, United Arab Emirates, 1–5 May 2023. [Google Scholar] [CrossRef]
- Chan, W.; Gai, K.; Yu, J.; Zhu, L. Blockchain-Assisted Self-Sovereign Identities on Education: A Survey. Blockchains 2025, 3, 3. [Google Scholar] [CrossRef]
- Lo, S.K.; Staples, M.; Xu, X. Modelling Schemes for Multi-Party Blockchain-Based Systems to Support Integrity Analysis. Blockchain Res. Appl. 2021, 2, 100024. [Google Scholar] [CrossRef]
- Bae, Y.S.; Park, Y.; Lee, S.M.; Seo, H.H.; Lee, H.; Ko, T.; Lee, E.; Park, S.M.; Yoon, H.-J. Development of Blockchain-Based Health Information Exchange Platform Using HL7 FHIR Standards: Usability Test. IEEE Access 2022, 10, 79264–79271. [Google Scholar] [CrossRef]
- Reegu, F.A.; Abas, H.; Gulzar, Y.; Xin, Q.; Alwan, A.A.; Jabbari, A.; Sonkamble, R.G.; Dziyauddin, R.A. Blockchain-Based Framework for Interoperable Electronic Health Records for an Improved Healthcare System. Sustainability 2023, 15, 6337. [Google Scholar] [CrossRef]
- Arcenegui, J.; Arjona, R.; Baturone, I. Secure Management of IoT Devices Based on Blockchain Non-Fungible Tokens and Physical Unclonable Functions. Lect. Notes Comput. Sci. 2020, 12418, 24–40. [Google Scholar] [CrossRef]
- Alkadi, O.; Moustafa, N.; Turnbull, B.; Choo, K.K.R. A Deep Blockchain Framework-Enabled Collaborative Intrusion Detection for Protecting IoT and Cloud Networks. IEEE Internet Things J. 2021, 8, 9463–9472. [Google Scholar] [CrossRef]
- Guo, J.; Zhou, H.; Yang, L.; Chen, X. Research on Digital Copyright Blockchain Technology. In Proceedings of the 2020 3rd International Conference on Smart Blockchain, SmartBlock 2020, Zhengzhou, China, 23–25 October 2020. [Google Scholar] [CrossRef]
- Verma, M. The Study on Blockchain-Based Library Management and Its Characterization. Int. J. Trend Sci. Res. Dev. 2021, 5, 1147–1149. [Google Scholar]
- Lee, G. Legal Issues Related to Blockchain Technology—Examples from Korea. In Perspectives in Law, Business and Innovation; Springer: Singapore, 2020. [Google Scholar] [CrossRef]
- Song, Z.; Yu, Z.; Shang, W.; Li, Y.X. A Digital Copyright Protection Method Based on Blockchain. In Communications in Computer and Information Science; Springer: Singapore, 2021. [Google Scholar] [CrossRef]
- Patil, P.; Sangeetha, M.; Bhaskar, V. Blockchain for IoT Access Control, Security and Privacy: A Review. Wirel. Pers. Commun. 2021, 117, 1815–1834. [Google Scholar] [CrossRef]
- Shrestha, A.K.; Deters, R.; Vassileva, J. User-Controlled Privacy-Preserving User Profile Data Sharing Based on Blockchain. arXiv 2019, arXiv:1909.05028. [Google Scholar]
- Raj, A.; Kumar, A.; Sharma, V.; Rani, S.; Shanu, A.K. Enhancing Security Feature in Financial Transactions Using Multichain-Based Blockchain Technology. In Proceedings of the 4th International Conference on Intelligent Engineering and Management (ICIEM 2023), London, UK, 9–11 May 2023. [Google Scholar] [CrossRef]
- Li, X.; Luo, Q.; Yang, X.; Luo, N.; Xu, D.; Sun, C. Design and Implementation of Blockchain Hierarchical Supervision Model for Wheat Supply Chain. Nongye Jixie Xuebao/Trans. Chin. Soc. Agric. Mach. 2023, 54, 363–371. [Google Scholar] [CrossRef]
- Prata, D.N.; Araújo, H.X.; Santos, C. Blockchain Technology Applied to Education. Int. J. Adv. Eng. Res. Sci. 2019, 6, 295–298. [Google Scholar] [CrossRef]
- Meyliana; Surjandy; Fernando, E.; Widjaja, H.A.E.; Cassandra, C.; Tan, A.; Carolina, M.; Carolina, M. Blockchain Technology for Vehicle Maintenance Registration. In Proceedings of the 2021 International Conference on Information Management and Technology (ICIMTech 2021), Jakarta, Indonesia, 19–20 August 2021. [Google Scholar] [CrossRef]
- Prasad, N.B.L.V.; Pramodh, M.N.A.; Lalitha, R.V.S.; Kavitha, K.; Saritha, K. Tracking Industrial Assets Using Blockchain Technology. In Lecture Notes in Electrical Engineering; Springer: Singapore, 2022. [Google Scholar] [CrossRef]
- Huynh-The, T.; Gadekallu, T.R.; Wang, W.; Yenduri, G.; Ranaweera, P.; Pham, Q.; Benevides, D.; Liyanage, M. Blockchain for the metaverse: A Review. Future Gener. Comput. Syst. 2023, 143, 401–419. [Google Scholar] [CrossRef]
- Kim, C.G. A Study on Technology to Counter Copyright Infringement According to NFT Transaction Types. J. Semicond. Disp. Technol. 2021, 20, 187–191. [Google Scholar]
- Yang, W.; He, P.; Yang, Z.; Yi, X.; Chen, C. Digital Copyright Depository System Enhanced by Blockchain. In Proceedings of the 2020 International Conference on Culture-Oriented Science and Technology (ICCST 2020), Beijing, China, 28–31 October 2020. [Google Scholar] [CrossRef]
- Rafli, D.P.A.D. NFT Become a Copyright Solution. J. Digit. Law Policy 2022, 1, 87–96. [Google Scholar] [CrossRef]
- Altaf, A.; Iqbal, F.; Latif, R.; Yakubu, B.M.; Latif, S.; Samiullah, H. A Survey of Blockchain Technology: Architecture, Applied Domains, Platforms, and Security Threats. Soc. Sci. Comput. Rev. 2022, 41, 1941–1962. [Google Scholar] [CrossRef]
- Bamakan, M.; Nezhadsistani, N.; Bodaghi, O.; Qu, Q. A Decentralized Framework for Patents and Intellectual Property as NFT in Blockchain Networks. Comput. Math. Theor. Comput. Sci. 2021. [Google Scholar] [CrossRef]
- Qin, R.; Li, J.; Wang, X.; Zhu, J.; Yuan, Y.; Wang, F.Y. NFT: Blockchain-Based Non-Fungible Token and Applications. Chin. J. Intell. Sci. Technol. 2021, 3, 110–118. [Google Scholar] [CrossRef]
- Bellagarda, J.; Abu-Mahfouz, A.M. Connect2NFT: A Web-Based, Blockchain Enabled NFT Application with the Aim of Reducing Fraud and Ensuring Authenticated Social, Non-Human Verified Digital Identity. Mathematics 2022, 10, 3934. [Google Scholar] [CrossRef]
- Mazur, M. Non-Fungible Tokens (NFT). The Analysis of Risk and Return (31 October 2021). Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3953535 (accessed on 14 August 2024). [CrossRef]
- Chen, C.; Huang, H.; Zhao, B.; Shu, D.; Wang, Y. The Research of AHP-Based Credit Rating System on a Blockchain Application. Electronics 2023, 12, 887. [Google Scholar] [CrossRef]
- Taherdoost, H. Non-Fungible Tokens (NFT): A Systematic Review. Information 2023, 14, 26. [Google Scholar] [CrossRef]
- Ko, K.; Jeong, T.; Woo, J.; Hong, J.W. Survey on Blockchain-Based Non-Fungible Tokens: History, Technologies, Standards, and Open Challenges. Int. J. Netw. Manag. 2024, 34, e2245. [Google Scholar] [CrossRef]
- Manzoor, A.; Samarin, M.; Mason, D.; Ylianttila, M. Scavenger Hunt: Utilization of Blockchain and IoT for a Location-Based Game. IEEE Access 2020, 8, 204863–204879. [Google Scholar] [CrossRef]
- Hong, S.; Noh, Y.; Hwang, J.; Park, C. Fabasset: Unique Digital Asset Management System for Hyperledger Fabric. In Proceedings of the International Conference on Distributed Computing Systems, Singapore, 29 November–1 December 2020. [Google Scholar] [CrossRef]
- Uribe, D.; Waters, G. Privacy Laws, Genomic Data, and Non-Fungible Tokens. J. Br. Blockchain Assoc. 2020, 3. [Google Scholar] [CrossRef]
- Grech, A.; Sood, I.; Ariño, L. Blockchain, Self-Sovereign Identity and Digital Credentials: Promise Versus Praxis in Education. Front. Blockchain 2021, 4, 616779. [Google Scholar] [CrossRef]
- Cantu, A.; Geng, J.; Rong, C. NFT as a Proof of Digital Ownership-Reward System Integrated to a Secure Distributed Computing Blockchain Framework. In Proceedings of the International Conference on Cloud Computing Technology and Science (CloudCom), Bangkok, Thailand, 13–16 December 2022. [Google Scholar] [CrossRef]
- Lendo, R.; Jacobus, A.; Mapaly, H.A. Rancang Bangun Aplikasi Perpustakaan Digital Berbasis Mobile Menggunakan Framework Flutter. J. Tek. Inform. 2023, 18, 353–362. [Google Scholar] [CrossRef]
- Moreaux, A.C.; Mitrea, M.P. Royalty-Friendly Digital Asset Exchanges on Blockchains. IEEE Access 2023, 11, 56235–56247. [Google Scholar] [CrossRef]
- Turchet, L.; Ngo, C.N. Blockchain-Based Internet of Musical Things. Blockchain Res. Appl. 2022, 3, 100083. [Google Scholar] [CrossRef]
- Cheung, A.; Keung, J. On the Scrutinization of the NFT Valuation Factors. In Proceedings of the Asia-Pacific Software Engineering Conference (APSEC), Virtual Event, 6–9 December 2022. [Google Scholar] [CrossRef]
- Kucheryaviy, O. System of Professional-Digital Competencies of a Teacher of a Higher Pedagogical Educational Institution. Sci. Pedagog. Educ. 2022, 2, 44–49. [Google Scholar] [CrossRef]
- Casillo, M.; Colace, F.; Gupta, B.B.; Lorusso, A.; Marongiu, F.; Santaniello, D. Blockchain and NFT: A Novel Approach to Support BIM and Architectural Design. In Proceedings of the 2022 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT 2022), Sakheer, Bahrain, 20–21 November 2022. [Google Scholar] [CrossRef]
- Martínez Luna, W.F.; Moreno Ballesteros, A.M.; Ruiz Dorantes, E.J. Linking a Digital Asset to an NFT—Technical and Legal Analysis. Laws 2024, 13, 59. [Google Scholar] [CrossRef]
- Ante, L. Non-Fungible Token (NFT) Markets on the Ethereum Blockchain: Temporal Development, Cointegration and Interrelations. SSRN Electron. J. 2021, 32, 1216–1234. [Google Scholar] [CrossRef]
- Wu, C.-H.; Liu, C.-Y. Educational Applications of Non-Fungible Token (NFT). Sustainability 2023, 15, 7. [Google Scholar] [CrossRef]
- Islam, M.M.; In, H.P. Decentralized Global Copyright System Based on Consortium Blockchain with Proof of Authority. IEEE Access 2023, 11, 43101–43115. [Google Scholar] [CrossRef]
- Qureshi, A.; Jiménez, D.M. Blockchain-Based Multimedia Content Protection: Review and Open Challenges. Appl. Sci. 2021, 11, 1. [Google Scholar] [CrossRef]
- Kaushik, A.; Malik, M. Securing the Transfer and Controlling the Piracy of Digital Files Using Blockchain. In Proceedings of the 2022 5th International Conference on Computational Intelligence and Communication Technologies (CCICT 2022), Sonepat, India, 8–9 July 2022. [Google Scholar] [CrossRef]
- Ante, L. The Non-Fungible Token (NFT) Market and Its Relationship with Bitcoin and Ethereum. SSRN Electron. J. 2021. [Google Scholar] [CrossRef]
- Zagidullin, D.R.; Pulyavina, N.S. The Prospects for the Development of Blockchain Technology in the NFT Format. Lizing 2021, 1, 40–44. [Google Scholar] [CrossRef]
- Rasolroveicy, M.; Fokaefs, M. Performance and Cost Evaluation of Public Blockchain: An NFT Marketplace Case Study. In Proceedings of the 2022 4th Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), Paris, France, 27–30 September 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 79–86. [Google Scholar] [CrossRef]
- Sun, L.; Li, X.F.; Zhao, H.; Yu, B.; Zhou, T.; Li, X.R. NFT-Based Method for Assetization of Physical Assets on Blockchain. Zhejiang Daxue Xuebao (Gongxue Ban)/J. Zhejiang Univ. 2022, 56, 1900–1911. [Google Scholar] [CrossRef]
- Rudytsia, Y.; Bogdanova, N. UML Model of the Property Right Distribution Module Using NFT Fractionalization Based on Blockchain Technology. Int. Sci. J. Eng. Agric. 2022, 1, 98–109. [Google Scholar] [CrossRef]
- Gia, K.H.; Huong, L.H.; Vo, H.K.; Trong, P.N.; Dang, K.T.; Le Van, H.; Phu, L.V.C.; Quoc, D.N.T.; Tran, N.H.; The, A.N.; et al. Delivery Management System Based on Blockchain, Smart Contracts, and NFT: A Case Study in Vietnam. Int. J. Adv. Comput. Sci. Appl. 2023, 14. [Google Scholar] [CrossRef]
- Lee, Y.; Rathore, S.; Park, J.H.; Park, J.H. A Blockchain-Based Smart Home Gateway Architecture for Preventing Data Forgery. Hum.-Centric Comput. Inf. Sci. 2020, 10, 9. [Google Scholar] [CrossRef]
- Luan, B. On the Inheritance of National Music Culture in Colleges and Universities and the Reform and Innovation of Music Education in Colleges and Universities Under Blockchain Technology. In ACM International Conference Proceeding Series, Proceedings of the ICISCAE 2021: 2021 IEEE 4th International Conference on Information Systems and Computer Aided Education, Dalian, China, 24–26 September 2021; Association for Computing Machinery: New York, NY, USA, 2021. [Google Scholar] [CrossRef]
- Almajed, R.; Abualkishik, A.Z.; Ibrahim, A.; Mourad, N. Forecasting NFT Prices on Web3 Blockchain Using Machine Learning to Provide SAAS NFT Collectors. Fusion Pract. Appl. 2023, 10, 55–68. [Google Scholar] [CrossRef]
- Agudelo-Gonzalez, L.E.; Marta-Lazo, C.; Aguaded, I. Digital Competencies in the Journalism Curriculum: Case Analysis of a Central American University. Vivat Acad. 2022, 155, 297–317. [Google Scholar]
- Dowling, M. Is Non-Fungible Token Pricing Driven by Cryptocurrencies? Financ. Res. Lett. 2022, 44, 102097. [Google Scholar] [CrossRef]
- Mwanzu, A. Perceptions of Librarians on the Usefulness of DRM Technology in Protecting Against Copyright Violation. Libr. Philos. Pract. 2021, 2021, 5517. [Google Scholar]
- Sung, E.; Kwon, O.; Sohn, K. NFT Luxury Brand Marketing in the Metaverse: Leveraging Blockchain-Certified NFTs to Drive Consumer Behavior. Psychol. Mark. 2023, 40, 2306–2325. [Google Scholar] [CrossRef]
- Khan, P.W.; Byun, Y.C.; Park, N. A Data Verification System for CCTV Surveillance Cameras Using Blockchain Technology in Smart Cities. Electronics 2020, 9, 484. [Google Scholar] [CrossRef]
- Takahashi, H.; Lakhani, U. Voting Blockchain for High Security NFT. In Proceedings of the 2021 IEEE 10th Global Conference on Consumer Electronics (GCCE 2021), Kyoto, Japan, 12–15 October 2021. [Google Scholar] [CrossRef]
- Hari, M.K.; Agrawal, A.; Bhatia, R.; Bhatia, A.; Tiwari, K. T-PASS: A Blockchain-Based NFT Enabled Property Management and Exchange System. In Proceedings of the 2023 International Conference on Information Networking (ICOIN), Bangkok, Thailand, 11–14 January 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 140–145. [Google Scholar] [CrossRef]
- Wilson, K.B.; Karg, A.; Ghaderi, H. Prospecting Non-Fungible Tokens in the Digital Economy: Stakeholders and Ecosystem, Risk and Opportunity. Bus. Horiz. 2022, 65, 657–670. [Google Scholar] [CrossRef]
- Li, P. The Application of Blockchain and Cryptocurrency in Meta-Universe and NFT. BCP Bus. Manag. 2023, 44, 55–61. [Google Scholar] [CrossRef]
- Igarashi, T.; Kazuhiko, T.; Kobayashi, Y.; Kuno, H.; Diehl, E. Photrace: A Blockchain-Based Traceability System for Photographs on the Internet. In Proceedings of the 2021 IEEE International Conference on Blockchain, Blockchain 2021, Melbourne, Australia, 6–8 December 2021. [Google Scholar] [CrossRef]
- Cabrera-Gutierrez, A.J.; Castillo, E.; Escobar-Molero, A.; Alvarez-Bermejo, J.A.; Morales, D.P.; Parrilla, L. Integration of Hardware Security Modules and Permissioned Blockchain in Industrial IoT Networks. IEEE Access 2022, 10, 114331–114345. [Google Scholar] [CrossRef]
- Kräussl, R.; Tugnetti, A. Non-Fungible Tokens (NFTs): A Review of Pricing Determinants, Applications, and Opportunities. J. Econ. Surv. 2024, 38, 555–574. [Google Scholar] [CrossRef]
- Kholiavko, N.; Popelo, O.; Bazhenkov, I.; Shaposhnykova, I.; Sheremet, O. Information and Communication Technologies as a Tool of Strategy for Ensuring the Higher Education Adaptability to the Digital Economy Challenges. Int. J. Comput. Sci. Netw. Secur. 2021, 21, 187–195. [Google Scholar]
- Bamakan, S.M.H.; Nezhadsistani, N.; Bodaghi, O.; Qu, Q. Patents and Intellectual Property Assets as Non-Fungible Tokens: Key Technologies and Challenges. Sci. Rep. 2022, 12, 2178. [Google Scholar] [CrossRef]
- Far, S.B.; Bamakan, S.M.H.; Qu, Q.; Jiang, Q. A Review of Non-Fungible Tokens Applications in the Real-World and Metaverse. Procedia Comput. Sci. 2022, 214, 755–762. [Google Scholar] [CrossRef]
- Liu, C.; Zhang, X.; Chai, K.K.; Loo, J.; Chen, Y. A Survey on Blockchain-Enabled Smart Grids: Advances, Applications, and Challenges. IET Smart Cities 2021, 3, 56–78. [Google Scholar] [CrossRef]
- Jing, N.; Liu, Q.; Sugumaran, V. A Blockchain-Based Code Copyright Management System. Inf. Process. Manag. 2021, 58, 102518. [Google Scholar] [CrossRef]
- Ali, A.; Abideen, Z.U.; Ullah, K. SESCon: Secure Ethereum Smart Contracts by Vulnerable Patterns’ Detection. Secur. Commun. Netw. 2021, 2021, 2897565. [Google Scholar] [CrossRef]
- Hu, S. Improved Private Data Protection Scheme for Blockchain Smart Contracts. Int. J. Distrib. Sens. Netw. 2023, 2023, 5963039. [Google Scholar] [CrossRef]
- Barbosa, S.; Butler, R.; Pettey, C. A MultiChain-Based Homework Submission System. In Proceedings of the 2017 International Conference on Computational Science and Computational Intelligence (CSCI 2017), Las Vegas, NV, USA, 14–16 December 2017. [Google Scholar] [CrossRef]
- Naz, M.; Al-Zahrani, F.A.; Khalid, R.; Javaid, N.; Qamar, A.M.; Afzal, M.K.; Shafiq, M. A Secure Data Sharing Platform Using Blockchain and Interplanetary File System. Sustainability 2019, 11, 7054. [Google Scholar] [CrossRef]
- Chun, D. When the NFT Hype Settles, What Is Left Beyond Profile Pictures? A Critical Review on the Impact of Blockchain Technologies in the Art Market. Arts 2023, 12, 181. [Google Scholar] [CrossRef]
- Núñez-Gómez, C.; Garcia-Font, V. HyperNet: A Conditional k-Anonymous and Censorship Resistant Decentralized Hypermedia Architecture. Expert Syst. Appl. 2022, 208, 118079. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhao, L. A Design of Digital Rights Management Mechanism Based on Blockchain Technology. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2018. [Google Scholar] [CrossRef]
- Muthaiyah, S.; Phang, K.; Sembakutti, S. Bridging Skill Gaps and Creating Future-Ready Accounting and Finance Graduates: An Exploratory Study. F1000Research 2021, 10, 892. [Google Scholar] [CrossRef]
- Kumar, A.; Gupta, A.; Sanagavarapu, L.M.; Reddy, Y.R. An Approach to Open-Source Software License Management Using Blockchain-Based Smart Contracts. In ACM International Conference Proceeding Series, Proceedings of the ISEC 2022: 15th Innovations in Software Engineering Conference, Gandhinagar, India, 24–26 February 2022; Association for Computing Machinery: New York, NY, USA, 2022. [Google Scholar] [CrossRef]
- Liang, W.; Zhang, D.; Lei, X.; Tang, M.; Li, K.C.; Zomaya, A.Y. Circuit Copyright Blockchain: Blockchain-Based Homomorphic Encryption for IP Circuit Protection. IEEE Trans. Emerg. Top. Comput. 2021, 9, 1410–1420. [Google Scholar] [CrossRef]
- Chen, X.; Yang, A.; Weng, J.; Tong, Y.; Huang, C.; Li, T. A Blockchain-Based Copyright Protection Scheme with Proactive Defense. IEEE Trans. Serv. Comput. 2023, 16, 2316–2329. [Google Scholar] [CrossRef]
- Cai, Z. Usage of Deep Learning and Blockchain in Compilation and Copyright Protection of Digital Music. IEEE Access 2020, 8, 164144–164154. [Google Scholar] [CrossRef]
- Luo, L. Application of Blockchain Technology in Intellectual Property Protection. Math. Probl. Eng. 2022, 2022, 4641559. [Google Scholar] [CrossRef]
- Falco, G.; Siegel, J.E. Assuring Automotive Data and Software Integrity Employing Distributed Hash Tables and Blockchain: A Preprint. arXiv 2020, arXiv:2002.02780. [Google Scholar]
- Borandag, E. A Blockchain-Based Recycling Platform Using Image Processing, QR Codes, and IoT System. Sustainability 2023, 15, 6116. [Google Scholar] [CrossRef]
- Chen, C.; Li, Y.; Wu, Z.; Xu, M.; Wang, R.; Zheng, Z. Towards Reliable Utilization of AIGC: Blockchain-Empowered Ownership Verification Mechanism. IEEE Open J. Comput. Soc. 2023, 4, 326–337. [Google Scholar] [CrossRef]
- Ferro, E.; Saltarella, M.; Rotondi, D.; Giovanelli, M.; Corrias, G.; Moncada, R.; Cavallaro, A.; Favenza, A. Digital Assets Rights Management Through Smart Legal Contracts and Smart Contracts. Blockchain Res. Appl. 2023, 4, 100142. [Google Scholar] [CrossRef]
- Ma, Z.; Huang, W.; Gao, H. Secure DRM Scheme Based on Blockchain with High Credibility. Chin. J. Electron. 2018, 27, 1025–1036. [Google Scholar] [CrossRef]
- Zaidi, S.Y.A.; Shah, M.A.; Khattak, H.A.; Maple, C.; Rauf, H.T.; El-Sherbeeny, A.M.; El-Meligy, M.A. An Attribute-Based Access Control for IoT Using Blockchain and Smart Contracts. Sustainability 2021, 13, 10556. [Google Scholar] [CrossRef]
- Mentzer, K.; Price, J.; Powers, E.; Lavrenchuk, N. Examining the Hype Behind the Blockchain NFT Market. Issues Inf. Syst. 2022, 23, 15–29. [Google Scholar] [CrossRef]
- Jiang, Z.; Chen, K.; Wen, H.; Zheng, Z. Applying Blockchain-Based Method to Smart Contract Classification for CPS Applications. Digit. Commun. Netw. 2022, 8, 964–975. [Google Scholar] [CrossRef]
- ISO/IEC 21000-23:2022; Information Technology—Multimedia Framework (MPEG-21)—Part 23: Smart Contracts for Media. ISO: Geneva, Switzerland, 2022.
- Dev, A.; Shaji Gomez, K.; Mathew, S.V. NON-Fungible Tokens (NFT): New Emerging Digital Asset. Int. J. Res. Eng. Sci. (IJRES) 2022, 10, 1–7. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).