The Effect of Motivation on the Behavioral Intention to Protect Industrial Techniques of High-Tech Firms’ Employees
Abstract
:1. Introduction
2. Literature Review and Hypothesis Development
2.1. Motivation and Theory of Planned Behavior
2.2. Motivation and TPB in Relation to Technology Protection
2.3. Behavioral Intention to Protect Industrial Techniques
3. Research Methods
3.1. Research Model
3.2. Measurement Variable and Data Collection
3.3. Demographic Information from the Data
4. Results
4.1. Reliability and Validity Results
4.2. Analysis Results of Structural Model
4.3. Mediated Effect
5. Discussions
6. Conclusions
6.1. Research Implications
6.2. Limitations and Future Directions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Adler, Barry E., and Marcel Kahan. 2013. The technology of creditor protection. University of Pennsylvania Law Review 161: 1773–814. [Google Scholar]
- Ahmad, Atif, Rachelle Bosua, and Rens Scheepers. 2014. Protecting organizational competitive advantage: A knowledge leakage perspective. Computers & Security 42: 27–39. [Google Scholar]
- Ajzen, Icek. 1985. From Intentions to Actions: A Theory of Planned Behavior. Berlin/Heidelberg: Springer. [Google Scholar]
- Ajzen, Icek. 1988. Attitudes, Personality, and Behavior. Chicago: Dorsey Press. [Google Scholar]
- Ajzen, Icek. 1991. The theory of planned behavior. Organizational Behavior and Human Decision Processes 50: 179–211. [Google Scholar] [CrossRef]
- Ajzen, Icek. 2006. Constructing a TpB Questionnaire: Conceptual and Methodological Considerations. Working Paper. Amherst: University of Massachusetts. Available online: http://www-unix.oit.umass.edu/~aizen/pdf/tpb.measurement.pdf (accessed on 15 June 2024).
- Ajzen, Icek, and Beverly Driver. 1992. Application of the theory of planned behavior to leisure choice. Journal of Leisure Research 24: 207–24. [Google Scholar] [CrossRef]
- Ajzen, Icek, and Martin Fishbein. 1980. Understanding Attitudes and Predicting Social Behavior. Englewood Cliffs: Prentice Hall. [Google Scholar]
- Armitage, Christopher, and Mark Conner. 2001. Efficacy of the theory of planned behavior: A meta-analytic review. British Journal of Social Psychology 40: 471–99. [Google Scholar] [CrossRef] [PubMed]
- Atkinson, John W. 1964. An Introduction to Motivation. Princeton: Van Nostrand. [Google Scholar]
- Baele, Stephane, David Lewis, Anke Hoeffler, Olivier Sterck, and Thibaut Slingeneyer. 2018. The ethics of security research: An ethics framework for contemporary security studies. International Studies Perspectives 19: 105–27. [Google Scholar] [CrossRef]
- Bandura, Albert. 1977. Social Learning Theory. Englewood Cliffs: Prentice-Hall. [Google Scholar]
- Carrière, Jean-Bernard, Jacqueline Dionne-Proulx, and Yves Beauchamp. 1998. Strategic management of new technologies and prevention of industrial accidents: Theoretical framework and empirical analyses. Human Factors and Ergonomics in Manufacturing & Service Industries 8: 1–22. [Google Scholar]
- Chun, Yongtae, and Julak Lee. 2014. An analysis on the industrial technology leakage cases in South Korea. British Journal of Business and Management Research 1: 103–14. [Google Scholar] [CrossRef]
- Conner, Mark, and Christopher Armitage. 1998. Extending the theory of planned behavior: A review and avenues for further research. Journal of Applied Social Psychology 28: 1429–64. [Google Scholar] [CrossRef]
- Dang, Chongyu, Zhichuan Frank Li, and Chen Yang. 2018. Measuring firm size in empirical corporate finance. Journal of Banking & Finance 86: 159–76. [Google Scholar]
- Deci, Edward L. 1971. Effects of externally mediated rewards on intrinsic motivation. Journal of Personality and Social Psychology 18: 105–11. [Google Scholar] [CrossRef]
- Deci, Edward L., and Richard M. Ryan. 1985a. Intrinsic Motivation and Self-Determination in Human Behavior. New York: Plenum. [Google Scholar]
- Deci, Edward L., and Richard M. Ryan. 1985b. The general causality orientations scale: Self-determination in personality. Journal of Research in Personality 19: 109–34. [Google Scholar] [CrossRef]
- Deci, Edward L., and Richard M. Ryan. 2000. The “What” and “Why” of goal pursuits: Human needs and the self-determination of behavior. Psychological Inquiry 11: 227–68. [Google Scholar] [CrossRef]
- Deci, Edward L., Richard Koestner, and Richard Ryan. 1999. A meta-analytic review of experiments examining the effects of extrinsic rewards on intrinsic motivation. Psychological Bulletin 125: 627–68. [Google Scholar] [CrossRef] [PubMed]
- Delaney, Mark, and Michael Royal. 2017. Breaking engagement apart: The role of intrinsic and extrinsic motivation in engagement strategies. Industrial and Organizational Psychology 10: 127–40. [Google Scholar] [CrossRef]
- Dweck, Carol S. 1986. Motivational processes affecting learning. American Psychologist 41: 1040–48. [Google Scholar] [CrossRef]
- Eccles, Jacquelynne, and Allan Wigfield. 2002. Motivational beliefs, values, and goals. Annual Review of Psychology 53: 109–32. [Google Scholar] [CrossRef] [PubMed]
- Fair, Ellen, and Leonard Silvestri. 1992. Effects of rewards, competition and outcome on intrinsic motivation. Journal of Instructional Psychology 19: 3–8. [Google Scholar]
- Fischer, Carmen, Charlotte Malycha, and Ernestine Schafmann. 2019. The influence of intrinsic motivation and synergistic extrinsic motivators on creativity and innovation. Frontiers in Psychology 10: 137. [Google Scholar] [CrossRef]
- Fishbein, Martin. 1963. An investigation of the relationships between beliefs about an object and the attitude toward that object. Human Relations 16: 233–39. [Google Scholar] [CrossRef]
- Fishbein, Martin, and Icek Ajzen. 1975. Belief, Attitude, Intention, and Behavior. An Introduction to Theory and Research. Reading: Addison-Wesley. [Google Scholar]
- Goel, Nidhi, and Kumari Rashmi. 2023. Impact of motivation on employee engagement: A literature review. Journal of Statistics and Management Systems 26: 537–47. [Google Scholar] [CrossRef]
- Guay, Frédéric, Robert J. Vallerand, and Céline Blanchard. 2000. On the assessment of situational intrinsic and extrinsic motivation: The Situational Motivation Scale (SIMS). Motivation and Emotion 24: 175–213. [Google Scholar] [CrossRef]
- Ha, Reeda, and Hwansoo Lee. 2024. Legal improvements to protect and manage industrial technology. Korean Security Journal 78: 29–52. [Google Scholar] [CrossRef]
- Hagger, Martin S., and Nikos L. D. Chatzisarantis. 2007. Self-Determination Theory and the Theory of Planned Behavior: An Integrative Approach toward a More Complete Model of Motivation. In Psychology of Motivation. Edited by Lois V. Brown. Hauppauge: Nova Science Publishers, pp. 83–98. [Google Scholar]
- Hagger, Martin S., and Nikos L. D. Chatzisarantis. 2009a. Integrating the theory of planned behaviour and self-determination theory in health behaviour: A meta-analysis. British Journal of Health Psychology 14: 275–302. [Google Scholar] [CrossRef] [PubMed]
- Hagger, Martin S., and Nikos L. D. Chatzisarantis. 2009b. Intrinsic Motivation and Self-Determination in Exercise and Sport. Champaign: Human Kinetics. [Google Scholar]
- Heider, Fritz. 1958. The Psychology of Interpersonal Relations. New York: Wiley. [Google Scholar]
- Hoecht, Andreas, and Paul Trott. 2006. Innovation risks of strategic outsourcing. Technovation 26: 672–81. [Google Scholar] [CrossRef]
- Huang, Yung-Chuan. 2023. Integrated concepts of the UTAUT and TPB in virtual reality behavioral intention. Journal of Retailing and Consumer Services 70: 103127. [Google Scholar] [CrossRef]
- Hungerford, Harold, and Trudi Volk. 1990. Changing learner behavior through environmental education. Journal of Environmental Education 21: 8–21. [Google Scholar] [CrossRef]
- Husman, Jenefer, and Willy Lens. 1999. The role of the future in student motivation. Educational Psychologist 34: 113–25. [Google Scholar] [CrossRef]
- Hwang, Hyundong, and Changmoo Lee. 2016. A study on the relationship between industrial technology leakage, self-control, and organizational attachment. Journal of Korean Security Guard Association 47: 119–38. [Google Scholar]
- Hwang, Inho, and Sungho Hu. 2018. A study on the influence of information security compliance intention of employee: Theory of planned behavior, Justice Theory, and Motivation Theory Applied. Digital Convergence Research 16: 225–36. [Google Scholar]
- Ifinedo, Princely. 2012. Understanding information systems security policy compliance: An integration of the theory of planned behavior and the protection motivation theory. Computers & Security 31: 83–95. [Google Scholar]
- Jung, Jeyong. 2024. Analysis of the US industrial technology leak response system and legislation. Crime Investigation Research 19: 233–57. [Google Scholar] [CrossRef]
- Kim, Jongki, and Jian Mou. 2020. Meta-analysis of information security policy compliance based on theory of planned behavior. Journal of Digital Convergence 18: 169–76. [Google Scholar]
- Kim, Seonwook. 2021. Legislative improvement plan for the prevention of national core technology leakage by industrial spy. Wonkwang Law Review 37: 33–53. [Google Scholar] [CrossRef]
- Kim, Soonseok, and Jaechul Shin. 2010. The plan for core personnel management to prevent industrial technology leakage. Journal of Korean Security Science Association 25: 109–30. [Google Scholar] [CrossRef]
- Kline, Rex. 2005. Principles and Practice of Structural Equation Modeling, 2nd ed. New York: The Guilford Press. [Google Scholar]
- Kor, Kenny, and Barbara Mullan. 2011. Sleep hygiene behaviours: An application of the theory of planned behavior and the investigation of perceived autonomy support, past behavior and response inhibition. Psychology & Health 26: 1208–24. [Google Scholar]
- Kranz, Johann, and Felix Haeussinger. 2014. Why Deterrence Is Not Enough: The Role of Endogenous Motivations on Employees’ Information Security Behavior. Paper presented at the IS Security and Privacy, Thirty Fifth International Conference on Information Systems, Auckland, New Zealand, December 14–17. [Google Scholar]
- Landy, Frank, and William Becker. 1987. Motivation theory reconsidered. Research in Organizational Behavior 9: 1–38. [Google Scholar]
- Lee, Ganghook. 2020. Study on the risk of industrial technology infringement by insiders: Focusing on R&D workers. Security Research 63: 129–52. [Google Scholar]
- Li, Chunxiao, Yandan Wu, and YingHwa Kee. 2016. Validation of the volunteer motivation scale and its relations with work climate and intention among Chinese volunteers. Asian Journal of Social Psychology 19: 124–33. [Google Scholar] [CrossRef]
- Manning, Mark. 2011. When we do what we see: The moderating role of social motivation on the relation between subjective norms and behavior in the theory of planned behavior. Basic and Applied Social Psychology 33: 351–64. [Google Scholar] [CrossRef]
- McKinsey Global Institute. 2016. Digital Globalization: The New Era of Global Flows. Chicago: McKinsey & Company. [Google Scholar]
- National Police Agency. 2023. 2023 Year Special Crackdown on Economic Security Crimes; Seoul: National Police Agency Press Release.
- National Statistical Office in South Korea. 2024. Company Size Classification. Available online: https://kostat.go.kr/board.es?mid=a10502010000&bid=12282&tag=&act=view&list_no=414440&ref_bid= (accessed on 8 August 2024).
- Nicholls, John. 1984. Achievement motivation: Conceptions of ability, subjective experience, task choice, and performance. Psychological Review 91: 328–46. [Google Scholar] [CrossRef]
- Norman, Paul, Tim Clark, and Glen Walker. 2005. The Theory of Planned Behavior, Descriptive Norms, and the Mediation Role of Group Identification. Journal of Applied Social Psychology 35: 1008–29. [Google Scholar] [CrossRef]
- Otchengco, Alberto Magtoto, Jr., and Yuri Walter Dulay Akiate. 2021. Entrepreneurial intentions on perceived behavioral control and personal attitude: Moderated by structural support. Asia Pacific Journal of Innovation and Entrepreneurship 15: 14–25. [Google Scholar] [CrossRef]
- Padayachee, Keshnee. 2012. Taxonomy of compliant information security behavior. Computers & Security 31: 673–80. [Google Scholar]
- Pandya, Jainisha. D. 2024. Intrinsic & extrinsic motivation & its impact on organizational performance at Rajkot city: A review. Journal of Management Research and Analysis 11: 46–53. [Google Scholar]
- Quintal, Vanessa, Julie Lee, and Geoffrey Soutar. 2010. Risk, uncertainty and the theory of planned behavior: A tourism example. Tourism Management 31: 797–805. [Google Scholar] [CrossRef]
- Rivis, Amanda, and Paschal Sheeran. 2003. Social influence and the theory of planned behaviour: Evidence for a direct relationship between prototypes and young people exercise behaviour. Psychology and Health 18: 567–83. [Google Scholar] [CrossRef]
- Robbins, Stephen, and Timothy Judge. 2011. Organizational Behavior. Boston: Prentice Hall. [Google Scholar]
- Ryan, Richard, and Edward L. Deci. 2000a. Intrinsic and extrinsic motivations: Classic definitions and new directions. Contemporary Educational Psychology 25: 54–67. [Google Scholar] [CrossRef] [PubMed]
- Ryan, Richard, and Edward L. Deci. 2000b. Self-determination theory and the facilitation of intrinsic motivation, social development, and well-being. American Psychologist 55: 68–78. [Google Scholar] [CrossRef]
- Safa, Nader Sohrabi, and Rossouw Von Solms. 2016. An information security knowledge sharing model in organizations. Computers in Human Behavior 57: 442–51. [Google Scholar] [CrossRef]
- Sahyunu, La Ode Abdul Manan, Ghalib Suprianto, Sri Wiyati Mahrani, and Wa Ode Safariati. 2023. The effect of intrinsic and extrinsic motivation on employee performance at digital engineering consultant. IOSR Journal of Business and Management 25: 50–55. [Google Scholar]
- Security Magazine. 2024. Insider-Driven Data Loss Incidents Cost an Average of $15 Million. Available online: https://www.securitymagazine.com/articles/100483-insider-driven-data-loss-incidents-cost-an-average-of-15-million (accessed on 15 June 2024).
- Singh, Rajesh. 2016. The impact of intrinsic and extrinsic motivators on employee engagement in information organizations. Journal of Education for Library and Information Science 57: 197–206. [Google Scholar]
- Sommestad, Teodor, and Johan Hallberg. 2013. A Review of the Theory of Planned Behaviour in the Context of Information Security Policy Compliance. In Security and Privacy Protection in Information Processing Systems. Edited by Lech J. Janczewski, Henry B. Wolfe and Sujeet Shenoi. IFIP Advances in Information and Communication Technology. Berlin: Springer, vol. 405, pp. 243–57. [Google Scholar] [CrossRef]
- Sung, Jinki. 2024. A study on the introduction of the technology valuation system to investigation on industrial technology leaks. Crime Investigation Research 19: 213–32. [Google Scholar] [CrossRef]
- Vansteenkiste, Maarten, and Willy Lens. 2006. Intrinsic versus extrinsic goal contents in self-determination theory: Another look at the quality of academic motivation. Educational Psychologist 41: 19–31. [Google Scholar] [CrossRef]
- Weiner, Bernard. 1985. An attributional theory of achievement motivation and emotion. Psychological Review 92: 548–73. [Google Scholar] [CrossRef] [PubMed]
- Workman, Michael, and John Gathegi. 2007. Punishment and ethics deterrents: A study of insider security contravention. Journal of the American Society for Information Science and Technology 58: 212–22. [Google Scholar] [CrossRef]
- Yılmaz, Ercan Nurcan, and Serkan Gönen. 2018. Attack detection/prevention system against cyber attack in industrial control systems. Computers & Security 77: 94–105. [Google Scholar]
- Youn, Yunsung. 1999. Teaching-learning theories and effective motivational strategies. Journal of Social Science 2: 209–35. [Google Scholar]
- Zhu, Sherry, Eric Guo, Max Lu, and Anna Yue. 2016. An Efficient Data Leakage Prevention Framework for Semiconductor Industry. Paper presented at the 2016 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Bali, Indonesia, December 4–7. [Google Scholar]
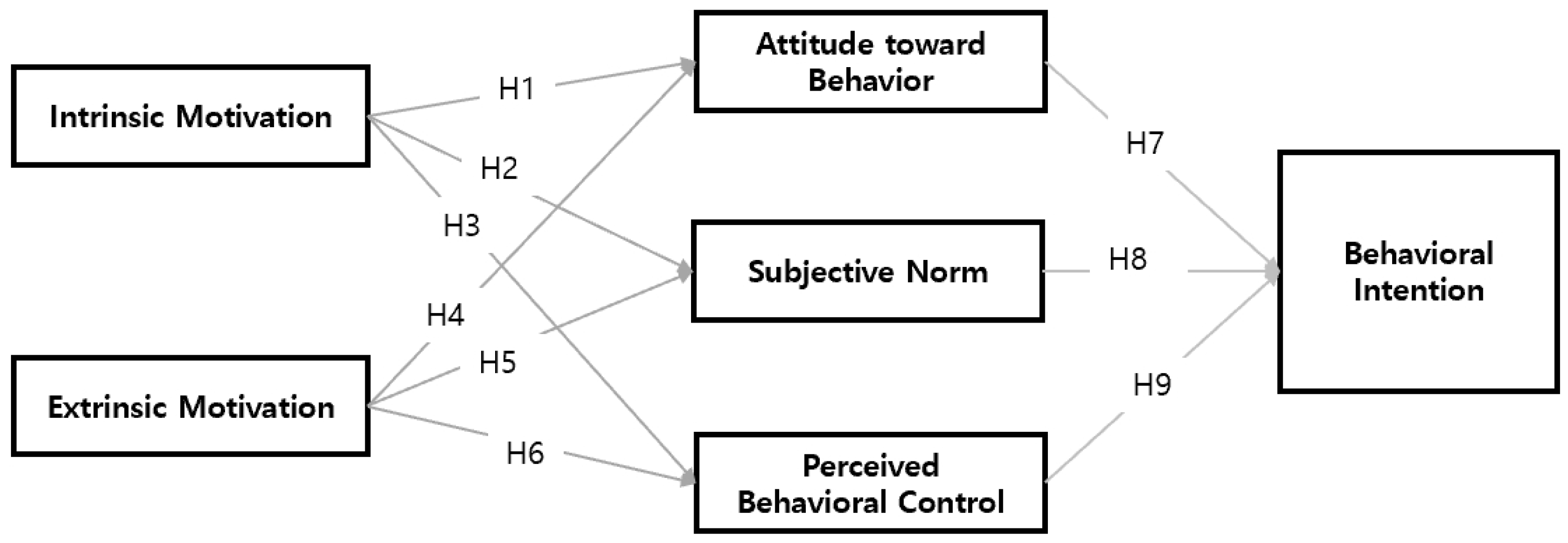
| Theories | Key Concepts | Sources and Representative Scholars |
|---|---|---|
| Intrinsic/extrinsic motivation theory | The theory states that behavior is driven by intrinsic motivation, where individuals are motivated by the enjoyment or interest of the activity, and extrinsic motivation, where individuals are motivated by external rewards or punishments. | Deci and Ryan (1985b, 2000) |
| Attribution theory | The theory posits that individuals’ behaviors and emotions are shaped by their reasoning about the causes of their own and others’ behaviors, which they attribute to internal factors (ability, effort) or external factors (luck, circumstances). | Heider (1958) and Weiner (1985) |
| Expectancy–value theory | The theory posits that an individual’s behavior is motivated by the anticipation of success and the perceived value of that success. | Eccles and Wigfield (2002) |
| Self-determination theory | The theory posits that intrinsic motivation is enhanced when three fundamental psychological needs are fulfilled: autonomy, competence, and relatedness. | Deci and Ryan (1985b) |
| Self-efficacy theory | The theory posits that an individual’s belief in their ability to successfully perform a particular task influences their subsequent behavior and motivation. | Bandura (1977) |
| Achievement goal theory | The theory posits that individuals are motivated by how they seek achievement, and that this motivation can be divided into two categories: mastery goals, which prioritize learning and growth, and performance goals, which prioritize comparison with others. | Nicholls (1984) and Dweck (1986) |
| Future time perspective theory | The theory that an individual’s perspective on the future affects their motivations and behaviors in the present. | Husman and Lens (1999) |
| Factor | Measurement Item | Reference |
|---|---|---|
| Intrinsic motivation |
| Deci and Ryan (1985a, 1985b) Ryan and Deci (2000a, 2000b) Guay et al. (2000) Li et al. (2016) |
| Extrinsic motivation |
| |
| Attitude toward behavior |
| Ajzen and Driver (1992), Ajzen (2006), Quintal et al. (2010) |
| Subjective norm |
| |
| Perceived behavioral control |
| |
| Behavioral intention |
|
| Classification | Frequency | Percentage (%) | |
|---|---|---|---|
| Gender | Male | 130 | 65.0 |
| Female | 70 | 35.0 | |
| Age | 20 to 29 | 15 | 7.5 |
| 30 to 39 | 76 | 38.0 | |
| 40 to 49 | 73 | 36.5 | |
| 50 to 59 | 30 | 15.0 | |
| 60 to 69 | 6 | 3.0 | |
| Field | Electronics (semiconductors, displays) | 45 | 22.5 |
| Information technology (IT) | 93 | 46.5 | |
| Genetics and biotechnology | 25 | 12.5 | |
| New materials | 32 | 16.0 | |
| Other | 5 | 2.5 | |
| Title | Superior to executives | 19 | 9.5 |
| Department manager, Director | 34 | 17.0 | |
| Manager, Deputy general manager | 82 | 41.0 | |
| Staff, Associate, Assistant manager | 65 | 32.5 | |
| Corporation size | Large companies | 94 | 47.0 |
| Small and Medium-sized enterprises | 105 | 52.5 | |
| Other | 1 | 0.5 | |
| Work experience | Less than 5 years | 47 | 23.5 |
| 5 to 10 years | 68 | 34.0 | |
| 10 to 20 years | 55 | 27.5 | |
| More than 20 years | 30 | 15.0 | |
| Experience in industrial technology protection | Yes | 82 | 41.0 |
| No | 74 | 37.0 | |
| I am not sure | 44 | 22.0 | |
| Variable | N | Minimum | Maximum | Mean | Standard Deviation | Skewness | Kurtosis |
|---|---|---|---|---|---|---|---|
| Intrinsic motivation | 200 | 2 | 5 | 3.90 | 0.575 | 0.013 | −0.079 |
| Extrinsic motivation | 200 | 1 | 5 | 3.06 | 0.793 | −0.391 | 0.062 |
| Attitude toward behavior | 200 | 2 | 5 | 4.22 | 0.596 | −0.346 | −0.173 |
| Subjective norm | 200 | 2 | 5 | 3.82 | 0.710 | −0.065 | −0.271 |
| Perceived behavioral control | 200 | 2 | 5 | 3.52 | 0.788 | −0.113 | −0.381 |
| Behavioral intention | 200 | 2 | 5 | 3.87 | 0.645 | 0.029 | −0.369 |
| Variable | Measurement Question | Factor Loadings | C.R. (p) | CV | AVE | Cronbach α |
|---|---|---|---|---|---|---|
| Intrinsic motivation | IM1 | 0.805 | 0.856 | 0.664 | 0.777 | |
| IM2 | 0.798 | 8.547 *** | ||||
| IM3 | 0.784 | 8.634 *** | ||||
| Extrinsic motivation | EM1 | 0.850 | 0.760 | 0.616 | 0.742 | |
| EM2 | 0.782 | 5.882 *** | ||||
| EM3 | 0.726 | 14.170 *** | ||||
| Attitude toward behavior | AB1 | 0.876 | 0.949 | 0.822 | 0.896 | |
| AB 2 | 0.857 | 13.044 *** | ||||
| AB 3 | 0.839 | 13.722 *** | ||||
| Subjective norm | SN1 | 0.878 | 0.908 | 0.767 | 0.861 | |
| SN 2 | 0.828 | 13.012 *** | ||||
| SN 3 | 0.799 | 13.004 *** | ||||
| Perceived behavioral control | PBC1 | 0.911 | 0.700 | 0.534 | 0.650 | |
| PBC 2 | 0.696 | 7.638 *** | ||||
| Behavioral intention | BI1 | 0.887 | 0.903 | 0.757 | 0.835 | |
| BI2 | 0.882 | 12.055 *** | ||||
| BI3 | 0.836 | 11.514 *** |
| χ2 | df | p | TLI | CFI | RMSEA | SRMR | ||
|---|---|---|---|---|---|---|---|---|
| Value | Lower Bound | Upper Bound | ||||||
| 234.019 | 104 | 0.000 | 0.906 | 0.928 | 0.079 | 0.066 | 0.093 | 0.047 |
| Intrinsic Motivation | Extrinsic Motivation | Attitude toward Behavior | Subjective Norm | Perceived Behavioral Control | Behavioral Intention | |
|---|---|---|---|---|---|---|
| Intrinsic motivation | 0.815 | |||||
| Extrinsic motivation | 0.038 | 0.785 | ||||
| Attitude toward behavior | 0.504 | −0.180 | 0.907 | |||
| Subjective norm | 0.435 | 0.185 | 0.452 | 0.767 | ||
| Perceived behavioral control | 0.429 | 0.243 | 0.264 | 0.514 | 0.731 | |
| Behavioral intention | 0.592 | 0.042 | 0.593 | 0.613 | 0.566 | 0.870 |
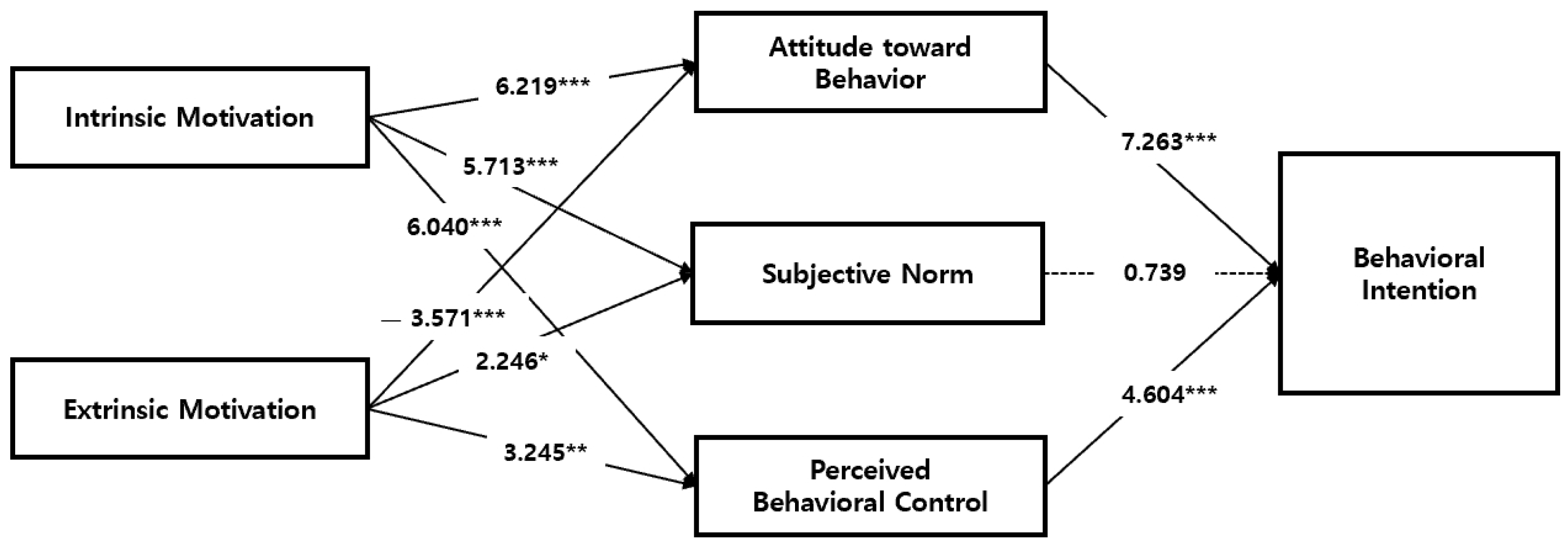
| Path | S.E. | β | C.R. (p) | Hypothesis | |
|---|---|---|---|---|---|
| H1 | Intrinsic motivation -> Attitude toward behavior | 0.090 | 0.552 | 6.219 *** | Accepted |
| H2 | Intrinsic motivation -> Subjective norm | 0.112 | 0.511 | 5.713 *** | Accepted |
| H3 | Intrinsic motivation -> Perceived behavioral control | 0.131 | 0.694 | 6.040 *** | Accepted |
| H4 | Extrinsic motivation -> Attitude toward behavior | 0.055 | −0.273 | −3.571 *** | Accepted |
| H5 | Extrinsic motivation -> Subjective norm | 0.071 | 0.178 | 2.246 * | Accepted |
| H6 | Extrinsic motivation -> Perceived behavioral control | 0.070 | 0.280 | 3.245 ** | Accepted |
| H7 | Attitude toward behavior -> Behavioral intention | 0.076 | 0.564 | 7.263 *** | Accepted |
| H8 | Subjective norms -> Behavioral intention | 0.083 | 0.078 | 0.739 | Rejected |
| H9 | Perceived behavioral control -> Behavioral intention | 0.104 | 0.548 | 4.604 *** | Accepted |
| Dependent Variable | Explanatory Variable | Direct Effect | Indirect Effect | Total Effect |
|---|---|---|---|---|
| Intrinsic motivation | Attitude toward behavior | 0.558 ** | 0.060 | |
| Subjective norm | 0.643 ** | |||
| Perceived behavioral control | 0.789 ** | |||
| Attitude toward behavior -> Behavioral intention | 0.309 ** | 0.005 | ||
| Subjective norms -> Behavioral intention | 0.039 | |||
| Perceived behavioral control -> Behavioral intention | 0.378 ** | 0.010 | ||
| Extrinsic motivation | Attitude toward behavior | −0.197 ** | 0.094 | |
| Subjective norm | 0.161 ** | 0.007 | ||
| Perceived behavioral control | 0.228 ** | 0.016 | ||
| Attitude toward behavior -> Behavioral intention | −0.109 ** | |||
| Subjective norms -> Behavioral intention | 0.010 | |||
| Perceived behavioral control -> Behavioral intention | 0.109 ** |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, S.; Kim, B.; Ivan, U.V. The Effect of Motivation on the Behavioral Intention to Protect Industrial Techniques of High-Tech Firms’ Employees. Adm. Sci. 2024, 14, 176. https://doi.org/10.3390/admsci14080176
Lee S, Kim B, Ivan UV. The Effect of Motivation on the Behavioral Intention to Protect Industrial Techniques of High-Tech Firms’ Employees. Administrative Sciences. 2024; 14(8):176. https://doi.org/10.3390/admsci14080176
Chicago/Turabian StyleLee, Sangwoo, Boyoung Kim, and Ureta Vaquero Ivan. 2024. "The Effect of Motivation on the Behavioral Intention to Protect Industrial Techniques of High-Tech Firms’ Employees" Administrative Sciences 14, no. 8: 176. https://doi.org/10.3390/admsci14080176





