A Traceable Online Will System Based on Blockchain and Smart Contract Technology
Abstract
:1. Introduction
- (1)
- (2)
- (3)
- (4)
- (5)
- (6)
- (7)
- (8)
- (9)
2. Preliminary
2.1. Elliptic Curve Digital Signature Algorithm (ECDSA)
2.2. Smart Contract
2.3. ERC-20
3. Method
3.1. System Architecture
- Applicant (A): Pre-written testator.
- Court (C): Accepts the registration of applicants for wills and applications for wills arbitration. This represents the review and arbitration department for will applications.
- Hospital (H): The hospital that issued the death certificate when the person who made the will dies.
- Testamentary Successor (TS): This is the owner of the inheritance will after the testator dies, for example, the testator’s family.
- Blockchain Center (BCC): According to the instructions of the will, a smart contract is issued and executed.
- Step1.
- Each role in the system needs to register with the blockchain center before using the system and fill in relevant information on the registration webpage as needed, such as personal data, passwords, and Ethereum accounts. When making a will, the system will also verify whether the user’s information is correct. If the format is incorrect, the front platform will return a corresponding error message. Finally, when each role transmits sensitive data to the blockchain center, it will use the Transport Layer Security (TLS) protocol to encrypt the data in transmission. After successful registration, the applicant will obtain the public and private signature key pair for the ECDSA.
- Step2.
- Before the applicant makes a will, he/she will first download the will template for the court to fill out. The will template contains the applicant’s sensitive personal information and the inheritance and distribution of the property. After the applicant fills in the contents of the will, the will content will be sent to the court for review. After the court receives the applicant’s will information, it commences the stage of uploading the will. The court will review the contents of the applicant’s will. After the review is passed, the private key of the court will be used to sign the content of the will with the ECDSA and it will be uploaded to the blockchain center.
- Step3.
- When the applicant of a will dies, the testamentary heir should provide the hospital with relevant information about the applicant before applying for a death certificate. When the hospital receives information from the testamentary heir, it will begin to review whether the information provided is correct. If it is correct, the content of the death certificate will be published and uploaded to the blockchain center. At this time, procedures related to the content of the will will be executed accordingly and the process will enter the stage of property distribution of the will.
- Step4.
- The testamentary heir brings the death certificate to the court to apply for the contents of the will. When the court receives an application from the family of the testamentary heir, the court will judge whether the information provided by the family of the testamentary heir is correct. If it is correct, the will content will be downloaded from the blockchain center, so the will has a legal effect. If the testamentary successor has questions about the distribution of the property, he/she can also apply to the court for arbitration. The court will review the content of the testamentary heir’s application. If the content of the application is correct, the result of the arbitration shall be determined.
3.2. Notations
3.3. Initialization Phase
| Algorithm 1. Smart contract WillContent of the proposed scheme. | |
| struct smart contract WillContent { string ap_name; address ap_account; Gender ap_gender; string ap_idNumber; string ap_createDate; Successor[] successor; } | struct smart contract Successor { string ts_address; string ts_pay; string remarks; } |
| Algorithm 2. Smart contract Death of the proposed scheme. | |
| struct Death { address doctor_account; string hospital_name; string doctor_name; DeathType death_type; string de_name; | string de_idNumber; Gender de_gender; string de_datetime; string de_remarks; } |
- (1)
- In the structure of the will message, sensitive information about the identity of the testator, a list of heirs and distributions, and other types of information are recorded.
- (2)
- In the structure of the death certificate, sensitive information about the identity of the deceased, the department that issued the death certificate, the date of death, and the attributes of the death are recorded.
3.4. Registration Phase
- Step1.
- Role X generates an identity IDX, and sends it to the blockchain center.
- Step2.
- The blockchain center generates an ECDSA private key dx based on the role X, calculates QX=dX*G. If the identity of the registered role is verified as being correct, the smart contract xIns will be triggered, the content of which is the Algorithm 3 as follows:
| Algorithm 3. Smart contract xIns of the proposed scheme. | |
| function insert x smart contract xIns ( string x id, string x detail) { count ++; x id.count = id; | x detail.count = detail; } string x keypairs; |
- Step3.
- The role X will store the key (dX, QX).
3.5. Will Editing Phase
- Step1.
- The applicant first downloads the will from the court website and then fills in the contents of the will. After the applicant fills in the content of the will, the applicant will generate a random value and use the court’s public key PukC to encrypt the content of the will. The signature will be calculated , , , , , and then is sent to the court.
- Step2.
- The court first uses to check whether the timestamp is valid. Then, the correctness of the ECDSA signature is verified and the following is calculated: , , , , . If the verification is recognized, and the signature obtained by the representative is correct, the court will obtain information related to the will and trigger the smart contract will. the content of which is the Algorithm 4 as follows:
Algorithm 4. Smart contract willIns of the proposed scheme. function insert smart contract willIns (
string ap_name, address ap_account, Gender ap_gender, string ap_idNumber, string ap_createDate, Successor[] successor;
) {
WillContent.ap_name = ap_name;
WillContent.ap_account = ap_account;
WillContent.ap_gender = ap_gender;WillContent.ap_idNumber = ap_idNumber;
WillContent.ap_createDate = ap_createDate;
WillContent.successor = successor;
}
3.6. Death Certificate Issuing Phase
- Step1.
- The testamentary heir submits an application for a death certificate to the hospital. When the hospital receives the testamentary heir’s application, the hospital generates a random value kH-BCC, executes the signature calculation , , , , and then sends to the blockchain center.
- Step2.
- The blockchain center (BCC) first uses to check whether the timestamp is valid, then it verifies the correctness of the ECDSA signature, and calculates , , , , , and if it passes the verification, it means that the obtained signature is correct and triggers the smart contract deaths. the content of which is the Algorithm 5 as follows:
Algorithm 5. Smart contract willIns of the proposed scheme. function insert smart contract deathIns(
address doctor_account, string hospital_name, string doctor_name, DeathType death_type, string de_name, string de_idNumber, Gender de_gender, string de_datetime, string de_remarks) {
Death.doctor_account = doctor_account;
Death.hospital_name = hospital_name;
Death.doctor_name = doctor_name;
Death.death_type = death_type;Death.de_name = de_name;
Death.de_idNumber = de_idNumber;
Death.de_gender = de_gender;
Death.de_datetime = de_datetime;
Death.de_remarks = de_remarks;
}
3.7. Will Assets Distributing Phase
- Step1.
- After the hospital issues the death certificate and uploads it to the blockchain center, it enters the testamentary property distribution process, then, the blockchain center generates a random value kBCC-C, executes the signature to calculate , , , , and then sends to the court.
- Step2.
- After the court receives the message from the blockchain center, it will first use to check whether the timestamp is valid, then verify the correctness of the ECDSA signature, and calculate , , , . If the verification is recognized, and the signature is correct, the court will use DprkC to decrypt the contents of the will. The court generates a random value kC-BCC, executes the signature calculation , , , , , and then transmits to the blockchain center.
- Step3.
- When the blockchain center receives a message from the court, it will first use to check whether the timestamp is valid, then verify the correctness of the ECDSA signature and calculate , , , . If the verification is recognized, it is confirmed that the signature is correct. Then, the blockchain center will use the private key to decrypt the encrypted content , read the successor list in the will, refer to the contract content proposed in the initialization phase, find the ts_address and ts_pay data from the contract, and then use the Ethereum ERC20 protocol [23], and Call the transferFrom function to execute the asset transfer process. The Algorithm 6 is the content of transferFrom.
Algorithm 6. Smart contract transferFrom of the ERC20 protocol. function transferFrom(address _from, address _to, uint256 _amount) returns (bool success) {
if (balances[_from] >= _amount && allowed[_from][msg.sender] >= _amount && _amount > 0 && balances[_to] + _amount > balances[_to]
) {
balances[_from] -= _amount;
balances[_to] += _amount;Transfer(_from, _to, _amount);
return true;
} else {
return false;
}
}
3.8. Arbitration Phase
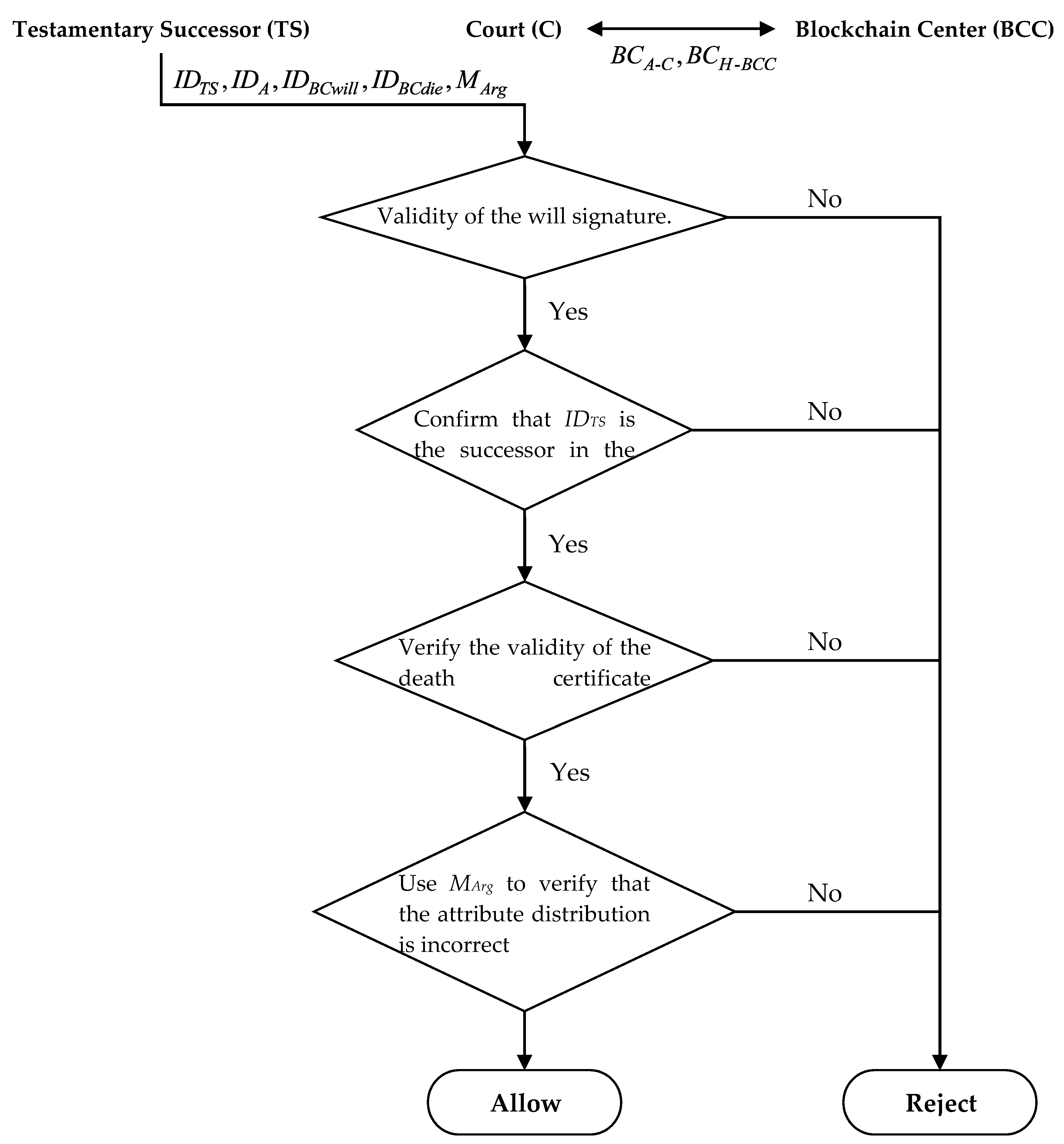
- Step1.
- The testamentary heir applies to the court for arbitration and sends a message to the court. After the court receives it, it enters the arbitration procedure. The court uses to obtain the testator’s signature and uses to retrieve the blockchain data of the testator’s will and verify the blockchain data . If the verification fails, the court will reject the arbitration application.
- Step2.
- After the court verifies the validity of the will signature, the court checks the content of the will blockchain data and compares with the ts_address data in the testament succession list to confirm if the identity of the testamentary heir is inherited by the testator . If the verification fails, the court will reject the arbitration application.
- Step3.
- After the court verifies the validity of the testamentary successor, the court uses to obtain the testator’s signature and uses to retrieve the death certificate blockchain data BB, and verify the death certificate blockchain signature data . If it fails, the court will reject the arbitration application.
- Step4.
- If the court verifies the validity of the death certificate, the court will use the will blockchain data obtained in the second step, and then compare these with the information in the inheritance list in the will. The message contains the address of the testamentary heir and property currently allocated to the testamentary heir. The court will then check the successor list from the . The heir list will refer to the contract content proposed in the initialization phase, and merge the ts_pay and into the heir list. It will compare the amount of property currently allocated by the probate heir to check whether the property allocation is incorrect . If the verification fails, the court will reject the arbitration application. If the verification is successful, it means that the blockchain data have been fully verified and the arbitration application of the testamentary heir has also been established.
- Step5.
- When the testamentary heir receives the messages that the arbitration has been established, the testamentary heir can retain the results of the arbitration to execute legal procedures and redistribute the property through administrative procedures.
4. Security Analysis
4.1. Integrity
4.2. Public Verifiability
4.3. Unforgeability
4.4. Non-Repudiation
4.5. Message Irreversibility
4.6. Resist Counterfeiting Attacks
4.7. Tamperproof
4.8. System Decentralization
4.9. Fair Arbitration
5. Discussion
5.1. Calculation Cost Analysis
5.2. Total Communication Cost Analysis
5.3. Function Comparison
5.4. Limitations
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Peter, A. Jimi Hendrix Ongoing Estate Litigation. Available online: https://medium.com/@injudiciouslex/jimi-hendrix-ongoing-estate-litigation-c16c39f81692 (accessed on 1 February 2021).
- O’Malley Greenburg, Z. The Scandalously Boring Truth About Michael Jackson’s Will. Available online: https://www.forbes.com/sites/zackomalleygreenburg/2012/08/17/the-scandalously-boring-truth-about-michael-jacksons-will/?sh=16cebb6348ed (accessed on 1 February 2021).
- He, H.S. Family Property Distribution Disputes, Wikipedia Contributors. Available online: https://zh.wikipedia.org/w/index.php?title=%E4%BD%95%E9%B4%BB%E7%87%8A%E5%AE%B6%E6%97%8F%E5%88%86%E7%94%A2%E7%B3%BE%E7%B4%9B%E4%BA%8B%E4%BB%B6&oldid=59972272 (accessed on 1 February 2021).
- Chien, H.Y.; Lin, R.Y. The Study of Secure E-Will System on the Internet. J. Inf. Sci. Eng. 2009, 25, 877–893. [Google Scholar]
- Lee, K.; Won, D.; Kim, S. A practical approach to a secure e-will system in the ROC. In Proceedings of the 2010 IEEE 5th International Conference on Ubiquitous Information Technologies and Applications, Sanya, China, 16–18 December 2010; pp. 1–6. [Google Scholar]
- Chen, C.L.; Lee, C.C.; Tseng, Y.M.; Chou, T.T. A private online system for executing wills based on a secret sharing mechanism. Secur. Commun. Netw. 2012, 5, 725–737. [Google Scholar] [CrossRef]
- Sreehari, P.; Nandakishore, M.; Krishna, G.; Jacob, J.; Shibu, V.S. Smart will converting the legal testament into a smart contract. In Proceedings of the 2017 IEEE International Conference on Networks & Advances in Computational Technologies (NetACT), Thiruvanthapuram, India, 20–22 July 2017; pp. 203–207. [Google Scholar]
- Ettoday, Launched the First Will App in Taiwan. Lawyer Liu Weide Spent Millions of NT Dollars to Develop and Provide Free Download. 2019. Available online: https://www.ettoday.net/news/20190403/1414747.htm (accessed on 1 February 2021).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2019. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 February 2021).
- Buterin, V. A next-generation smart contract and decentralized application platform. White Paper 2014, 3, 1–36. [Google Scholar]
- Shih, T.F.; Chen, C.L.; Syu, B.Y.; Deng, Y.Y. A Cloud-Based Crime Reporting System with Identity Protection. Symmetry 2019, 11, 255. [Google Scholar] [CrossRef] [Green Version]
- Chen, C.L.; Chiang, M.L.; Deng, Y.Y.; Weng, W.; Wang, K.; Liu, C.C. A traceable firearm management system based on blockchain and IoT technology. Symmetry 2021, 13, 439. [Google Scholar] [CrossRef]
- HASH Coron, J.S.; Dodis, Y.; Malinaud, C.; Puniya, P. Merkle-Damgård revisited: How to construct a hash function. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2005; pp. 430–448. [Google Scholar]
- Chen, C.L.; Deng, Y.Y.; Weng, W.; Zho, M.; Sun, H. A Blockchain Based Intelligent Anti-switch Package in Tracing Logistics System. J. Supercomp. 2021. [Google Scholar] [CrossRef]
- Chen, C.L.; Deng, Y.Y.; Li, C.T.; Zhu, S.; Chiu, Y.J.; Chen, P.Z. An IoT-Based Traceable Drug Anti-Counterfeiting Management System. IEEE Access 2020, 8, 224532–224548. [Google Scholar] [CrossRef]
- Li, C.T.; Shih, D.H.; Wang, C.C.; Chen, C.L.; Lee, C.C. A Blockchain Based Data Aggregation and Group Authentication Scheme for Electronic Medical System. IEEE Access 2020, 8, 173904–173917. [Google Scholar] [CrossRef]
- Chen, C.L.; Deng, Y.Y.; Weng, W.; Sun, H.; Zho, M. A Blockchain-Based Secure Inter-Hospital EMR Sharing System. Appl. Sci. 2020, 10, 4958. [Google Scholar] [CrossRef]
- Wang, Y.C.; Chen, C.L.; Deng, Y.Y. Authorization mechanism based on blockchain technology for protecting museum digital property rights. Appl. Sci. 2021, 11, 1085. [Google Scholar] [CrossRef]
- Lin, C.C.; Chang, C.C.; Zheng, Y.Z. A Ring Signature Based Anonymity Authentication Scheme for Group Medical Consultation. Symmetry 2020, 12, 2009. [Google Scholar] [CrossRef]
- Chen, C.L.; Shih, T.F.; Wang, K.H.; Chen, C.H.; Tsaur, W.J. An Investigator Unearths Illegal Behavior via a Subliminal Channel. J. Internet Technol. 2018, 19, 573–580. [Google Scholar]
- Chen, C.L.; Liao, J.J. A fair online payment system for digital content via subliminal channel. Electron. Commer. Res. Appl. 2011, 10, 279–287. [Google Scholar] [CrossRef]
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Kang, B.; Shao, D.; Wang, J. A fair electronic payment system for digital content using elliptic curve cryptography. J. Algorithms Comput. Technol. 2018, 12, 13–19. [Google Scholar] [CrossRef] [Green Version]
- Pornin, T. Deterministic usage of the digital signature algorithm (DSA) and elliptic curve digital signature algorithm (ECDSA). Internet Eng. Task Force RFC 2013, 6979, 1–79. [Google Scholar]
- Szabo, N. The Idea of Smart Contracts. 1997. Available online: http://www.fon.hum.uva.nl/rob/Courses/InformationInSpeech/CDROM/Literature/LOTwinterschool2006/szabo.best.vwh.net/smart_contracts_idea.html (accessed on 1 February 2021).
- Wang, S.; Ouyang, L.; Yuan, Y.; Ni, X.; Han, X.; Wang, F.Y. Blockchain-enabled smart contracts: Architecture, applications, and future trends. IEEE Transact. Syst. Man Cybern. Syst. 2019, 49, 2266–2277. [Google Scholar] [CrossRef]
- Vogelsteller, F.; Buterin, V. EIP-20: ERC-20 Token Standard. 2015. Available online: https://eips.ethereum.org/EIPS/eip-20 (accessed on 1 February 2021).
- Chen, C.L.; Li, Y.T.; Deng, Y.Y.; Li, C.T. Robot identification and authentication in a robot cloud service system. IEEE Access 2018, 6, 56488–56503. [Google Scholar] [CrossRef]






| Symbol | Description |
|---|---|
| q | A k-bit prime number |
| GF(q) | Finite group q |
| E | The elliptic curve defined on finite group q |
| G | A generating point based on the elliptic curve E |
| IDX | X’s identity |
| kX | A random value on the elliptic curve |
| (rX, sX) | Elliptic curve signature value of X |
| (xX, yX) | An ECDSA(Elliptic Curve Digital Signature Algorithm) signature message of X |
| IDBCi | The index value of blockchain message |
| BCX | Blockchain message of X |
| Mwill | The plain text of the will |
| MArg | Arbitration dispute message content |
| MArgID | Identity information of an applicant for arbitration |
| MArgpay | The message of the arbitrator’s estate distribution |
| TSX | Timestamp message of X |
| h(.) | Hash function |
| CX | The ciphertext of role X |
| EpukX(M) | Use X’s public key PukX to encrypt message M |
| DprkX(M) | Use X’s private key PrkX to decrypt message M |
| Verify whether A is equal to B |
| Item | Signature | Sender | Receiver | Signature Verification | |
|---|---|---|---|---|---|
| Phase | |||||
| Will editing phase | Applicant (A) | Court (C) | |||
| Death certificate issuing phase | Hospital (H) | Blockchain Center (BCC) | |||
| Will assets distributing phase | Blockchain Center (BCC) | Court (C) | |||
| Court (C) | Blockchain Center (BCC) | ||||
| Role | BCC | A | C | H | TS | |
|---|---|---|---|---|---|---|
| Phase | ||||||
| Registration phase | N/A | N/A | N/A | N/A | ||
| Will editing phase | N/A | N/A | N/A | |||
| Death certificate issuing phase | N/A | N/A | N/A | |||
| Will assets distribution phase | N/A | N/A | N/A | |||
| Item | Message Length | Rounds | 3.5G (14 Mbps) | 4G (100 Mbps) | 5G (20 Gbps) | |
|---|---|---|---|---|---|---|
| Phase | ||||||
| Registration phase | 480 bits | 2 | 0.034 ms | 0.005 ms | 0.024 us | |
| Will editing phase | 720 bits | 1 | 0.051 ms | 0.072 ms | 0.036 us | |
| Death certificate issing phase | 640 bits | 1 | 0.046 ms | 0.064 ms | 0.032 us | |
| Will assets distributing phase | 1280 bits | 2 | 0.091 ms | 0.128 ms | 0.021 us | |
| Scheme | Chien and Lin [4] | Lee et al. [5] | Chen et al. [6] | Sreehari et al. [7] | Our Proposed Scheme | |
|---|---|---|---|---|---|---|
| Feature | ||||||
| Integrity | Y | N | Y | N | Y | |
| Public verifiability | N | N | Y | Y | Y | |
| Unforgeability | Y | Y | Y | N | Y | |
| Non-repudiation | N | Y | Y | N | Y | |
| Message irreversibility | N | N | N | N | Y | |
| Resist counterfeiting attacks | N | N | N | N | Y | |
| Tamperproof | N | N | N | N | Y | |
| System decentralization | N | N | N | N | Y | |
| Fair arbitration | N | N | N | N | Y | |
| Blockchain issues | N | N | N | Y | Y | |
| Propose an architecture or framework | Y | Y | Y | Y | Y | |
| Implementation of the legacy distribution mechanism | N | N | N | N | Y | |
| Smart contract mechanism | N | N | N | N | Y | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, C.-L.; Lin, C.-Y.; Chiang, M.-L.; Deng, Y.-Y.; Chen, P.; Chiu, Y.-J. A Traceable Online Will System Based on Blockchain and Smart Contract Technology. Symmetry 2021, 13, 466. https://doi.org/10.3390/sym13030466
Chen C-L, Lin C-Y, Chiang M-L, Deng Y-Y, Chen P, Chiu Y-J. A Traceable Online Will System Based on Blockchain and Smart Contract Technology. Symmetry. 2021; 13(3):466. https://doi.org/10.3390/sym13030466
Chicago/Turabian StyleChen, Chin-Ling, Ching-Ying Lin, Mao-Lun Chiang, Yong-Yuan Deng, Peizhi Chen, and Yi-Jui Chiu. 2021. "A Traceable Online Will System Based on Blockchain and Smart Contract Technology" Symmetry 13, no. 3: 466. https://doi.org/10.3390/sym13030466
APA StyleChen, C.-L., Lin, C.-Y., Chiang, M.-L., Deng, Y.-Y., Chen, P., & Chiu, Y.-J. (2021). A Traceable Online Will System Based on Blockchain and Smart Contract Technology. Symmetry, 13(3), 466. https://doi.org/10.3390/sym13030466







