A Multi-Hop Data Dissemination Algorithm for Vehicular Communication
Abstract
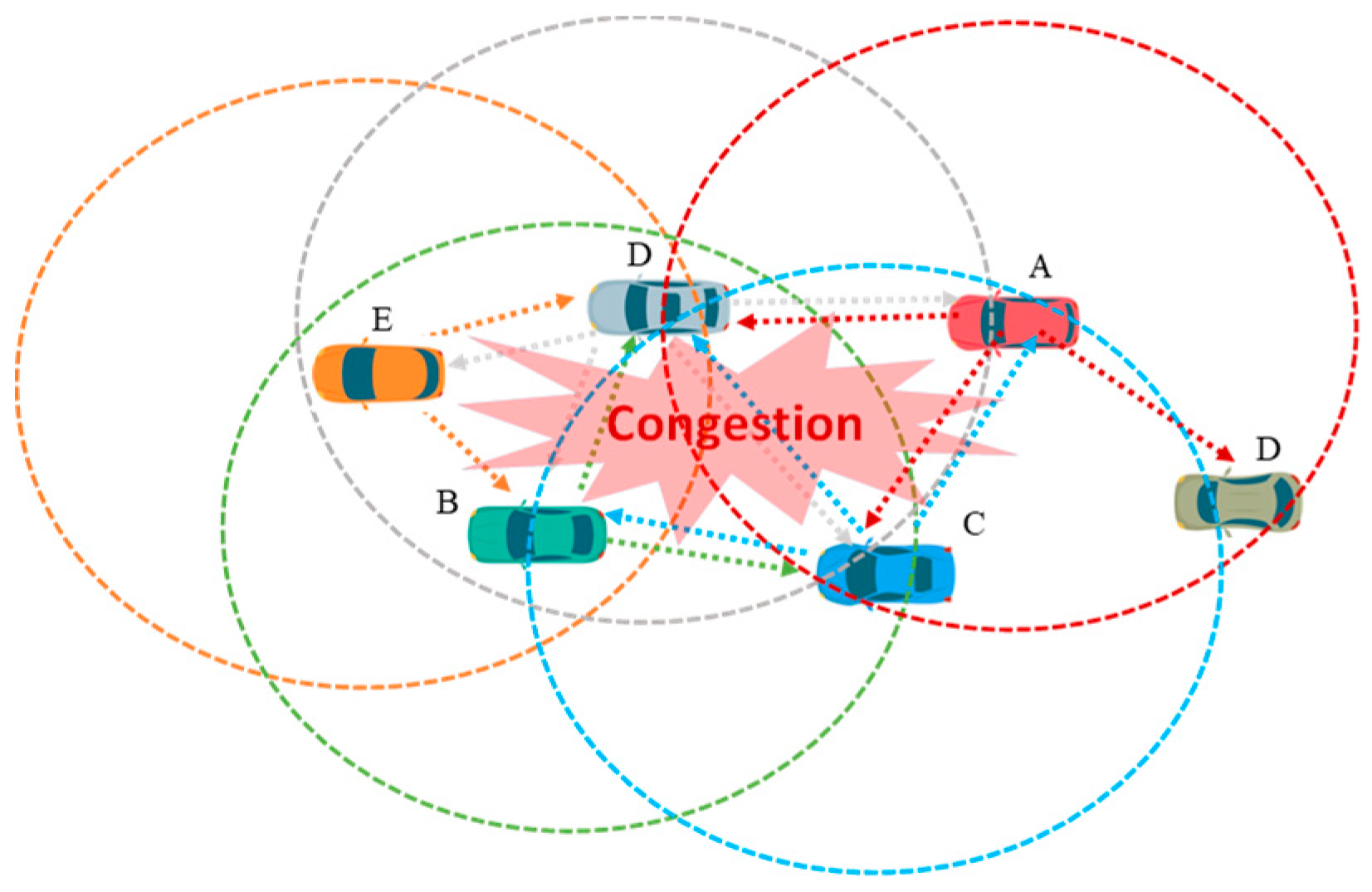
:1. Introduction
- The proposed algorithm can select a set of optimal relay vehicles in various network scenarios.
- Our approach quickly identifies the best relay neighbor using basic positional information. In this process, it also defines an upper sector area for each receiver, which is eventually converted to the retransmission back-off timer.
- In this scheme, a lane information of each neighbor is considered as one of the selection criteria. It is used in a such way that the neighbor in a closer lane is chosen as a relay node.
- This scheme provides unique retransmission back-off timer to each receiver so that the selected relay node can perform rebroadcast without facing a contention to channel access.
- This work also presents a broad simulation analysis for various system parameters in different network scenarios.
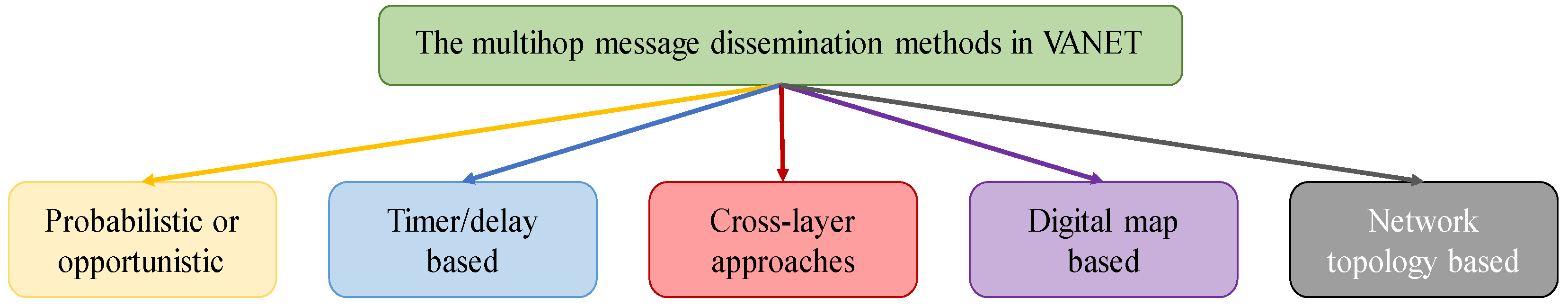
2. Related Works
2.1. Probabilistic or Opportunistic Method
2.2. Timer/Delay-Based Method
2.3. Cross-Layer Approach
2.4. Digital Map-Based Approach
2.5. Network Topology-Based Method
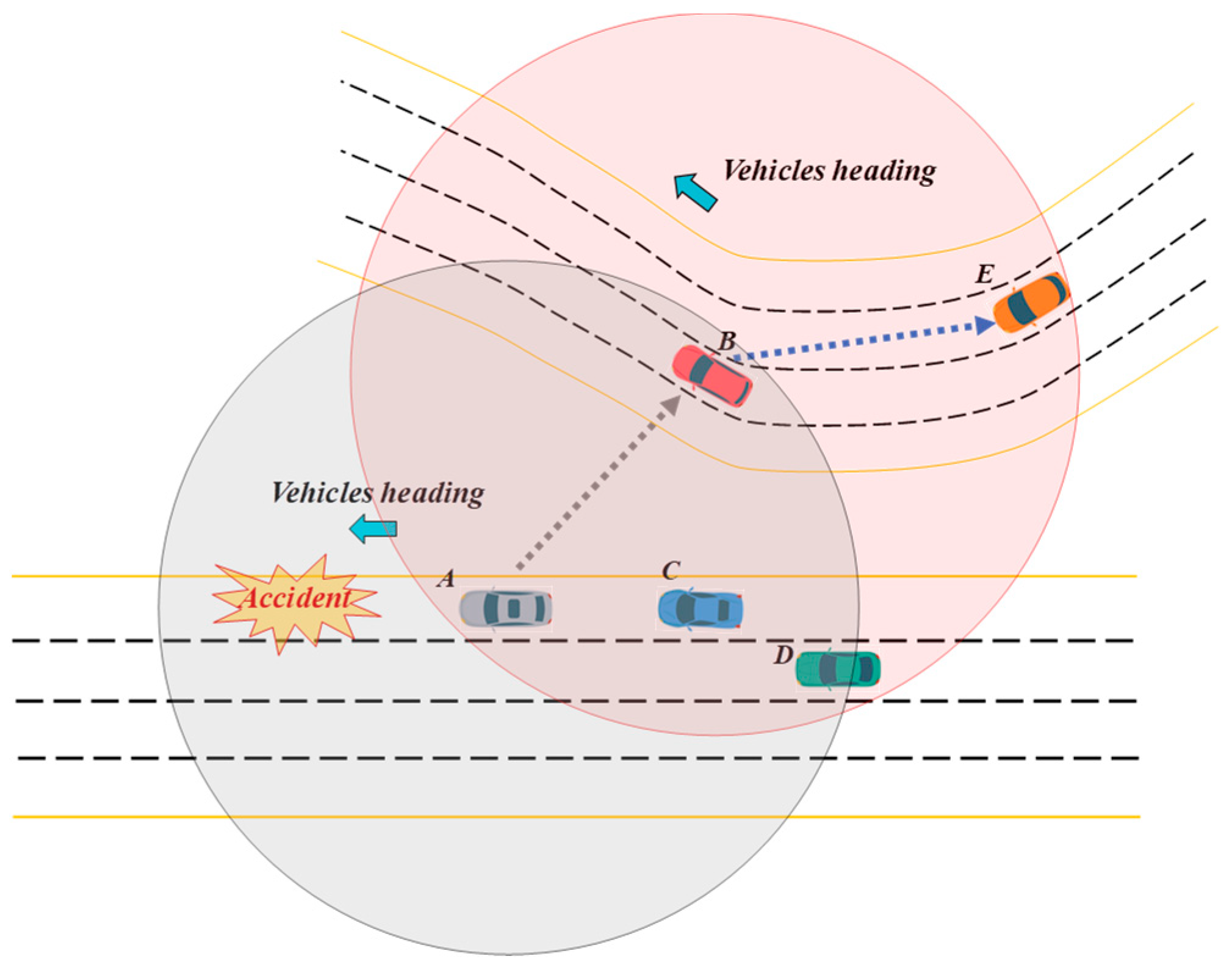
3. Proposed Method
3.1. Systems Model
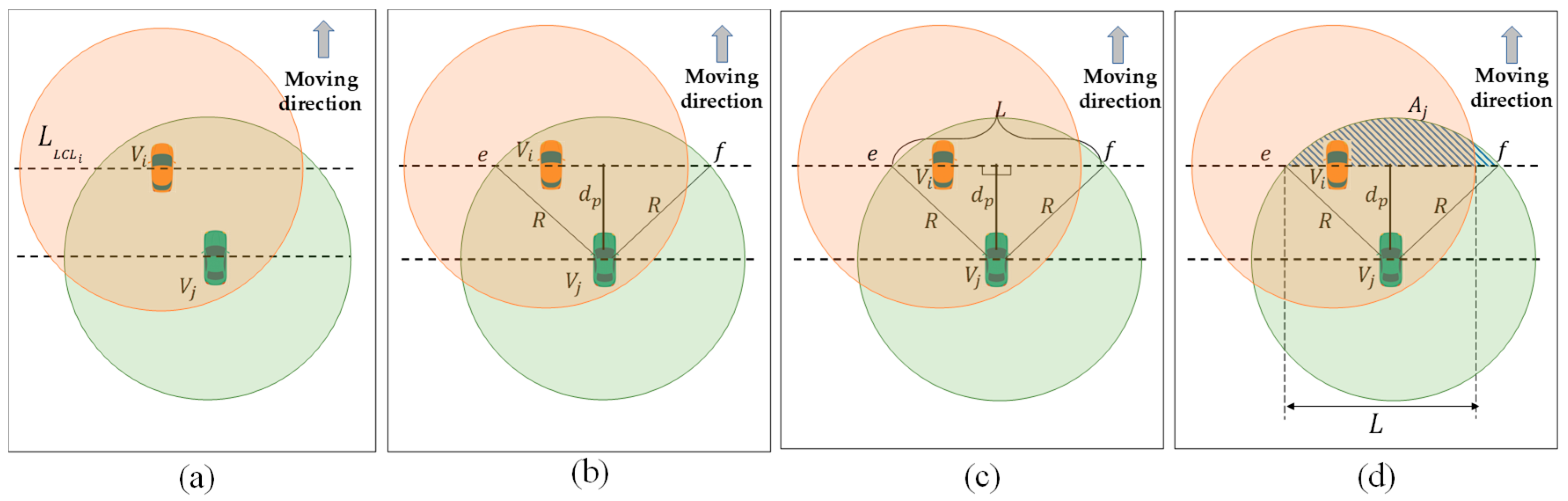
3.2. Definition of LCL Algorithm
| Algorithm 1: Lateral Crossing Line Based Forwarding | ||||
| Input parameters: | ||||
| transmitter and receiver, respectively, a multi-hop broadcast message received from , the wireless range, positional distance between and , LCL of , direction of message dissemination, width of lane, lateral distance between and | ||||
| Output: | ||||
| A unique back off timer for all ; | ||||
| 1 | /* calculate LCL of each */ | |||
| 2 | FOR each receiver of message DO | |||
| 3 | IFTHEN | |||
| 4 | IFTHEN | |||
| 5 | // source is heading west | |||
| 6 | ELSE IF | |||
| 7 | // source is heading east | |||
| 8 | END IF | |||
| 9 | ELSE | |||
| 10 | IFTHEN | |||
| 11 | // source is heading north | |||
| 12 | ELSE IF | |||
| 13 | // source is heading south | |||
| 14 | END IF | |||
| 15 | END IF | |||
| 16 | IFTHEN // in sparse network can be zero | |||
| 17 | ||||
| 18 | /* triangular area definition for neighbor j */ | |||
| 19 | ||||
| 20 | /* definition of lane position */ | |||
| 21 | ; | |||
| 22 | /* definition of waiting delay */ | |||
| 23 | ; // select corresponding | |||
| 24 | ELSE | |||
| 25 | ||||
| 26 | END IF | |||
| 27 | END FOR | |||
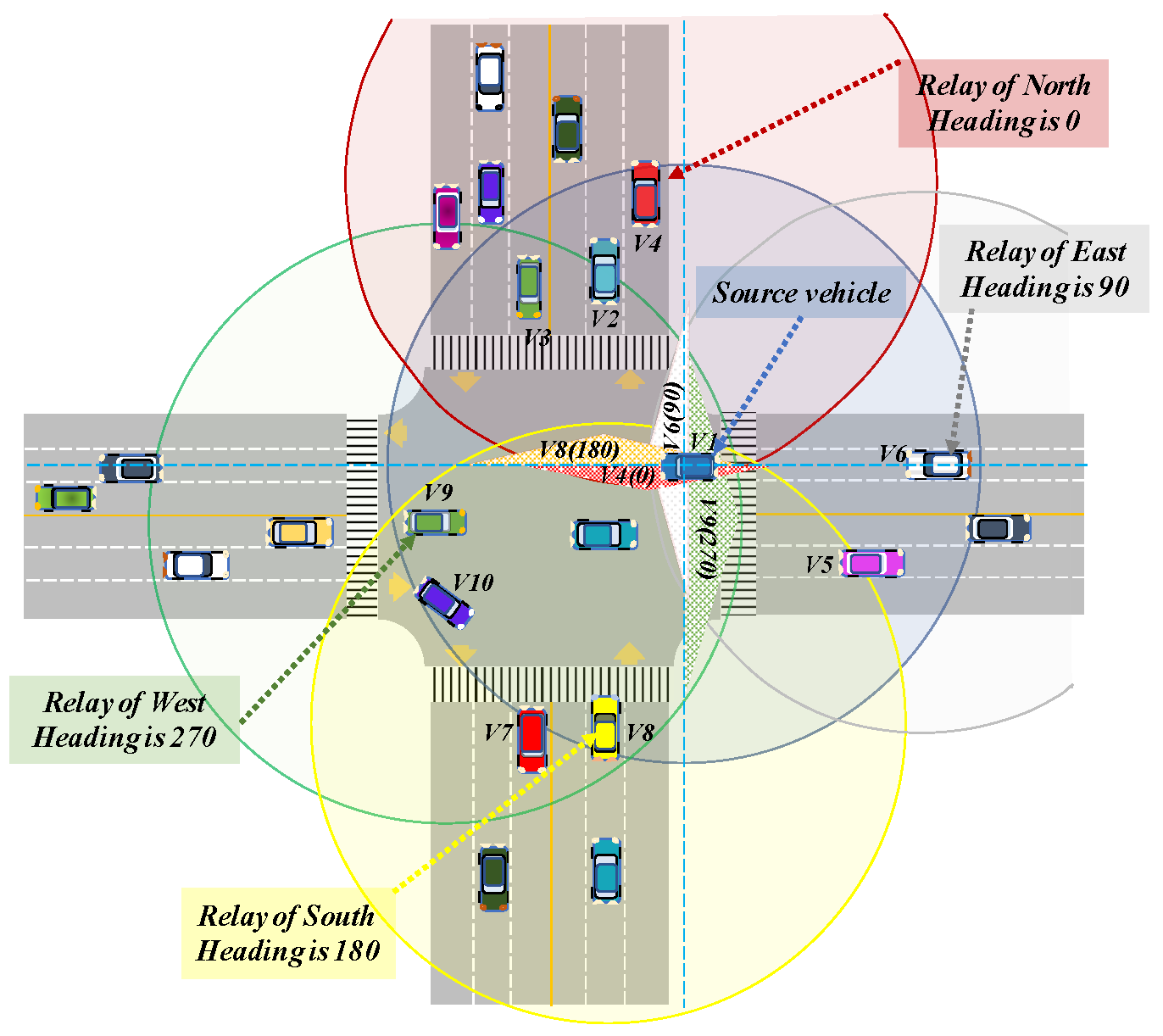
3.3. Message Dissemination in Intersection Area
| Algorithm 2: Relay Selection in Intersection Area | |||
| Input parameters: | |||
| distance to the on X axis, distance to the on Y axis, position details of intersection zone, the heading angle of , dissemination direction of event message received from , threshold distance set to limit the number of relay candidates, | |||
| Output: | |||
| Back off timer values ; | |||
| 8 | FOR each neighbor node of DO | ||
| 9 | IF the value of is DO | ||
| 10 | |||
| 11 | |||
| 12 | END IF | ||
| 13 | IFTHEN // in extreme sparse network, | ||
| 14 | |||
| 15 | ; | ||
| 16 | ELSE | ||
| 17 | |||
| 18 | END IF | ||
| 19 | IFDO | ||
| 20 | |||
| 21 | ; | ||
| 22 | ELSE | ||
| 23 | |||
| 24 | END IF | ||
| 25 | END FOR | ||
| 26 | IF is received from vehicle THEN | ||
| 27 | Dismiss the transmission scheduled to corresponding direction | ||
| 28 | END IF | ||
4. Simulation Parameters
- A multilane, two directional highway comprises 10 km length. The number of vehicles varies from 10 to 50 . Inter-vehicle distance value follows an exponential distribution, whereas speed of vehicles is uniformly distributed between 10~40 m/s.
- An urban environment with well-known Manhattan grid (2000 2000 ) comprise 3 3 blocks and four-ways intersections [32], as presented in Figure 10. All streets are two-way, with one lane in each direction. Car movements are constrained by these lanes. The direction of each node in every moment will be random. It cannot be repeated in two consecutive movements. Distance between two intersections is around 700 m. Speed of the vehicles is distributed randomly with 0.2 standard deviation. A density of the network varies from 12 and 62 .
- Average hop-to-hop delay—indicates average delays within each hop during propagation of data up to target distance;
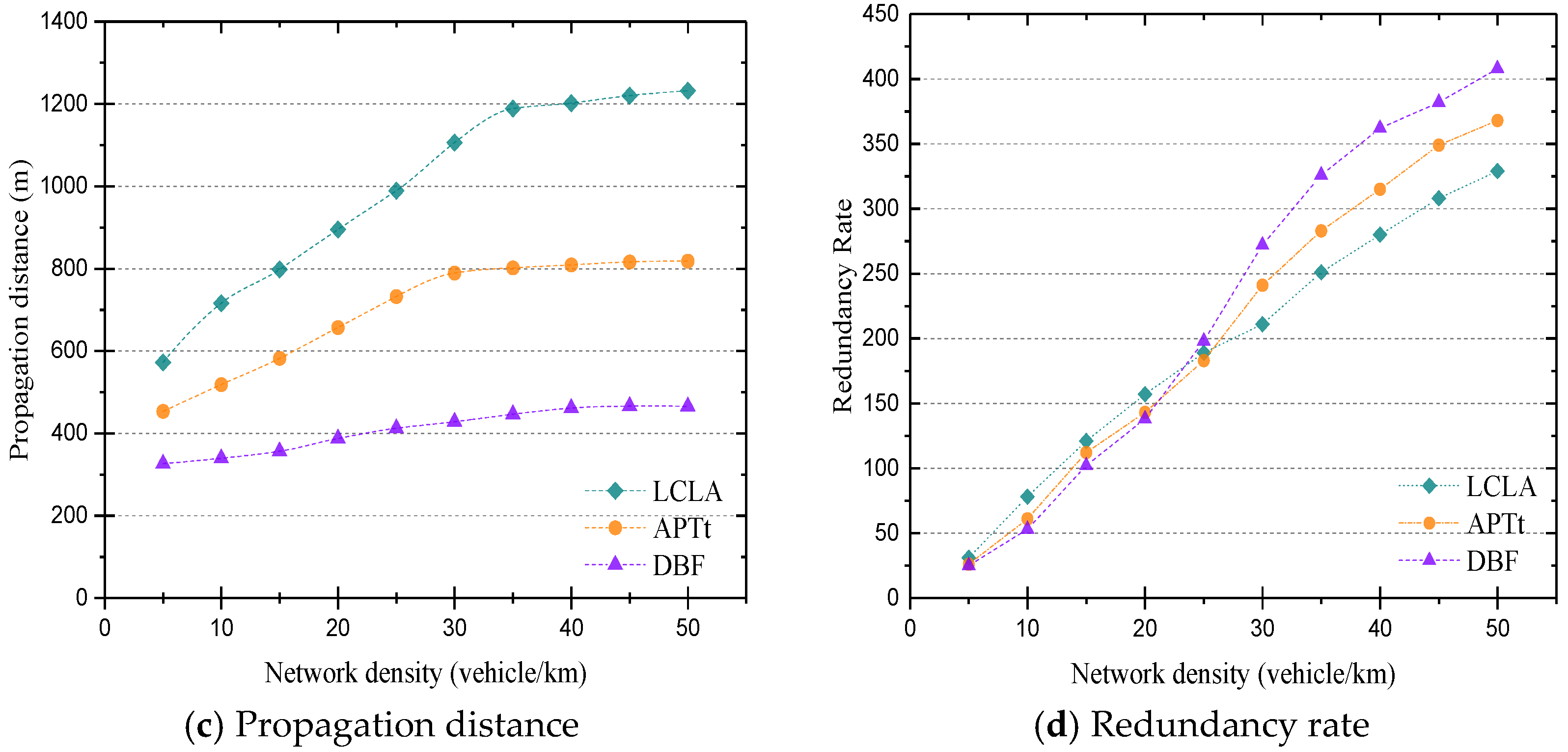
- Redundancy rate—represents the average number of duplicate messages received in each hop;
- Relay coverage—estimates the average number of vehicles covered by the relay node in each hop. This criterion shows how effective a selection method of relay node is;
- A propagation distance—indicates an average distance that a multi-hop broadcast message is delivered within the predefined period;
- A message delivery ratio within the relevant area—it the percentage of vehicles that received the message in a relevant area. This performance metric is evaluated only in an urban scenario.
5. Performance Analysis and Simulation Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Intelligent Transport Systems (ITS). Decentralized Congestion Control for Intelligent Transport Systems Operating in the 5 GHz Range; Access Layer Part; ETSI TS 102 687 V1.1.1 (2011-07); European Telecommunications Standards Institute: Valbonne, France, 2011. [Google Scholar]
- IEEE Standard for Wireless Access in Vehicular Environment (WAVE); IEEE Vehicular Technology Society Supported by the Intelligent Transmission Systems Committee; IEEE: Piscataway, NJ, USA, 2016; revised draft 2014.
- Annual Road Crash Statistics of Association of Safe International Road Travel. Available online: http://asirt.org/initiatives/informing-road-users/road-safety-facts/road-crash-statistics (accessed on 3 November 2019).
- Wisitpongphan, N.; Tonguz, O.K.; Parikh, J.S.; Mudalige, P.; Bai, F.; Sadekar, V. Broadcast storm mitigation technique in vehicular ad hoc networks. IEEE Wirel. Commun. 2007, 14, 84–94. [Google Scholar] [CrossRef]
- Schwartz, R.S.; Das, K.; Scholten, H.P. Having a Exploiting beacons for scalable broadcast data dissemination in VANETs. In Proceedings of the 9th ACM International Workshop on Vehicular Inter-Networking Systems and Applications, Newcastle, UK, 11–15 June 2012. [Google Scholar]
- Department of Transportation. National Highway Traffic Safety Administration 49 CFR Part 571; Docket No. NHTSA-2016-0126, RIN 2127-AL55; Federal Motor Vehicle Safety Standards; V2V Communications, Proposed Rules; National Highway Traffic Safety Administration (NHTSA), Department of Transportation (DOT): Washington, DC, USA, 2016.
- U.S. Department of Transportation. Vehicle Safety Communication Applications (VSA-A). In Final Report U.S. Department of Transportation; National Highway Traffic Safety Administration: Washington, DC, USA, 2011. [Google Scholar]
- Perkins, C.; Belding-Royer, E.; Das, S. Ad hoc On-Demand Distance Vector (AODV) Routing. RFC 3561. Available online: https://www.rfc-editor.org/info/rfc3561 (accessed on 11 November 2019).
- Tonguz, K.O.; Wisitpongphan, N.; Bai, F. DV-CAST: A distributed vehicular broadcast protocol for vehicular ad hoc networks. IEEE Wirel. Commun. 2010, 17, 2. [Google Scholar] [CrossRef]
- Viriyasitavat, W.; Tonguz, O.; Bai, F. UV-CAST: An urban vehicular broadcast protocol. IEEE Commun. Mag. 2011, 49, 116–124. [Google Scholar] [CrossRef]
- Leandro, A.V.; Boukerche, A.; Maia, G.; Pazzi, R.W.; Loureiro, A. Drive: An efficient and robust data dissemination protocol for highway and urban vehicular ad hoc networks. Comput. Netw. 2014, 75, 381–394. [Google Scholar]
- Briesemeister, L.; Hommel, G. Role-Based Multicast in Highly Mobile but Sparsely Connected Ad Hoc Networks. In Proceedings of the 2000 First Annual Workshop on Mobile and Ad Hoc Networking and Computing, Boston, MA, USA, 11 August 2000; pp. 45–50. [Google Scholar]
- Khan, A.; Cho, Z.Y. BL-CAST: Beacon-Less Broadcast Protocol for Vehicular Ad Hoc Networks. KSII Trans. Internet Inf. Syst. 2014, 8, 1223–1236. [Google Scholar]
- SAE International Standard for Dedicated Short Range Communications (DSRC) Message Set Dictionary J2735_200911. Available online: https://www.sae.org/standards/content/j2735_200911/ (accessed on 27 March 2020).
- Yair, A.; Michael, S. Cluster-Based Beaconing Process for VANET. Veh. Commun. 2015, 2, 80–94. [Google Scholar]
- Gupta, N.; Prakash, A.; Tripathi, R. Adaptive Beaconing in Mobility Aware Clustering Based MAC Protocol for Safety Message Dissemination in VANET Hindawi. Wirel. Commun. Mob. Comput. 2017, 2017, 1246172. [Google Scholar] [CrossRef] [Green Version]
- Alotaibi, M.M.; Mouftan, H.T. Relay Selection for Heterogeneous Transmission Power in VANETs. IEEE Access 2017, 5, 4870–4886. [Google Scholar] [CrossRef]
- Salvo, P.; Cuomo, A.B.; Rubin, I. Probabilistic relay selection in timer-based dissemination protocols for vanets. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014. [Google Scholar]
- Panichpapiboon, S.; Pattara-atikom, W. A review of information dissemination protocols for vehicular ad hoc networks. IEEE Commun. Surv. Tutor. 2011, 14, 784–798. [Google Scholar] [CrossRef]
- Li, M.; Zeng, K.; Lou, W. Opportunistic broadcast of event-driven warning messages in vehicular ad hoc networks with lossy links. Comput. Netw. 2011, 55, 2443–2464. [Google Scholar] [CrossRef]
- Bharati, S.; Zhuang, W. CRB: Cooperative Relay Broadcasting for Safety Applications in Vehicular Networks. IEEE Trans. Veh. Technol. 2016, 65, 9542–9553. [Google Scholar] [CrossRef]
- Chaqfeh, M.; Lakas, A. A novel approach for scalable multi-hop data dissemination in vehicular ad hoc networks. Ad Hoc Netw. 2016, 37, 228–239. [Google Scholar] [CrossRef]
- Bakhouya, M.; Gaber, J.; Lorenz, P. An adaptive approach for information dissemination in vehicular ad hoc networks. J. Netw. Comput. Appl. 2011, 34, 1971–1978. [Google Scholar] [CrossRef]
- Moussaoui, B.; Soufiene, D.; Mohamed, S.; John, M. A cross layer approach for efficient multimedia data dissemination in VANETs. Veh. Commun. 2017, 9, 127–134. [Google Scholar] [CrossRef]
- Zemouri, S.; Djahel, S.; Murphy, J. A fast, reliable and lightweight distributed dissemination protocol for safety messages in Urban Vehicular Networks. Ad Hoc Netw. 2015, 27, 26–43. [Google Scholar] [CrossRef] [Green Version]
- Fogue, M.; Piedad, G.; Francisco, J.M.; Juan-Carlos, C.; Carlos, T.C.; Pietro, M. Evaluating the impact of a novel message dissemination scheme for vehicular networks using real maps. Transp. Res. Part C Emerg. Technol. 2012, 25, 61–80. [Google Scholar] [CrossRef]
- Liu, X.; Yan, G. Analytically modeling data dissemination in vehicular ad hoc networks. Ad Hoc Netw. 2016, 52, 17–27. [Google Scholar] [CrossRef]
- Baiocchi, A. Analysis of timer-based message dissemination protocols for inter-vehicle communications. Transp. Res. Part B Methodol. 2016, 90, 105–134. [Google Scholar] [CrossRef]
- Eyobu, O.S.; Joo, J.; Han, D.S. CMD: A Multichannel Coordination Scheme for Emergency Message Dissemination in IEEE 1609.4. Mob. Inf. Syst. 2018, 2018, 9876437. [Google Scholar]
- Xie, X.; Liao, W.; Aghajan, H.; Veelaert, P.; Philips, W. Detecting Road Intersections from GPS Traces Using Longest Common Subsequence Algorithm. ISPRS Int. J. Geo-Inf. 2017, 6, 1. [Google Scholar] [CrossRef] [Green Version]
- Park, J.; Cho, H. Virtual Running Model for Locating Road Intersections using GPS Trajectory data. In Proceedings of the 11th International Conference on Ubiquitous Information Management and Communication, Beppu, Japan, 5–7 January 2017. [Google Scholar]
- Katsaros, K.; Dianati, M.; Tafazolli, R.; Kernchen, R. CLWPR—A novel cross-layer optimized position-based routing protocol for VANETs. In Proceedings of the 2011 IEEE Vehicular Networking Conference (VNC), Amsterdam, The Netherlands, 14–16 November 2011. [Google Scholar]







| Network Parameters | Value |
|---|---|
| MAC and PHY parameters | IEEE 802.11p |
| Carrier frequency | 5.9 GHz |
| Wireless range | 250 m |
| Link Rate | 6 Mbps |
| Message size | 273 bytes |
| Beacon frequency | 10 Hz |
| Simulation time | 100 s |
| Highway Mobility | |
| Network scale | 10 km |
| Lane width | 3.5 m |
| Number of lanes | 4 |
| Channel fading model | Two-ray-ground |
| Urban Mobility | |
| Network scale | 2000 2000 |
| Lane width | 3 m |
| Channel fading model | WINNER II channel model |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Urmonov, O.; Kim, H. A Multi-Hop Data Dissemination Algorithm for Vehicular Communication. Computers 2020, 9, 25. https://doi.org/10.3390/computers9020025
Urmonov O, Kim H. A Multi-Hop Data Dissemination Algorithm for Vehicular Communication. Computers. 2020; 9(2):25. https://doi.org/10.3390/computers9020025
Chicago/Turabian StyleUrmonov, Odilbek, and HyungWon Kim. 2020. "A Multi-Hop Data Dissemination Algorithm for Vehicular Communication" Computers 9, no. 2: 25. https://doi.org/10.3390/computers9020025
APA StyleUrmonov, O., & Kim, H. (2020). A Multi-Hop Data Dissemination Algorithm for Vehicular Communication. Computers, 9(2), 25. https://doi.org/10.3390/computers9020025






