Enhancing the Security of Pattern Unlock with Surface EMG-Based Biometrics
Abstract
:1. Introduction
2. Related Work
2.1. Improving the Security of Pattern Unlock
2.2. Biometrics-Based Mobile User Authentication
3. Background
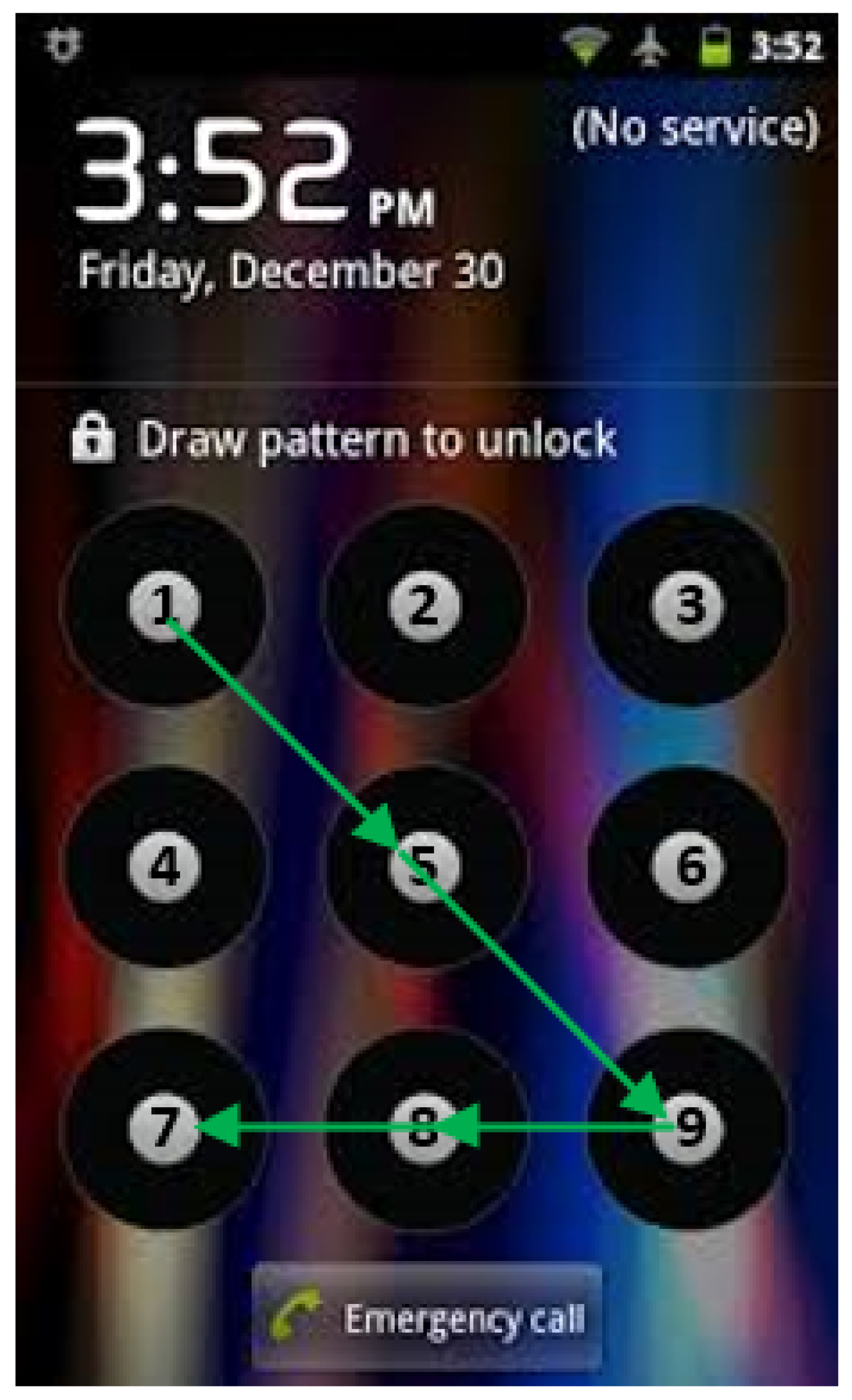
3.1. Pattern Unlock
3.2. EMG Signals
4. Materials and Methods
4.1. Overview of Proposed Scheme
4.2. Subjects
4.3. Experimental Protocol
4.3.1. sEMG Signal Acquisition and Pre-Processing
4.3.2. Experiment Procedure
4.4. sEMG Feature Extraction
4.4.1. Mean Absolute Value (MAV)
4.4.2. Variance (VAR)
4.4.3. High-Order Temporal Moment (TM)
4.4.4. Mean Square Root (MSR)
4.4.5. Root Mean Square (RMS)
4.4.6. Log Detector (LD)
4.4.7. Waveform Length (WL)
4.4.8. Difference Absolute Standard Deviation Value (DASDV)
4.4.9. Number of Zero Crossing (NZC)
4.5. One-Class Classification Algorithms
4.5.1. OCSVM
4.5.2. LOF
5. Performance Evaluation and Results
5.1. Dataset
5.2. Performance Metrics
5.3. Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Mobile vs. Desktop Usage. Available online: https://www.broadbandsearch.net/blog/mobile-desktop-internet-usage-statistics (accessed on 6 December 2019).
- Bruggen, D.V. Studying the Impact of Security Awareness Efforts on User Behavior. Ph.D. Thesis, University of Notre Dame, Notre Dame, IN, USA, 2014. [Google Scholar]
- Von Zezschwitz, E.; Dunphy, P.; de Luca, A. Patterns in the wild: A field study of the usability of pattern and pin-based authentication on mobile devices. In Proceedings of the 15th International Conference on Human-Computer Interaction with Mobile Devices and Services, Munich, Germany, 27–30 August 2013; pp. 261–270. [Google Scholar]
- Cha, S.; Kwag, S.; Kim, H.; Huh, J. Boosting the guessing attack performance on android lock patterns with smudge attacks. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security, Abu Dhabi, UAE, 2–6 April 2017; pp. 313–326. [Google Scholar]
- Aviv, A.J.; Wolf, F.; Kuber, R. Comparing video based shoulder surfing with live simulation. In Proceedings of the 34th Annual Computer Security Applications Conference (ACSAC’18), San Juan, PR, USA, 3–7 December 2018; pp. 452–466. [Google Scholar]
- Aviv, A.J.; Gibson, K.; Mossop, E.; Blaze, M.; Smith, J.M. Smudge attacks on smartphone touch screens. In Proceedings of the 4th USENIX Conference on Offensive Technologies (WOOT’10), Washington, DC, USA, 9 August 2010; pp. 1–7. [Google Scholar]
- Aviv, A.J.; Sapp, B.; Blaze, M.; Smith, J.M. Practicality of accelerometer side channels on smartphones. In Proceedings of the 28th Annual Computer Security Applications Conference (ACSAC’12), Orlando, FL, USA, 3–7 December 2012; pp. 41–50. [Google Scholar]
- Ye, G.; Tang, Z.; Fang, D.; Chen, X.; Kim, K.; Taylor, B.; Wang, Z. Cracking Android pattern lock in five attempts. In Proceedings of the 2017 Network and Distributed System Security Symposium (NDSS’17), San Diego, CA, USA, 26 February–1 March 2017. [Google Scholar]
- Kwon, T.; Na, S. TinyLock: Affordable defense against smudge attacks on smartphone pattern lock systems. Comput. Secur. 2014, 42, 137–150. [Google Scholar] [CrossRef]
- Schneegass, S.; Steimle, F.; Bulling, A.; Alt, F.; Schmidt, A. SmudgeSafe: Geometric image transformations for smudge resistant user authentication. In Proceedings of the 2014 ACM International Joint Conference on Pervasive and Ubiquitous Computing (UbiComp’14), Seattle, MA, USA, 13–17 September 2014; pp. 775–786. [Google Scholar]
- Von Zezschwitz, E.; Koslow, A.; de Luca, A.; Hussmann, H. Making graphic-based authentication secure against smudge attacks. In Proceedings of the 2013 International Conference on Intelligent User Interfaces (IUI’13), Santa Monica, CA, USA, 19–22 March 2013; pp. 277–286. [Google Scholar]
- Zheng, J.; Chigurupati, S.K. M-Pattern: A novel scheme for improving the security of Android pattern unlock against smudge attacks. ICT Express 2019, 5, 192–195. [Google Scholar] [CrossRef]
- Higashikawa, S.; Kosugi, T.; Kitajima, S.; Mambo, M. Shoulder-surfing resistant authentication using pass pattern of pattern lock. IEICE Trans. Inf. Syst. 2018, E101.D, 45–52. [Google Scholar] [CrossRef] [Green Version]
- Tupsamudre, H.; Banahatti, V.; Lodha, S.; Vyas, K. Pass-O: A proposal to improve the security of pattern unlock scheme. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security (ASIA CCS’17), Abu Dhabi, UAE, 2–6 April 2017; pp. 400–407. [Google Scholar]
- Chiang, H.; Chiasson, S. Improving user authentication on mobile devices: A touchscreen graphical password. In Proceedings of the 15th International Conference on Human-Computer Interaction with Mobile Devices and Services (MobileHCI’13), Munich, Germany, 27–30 August 2013; pp. 251–260. [Google Scholar]
- Sun, C.; Wang, Y.; Zheng, J. Dissecting pattern unlock: The effect of pattern strength meter on pattern selection. J. Inf. Secur. Appl. 2014, 19, 308–320. [Google Scholar] [CrossRef]
- Tupsamudre, H.; Vaddepalli, S.; Banahatti, V.; Lodha, S. TinPal: An enhanced interface for pattern locks. In Proceedings of the 2018 Workshop on Usable Security (USEC 2018), Cambridge, UK, 19–21 March 2018; pp. 1–11. [Google Scholar]
- Matsumoto, T.; Matsumoto, H.; Yamada, K.; Hoshino, S. Impact of artificial ‘gummy’ fingers on fingerprint systems. In Proceedings of the SPIE Optical Security and Counterfeit Deterrence Techniques IV, Berlin, Germany, 19 April 2002; Volume 4677, pp. 275–289. [Google Scholar]
- Lee, H.; Hwang, J.Y.; Kim, D.I.; Lee, S.; Lee, S.-H.; Shin, J.S. Understanding keystroke dynamics for smartphone users authentication and keystroke dynamics on smartphones built-in motion sensors. Secur. Commun. Netw. 2018, 2018, 2567463. [Google Scholar] [CrossRef]
- Lamiche, I.; Bin, G.; Jing, Y.; Yu, Z.; Hadid, A. A continuous smartphone authentication method based on gait patterns and keystroke dynamics. J. Ambient Intell. Humaniz. Comput. 2019, 10, 4417–4430. [Google Scholar] [CrossRef]
- Li, W.; Tan, J.; Meng, W.; Wang, Y.; Li, J. SwipeVLock: A supervised unlocking mechanism based on swipe behavior on smartphones. In Proceedings of the International Conference on Machine Learning for Cyber Security (ML4CS 2019), Xi’an, China, 19–21 September 2019; pp. 140–153. [Google Scholar]
- Huang, P.; Guo, L.; Li, M.; Fang, Y. Pratical privacy-preserving ECG-based authentication for IoT-based healthcare. IEEE Internet Things J. 2019, 6, 9200–9210. [Google Scholar] [CrossRef]
- Klonovs, J.; Petersen, C.K.; Olesen, H.; Hammershoj, A. ID proof on the go: Development of a mobile EEG-based biometric authentication system. IEEE Veh. Technol. Mag. 2013, 8, 81–89. [Google Scholar] [CrossRef]
- Kumar, P.; Saini, R.; Roy, P.P.; Dogra, P.D. A bio-signal based framework to secure mobile devices. J. Netw. Comput. Appl. 2017, 89, 62–71. [Google Scholar] [CrossRef]
- Yamaba, H.; Kurogi, K.; Kubota, S.; Katayama, T.; Park, M.; Okazaki, N. Evaluation of feature values of surface electromyograms for user authentication on mobile devices. Artif. Life Robot. 2017, 22, 108–112. [Google Scholar] [CrossRef]
- Yamaba, H.; Aburada, K.; Katayama, T.; Park, M.; Okazaki, N. Evaluation of user identification methods for realizing an authentication system using s-EMG. In Proceedings of the International Conference on Network-Based Information Systems (NBiS 2018), Bratislava, Slovakia, 10–12 September 2018; pp. 733–742. [Google Scholar]
- Tendons. Available online: http://www.assh.org/handcare/Anatomy/Tendons (accessed on 6 December 2019).
- Phinyomark, A.; Phukpattaranont, P.; Limsakul, C. Feature reduction and selection for EMG signal classification. Expert Syst. Appl. 2012, 39, 7420–7431. [Google Scholar] [CrossRef]
- Phinyomark, A.; Quaine, F.; Charnonnier, S.; Serviere, C.; Tarpin-Bernard, F.; Laurillau, Y. Feature extraction of the first difference of EMG time series for EMG pattern recognition. Comput. Methods Programs Biomed. 2014, 117, 247–256. [Google Scholar] [CrossRef] [PubMed]
- Yang, Z.; Chen, Y. Surface EMG-based sketching recognition using two analysis windows and gene expression programming. Front. Neurosci. 2016, 10, 445. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Samuel, O.W.; Zhou, H.; Li, X.; Wang, H.; Zhang, H.; Sangaiah, A.K.; Li, G. Pattern recognition of electromyography signals based on novel time domain features for amputees’ limb motion classification. Comput. Electr. Eng. 2018, 67, 646–655. [Google Scholar] [CrossRef]
- Qi, J.; Jiang, G.; Li, G.; Sun, Y.; Tao, B. Intelligent human-computer interaction based on surface EMG gesture recognition. IEEE Access 2019, 7, 61378–61387. [Google Scholar] [CrossRef]
- Hudgins, B.; Parker, P.; Scott, R.N. A new strategy for multifunction myoelectric control. IEEE Trans. Biomed. Eng. 1993, 40, 82–94. [Google Scholar] [CrossRef] [PubMed]
- Zardoshti-Kermani, M.; Wheeler, B.C.; Badie, K.; Hashemi, R.M. EMG feature evaluation for movement control of upper extremity prostheses. IEEE Trans. Rehabil. Eng. 1995, 3, 324–333. [Google Scholar] [CrossRef]
- Saridis, G.N.; Gootee, T.P. EMG pattern analysis and classification for a prosthetic arm. IEEE Trans. Biomed. Eng. 1982, 29, 403–412. [Google Scholar] [CrossRef] [PubMed]
- Kim, K.S.; Choi, H.H.; Moon, C.S.; Mun, C.W. Comparison of k-nearest neighbor, quadratic discriminant and linear discriminant analysis in classification of electromyogram signals based on the wrist-motion directions. Curr. Appl. Phys. 2011, 11, 740–745. [Google Scholar] [CrossRef]
- Scholkopf, B.; Williamson, R.C.; Smola, A.J.; Shawe-Taylort, J.; Platt, J. Support vector method for novelty detection. In Proceedings of the 12th International Conference on Neural Information Processing Systems, Denver, CO, USA, 29 November–4 December 1999; pp. 582–588. [Google Scholar]
- Scholkopf, B.; Smola, A.J.; Williamson, R.C.; Bartlett, P.L. New support vector algorithms. Neural Comput. 2000, 12, 1207–1245. [Google Scholar] [CrossRef] [PubMed]
- Breunig, M.M.; Kriegel, H.-P.; Ng, R.T.; Sander, J. LOF: Identifying density-based local outliers. In Proceedings of the 2000 ACM SIGMOD International Conference on Management of Data, Dallas, TX, USA, 16–18 May 2000; pp. 93–104. [Google Scholar]
- Chuang, J.; Nguyen, H.; Wang, C.; Johnson, B. I think, therefor i am: Usability and security of authentication using biometrics. In Proceedings of the International Conference on Financial Cryptography and Data Security, Okinawa, Japan, 1–5 April 2013; pp. 1–16. [Google Scholar]
- Scikit-Learn: Machine Learning in Python. Available online: https://scikit-learn.org/ (accessed on 6 December 2019).
- Vehicle Access Control Market by Biometric (Fingerprint, Face, Iris, Voice), Non-biometric (Stolen Vehicle Assist, Keyless, Immobilizer, Alarm, Steering Lock), Technology (Bluetooth, NFC, RFID, Wi-Fi), Vehicle Type, EV & Region—Global Forecast to 2027. Available online: https://www.marketsandmarkets.com/Market-Reports/vehicle-access-control-market-266613080.html (accessed on 6 December 2019).
- MyoWare Muscle Sensor. Available online: http://www.advancertechnologies.com/p/myoware.html (accessed on 6 December 2019).
- Myo Armband. Available online: https://newatlas.com/myo-gesture-control-armband-review/39103/ (accessed on 6 December 2019).






| OCSVM | LOF | |||
|---|---|---|---|---|
| Subject | HTER | HTER | ||
| 1 | 0.9760 ± 0.0054 | 0.1911 ± 0.0505 | 0.9755 ± 0.0060 | 0.1200 ± 0.0338 |
| 2 | 0.9746 ± 0.0066 | 0.2350 ± 0.0626 | 0.9882 ± 0.0045 | 0.1031 ± 0.0383 |
| 3 | 0.9786 ± 0.0075 | 0.1931 ± 0.0740 | 0.9812 ± 0.0070 | 0.1144 ± 0.0720 |
| 4 | 0.9786 ± 0.0042 | 0.1975 ± 0.0399 | 0.9789 ± 0.0067 | 0.1281 ± 0.0363 |
| 5 | 0.9764 ± 0.0071 | 0.1706 ± 0.0496 | 0.9751 ± 0.0072 | 0.1003 ± 0.0388 |
| 6 | 0.9602 ± 0.0104 | 0.2042 ± 0.0478 | 0.9617 ± 0.0109 | 0.1094 ± 0.0256 |
| 7 | 0.9831 ± 0.0064 | 0.1550 ± 0.0599 | 0.9912 ± 0.0046 | 0.0733 ± 0.0442 |
| 8 | 0.9759 ± 0.0052 | 0.2225 ± 0.0492 | 0.9920 ± 0.0049 | 0.0725 ± 0.0045 |
| 9 | 0.9812 ± 0.0058 | 0.1725 ± 0.0546 | 0.9920 ± 0.0047 | 0.0725 ± 0.0432 |
| 10 | 0.9807 ± 0.0054 | 0.1775 ± 0.0506 | 0.9844 ± 0.0033 | 0.0844 ± 0.0254 |
| OCSVM | LOF | |||
|---|---|---|---|---|
| Subject | HTER | HTER | ||
| 1 | 0.9780 ± 0.0051 | 0.2025 ± 0.0480 | 0.9892 ± 0.0047 | 0.0731 ± 0.0337 |
| 2 | 0.9386 ± 0.0085 | 0.1931 ± 0.0452 | 0.9402 ± 0.0162 | 0.1328 ± 0.0253 |
| 3 | 0.9779 ± 0.0058 | 0.1870 ± 0.0605 | 0.9789 ± 0.0047 | 0.1100 ± 0.0215 |
| 4 | 0.9762 ± 0.0068 | 0.2200 ± 0.0643 | 0.9885 ± 0.0050 | 0.0850 ± 0.0564 |
| 5 | 0.9804 ± 0.0044 | 0.1800 ± 0.0415 | 0.9898 ± 0.0027 | 0.0814 ± 0.0303 |
| 6 | 0.9717 ± 0.0058 | 0.2625 ± 0.0556 | 0.9901 ± 0.0054 | 0.0771 ± 0.0592 |
| 7 | 0.9767 ± 0.0053 | 0.2106 ± 0.0537 | 0.9763 ± 0.0111 | 0.1192 ± 0.0405 |
| 8 | 0.9748 ± 0.0045 | 0.2325 ± 0.0426 | 0.9920 ± 0.0044 | 0.0725 ± 0.0399 |
| 9 | 0.9523 ± 0.0899 | 0.2500 ± 0.0402 | 0.9465 ± 0.0083 | 0.1272 ± 0.0442 |
| 10 | 0.9745 ± 0.0057 | 0.2008 ± 0.0581 | 0.9733 ± 0.0118 | 0.1042 ± 0.0412 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Q.; Dong, P.; Zheng, J. Enhancing the Security of Pattern Unlock with Surface EMG-Based Biometrics. Appl. Sci. 2020, 10, 541. https://doi.org/10.3390/app10020541
Li Q, Dong P, Zheng J. Enhancing the Security of Pattern Unlock with Surface EMG-Based Biometrics. Applied Sciences. 2020; 10(2):541. https://doi.org/10.3390/app10020541
Chicago/Turabian StyleLi, Qingqing, Penghui Dong, and Jun Zheng. 2020. "Enhancing the Security of Pattern Unlock with Surface EMG-Based Biometrics" Applied Sciences 10, no. 2: 541. https://doi.org/10.3390/app10020541
APA StyleLi, Q., Dong, P., & Zheng, J. (2020). Enhancing the Security of Pattern Unlock with Surface EMG-Based Biometrics. Applied Sciences, 10(2), 541. https://doi.org/10.3390/app10020541





