Symmetric Color Image Encryption Using a Novel Cross–Plane Joint Scrambling–Diffusion Method
Abstract
1. Introduction
- A novel cross–plane joint scrambling–diffusion method is proposed for color image encryption that simultaneously satisfies security and efficiency requirements.
- By splicing horizontally and vertically, the R, G, and B color planes serve as a whole so that the encryption effect of any color plane cross–influences others, overcoming the potential drawbacks of encrypting each color plane separately.
- The joint scrambling–diffusion method embeds the scrambling process with diffusion to singularly complicate the relationship between plain and cipher images and has a satisfactory execution speed optimized by the vectorization technique.
- The key streams for the encryption process are generated using enhanced 1D chaotic maps and 2D hyperchaotic systems, which can balance the iteration speed and random properties for fast and high–strength encryption.
- The session key of the proposed algorithm consists of both hash value of plain image and a dynamic true random number, which not only achieves high plaintext sensitivity but also ensure forced update for every encryption task.
- The outstanding performance of the proposed algorithm was verified through numerous experiments and analyses using standard test color images.
2. Preliminaries
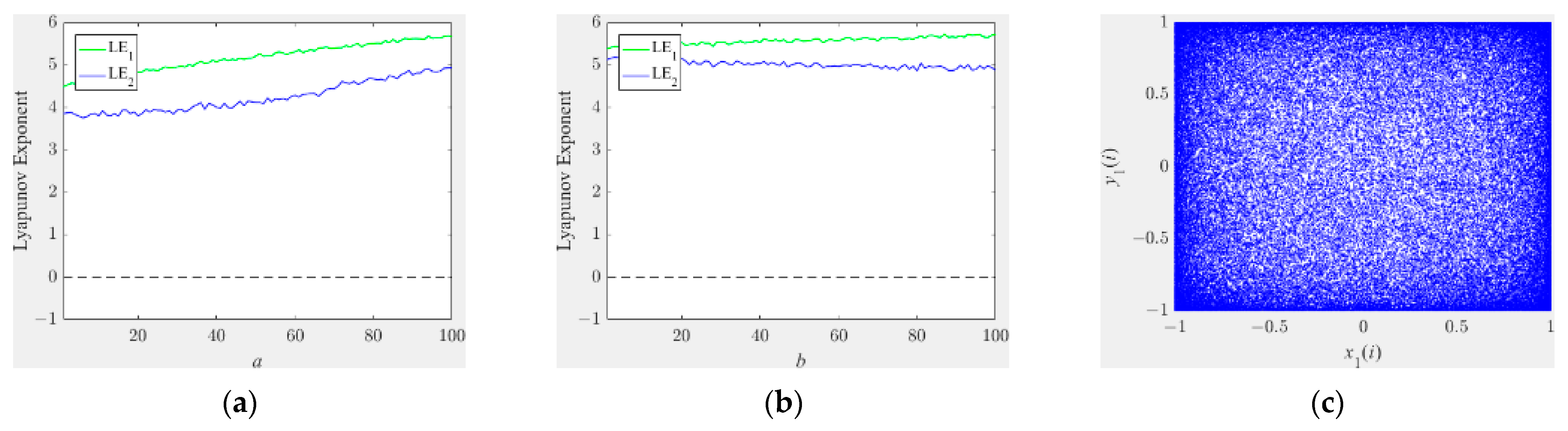
2.1. Employed 2D Hyperchaotic Systems
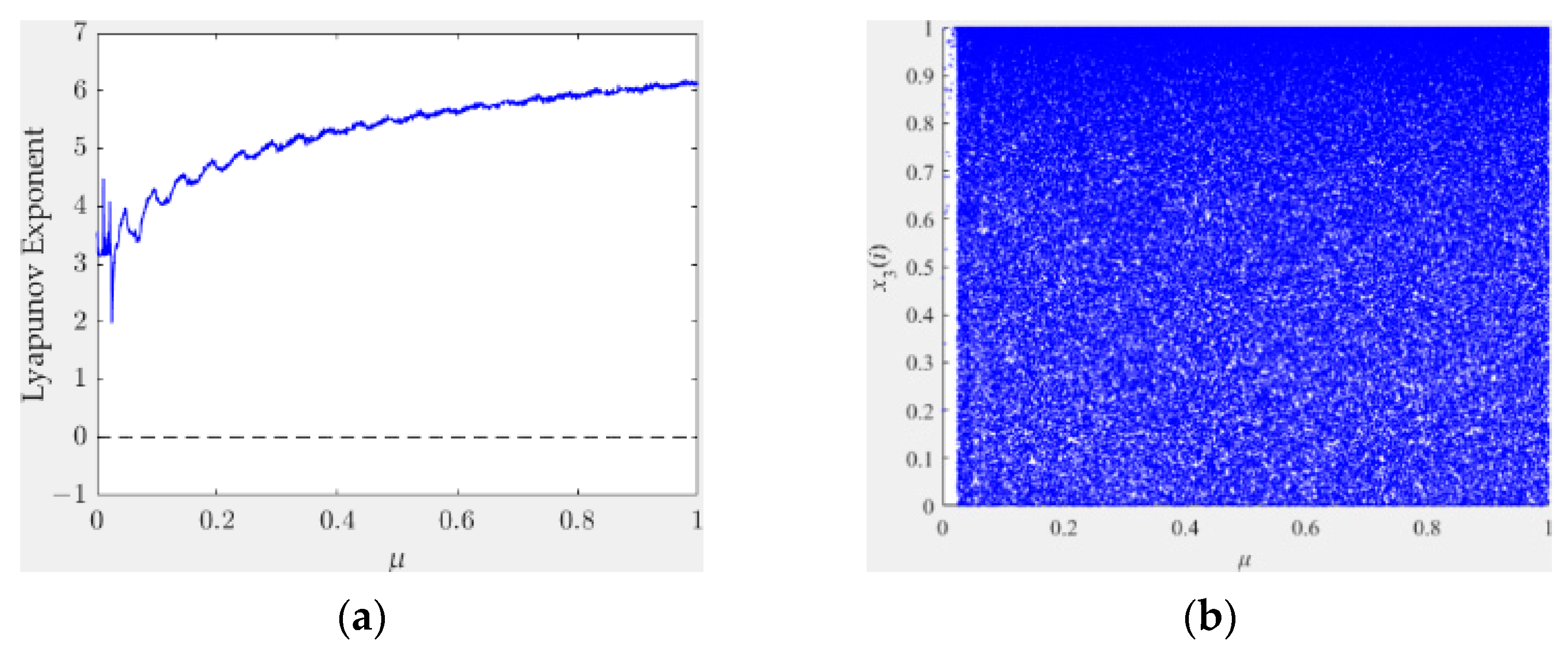
2.2. Employed 1D Chaotic Systems
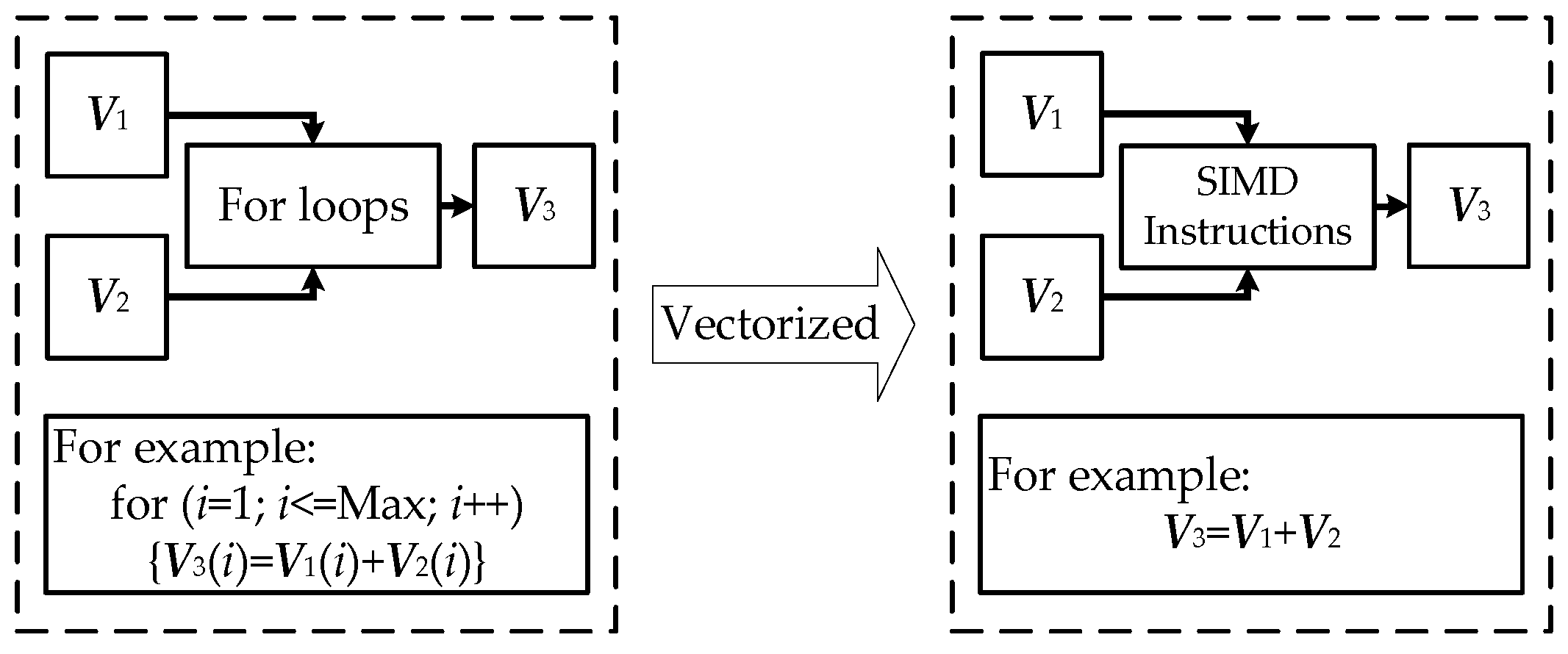
2.3. Vectorization Technique
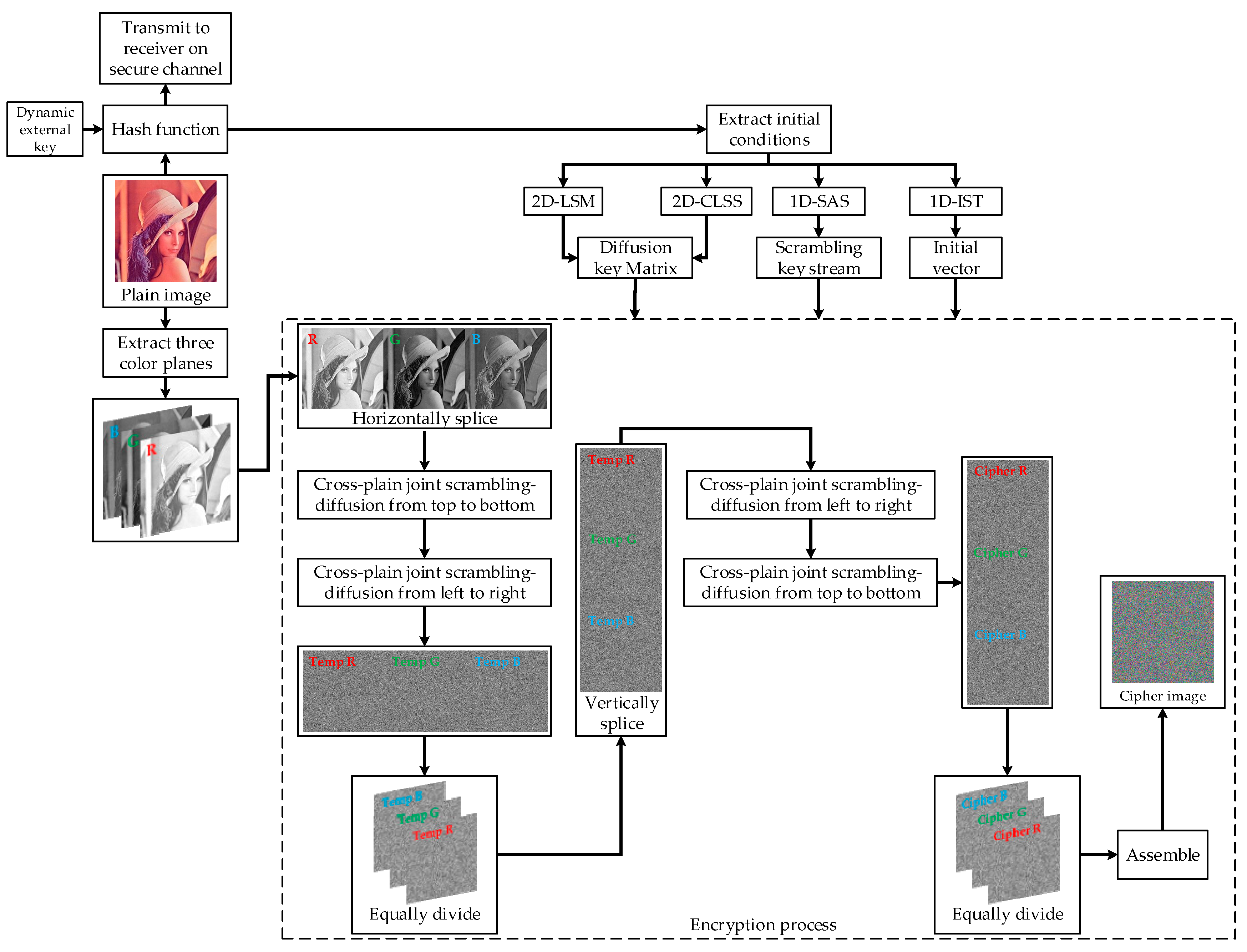
3. Proposed Color Image Encryption Algorithm
3.1. Creation and Extraction of the Session Key
- -
- Step A1: Arrange P and Ke into a sequence, and then input them into SHA–256 so that we can obtain a 256–bit SK for post–processing, which is also transmitted to the receiver on a secure channel (protected by a low–capacity public key cryptosystem) for decryption.
- -
- Step A2: First, extract initial values for the employed chaotic systems by the following method, where the operator ⊕ represents a bit–level exclusive or operation:
- -
- Step A3: Because the pre–iteration of chaotic systems avoids the insecurity of the transient effect and may lead to entirely different encryption results, we employ the remaining bits of SK to determine the pre–iteration times of each chaotic system using the following equation.
3.2. Generation and Schedule of the Key Stream for Diffusion
- -
- Step B1: Input x1(1) and y1(1) into 2D–LSM, and x2(1) and y2(1) into 2D–CLSS, and then separately pre–iterate the 2D–LSM and 2D–CLSS pre1 and pre2 times.
- -
- Step B2: Update x1(1), y1(1), x2(1), and y2(1) to the final state values of the pre–iterations.
- -
- Step B3: Initialize four empty sequences S1, S2, S3, and S4.
- -
- Step B4: Iterate the 2D–LSM and 2D–CLSS W × H times using new x1(1), y1(1), x2(1), and y2(1), and fill S1, S2, S3, and S4 with
- -
- Step B5: Convert all the elements of S1, S2, S3, and S4 into integers in the range [0, 255] using
- -
- Step B6: Initialize three empty sequences DKR, DKG, and DKB.
- -
- Step B7: Fill DKR, DKG, and DKB by
- -
- Step B8: Finally, reshape DKR, DKG, and DKB into three W × H matrices of random numbers for subsequent diffusion and delete S1, S2, S3, and S4.
3.3. Generation and Schedule of the Key Stream for Scrambling
- -
- Step C1: Input x3(1) into the 1D–IST and pre–iterate the 1D–IST pre3 times.
- -
- Step C2: Update x3(1) to the last state value of the pre–iteration.
- -
- Step C3: Initialize an empty sequence S.
- -
- Step C4: Iterate 1D–IST 4W + 4H times using the new x3(1), and fill S with S = {S, x3(i)}, i = 1, 2, …, 4W + 4H − 1, 4W + 4H.
- -
- Step C5: Initialize four empty sequences SK1, SK2, SK3, and SK4.
- -
- Step C6: Fill SK1, SK2, SK3, and SK4 for subsequent scrambling by
- -
- Step C7: Finally, delete S.
3.4. Generation and Schedule of the Key Stream Initial Vector
- -
- Step D1: Input x4(1) into the 1D–SAS and pre–iterate the 1D–SAS pre4 times.
- -
- Step D2: Update x4(1) to the last state value of the pre–iteration.
- -
- Step D3: Initialize an empty sequence, S.
- -
- Step D4: Iterate 1D–SAS 3W times using the new x4(1), and fill S with S = {S, x4(i)}, i = 1, 2, …, 3W − 1, 3W.
- -
- Step D5: Initialize an empty sequence, IV.
- -
- Step D6: Fill IV to commence the subsequent diffusion process by
- -
- Step D7: Finally, delete S.
3.5. Encryption Process
| Algorithm 1 Cross–plane Joint Scrambling–diffusion Method |
| Input: P, IV, DKR, DKG, DKB, SK1, SK2, SK3, SK4 |
| Output: C |
| 1: Extract three color planes from plain image by PR = P(:, :, 1), PG = P(:, :, 2), PB = P(:, :, 3) |
| 2: Splice three color planes and diffusion key matrixes horizontally by M1 = {PR, PG, PB} and K1 = {DKR, DKG, DKB}. |
| //Use IV, K1(1, :), and SK1(1) to start diffusion from first row of M1 and circular shift (>>) it |
| 3: Temp ← (IV + M1(1, :))%256 4: Temp ← K1(1, :)⊕Temp 5: TC(1, :) ←Temp >> SK1(1) |
| //Continue to encryption the remainder of rows of M1 |
| 6: for i from 2 to H − 1 7: Temp ← (TC(i − 1, :) + M1(i, :))%256 8: Temp ← K1(i, :)⊕Temp 9: TC(i, :) ← Temp >> SK1(i)) 10: end for |
| //Update IV and use K1(:, 1), and SK2(1) to start diffusion from the first column of TC and circular shift it |
| 11: IV ← TC(:, 3W) 12: Temp ← (IV + TC(:, 1))%256 13: Temp ← K1(:, 1)⊕Temp 14: TC(:, 1) ← Temp >> SK2(1) |
| //Continue to encryption the remainder columns of TC |
| 15: for i from 2 to 3W 16: Temp ← (TC(:, i − 1) + TC(:, i))%256 17: Temp ← K1(:, i)⊕Temp 18: TC(:, i) ← Temp >> SK2(i) 19: end for |
| 20: Cut the TC and resplice it in vertical by M2 = {TC(1:W, :); TC(W + 1:2W, :), TC(2W + 1:3W, :)} and also resplice three key matrixes in vertical by K2 = {DKR; DKG; DKB} |
| //Update IV and use K2(:, 1), and SK3(1) to start diffusion from first column of M2 and circular shift it |
| 21: IV ← M2(:, W) 22: Temp ← (IV+ M2(:, 1))%256 23: Temp ← K2(:, 1)⊕Temp 24: TC(:, 1) ← Temp >> SK3(1) |
| //Continue to encryption the remainder columns of TC |
| 25: for i from 2 to W 26: Temp ← (TC(:, i − 1)+ M2(:, i))%256 27: Temp ← K2(:, i)⊕Temp 28: TC(:, i) ← Temp >> SK3(i) 29: end for |
| //Update IV and use K2(1, :), and SK4(1) to start diffusion from the first row of TC and circular shift it |
| 30: IV ← TC(3H, :) 31: Temp ← (IV + TC(1, :))%256 32: Temp ← K2(1, :)⊕Temp 33: TC(1, :) ← Temp >> SK4(1) |
| //Continue to encryption the remainder of rows of TC |
| 34: for i from 2 to 3H 35: Temp ← (TC(i−1, :)+ TC (i, :))%256 36: Temp ← K2(i, :)⊕Temp 37: TC(i, :) ← Temp >> SK4(i) 38: end for |
| 39: Obtain the final cipher color image by C(:, :, 1) = TC(1:H, :), C(:, :, 2) = TC(H + 1:2H, :), C(:, :, 3) = TC(2H + 1:3H, :) |
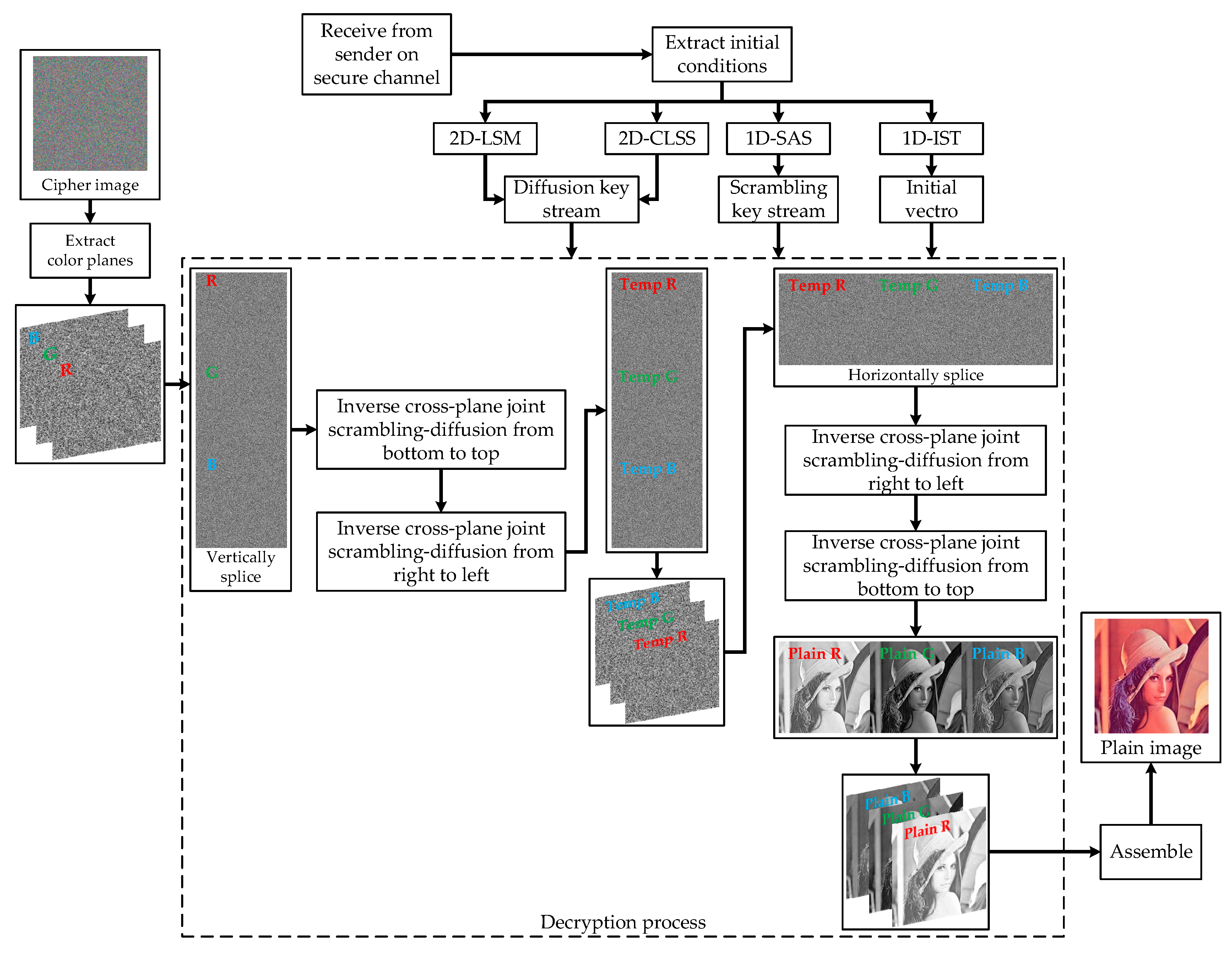
3.6. Decryption Process
4. Experimental Results and Analyses
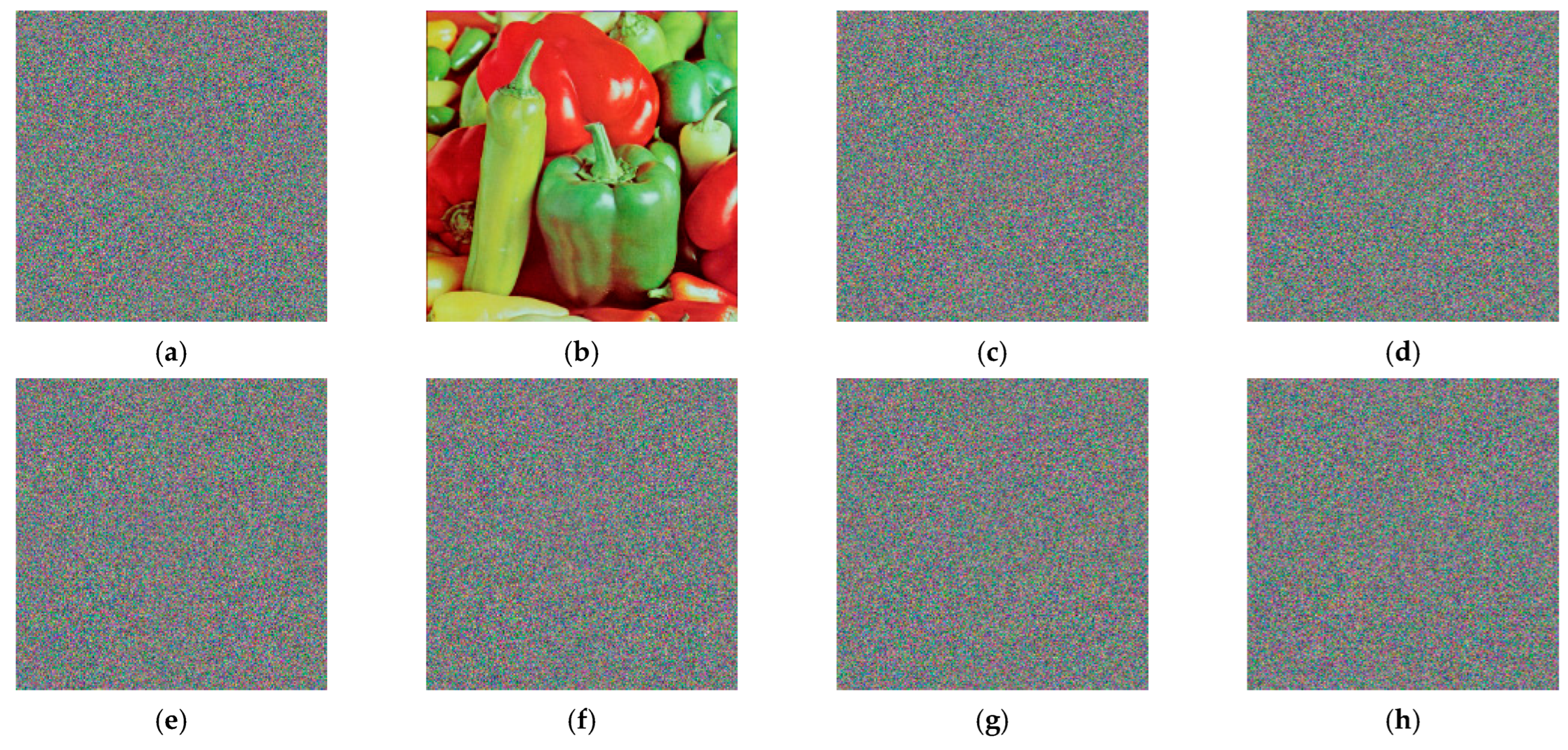
4.1. Histogram Analysis
4.2. Randomness Analysis
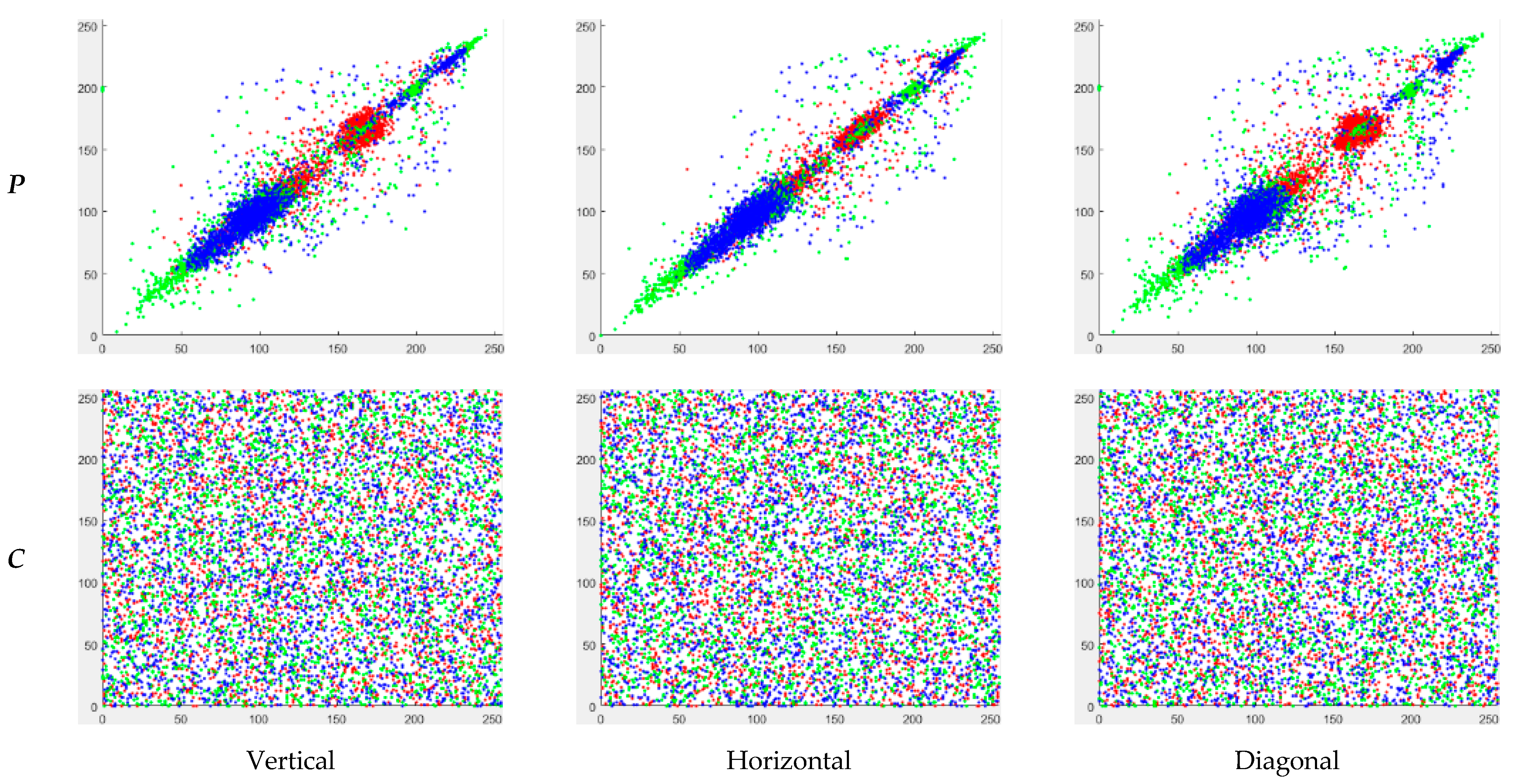
4.3. Correlation Analysis between Adjacent Pixels
4.4. Information Entropy
4.5. Plaintext Sensitivity Analysis
4.6. Key Sensitivity Analysis
4.7. Key Space Analysis
4.8. Resistance against CPA/CCA Analysis
4.9. Time Complexity Analysis
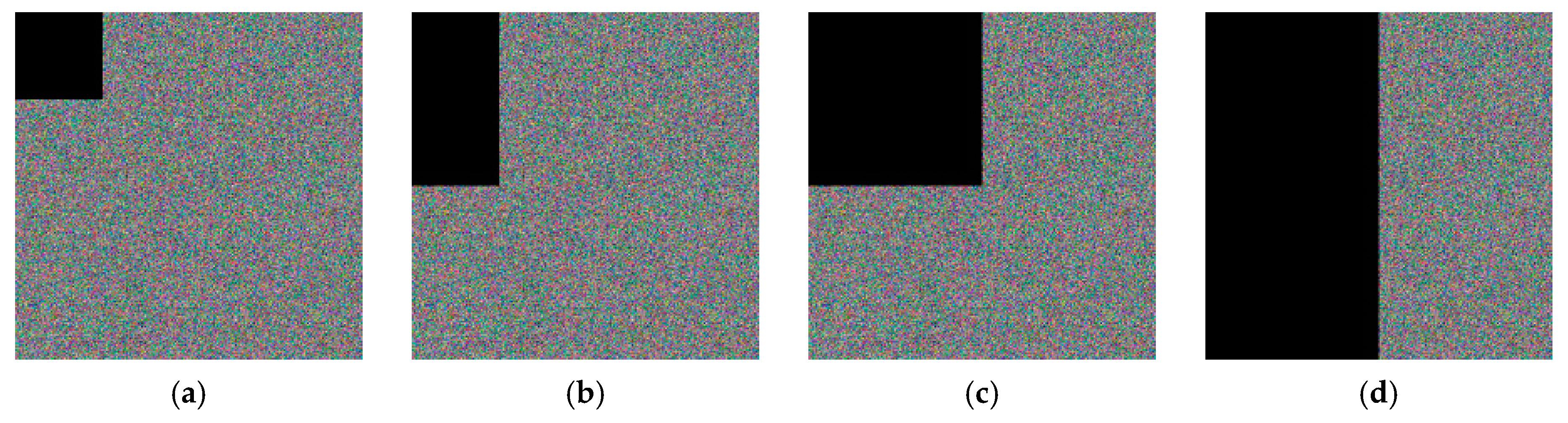
4.10. Robustness Analysis
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| 3DES | Triple Data Encryption Standard |
| AES | Advanced Encryption Standard |
| DNA | Deoxyribonucleic Acid |
| CMY | Cyan–Magenta–Yellow |
| HSV | Hue–Saturation–Value |
| RGB | Red–Green–Blue |
| YCbCr | Y is luma (brightness), Cb is blue minus luma (B–Y), and Cr is red minus luma (R–Y) |
| 2D–LSM | Two–Dimensional Logistic–Sine Map |
| LE | Lyapunov Exponents |
| 2D–CLSS | Two–Dimensional Chaotic–Logistic–Sine–Sine |
| 1D–IST | One–Dimensional Improved Sine–Tangent |
| 1D–SAS | One–Dimensional Sine–Arcsine |
| AMD | Advanced Micro Devices |
| ARM | Advanced RISC Machines |
| MATLAB | Matrix Laboratory |
| CPA | Chosen Plaintext Attack |
| CCA | Chosen Ciphertext Attack |
| NPCR | Number of Pixels Change Rate |
| UACI | Unified Average Changing Intensity |
| PSNR | Peak Signal–to–Noise Ratio |
References
- Mathivanan, P.; Ganesh, A.B. QR code based color image cryptography for the secured transmission of ECG signal. Multimed. Tools Appl. 2019, 78, 6763–6786. [Google Scholar] [CrossRef]
- Stryker, S.; Kapadia, A.J.; Greenberg, J.A. Application of machine learning classifiers to X-ray diffraction imaging with medically relevant phantoms. Med. Phys. 2022, 49, 532–546. [Google Scholar] [CrossRef]
- Mathivanan, P.; Ganesh, A.B. ECG steganography using Base64 encoding and pixel swapping technique. Multimed. Tools Appl. 2023, 82, 14945–14962. [Google Scholar] [CrossRef]
- Evsutin, O.; Dzhanashia, K. Watermarking schemes for digital images: Robustness overview. Signal Process. Image Commun. 2022, 100, 116523. [Google Scholar] [CrossRef]
- Wan, W.; Wang, J.; Zhang, Y.; Li, J.; Yu, H.; Sun, J. A comprehensive survey on robust image watermarking. Neurocomputing 2022, 488, 226–247. [Google Scholar] [CrossRef]
- NIST SP 958; Data Encryption Standard (DES). NIST: Gaithersburg, MD, USA, 2001. Available online: https://csrc.nist.gov/pubs/book-section/2001/01/data-encryption-standard/final (accessed on 30 May 2023).
- FIPS Standard 197; Advanced Encryption Standard (AES). NIST: Gaithersburg, MD, USA, 2001. Available online: https://csrc.nist.gov/pubs/fips/197/final (accessed on 30 May 2023).
- Lin, H.; Wang, C.; Cui, L.; Sun, Y.; Xu, C.; Yu, F. Brain-Like Initial-Boosted Hyperchaos and Application in Biomedical Image Encryption. IEEE Trans. Ind. Inform. 2022, 18, 8839–8850. [Google Scholar] [CrossRef]
- Li, X.; Mou, J.; Banerjee, S.; Wang, Z.; Cao, Y. Design and DSP implementation of a fractional-order detuned laser hyperchaotic circuit with applications in image encryption. Chaos Solitons Fractals 2022, 159, 112133. [Google Scholar] [CrossRef]
- Zia, U.; McCartney, M.; Scotney, B.; Martinez, J.; AbuTair, M.; Memon, J.; Sajjad, A. Survey on image encryption techniques using chaotic maps in spatial, transform and spatiotemporal domains. Int. J. Inf. Secur. 2022, 21, 917–935. [Google Scholar] [CrossRef]
- Himthani, V.; Dhaka, V.S.; Kaur, M.; Singh, D.; Lee, H.-N. Systematic Survey on Visually Meaningful Image Encryption Techniques. IEEE Access 2022, 10, 98360–98373. [Google Scholar] [CrossRef]
- Zhou, S.; Zhao, Z.; Wang, X. Novel chaotic colour image cryptosystem with deep learning. Chaos Solitons Fractals 2022, 161, 112380. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Sun, J.; Zhang, X.; Sun, Y.; Iu, H.H. Memristor-coupled asymmetric neural networks: Bionic modeling, chaotic dynamics analysis and encryption application. Chaos Solitons Fractals 2023, 166, 112905. [Google Scholar] [CrossRef]
- Liang, Q.; Zhu, C. A new one-dimensional chaotic map for image encryption scheme based on random DNA coding. Opt. Laser Technol. 2023, 160, 109033. [Google Scholar] [CrossRef]
- Arthi, G.; Thanikaiselvan, V.; Amirtharajan, R. 4D Hyperchaotic map and DNA encoding combined image encryption for secure communication. Multimed. Tools Appl. 2022, 81, 15859–15878. [Google Scholar] [CrossRef]
- Liu, X.; Tong, X.; Wang, Z.; Zhang, M. A new n-dimensional conservative chaos based on Generalized Hamiltonian System and its’ applications in image encryption. Chaos Solitons Fractals 2022, 154, 111693. [Google Scholar] [CrossRef]
- Signing, V.F.; Tegue, G.G.; Kountchou, M.; Njitacke, Z.; Tsafack, N.; Nkapkop, J.; Etoundi, C.L.; Kengne, J. A cryptosystem based on a chameleon chaotic system and dynamic DNA coding. Chaos Solitons Fractals 2022, 155, 111777. [Google Scholar] [CrossRef]
- Njitacke, Z.T.; Nkapkop, J.D.D.; Signing, V.F.; Tsafack, N.; Sone, M.E.; Awrejcewicz, J. Novel Extreme Multistable Tabu Learning Neuron: Circuit Implementation and Application to Cryptography. IEEE Trans. Ind. Inform. 2023, 19, 8943–8952. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X.; Yan, X.; Li, Q.; Wang, X. Image Encryption Based on Chaotic Sub-Block Scrambling and Chaotic Digit Selection Diffusion. Opt. Lasers Eng. 2020, 134, 106202. [Google Scholar] [CrossRef]
- Xu, C.; Sun, J.; Wang, C. A novel image encryption algorithm based on bit-plane matrix rotation and hyper chaotic systems. Multimed. Tools Appl. 2020, 79, 5573–5593. [Google Scholar] [CrossRef]
- Alexan, W.; Chen, Y.-L.; Por, L.Y.; Gabr, M. Hyperchaotic Maps and the Single Neuron Model: A Novel Framework for Chaos-Based Image Encryption. Symmetry 2023, 15, 1081. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Chen, Y.; Zhang, Y. A visually secure image encryption scheme based on compressive sensing. Signal Process. 2017, 134, 35–51. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, M.; Tong, X.; Wang, Z. Image compression and encryption algorithm based on 2D compressive sensing and hyperchaotic system. Multimed. Syst. 2022, 28, 595–610. [Google Scholar] [CrossRef]
- Zhang, Q.; Guo, L.; Wei, X. Image encryption using DNA addition combining with chaotic maps. Math. Comput. Model. 2010, 52, 2028–2035. [Google Scholar] [CrossRef]
- Ghanbari, H.; Enayatifar, R.; Motameni, H. Chaos-based image encryption using hybrid model of linear-feedback shift register system and deoxyribonucleic acid. Multimed. Tools Appl. 2022, 81, 31815–31830. [Google Scholar] [CrossRef]
- Xiao, Y.; Lin, Z.-R.; Xu, Q.; Du, J.; Gong, L.-H. Image encryption algorithm based on semi-tensor product theory. J. Mod. Opt. 2022, 69, 1063–1078. [Google Scholar] [CrossRef]
- Ping, P.; Yang, X.; Zhang, X.; Mao, Y.; Khalid, H. Generating visually secure encrypted images by partial block pairing-substitution and semi-tensor product compressed sensing. Digit. Signal Process. 2022, 120, 103263. [Google Scholar] [CrossRef]
- Demirtaş, M. A new RGB color image encryption scheme based on cross-channel pixel and bit scrambling using chaos. Optik 2022, 265, 169430. [Google Scholar] [CrossRef]
- Liu, Z.; Wu, C.; Wang, J.; Hu, Y. A Color Image Encryption Using Dynamic DNA and 4-D Memristive Hyper-Chaos. IEEE Access 2019, 7, 78367–78378. [Google Scholar] [CrossRef]
- Basha, S.M.; Mathivanan, P.; Ganesh, A.B. Bit level color image encryption using Logistic-Sine-Tent-Chebyshev (LSTC) map. Optik 2022, 259, 168956. [Google Scholar] [CrossRef]
- Kumar, K.; Roy, S.; Rawat, U.; Malhotra, S. IEHC: An efficient image encryption technique using hybrid chaotic map. ChaosSolitons Fractals 2022, 158, 111994. [Google Scholar] [CrossRef]
- Lone, M.A.; Qureshi, S. RGB image encryption based on symmetric keys using Arnold transform, 3D chaotic map and affine hill cipher. Optik 2022, 260, 168880. [Google Scholar] [CrossRef]
- Yan, S.; Li, L.; Gu, B.; Cui, Y.; Wang, J.; Song, J. Design of hyperchaotic system based on multi-scroll and its encryption algorithm in color image. Integration 2023, 88, 203–221. [Google Scholar] [CrossRef]
- Ghadirli, H.M.; Nodehi, A.; Enayatifar, R. An overview of encryption algorithms in color images. Signal Process. 2019, 164, 163–185. [Google Scholar] [CrossRef]
- Tahiri, M.A.; Karmouni, H.; Bencherqui, A.; Daoui, A.; Sayyouri, M.; Qjidaa, H.; Hosny, K.M. New color image encryption using hybrid optimization algorithm and Krawtchouk fractional transformations. Vis. Comput. 2022, 1–26. [Google Scholar] [CrossRef]
- Singh, M.; Singh, A.K. A comprehensive survey on encryption techniques for digital images. Multimed. Tools Appl. 2023, 82, 11155–11187. [Google Scholar] [CrossRef]
- Chai, X.; Zhi, X.; Gan, Z.; Zhang, Y.; Chen, Y.; Fu, J. Combining improved genetic algorithm and matrix semi-tensor product (STP) in color image encryption. Signal Process. 2021, 183, 108041. [Google Scholar] [CrossRef]
- Yang, Y.-G.; Wang, B.-P.; Zhou, Y.-H.; Shi, W.-M.; Liao, X. Efficient color image encryption by color-grayscale conversion based on steganography. Multimed. Tools Appl. 2022, 82, 10835–10866. [Google Scholar] [CrossRef]
- Hosny, K.M.; Kamal, S.T.; Darwish, M.M. A color image encryption technique using block scrambling and chaos. Multimed. Tools Appl. 2022, 81, 505–525. [Google Scholar] [CrossRef]
- Wang, X.; Chen, X.; Feng, S.; Liu, C. Color image encryption scheme combining cross-plane Zigzag scrambling and pseudo-random combination RGB component diffusion. Optik 2022, 269, 169933. [Google Scholar] [CrossRef]
- Zhang, X.; Gong, Z. Color image encryption algorithm based on 3D Zigzag transformation and view planes. Multimed. Tools Appl. 2022, 81, 31753–31785. [Google Scholar] [CrossRef]
- Jasra, B.; Moon, A.H. Color image encryption and authentication using dynamic DNA encoding and hyper chaotic system. Expert Syst. Appl. 2022, 206, 117861. [Google Scholar] [CrossRef]
- Wang, S.; Peng, Q.; Du, B. Chaotic color image encryption based on 4D chaotic maps and DNA sequence. Opt. Laser Technol. 2022, 148, 107753. [Google Scholar] [CrossRef]
- Ouyang, X.; Luo, Y.; Liu, J.; Cao, L.; Liu, Y. A color image encryption method based on memristive hyperchaotic system and DNA encryption. Int. J. Mod. Phys. B 2020, 34, 2050014. [Google Scholar] [CrossRef]
- Li, D.; Li, J.; Di, X.; Li, B. Design of cross-plane colour image encryption based on a new 2D chaotic map and combination of ECIES framework. Nonlinear Dyn. 2023, 111, 2917–2942. [Google Scholar] [CrossRef]
- Zhang, H.; Li, Z.; Yan, P.; Wang, X.; Wang, X. A plain-text independent color image encryption system with multi-thread permutation and multi-channel diffusion. Int. J. Mod. Phys. C 2022, 33, 2250074. [Google Scholar] [CrossRef]
- Li, T.; Shi, J.; Zhang, D. Color image encryption based on joint permutation and diffusion. J. Electron. Imaging 2021, 30, 013008. [Google Scholar] [CrossRef]
- Teng, L.; Wang, X.; Yang, F.; Xian, Y. Color image encryption based on cross 2D hyperchaotic map using combined cycle shift scrambling and selecting diffusion. Nonlinear Dyn. 2021, 105, 1859–1876. [Google Scholar] [CrossRef]
- Yu, J.; Xie, W.; Zhong, Z.; Wang, H. Image encryption algorithm based on hyperchaotic system and a new DNA sequence operation. Chaos Solitons Fractals 2022, 162, 112456. [Google Scholar] [CrossRef]
- Zhou, S.; Qiu, Y.; Wang, X.; Zhang, Y. Novel image cryptosystem based on new 2D hyperchaotic map and dynamical chaotic S-box. Nonlinear Dyn. 2023, 111, 9571–9589. [Google Scholar] [CrossRef]
- Hua, Z.; Zhu, Z.; Chen, Y.; Li, Y. Color image encryption using orthogonal Latin squares and a new 2D chaotic system. Nonlinear Dyn. 2021, 104, 4505–4522. [Google Scholar] [CrossRef]
- Teng, L.; Wang, X.; Xian, Y. Image encryption algorithm based on a 2D-CLSS hyperchaotic map using simultaneous permutation and diffusion. Inf. Sci. 2022, 605, 71–85. [Google Scholar] [CrossRef]
- Belazi, A.; Kharbech, S.; Aslam, N.; Talha, M.; Xiang, W.; Iliyasu, A.M.; Abd El-Latif, A.A. Improved Sine-Tangent chaotic map with application in medical images encryption. J. Inf. Secur. Appl. 2022, 66, 103131. [Google Scholar] [CrossRef]
- Wang, X.; Liu, H. Cross-plane multi-image encryption using chaos and blurred pixels. Chaos Solitons Fractals 2022, 164, 112586. [Google Scholar] [CrossRef]
- Al Hasib, A.; Cebrian, J.M.; Natvig, L. A vectorized k-means algorithm for compressed datasets: Design and experimental analysis. J. Supercomput. 2018, 74, 2705–2728. [Google Scholar] [CrossRef]
- Kelefouras, V.; Keramidas, G. Design and Implementation of 2D Convolution on x86/x64 Processors. IEEE Trans. Parallel Distrib. Syst. 2022, 33, 3800–3815. [Google Scholar] [CrossRef]
- Qu, J.; Faney, T.; de Hemptinne, J.-C.; Yousef, S.; Gallinari, P. PTFlash: A vectorized and parallel deep learning framework for two-phase flash calculation. Fuel 2023, 331, 125603. [Google Scholar] [CrossRef]
- Haahr, M. Random.Org. Available online: https://www.random.org/ (accessed on 2 March 2021).
- Pareschi, F.; Rovatti, R.; Setti, G. On Statistical Tests for Randomness Included in the NIST SP800-22 Test Suite and Based on the Binomial Distribution. IEEE Trans. Inf. Forensics Secur. 2012, 7, 491–505. [Google Scholar] [CrossRef]
- Wu, Y.; Zhou, Y.; Saveriades, G.; Agaian, S.; Noonan, J.P.; Natarajan, P. Local Shannon entropy measure with statistical tests for image randomness. Inf. Sci. 2013, 222, 323–342. [Google Scholar] [CrossRef]
- Li, Z.; Peng, C.; Li, L.; Zhu, X. A novel plaintext-related image encryption scheme using hyper-chaotic system. Nonlinear Dyn. 2018, 94, 1319–1333. [Google Scholar] [CrossRef]











| External Key | Ke |
|---|---|
| Value | b3659e41054ea5afd76c1c988c91ac1985abcbe4d0196af2c1393d35ba7032a3 |
| Image | Color Plane | Plain | Cipher | p-Value | Result |
|---|---|---|---|---|---|
| House | R | 2.5858 × 105 | 261.5078 | 0.9088 | Pass |
| G | 2.9916 × 105 | 225.7969 | 0.9987 | ||
| B | 3.9404 × 105 | 279.1328 | 0.9702 | ||
| Lena | R | 5.9307 × 104 | 237.2422 | 0.9929 | Pass |
| G | 3.1305 × 104 | 237.5078 | 0.9926 | ||
| B | 8.0949 × 104 | 239.3438 | 0.9903 | ||
| Mandrill | R | 8.2840 × 104 | 253.6230 | 0.9543 | Pass |
| G | 1.4281 × 105 | 236.1797 | 0.9938 | ||
| B | 7.9943 × 104 | 253.4082 | 0.9553 | ||
| Peppers | R | 2.1319 × 105 | 231.9101 | 0.9966 | Pass |
| G | 3.1838 × 105 | 254.3223 | 0.9512 | ||
| B | 4.9143 × 105 | 267.7500 | 0.8548 | ||
| Oakland | R | 1.7335 × 106 | 271.7480 | 0.8113 | Pass |
| G | 3.5513 × 106 | 218.3091 | 0.9996 | ||
| B | 9.2953 × 106 | 240.4688 | 0.9892 | ||
| San Diego | R | 2.8155 × 105 | 248.0635 | 0.9740 | Pass |
| G | 1.4036 × 106 | 267.9277 | 0.8530 | ||
| B | 1.5631 × 1046 | 264.8472 | 0.8820 |
| No. | 01 | 02 | 03 | 04 | 05 |
|---|---|---|---|---|---|
| Test | Frequency | Block Frequency | Cumulative Sums | Runs | Longest Runs of Ones |
| No. | 06 | 07 | 08 | 09 | 10 |
| Test | Rank | Spectral DFT | Nonperiodic Template Matchings | Overlapping Template Matchings | Universal Statistical |
| No. | 11 | 12 | 13 | 14 | 15 |
| Test | Approximate Entropy | Random Excursions | Random Excursions Variant | Serial | Linear Complexity |
| Test | p-Value | |||||||
|---|---|---|---|---|---|---|---|---|
| DK | SK | House | Lena | Mandrill | Peppers | Oakland | San Diego | |
| 01 | 0.1489 | 0.5804 | 0.5812 | 0.9255 | 0.2884 | 0.9448 | 0.9343 | 0.1917 |
| 02 | 0.8324 | 0.6731 | 0.3556 | 0.1999 | 0.3948 | 0.4201 | 0.1900 | 0.9025 |
| 03 | 0.7625 | 0.2767 | 0.2546 | 0.0676 | 0.6383 | 0.5122 | 0.3610 | 0.4484 |
| 04 | 0.2953 | 0.6168 | 0.3007 | 0.2520 | 0.3483 | 0.8983 | 0.7339 | 0.3003 |
| 05 | 0.5049 | 0.2370 | 0.8657 | 0.0461 | 0.0976 | 0.2630 | 0.4957 | 0.9579 |
| 06 | 0.9685 | 0.7866 | 0.7766 | 0.5413 | 0.4749 | 0.7779 | 0.1998 | 0.7498 |
| 07 | 0.6763 | 0.7967 | 0.3500 | 0.7289 | 0.9643 | 0.8084 | 0.7782 | 0.3455 |
| 08 | 0.4701 | 0.2660 | 0.8263 | 0.0470 | 0.7748 | 0.8770 | 0.2951 | 0.9938 |
| 09 | 0.4711 | 0.4672 | 0.6833 | 0.9006 | 0.9355 | 0.9641 | 0.5907 | 0.3607 |
| 10 | 0.0505 | 0.1085 | 0.3930 | 0.1791 | 0.5405 | 0.6017 | 0.7792 | 0.6711 |
| 11 | 0.9567 | 0.8608 | 0.2240 | 0.7519 | 0.2587 | 0.3205 | 0.6995 | 0.0711 |
| 12 | 0.4899 | 0.0106 | 0.9687 | 0.7757 | 0.3329 | 0.1835 | 0.7780 | 0.1406 |
| 13 | 0.0809 | 0.4519 | 0.3803 | 0.6973 | 0.0573 | 0.4034 | 0.2162 | 0.5365 |
| 14 | 0.6794 | 0.7734 | 0.8624 | 0.4620 | 0.6705 | 0.2373 | 0.8090 | 0.8095 |
| 15 | 0.6932 | 0.8696 | 0.2014 | 0.8432 | 0.7316 | 0.8360 | 0.5135 | 0.9171 |
| Result | Pass | Pass | Pass | Pass | Pass | Pass | Pass | Pass |
| Direction | Color Plane | Image | ||||||
|---|---|---|---|---|---|---|---|---|
| House | Lena | Mandrill | Peppers | Oakland | San Diego | |||
| Vertical | R | P | 0.9326 | 0.9683 | 0.8624 | 0.9639 | 0.9218 | 0.9216 |
| C | −0.0001 | −0.0017 | −0.0013 | 0.0004 | 0.0017 | 0.0002 | ||
| G | P | 0.9409 | 0.9709 | 0.7591 | 0.9771 | 0.8512 | 0.9139 | |
| C | 0.0036 | −0.0007 | 0.0027 | 0.0006 | −0.0001 | −0.0001 | ||
| B | P | 0.9668 | 0.9423 | 0.8782 | 0.9619 | 0.6958 | 0.8941 | |
| C | −0.0042 | 0.0024 | −0.0024 | −0.0008 | 0.0001 | −0.0017 | ||
| Horizontal | R | P | 0.9642 | 0.9393 | 0.9218 | 0.9618 | 0.9331 | 0.9245 |
| C | 0.0055 | −0.0015 | 0.0024 | 0.0003 | 0.0009 | −0.0009 | ||
| G | P | 0.9760 | 0.9398 | 0.8643 | 0.9777 | 0.8672 | 0.9169 | |
| C | 0.0035 | −0.0013 | −0.0003 | 0.0033 | 0.0003 | 0.0002 | ||
| B | P | 0.9777 | 0.8911 | 0.9071 | 0.9628 | 0.7111 | 0.8975 | |
| C | −0.0007 | −0.0016 | 0.0020 | −0.0001 | 0.0004 | −0.0001 | ||
| Diagonal | R | P | 0.9126 | 0.9306 | 0.8531 | 0.9575 | 0.8933 | 0.9027 |
| C | −0.0004 | 0.0024 | −0.0010 | 0.0002 | −0.0007 | −0.0010 | ||
| G | P | 0.9317 | 0.9327 | 0.7299 | 0.9698 | 0.8056 | 0.8952 | |
| C | −0.0031 | 0.0015 | −0.0017 | 0.0005 | 0.0001 | −0.0005 | ||
| B | P | 0.9627 | 0.8712 | 0.8411 | 0.9478 | 0.6554 | 0.8717 | |
| C | −0.0020 | −0.0005 | 0.0012 | −0.0004 | −0.0013 | 0.0005 | ||
| Algorithm | Color Plane | Ours | Ref. [43] | Ref. [45] | Ref. [46] | Ref. [47] |
|---|---|---|---|---|---|---|
| Vertical | R | −0.0017 | −0.0096 | 0.0012 | −0.0046 | −0.0013 |
| G | −0.0007 | −0.0032 | 0.0019 | −0.0166 | 0.0020 | |
| B | 0.0024 | −0.0023 | 0.0025 | −0.0042 | 0.0001 | |
| Horizontal | R | −0.0024 | −0.0050 | −0.0012 | −0.0057 | 0.0033 |
| G | −0.0015 | 0.0025 | 0.0025 | −0.0032 | 0.0001 | |
| B | −0.0016 | 0.0035 | 0.0003 | 0.0044 | 0.0001 | |
| Diagonal | R | 0.0024 | 0.0018 | −0.0011 | 0.0091 | −0.0003 |
| G | 0.0015 | 0.0015 | −0.0011 | −0.0050 | −0.0012 | |
| B | −0.0005 | −0.0042 | −0.0004 | −0.0044 | 0.0004 |
| Image | House | Lena | Mandrill | Peppers | Oakland | San Diego | |
|---|---|---|---|---|---|---|---|
| R | P | 6.43105 | 7.29199 | 7.70667 | 7.33883 | 6.74584 | 7.72290 |
| C | 7.99723 | 7.99739 | 7.99930 | 7.99936 | 7.99981 | 7.99983 | |
| G | P | 6.53893 | 7.56580 | 7.47443 | 7.49625 | 6.06775 | 7.52891 |
| C | 7.99751 | 7.99738 | 7.99935 | 7.99930 | 7.99985 | 7.99982 | |
| B | P | 6.23204 | 7.05309 | 7.75222 | 7.05831 | 4.94606 | 6.83176 |
| C | 7.99741 | 7.99736 | 7.99930 | 7.99926 | 7.99984 | 7.99982 | |
| Image Size | Ours | Ref. [43] | Ref. [45] | Ref. [46] | Ref. [47] |
|---|---|---|---|---|---|
| 256 × 256 | 7.9974 | 7.9974 | – | – | – |
| 512 × 512 | 7.9993 | 7.9993 | 7.9993 | 7.9993 | 7.9993 |
| Image | House | Lena | Mandrill | Peppers | Oakland | San Diego |
|---|---|---|---|---|---|---|
| R | 7.902887399 | 7.902315714 | 7.902342208 | 7.902749564 | 7.902603517 | 7.902773850 |
| G | 7.902361871 | 7.902867975 | 7.901948419 | 7.902590272 | 7.902464163 | 7.902046266 |
| B | 7.902284269 | 7.902686604 | 7.902843902 | 7.902353755 | 7.902219158 | 7.902947226 |
| Result | Pass | Pass | Pass | Pass | Pass | Pass |
| Image | NPCR | UACI | ||||
|---|---|---|---|---|---|---|
| R | G | B | R | G | B | |
| House | 99.6105 | 99.6077 | 99.6076 | 33.4547 | 33.4681 | 33.4735 |
| Lena | 99.6082 | 99.6106 | 99.6098 | 33.4699 | 33.4574 | 33.4673 |
| Mandrill | 99.6081 | 99.6101 | 99.6076 | 33.4594 | 33.4537 | 33.4747 |
| Peppers | 99.6095 | 99.6092 | 99.6091 | 33.4878 | 33.4648 | 33.4501 |
| Oakland | 99.6078 | 99.6088 | 99.6086 | 33.4693 | 33.4614 | 33.4680 |
| San Diego | 99.6083 | 99.6092 | 99.6100 | 33.4636 | 33.4725 | 33.4715 |
| Test | Color Plane | Ours | Ref. [43] | Ref. [45] | Ref. [46] | Ref. [47] |
|---|---|---|---|---|---|---|
| NPCR | R | 99.6082 | 99.6155 | 99.61 | 99.6048 | 99.5943 |
| G | 99.6106 | 99.6017 | 99.61 | 99.5979 | 99.6113 | |
| B | 99.6098 | 99.6048 | 99.62 | 99.6166 | 99.6052 | |
| UACI | R | 33.4699 | 33.4371 | 33.47 | 33.4810 | 33.4866 |
| G | 33.4574 | 33.5437 | 33.46 | 33.4913 | 33.4360 | |
| B | 33.4673 | 33.4260 | 33.48 | 33.4971 | 33.4773 |
| Part | Original | Modified | NPCR | UACI | ||||
|---|---|---|---|---|---|---|---|---|
| R | G | B | R | G | B | |||
| 1 | 7f90e74697 | 7f90e74696 | 99.6169 | 99.6155 | 99.6041 | 33.4744 | 33.4592 | 33.4821 |
| 2 | 6ca763cca5 | 6ca763cca4 | 99.5964 | 99.6029 | 99.6144 | 33.4724 | 33.4533 | 33.4794 |
| 3 | 2557001fff | 2557001ffe | 99.6107 | 99.6288 | 99.5975 | 33.4677 | 33.4578 | 33.4751 |
| 4 | f394bd518b | f394bd518a | 99.6201 | 99.6074 | 99.6231 | 33.4697 | 33.4595 | 33.4892 |
| 5 | 05c007d747 | 05c007d746 | 99.6147 | 99.6277 | 99.6044 | 33.4522 | 33.4617 | 33.4663 |
| 6 | 172c065c5e | 172c065c5f | 99.6078 | 99.6071 | 99.6048 | 33.4501 | 33.4752 | 33.4904 |
| 7 | 2 | 3 | 99.6101 | 99.6217 | 99.6098 | 33.4836 | 33.4522 | 33.4651 |
| 8 | 3 | 2 | 99.6052 | 99.6101 | 99.5949 | 33.4589 | 33.4903 | 33.4547 |
| 9 | e | F | 99.6089 | 99.5979 | 99.6021 | 33.4539 | 33.6217 | 33.4587 |
| 10 | 0 | 1 | 99.6036 | 99.6117 | 99.6052 | 33.4578 | 33.4706 | 33.4509 |
| Part | Correct | Wrong | NPCR | UACI | ||||
|---|---|---|---|---|---|---|---|---|
| R | G | B | R | G | B | |||
| 1 | 7f90e74697 | 7f90e74696 | 99.5945 | 99.6037 | 99.6149 | 33.4678 | 33.5018 | 33.4714 |
| 2 | 6ca763cca5 | 6ca763cca4 | 99.6151 | 99.6127 | 99.6086 | 33.4818 | 33.4621 | 33.4613 |
| 3 | 2557001fff | 2557001ffe | 99.6056 | 99.6212 | 99.6052 | 33.4603 | 33.4519 | 33.4892 |
| 4 | f394bd518b | f394bd518a | 99.5972 | 99.6204 | 99.6101 | 33.4729 | 33.5009 | 33.4722 |
| 5 | 05c007d747 | 05c007d746 | 99.5953 | 99.5949 | 99.6170 | 33.5025 | 33.4921 | 33.4688 |
| 6 | 172c065c5e | 172c065c5f | 99.5968 | 99.5991 | 99.6216 | 33.4714 | 33.4657 | 33.4543 |
| 7 | 2 | 3 | 99.6251 | 99.6117 | 99.6204 | 33.4975 | 33.4869 | 33.4587 |
| 8 | 3 | 2 | 99.6166 | 99.6006 | 99.6201 | 33.4809 | 33.4504 | 33.5059 |
| 9 | e | F | 99.6258 | 99.6117 | 99.6208 | 33.5024 | 33.47.9 | 33.4579 |
| 10 | 0 | 1 | 99.6056 | 99.6132 | 99.5956 | 33.4560 | 33.4615 | 33.4627 |
| Image | Color Plane | χ2 Test | NPCR(%) | UACI(%) | Entropy | Correlation Coefficient | |||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Plaintext | Key | Plaintext | Key | SIE | LIE | Horizontal | Vertical | Diagonal | |||
| Black | R | 0.9998 | 99.6109 | 99.6151 | 33.4737 | 33.4762 | 7.999 | 7.9026 | 0.0002 | −0.0001 | −0.0014 |
| G | 0.9885 | 99.6083 | 99.5968 | 33.4543 | 33.4553 | 7.999 | 7.9019 | 0.0001 | −0.0018 | −0.0009 | |
| B | 0.9342 | 99.6112 | 99.6120 | 33.4679 | 33.4709 | 7.999 | 7.9030 | 0.0008 | 0.0017 | −0.0002 | |
| White | R | 0.9980 | 99.6113 | 99.6071 | 33.4507 | 33.4591 | 7.999 | 7.9022 | −0.0003 | 0.0023 | 0.0019 |
| G | 0.9961 | 99.6091 | 99.5946 | 33.4876 | 33.4871 | 7.999 | 7.9020 | −0.0024 | 0.0006 | 0.0022 | |
| B | 0.7211 | 99.6069 | 99.6094 | 33.4713 | 33.4583 | 7.999 | 7.9028 | −0.0009 | −0.0018 | −0.0009 | |
| Image | Algorithm | SIE | Correlation Coefficient | ||
|---|---|---|---|---|---|
| Horizontal | Vertical | Diagonal | |||
| Black | Ours | 7.9999 | 0.0004 | −0.0001 | −0.0008 |
| Ref. [16] | 7.9993 | −0.0050 | −0.0019 | −0.0036 | |
| Ref. [37] | 7.9972 | 0.1483 | 0.0059 | 0.0078 | |
| Ref. [44] | 7.9998 | −0.0031 | −0.0022 | −0.0009 | |
| White | Ours | 7.9999 | −0.0012 | 0.0004 | 0.0011 |
| Ref. [16] | 7.9994 | 0.0025 | 0.0016 | −0.0057 | |
| Ref. [37] | 7.9972 | 0.1474 | −0.0068 | 0.0038 | |
| Ref. [44] | 7.998 | −0.0016 | 0.0064 | 0.0038 | |
| Size | Image | Ours | Ref. [42] | Ref. [45] | Ref. [46] | Ref. [47] | Ref. [48] |
|---|---|---|---|---|---|---|---|
| 256 × 256 | House | 0.0105 | – | 0.077 | – | – | 0.4598 |
| Lena | 0.0113 | ||||||
| 512 × 512 | Mandrill | 0.0569 | 0.328 | 0.281 | – | 2.1274 | 1.7697 |
| Peppers | 0.0571 | ||||||
| 1024 × 1024 | Oakland | 0.2572 | – | 0.944 | – | – | – |
| San Diego | 0.2581 | ||||||
| Time complexity of encryption process | O(4W + 4H) | O(WH) | O(2WH) | O(3WH) | O(WH) | O(WH) | |
| Algorithm | Lena Cipher Image Polluted by | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Salt&Peppers with Intensity of | Gaussian with Variance of | Data Loss of | ||||||||
| 0.001 | 0.003 | 0.005 | 0.001 | 0.003 | 0.005 | 1/16 | 1/8 | 1/4 | 1/2 | |
| Ours | 20.46 | 16.01 | 14.09 | 15.29 | 13.29 | 12.73 | 21.54 | 18.21 | 15.37 | 12.73 |
| Ref. [16] | 17.97 | 14.55 | 11.99 | – | – | – | – | – | – | – |
| Ref. [28] | 14.76 | 13.42 | 11.98 | 16.89 | – | 13.68 | – | 20.01 | 14.19 | 11.19 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ge, B.; Shen, Z.; Wang, X. Symmetric Color Image Encryption Using a Novel Cross–Plane Joint Scrambling–Diffusion Method. Symmetry 2023, 15, 1499. https://doi.org/10.3390/sym15081499
Ge B, Shen Z, Wang X. Symmetric Color Image Encryption Using a Novel Cross–Plane Joint Scrambling–Diffusion Method. Symmetry. 2023; 15(8):1499. https://doi.org/10.3390/sym15081499
Chicago/Turabian StyleGe, Bin, Zhihua Shen, and Xiao Wang. 2023. "Symmetric Color Image Encryption Using a Novel Cross–Plane Joint Scrambling–Diffusion Method" Symmetry 15, no. 8: 1499. https://doi.org/10.3390/sym15081499
APA StyleGe, B., Shen, Z., & Wang, X. (2023). Symmetric Color Image Encryption Using a Novel Cross–Plane Joint Scrambling–Diffusion Method. Symmetry, 15(8), 1499. https://doi.org/10.3390/sym15081499








