Fast and Efficient Data Forwarding Scheme for Tracking Mobile Targets in Sensor Networks
Abstract
:1. Introduction
2. Related Work
2.1. Target Detection in Stationary Sink Network
2.2. Tracking Mobile Target
2.3. Target Detection in Mobile Sink Network
2.4. Track Mobile Target with Mobile Sink Network
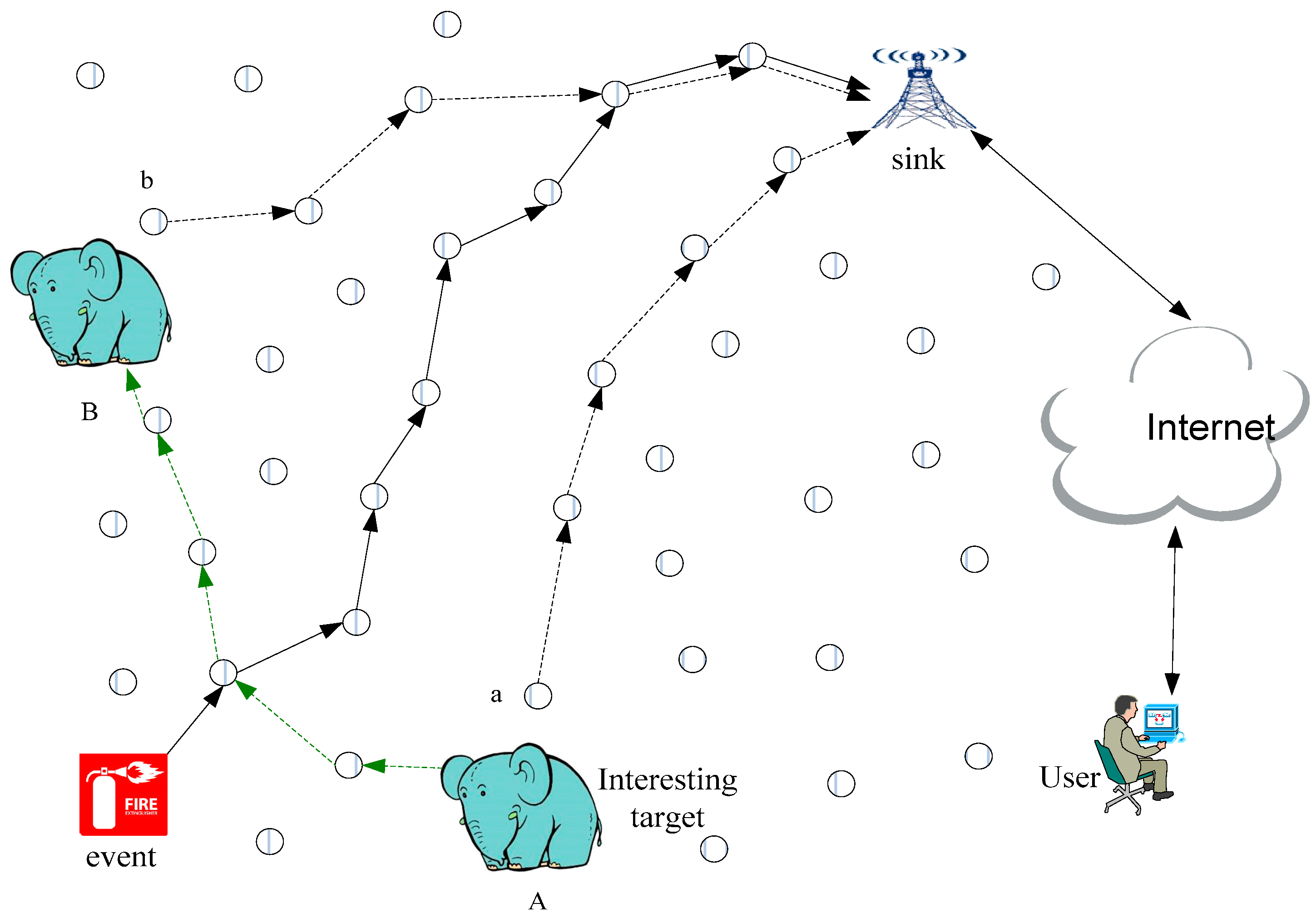
3. System Model and Problem Statement
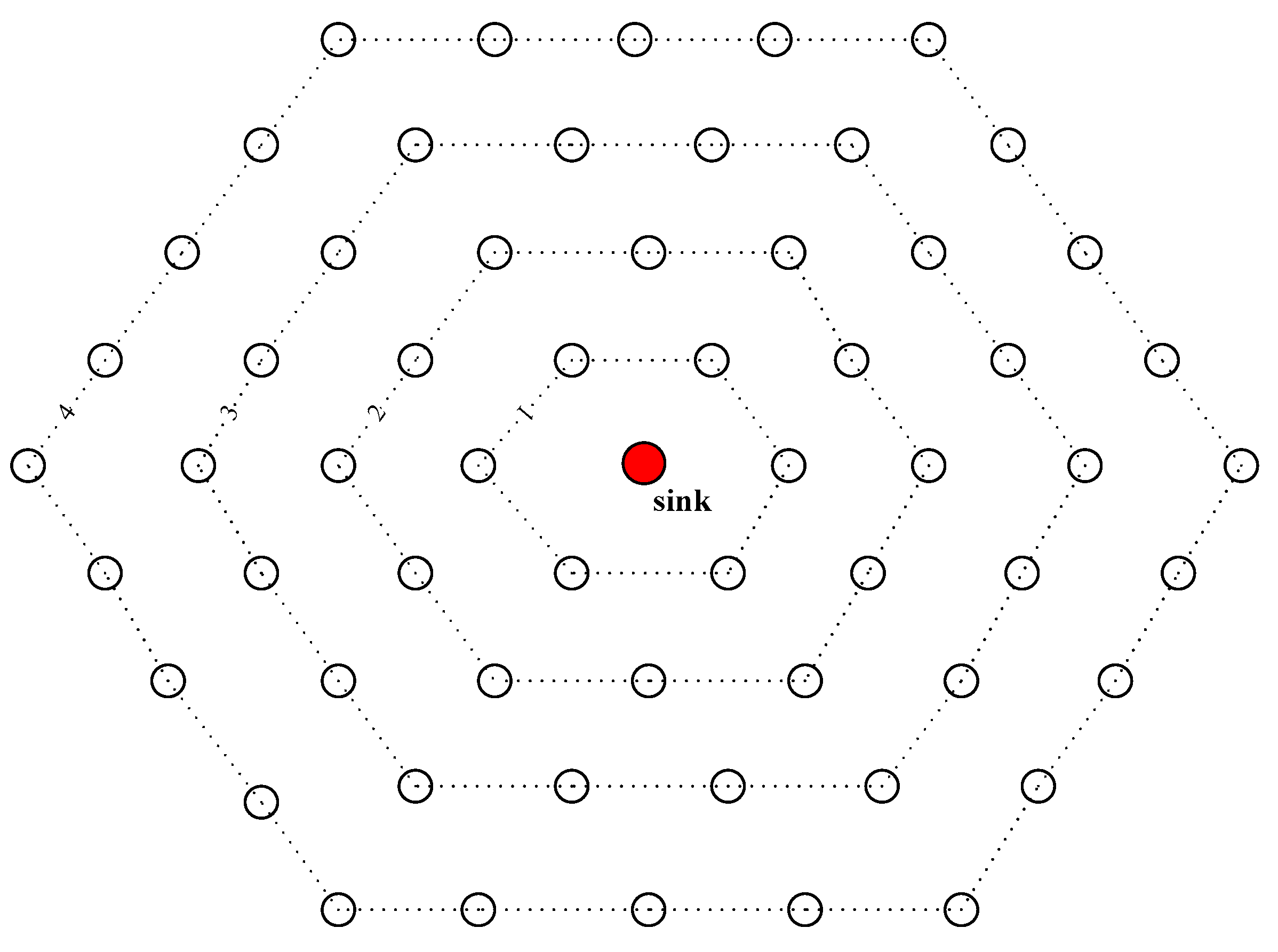
3.1. System Model
3.2. Network Parameters
3.3. Problem Statement
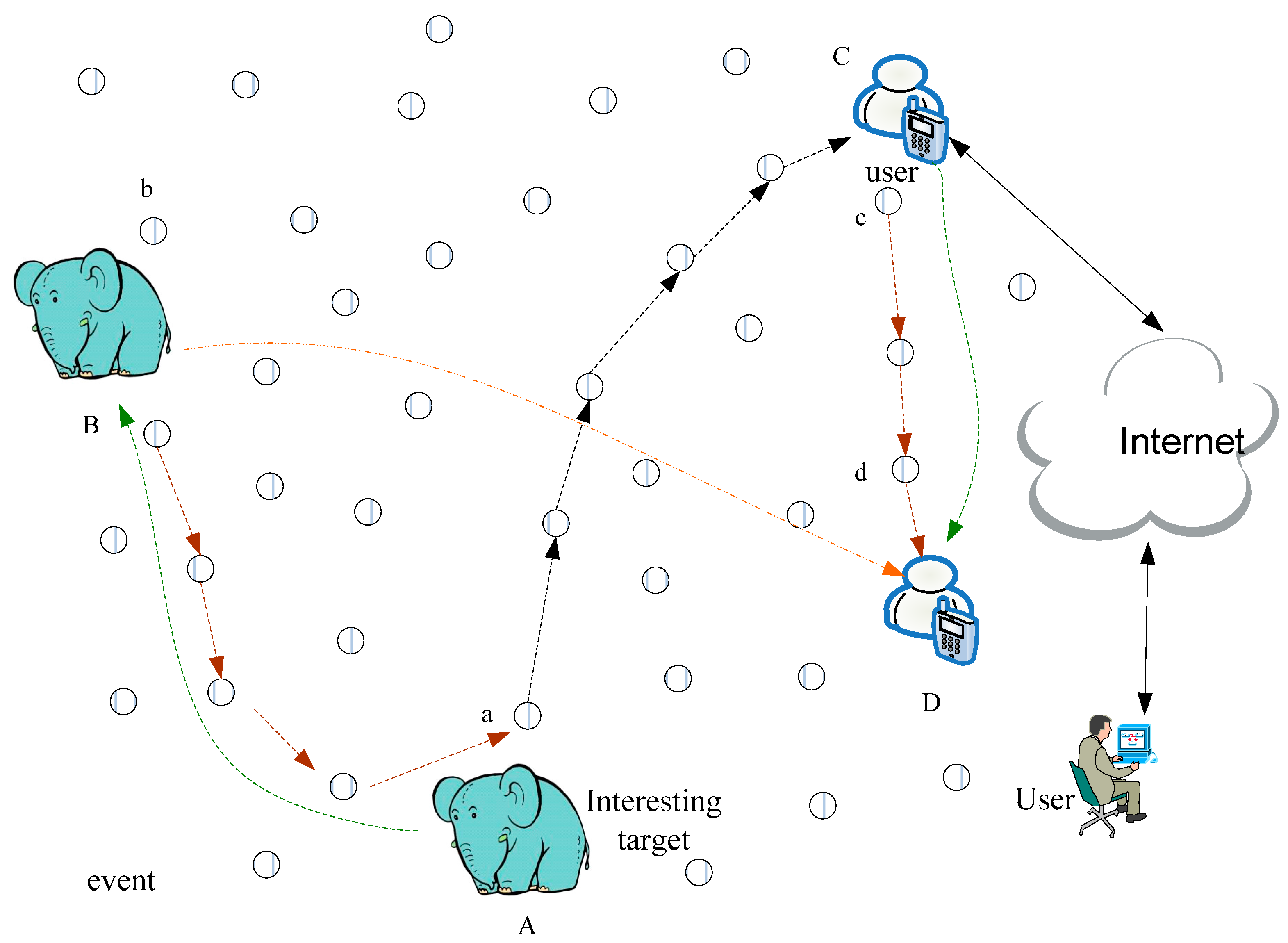
4. The Design of FEDF Scheme
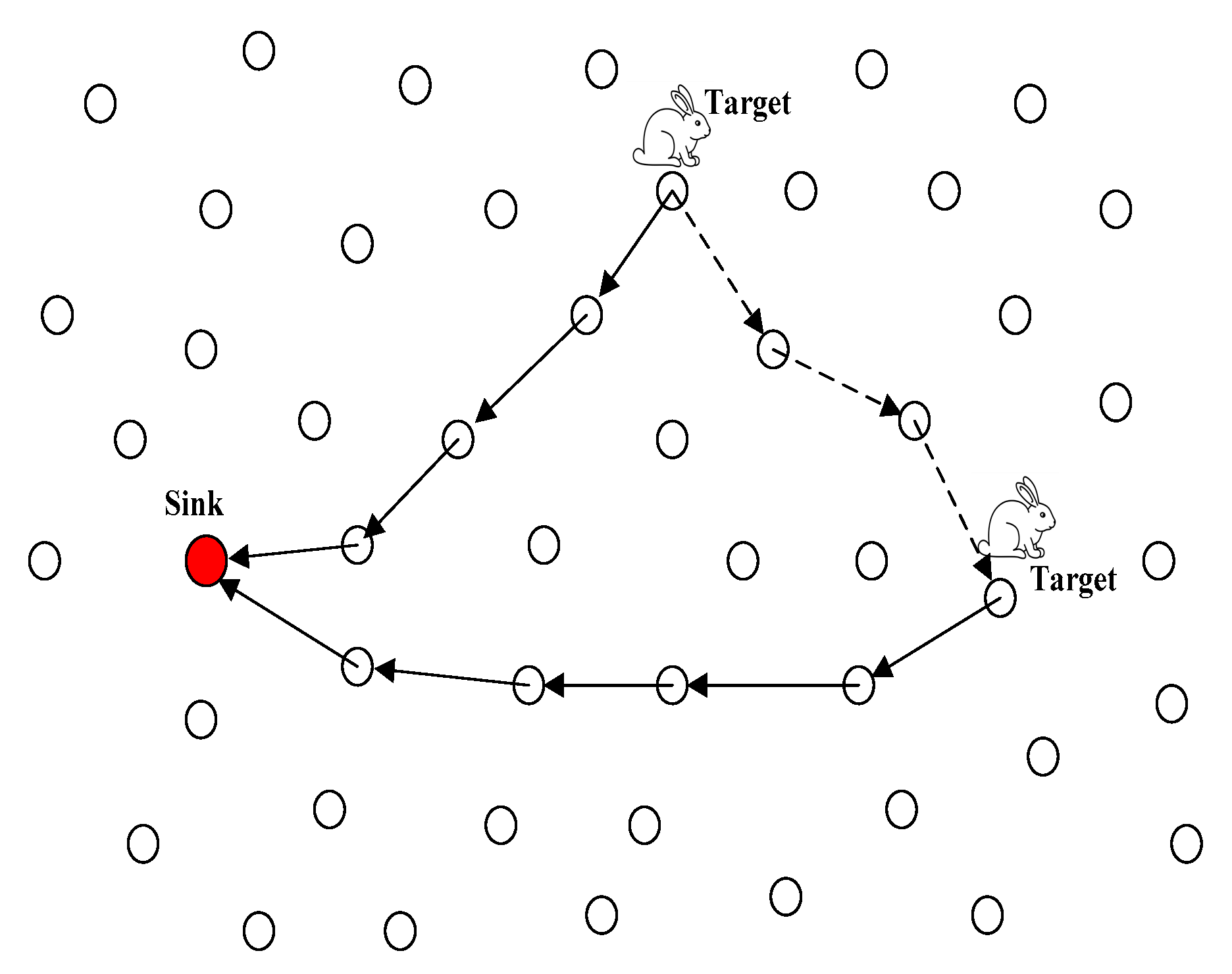
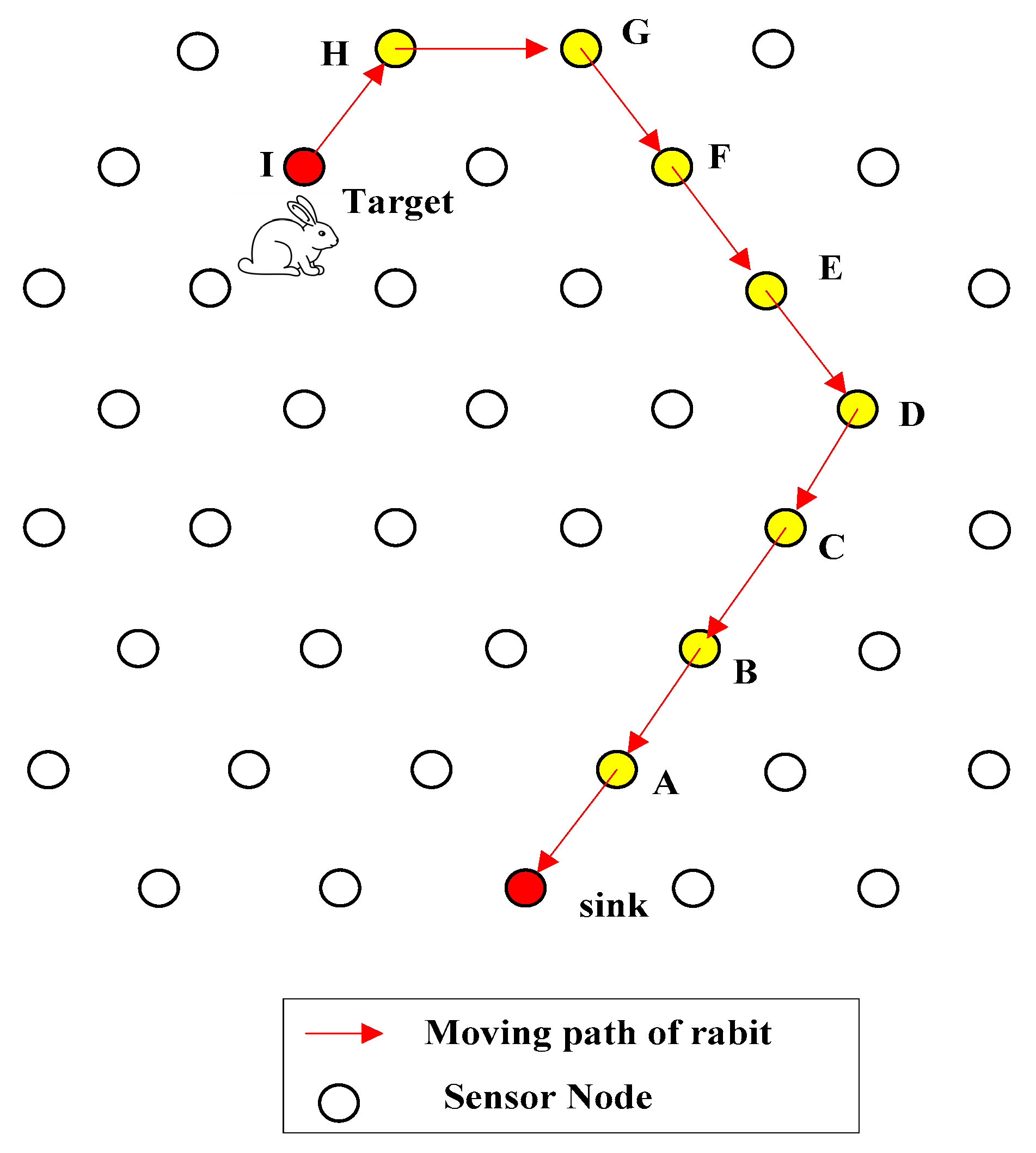
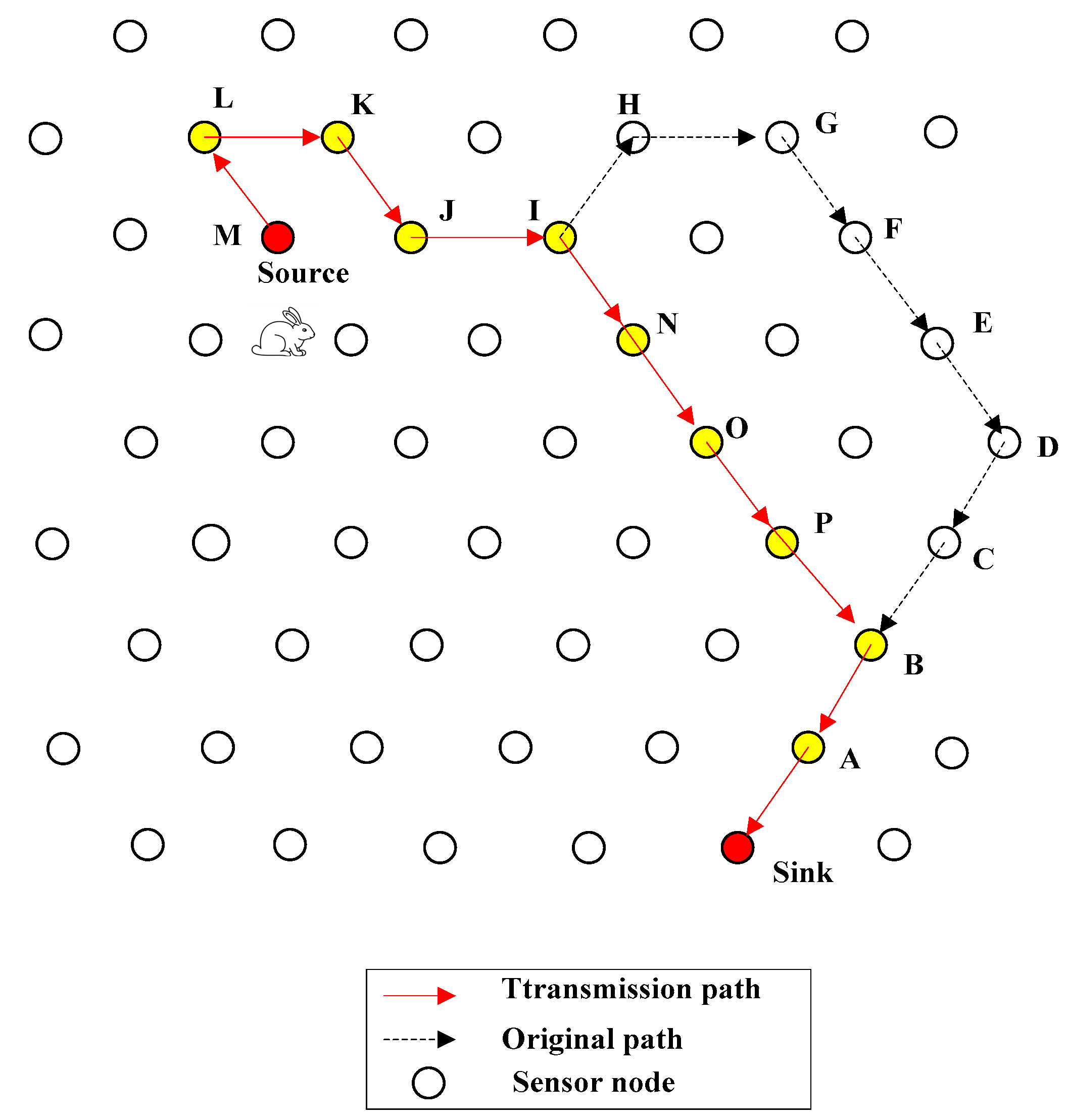
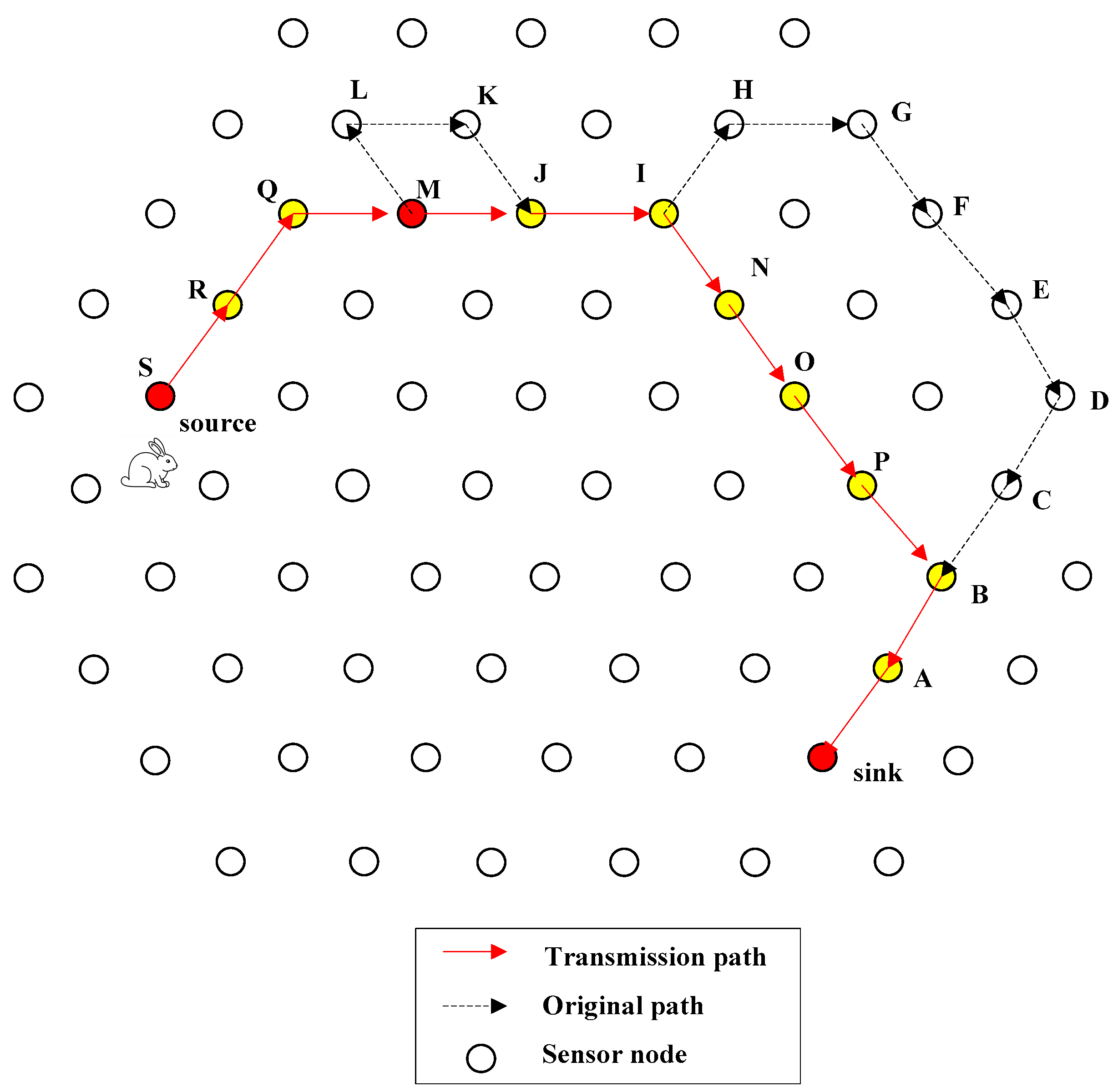
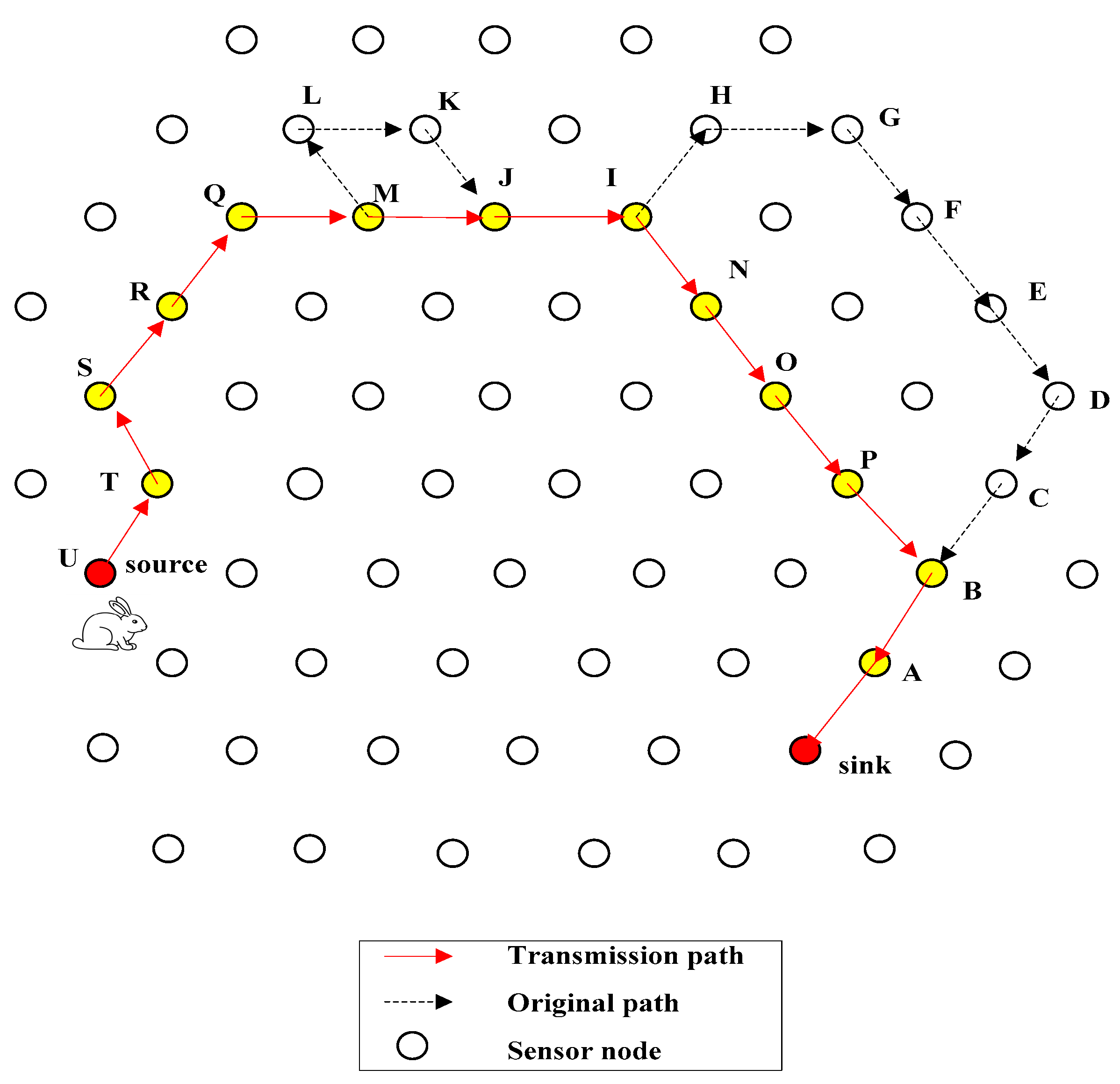
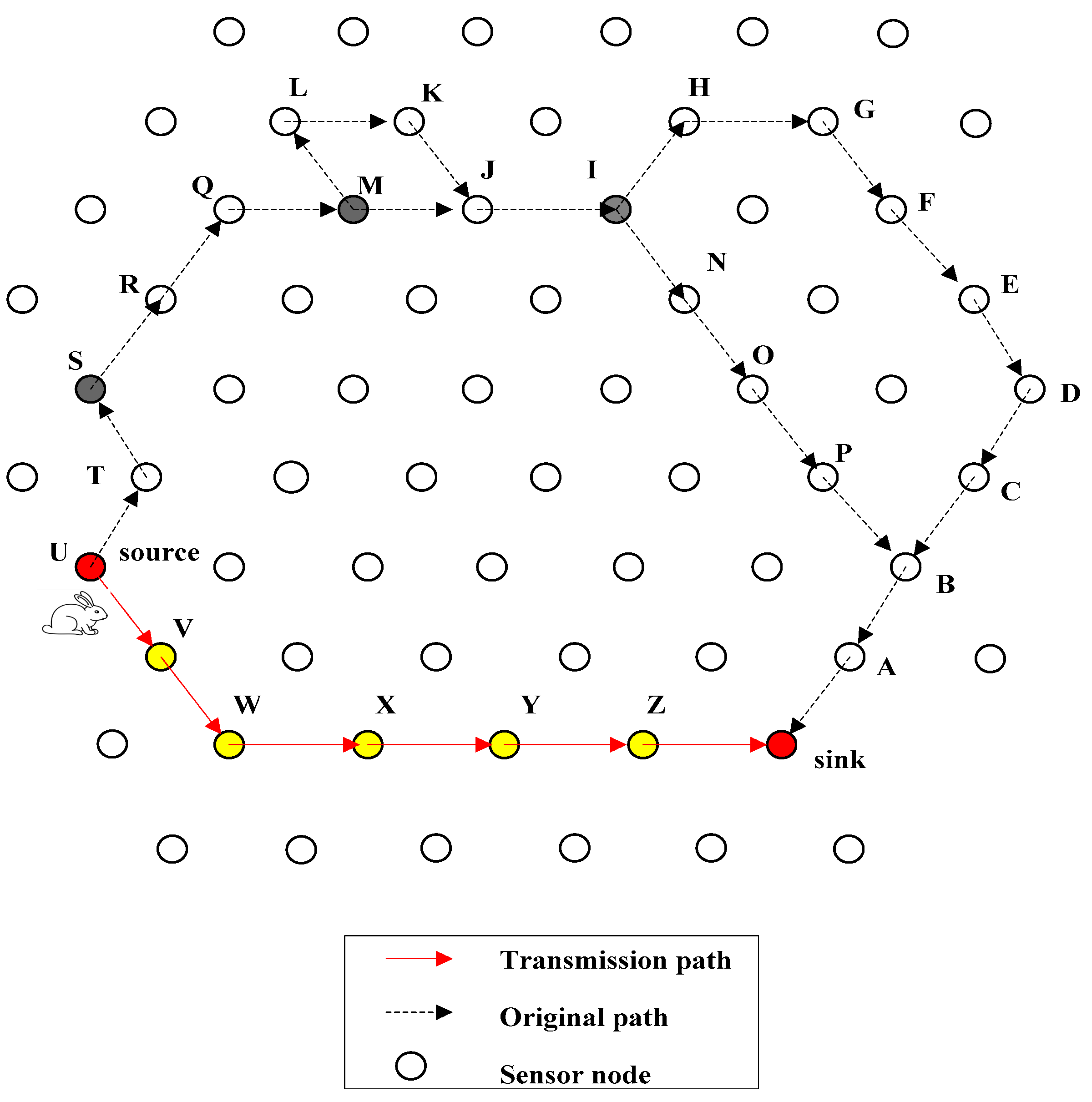
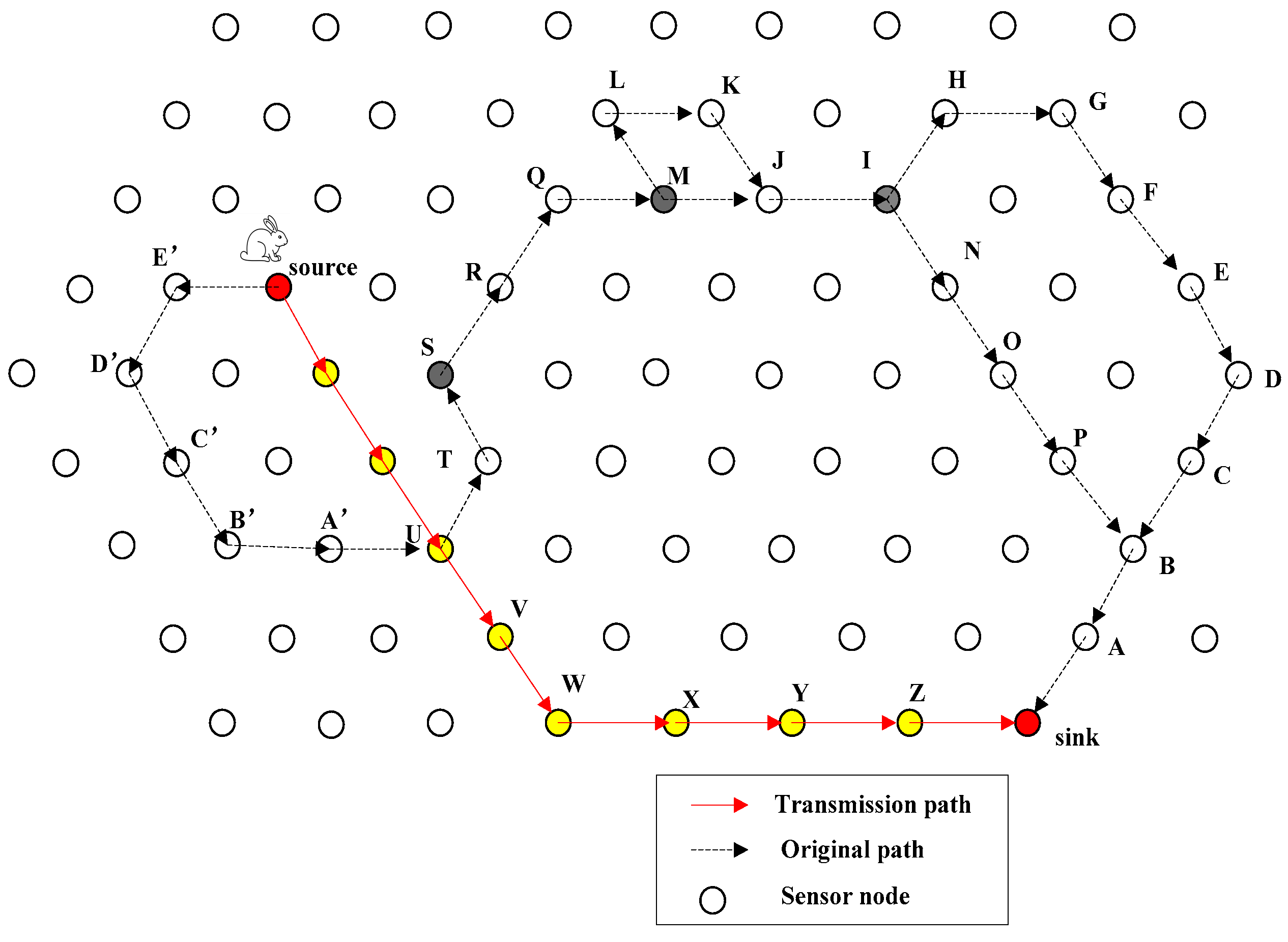
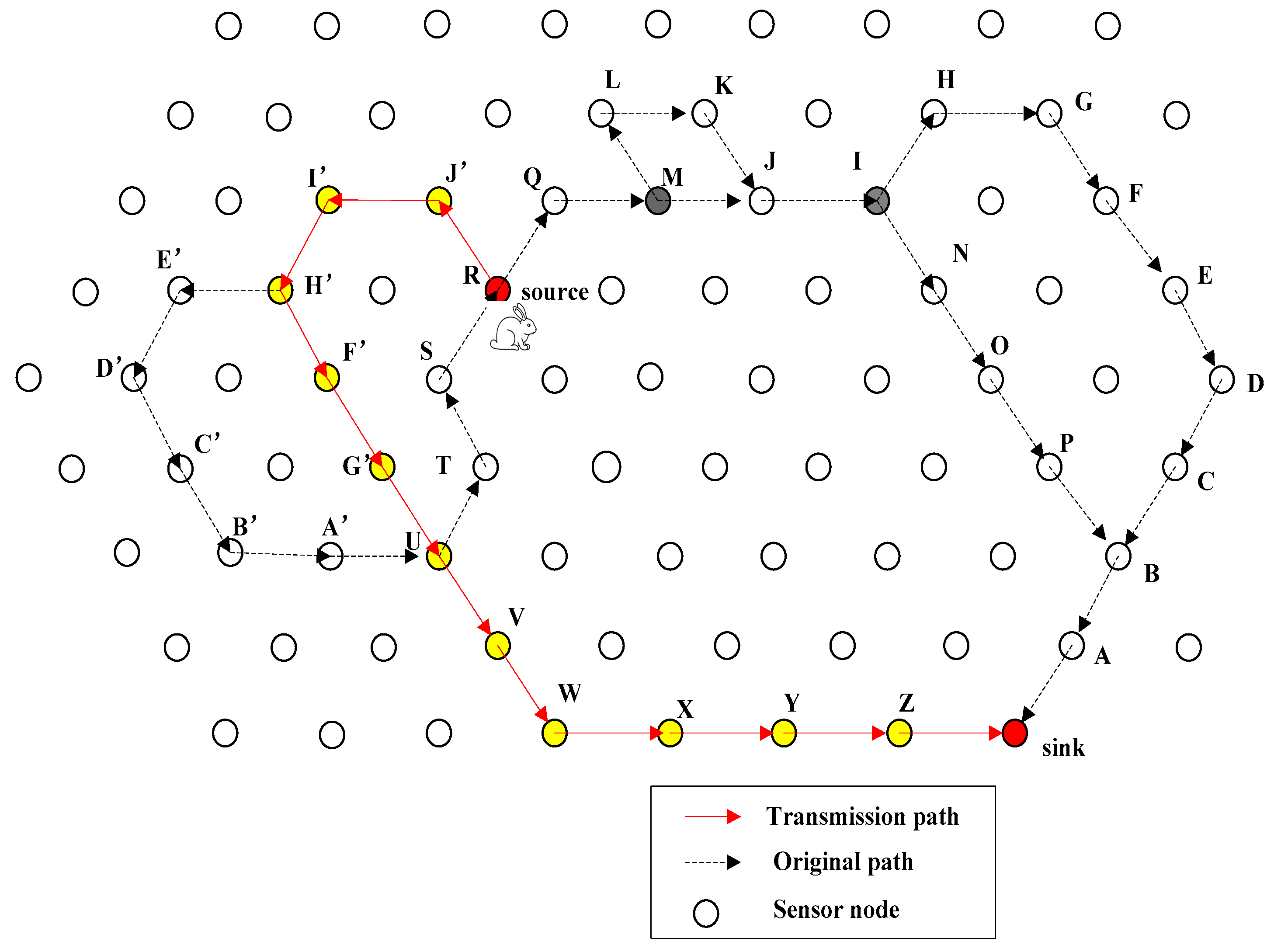
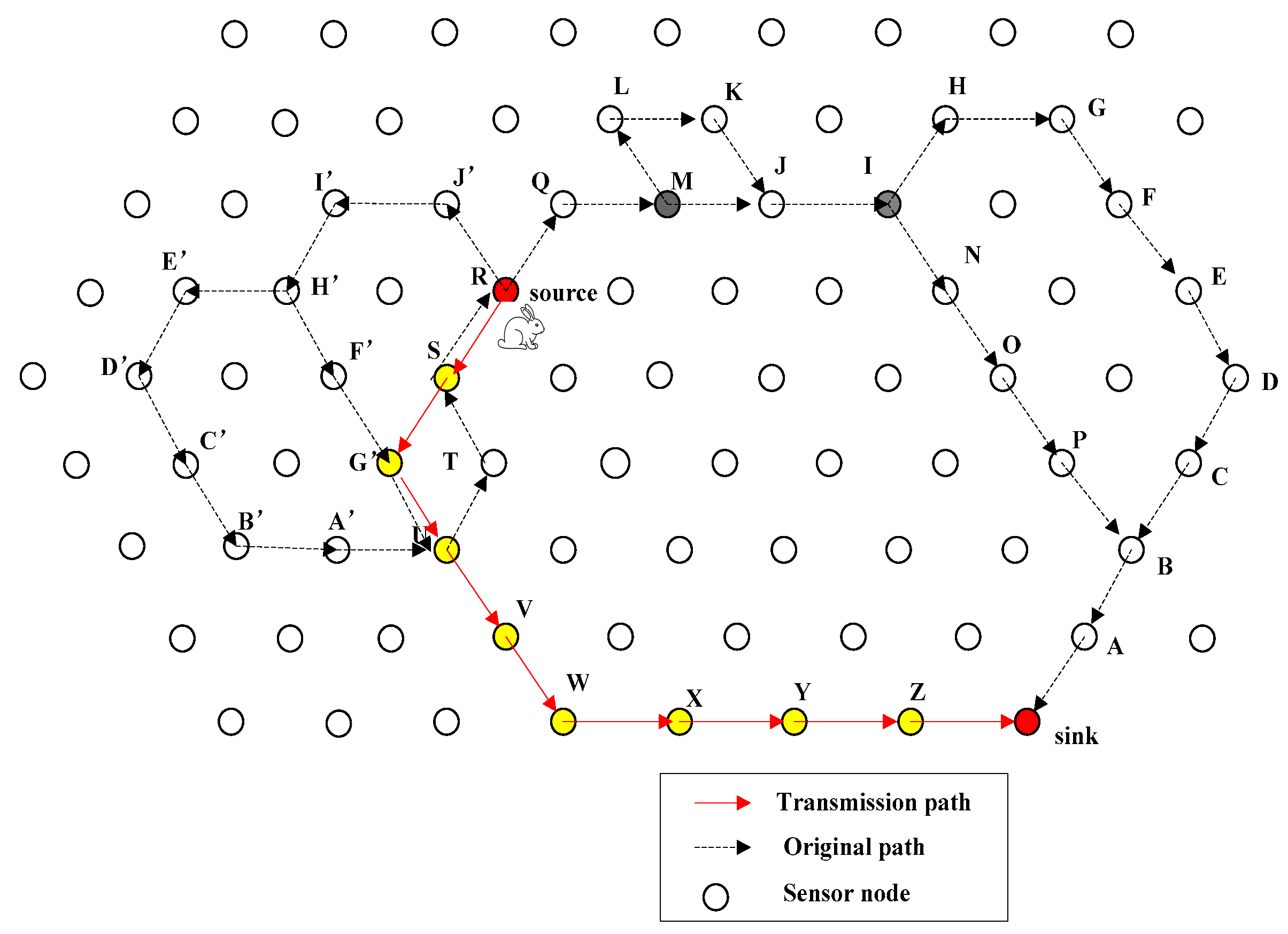
4.1. Introduction of QRR Path
4.2. General Design of FEDF Scheme
| Algorithm 1 Initialize the network |
| 1: Initialize = 0 2: Initialize every node in the network: = ∞ 3: sink broadcast its , and assume node’s received from others is 4: For every node in the network Do 5: If > + 1 Then 6: = + 1 7: End if 8: Else 9: keep its original value 10: End else 11: End for |
| Algorithm 2 create a quickly reacted routing path |
| 1: While > 0 Do 2: = false 3: For each node in the network Do 4: If ( < ) Then 5: = true 6: = 7: = 8: End if 9: End For 10: End while |
| Algorithm 3 updating path recording table(RRT) |
| 1:begin 2: For(LN.next) LN.next = CN LN = CN 5: ++ 6: CN.DR = 1 7: add CN to visited_list 8: End for 9: End |
| Algorithm 4 Identifying the possible EDPs |
| 1: Find_pEDP (Node source, Threshold η) 2: Begin 3: //η: threshold for shortcuts 4: //pre_list: the set of pEDP 5: For each node p in source.Visited _list Do 6: If (η) Then 7: Calculate of p 8: add p to pre_list 9: End if 10: End for 11: End |
| Algorithm 5 Determining the EDP |
| 1: begin 2: For each node in pre_list 3: Find min{ + } 4: return p 5: End for 6: End |
| Algorithm 6 Creating a straight line path |
| 1: Find_Nexthop (NH) 2: begin 3: //NH: next hop 4: If (NH is not sink) Then 5: nextHop(x, y) = (x-x.offset, y-y.offset) 6: If (search_neighbor (nextHop) != NULL) Then 7: return nextHop 8: End if 9: End if 10: End |
5. Performance Analysis of FEDF Scheme
5.1. Transmission Delay
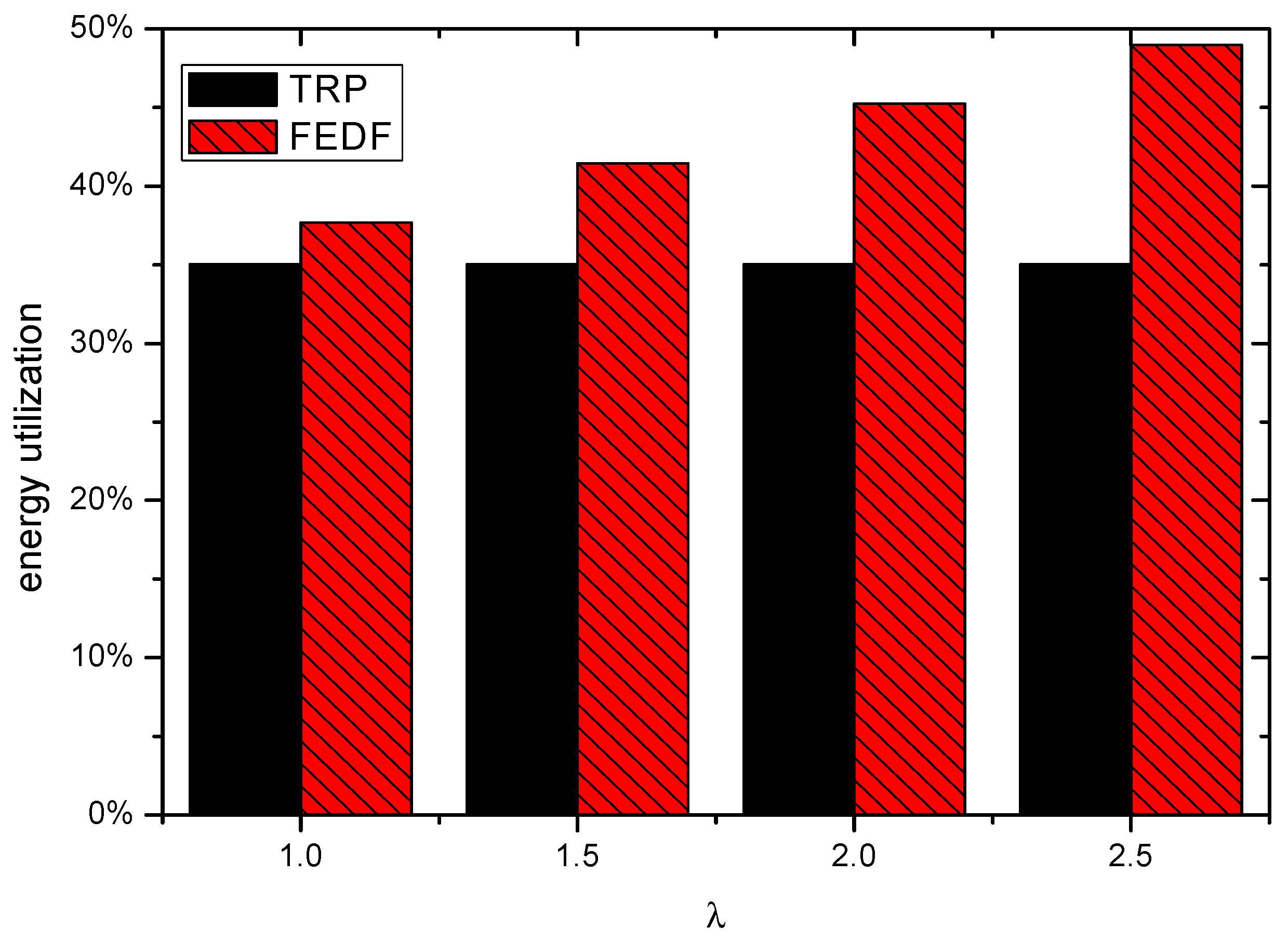
5.2. Energy Utilization
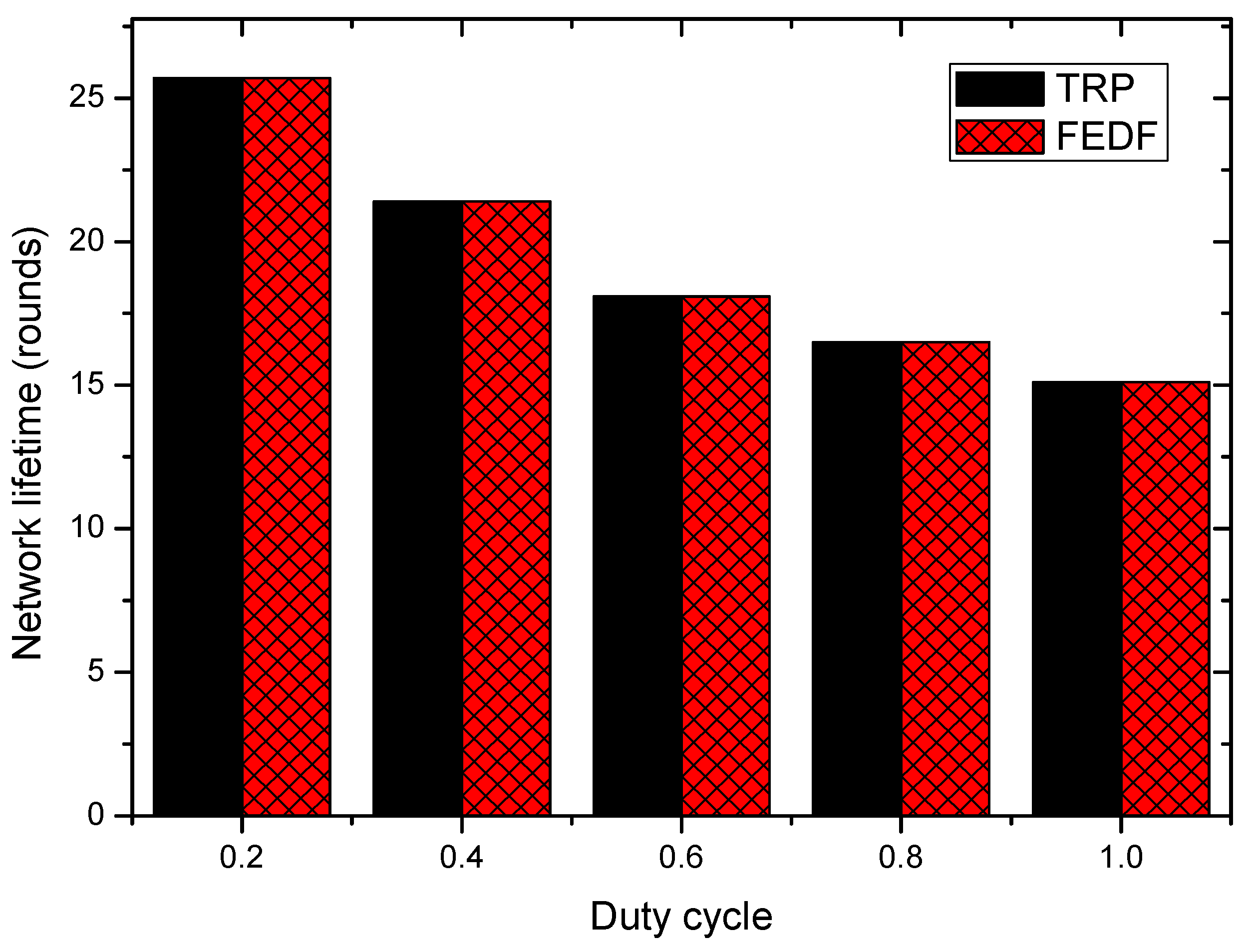
5.3. Network Lifetime
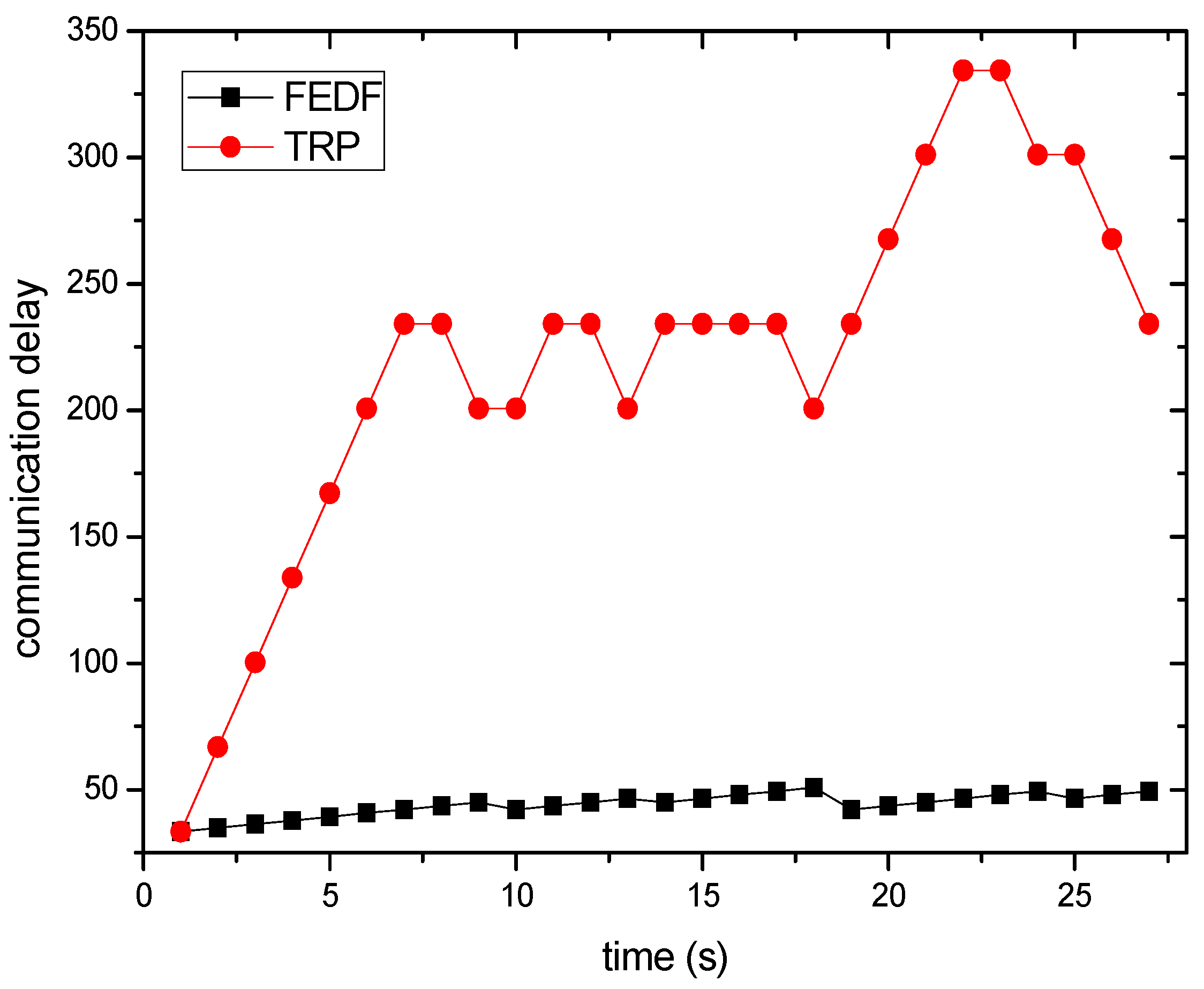
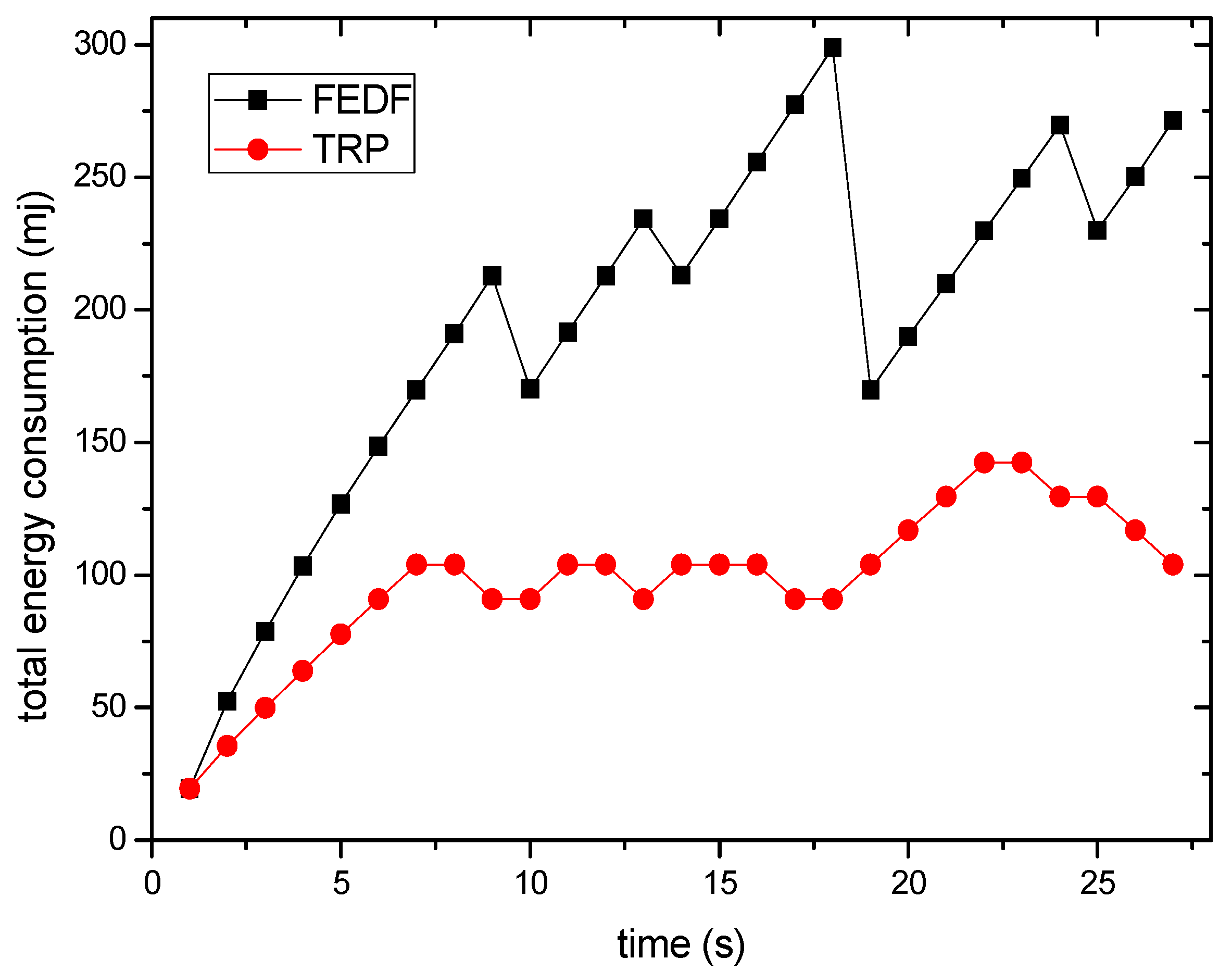
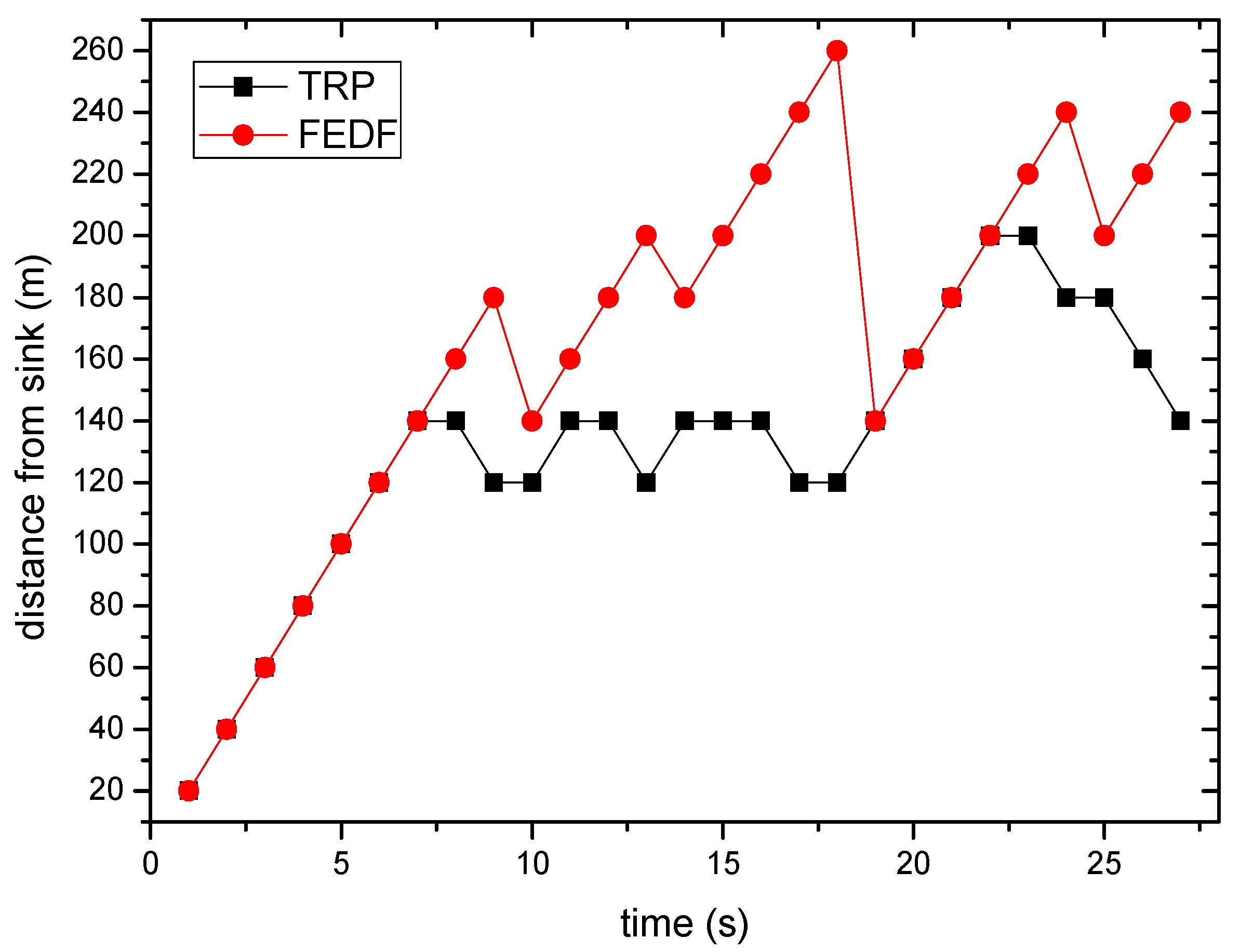
6. Experimental Results
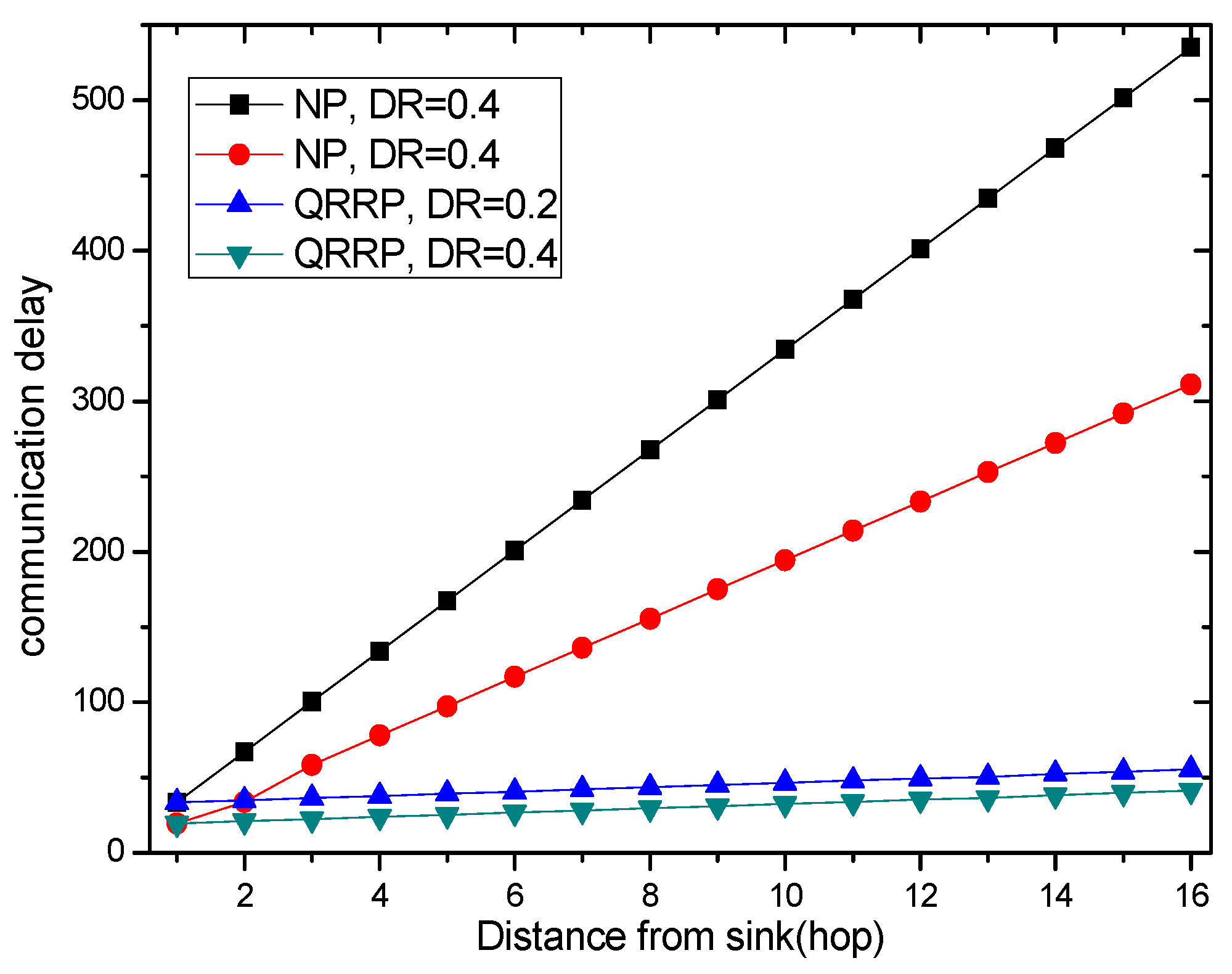
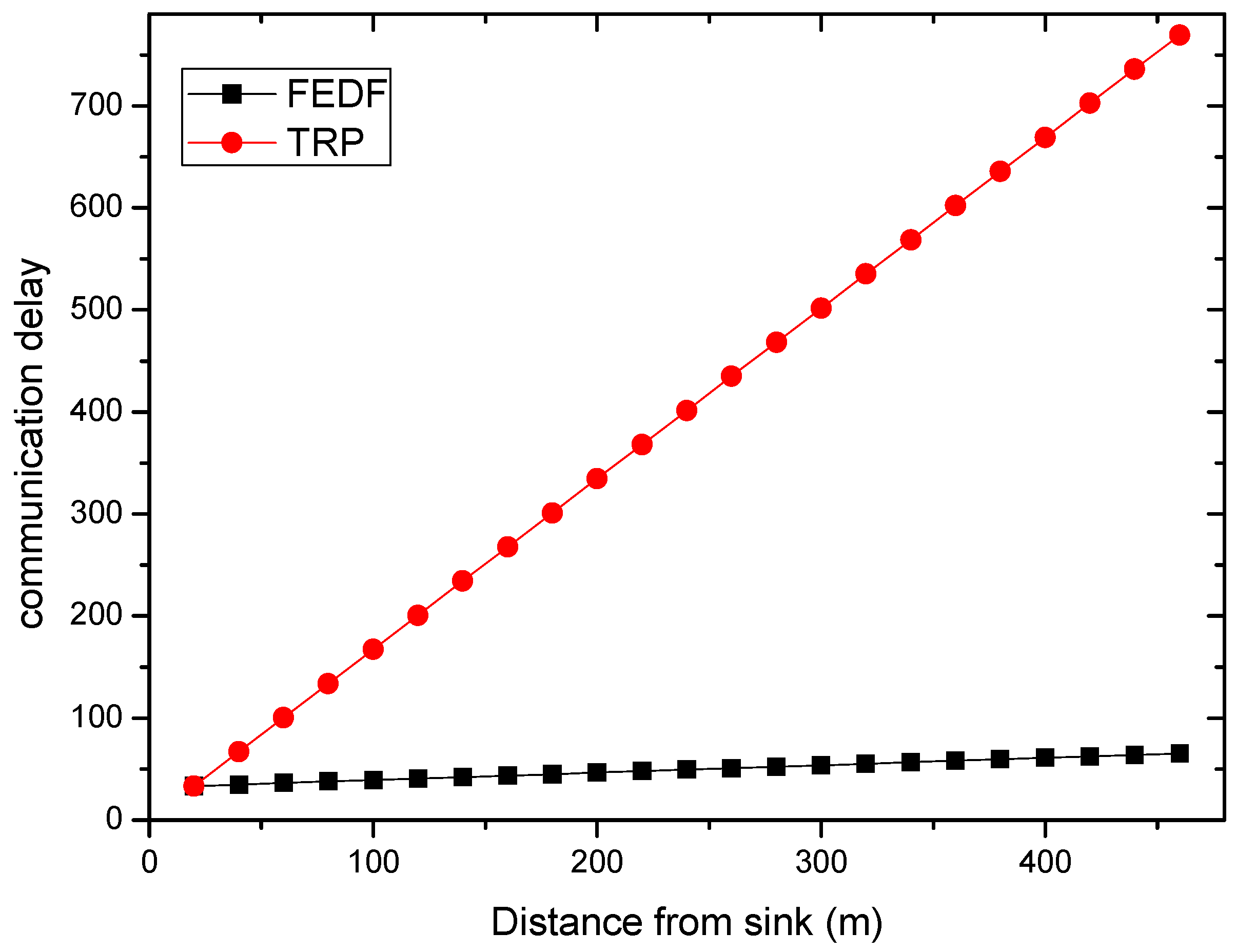
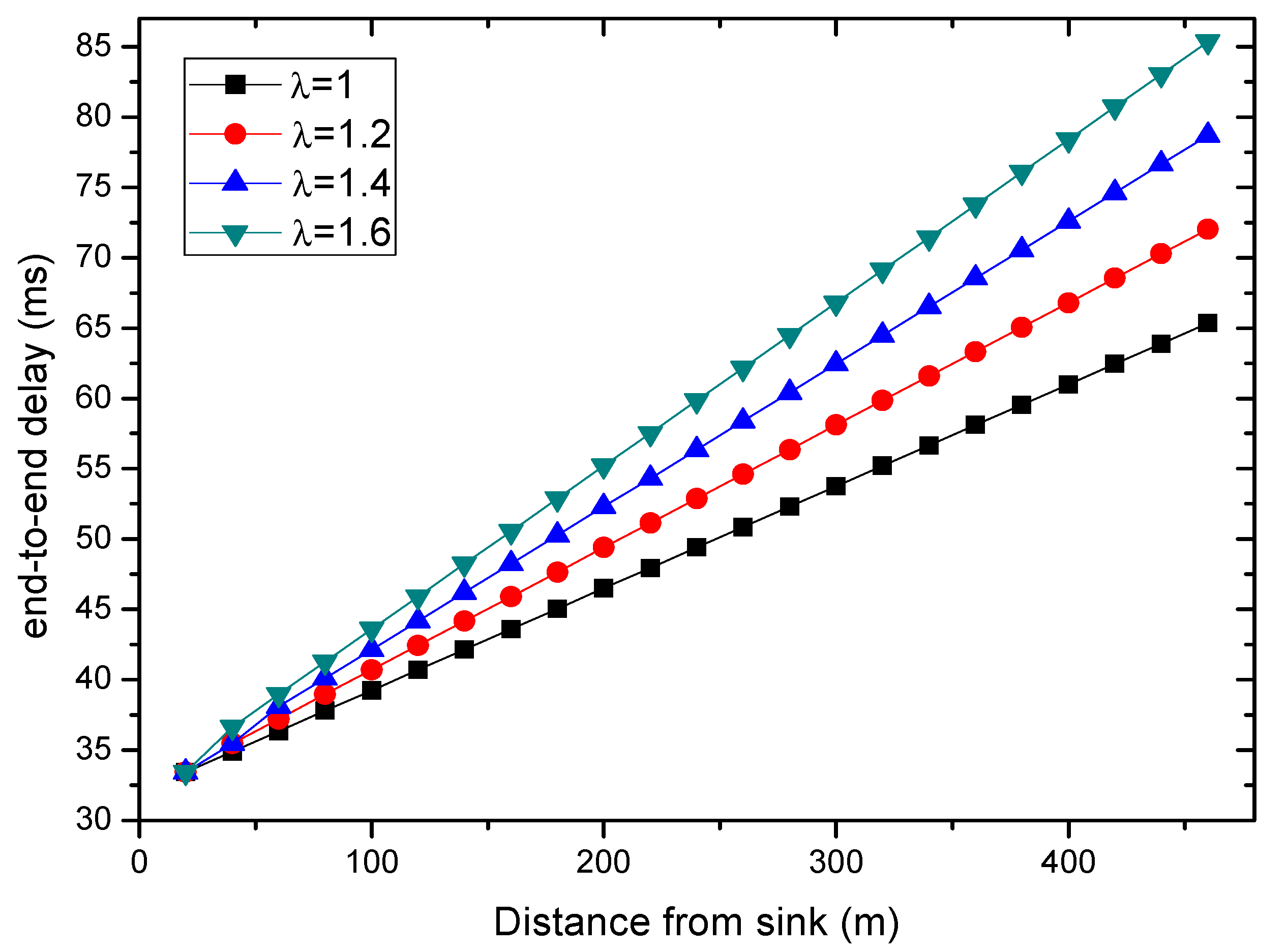
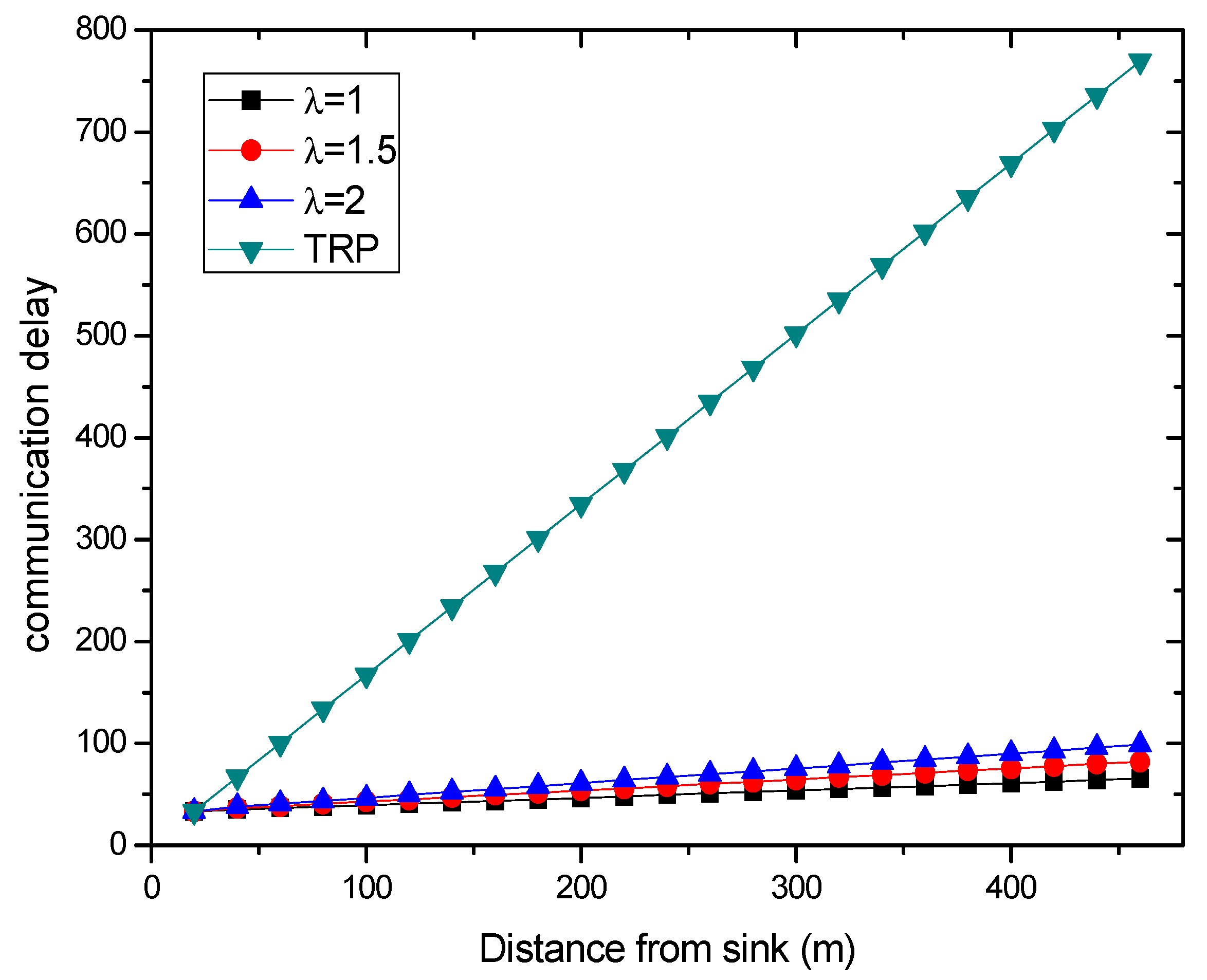
6.1. Transmission Delay
6.2. Energy Consumption
6.3. Path Length
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Kim, M.S.; Lee, J.K.; Park, J.H.; Kang, J.H. Security Challenges in Recent Internet Threats and Enhanced Security Service Model for Future IT Environments. J. Internet Technol. 2016, 17, 947–955. [Google Scholar]
- Kim, H.W.; Park, J.H.; Jeong, Y.S. Efficient Resource Management Scheme for Storage Processing in Cloud Infrastructure with Internet of Things. Wirel. Pers. Commun. 2016, 91, 1635–1651. [Google Scholar] [CrossRef]
- Liu, A.; Zhang, Q.; Li, Z.; Choi, Y.J.; Li, J.; Komuro, N. A green and reliable communication modeling for industrial internet of things. Comput. Electr. Eng. 2017, 58, 364–381. [Google Scholar] [CrossRef]
- Park, J.H.; Chao, H.C. Advanced IT-Based Future Sustainable Computing. Sustainability 2017, 9, 757. [Google Scholar] [CrossRef]
- Liu, A.; Chen, Z.; Xiong, N. An adaptive virtual relaying set scheme for loss-and-delay sensitive WSNs. Inform. Sci. 2018, 424, 118–136. [Google Scholar] [CrossRef]
- Liu, X.; Liu, Y.; Song, H.; Liu, A. Big data orchestration as a service networking. IEEE Commun. Mag. 2017, 55, 94–101. [Google Scholar]
- Wang, J.; Liu, A.; Zhang, S. Key parameters decision for cloud computing: Insights from a multiple game model. Concurr. Comput. Pract. Exp. 2017. [Google Scholar] [CrossRef]
- Su, Z.; Xu, Q.; Fei, M.; Don, M. Game Theoretic Resource Allocation in Media Cloud with Mobile Social Users. IEEE Trans. Multimed. 2016, 18, 1650–1660. [Google Scholar] [CrossRef]
- Li, H.; Liu, D.; Dai, Y.; Luan, T.H. Engineering searchable encryption of mobile cloud networks: When QoE meets QoP. IEEE Wirel. Commun. 2015, 22, 74–80. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, A.; Guo, S.; Li, Z.; Choi, Y.J.; Sekiya, H. Context-aware collect data with energy efficient in Cyber-physical cloud systems. Future Gener. Comput. Syst. 2017. [Google Scholar] [CrossRef]
- Zhang, Q.; Liu, A. An unequal redundancy level based mechanism for reliable data collection in wireless sensor networks. EURASIP J. Wirel. Commun. Netw. 2016, 258, 1–22. [Google Scholar] [CrossRef]
- Liu, X.; Dong, M.; Ota, K.; Yang, L.T.; Liu, A. Trace malicious source to guarantee cyber security for mass monitor critical infrastructure. J. Comput. Syst. Sci. 2016. [Google Scholar] [CrossRef]
- Liu, X.; Zhao, S.; Liu, A.; Xiong, N.; Vasilakos, A.V. Knowledge-aware Proactive Nodes Selection Approach for Energy management in Internet of Things. Future Gener. Comput. Syst. 2017. [Google Scholar] [CrossRef]
- Liu, A.; Liu, X.; Wei, T.; Yang, L.T.; Rho, S.C.; Paul, A. Distributed Multi-representative Re-Fusion approach for Heterogeneous Sensing Data Collection. ACM Trans. Embed. Comput. Syst. 2017, 16, 73. [Google Scholar] [CrossRef]
- He, S.; Shin, D.; Zhang, J.; Chen, J.; Sun, Y. Full-view area coverage in camera sensor networks: Dimension reduction and near-optimal solutions. IEEE Trans. Veh. Technol. 2016, 65, 7448–7461. [Google Scholar] [CrossRef]
- Chen, X.; Ma, M.; Liu, A. Dynamic power management and adaptive packet size selection for IoT in e-Healthcare. Comput. Electr. Eng. 2017. [Google Scholar] [CrossRef]
- Chen, X.; Xu, Y.; Liu, A. Cross layer design for optimal delay, energy efficiency and lifetime in body sensor networks. Sensors 2017, 17, 900. [Google Scholar] [CrossRef] [PubMed]
- Xu, Y.; Chen, X.; Liu, A.; Hu, C. A latency and coverage optimized data collection scheme for smart cities based on vehicular ad-hoc networks. Sensors 2017, 17, 888. [Google Scholar] [CrossRef] [PubMed]
- Xu, Y.; Liu, A.; Huang, C. Delay-aware program codes dissemination scheme in Internet of everything. Mob. Inform. Syst. 2016. [Google Scholar] [CrossRef]
- Li, T.; Liu, Y.; Gao, L.; Liu, A. A Cooperative-based Model for Smart-Sensing Tasks in Fog Computing. IEEE Access 2017. [Google Scholar] [CrossRef]
- Chen, Z.; Liu, A.; Li, Z.; Choi, Y.J.; Sekiya, H.; Li, J. Energy-efficient broadcasting scheme for smart industrial wireless sensor networks. Mob. Inform. Syst. 2017, 2017, 7538190. [Google Scholar] [CrossRef]
- He, S.; Chen, J.; Li, X.; Shen, X.S.; Sun, Y. Mobility and intruder prior information improving the barrier coverage of sparse sensor networks. IEEE Trans. Mob. Comput. 2014, 13, 1268–1282. [Google Scholar]
- Zhao, S.; Liu, A. High performance target tracking scheme with low prediction precision requirement in WSNs. Int. J. Ad Hoc Ubiquitous Comput. 2017, in press. [Google Scholar]
- Chi, Y.P.; Chang, H.P. A tracking-assisted routing scheme for wireless sensor networks. Wirel. Pers. Commun. 2013, 70, 411–433. [Google Scholar] [CrossRef]
- Hu, Y.; Dong, M.; Ota, K.; Liu, A.; Guo, M. Mobile Target Detection in Wireless Sensor Networks with Adjustable Sensing Frequency. IEEE Syst. J. 2016, 10, 1160–1171. [Google Scholar] [CrossRef]
- Liu, A.; Liu, X.; Tang, Z.; Yang, L.T.; Shao, Z. preserving smart sink location privacy with delay guaranteed routing scheme for WSNs. ACM Trans. Embed. Comput. Syst. 2017, 16, 68. [Google Scholar] [CrossRef]
- Chen, Z.; Liu, A.; Li, Z.; Choi, Y.J.; Li, J. Distributed Duty cycle control for delay improvement in wireless sensor networks. Peer-to-Peer Netw. Appl. 2017, 10, 559–578. [Google Scholar] [CrossRef]
- Liu, X.; Li, G.; Zhang, S.; Liu, A. Big program code dissemination scheme for emergency software-define wireless sensor networks. Peer-to-Peer Netw. Appl. 2017. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, A.; Li, Y.; Li, Z.; Choi, Y.J.; Sekiya, H.; Li, J. APMD: A fast data transmission protocol with reliability guarantee for pervasive sensing data communication. Pervasive Mob. Comput. 2017. [Google Scholar] [CrossRef]
- Huang, C.; Ma, M.; Liu, Y.; Liu, A. Preserving source location privacy for energy harvesting WSNs. Sensors 2017, 17, 724. [Google Scholar] [CrossRef] [PubMed]
- Gui, J.; Zhou, K. Flexible Adjustments between Energy and Capacity for Topology Control in Heterogeneous Wireless Multi-Hop Networks. J. Netw. Syst. Manag. 2016, 24, 789–812. [Google Scholar] [CrossRef]
- Liu, Q.; Liu, A. On the hybrid using of unicast-broadcast in wireless sensor networks. Comput. Electr. Eng. 2017. [Google Scholar] [CrossRef]
- Liu, X.; Liu, A.; Li, Z.; Tian, S.; Choi, Y.J.; Sekiya, H.; Li, J. Distributed cooperative communication nodes control and optimization reliability for resource-constrained WSNs. Neurocomputing 2017. [Google Scholar] [CrossRef]
- Chen, Z.; Ma, M.; Liu, X.; Liu, A.; Zhao, M. Reliability Improved Cooperative Communications over Wireless Sensor Networks. Symmetry 2017, 9, 209. [Google Scholar] [CrossRef]
- Wang, J.; Liu, A.; Yan, T.; Zeng, Z. A resource allocation model based on double-sided combinational auctions for transparent computing. Peer-to-Peer Netw. Appl. 2017. [Google Scholar] [CrossRef]
- Su, Z.; Xu, Q.; Zhu, H.; Wang, Y. A novel design for content delivery over software defined mobile social networks. IEEE Netw. 2015, 29, 62–67. [Google Scholar] [CrossRef]
- Li, T.; Liu, A.; Huang, C. A similarity scenario-based recommendation model with small disturbances for unknown items in social networks. IEEE Access 2016, 4, 9251–9272. [Google Scholar] [CrossRef]
- Zhou, S.; Xu, Q. Content distribution over content centric mobile social networks in 5G. IEEE Commun. Mag. 2015, 53, 66–72. [Google Scholar] [CrossRef]
- Liu, X.; Liu, A.; Huang, C. Adaptive Information Dissemination Control to Provide Diffdelay for Internet of Things. Sensors 2017, 17, 38. [Google Scholar] [CrossRef] [PubMed]
- Asudeh, A.; Zaruba, G.V.; Das, S.K. A general model for MAC protocol selection in wireless sensor networks. Ad Hoc Netw. 2016, 36, 189–202. [Google Scholar] [CrossRef]
- Feng, X.; Wang, Z.; Liu, X.; Liu, J. ADCNC-MAC: Asynchronous duty cycle with network-coding MAC protocol for underwater acoustic sensor networks. EURASIP J. Wirel. Commun. Netw. 2015, 2015, 207. [Google Scholar] [CrossRef]
- Bakshi, M.; Kaddour, M.; Jaumard, B.; Narayanan, L. An efficient method to minimize TDMA frame length in wireless sensor networks. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; pp. 825–830. [Google Scholar]
- Gao, D.; Wu, G.; Liu, Y.; Zhang, F. Bounded end-to-end delay with Transmission Power Control techniques for rechargeable wireless sensor networks. AEU Int. J. Electron. Commun. 2014, 68, 396–405. [Google Scholar] [CrossRef]
- Merlin, C.J.; Heinzelman, W.B. Duty cycle control for low-power-listening MAC protocols. IEEE Trans. Mob. Comput. 2010, 9, 1508–1521. [Google Scholar] [CrossRef]
- Sun, Y.; Du, S.; Johnson, D.B.; Gurewitz, O. DW-MAC: A low latency, energy efficient demand—Wakeup MAC protocol for wireless sensor networks. In Proceedings of the 9th ACM International Symposium on Mobile ad Hoc Networking and Computing, Hong Kong, China, 26–30 May 2008; pp. 53–62. [Google Scholar]
- Zhao, Y.Z.; Ma, M.; Miao, C.Y.; Nguyen, T.N. An energy-efficient and low-latency MAC protocol with adaptive scheduling for multi-hop wireless sensor networks. Comput. Commun. 2010, 33, 1452–1461. [Google Scholar] [CrossRef]
- Xu, J.; Liu, X.; Ma, M.; Liu, A.; Wang, T.; Huang, C. Intelligent Aggregation based on Content Routing Scheme for Cloud Computing. Symmetry 2017, 9, 221. [Google Scholar] [CrossRef]
- Naveen, K.P.; Kumar, A. Relay selection for geographical forwarding in sleep-wake cycling wireless sensor networks. IEEE Trans. Mob. Comput. 2013, 12, 475–488. [Google Scholar] [CrossRef]





| Parameter | Value | Description |
|---|---|---|
| 0.5 | Initial energy (J) | |
| 15 | Sensing duration (s) | |
| 100 | Communication duration (ms) | |
| 0.26 | Preamble duration (ms) | |
| 0.26 | Acknowledge window duration (ms) | |
| 0.93 | Data packet duration (ms) | |
| 0.0511 | Power consumption in transmission (w) | |
| 0.0588 | Power consumption in receiving (w) | |
| 0.0036 | Power consumption in sensing (w) | |
| 2.4 × 10−7 | Power consumption in sleeping (w) |
| Symbol | Description |
|---|---|
| Sensing duty cycle | |
| Communication duty cycle | |
| Energy consumption in low power listening | |
| Energy consumption in data transmission | |
| Energy consumption in event sensing | |
| Energy consumption in data receiving |
| Cost/pEDP | Sink | A | B | C | D | E | F |
|---|---|---|---|---|---|---|---|
| CCP | 267.94 | 215.03 | 165.49 | 165.49 | 165.05 | 117.39 | 69.78 |
| CSD | 189.22 | 169.76 | 169.76 | 216.97 | 241.24 | 192.12 | 235.43 |
| TC | 212.84 | 183.34 | 168.48 | 201.52 | 218.38 | 169.70 | 185.74 |
| Cost/pEDP | J | A | N | O | P | B | Original |
|---|---|---|---|---|---|---|---|
| CCP | 23.10 | 267.94 | 117.39 | 165.05 | 213.33 | 264.57 | 0 |
| CSD | 235.43 | 210.04 | 239.15 | 241.24 | 244.71 | 258.20 | 280.90 |
| TC | 171.74 | 227.41 | 202.62 | 218.38 | 235.30 | 260.11 | 196.63 |
| Cost/pEDP | Sink | N | O | P | B | A | Original |
|---|---|---|---|---|---|---|---|
| CCP | 314.24 | 211.35 | 211.35 | 259.19 | 308.73 | 308.73 | 0 |
| CSD | 211.96 | 288.94 | 263.97 | 267.16 | 272.45 | 237.96 | 305.43 |
| TC | 242.64 | 265.66 | 248.18 | 264.77 | 283.34 | 259.19 | 213.80 |
| Cost/pEDP | Sink | A | B | P | O | N | I | J |
|---|---|---|---|---|---|---|---|---|
| CCP | 267.94 | 267.94 | 264.57 | 264.57 | 262.87 | 260.730 | 259.59 | 211.67 |
| CSD | 189.22 | 210.14 | 258.20 | 285.95 | 305.21 | 321.69 | 340.28 | 335.30 |
| TC | 212.84 | 227.48 | 260.11 | 279.53 | 292.51 | 303.40 | 316.07 | 298.21 |
| Cost/pEDP | U | A’ | B’ | C’ | Original |
|---|---|---|---|---|---|
| CCP | 114.31 | 114.31 | 114.03 | 67.70 | 0 |
| CSD | 254.99 | 277.73 | 298.19 | 297.89 | 319.08 |
| TC | 212.79 | 228.71 | 242.94 | 228.83 | 223.36 |
| Cost/pEDP | G’ | F’ | H’ | Original |
|---|---|---|---|---|
| CCP | 67.87 | 69.02 | 69.02 | 0 |
| CSD | 257.42 | 277.89 | 299.33 | 320.77 |
| TC | 201.16 | 215.23 | 230.24 | 224.54 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, M.; Zhao, M.; Liu, A.; Ma, M.; Wang, T.; Huang, C. Fast and Efficient Data Forwarding Scheme for Tracking Mobile Targets in Sensor Networks. Symmetry 2017, 9, 269. https://doi.org/10.3390/sym9110269
Zhou M, Zhao M, Liu A, Ma M, Wang T, Huang C. Fast and Efficient Data Forwarding Scheme for Tracking Mobile Targets in Sensor Networks. Symmetry. 2017; 9(11):269. https://doi.org/10.3390/sym9110269
Chicago/Turabian StyleZhou, Mi, Ming Zhao, Anfeng Liu, Ming Ma, Tiang Wang, and Changqin Huang. 2017. "Fast and Efficient Data Forwarding Scheme for Tracking Mobile Targets in Sensor Networks" Symmetry 9, no. 11: 269. https://doi.org/10.3390/sym9110269
APA StyleZhou, M., Zhao, M., Liu, A., Ma, M., Wang, T., & Huang, C. (2017). Fast and Efficient Data Forwarding Scheme for Tracking Mobile Targets in Sensor Networks. Symmetry, 9(11), 269. https://doi.org/10.3390/sym9110269







