Chaos Based Cryptographic Pseudo-Random Number Generator Template with Dynamic State Change †
Abstract
:Featured Application
Abstract
1. Introduction
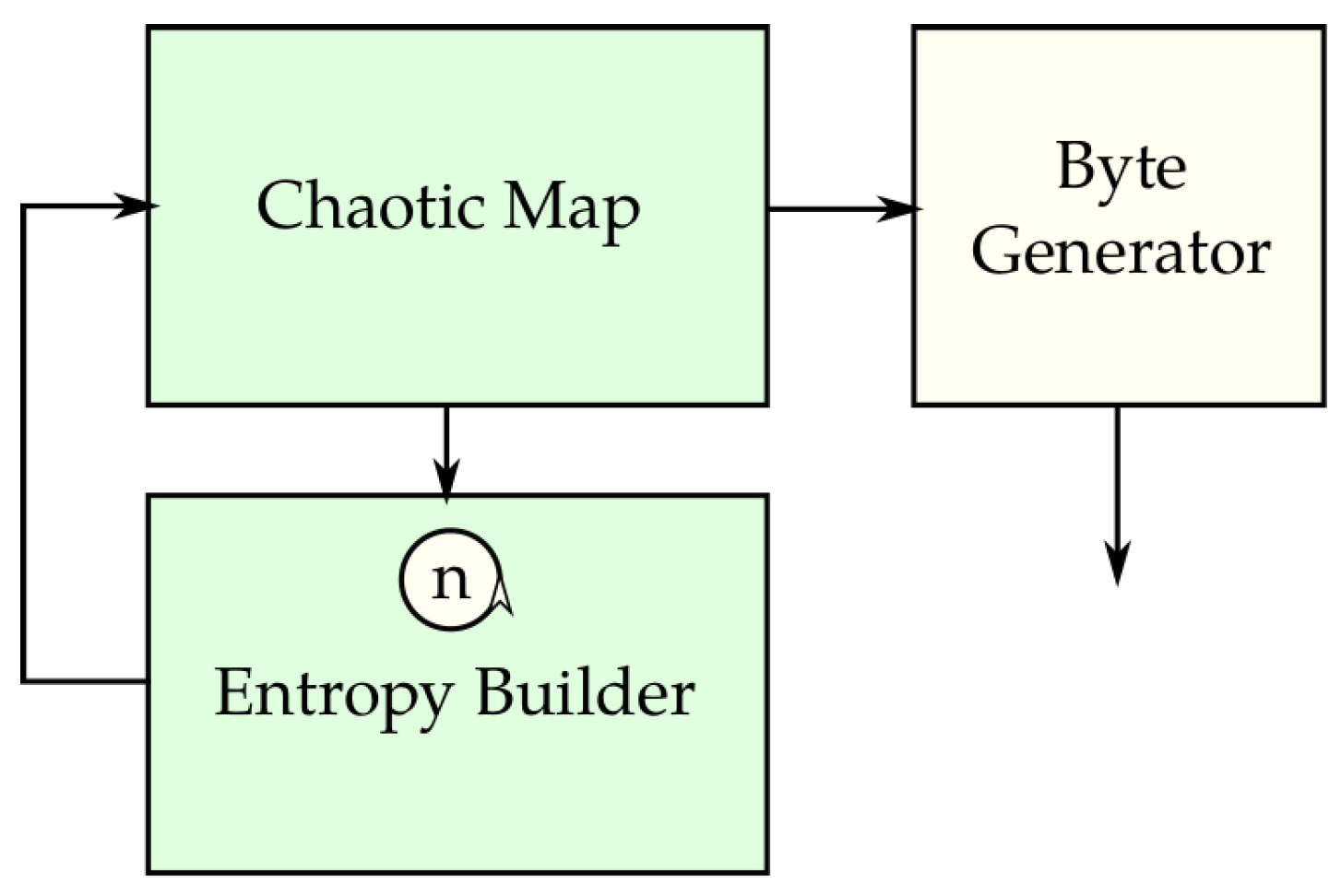
2. New Generator Design
3. Generator Implementation and Testing
3.1. Testing Setup
- generator—an application that takes as arguments a byte count, the name of the map, the entropy builder, the number of iterations for time spacing and the initial state values and parameters and generates a text file with the specified number of bytes, one per line, in binary format;
- test_suite—an application that takes as arguments the name of the map, the entropy builder, the number of iterations for time spacing and the initial state values and parameters and runs the TestU01 and NIST test batteries, outputting the results in a corresponding file, and appending a summary to the results.csv file;
- throughput_test—an application that takes as arguments a byte count, the name of the map, the entropy builder, the number of iterations for time spacing and the initial state values and parameters and computes the throughput of the specified generator in MB/s;
- codec—an application that takes as arguments the name of the input PNG file, the name of the output PNG file, the name of the map, the entropy builder, the number of iterations for time spacing and the initial state values and parameters and encrypts (or decrypts, as the stream cipher is symmetric) the input image, writing the results in the output file.
- Mersenne Twister—a non-cryptographically secure pRNG, described in [37] and implemented in the GCC C++ standard library;
- ChaCha—a cryptographically secure pRNG, from the stream cipher implementation in [38];
- Adaptive Chirikov Map pRNG—another chaos-based pRNG proposed in [9] which uses two adaptive Chirikov maps and a comparison procedure to generate random bits.
3.2. Randomness Test Results
3.3. Throughput Test Results
4. One-Time Pad Stream Cipher Application
4.1. Application Design
4.2. Results Analysis
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| API | Application Programming Interface |
| AVX | Advanced Vector Extension |
| CPU | Central Processing Unit |
| CSPRNG | Cryptographically Secure Pseudo-Random Number Generator |
| DDR4 | Double Data Rate (Synchronous Dynamic Random-Access Memory), version 4 |
| GCC | GNU Compiler Collection |
| GNU | GNU’s Not Unix! |
| NIST | National Institute of Standards and Technology |
| PNG | Portable Network Graphics |
| pRNG | Pseudo-Random Number Generator |
| RGB | Red Green Blue |
| SIMD | Single Instruction Multiple Data |
| SODIMM | Small-Outline Dual Inline Memory Module |
| TSP | Telecommunications and Signal Processing Conference |
References
- Tutueva, A.V.; Butusov, D.N.; Pesterev, D.O.; Belkin, D.A.; Ryzhov, N.G. Novel normalization technique for chaotic Pseudo-random number generators based on semi-implicit ODE solvers. In Proceedings of the 2017 International Conference Quality Management, Transport and Information Security, Information Technologies, St. Petersburg, Russia, 24–30 September 2017; pp. 292–295. [Google Scholar] [CrossRef]
- Wang, L.; Cheng, H. Pseudo-Random Number Generator Based on Logistic Chaotic System. Entropy 2019, 21, 960. [Google Scholar] [CrossRef] [Green Version]
- Nardo, L.G.; Nepomuceno, E.G.; Arias-Garcia, J.; Butusov, D.N. Image encryption using finite-precision error. Chaos Solitons Fractals 2019, 123, 69–78. [Google Scholar] [CrossRef]
- Garcia-Bosque, M.; Pérez-Resa, A.; Sánchez-Azqueta, C.; Celma, S. A new randomness-enhancement method for chaos-based cryptosystem. In Proceedings of the 2018 IEEE 9th Latin American Symposium on Circuits & Systems, Puerto Vallarta, Mexico, 25–28 February 2018. [Google Scholar] [CrossRef]
- Min, L.; Hu, K.; Zhang, L.; Zhang, Y. Study on pseudorandomness of some pseudorandom number generators with application. In Proceedings of the 2013 Ninth International Conference on Computational Intelligence and Security, Leshan, China, 14–15 December 2013; pp. 569–574. [Google Scholar] [CrossRef]
- Patidar, V.; Sud, K.K.; Pareek, N.K. A Pseudo Random Bit Generator Based on Chaotic Logistic Map and its Statistical Testing. Informatica 2009, 33, 441–452. [Google Scholar]
- Hamdi, M.N.M.; Rhouma, R.; Belghith, S. A Very Efficient Pseudo-Random Number Generator Based On Chaotic Maps and S-Box Tables. World Acad. Sci. Eng. Technol. Int. J. Electr. Comm. Eng. 2015, 9, 481–485. [Google Scholar] [CrossRef]
- Cai, B.; Wang, G.; Yuan, F. Pseudo random sequence generation from a new chaotic system. In Proceedings of the 2015 IEEE 16th International Conference on Communication Technology (ICCT), Hangzhou, China, 18–20 October 2015; pp. 863–867. [Google Scholar] [CrossRef]
- Tutueva, A.; Pesterev, D.; Karimov, A.; Butusov, D.; Ostrovskii, V. Adaptive Chirikov Map for Pseudo-random Number Generation in Chaos-based Stream Encryption. In Proceedings of the 25th Conference of FRUCT Association, Helsinki, Finland, 5–8 November 2019; Available online: https://fruct.org/publications/fruct25/files/Tut.pdf (accessed on 16 December 2019).
- Nepomuceno, E.G.; Nardo, L.G.; Arias-Garcia, J.; Butusov, D.N.; Tutueva, A. Image encryption based on the pseudo-orbits from 1D chaotic map. Chaos Interdiscip. J. Nonlinear Sci. 2019, 29, 061101. [Google Scholar] [CrossRef] [PubMed]
- Machicao, J.; Bruno, O.M. Improving the pseudo-randomness properties of chaotic maps using deep-zoom. Chaos 2017, 27, 053116. [Google Scholar] [CrossRef] [PubMed]
- Bhattacharjee, K.; Maity, K.; Das, S. A Search for Good Pseudo-random Number Generators: Survey and Empirical Studies. arXiv 2018, arXiv:1811.04035. [Google Scholar]
- Hellekalek, P. Good random number generators are (not so) easy to find. Math. Comput. Simul. 1998, 46, 485–505. [Google Scholar] [CrossRef]
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E.; Leigh, S.; Levenson, M.; Vangel, M.; Banks, D.; Heckert, A.; et al. A statistical test suite for random and pseudorandom number generators for cryptographic applications. Revised: April 2010 by Lawrence E. Bassham, National Institute of Standards and Technology Special Publication 800-22 revision 1a, Natl. Inst. Stand. Technol. Spec. Publ. 800-22rev1a, 131 Pages (April 2010). Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-22r1a.pdf (accessed on 27 December 2019).
- Katz, J.; Lindell, Y. Theoretical Constructions of Pseudorandom Objects. In Introduction to Modern Cryptography; Chapman and Hall/CRC: New York, NY, USA, 2007; pp. 181–226. ISBN 10: 1584885513, 13: 978-1584885511. Available online: https://repo.zenk-security.com/Cryptographie%20.%20Algorithmes%20.%20Steganographie/Introduction%20to%20Modern%20Cryptography.pdf (accessed on 27 December 2019).
- Hobincu, R.; Datcu, O. A novel Chaos Based PRNG Targeting Secret Communication. In Proceedings of the 12 the IEEE International Conference on Communications (COMM), Bucharest, Romania, 14–16 June 2018; pp. 459–462. [Google Scholar] [CrossRef]
- Shukla, M.K.; Sharma, B.B. Investigation of chaos in fractional order generalized hyperchaotic Hénon map. AEU Int. J. Electr. Commun. 2017, 78, 265–273. [Google Scholar] [CrossRef]
- Richter, H. The Generalized Hénon maps: Examples for higher-dimensional chaos. IJBC Int. J. Bifurc. Chaos 2002, 1371–1384. [Google Scholar] [CrossRef]
- Sava, D.; Vlad, A.; Tataru, R. A new type of keystream generator based on chaotic maps: Illustration on a Hénon generalized map. In Proceedings of the 10th International Conference on Communications (COMM), Bucharest, Romania, 29–31 May 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Hodea, O.; Vlad, A.; Datcu, O. Evaluating the sampling distance to achieve independently and identically distributed data from generalized Hénon map. In Proceedings of the ISSCS 2011—International Symposium on Signals, Circuits and Systems, Lasi, Romania, 30 June–1 July 2011. [Google Scholar] [CrossRef]
- Stanciu, M.O.; Datcu, O. Atmel AVR microcontroller implementation of a new enciphering algorithm based on a chaotic generalized Hénon map. In Proceedings of the 9th International Conference on Communications (COMM), Bucharest, Romania, 21–23 June 2012; pp. 319–322. [Google Scholar] [CrossRef]
- Datcu, O.; Barbot, J.-P.; Vlad, A. New enciphering algorithm based on chaotic generalized Hénon map. In Proceedings of the Chaos Theory: Modeling, Simulation and Applications, Selected Papers from the 3rd Chaotic Modeling and Simulation International Conference (Chaos2010), Chania, Crete, Greece, 1–4 June 2010; pp. 143–150. [Google Scholar] [CrossRef] [Green Version]
- Hobincu, R.; Datcu, O. NIST tests versus bifurcation diagrams and Lyapunov exponents when evaluating chaos-based pRNGs. In Proceedings of the International Conference on Time Series and Forecasting Proceedings of Papers, Granada, Spain, 25–27 September 2018; ISBN 978-84-17293-57-4. [Google Scholar]
- Hobincu, R.; Datcu, O. FPGA Implementation of a Chaos Based PRNG Targetting Secret Communication. In Proceedings of the 13th Symposium on Electronics and Telecommunications (ISETC), Timişoara, Romania, 8–9 November 2018. [Google Scholar] [CrossRef]
- Zheng, J.; Wang, Z.; Li, Y.; Wang, J. Bifurcations and chaos in a three-dimensional generalized Hénon map. In Advances in Difference Equations; Springer: New York, NY, USA, 2018; ISSN 1687-1847. [Google Scholar] [CrossRef] [Green Version]
- Butusov, D.N.; Ostrovskii, V.Y.; Tutueva, A.V.; Savelev, A.O. Comparing the algorithms of multiparametric bifurcation analysis. In Proceedings of the 2017 XX IEEE International Conference on Soft Computing and Measurements (SCM), St. Petersburg, Russia, 24–26 May 2017; pp. 194–198. [Google Scholar] [CrossRef]
- Wolf, A.; Swift, J.B.; Swinney, H.L.; Vastano, J.A. Determining Lyapunov exponents from a time series. Phys. D Nonlinear Phenomena 1985, 16, 285–317. [Google Scholar] [CrossRef] [Green Version]
- Carbonneau, M.A.; Cheplygina, V.; Granger, E.; Gagnon, G. Multiple instance learning: A survey of problem characteristics and applications. Pattern Recog. 2018, 77, 329–353. [Google Scholar] [CrossRef]
- Boeing, G. Visual Analysis of Nonlinear Dynamical Systems: Chaos, Fractals, Self-Similarity and the Limits of Prediction. Systems 2016, 4, 37. [Google Scholar] [CrossRef] [Green Version]
- Aguirre, J.; Viana, R.L.; Sanjuán, M.A. Fractal structures in nonlinear dynamics. Rev. Mod. Phys. 2009, 81, 333–386. [Google Scholar] [CrossRef]
- Petrică, L. FPGA optimized cellular automaton random number generator. J. Parallel Distrib. Comput. 2018, 111, 251–259. [Google Scholar] [CrossRef]
- Hobincu, R.; Datcu, O.; Macovei, C. Entropy global control for a chaos based pRNG. In Proceedings of the 42nd International Conference on Telecommunications and Signal Processing (TSP), Budapest, Hungary, 3–5 July 2019; pp. 432–435. [Google Scholar] [CrossRef]
- Datcu, O.; Lupu, A.-E.; Blaj, T.; Hobincu, R. NIST Tests, Lyapunov Exponents and Bifurcation Diagrams when Evaluating Chaos-based PRNGs. In Special Issue of Proceedings of the Romanian Academy, Proceedings of Romanian Cryptology Days, 5th ed.; Publishing House of the Romanian Academy: Bucharest, Romania, 2020; forthcoming. [Google Scholar]
- Jiang, H.; Liu, Y.; Wei, Z.; Zhang, L. A New Class of Three-Dimensional Maps with Hidden Chaotic Dynamics. IJBC Int. J. Bifurc. Chaos 2016, 26. [Google Scholar] [CrossRef]
- Marsaglia, G. The Marsaglia Random Number CDROM: Including the Diehard Battery of Tests of Randomness; Florida State University: Tallahassee, FL, USA, 1995. [Google Scholar]
- Suciu, A.; Toma, R.A.; Marton, K. Parallel implementation of the TestU01 statistical test suite. In Proceedings of the 2012 IEEE 8th International Conference on Intelligent Computer Communication and Processing, Cluj-Napoca, Romania, 30 August–1 September 2012; pp. 317–322. [Google Scholar] [CrossRef]
- Matsumoto, M.; Nishimura, T. Mersenne twister: A 623-dimensionally equidistributed uniform pseudo-random number generator. ACM Trans. Model. Comput. Simul. (TOMACS) 1998, 8, 3–30. [Google Scholar] [CrossRef] [Green Version]
- Bernstein, D.J. ChaCha, A Variant of Salsa20. Workshop Record of SASC 2008: The State of the Art of Stream Ciphers. Available online: https://cr.yp.to/chacha/chacha-20080120.pdf (accessed on 27 December 2019).
- Yavuz, E.; Yazıcı, R.; Kasapbaş, M.C.; Yamaç, E. A chaos-based image encryption algorithm with simple logical functions. Comput. Electr. Eng. 2016, 54, 471–483. [Google Scholar] [CrossRef]
- Miller, D.A.; Grassi, G. A discrete generalized hyperchaotic Hénon map circuit. In Proceedings of the 44th IEEE 2001 Midwest Symposium on Circuits and Systems, MWSCAS 2001 (Cat. No.01CH37257), Dayton, OH, USA, 14–17 August 2001; Volume 1, pp. 328–331. [Google Scholar] [CrossRef]
- Ilyas, A.; Vlad, A.; Luca, A. Statistical analysis of pseudorandom binary sequences generated by using tent map. UPB Sci. Bull. 2013, 75. Available online: https://www.scientificbulletin.upb.ro/rev_docs_arhiva/fullf87_565183.pdf (accessed on 3 January 2020).
- Vlad, A.; Luca, A.; Hodea, O.; Tataru, R. Generating Chaotic Secure Sequences Using Tent Map and a Running-Key Approach. Available online: https://pdfs.semanticscholar.org/b832/46775feb22dd2b4bf137ec5c9b8860b0dbe5.pdf (accessed on 27 December 2019).












| Position | a | b |
|---|---|---|
| top left | 1.066073952077004 | −0.122171054133312 |
| bottom left | 1.822849696327467 | −0.210260146847663 |
| top right | 1.422086796614167 | −0.292608160780357 |
| bottom right | 1.566451149781642 | 0.210678068488918 |
| ID | Maps | Cases |
|---|---|---|
| 1 | ||
| 2 | ||
| 3 | ||
| 4 | ||
| 5 | ||
| 6 | ||
| 7 | ||
| 8 | ||
| 9 | ||
| 10 | ||
| 11 | ||
| 12 | ||
| 13 |
| Entropy | Interval | Failed | Failed |
|---|---|---|---|
| Builder | TestU01 | NIST | |
| – | – | 15 | 162 |
| 1 | 0 | 0 | |
| 1 | 15 | 162 | |
| 1 | 0 | 0 | |
| 100 | 12 | 2 | |
| 45 | 2 | 0 | |
| 35 | 0 | 0 | |
| 25 | 0 | 0 | |
| 15 | 0 | 3 | |
| 100 | 15 | 10 | |
| 45 | 3 | 1 | |
| 35 | 0 | 0 | |
| 25 | 1 | 0 | |
| 15 | 0 | 0 | |
| 100 | 14 | 4 | |
| 45 | 2 | 0 | |
| 35 | 1 | 0 | |
| 25 | 0 | 0 | |
| 15 | 0 | 0 |
| Entropy | Entropy | ||
|---|---|---|---|
| original image | 7.17 | original image | 0.19 |
| encrypted; | 7.20 | encrypted; | 1.19 |
| encrypted; | 7.99 | encrypted; | 7.99 |
| encrypted with | 7.99 | encrypted with | 7.99 |
| encrypted with | 7.94 | encrypted with | 5.55 |
| encrypted using and | 7.99 | encrypted with and | 7.99 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Datcu, O.; Macovei, C.; Hobincu, R. Chaos Based Cryptographic Pseudo-Random Number Generator Template with Dynamic State Change. Appl. Sci. 2020, 10, 451. https://doi.org/10.3390/app10020451
Datcu O, Macovei C, Hobincu R. Chaos Based Cryptographic Pseudo-Random Number Generator Template with Dynamic State Change. Applied Sciences. 2020; 10(2):451. https://doi.org/10.3390/app10020451
Chicago/Turabian StyleDatcu, Octaviana, Corina Macovei, and Radu Hobincu. 2020. "Chaos Based Cryptographic Pseudo-Random Number Generator Template with Dynamic State Change" Applied Sciences 10, no. 2: 451. https://doi.org/10.3390/app10020451






