DroidPortrait: Android Malware Portrait Construction Based on Multidimensional Behavior Analysis
Abstract
:1. Introduction
- —
- To introduce a behavioral portrait technique to depict Android malware behavior for detection purposes. This approach relies on characteristic extraction, selection, behavioral tag construction and it builds a behavioral portrait that could consider both static and dynamic behavioral characteristic;
- —
- To propose a random forest-based malware detection algorithm, which can dynamically select decision trees with higher classification performance. This algorithm overall improves decision tree fusion effectiveness and ensures the generality of the algorithm;
- —
- To evaluate the efficiency and effectiveness of the proposed approach by using three real-world Android app datasets. Based on the experimental results, we find that the DroidPortrait approach can achieve 99% accuracy for making a comprehensive portrait for an Android app and it can achieve more than 97% accuracy for the detection of malware;
2. Related Work
2.1. Static Analysis Based Malware Detection Approaches
2.2. Dynamic Analysis-Based Malware Detection
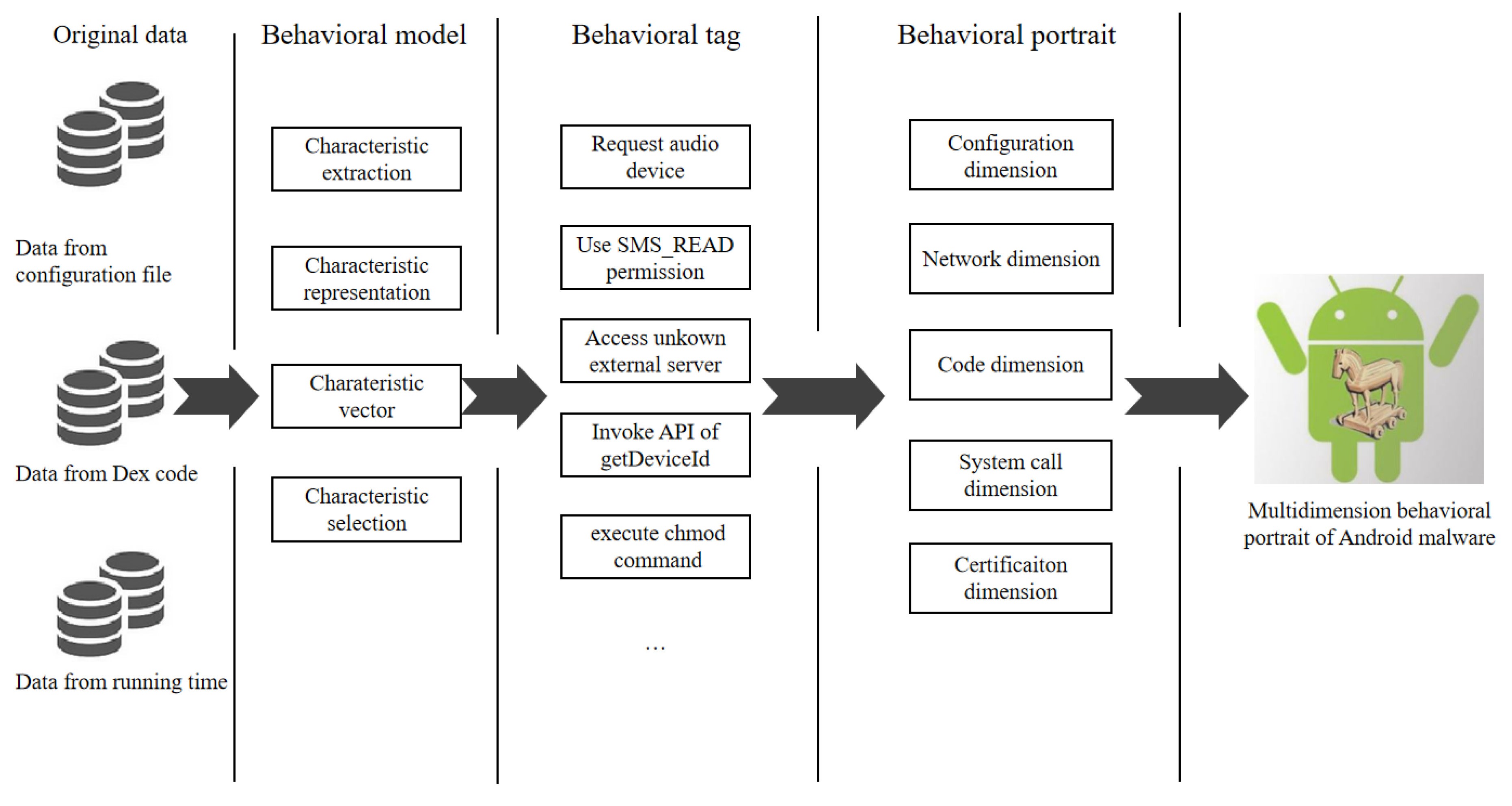
3. The Overall, Design of DroidPortrait
3.1. Behavioral Model Construction
3.1.1. Behavioral Characteristic Extraction
| Listing 1: An example of extracting API |
| <rule> |
| <id>5</id> |
| <category>FrameworkAPI</category> |
| <description>Extract APIs of Framework</description> |
| <regex>Landroid(/\w+)+;->\w+|Landroid(/\w+)+\$\w+</regex> |
| <targetfile>smali</targetfile> |
| <multiMatch>true</multiMatch> |
| </rule> |
3.1.2. Behavioral Characteristic Transformation
3.1.3. Behavioral Characteristic Selection
3.2. Behavioral Tag
3.3. Behavioral Portrait
4. Android Malware Behavioral Portrait Training
4.1. Back Propagation Neural Network
| Algorithm 1 Algorithm of BPPN |
| Input: training dataset , learning rate |
| Output: BPPN model with established weight and corresponding bias |
| 1 Random initialized weight and bias of BPPN in range of (0,1) |
| 2 for all do |
| 3 // Output results of BPPN |
| 4 // Neuronal gradient of the output layer |
| 5 // Neuronal gradient of hidden layer |
| 6 // Weight update |
| 7 // Bias update |
| 8 // Input layer update |
| 9 // Error rate update |
| 10 end for |
| 11 Repeat the above steps, until is less than the threshold; |
4.2. Optimized Random Forest
4.2.1. Decision Tree Construction
4.2.2. Decision Tree Selection and Ensemble
5. Evaluation
5.1. Dataset
5.2. Evaluating Behavioral Characteristic Selection Approach
5.2.1. Static Behavioral Characteristic Selection
5.2.2. Dynamic Behavioral Characteristic Selection
5.3. Evaluation of Behavioral Portrait
5.3.1. Behavioral Portrait Visualization
5.3.2. Performance of Characteristic Behavioral Dimension
5.3.3. Performance of Behavioral Portrait
5.4. Evaluating the Performance of Unknown Android App Detection
6. Conclusions
- We extract two categories of behavioral characteristics from the Android app, namely, static behavioral characteristics and dynamic behavioral characteristics. These kinds of characteristic can cover Android malware behavior as much as possible. Meanwhile, we proposed two kinds of characteristic selection approaches for both kinds of behavioral characteristics to find intrinsic behavioral characteristics for Android malware detection;
- We divide these behavioral characteristics into five dimensions to build a behavioral tag. Then, we employ these behavioral tags are utilized to build a portrait of Android malware. After portrait construction, we employ two kinds of machine learning algorithms to train the Android malware behavioral portrait;
- We conduct three kinds of experiments to evaluate the proposed approach. First, we evaluate static and dynamic behavioral characteristic selection and using the selected behavioral characteristics to train classification models can achieve more than 90% accuracy and recall. Second, we evaluate the portrait of Android malware, which includes portrait visualize, the performance of behavioral dimension and portrait. We also compare with three well-known classification algorithms. Third, we evaluate the performance of our approach in detecting unknown Android malware and compare it with three well-known detection approaches.
Author Contributions
Funding
Conflicts of Interest
References
- Li, J.; Sun, L.; Yan, Q.; Li, Z.; Srisa-an, W.; Ye, H. Significant Permission Identification for Machine-Learning-Based Android Malware Detection. IEEE Trans. Ind. Inform. 2018, 14, 3216–3225. [Google Scholar] [CrossRef]
- Aafer, Y.; Du, W.L.; Yin, H. Droidapiminer: Mining api-level features for robust malware detection in Android. In Proceedings of the International ICST Conference on Security and Privacy in Communication Networks, Orlando, FL, USA, 23–25 October 2013; pp. 86–103. [Google Scholar]
- Talha, K.A.; Alper, D.I.; Aydin, C. Apk auditor: Permission-based android malware detection system. Digit. Investig. 2015, 13, 1–14. [Google Scholar] [CrossRef]
- Arp, D.; Spreitzenbarth, M.; Hubner, M.; Gascon, H.; Rieck, K.; Siemens, C. Drebin: Effective and explainable detection of android malware in your pocket. In Proceedings of the Annual Symposium on Network and Distributed System Security, San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Xie, N.; Wang, X.; Wang, W.; Liu, J. Fingerprinting Android malware families. Front. Comput. Sci. 2018, 13, 637–646. [Google Scholar] [CrossRef]
- Liang, W.; Li, K.C.; Long, J.; Kui, X.; Zomaya, A. An Industrial Network Intrusion Detection Algorithm based on Multi-Characteristic Data Clustering Optimization Model. IEEE Trans. Ind. Inform. 2019, 16, 2063–2071. [Google Scholar] [CrossRef]
- Deepa, K.; Radhamani, G.; Vinod, P.; Shojafar, M.; Kumar, N.; Conti, M. Identification of Android malware using refined system calls. Concurr. Comput. Pract. Exp. 2019, 31. [Google Scholar] [CrossRef]
- Yerima, S.Y.; Alzaylaee, M.K.; Sezer, S. Machine Learning Based Dynamic Analysis of Android apps with Improved Code Coverage. EURASIP J. Inf. Secur. 2019, 1, 1–24. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Ma, J.; Wang, W.; Liu, C. Cryptanalysis and improvement of a biometrics-based remote user authentication scheme using smart card. J. Netw. Comput. Appl. 2011, 34, 73–79. [Google Scholar] [CrossRef]
- Li, X.; Ma, J.; Wang, W.; Xiong, Y.; Zhang, J. A novel smart card and dynamic ID based remote user authentication scheme for multi-server environment. Math. Comput. Model. 2013, 58, 85–95. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Khan, M.K.; Liao, J. An enhanced smart card based remote user password authentication scheme. J. Netw. Comput. Appl. 2013, 36, 1365–1371. [Google Scholar] [CrossRef]
- Enck, W.; Gilbert, P.; Chun, B.; Cox, L.; Jung, J.; McDaniel, P.; Sheth, A. TaintDroid: An information-flow tracking system for real-time privacy monitoring on smartphones. ACM Trans. Comput. Syst. 2014, 32, 1–29. [Google Scholar] [CrossRef]
- Su, X.; Liu, X.; Lin, J.; He, S.; Fu, Z.; Li, W. De-cloaking Malicious Activities in Smartphones Using HTTP Flow Mining. KSII Trans. Internet Inf. Syst. 2017, 11, 3230–3253. [Google Scholar]
- Wu, F.; Lu, J.; Cao, W. Multi Feature Detection of Malicious Programs Based on Android Platform. J. Chin. Comput. Syst. 2018, 39, 151–155. [Google Scholar]
- Nath, H. Static Malware Analysis Using Machine Learning Methods. In Recent Trends in Computer Networks and Distributed Systems Security; Springer: Berlin/Heidelberg, Germany, 2014; pp. 440–450. [Google Scholar]
- Gorla, A.; Tavecchia, I.; Gross, F.; Zeller, A. Checking app behavior against app descriptions. In Proceedings of the 36th International Conference on Software Engineering (ICSE), Hyderabad, India, 31 May–7 June 2014; pp. 1025–2035. [Google Scholar]
- Yu, F.; Saswat, A.; Isil, D.; Alex, A. Apposcopy: Semantics-based detection of android malware through static analysis. In Proceedings of the 22nd ACM SIGSOFT International Symposium on Foundations of Software Engineering (FSE), Hong Kong, China, 16–21 November 2014; pp. 576–587. [Google Scholar]
- Zhu, H.; You, Z.; Zhu, Z.; Shi, W.; Chen, X.; Cheng, L. DroidDet: Effective and robust detection of android malware using static analysis along with rotation forest model. Neurocomputing 2017, 272, 638–646. [Google Scholar] [CrossRef]
- Xie, L.; Li, S. Android malware detection model based on Bagging-SVM. J. Comput. Appl. 2018, 38, 818–823. [Google Scholar]
- Park, J.; Chun, H.; Jing, S. API and permission-based classification system for Android malware analysis. In Proceedings of the 2018 International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 10–12 January 2018; Volume 1, pp. 930–935. [Google Scholar]
- Junaid, M.; Liu, D.G.; Kung, D. Dexteroid: Detecting malicious behaviors in Android apps using reverse-engineered life cycle models. Comput. Secur. 2016, 59, 92–117. [Google Scholar] [CrossRef] [Green Version]
- Wu, D.; Mao, C.; Wei, T.; Lee, H.; Wu, K. DroidMat: Android Malware Detection through Manifest and API Calls Tracing. In Proceedings of the 2012 Seventh Asia Joint Conference on Information Security, Tokyo, Japan, 9–10 August 2012; pp. 62–69. [Google Scholar]
- Yan, L.K.; Yin, H. Droidscope: Seamlessly reconstructing the os and Dalvik semantic views for dynamic android malware analysis. In Proceedings of the 21st USENIX Conference on Security Symposium, Bellevue, WA, USA, 8–10 August 2012; p. 29. [Google Scholar]
- Burguera, I.; Zurutuza, U.; Tehrani, S.N. Crowdroid: Behavior-based malware detection system for Android. In Proceedings of the 1st ACM Workshop on Security and Privacy in Smartphones and Mobile Devices, Chicago, IL, USA, 17 October 2011; pp. 15–26. [Google Scholar]
- Saracino, A.; Sgandurra, D.; Dini, G.; Martinelli, F. MADAM: Effective and Efficient Behavior-based Android Malware Detection and Prevention. IEEE Trans. Dependable Secur. Comput. 2018, 15, 83–97. [Google Scholar] [CrossRef] [Green Version]
- Mehtab, A.; Shahid, W.B.; Yaqoob, T.; Abbas, H.; Afzal, H.; Saqib, M.N. AdDroid: Rule-Based Machine Learning Framework for Android Malware Analysis. Mob. Netw. Appl. 2019, 24, 1–13. [Google Scholar] [CrossRef]
- Hou, S.; Saas, A.; Chen, L.; Ye, Y. Deep4MalDroid: A Deep Learning Framework for Android Malware Detection Based on Linux Kernel System Call Graphs. In Proceedings of the IEEE/WIC/ACM International Conference on Web Intelligence Workshops (WIW), Omaha, NE, USA, 13–16 October 2016; pp. 104–111. [Google Scholar]
- Ali, F.; Badrul, A.N.; Rosli, S. Evaluation of Network Traffic Analysis Using Fuzzy C-Means Clustering Algorithm in Mobile Malware Detection. Adv. Sci. Lett. 2018, 24, 929–932. [Google Scholar]
- Mohammed, K.; Suleiman, Y.; Sakir, S. DL-Droid: Deep learning based android malware detection using real devices. Comput. Secur. 2020, 89, 101663. [Google Scholar]
- Su, X.; Chuah, M.; Tan, G. Smartphone Dual Defense Protection Framework: Detecting malicious applications in Android Markets. In Proceedings of the 2012 8th International Conference on Mobile Ad-hoc and Sensor Networks, Chengdu, China, 14–16 December 2012; pp. 153–160. [Google Scholar]
- Yu, L.; Pan, Z.L.; Liu, J.J.; Shen, Y. Android Malware Detection Technology Based on Improved Bayesian Classification. In Proceedings of the 2013 Third International Conference on Instrumentation, Measurement, Computer, Communication and Control, Shenyang, China, 21–23 September 2013; pp. 1338–1341. [Google Scholar]
- Wang, C.Z.; Liang, G.; Yang, J.; Chen, W. The Method of Malware Detection based on Information Gain Characteristics Optimization Select. Netw. Comput. Secur. 2013, 4, 13–17. [Google Scholar]
- Zhao, K.; Zhang, D.F.; Su, X.; Li, W.J. Fest: A Feature Extraction and Selection Tool for Android Malware Detection. In Proceedings of the 20th IEEE Symposium on Computers and Communication, Larnaca, Cyprus, 6–9 July 2015; pp. 714–720. [Google Scholar]
- Yang, H.; Zhang, Y.; Hu, Y.; Liu, Q. Android malware detection method based on permission sequential pattern mining algorithm. J. Commun. 2013, 34, 106–115. [Google Scholar]
- Heermann, P.D.; Khazenie, N. Classification of multispectral remote sensing data using a back-propagation neural network. IEEE Trans. Geosci. Remote Sens. 1992, 30, 81–88. [Google Scholar] [CrossRef]
- Srivastava, N.; Hinton, G.; Krizhevsky, A. Dropout: A simple way to prevent neural networks from overfitting. J. Mach. Learn. Res. 2014, 15, 1929–1958. [Google Scholar]
- Liang, W.; Huang, W.; Long, J.; Zhang, K.; Li, K.; Zhang, D. Deep Reinforcement Learning for Resource Protection and Real-time Detection in IoT Environment. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Lipowski, A.; Lipowska, D. Roulette-wheel selection via stochastic acceptance. Phys. A Stat. Mech. Appl. 2012, 391, 2193–2196. [Google Scholar] [CrossRef] [Green Version]
- Liang, W.; Fan, Y.; Li, K.; Zhang, D.; Gaudiot, J. Secure Data Storage and Recovery in Industrial Blockchain Network Environments. IEEE Trans. Ind. Inform. 2020. [Google Scholar] [CrossRef]
- Liang, W.; Tang, M.; Long, J.; Peng, X.; Xu, J.; Li, K.C. A Secure FaBric Blockchain based Data Transmission Technique for Industrial IoT. IEEE Trans. Ind. Inform 2019, 15, 3582–3592. [Google Scholar] [CrossRef]











| Dimension Category | Behavioral Characteristic | Instances |
|---|---|---|
| Configuration dimension | Requested permission | ACCESS_GPS, WAKE_LOCK |
| App component | com.google.ssearch, com.eguan.state, com.google.update | |
| Intent | PHONE_STATE, MAIN, SIG_STR | |
| Hardware | CAMERA, NPC, AUDIO | |
| code dimension | API call | util.log.w, Dialog.show, Uri.prase |
| Protected API | getDeviceId, sendSMS, getWififiState | |
| Used permission | INTERNET, SEND_SMS, READ_CONTACT | |
| code pattern | MessageDigest, loadLibrary, pathClassLoader | |
| String | map.google.com, www.umeng.com, media. admob.com | |
| certification dimension | certification information | 2b7172a335 b66873dc793af3fe5c3fc6d8…. 5fb16d12bc8a36b9071907bc6e042840c2… |
| Payload information | .MF,.RSA,.jpg | |
| Network dimension | Quantitative | Number of bytes, number of packets |
| Time | Flow duration | |
| Semantic | Length of URI, length of the page | |
| System call dimension | System call | Chmod, fork, kill |
| Behavioral Characteristic Category | Characteristic Name | Characteristic Description |
|---|---|---|
| Network traffic | Number of packets | Number of packets transmitted between app and server |
| Number of bytes | Number of bytes transmitted between app and server | |
| Number of received packets | Number of packets received by the app | |
| Average bytes of received packets | Average bytes of packets received by the app | |
| Average size of packets | Average size of packets transmitted between app and server | |
| In/out ratio | Ration of traffic size between sent and received of app | |
| Flow duration | TCP session length | |
| Number of bytes per second | Number of bytes transmitted between app and server per second | |
| Length of URI per GET/POST request | The number of resources requested by app | |
| Length of page per GET/POST request | The length of paths visited by the app to obtain the resources | |
| Length of parameter per GET/POST request | The length of parameter contained in each request | |
| System call | sys_chmod, sys_chown, sys_mount, sys_access, sys_open, sys_clone, sys_getpriority, sys_mmap, sys_read, sys_exit, sys_kill, sys_brk, sys_execve, sys_kill, sys_times and sys_nice | Number of functions listed in left row was called by app during running time |
| Behavioral Characteristics | Accuracy | Precision | Recall | F-Measure |
|---|---|---|---|---|
| Network | 0.929 | 0.929 | 0.929 | 0.929 |
| System call | 0.907 | 0.907 | 0.907 | 0.907 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Su, X.; Xiao, L.; Li, W.; Liu, X.; Li, K.-C.; Liang, W. DroidPortrait: Android Malware Portrait Construction Based on Multidimensional Behavior Analysis. Appl. Sci. 2020, 10, 3978. https://doi.org/10.3390/app10113978
Su X, Xiao L, Li W, Liu X, Li K-C, Liang W. DroidPortrait: Android Malware Portrait Construction Based on Multidimensional Behavior Analysis. Applied Sciences. 2020; 10(11):3978. https://doi.org/10.3390/app10113978
Chicago/Turabian StyleSu, Xin, Lijun Xiao, Wenjia Li, Xuchong Liu, Kuan-Ching Li, and Wei Liang. 2020. "DroidPortrait: Android Malware Portrait Construction Based on Multidimensional Behavior Analysis" Applied Sciences 10, no. 11: 3978. https://doi.org/10.3390/app10113978
APA StyleSu, X., Xiao, L., Li, W., Liu, X., Li, K.-C., & Liang, W. (2020). DroidPortrait: Android Malware Portrait Construction Based on Multidimensional Behavior Analysis. Applied Sciences, 10(11), 3978. https://doi.org/10.3390/app10113978







