Secure Delivery Scheme of Common Data Model for Decentralized Cloud Platforms
Abstract
Featured Application
Abstract
1. Introduction
- The SC-CDM is the first approach of demultiplexing with the data confidentiality proof of CDM based on asymmetric key cryptography. We analyze and prove the security of SC-CDM.
- Compared to previous solutions, we adopt a byte-level challenge with encryption to ensure efficiency while handling a large CDM.
- The comparison results show that our scheme has the higher performance compared to other schemes.
- By using X.509 asymmetric key for DID (Decentralized Identifier)-based identity management (signing and using the DID operating, autonomous generation, updating, and removal functions), the risk of personal information exposure would be reduced.
2. Materials and Methods
2.1. Materials
2.1.1. Distributed Ledger
2.1.2. Decentralized Identifier (DID)
2.1.3. Blockchain
2.1.4. Common Data Model (CDM)
2.1.5. Blockchain Application in CDM Environment
2.2. Methods for Adapting to CDM Model
2.2.1. The Baseline CDM Model
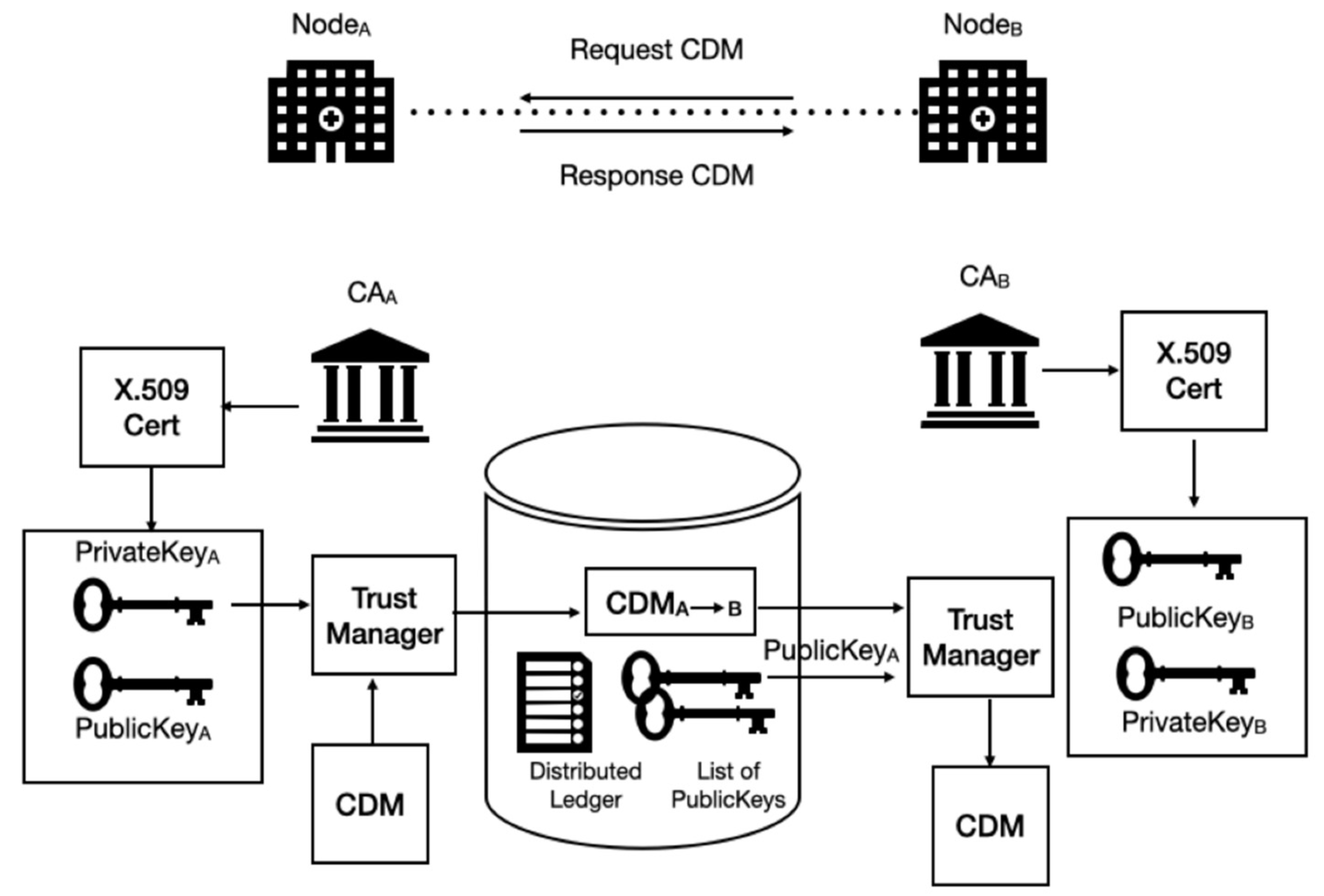
2.2.2. The Secure Operation Scheme for the SC-CDM
- Cryptography can be used for protecting information, using a hash value to maintain management of large-capacity CDMs.
- DID is applied to solve the risk of central ID management caused by SPF and privacy leakage problems.
- Distributed ledger is used to provide data integrity and share information through CDM signature.
2.2.3. Applied Security and Privacy Method in SC-CDM
2.2.4. CDM Separate Block Encryption/Decryption Algorithm
- Gen generates a random key (32 byte) and an IV (16 byte);
- Enc/Dec is based on Advanced Encryption Standard (AES) and Cipher Block Chaining with IV;
- D: CDM derived by EMR.
- IV;
- Shared key (generated by symmetric key protocol);
- Two hash values generated by SHA-256.
3. Results
3.1. Experimental Setup
3.2. Construction of Storage Structure for SC-CDM
3.3. X.509 Based Key Management
-----BEGIN PUBLIC KEY-----MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsZhhPfQsP3MTrCnn7wsJwLX/VWxg1/Qf4Usv/uIfJGta2hcg2hg+TzSqv3bHjFssKBCSp7QnxC1dITt1QbAKoifDT0dEOoOyYZ7o1xTZBfJUZBa6w7vAnMmOnKPdf/QXgOZjHXr+c4mPjOB5OBVAwIaiO3ASSACkdeGZ2lZxrZe3tXYeX3Ng8a/nJ8OSdxWuoMKTQ3roooi8I4iC2SXU5sgb9TxAF/nnm8q4vEiMPBi8d7FqsVPfh4tA2PoESqO/4g4c295Awfm2FT7ut8Z5n1YyS3PZP7AcGnInWcZ6K5NAsUzsA60+WAgXIuUb4lzuCX9ZhhHM+/utu50in0ZdxQIDAQAB-----END PUBLIC KEY-----
3.4. Our Encryption and Decryption Scheme for Delivering in SC-CDM
3.4.1. Integrity Auditing with the Digital Signature Based on Asymmetric Key Cryptography
3.4.2. Secure Proof of Ownership over Secure Transaction
3.4.3. Privacy Leakage Resilience of SC-CDM
3.5. Analysis of SC-CDM
3.6. Performance Evaluation
4. Discussion
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Shivade, C.; Raghavan, P.; Fosler-Lussier, E.; Embi, P.J.; Elhadad, N.; Johnson, S.B.; Lai, A.M. A review of approaches to identifying patient phenotype cohorts using electronic health records. J. Am. Med. Inform. Assoc. 2014, 21, 221–230. [Google Scholar] [CrossRef] [PubMed]
- You, S.C.; Lee, S.; Cho, S.-Y.; Park, H.; Jung, S.; Cho, J.; Yoon, D.; Park, R.W. Conversion of National Health Insurance Service-National Sample Cohort (NHIS-NSC) Database into Observational Medical Outcomes Partnership-Common Data Model (OMOP-CDM). Stud. Health Technol. Inf. 2017, 245, 467–470. [Google Scholar]
- Muralidharan, S.; Ko, H. An InterPlanetary File System (IPFS) based IoT framework. In Proceedings of the 2019 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 11–13 January 2019; pp. 1–2. [Google Scholar]
- Pãnescu, A.-T.; Manta, V. Smart Contracts for Research Data Rights Management over the Ethereum Blockchain Network. Sci. Technol. Libr. 2018, 37, 235–245. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; ACM: New York, NY, USA, 2018; p. 30. [Google Scholar]
- Dagher, G.G.; Mohler, J.; Milojkovic, M.; Marella, P.B. Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology. Sustain. Cities Soc. 2018, 39, 283–297. [Google Scholar] [CrossRef]
- Silberschatz, A.; Korth, H.F.; Sudarshan, S. Database System Concepts; McGraw-Hill: New York, NY, USA, 1997. [Google Scholar]
- Xiong, L.; Li, F.-G.; Zeng, S.-K.; Peng, T.; Liu, Z.-C. A Blockchain-Based Privacy-Awareness Authentication Scheme with Efficient Revocation for Multi-Server Architectures. IEEE Access 2019, 7, 125840–125853. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. May 2009. Available online: http://www.bitcoin.org/bitcoin.pdf (accessed on 27 August 2020).
- Shrestha, A.K.; Vassileva, J. Blockchain-Based Research Data Sharing Framework for Incentivizing the Data Owners. In Proceedings of the International Conference on Blockchain, Seattle, WA, USA, 25–30 June 2018; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany; Volume 10974, pp. 259–266. [Google Scholar]
- Allen, C. The Path to Self-Sovereign Identity. 2016. Available online: http://www.lifewithalacrity.com/2016/04/the-path-to-self-soverereign-identity.html (accessed on 27 August 2020).
- UK Government. Distributed Ledger Technology: Beyond Block Chain (PDF) (Report); UK Government, Office for Science: London, UK, January 2016.
- Augot, D.; Chabanne, H.; Chenevier, T.; George, W.; Lambert, L. A User-Centric System for Verified Identities on the Bitcoin Blockchain. In Data Privacy Management, Cryptocurrencies and Blockchain Technology; Springer: Oslo, Norway, 2017; Volume 10436, pp. 390–407. [Google Scholar]
- Halpin, H. NEXTLEAP: Decentralizing Identity with Privacy for Secure Messaging. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August–1 September 2017; pp. 1–10. [Google Scholar]
- David, B.; Gaži, P.; Kiayias, A.; Russell, A. Ouroboros Praos: An Adaptively-Secure, Semi-synchronous Proof-of-Stake Blockchain. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Dan Panorama Tel-Aviv, Tel Aviv, Israel, 29 April–3 May 2018; pp. 66–98. [Google Scholar]
- Hardjono, T.; Pentland, A. Verifiable Anonymous Identities and Access Control in Permissioned Blockchains. arXiv 2019, arXiv:1903.04584. [Google Scholar]
- Pass, R.; Shi, E. Thunderella: Blockchains with Optimistic Instant Confirmation. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Dan Panorama Tel-Aviv, Tel Aviv, Israel, 29 April–3 May 2018; Springer: Cham, Switzerland, 2018; pp. 3–33. [Google Scholar]
- Garay, J.; Kiayias, A.; Leonardos, N. The Bitcoin Backbone Protocol with Chains of Variable Difficulty. In Proceedings of the 37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Springer: Cham, Switzerland, 2017; pp. 291–323. [Google Scholar]
- Pass, R.; Seeman, L.; Shelat, A. Analysis of the Blockchain Protocol in Asynchronous Networks. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Paris, France, 30 April–4 May 2017; Springer: Cham, Switzerland, 2017; pp. 643–673. [Google Scholar]
- Badertscher, C.; Maurer, U.; Tschudi, D.; Zikas, V. Bitcoin as a Transaction Ledger: A Composable Treatment. In Proceedings of the 37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Springer: Cham, Switzerland, 2017; pp. 324–356. [Google Scholar]
- Javed, M.U.; Rehman, M.; Javaid, N.; Aldegheishem, A.; Alrajeh, N.; Tahir, M. Blockchain-Based Secure Data Storage for Distributed Vehicular Networks. Appl. Sci. 2020, 10, 2011. [Google Scholar] [CrossRef]
- Seol, Y.; Ahn, J.; Park, S.; Ji, M.; Chae, H.; Yi, J.; Paek, J. DDNB—Doubly Decentralized Network Blockchain Architecture for Application Services. Appl. Sci. 2020, 10, 5212. [Google Scholar] [CrossRef]
- Vukolić, M. The quest for scalable blockchain fabric: Proof-of-work vs. BFT replication. In International Workshop on Open Problems in Network Security; Springer: Cham, Switzerland, 2015; pp. 112–125. [Google Scholar]
- Tschorsch, F.; Scheuermann, B. Bitcoin and Beyond: A Technical Survey on Decentralized Digital Currencies. IEEE Commun. Surv. Tutor. 2016, 18, 2084–2123. [Google Scholar] [CrossRef]
- Schneeweiss, S.; Brown, J.S.; Bate, A.; Trifirò, G.; Bartels, D.B. Choosing Among Common Data Models for Real-World Data Analyses Fit for Making Decisions About the Effectiveness of Medical Products. Clin. Pharmacol. Ther. 2020, 107, 827–833. [Google Scholar] [CrossRef] [PubMed]
- Glicksberg, B.S.; Oskotsky, B.; Thangaraj, P.M.; Giangreco, N.; Badgeley, M.A.; Johnson, K.W.; Datta, D.; Rudrapatna, V.A.; Rappoport, N.; Shervey, M.M.; et al. PatientExploreR: An extensible application for dynamic visualization of patient clinical history from electronic health records in the OMOP common data model. Bioinformatics 2019, 35, 4515–4518. [Google Scholar] [CrossRef] [PubMed]
- Choi, W.; Ko, S.J.; Jung, H.J.; Kim, T.M.; Choi, I. Expansion of EHR-Based Common Data Model (CDM). Stud. Health Technol. Inf. 2019, 264, 1443–1444. [Google Scholar]
- Ji, H.; Kim, S.; Yi, S.; Hwang, H.; Kim, J.-W.; Yoo, S. Converting clinical document architecture documents to the common data model for incorporating health information exchange data in observational health studies: CDA to CDM. J. Biomed. Inf. 2020, 107, 103459. [Google Scholar] [CrossRef] [PubMed]
- Yoon, D.; Ahn, E.K.; Park, M.Y.; Cho, S.Y.; Ryan, P.; Schuemie, M.J.; Shin, D.; Park, H.; Park, R.W. Conversion and Data Quality Assessment of Electronic Health Record Data at a Korean Tertiary Teaching Hospital to a Common Data Model for Distributed Network Research. Health Inf. Res. 2016, 22, 54–58. [Google Scholar] [CrossRef] [PubMed]
- Lamer, A.; DePas, N.; Doutreligne, M.; Parrot, A.; Verloop, D.; Defebvre, M.-M.; Ficheur, G.; Chazard, E.; Beuscart, J.-B. Transforming French Electronic Health Records into the Observational Medical Outcome Partnership’s Common Data Model: A Feasibility Study. Appl. Clin. Inf. 2020, 11, 013–022. [Google Scholar]
- Kim, H.K.; Jeong, E.Y.; Park, D.K. Study on HIPAA PHI application method to protect personal medical information in OMOP CDM construction. J. KINGComput. 2017, 13, 66–76. [Google Scholar]
- Shin, S.J.; You, S.C.; Park, Y.R.; Roh, J.; Kim, J.-H.; Haam, S.J.; Reich, C.G.; Blacketer, C.; Son, D.-S.; Oh, S.; et al. Genomic Common Data Model for Seamless Interoperation of Biomedical Data in Clinical Practice: Retrospective Study. J. Med. Internet Res. 2019, 21, e13249. [Google Scholar] [CrossRef]
- Kattamuri, M. Block Cipher Modes of Operation. Available online: https://www.geeksforgeeks.org/block-cipher-modes-of-operation (accessed on 27 August 2020).
- Benet, J. IPFS—Content Addressed, Versioned, P2P File System. arXiv 2017, arXiv:1407.3561. [Google Scholar]
- Khatal, S.; Rane, J.; Patel, D.; Patel, P.; Busnel, Y. FileShare: A Blockchain and IPFS Framework for Secure File Sharing and Data Provenance. In Proceedings of the Computing Algorithms with Applications in Engineering; Springer: Cham, Switzerland, 2020; pp. 825–833. [Google Scholar]
- Aydar, M.; Cetin, S.C.; Ayvaz, S.; Aygun, B. Private key encryption and recovery in blockchain. arXiv 2019, arXiv:1907.04156. [Google Scholar]
- Jayaraman, I.; Mohammed, M. Secure Privacy Conserving Provable Data Possession (SPC-PDP) framework. Inf. Syst. e-Bus. Manag. 2019, 1–27. [Google Scholar] [CrossRef]
- Park, C.; Kim, H.; Hong, D.; Seo, C. A Symmetric Key Based Deduplicatable Proof of Storage for Encrypted Data in Cloud Storage Environments. Secur. Commun. Netw. 2018, 2018, 2193897. [Google Scholar] [CrossRef]
- TetraCoin. What Is Genesis Block and Why Genesis Block Is Needed? Available online: https://medium.com/@tecracoin/what-is-genesis-block-and-why-genesis-block-is-needed-1b37d4b75e43 (accessed on 27 August 2020).
- Zhang, R.; Xue, R.; Liu, L. Security and Privacy on Blockchain. ACM Comput. Surv. 2019, 52, 1–34. [Google Scholar] [CrossRef]
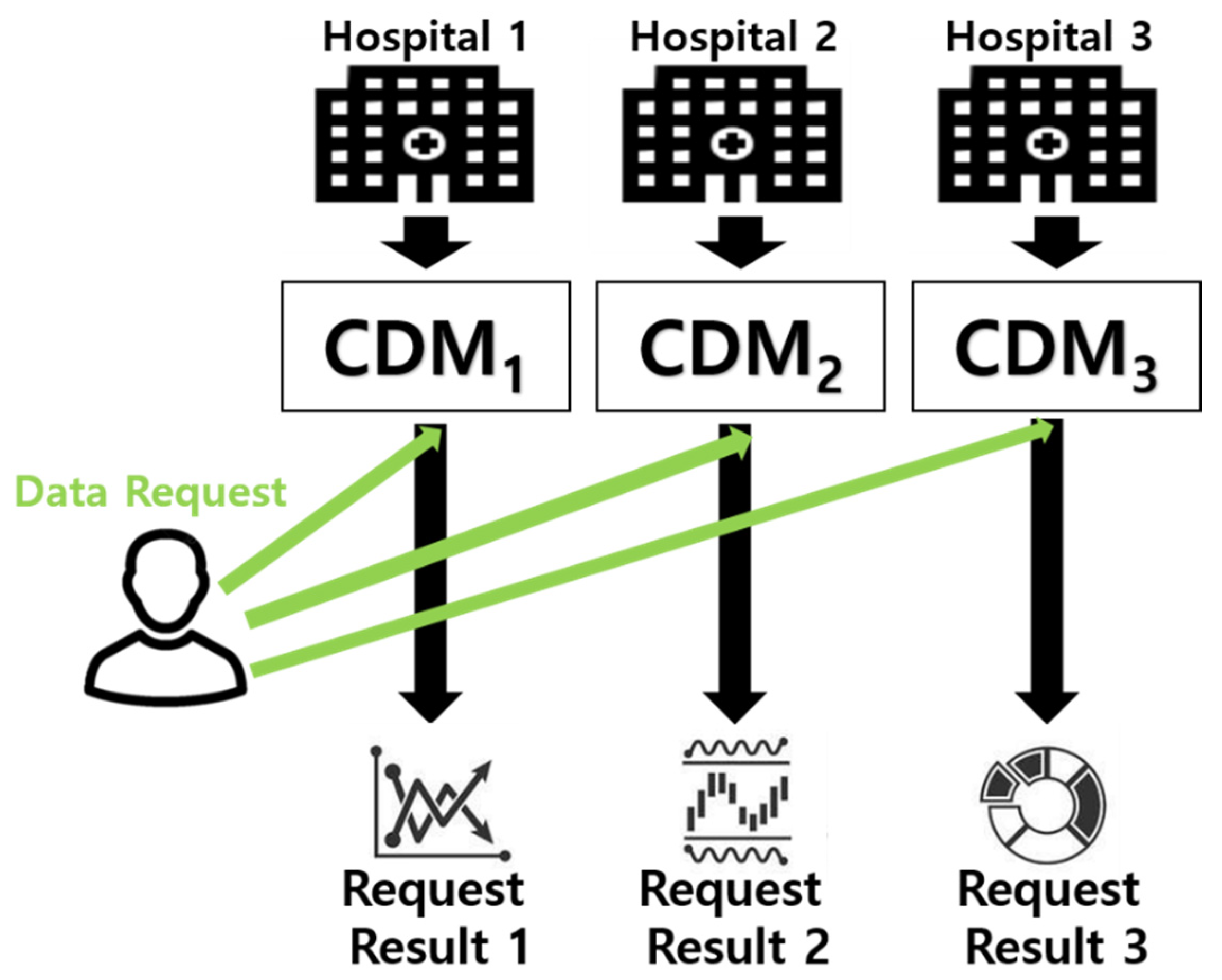











| Component | CDM Blockchain | |
|---|---|---|
| 1 | Digital asset | CDM with generated digest |
| 2 | Participant | CDM provider CDM consumer Service broker |
| 3 | Transaction | Write the digest of CDM Read the signed CDM Read the digest associated with CDM |
| 4 | Access control | Read a public key by CDM provider Read a public key by CDM consumer Write a public key by Service broker |
| 5 | ID management | X.509 public/private key |
| The Baseline CDM Model | The Proposed Secure-Cloud CDM Model (SC-CDM) | |
|---|---|---|
| Fault tolerance | Limitation of single point of failure | High availability with Replication |
| Data Sharing | High cost of sharing large CDM data | Low cost of data sharing using P2P repository and distributed ledger |
| Privacy | The exposure of CDM data ownership | Enhanced secure DID ownership |
| Data integrity | Vulnerability of CDM Data integrity | Ensuring data integrity with cryptography |
| DID = Decentralized Identifier; P2P = peer-to-peer. | ||
| No. | Item | Contents |
|---|---|---|
| 1 | Sender | fK5q+LBx9DXQm9vxAJPaw1zBWA9UT60V5Ma12uxXGDQ= |
| 2 | Recipient | HhhAXOj+iMqRRNJJgDaRD/xK78 × 1248F7WNr9cEjxHk= |
| 3 | Key | KMGFK4HR3IFSHYMYUIYZUYZRCZZPR444B6K7D3BNZCGJ7D6C3OXA==== |
| 4 | IV | F9A90A83DA5E986ACEE3EE4F7AEA8343 |
| 5 | Hash1 | QmPs2BsjB9VBuV6pHxdVYJP8fsnbLu8BTY93b9anwwW6SM |
| 6 | Hash2 | QmfHCn3qnnWobcmmWrVZTioWW6UdWxMrUqkBbD1BiTihiv |
| IV = Initialization Vector. | ||
| No. | The Size of CDM | SC-CDM (Local IPFS) | Conventional Method (Remote IPFS) | Comparison of Elapse Time | ||
|---|---|---|---|---|---|---|
| Elapsed Time | Standard Deviation | Elapsed Time | Standard Deviation | |||
| 1 | 1 MB | 0.263663 | 0.010216 | 0.234719 | 0.010720 | 1.079860 |
| 2 | 10 MB | 0.289340 | 0.010536 | 1.056073 | 0.006692 | 3.649938 |
| 3 | 100 MB | 1.102761 | 0.019368 | 9.671313 | 0.012963 | 8.770090 |
| 4 | 200 MB | 2.066382 | 0.021744 | 19.249866 | 0.026164 | 9.315734 |
| 5 | 500 MB | 4.934743 | 0.045454 | 48.105810 | 0.028492 | 9.748392 |
| 6 | 750 MB | 7.296134 | 0.029448 | 72.207809 | 0.036717 | 9.896722 |
| 7 | 1 GB | 9.931975 | 0.058510 | 98.620600 | 0.049551 | 9.929606 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cho, J.H.; Kang, Y.; Park, Y.B. Secure Delivery Scheme of Common Data Model for Decentralized Cloud Platforms. Appl. Sci. 2020, 10, 7134. https://doi.org/10.3390/app10207134
Cho JH, Kang Y, Park YB. Secure Delivery Scheme of Common Data Model for Decentralized Cloud Platforms. Applied Sciences. 2020; 10(20):7134. https://doi.org/10.3390/app10207134
Chicago/Turabian StyleCho, Jae Hyuk, Yunhee Kang, and Young B. Park. 2020. "Secure Delivery Scheme of Common Data Model for Decentralized Cloud Platforms" Applied Sciences 10, no. 20: 7134. https://doi.org/10.3390/app10207134
APA StyleCho, J. H., Kang, Y., & Park, Y. B. (2020). Secure Delivery Scheme of Common Data Model for Decentralized Cloud Platforms. Applied Sciences, 10(20), 7134. https://doi.org/10.3390/app10207134





