An Artwork Rental System Based on Blockchain Technology
Abstract
:1. Introduction
1.1. Background
- Using the Hyperledger technology, the various art banks are combined into a single alliance, and information among alliance members can be shared, which facilitates the integrated query of a single entry by the renter.
- Use blockchain technology to ensure that the details of artwork information are shared under the premise of preventing the tampering of artwork-related information in an environment without a central authority.
- Compile traditional lease agreements into smart contract lease contracts to automatically run and operate data.
- When a lease dispute occurs, a third-party arbitration institution can conduct a fair arbitration judgment based on the information stored in the blockchain.
1.2. Problem Formulation
- (1)
- Decentralization and information sharing: Under the decentralized environment framework of the blockchain, all nodes in the environment have the same rights and obligations, and can store and share information. Therefore, data errors or failure shutdowns of a few nodes in the environment will not affect the operation of the entire blockchain network.
- (2)
- Openness: The blockchain has a public key system. We can use the private key to encrypt private information, and allow others to query and verify the correctness of the open blockchain data through the public key. In the blockchain environment, blockchain data will be open and transparent, reducing public distrust caused by information asymmetry. Through the open data of the blockchain architecture, the related applications of big data and cloud computing can be improved.
- (3)
- Privacy and access control: Even with the application of blockchain technology, extremely high levels of privacy can be achieved. Blockchain technology can also combine public key encryption and access control. Only allowed members can access and verify data. This is the concept of a consortium chain or private chain. Different from the public chain, through the alliance chain or private chain, only members in the chain can access the data and combine it with smart contracts for automatic script control.
- (4)
- Mutual authentication: Mutual authentication is a basic security verification condition in the field of information security. This is used to confirm whether a certain framework or communication protocol can verify the legitimacy of the identities of the communication parties. In the related research of researchers, Burrows–Abadi–Needham (BAN) logic proof is often used to judge whether the architecture or communication protocol has realized the mutual authentication of the communication parties.
- (5)
- Verifiable: Verifiability refers to a certain architecture or communication protocol. During the communication process, the message sent by the sender will be signed by the sender’s private key. After the message is sent to the receiver, the receiver can use the sender’s public key to verify that the sender’s signature is authentic.
- (6)
- Integrity and forgery: In related research, to guarantee the integrity of a certain framework or communication protocol during information transmission, a public key system is usually used to ensure that the transmitted information has not been tampered with by malicious persons.
- (7)
- Traceable: The use of blockchain technology means that information transmission is equal, and all participating nodes in the system have equal rights and obligations, so all nodes can cross-check transaction information on the system. In addition, due to the decentralized nature of blockchain technology, the change records of a certain node on the system will be saved by other nodes, achieving traceability.
- (8)
- Non-repudiation: The blockchain system has undeniable characteristics. After the information transmitted in the system is verified by a certain role and transmitted to the blockchain, the information will be permanently stored. In addition to verifying the correctness of the original message, this information also records the recording time of the message. If we want to change a message on the blockchain, we must change the content of more than half of the nodes in the system at the same time, which will be difficult to achieve under the open system architecture.
- (9)
- Resist man-in-the-middle attack: A man-in-the-middle attack means that an attacker can intercept a message during sending, and modify or resend an illegal message to the receiver. Under the framework of the blockchain, the message sent by the sender will be signed with its private key, and the attacker cannot obtain the private key of the message sender, so it will be difficult for the attacker to implement a man-in-the-middle attack.
2. Preliminary
2.1. Smart Contract
2.2. ECDSA
2.3. BAN Logic
2.4. Hyperledger Fabric
3. The Proposed Scheme
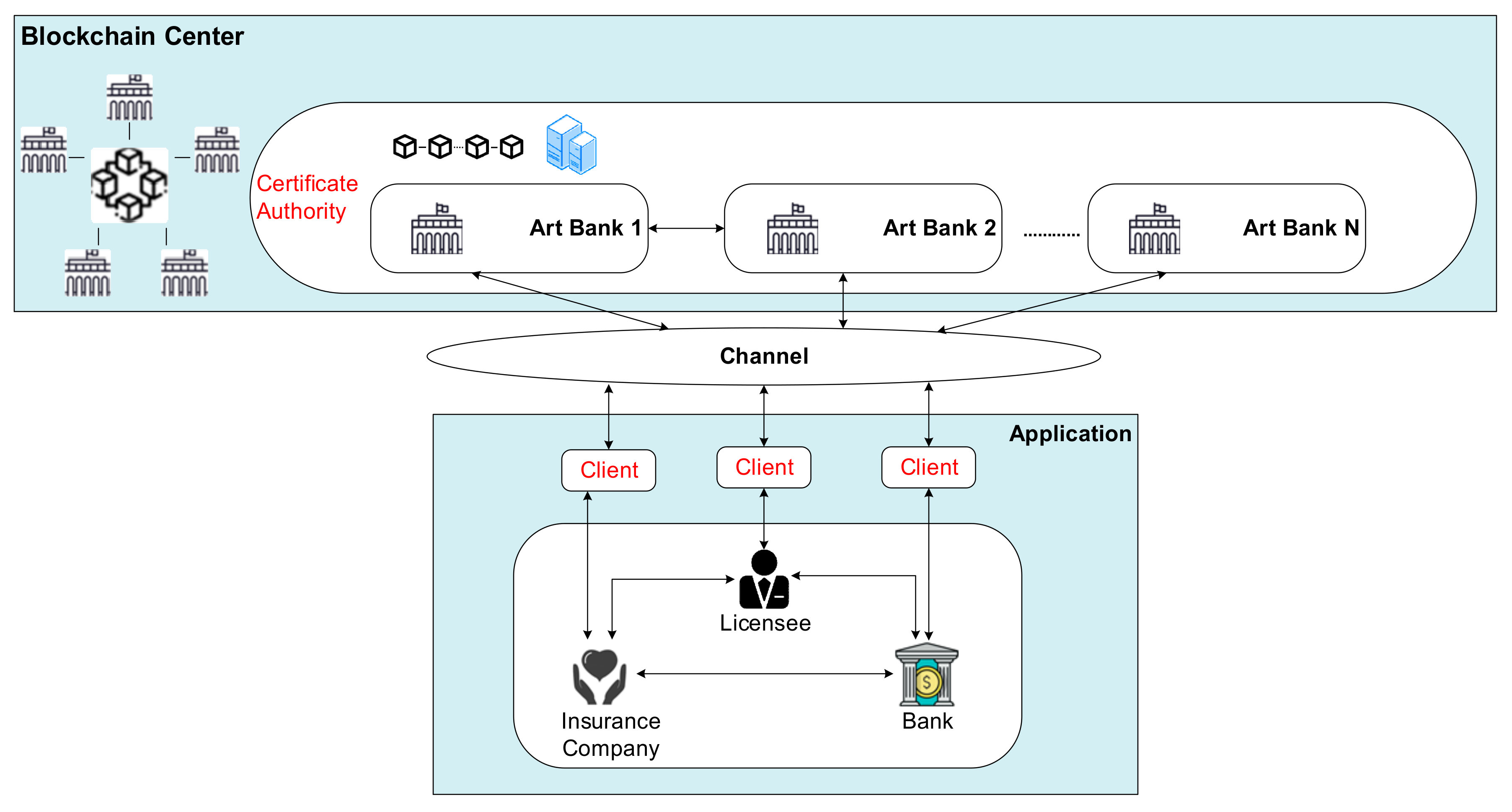
3.1. System Architecture
3.2. Notation
| q | A k-bit prime number |
| GF(q) | A finite group q |
| E | An elliptic curve that is defined on the finite group q |
| G | A generating point that is based on the elliptic curve E |
| PKx | An asymmetric public key of role x |
| SKx | An asymmetric private key of role x |
| IDx | A name that represents identity x |
| kx-y | A random value which on the elliptic curve of x to y |
| (rx-y, sx-y) | An elliptic curve signature value of x to y |
| Mx-y | A message that is transmitted from x to y |
| IDBC | An index value of the blockchain information |
| BCx-y | Blockchain information of x to y |
| TSx-y | A timestamp message of x to y |
| Checks that if the difference between two timestamps is less than a specified timestamp | |
| Encrypt an information M using the asymmetric public key of x | |
| Decrypt an information M using the asymmetric private key of x | |
| Encx-y | Encrypted information that uses the asymmetric key of x to y |
| Certx | A certificate of role x that conforms to the X.509 standard |
| BKx | A bank account of role x |
| RTx | A payment receipt of role x |
| ABx | An artwork rent contract of role x |
| ABTID | A transaction number that is issued by an art bank |
| ICx | An artwork insurance contract of role x |
| ICTID | A transaction number which is issued by an insurance company |
| h(.) | A hash function |
| A judgmental that verifies whether A is equal to B |
3.3. Registration Phase
3.4. Smart Contract Initialization
3.5. ECDSA Authentication Process
| Algorithm 1. Role A and role B’s ECDSA signature process |
| ; ; ; ; ; ; |
| Algorithm 2. Role A and role B’s ECDSA verification process |
| ; ; ; ; ; ; ; |
3.6. CA Communication Process
| Algorithm 3. The proposed scheme’s smart contract AP_CAins and AP_CAchk |
| func ins SC AP_CAins (str APid, str APdetail, str APcert, str APtsp) { cnt ++; AP[cnt].id = id; AP[cnt].detail = detail; AP[cnt].cert = cert; AP[cnt].tsp = tsp; } sign str APkey (APid, APdetail, APcert, APtsp); verify str APkey (APid, APdetail, APcert, APtsp); func chk SC AP_CAchk (str APid, str APdetail, str APcert, str APtsp) { rtn APid.exist; rtn APdetail.exist; rtn APcert.exist; rtn APtsp.exist; } |
| Algorithm 4. The proposed scheme’s smart contract CA_APins and CA_APchk |
| func ins SC CA_APins (str CAid, str CAdetail, str CAcert, str CAtsp) { cnt ++; CA[cnt].id = id; CA[cnt].detail = detail; CA[cnt].cert = cert; CA[cnt].tsp = tsp; } sign str CAkey (CAid, CAdetail, CAcert, CAtsp); verify str CAkey (CAid, CAdetail, CAcert, CAtsp); func chk SC CA_APchk (str CAid, str CAdetail, str CAcert, str CAtsp) { rtn CAid.exist; rtn CAdetail.exist; rtn CAcert.exist; rtn CAtsp.exist; } |
3.7. Artwork Rental Phase
| Algorithm 5. The proposed scheme’s smart contract LE_ABins and LE_ABchk |
| func ins SC LE_ABins (str LEid, str LEdetail, str LEcert, str LEtsp) { cnt ++; LE[cnt].id = id; LE[cnt].detail = detail; LE[cnt].cert = cert; LE[cnt].tsp = tsp; } sign str LEkey (LEid, LEdetail, LEcert, LEtsp); verify str LEkey (LEid, LEdetail, LEcert, LEtsp); func chk SC LE_ABchk (str LEid, str LEdetail, str LEcert, str LEtsp) { rtn LEid.exist; rtn LEdetail.exist; rtn LEcert.exist; rtn LEtsp.exist; } |
| Algorithm 6. The proposed scheme’s smart contract AB_LEins and AB_LEchk |
| func ins SC AB_LEins (str ABid, str ABdetail, str ABcert, str AB_LEABtid, str ABtsp) { cnt ++; AB[cnt].id = id; AB[cnt].detail = detail; AB[cnt].cert = cert; AB[cnt].LEABtid = LEABtid; AB[cnt].tsp = tsp; } sign str ABkey (ABid, ABdetail, ABcert, AB_LEABtid, ABtsp); verify str ABkey (ABid, ABdetail, ABcert, AB_LEABtid, ABtsp); func chk SC AB_LEchk (str ABid, str ABdetail, str ABcert, str AB_LEABtid, str ABtsp) { rtn ABid.exist; rtn ABdetail.exist; rtn ABcert.exist; rtn AB_LEABtid.exist; rtn ABtsp.exist; } |
3.8. Insurance Insured Phase
| Algorithm 7. The proposed scheme’s smart contract LE_Icins and LE_Icchk |
| func ins SC LE_Icins (str Leid, str Ledetail, str Lecert, str Letsp) { cnt ++; LE[cnt].id = id; LE[cnt].detail = detail; LE[cnt].cert = cert; LE[cnt].tsp = tsp; } sign str Lekey (Leid, Ledetail, Lecert, Letsp); verify str Lekey (Leid, Ledetail, Lecert, Letsp); func chk SC LE_Icchk (str Leid, str Ledetail, str Lecert, str Letsp) { rtn Leid.exist; rtn Ledetail.exist; rtn Lecert.exist; rtn Letsp.exist; } |
| Algorithm 8. The proposed scheme’s smart contract IC_Leins and IC_Lechk |
| func ins SC IC_Leins (str Icid, str Icdetail, str Iccert, str IC_LEICtid, str Ictsp) { cnt ++; IC[cnt].id = id; IC[cnt].detail = detail; IC[cnt].cert = cert; IC[cnt].LEICtid = LEICtid; IC[cnt].tsp = tsp; } sign str Ickey (Icid, Icdetail, Iccert, IC_LEICtid, Ictsp); verify str Ickey (Icid, Icdetail, Iccert, IC_LEICtid, Ictsp); func chk SC IC_Lechk (str Icid, str Icdetail, str Iccert, str IC_LEICtid, str Ictsp) { rtn Icid.exist; rtn Icdetail.exist; rtn Iccert.exist; rtn IC_LEICtid.exist; rtn Ictsp.exist; } |
3.9. Bank Payment Phase
| Algorithm 9. The proposed scheme’s smart contract LE_BKins and LE_BKchk |
| func ins SC LE_BKins (str LEid, str LEdetail, str LEcert, str LE_LEABtid, str LE_LEICtid, str LEtsp) { cnt ++; LE[cnt].id = id; LE[cnt].detail = detail; LE[cnt].cert = cert; LE[cnt].LEABtid = LEABtid; LE[cnt].LEICtid = LEICtid; LE[cnt].tsp = tsp; } sign str LEkey (LEid, LEdetail, LEcert, LE_LEABtid, LE_LEICtid, LEtsp); verify str LEkey (LEid, LEdetail, LEcert, LE_LEABtid, LE_LEICtid, LEtsp); func chk SC LE_BKchk (str LEid, str LEdetail, str LEcert, str LE_LEABtid, str LE_LEICtid, str LEtsp) { rtn LEid.exist; rtn LEdetail.exist; rtn LEcert.exist; rtn LE_LEABtid.exist; rtn LE_LEICtid.exist; rtn LEtsp.exist; } |
3.10. Contract Fulfillment Phase
| Algorithm 10. The proposed scheme’s smart contract BK_LEins and BK_LEchk |
| func ins SC BK_LEins (str BKid, str BKdetail, str BKcert, str BK_LErt, str BKtsp) { cnt ++; BK[cnt].id = id; BK[cnt].detail = detail; BK[cnt].cert = cert; BK[cnt].LErt = LErt; BK[cnt].tsp = tsp; } sign str BKkey (BKid, BKdetail, BKcert, BK_LErt, BKtsp); verify str BKkey (BKid, BKdetail, BKcert, BK_LErt, BKtsp); func chk SC BK_LEchk (str BKid, str BKdetail, str BKcert, str BK_LErt, str BKtsp) { rtn BKid.exist; rtn BKdetail.exist; rtn BKcert.exist; rtn BK_LErt.exist; rtn BKtsp.exist; } |
| Algorithm 11. The proposed scheme’s smart contract LE_ABins and LE_ABchk |
| func ins SC LE_ABins (str LEid, str LEdetail, str LEcert, str LE_LErt, str LE_LEABtid, str LE_LEICtid, str LEtsp) { cnt ++; LE[cnt].id = id; LE[cnt].detail = detail; LE[cnt].cert = cert; LE[cnt].LErt = LErt; LE[cnt].LEABtid = LEABtid; LE[cnt]. LEICtid = LEICtid; LE[cnt].tsp = tsp; } sign str LEkey (LEid, LEdetail, LEcert, LE_LErt, LE_LEABtid, LE_LEICtid, LEtsp); verify str LEkey (LEid, LEdetail, LEcert, LE_LErt, LE_LEABtid, LE_LEICtid, LEtsp); func chk SC LE_ABchk (str LEid, str LEdetail, str LEcert, str LE_LErt, str LE_LEABtid, str LE_LEICtid, str LEtsp) { rtn LEid.exist; rtn LEdetail.exist; rtn LEcert.exist; rtn LE_LErt.exist; rtn LE_LEABtid.exist; rtn LE_LEICtid.exist; rtn LEtsp.exist; } |
| Algorithm 12. The proposed scheme’s smart contract AB_LEins and AB_LEchk |
| func ins SC AB_LEins (str ABid, str ABdetail, str ABcert, str ABtsp) { cnt ++; AB[cnt].id = id; AB[cnt].detail = detail; AB[cnt].cert = cert; AB[cnt].tsp = tsp; } sign str ABkey (ABid, ABdetail, ABcert, ABtsp); verify str ABkey (ABid, ABdetail, ABcert, ABtsp); func chk SC AB_LEchk (str ABid, str ABdetail, str ABcert, str ABtsp) { rtn ABid.exist; rtn ABdetail.exist; rtn ABcert.exist; rtn ABtsp.exist; } |
3.11. Arbitration Mechanism Phase
4. Analysis of Advantage and Threat Model
4.1. Decentralization and Information Sharing
4.2. Openness
4.3. Privacy and Access Control
4.4. Mutual Authentication
- a.
- Party Y confirms party X.
- b.
- Party X confirms party Y.
4.5. Verifiable
4.6. Integrity and Unforgery
4.7. Traceable
4.8. Non-repudiation
4.9. Resist Man-in-the-Middle Attack
5. Discussions
5.1. Computation Cost Analysis
5.2. Communication Performance Analysis
5.3. Efficiency Quantitative Analysis and Estimation
5.4. Characteristic Comparison
6. Conclusions and Future Work
- (1)
- Lease items and prices are open and transparent:The art banks will form a consortium to jointly register and maintain the information on the artworks. The types of artwork and rental information are open and transparent. The renters can use reasonable rents to rent their favorite artworks, which will increase the renters’ willingness to rent.
- (2)
- Public investment for mutual benefit and common prosperity:Usually, the price of art is extremely expensive. Art banks do not have enough funds to buy a large amount of art. At this time, people can be open to investing and subscribing to art. If the art is successfully rented out, the investing public can get profit dividends. Through the non-tampering feature of the blockchain and investors’ trust in the Art Bank is also improved.
- (3)
- Positive circulation and sustainable operation:Through blockchain technology, renters can quickly find their favorite artworks due to the convenient search mechanism. Due to the open and transparent rental price, the renters’ willingness to rent will be greatly increased. Investors can check the lease status of the artwork they invest in at any time, and the dividend information is open and transparent, which improves investors’ willingness to invest. Such a positive cycle between the two parties will ensure the sustainable operation of the Art Bank.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Parry, R. Recoding the Museum: Digital Heritage and the Technologies of Change; Routledge: London, UK, 2007; pp. 58–81. [Google Scholar]
- Chiou, S.-C.; Wang, Y.-C. The example application of a genetic algorithm for the framework of cultural and creative brand design in Tamsui Historical Museum. Soft Comput. 2018, 22, 2527–2545. [Google Scholar] [CrossRef]
- Chang, C.-W.; Wang, S.-I.; Yang, C.-J.; Shao, K.-T. Fish fauna in subtidal waters adjacent to the National Museum of Marine Biology and Aquarium. P1atax 2011, 8, 41–51. [Google Scholar]
- Triet, T.M.; Due, D.A. Applying the psychoacoustic audio watermarking technique in internet digital traditional music museum in Vietnam. In Proceedings of the 38th Annual 2004 International Carnahan Conference on Security Technology, Albuquerque, NM, USA, 11–14 October 2004; pp. 285–288. [Google Scholar]
- Chen, C.-T.; Lin, K.-D.; Wu, Y.-C.; Lee, K.-L. An Approach of Digital Rights Management for E-Museum with Enforce Context Constraints in RBAC Environments. In Proceedings of the 2006 IEEE International Conference on Systems, Man and Cybernetics, Taipei, Taiwan, 8–11 October 2006; Volume 3, pp. 1871–1878. [Google Scholar]
- Yu, Y.; Dong, Y.; Guo, X. Pricing for sales and per-use rental services with vertical differentiation. Eur. J. Oper. Res. 2018, 270, 586–598. [Google Scholar] [CrossRef]
- Yuan, Y.; Wang, F.-Y. Blockchain: The State of the Art and Future Trends. Acta Autom. Sin. 2016, 42, 481–494. [Google Scholar]
- Kim, H.; Laskowski, M. A Perspective on Blockchain Smart Contracts: Reducing Uncertainty and Complexity in Value Exchange; Social Science Electronic Publishing: Rochester, NY, USA, 2018; pp. 1–6. [Google Scholar]
- Cong, W.; He, Z. Blockchain Disruption and Smart Contracts; Social Science Electronic Publishing: Rochester, NY, USA, 2018; pp. 7–10. [Google Scholar]
- Li, R.; Shen, W.; Yang, Y.; Zhou, L.; Wang, Y. Design and implementation of housing rental distribution system based on blockchain. Softw. Guide 2019, 18, 111–116. [Google Scholar]
- Chen, Q.-L.; Ye, R.-H.; Lin, F.-L. A Blockchain-based Housing Rental System. In Proceedings of the International Conference on Advances in Computer Technology, Information Science and Communications (CTISC 2019), Xiamen, China, 15–17 March 2019; pp. 184–190. [Google Scholar]
- Xue, Q.; Hou, Z.; Ma, H.; Zhu, H.; Ju, X.; Sun, Y. Housing rental system based on blockchain Technology. IoTAIMA 2021, 1948, 012058. [Google Scholar] [CrossRef]
- Huang, Z.; Su, B. Research on hierarchical blockchain architecture based on Ethereum. Comput. Appl. Softw. 2020, 37, 16–19. [Google Scholar]
- Hong, W.; Wang, Q. Construction and analysis of intelligent contract framework for maritime industry based on blockchain. Logist. Technol. 2020, 43, 97–101. [Google Scholar]
- Fu, X.; Wang, H.; Shi, P. A survey of Blockchain consensus algorithms: Mechanism, design and applications. Sci. China Inf. Sci. 2020, 64, 121101. [Google Scholar] [CrossRef]
- Pan, J.; Han, D.; Guo, F.; Zheng, W.; Yu, J.; Chen, W. A visual exploration method for bitcoin trading network topology. Software J. 2019, 30, 3017–3025. [Google Scholar]
- Pan, W.; Huang, X. Identity management and authentication model based on smart contract. Comput. Eng. Des. 2020, 41, 915–919. [Google Scholar]
- Li, F.; Li, J.; Zhen, S.; Zhang, L.-L.; Lu, Y. Market oriented trading model and algorithm of multi microgrid based on smart contract. J. Netw. Inf. Secur. 2020, 6, 56–66. [Google Scholar]
- Chen, C.-L.; Deng, Y.-Y.; Weng, W.; Zhou, M.; Sun, H. A blockchain-based intelligent anti-switch package in tracing logistics system. J. Supercomput. 2021, 77, 7791–7832. [Google Scholar] [CrossRef]
- Chen, C.-L. A secure and traceable E-DRM system based on mobile device. Expert Syst. Appl. 2008, 35, 878–886. [Google Scholar] [CrossRef]
- Chen, C.-L. An all-in-one mobile DRM system design. Int. J. Innov. Comput. Inf. Control 2010, 6, 897–911. [Google Scholar]
- Chen, C.-L.; Tsaur, W.-J.; Chen, Y.-Y.; Chang, Y.-C. A secure mobile DRM system based on cloud architecture. Comput. Sci. Inf. Syst. 2014, 11, 925–941. [Google Scholar] [CrossRef]
- Zhao, B.; Fang, L.; Zhang, H.; Ge, C.; Meng, W.; Liu, L.; Su, C. Y-DWMS: A digital watermark management system based on smart contracts. Sensors 2019, 19, 3091. [Google Scholar] [CrossRef] [Green Version]
- Ma, Z.; Jiang, M.; Gao, H.; Wang, Z. Blockchain for digital rights management. Future Gener. Comput. Syst. 2018, 89, 746–764. [Google Scholar] [CrossRef]
- Vishwa, A.; Hussain, F.-K. A blockchain based approach for multimedia privacy protection and provenance. In Proceedings of the 2018 IEEE Symposium Series on Computational Intelligence (SSCI), Bengaluru, India, 18–21 November 2018; pp. 1941–1945. [Google Scholar]
- Ma, Z.; Huang, W.; Bi, W.; Gao, H.; Wang, Z. A master-slave blockchain paradigm and application in digital rights management. China Commun. 2018, 15, 174–188. [Google Scholar] [CrossRef]
- Lu, Z.; Shi, Y.; Tao, R.; Zhang, Z. Blockchain for digital rights management of design works. In Proceedings of the 2019 IEEE 10th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 18–20 October 2019; pp. 596–603. [Google Scholar]
- Ma, Z. Digital rights management: Model, technology and application. China Commun. 2017, 14, 156–167. [Google Scholar]
- Du Toit, J. Protecting private data using digital rights management. J. Inf. Warf. 2018, 17, 64–77. [Google Scholar]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A survey of IoT security based on a layered architecture of sensing and data analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef]
- Han, W.; Zhu, Z. An ID-based mutual authentication with key agreement protocol for multiserver environment on elliptic curve cryptosystem. Int. J. Commun. Syst. 2014, 27, 1173–1185. [Google Scholar] [CrossRef]
- Boneh, D.; Lynn, B.; Shacham, H. Short signatures from the Weil pairing. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security; Springer: Heidelberg/Berlin, Germany, 2001; pp. 514–532. [Google Scholar]
- Chen, C.-L.; Yang, T.-T.; Chiang, M.-L.; Shih, T.-F. A privacy authentication scheme based on cloud for medical environment. J. Med. Syst. 2014, 38, 143. [Google Scholar] [CrossRef] [PubMed]
- Chen, C.-L.; Yang, T.-T.; Shih, T.-F. A secure medical data exchange protocol based on cloud environment. J. Med. Syst. 2014, 38, 112. [Google Scholar] [CrossRef] [PubMed]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1998; pp. 127–144. [Google Scholar]
- Szabo, N. Smart contracts: Building blocks for digital markets. Extropy J. Transhumanist Thought 1996, 18, 16. [Google Scholar]
- Szabo, N. The Idea of Smart Contracts. 1997. Available online: http://www.fon.hum.uva.nl/rob/Courses/InformationInSpeech/CDROM/Literature/LOTwinterschool2006/szabo.best.vwh.net/smart_contracts_idea.html (accessed on 25 January 2023).
- Vanstone, S. Responses to NIST’s proposal. Commun. ACM 1992, 35, 50–52. [Google Scholar]
- Johnson, D.; Menezes, A.; Vanstone, S. The Elliptic Curve Digital Signature Algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Sierra, J.-M.; Hernández, J.-C.; Alcaide, A.; Torres, J. Validating the Use of Ban Logic; Springer: Berlin/Heidelberg, Germany, 2004; pp. 851–858. [Google Scholar]
- Hyperledger Fabric Docs. Available online: https://hlf.readthedocs.io/en/v2.2.0 (accessed on 25 January 2023).
- Foschini, L.; Gavagna, A.; Martuscelli, G.; Montanari, R. Hyperledger Fabric Blockchain: Chaincode Performance Analysis. In Proceedings of the ICC 2020–2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Uddin, M. Blockchain Medledger: Hyperledger fabric enabled drug traceability system for counterfeit drugs in pharmaceutical industry. Int. J. Pharm. 2021, 597, 120235. [Google Scholar] [CrossRef]
- Marcus, M.J. 5G and IMT for 2020 and beyond. IEEE Wirel. Commun. 2015, 22, 2–3. [Google Scholar] [CrossRef]
- Pongnumkul, S.; Siripanpornchana, C.; Thajchayapong, S. Performance Analysis of Private Blockchain Platforms in Varying Workloads. In Proceedings of the 2017 26th International Conference on Computer Communication and Networks (ICCCN), Vancouver, BC, Canada, 31 July–3 August 2017. [Google Scholar] [CrossRef]
- Nasir, Q.; Qasse, I.A.; Talib, M.A.; Nassif, A.B. Performance Analysis of Hyperledger Fabric Platforms. Secur. Commun. Netw. Hindawi 2018, 2018, 3976093. [Google Scholar] [CrossRef] [Green Version]









| Item | Signature | Sender | Receiver | Signature Verification |
|---|---|---|---|---|
| Phase | ||||
| CA communication process | AP | CA | ||
| CA | AP | |||
| Artwork rental phase | LE | AB | ||
| AB | LE | |||
| Insurance insured phase | LE | IC | ||
| IC | LE | |||
| Bank payment phase | LE | BK | ||
| BK | LE | |||
| Contract fulfillment phase | LE | AB | ||
| AB | LE |
| Party | LE | AB | IC | BK |
|---|---|---|---|---|
| Phase | ||||
| Artwork rental phase | ||||
| Insurance insured phase | ||||
| Bank payment phase | ||||
| Contract fulfillment phase |
| Party | Message Length | Round | 4G (100 Mbps) | 5G(20Gbps) |
|---|---|---|---|---|
| Phase | ||||
| CA communication process | 2Tsig + 2Tasy + 5Tohter = 2*384 + 2*1024 + 2*160 = 3136 bits | 2 | 3136/102,400 = 0.031 ms | 3136/20,480,000 = 0.15 us |
| Artwork rental phase | 2Tsig + 2Tasy + 5Tohter = 2*384 + 2*1024 + 2*160 = 3136 bits | 2 | 3136/102,400 = 0.031 ms | 3136/20,480,000 = 0.15 us |
| Insurance insured phase | 2Tsig + 2Tasy + 5Tohter = 2*384 + 2*1024 + 2*160 = 3136 bits | 2 | 3136/102,400 = 0.031 ms | 3136/20,480,000 = 0.15 us |
| Bank payment phase | 2Tsig + 2Tasy + 5Tohter = 2*384 + 2*1024 + 2*160 = 3136 bits | 2 | 3136/102,400 = 0.031 ms | 3136/20,480,000 = 0.15 us |
| Contract fulfillment phase | 2Tsig + 2Tasy + 5Tohter = 2*384 + 2*1024 + 2*160 = 3136 bits | 2 | 3136/102,400 = 0.031 ms | 3136/20,480,000 = 0.15 us |
| Authors | Year | Item | System | Transactions per Block/Second | |||
|---|---|---|---|---|---|---|---|
| 10 | 100 | 1000 | 10,000 | ||||
| Pongnumkul et al. [46] | 2017 | Throughput | Ethereum 1.5.8 | 27.49 | 38.93 | 34.40 | 20.60 |
| Hyperledger Fabric 0.6 | 68.02 | 299.85 | 251.02 | 159.76 | |||
| Latency | Ethereum 1.5.8 | 0.24 | 2.15 | 25.95 | 484.78 | ||
| Hyperledger Fabric 0.6 | 0.11 | 0.17 | 1.99 | 34.08 | |||
| Nasir et al. [47] | 2018 | Throughput | Hyperledger Fabric 0.6 | 116.69 | 183.86 | 155 | 158.25 |
| Hyperledger Fabric 1.0 | 44 | 174 | 185 | 169 | |||
| Latency | Hyperledger Fabric 0.6 | 0.084 | 0.52 | 5.18 | 46.147 | ||
| Hyperledger Fabric 1.0 | 0.022 | 0.205 | 1.37 | 10.97 | |||
| Authors | Year | Objective | 1 | 2 | 3 | 4 | 5 | 6 |
|---|---|---|---|---|---|---|---|---|
| Chen et al. [11] | 2019 | Proposed a blockchain-based housing rental system | Y | NA | Y | NA | Y | NA |
| Chen et al. [19] | 2020 | Proposed a blockchain-based intelligent anti-switch package in tracing logistics system | Y | NA | Y | Y | Y | Y |
| Xue et al. [12] | 2021 | Proposed a housing rental system based on blockchain technology | Y | NA | NA | NA | Y | NA |
| Our scheme | 2022 | Proposed an artwork rental system based on blockchain technology | Y | Y | Y | Y | Y | Y |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, D.-C.; Liu, L.-C.; Deng, Y.-Y.; Chen, C.-L. An Artwork Rental System Based on Blockchain Technology. Symmetry 2023, 15, 341. https://doi.org/10.3390/sym15020341
Huang D-C, Liu L-C, Deng Y-Y, Chen C-L. An Artwork Rental System Based on Blockchain Technology. Symmetry. 2023; 15(2):341. https://doi.org/10.3390/sym15020341
Chicago/Turabian StyleHuang, Der-Chen, Ling-Chun Liu, Yong-Yuan Deng, and Chin-Ling Chen. 2023. "An Artwork Rental System Based on Blockchain Technology" Symmetry 15, no. 2: 341. https://doi.org/10.3390/sym15020341
APA StyleHuang, D.-C., Liu, L.-C., Deng, Y.-Y., & Chen, C.-L. (2023). An Artwork Rental System Based on Blockchain Technology. Symmetry, 15(2), 341. https://doi.org/10.3390/sym15020341







