Failure Detection and Prevention for Cyber-Physical Systems Using Ontology-Based Knowledge Base
Abstract
:1. Introduction
2. Background and Related Work
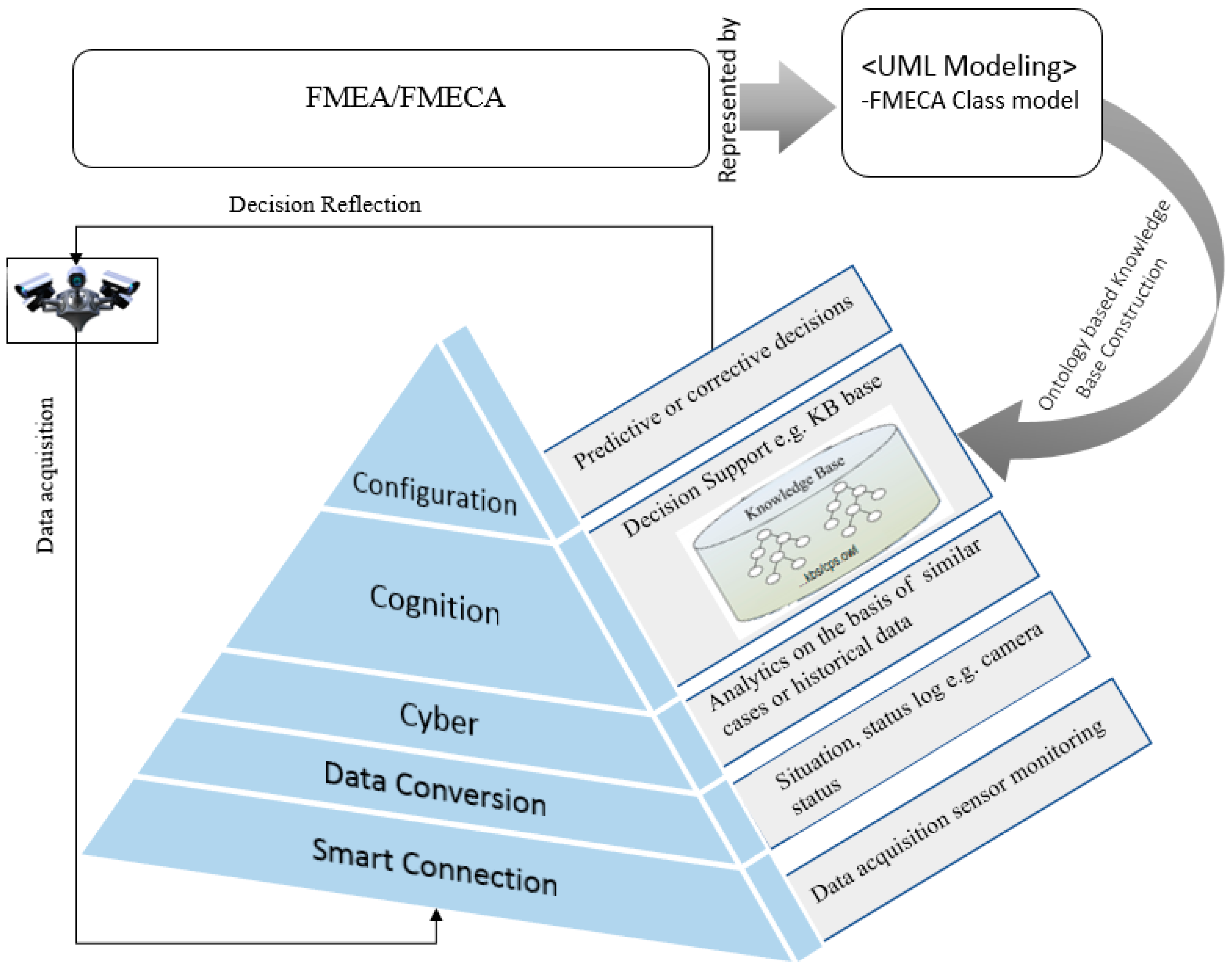
2.1. 5C Architecture
2.1.1. Smart Connection
2.1.2. Data-to-Information Conversion
2.1.3. Cyber
2.1.4. Cognition
2.1.5. Configuration
2.2. Ontology Engineering
2.3. Ontology and Cyber-Physical Systems
3. Proposed Approach
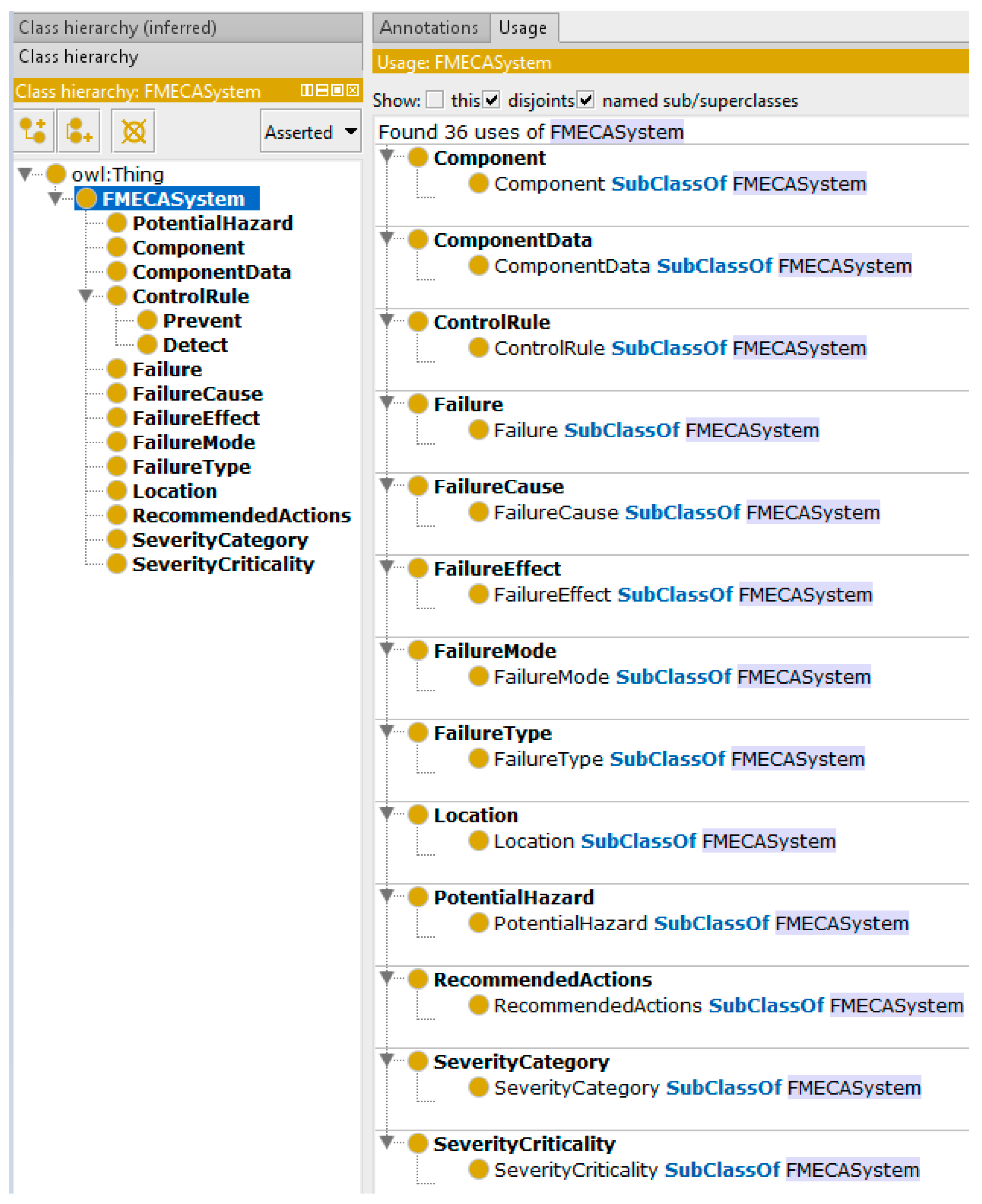
4. Implementation of FMECA Class Model
4.1. Presenting Class Hierarchy
4.2. Data Property and Object Property Representation
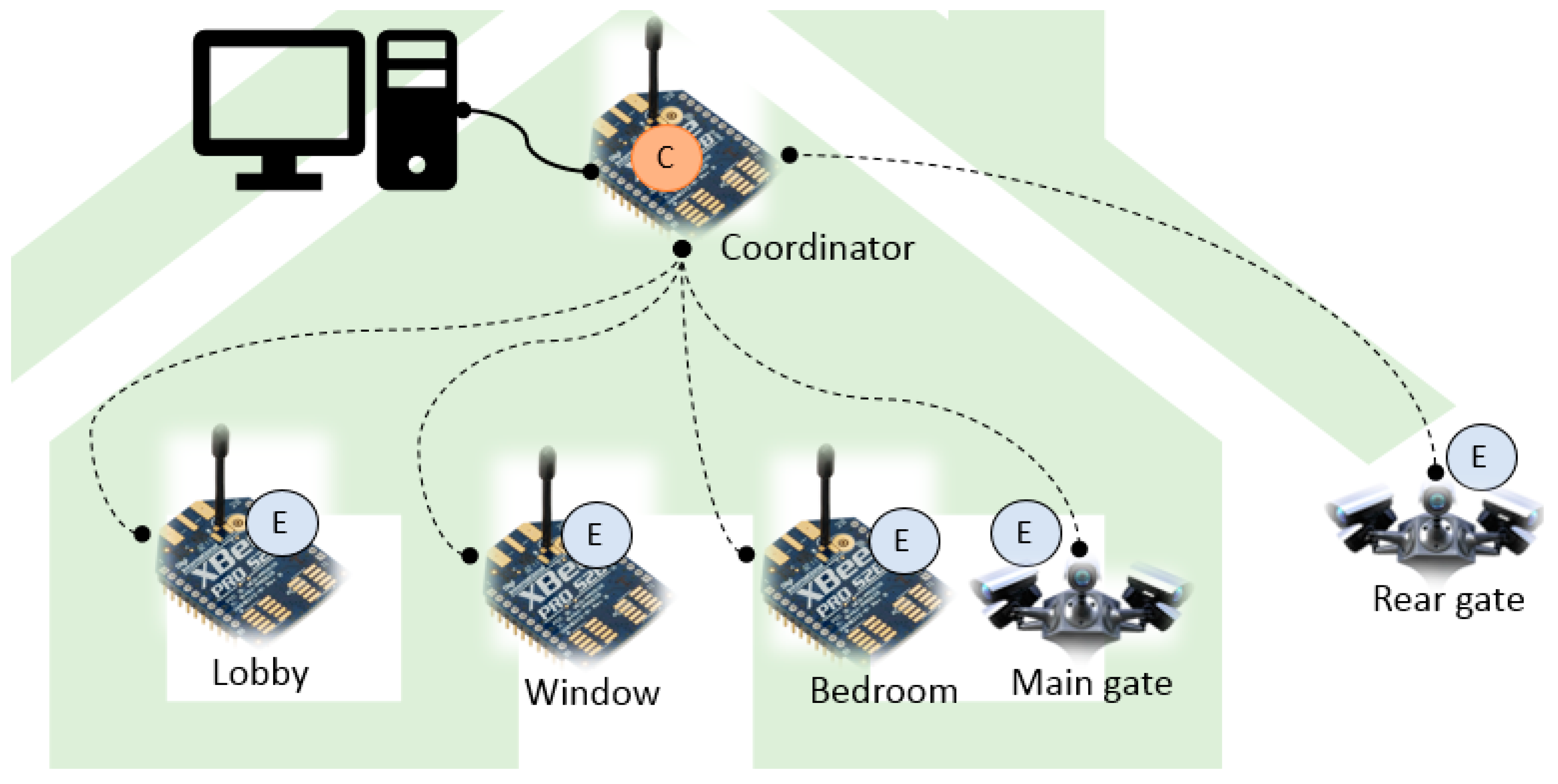
5. Approach Validation
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Nannapaneni, S.; Mahadevan, S.; Pradhan, S.; Dubey, A. Towards reliability-based decision making in cyber-physical systems. In Proceedings of the 2016 IEEE International Conference on Smart Computing (SMARTCOMP), St. Louis, MO, USA, 18–20 May 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Törngren, M.; Asplund, F.; Bensalem, S.; McDermid, J.; Passerone, R.; Pfeifer, H.; Sangiovanni-Vincentelli, A.; Schätz, B. Characterization, analysis, and recommendations for exploiting the opportunities of cyber-physical systems. In Cyber-Physical Systems; Elsevier Academic Press: Cambridge, MA, USA, 2017; pp. 1–14. [Google Scholar]
- Ghimire, S. Self-Evolutionary Cyber Physical Systems: Leap towards Smart CPS. Ph.D. Thesis, Universidade NOVA de Lisboa, Lisbon, Portugal, December 2016. [Google Scholar]
- NIST. Strategic R&D Opportunities for 21st Century Cyber-Physical Systems. Available online: http://www.nist.gov/el/upload/12-Cyber-Physical-Systems020113_final.pdf (accessed on 12 April 2018).
- Kabashkin, I.; Kundler, J. Reliability of Sensor Nodes in Wireless Sensor Networks of Cyber Physical Systems. Procedia Comput. Sci. 2017, 104, 380–384. [Google Scholar] [CrossRef]
- Sanislav, T.; Zeadally, S.; Mois, G.; Fouchal, H. Multi-agent architecture for reliable Cyber-Physical Systems (CPS). In Proceedings of the 2017 IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017; pp. 170–175. [Google Scholar] [CrossRef]
- Sanislav, T.; Zeadally, S.; Mois, G.D.; Fouchal, H. Reliability, failure detection and prevention in cyber-physical systems (CPSs) with agents. Concurr. Comput. Pract. Exp. 2018, e4481. [Google Scholar] [CrossRef]
- Nuñez, D.L.; Borsato, M. An ontology-based model for prognostics and health management of machines. J. Ind. Inf. Integr. 2017, 6, 33–46. [Google Scholar]
- Lee, J.; Bagheri, B.; Kao, H.A. A cyber-physical systems architecture for industry 4.0-based manufacturing systems. Manuf. Lett. 2015, 3, 18–23. [Google Scholar] [CrossRef]
- Kalaycı, İ.; Ercan, T. A framework model for data reliability in wireless sensor networks. In Proceedings of the Signal Processing and Communication Application Conference (SIU), Zonguldak, Turkey, 16–19 May 2016; pp. 1793–1796. [Google Scholar] [CrossRef]
- Jiang, W.; Zhuang, M.; Xie, C. A reliability-based method to sensor data fusion. Sensors 2017, 17, 1575. [Google Scholar] [CrossRef] [PubMed]
- Yuan, K.; Xiao, F.; Fei, L.; Kang, B.; Deng, Y. Modeling sensor reliability in fault diagnosis based on evidence theory. Sensors 2016, 16, 113. [Google Scholar] [CrossRef] [PubMed]
- Ahmadi, A.; Cherifi, C.; Cheutet, V.; Ouzrout, Y. A review of CPS 5 components architecture for manufacturing based on standards. In Proceedings of the SKIMA, International Conference on Software, Knowledge, Intelligent Management and Applications, Malabe, Sri Lanka, 6–8 December 2017. [Google Scholar]
- Lee, J.; Jin, C.; Liu, Z. Predictive big data analytics and cyber physical systems for TES systems. In Advances in Through-life Engineering Services; Springer: Cham, Switzerland, 2017; pp. 97–112. [Google Scholar]
- Kao, H.A.; Jin, W.; Siegel, D.; Lee, J. A cyber physical interface for automation systems—Methodology and examples. Machines 2015, 3, 93–106. [Google Scholar] [CrossRef]
- Brank, J.; Grobelnik, M.; Mladenić, D. A survey of ontology evaluation techniques. In Proceedings of the 8th International Multi-Conference Information Society, Ljubljana, Slovenia, 10–17 October 2005. [Google Scholar]
- Uschold, M.; King, M. Towards a methodology for building ontologies. 1995. Available online: http://www.aiai.ed.ac.uk/publications/documents/1995/95-ont-ijcai95-ont-method.pdf (accessed on 6 December 2018).
- Grüninger, M.; Fox, M.S. Methodology for the design and evaluation of ontologies. In Proceedings of the Workshop on Basic Ontological Issues in Knowledge Sharing, Montreal, QC, USA, 13 April 1995. [Google Scholar]
- López, M.F.; Gómez-Pérez, A.; Sierra, J.P.; Sierra, A.P. Building a chemical ontology using methontology and the ontology design environment. IEEE Intell. Syst. Their Appl. 1999, 14, 37–46. [Google Scholar] [CrossRef]
- Kozaki, K.; Kitamura, Y.; Mizoguchi, R. Developing Ontology-based Applications using Hozo. In Proceedings of the International Conference on Computational Intelligence, Alberta, Canada, 4–6 July 2005; pp. 273–277. [Google Scholar]
- Sure, Y.; Angele, J.; Staab, S. OntoEdit: Guiding ontology development by methodology and inferencing. In OTM Confederated International Conferences on the Move to Meaningful Internet Systems; Springer: Berlin/Heidelberg, Germany, 2002; pp. 1205–1222. [Google Scholar]
- García-Peñalvo, F.J.; Colomo-Palacios, R.; García, J.; Therón, R. Towards an ontology modeling tool. A validation in software engineering scenarios. Expert Syst. Appl. 2012, 39, 11468–11478. [Google Scholar] [CrossRef] [Green Version]
- Zhou, J.; Hänninen, K.; Lundqvist, K.; Provenzano, L. An ontological interpretation of the hazard concept for safety-critical systems. In Proceedings of the 27th European Safety and Reliability Conference ESREL’17, Portoroz, Slovenia, 18–22 June 2017; pp. 183–185. [Google Scholar]
- Zhou, J.; Hänninen, K.; Lundqvist, K.; Provenzano, L. An ontological approach to hazard identification for safety-critical systems. In Proceedings of the 2017 Second International Conference on Reliability Systems Engineering (ICRSE), Beijing, China, 10–12 July 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Zhou, J.; Hänninen, K.; Lundqvist, K.; Provenzano, L. An ontological approach to identify the causes of hazards for safety-critical systems. In Proceedings of the 2017 2nd International Conference on System Reliability and Safety (ICSRS), Milan, Italy, 20–22 December 2017; pp. 405–413. [Google Scholar] [CrossRef]
- Sanislav, T.; Mois, G. A dependability analysis model in the context of cyber-physical systems. In Proceedings of the 2017 18th International Carpathian Control Conference (ICCC), Sinaia, Romania, 28–31 May 2017; pp. 146–150. [Google Scholar] [CrossRef]
- Zhao, X.; Zhu, Y. Research of fmea knowledge sharing method based on ontology and the application in manufacturing process. In Proceedings of the 2010 2nd International Workshop on Database Technology and Applications (DBTA), Wuhan, China, 27–28 November 2010; pp. 1–4. [Google Scholar] [CrossRef]
- Zhao, L.; Ichise, R.; Sasaki, Y.; Liu, Z.; Yoshikawa, T. Fast decision making using ontology-based knowledge base. In Proceedings of the Intelligent Vehicles Symposium (IV), Gothenburg, Sweden, 19–22 June 2016; pp. 173–178. [Google Scholar] [CrossRef]
- Sureephong, P.; Chakpitak, N.; Ouzrout, Y.; Bouras, A. An ontology-based knowledge management system for industry clusters. In Global Design to Gain a Competitive Edge; Springer: London, UK, 2008; pp. 333–342. [Google Scholar]
- Sadik, A.R.; Urban, B. An Ontology-Based Approach to Enable Knowledge Representation and Reasoning in Worker–Cobot Agile Manufacturing. Future Internet 2017, 9, 90. [Google Scholar] [CrossRef]
- Törsleff, S.; Hildebrandt, C.; Daun, M.; Brings, J.; Fay, A. Developing Ontologies for the Collaboration of Cyber-Physical Systems: Requirements and Solution Approach. In Proceedings of the 2018 4th International Workshop on Emerging Ideas and Trends in the Engineering of Cyber-Physical Systems (EITEC), Porto, Portugal, 11 April 2018; pp. 25–32. [Google Scholar]
- Petnga, L.; Austin, M. An ontological framework for knowledge modeling and decision support in cyber-physical systems. Adv. Eng. Inform. 2016, 30, 77–94. [Google Scholar] [CrossRef] [Green Version]
- Coelhoa, M.; Austina, M.A.; Blackburnb, M.R. The Data-Ontology-Rule Footing: A Building Block for Knowledge-based Development and Event-driven Execution of Multi-Domain Systems. In Proceedings of the CSER 2018 16th Annual Conference on System Engineering Research, Charlottesville, VA, USA, 8–9 May 2018. [Google Scholar]
- Xu, F.; Liu, X.; Chen, W.; Zhou, C.; Cao, B. Ontology-Based Method for Fault Diagnosis of Loaders. Sensors 2018, 18, 729. [Google Scholar] [CrossRef] [PubMed]
- Maleki, E.; Belkadi, F.; Ritou, M.; Bernard, A. A Tailored Ontology Supporting Sensor Implementation for the Maintenance of Industrial Machines. Sensors 2017, 17, 2063. [Google Scholar] [CrossRef] [PubMed]
- González, E.; Marichal, R.; Hamilton, A. Software Experience for an Ontologybased Approach for the Definition of Alarms in Geographical Sensor Systems. IEEE Access 2018, 6, 55556–55572. [Google Scholar] [CrossRef]
- Alirezaie, M.; Renoux, J.; Köckemann, U.; Kristoffersson, A.; Karlsson, L.; Blomqvist, E.; Tsiftes, N.; Voigt, T.; Loutfi, A. An ontology-based context-aware system for smart homes: E-care@ home. Sensors 2017, 17, 1586. [Google Scholar] [CrossRef] [PubMed]
- Bouti, A.; Kadi, D.A. A state-of-the-art review of FMEA/FMECA. Int. J. Reliab. Qual. Saf. Eng. 1994, 1, 515–543. [Google Scholar] [CrossRef]
- FMEA-FMECA. Available online: http://www.fmea-fmeca.com/fmea-rpn.html (accessed on 6 December 2018).
- MIL-STD-1629. Available online: http://www.fmea-fmeca.com/milstd1629.pdf (accessed on 6 December 2018).
- ISO. Systems and Software Engineering–Architecture Description; ISO/IEC/IEEE 42010; IEEE: Piscataway, NJ, USA, 2011; pp. 1–46. [Google Scholar]
- Protégé 5.0. Available online: https://protege.stanford.edu/ (accessed on 6 December 2018).
- Horridge, M.; Jupp, S.; Moulton, G.; Rector, A.; Stevens, R.; Wroe, C. A practical guide to building owl ontologies using protégé 4 and co-ode tools edition 1.3. Available online: http://mowl-power.cs.man.ac.uk/protegeowltutorial/resources/ProtegeOWLTutorialP4_v1_3.pdf (accessed on 6 December 2018).
- Getting Started with the Intel® Galileo Board on Windows. Available online: https://software.intel.com/en-us/get-started-galileo-windows (accessed on 6 December 2018).
- Digi XBee/XBee-PRO ZigBee Modules (S2B)-Formerly ZB. Available online: https://www.digi.com/support/productdetail?pid=4549 (accessed on 6 December 2018).
- Next Generation Configuration Platform for XBee/RF Solutions. Available online: https://www.digi.com/products/xbee-rf-solutions/xctu-software/xctu (accessed on 6 December 2018).
- SPARQL Query Language for RDF. Available online: https://www.w3.org/TR/rdf-sparql-query/ (accessed on 5 December 2018).










© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, N.; Hong, J.-E. Failure Detection and Prevention for Cyber-Physical Systems Using Ontology-Based Knowledge Base. Computers 2018, 7, 68. https://doi.org/10.3390/computers7040068
Ali N, Hong J-E. Failure Detection and Prevention for Cyber-Physical Systems Using Ontology-Based Knowledge Base. Computers. 2018; 7(4):68. https://doi.org/10.3390/computers7040068
Chicago/Turabian StyleAli, Nazakat, and Jang-Eui Hong. 2018. "Failure Detection and Prevention for Cyber-Physical Systems Using Ontology-Based Knowledge Base" Computers 7, no. 4: 68. https://doi.org/10.3390/computers7040068
APA StyleAli, N., & Hong, J.-E. (2018). Failure Detection and Prevention for Cyber-Physical Systems Using Ontology-Based Knowledge Base. Computers, 7(4), 68. https://doi.org/10.3390/computers7040068




