Multi-Objective Caching Optimization for Wireless Backhauled Fog Radio Access Network
Abstract
:1. Introduction
- Closed-form expressions of the probabilities of a F-AP being a direct F-AP or a transit F-AP with respect to the requested content are derived, then the expressions are used to calculate the association probabilities.
- Using stochastic geometry tools, we derive expressions of the STP and average delay in the general signal-to-interference-plus-noise ratio (SINR) regime. To reduce the complexity, closed-form expressions of the asymptotic multi-objective STP and delay in the high signal-to-noise ratio (SNR) regime are derived.
- The multi-objective optimization problem is formulated to maximize the STP or minimize the average delay. Then, the asymptotic multi-objective optimization problem in the high SNR is considered to reduce the computational complexity.
- A novel projected multi-objective cuckoo search algorithm (PMOCSA) is proposed to compute the Pareto front of the optimal cache placement.
- The numerical results show that the developed PMOCSA outperforms the original multi-objective cuckoo search algorithm (MOCSA). Also, the proposed multi-objective caching scheme is shown to achieve higher performance than the benchmark caching schemes.
2. System Model
2.1. Network Model
2.2. Caching Model
2.3. Association Model
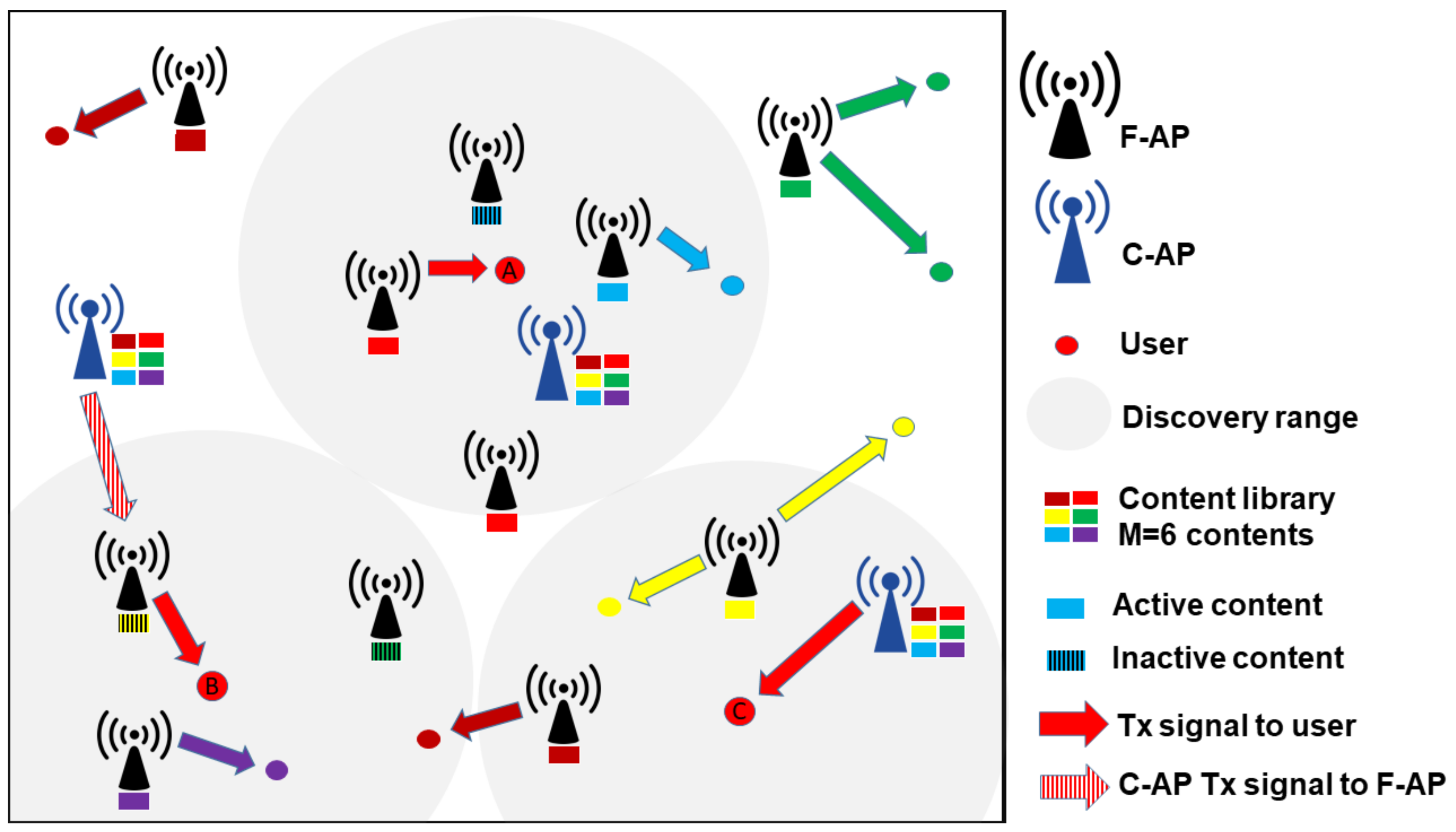
- If there are F-APs caching content m within R, will be associated with the nearest F-AP caching m to serve directly, e.g., user A in Figure 1. Therefore, is dubbed ’direct F-AP’. Denote as the probability of is being associated with a direct F-AP when it requests content m. As all the F-APs caching content m can serve as a direct F-AP with respect to content m, the point process of the direct F-APs is the thinned PPP with density , i.e., is the point process of the F-APs caching content m. Then, using the null property of PPP, can be obtained as in the following lemmaLemma 1.When requests content m, the probability of being associated to a direct F-AP within R is given byProof.Please refer to Appendix A. □
- If content m in not cached within R, then will be associated with the nearest available F-AP within R to fetch m from the nearest C-AP , e.g., user B in Figure 1. Here, is dubbed ’transit F-AP’ due to the 2-hop transmission. Moreover, the available F-AP is defined as the F-AP that caches inactive content (i.e., a content not requested by users within its association area). Let the random variable denote whether content cached by is being requested by users within its Voronoi cell, such that stands for the event of content being not requested, and otherwise. Then, the probability of the content being inactive can be obtained using proposition 1 of [20] asThe probability that a F-AP can be an available F-AP when content m is requested can be obtained as in the following lemmaLemma 2.The probability of available F-APs with respect to content m isProof.Please refer to Appendix B. □To proceed, we denote as the point process of available F-APs with respect to content m. As is a thinned PPP, its density can be obtained as . Then, the probability of the event that is associated with a transit F-AP within R when it requests content m can be obtained as in Lemma 3Lemma 3.When requests content m, the probability of is being associated with a transit F-AP within R is given byProof.Please refer to Appendix C. □
- If neither a direct nor a transit F-AP exists within R to be associated with, then will be associated with the nearest C-AP within R, e.g., user C in Figure 1. The probability of this event is given as in the following lemmaLemma 4.When requests content m, the probability of is being associated with the nearest C-AP within R is given byProof.Please refer to Appendix D. □
3. Performance Analysis
3.1. STP Analysis
3.2. Delay Analysis
4. Problem Formulation and Optimization
| Algorithm 1: Projected Multi-Objective Cuckoo Search Algorithm (PMOCSA). |
 |
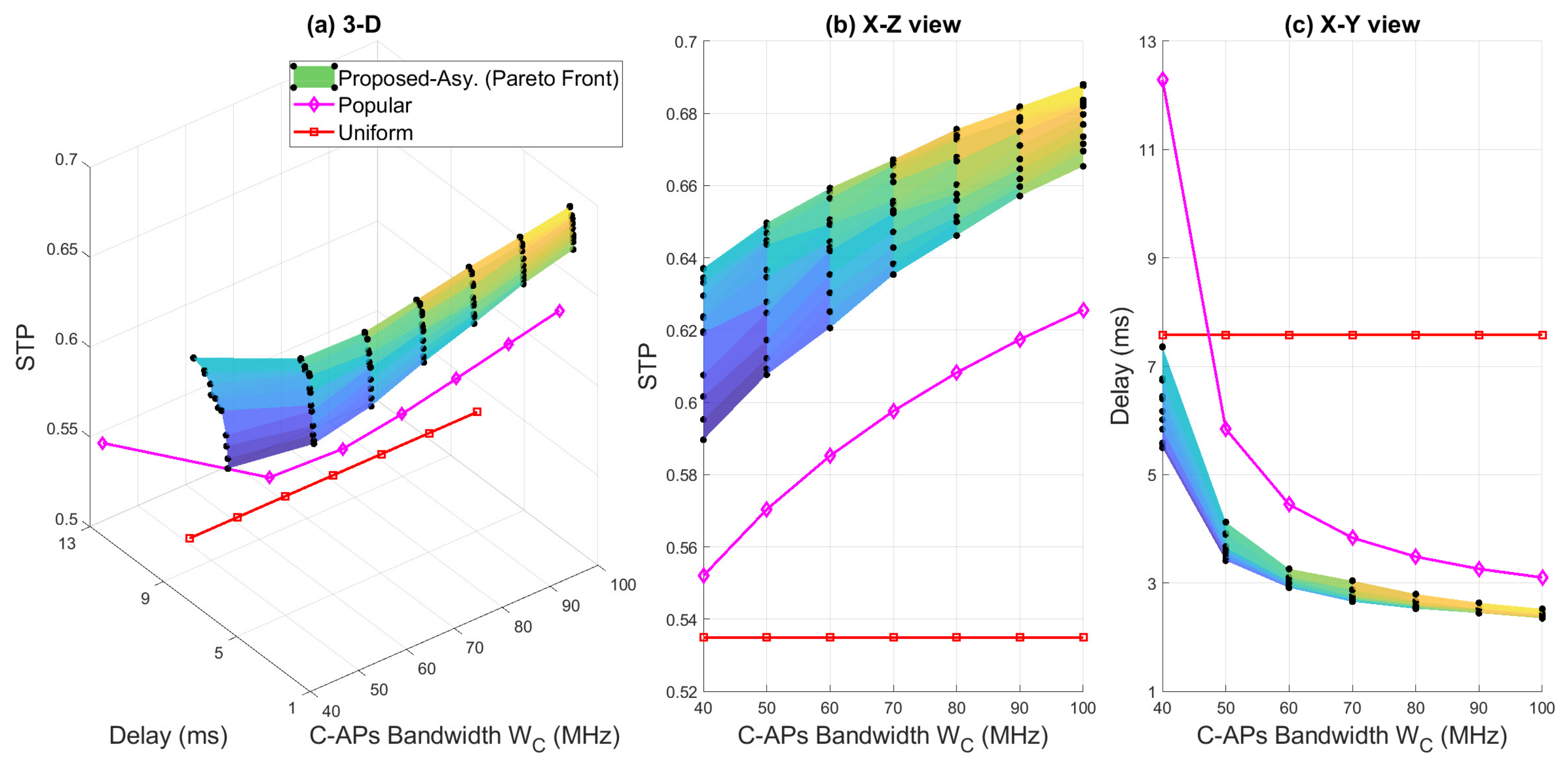
5. Numerical Results and Discussions
5.1. Numerical Results
5.2. Discussions
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A. Proof of Lemma 1
Appendix B. Proof of Lemma 2
Appendix C. Proof of Lemma 3
Appendix D. Proof of Lemma 4
Appendix E. Proof of Theorem 1
Appendix F. Proof of Theorem 2
Appendix G. Proof of Theorem 3
References
- Mukherjee, M.; Shu, L.; Wang, D. Survey of Fog Computing: Fundamental, Network Applications, and Research Challenges. IEEE Commun. Surv. Tutor. 2018, 20, 1826–1857. [Google Scholar] [CrossRef]
- Habibi, M.A.; Nasimi, M.; Han, B.; Schotten, H.D. A Comprehensive Survey of RAN Architectures Toward 5G Mobile Communication System. IEEE Access 2019, 7, 70371–70421. [Google Scholar] [CrossRef]
- Bani-Bakr, A.; Dimyati, K.; Hindia, M.N.; Wong, W.R.; Al-Omari, A.; Sambo, Y.A.; Imran, M.A. Optimizing the Number of Fog Nodes for Finite Fog Radio Access Networks under Multi-Slope Path Loss Model. Electronics 2020, 9, 2175. [Google Scholar] [CrossRef]
- Emara, M.; Elsawy, H.; Sorour, S.; Al-Ghadhban, S.; Alouini, M.; Al-Naffouri, T.Y. Optimal Caching in 5G Networks With Opportunistic Spectrum Access. IEEE Trans. Wirel. Commun. 2018, 17, 4447–4461. [Google Scholar] [CrossRef]
- Peng, A.; Jiang, Y.; Bennis, M.; Zheng, F.; You, X. Performance Analysis and Caching Design in Fog Radio Access Networks. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Wang, R.; Li, R.; Wang, P.; Liu, E. Analysis and Optimization of Caching in Fog Radio Access Networks. IEEE Trans. Veh. Technol. 2019, 68, 8279–8283. [Google Scholar] [CrossRef]
- Jiang, F.; Yuan, Z.; Sun, C.; Wang, J. Deep Q-Learning-Based Content Caching With Update Strategy for Fog Radio Access Networks. IEEE Access 2019, 7, 97505–97514. [Google Scholar] [CrossRef]
- Jiang, Y.; Ma, M.; Bennis, M.; Zheng, F.; You, X. User Preference Learning-Based Edge Caching for Fog Radio Access Network. IEEE Trans. Commun. 2019, 67, 1268–1283. [Google Scholar] [CrossRef] [Green Version]
- Jia, S.; Ai, Y.; Zhao, Z.; Peng, M.; Hu, C. Hierarchical content caching in fog radio access networks: Ergodic rate and transmit latency. China Commun. 2016, 13, 1–14. [Google Scholar] [CrossRef]
- Liu, J.; Bai, B.; Zhang, J.; Letaief, K.B. Cache Placement in Fog-RANs: From Centralized to Distributed Algorithms. IEEE Trans. Wirel. Commun. 2017, 16, 7039–7051. [Google Scholar] [CrossRef] [Green Version]
- Wei, X. Joint Caching and Multicast for Wireless Fronthaulin Fog Radio Access Networks. In Proceedings of the 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall), Toronto, ON, Canada, 24–27 September 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Li, Z.; Chen, J.; Zhang, Z. Socially Aware Caching in D2D Enabled Fog Radio Access Networks. IEEE Access 2019, 7, 84293–84303. [Google Scholar] [CrossRef]
- Dang, T.; Peng, M. Joint Radio Communication, Caching, and Computing Design for Mobile Virtual Reality Delivery in Fog Radio Access Networks. IEEE J. Sel. Areas Commun. 2019, 37, 1594–1607. [Google Scholar] [CrossRef]
- Wei, Y.; Yu, F.R.; Song, M.; Han, Z. Joint Optimization of Caching, Computing, and Radio Resources for Fog-Enabled IoT Using Natural Actor–Critic Deep Reinforcement Learning. IEEE Internet Things J. 2019, 6, 2061–2073. [Google Scholar] [CrossRef]
- Jiang, Y.; Hu, Y.; Bennis, M.; Zheng, F.; You, X. A Mean Field Game-Based Distributed Edge Caching in Fog Radio Access Networks. IEEE Trans. Commun. 2020, 68, 1567–1580. [Google Scholar] [CrossRef] [Green Version]
- Guo, B.; Zhang, X.; Sheng, Q.; Yang, H. Dueling Deep-Q-Network Based Delay-Aware Cache Update Policy for Mobile Users in Fog Radio Access Networks. IEEE Access 2020, 8, 7131–7141. [Google Scholar] [CrossRef]
- Rahman, G.M.S.; Peng, M.; Yan, S.; Dang, T. Learning Based Joint Cache and Power Allocation in Fog Radio Access Networks. IEEE Trans. Veh. Technol. 2020, 69, 4401–4411. [Google Scholar] [CrossRef]
- Jiang, Y.; Wan, C.; Tao, M.; Zheng, F.C.; Zhu, P.; Gao, X.; You, X. Analysis and Optimization of Fog Radio Access Networks With Hybrid Caching: Delay and Energy Efficiency. IEEE Trans. Wirel. Commun. 2021, 20, 69–82. [Google Scholar] [CrossRef]
- Jiang, Y.; Peng, A.; Wan, C.; Cui, Y.; You, X.; Zheng, F.; Jin, S. Analysis and Optimization of Cache-Enabled Fog Radio Access Networks: Successful Transmission Probability, Fractional Offloaded Traffic and Delay. IEEE Trans. Veh. Technol. 2020, 69, 5219–5231. [Google Scholar] [CrossRef]
- Yu, S.M.; Kim, S. Downlink capacity and base station density in cellular networks. In Proceedings of the 2013 11th International Symposium and Workshops on Modeling and Optimization in Mobile, Ad Hoc and Wireless Networks (WiOpt), Tsukuba, Japan, 13–17 May 2013; pp. 119–124. [Google Scholar]
- Vo, D.N.; Schegner, P.; Ongsakul, W. Cuckoo search algorithm for non-convex economic dispatch. IET Gener. Transm. Distrib. 2013, 7, 645–654. [Google Scholar] [CrossRef]
- Yang, X.; Deb, S. Cuckoo Search via Lévy flights. In Proceedings of the 2009 World Congress on Nature Biologically Inspired Computing (NaBIC), Coimbatore, India, 9–11 December 2009; pp. 210–214. [Google Scholar] [CrossRef]
- Yang, X.S.; Deb, S. Multiobjective cuckoo search for design optimization. Comput. Oper. Res. 2013, 40, 1616–1624. [Google Scholar] [CrossRef]
- Khodier, M. Comprehensive study of linear antenna array optimisation using the cuckoo search algorithm. IET Microw. Antennas Propag. 2019, 13, 1325–1333. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Vo, D.N. The application of one rank cuckoo search algorithm for solving economic load dispatch problems. Appl. Soft Comput. 2015, 37, 763–773. [Google Scholar] [CrossRef]
- Mantegna, R.N. Fast, accurate algorithm for numerical simulation of Lévy stable stochastic processes. Phys. Rev. E 1994, 49, 4677–4683. [Google Scholar] [CrossRef]
- Baştuǧ, E.; Bennis, M.; Kountouris, M.; Debbah, M. Cache-enabled small cell networks: Modeling and tradeoffs. EURASIP J. Wirel. Commun. Netw. 2015, 2015, 1–11. [Google Scholar] [CrossRef] [PubMed]
- Tamoor-ul-Hassan, S.; Bennis, M.; Nardelli, P.H.J.; Latva-Aho, M. Modeling and analysis of content caching in wireless small cell networks. In Proceedings of the 2015 International Symposium on Wireless Communication Systems (ISWCS), Brussels, Belgium, 25–28 August 2015; pp. 765–769. [Google Scholar] [CrossRef] [Green Version]
- Haenggi, M.; Ganti, R. Interference in Large Wireless Networks. Found. Trends Netw. 2009, 3, 127–248. [Google Scholar] [CrossRef]









| Notation | Description |
|---|---|
| Content library | |
| M | Total number of contents |
| Point process of the F-APs | |
| Point process of the C-APs | |
| Point process of the users | |
| Point process of the F-APs that cache content m | |
| Point process of the F-APs that do not cache content m | |
| Point process of the available F-APs with respect to content m | |
| Point process of the unavailable F-APs with respect to content m | |
| Density of | |
| Density of | |
| Density of | |
| Probability of content m being randomly requested by a user | |
| Caching distribution of the contents | |
| Probability of content m being cached at each F-AP | |
| Probability of the content being inactive | |
| Probability of available F-APs with respect to content m | |
| Direct F-AP with respect to content m | |
| Transit F-AP with respect to content m | |
| Nearest C-AP to | |
| Nearest C-AP to | |
| Probability of association with when content m is requested | |
| Probability of association with when content m is requested | |
| Probability of association with when content m is requested | |
| Total probability of association with an access point when content m is requested | |
| SINR at when it is associated with | |
| SINR at when it is associated with | |
| SINR at when is associated with | |
| SINR at when it is associated with | |
| Distance between and | |
| Distance between access point ℓ and | |
| Distance between and | |
| Distance between and | |
| Distance between access point ℓ and | |
| Distance between and | |
| Small-scale channel coefficient between and | |
| Small-scale channel coefficient between access point ℓ and | |
| Small-scale channel coefficient between and | |
| Small-scale channel coefficient between and | |
| Small-scale channel coefficient between access point ℓ and | |
| Small-scale channel coefficient between and | |
| STP of content m when is associated with | |
| conditioned on | |
| STP of content m when is associated with | |
| STP of content m over the link to | |
| conditioned on | |
| STP of content m over the link to | |
| conditioned on | |
| STP of content m when is associated with | |
| conditioned on | |
| STP of | |
| Asymptotic STP of when | |
| Average delay of content m when is associated with | |
| Average delay of content m when is associated with | |
| Average delay of content m over the links from to | |
| Average delay of content m over the link from to | |
| Average delay of content m when is associated with | |
| Average delay of | |
| Asymptotic delay of when |
Short Biography of Authors
 | Alaa Bani-Bakr received B.Sc. and M.Sc. degrees in electrical/telecommunication engineering from Mutah University, Karak, Jordan, in 2002 and 2006, respectively. He is currently pursuing a Ph.D. with the University of Malaya, Kuala Lumpur, Malaysia. He was a Lecturer at the Department of Electrical Engineering, AlBaha University, Saudi Arabia, from 2010 to 2012. His research interests are fog radio access networks, cache-enabled wireless networks, mmWave communication systems, stochastic analysis, and optimization. |
 | MHD Nour Hindia received a Ph.D. from the Faculty of Engineering in Telecommunication, University of Malaya, Kuala Lumpur, Malaysia, in 2015. He is currently involved with research in the field of wireless communications, especially in channel sounding, network planning, converge estimation, handover, scheduling, and quality of service enhancement for 5G networks. He is currently a Post-Doctoral Fellow from the Faculty of Engineering in Telecommunication, University of Malaya. Besides that, he is involved with research with the Research Group in Modulation and Coding Scheme for Internet of Things for Future Network. He has authored or co-authored a number of science citation index journals and conference papers. Dr. Hindia has participated as a Reviewer and a committee member of a number of ISI journals and conferences. |
 | Kaharudin Dimyati graduated from the University of Malaya, Malaysia, in 1992. He received a Ph.D. from the University of Wales Swansea, U.K., in 1996. He is currently a Professor at the Department of Electrical Engineering, Faculty of Engineering, University of Malaya. Since joining the university, he is actively involved in teaching, postgraduate supervision, research, and also administration. To date, he has supervised 15 Ph.D. students and 32 masters by research students. He has published over 100 journal articles. He is a member of IET and IEICE. He is a Professional Engineer and a Chartered Engineer. |
 | Effariza Hanafi rreceived a B.Eng. in telecommunications (first class Hons.) from the University of Adelaide, Adelaide, S.A., Australia, and the Ph.D. degree in electrical and electronic engineering from the University of Canterbury, Christchurch, New Zealand, in 2010 and 2014, respectively. She joined the University of Malaya, Kuala Lumpur, Malaysia, where she is now a Senior Lecturer at the Faculty of Engineering. In 2015, she was the recipient of the University of Malaya Excellence Awards. She is currently a Senior Member for IEEE (Institute of Electrical and Electronics Engineers). Her main research interests include wireless communications, Internet of Things, cognitive radio, cooperative communications, 5G networks, and beyond. |
 | Tengku Faiz Tengku Mohmed Noor Izam received a Ph.D. in electronic engineering from the University of Surrey, U.K., in 2016. He is currently a Lecturer with the Department of Electrical Engineering, University of Malaya, Malaysia. His research interests include, parasitic antenna, and MIMO system with antenna selection. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bani-Bakr, A.; Hindia, M.N.; Dimyati, K.; Hanafi, E.; Tengku Mohmed Noor Izam, T.F. Multi-Objective Caching Optimization for Wireless Backhauled Fog Radio Access Network. Symmetry 2021, 13, 708. https://doi.org/10.3390/sym13040708
Bani-Bakr A, Hindia MN, Dimyati K, Hanafi E, Tengku Mohmed Noor Izam TF. Multi-Objective Caching Optimization for Wireless Backhauled Fog Radio Access Network. Symmetry. 2021; 13(4):708. https://doi.org/10.3390/sym13040708
Chicago/Turabian StyleBani-Bakr, Alaa, MHD Nour Hindia, Kaharudin Dimyati, Effariza Hanafi, and Tengku Faiz Tengku Mohmed Noor Izam. 2021. "Multi-Objective Caching Optimization for Wireless Backhauled Fog Radio Access Network" Symmetry 13, no. 4: 708. https://doi.org/10.3390/sym13040708






