Deadlocks Detection in Multithreaded Applications Based on Source Code Analysis
Abstract
:1. Introduction
1.1. Resource Conflict and Deadlock Definition
1.2. The Structure of the Article
2. Thread Synchronisation Mechanisms
2.1. Locks
- PTHREAD_MUTEX_NORMAL (PMN)
- PTHREAD_MUTEX_ERRORCHECK (PME)
- PTHREAD_MUTEX_RECURSIVE (PMR)
- PTHREAD_MUTEX_DEFAULT (PMD)
2.2. Condition Variables
3. Multithreaded Application Source Code Model
- P is the application index,
- }, () is a set of threads of application, where is the main thread, ,
- , () is sequence of sets that are subsets of set containing threads working in the same time interval in application, with , i ,
- is a set of shared resources of application, and the next elements are sets of names of variables related to a single resource,
- , () is a set of all application operations which are atomic operations at a certain level of abstraction, i.e., dividing them into smaller operations is impossible. An operation should be understood as an instruction or function defined in a programming language. Index i indicates the number of the thread in which the operation is performed, and index j is the ordinal number of operations working within the same thread,
- – a set of locks available in the program, defined as a pair (mutex variable name , a type of lock ), where type is understood as one from the set value (PMN, PME, PMR, PMD),
- i , () – set of edges including:
- (a)
- transition edges – specifying the order in which the operation is performed. These edges are pairs , where the elements describe two successive operations ,
- (b)
- usage edges – indicating resources that change during the operation. These edges are pairs , in which one element is operation , and the other is resource ,
- (c)
- dependency edges – indicating operations depending on the current value of one of the resources. These edges are pairs , in which one element is the resource , and the other is the operation ,
- (d)
- locking edges – indicating the operation applying the selected lock. These edges are pair , in which one element is the lock, and the other is the locking operation,
- (e)
- unlocking edge – indicating the operation releasing the selected lock. These edges are pairs , in which one element is the unlocking operation, and the other is the released lock.
- should be understood as a set of vertices consisting of P, application operations, P application locks, and that application’s shared resources.is understood here as a subgraph of graph, which is built as a result of removing:
- all vertices of and their associated edges excluding thread operation,
- all vertices of set and the associated edges, excluding vertex,
- all vertices of set and their associated edges, excluding the edges between thread operations and the resources they use,
- transition edges for vertex, when there is an unlocking edge for this vertex .
4. Problem Definition
5. Deadlock
- Mutual exclusion: At least one resource must be non-shareable; that is, only one process can use this resource at a time. If another process requests access to the resource, it must be delayed until the resource is released.
- Hold and wait: There must be a process that has been allocated at least one resource, and that is awaiting the allocation of an additional resource that is being held by another process.
- No preemption: Resources are not subject to preemption, which means that a resource can only be released on the initiative of the holding process after the process has ended.
- Circular wait: There must be set of waiting processes, such that is waiting for the resource held by . is waiting for the resource held by is waiting for the resource held by , and waiting for the resource held by process.
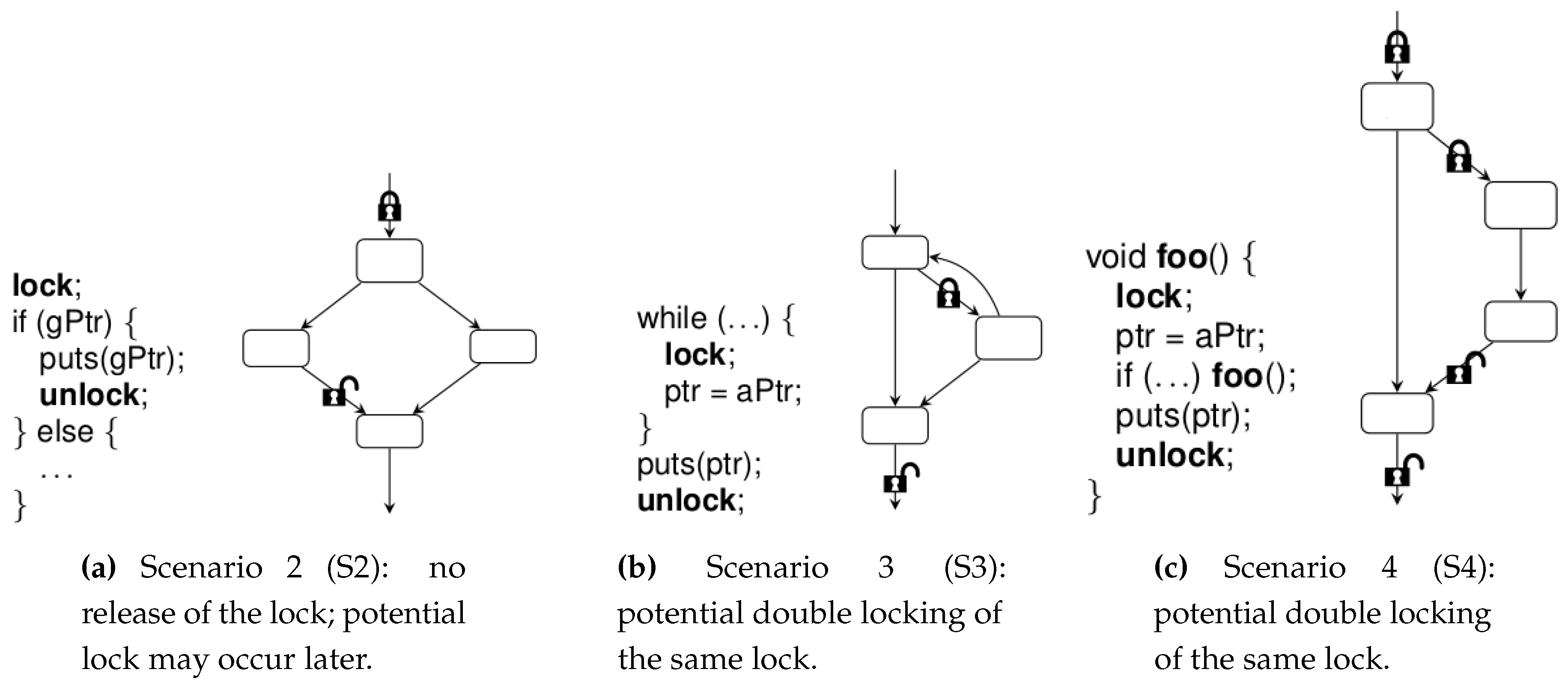
- mutually exclusive lock pairs (application implementing S1 scenario, let it be called DL0),
- missing the unlocking operation, e.g., as a result of a control instruction (application implementing the S2 scenario, let it be called DL1),
- retrying the lock as a result of:
- (a)
- loop operation (application implementing the S3 scenario, let it be called DL2),
- (b)
- recursive function call (application implementing the S4 scenario, let it be called DL3).
5.1. Gadara Project
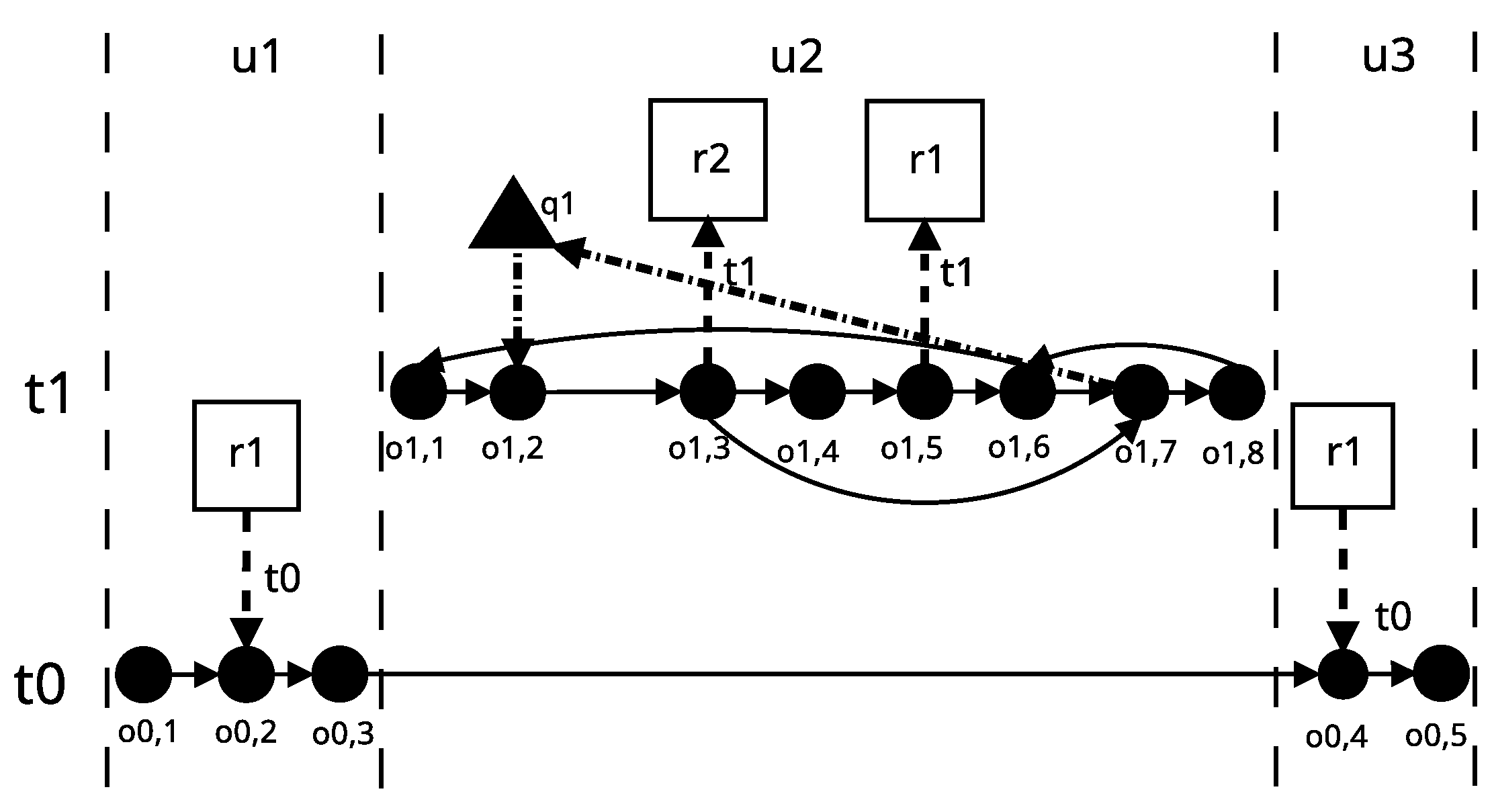
5.2. DL0 Application Model
| T = (t, t, t), | (o, o), (r, o), (o, o), | |
| U = ({t}, {t, t}, {t}), | (q, o), (o, o), (q, o), | |
| R = {{counter}}, | (o, o), (o, r), (o, o), | |
| O = {o, o, o, o, o, o, | (o, q), (o, ), (o, q), | |
| o, o, o, o, o, o, o, o, | (o, o), (q, o), (o, o), | |
| o, o}, | (q, o), (o, o), (o, r), | |
| Q = {(m, PMD), (n, PMD)}, | (o, o), (o, q), (o, o), | |
| F = {(o, o), (r, o), | (o, q), (o, o)}. |
DL1 Application Model

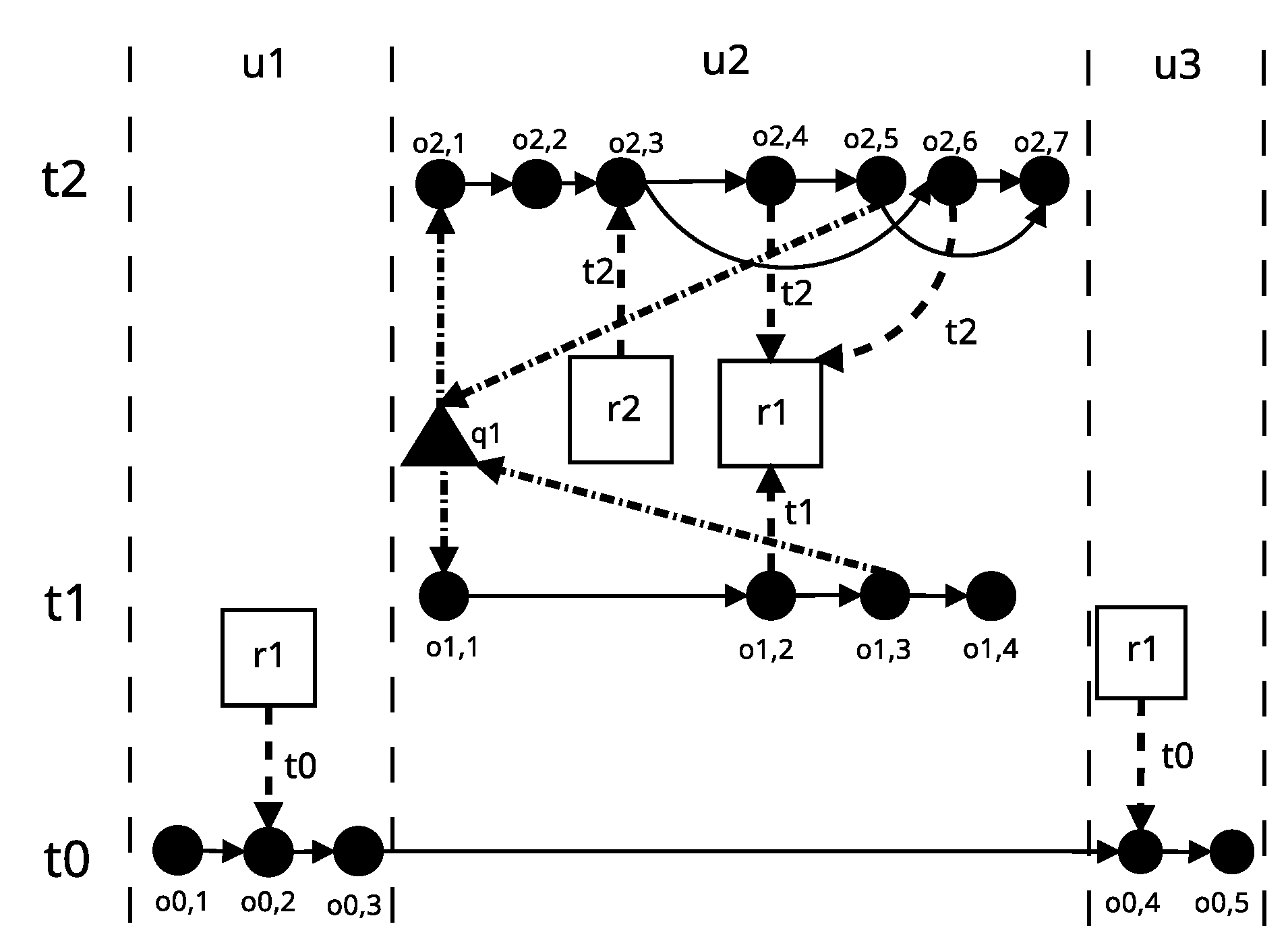
5.3. DL2 Application Model

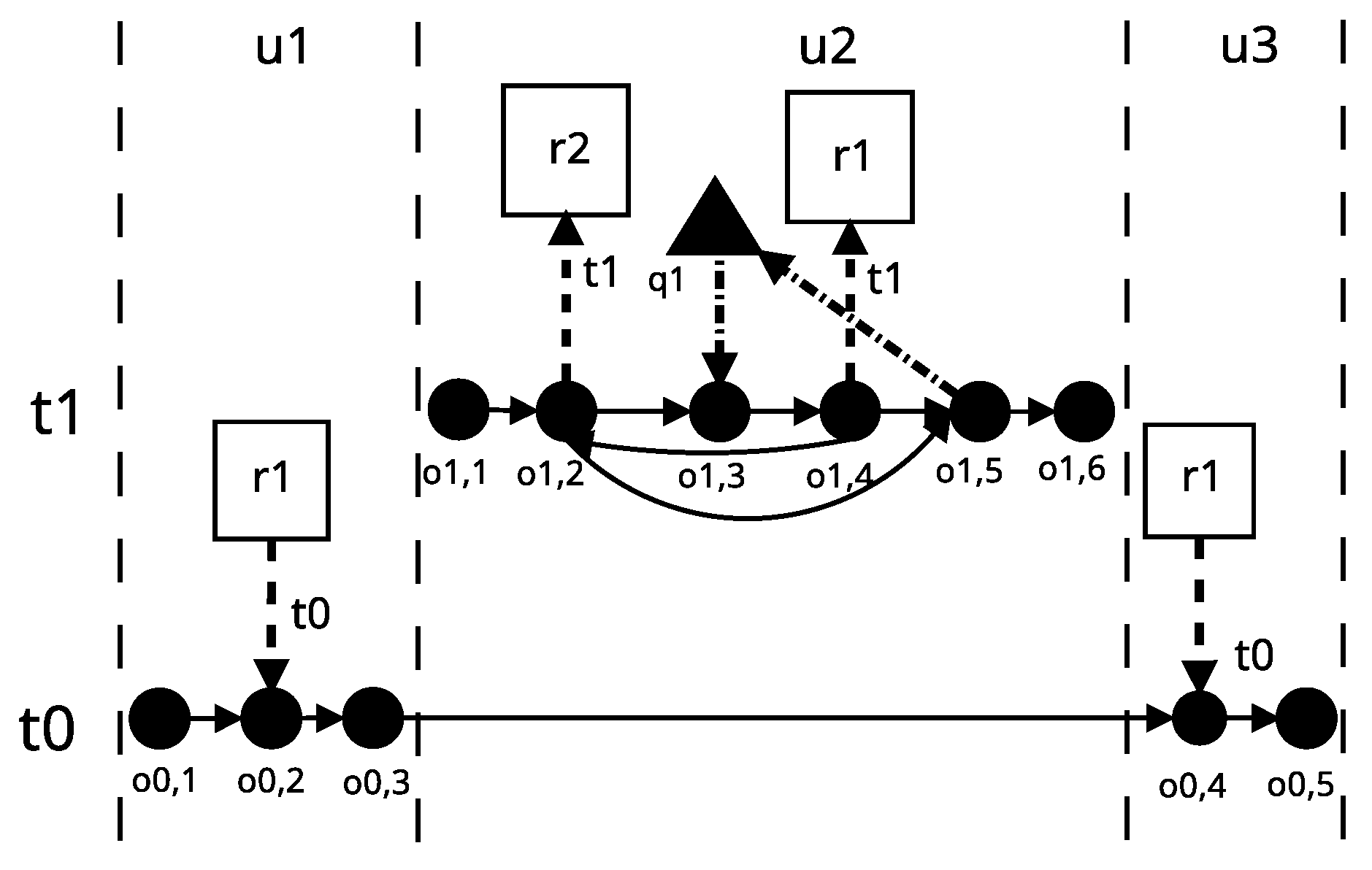
5.4. DL3 Application Model
6. Sufficient Condition
- there is a pair of threads setting the same pair of locks, with the order in which these locks are set is different in both threads (Lemma 1),
- in the operation graph involving thread, there exists a path that starts with and is not a cycle (Lemma 2),
- the thread calls the recursive function, in which the PMR type lock represented by the trapezium is not used (Lemma 3).
7. Using the Source Code Model of the Multithreaded Application in Practice
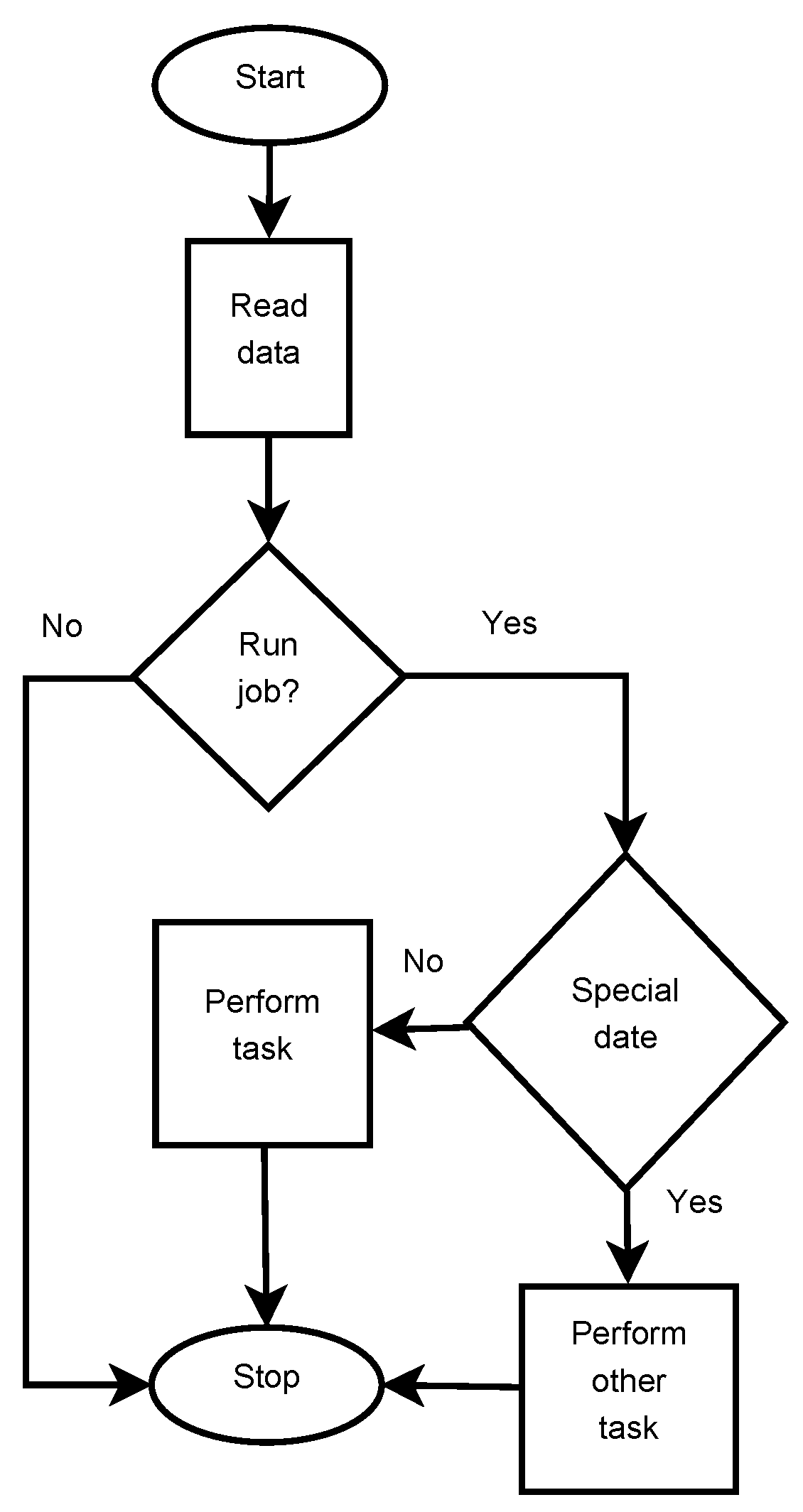
7.1. Leading Example
- minute,
- hour,
- day of the month,
- month,
- day of week,
- user,
- job.
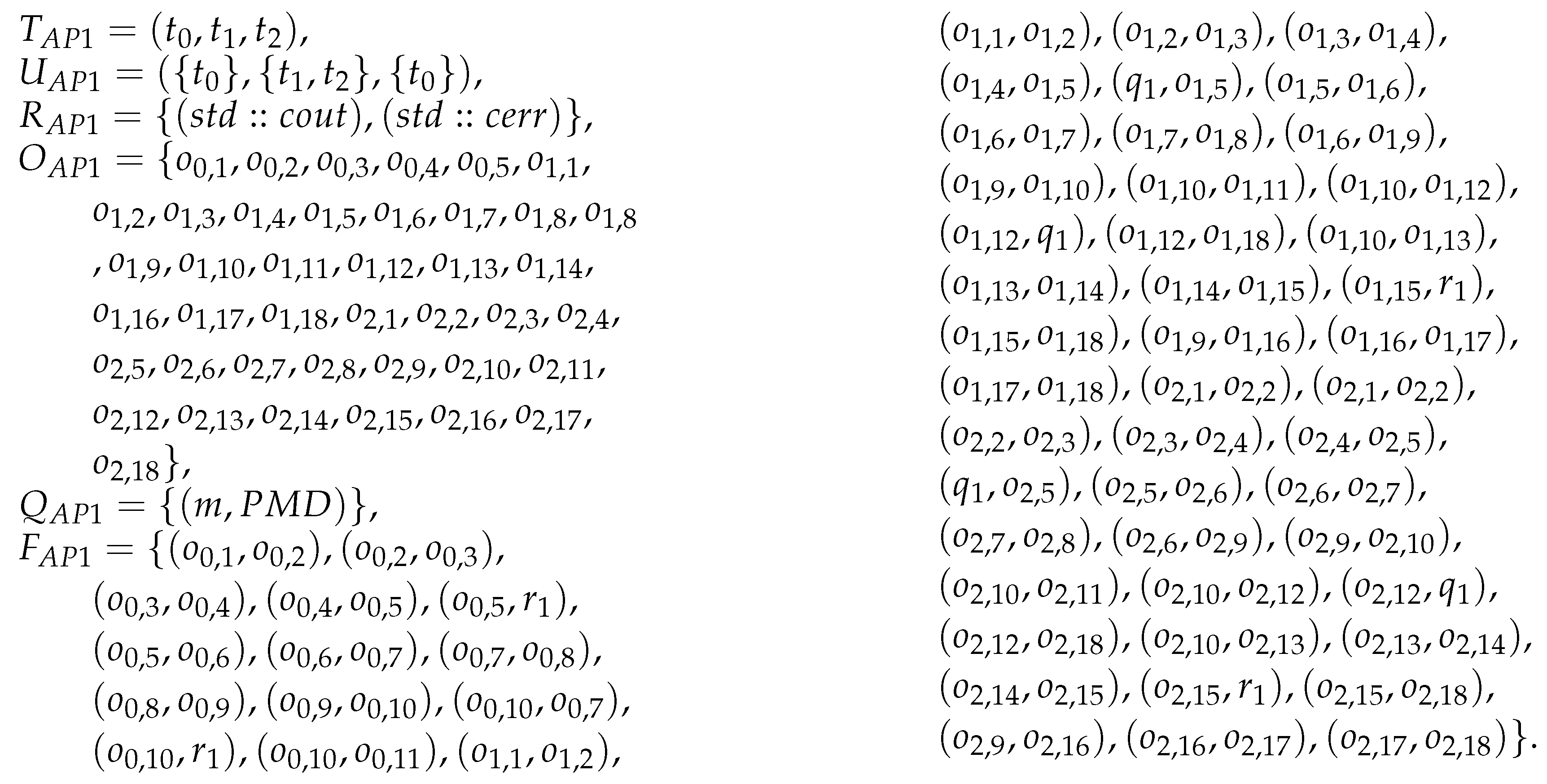
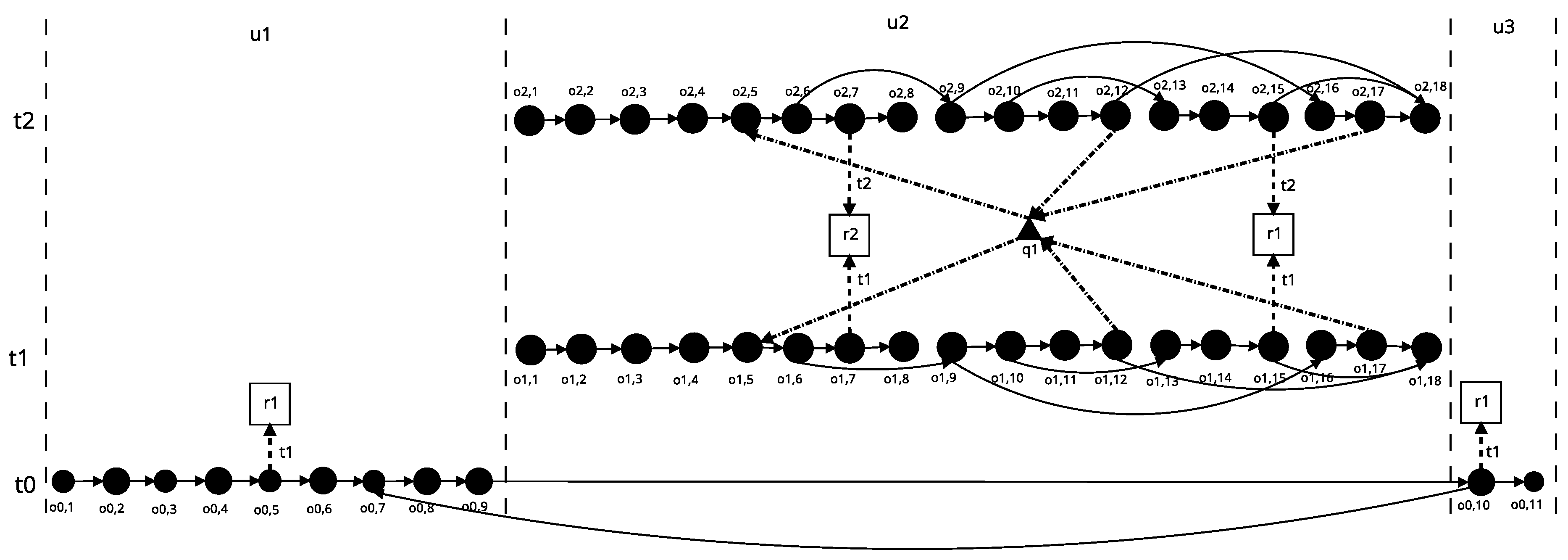
7.2. Deadlock Detection Using Petri Nets
7.3. Deadlock Phenomenon Detection Using a Multi-Thread Application Source Code Model
7.4. Implementation of the Method
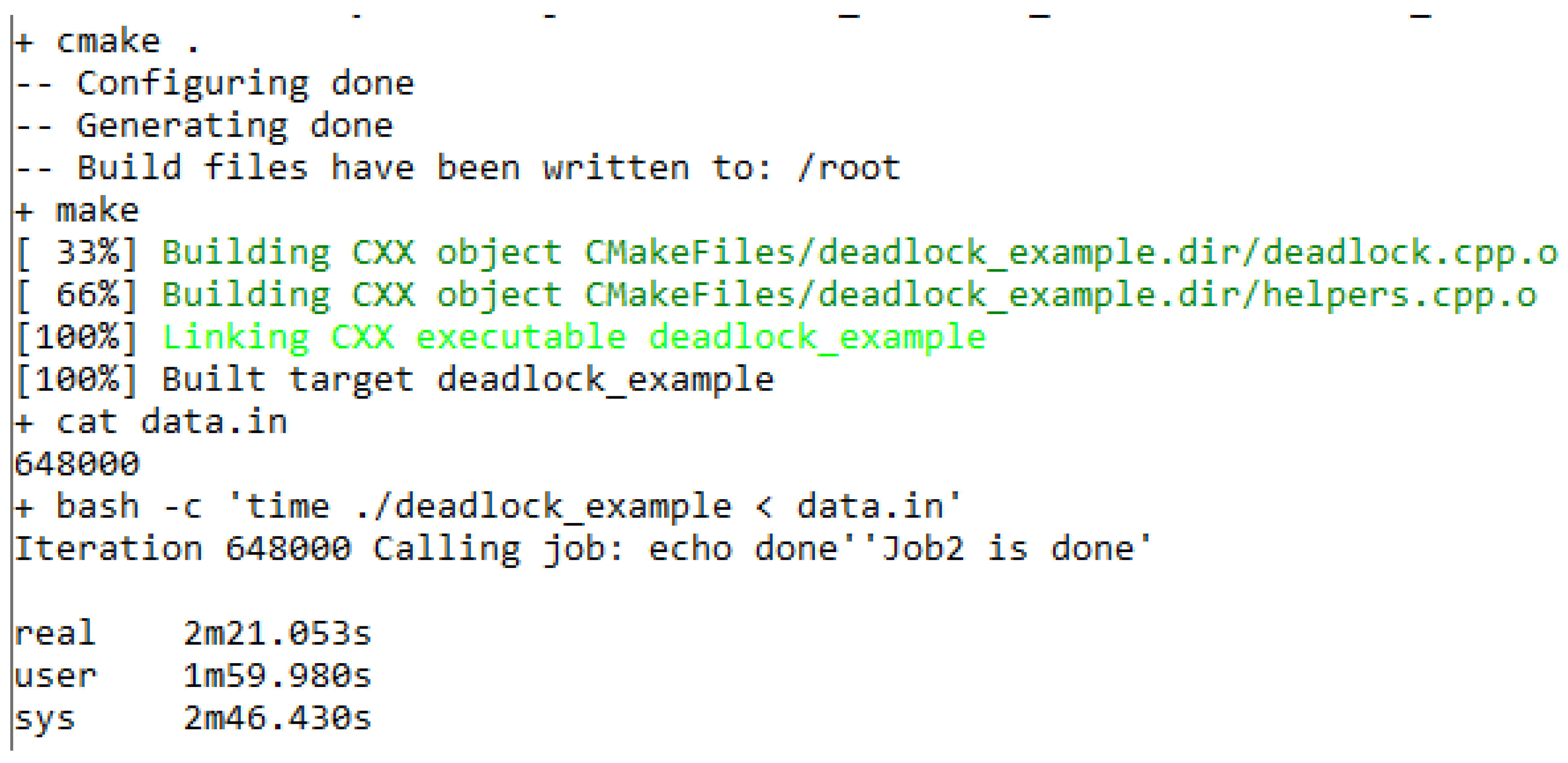
7.5. Experiment Assumptions
- Processor: AMD Ryzen 5 1500X, 3.5 GHz,
- RAM: Corsair Vengeance LPX, DDR3, 32GB, 3000MHz, CL15,
- Hard Drive: SSD Intenso 128GB SATA3, read speed 520 MB/s.
7.6. Results
8. Competitive Method
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| AST | Abstract Syntax Trees |
| DD | Deadlock Detector |
| DL0 | Example application implementing S1 scenario |
| DL1 | Example application implementing S2 scenario |
| DL2 | Example application implementing S3 scenario |
| DL3 | Example application implementing S4 scenario |
| PMD | Pthreads Mutex Default |
| PME | Pthreads Mutex Error Check |
| PMN | Pthreads Mutex Normal |
| PMR | Pthreads Mutex Recursive |
| PN | Petri Net |
| RCS | Resource Conflict Detector |
| S1 | Deadlock scenario caused by mutually exclusive locking pairs |
| S2 | Deadlock scenario with missing unlock |
| S3 | Deadlock scenario with double locking the same lock |
| S4 | Deadlock scenario with double locking during calling recursive functions |
References
- Savage, S.; Burrows, M.; Nelson, G.; Sobalvarro, P.; Anderson, T. Eraser: A dynamic data race detector for multithreaded programs. ACM Trans. Comput. Syst. 1997, 15, 391–411. [Google Scholar] [CrossRef] [Green Version]
- Silva, B.D.; Happi, A.W.; Braeken, A.; Touhafi, A. Evaluation of Classical Machine Learning Techniques towards Urban Sound Recognitionon Embedded Systems. Appl. Sci. 2019, 9, 3885. [Google Scholar] [CrossRef] [Green Version]
- Silberschatz, A.; Galvin, P.B.; Gagne, G. Operating System Concepts; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2013. [Google Scholar]
- Mitchell, M.; Oldham, J.; Samuel, A. Advanced Linux Programming; New Riders Publishing: Indianapolis, IN, USA, 2001. [Google Scholar]
- Lefebvre, D. Dynamical Scheduling and Robust Control in Uncertain Environments with Petri Nets for DESs. Processes 2017, 5, 54. [Google Scholar] [CrossRef]
- Lautenbach, K.; Schmid, H.A. Use of Petri Nets for Proving Correctness of Concurrent Process Systems. In Proceedings of the IFIP Congress, Stockholm, Sweden, 5–10 August 1974; pp. 187–191. [Google Scholar]
- Wang, Y.; Liao, H.; Reveliotis, S.; Kelly, T.; Mahlke, S.; Lafortune, S. Gadara nets: Modeling and analyzing lock allocation for deadlock avoidance in multithreaded software. In Proceedings of the 48h IEEE Conference on Decision and Control (CDC) Held Jointly with 2009 28th Chinese Control Conference, Shanghai, China, 15–18 December 2009; pp. 4971–4976. [Google Scholar]
- Lin, Y.; Kulkarni, S.S. Automatic repair for multi-threaded programs with deadlock/livelock using maximum satisfiability. In Proceedings of the 2014 International Symposium on Software Testing and Analysis, San Jose, CA, USA, 21–26 July 2014; pp. 237–247. [Google Scholar]
- Smith, E.K.; Barr, E.T.; Le Goues, C.; Brun, Y. Is the cure worse than the disease? overfitting in automated program repair. In Proceedings of the 2015 10th Joint Meeting on Foundations of Software Engineering, Bergamo, Italy, 30 August–4 September 2015; pp. 532–543. [Google Scholar]
- Chandy, K.M.; Misra, J.; Haas, L.M. Distributed deadlock detection. ACM Trans. Comput. Syst. 1983, 1, 144–156. [Google Scholar] [CrossRef]
- Ho, A.; Smith, S.; Hand, S. On Deadlock, Livelock, and Forward Progress; Technical Report; University of Cambridge, Computer Laboratory: Cambridge, UK, 2005. [Google Scholar]
- Singhal, M. Deadlock detection in distributed systems. Computer 1989, 22, 37–48. [Google Scholar] [CrossRef]
- Guo, J.; Seely, S. Monitor preprocessor for Pthreads. In Proceedings of the 34th Annual Frontiers in Education, Savannah, GA, USA, 22–23 October 2004. [Google Scholar]
- Giebas, D.; Wojszczyk, R. Multithreaded Application Model. In Proceedings of the 16th International Conference: Distributed Computing and Artificial Intelligence, Avila, Spain, 26–28 June 2019; Springer: Berlin/Heidelberg, Germany, 2019; Volume 1004, pp. 93–103. [Google Scholar]
- Shih, C.S.; Stankovic, J.A. Survey of Deadlock Detection in Distributed Concurrent Programming Environments and Its Application to Real-Time Systems and Ada; Technical Report UM-CS-1990-069; University of Massachusetts: Fall River, MA, USA, 1990. [Google Scholar]
- Jin, G.; Song, L.; Zhang, W.; Lu, S.; Liblit, B. Automated atomicity-violation fixing. In ACM Sigplan Notices; ACM: New York, NY, USA, 2011; Volume 46, pp. 389–400. [Google Scholar]
- Liu, P.; Zhang, C. Axis: Automatically fixing atomicity violations through solving control constraints. In Proceedings of the 2012 34th International Conference on Software Engineering (ICSE), Zurich, Switzerland, 2–9 June 2012; pp. 299–309. [Google Scholar]
- Park, S.; Lu, S.; Zhou, Y. CTrigger: Exposing atomicity violation bugs from their hiding places. In ACM SIGARCH Computer Architecture News; ACM: New York, NY, USA, 2009; Volume 37, pp. 25–36. [Google Scholar]
- Wang, Y.; Kelly, T.; Kudlur, M.; Lafortune, S.; Mahlke, S.A. Gadara: Dynamic Deadlock Avoidance for Multithreaded Programs. In Proceedings of the 8th USENIX Symposium on Operating Systems Design and Implementation, San Diego, CA, USA, 8–10 December 2008; Volume 8, pp. 281–294. [Google Scholar]
- Lafortune, S.; Wang, Y.; Reveliotis, S. Eliminating concurrency bugs in multithreaded software: An approach based on control of petri nets. In Proceedings of the International Conference on Applications and Theory of Petri Nets and Concurrency, Milan, Italy, 24–28 June 2013; pp. 21–28. [Google Scholar]
- Sen, K. Race directed random testing of concurrent programs. ACM Sigplan Not. 2008, 43, 11–21. [Google Scholar] [CrossRef]
- Cai, Y.; Wu, S.; Chan, W. ConLock: A constraint-based approach to dynamic checking on deadlocks in multithreaded programs. In Proceedings of the 36th International Conference on Software Engineering, Hyderabad, India, 31 May–7 June 2014; pp. 491–502. [Google Scholar]
- Kavi, K.; Moshtaghi, A.; Chen, D.J. Modeling multithreaded applications using Petri nets. Int. J. Parallel Program. 2002, 30, 353–371. [Google Scholar] [CrossRef]
- Ullman, J.D.; Aho, A.V. Principles of Compiler Design; Addison Wesley: Reading, MA, USA, 1977. [Google Scholar]
- Durve, N. Automatically Improving the Design of Code. Master’s Thesis, Department of Computing Imperial College, London, UK, 2007. [Google Scholar]
- Kroening, D.; Poetzl, D.; Schrammel, P.; Wachter, B. Sound static deadlock analysis for C/Pthreads. In Proceedings of the 31st IEEE/ACM International Conference on Automated Software Engineering, Singapore, 3–7 September 2016; pp. 379–390. [Google Scholar]
- Li, J.; Liu, X.; Jiang, L.; Liu, B.; Yang, Z.; Hu, X. An Intelligent Deadlock Locating Scheme for Multithreaded Programs. In Proceedings of the 2019 3rd International Conference on Intelligent Systems, Metaheuristics & Swarm Intelligence, Male, Maldives, 23–24 March 2019; pp. 14–18. [Google Scholar]
- Tongping, L.; Zhou, J.; Silvestro, S.; Liu, H. Defeating Deadlocks in Production Software. U.S. Patent App. 16/159,234, 18 April 2019. [Google Scholar]




© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Giebas, D.; Wojszczyk, R. Deadlocks Detection in Multithreaded Applications Based on Source Code Analysis. Appl. Sci. 2020, 10, 532. https://doi.org/10.3390/app10020532
Giebas D, Wojszczyk R. Deadlocks Detection in Multithreaded Applications Based on Source Code Analysis. Applied Sciences. 2020; 10(2):532. https://doi.org/10.3390/app10020532
Chicago/Turabian StyleGiebas, Damian, and Rafał Wojszczyk. 2020. "Deadlocks Detection in Multithreaded Applications Based on Source Code Analysis" Applied Sciences 10, no. 2: 532. https://doi.org/10.3390/app10020532




