Atomicity Violation in Multithreaded Applications and Its Detection in Static Code Analysis Process
Abstract
1. Introduction
2. Description of the Phenomenon
- (1)
- Undefined application behavior;
- (2)
- Incorrect application behavior.
3. Existing Solutions
4. Agreement Relationships between Operations
- Forward—a relationship in which the operation a always must be followed by an operation b;
- Backward—a relationship where operation a always has to precede operation b;
- Symmetric—a relationship where operation a always has to precede operation b, and operation b always has to follow operation a.
5. Multithreaded Application Source Code Model
- P is the application index;
- , is a a set of threads of application, where is the main thread ;
- , is a sequence of , sets which are subsets of containing threads working in the same period of time in the application , whereas , and ;
- is a collection of shared application resources , and the subsequent elements are sets of variable names relating to a single resource;
- , is a set of all application operations which are atomic at a certain level of abstraction—i.e., dividing them into smaller operations is impossible (it should be understood as an instruction or function defined in a programming language); Index i indicates the number of the thread in which the operation is performed, and index j is the ordinal number of operations working within the same thread;
- —a set of all locks available in the program, defined as a pair of variables, type of lock, where the type is understood as one of the set values (PMN, PME, PMR, PMD);
- and , ()—a set of edges including:
- (a)
- Transition edges—specifying the order in which the operation is performed. These edges are pairs , where the elements describe two successive operations ;
- (b)
- Usage edges—indicating resources that change during the operation. These edges are pairs , in which one element is operation , and the other is resource ;
- (c)
- Dependency edges—indicating operations depending on the current value of one of the resources. These edges are pairs , in which one element is the resource , and the other is the operation ;
- (d)
- Locking edges—indicating the operation applying the selected lock. These edges are pair , in which one element is the lock, and the other is the locking operation;
- (e)
- Unlocking edge—indicating the operation releasing the selected lock. These edges are pairs , in which one element is the unlocking operation, and the other is the released lock;
- —sequence of sets:
- a set of pairs of forward relationship operations:;
- a set of pairs of backward relationship operations:;
- family of pairs of operations related by a symmetrical relation:.
5.1. Relation Breakage
5.2. Reversal of Relation
6. Problem Definition
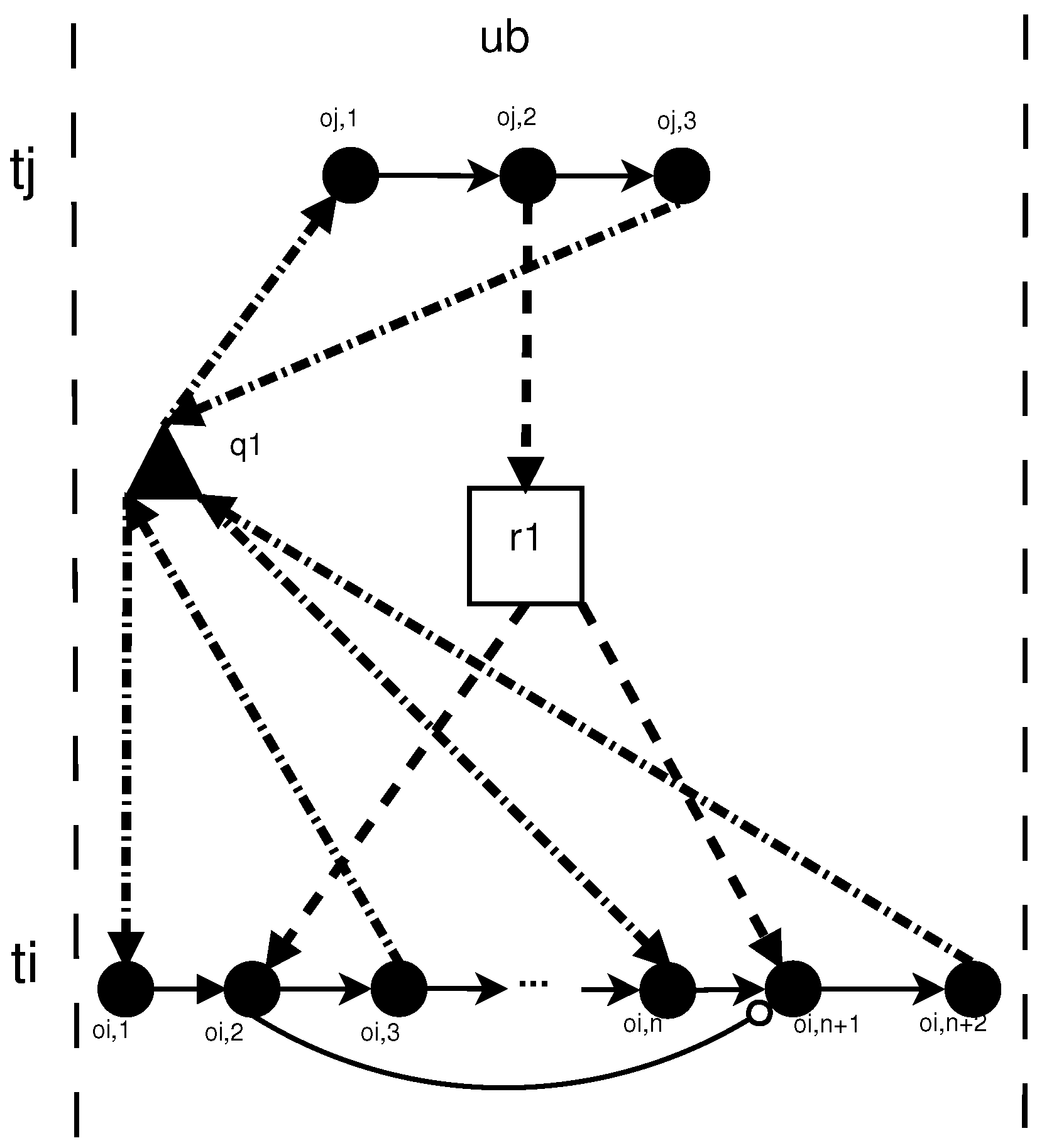
7. Sufficient Condition
- There are no conflicts causing race condition and deadlock;
- In graph [2], there is a pair of threads and working in the same range of ;
- In thread , there is a pair of operations and these operations are in an agreement relationship which is not completely broken;
- In thread , there is operation ;
- In the set of operations , at least one of them is connected to a resource with a shared use edge (one of the scenarios listed in Table 1 is fulfilled).
8. Leading Example
- ;
- ;
- ;
- ;
- ;
- ;
- .
- (1)
- can be violated by ;
- (2)
- can be violated by .
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| AII | Access Interleaving Invariants |
| AST | Abstract Syntax Trees |
| AV1 | Example application name |
| BWD | Backward |
| FWD | Forward |
| HAVE | Hybrid Atomicity Violation Explorer |
| JDK | Java Development Kit |
| MASCM | Multithreaded Application Source Code Model |
| PMD | Pthreads Mutex Default |
| PME | Pthreads Mutex Error Check |
| PMN | Pthreads Mutex Normal |
| PMR | Pthreads Mutex Recursive |
| SYM | Symmetric |
References
- Giebas, D.; Wojszczyk, R. Multithreaded Application Model. In Distributed Computing and Artificial Intelligence, 16th International Conference, Special Sessions; Springer: Cham, Germany, 2019; Volume 1004, pp. 93–103. [Google Scholar]
- Giebas, D.; Wojszczyk, R. Deadlocks Detection in Multithreaded Applications Based on Source Code Analysis. Appl. Sci. 2020, 10, 532. [Google Scholar] [CrossRef]
- Woo, J.; Choi, H.; Lee, J. Empirical Performance Analysis of Collective Communication for Distributed Deep Learning in a Many-Core CPU Environment. Appl. Sci. 2020, 10, 6717. [Google Scholar] [CrossRef]
- Rudy, J.; Bożejko, W. Reversed Amdahl’s Law for Hybrid Parallel Computing. In Computer Aided Systems Theory—EUROCAST 2017; Moreno-Díaz, R., Pichler, F., Quesada-Arencibia, A., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 101–108. [Google Scholar]
- Oh, Y.R.; Park, K.; Park, J.G. Online Speech Recognition Using Multichannel Parallel Acoustic Score Computation and Deep Neural Network (DNN)- Based Voice-Activity Detector. Appl. Sci. 2020, 10, 4091. [Google Scholar] [CrossRef]
- Jin, G.; Song, L.; Zhang, W.; Lu, S.; Liblit, B. Automated Atomicity-Violation Fixing. ACM SIGPLAN Not. 2011, 46, 389–400. [Google Scholar] [CrossRef]
- Park, S.; Lu, S.; Zhou, Y. CTrigger: Exposing Atomicity Violation Bugs from Their Hiding Places; ACM SIGARCH Computer Architecture News; ACM: New York, NY, USA, 2009; Volume 37, pp. 25–36. [Google Scholar]
- Park, C.; Sen, K. Randomized active atomicity violation detection in concurrent programs. In Proceedings of the 16th ACM SIGSOFT International Symposium on Foundations of Software Engineering, Atlanta, GA, USA, 9–14 November 2008; pp. 135–145. [Google Scholar]
- Flanagan, C.; Freund, S.N. Atomizer: A Dynamic Atomicity Checker for Multithreaded Programs. ACM SIGPLAN Not. 2004, 39, 256–267. [Google Scholar] [CrossRef]
- Rak, T. Performance Modeling Using Queueing Petri Nets. Commun. Comput. Inf. Sci. 2017, 718, 321–335. [Google Scholar]
- Von Praun, C.; Gross, T. Static Detection of Atomicity Violations in Object-Oriented Programs. J. Object Technol. 2004, 3, 103–122. [Google Scholar] [CrossRef]
- Zhou, Y.; Lu, S.; Tucek, J.A. Atomicity Violation Detection Using Access Interleaving Invariants. U.S. Patent 8,533,681, 10 September 2013. [Google Scholar]
- Dias, R.J.; Pessanha, V.; Lourenço, J.M. Precise detection of atomicity violations. In Proceedings of the Haifa Verification Conference, Haifa, Israel, 6–8 November 2012; pp. 8–23. [Google Scholar]
- Ceze, L. Detecting and Avoiding Atomicity Violations. Available online: https://www.nii.ac.jp/userimg/lectures/LuisCeze/nii-lecture4.pdf (accessed on 9 October 2019).
- Stroustrup, B. The C++ Programming Language, 4th ed.; Addison-Wesley: Boston, MA, USA, 2013. [Google Scholar]
- Chew, L.; Lie, D. Kivati: Fast detection and prevention of atomicity violations. In Proceedings of the 5th European Conference on Computer Systems, Paris, France, 13–15 April 2010; pp. 307–320. [Google Scholar]
- Yang, Y.; Gringauze, A.; Wu, D.; Rohde, H.K. Detecting Data Race and Atomicity Violation via Typestate-Guided Static Analysis. U.S. Patent 8,510,722, 13 August 2013. [Google Scholar]
- Lu, S.; Tucek, J.; Qin, F.; Zhou, Y. AVIO: Detecting atomicity violations via access interleaving invariants. ACM SIGOPS Oper. Syst. Rev. 2006, 40, 37–48. [Google Scholar] [CrossRef]
- Xu, M.; Bodík, R.; Hill, M.D. A serializability violation detector for shared-memory server programs. ACM SIGPLAN Not. 2005, 40, 1–14. [Google Scholar]
- Tongping, L.; Zhou, J.; Silvestro, S.; Liu, H. Defeating Deadlocks in Production Software. U.S. Patent Application No. 16/159,234, 18 April 2019. [Google Scholar]
- Sasturkar, A.; Agarwal, R.; Wang, L.; Stoller, S.D. Automated type-based analysis of data races and atomicity. In Proceedings of the tenth ACM SIGPLAN Symposium on Principles and Practice of Parallel Programming, Chicago, IL, USA, 15–17 June 2005; pp. 83–94. [Google Scholar]
- Wang, C.; Limaye, R.; Ganai, M.; Gupta, A. Trace-based symbolic analysis for atomicity violations. In Proceedings of the International Conference on Tools and Algorithms for the Construction and Analysis of Systems, Paphos, Cyprus, 20–28 March 2010; pp. 328–342. [Google Scholar]
- TIOBE Index. Available online: https://www.tiobe.com/tiobe-index/ (accessed on 12 October 2019).
- Chang, X.; Dou, W.; Gao, Y.; Wang, J.; Wei, J.; Huang, T. Detecting atomicity violations for event-driven Node.js applications. In Proceedings of the 41st International Conference on Software Engineering, Montreal, QC, Canada, 25–31 May 2019; pp. 631–642. [Google Scholar]
- Yu, Z.; Song, L.; Zhang, Y. Fearless Concurrency? Understanding Concurrent Programming Safety in Real-World Rust Software. arXiv 2019, arXiv:1902.01906. [Google Scholar]
- Roberson, M.; Boyapati, C. A Static Analysis for Automatic Detection of Atomicity Violations in Java Programs. 2010. Available online: https://www.eecs.umich.edu/techreports/cse/2011/CSE-TR-569-11.pdf (accessed on 11 November 2020).
- Chen, Q.; Wang, L.; Yang, Z.; Stoller, S.D. HAVE: Detecting atomicity violations via integrated dynamic and static analysis. In Proceedings of the International Conference on Fundamental Approaches to Software Engineering, York, UK, 22–29 March 2009; pp. 425–439. [Google Scholar]
- Huss, E. The C Library Reference Guide. Available online: http://www.fortran-2000.com/ArnaudRecipes/Cstd/ (accessed on 11 November 2020).


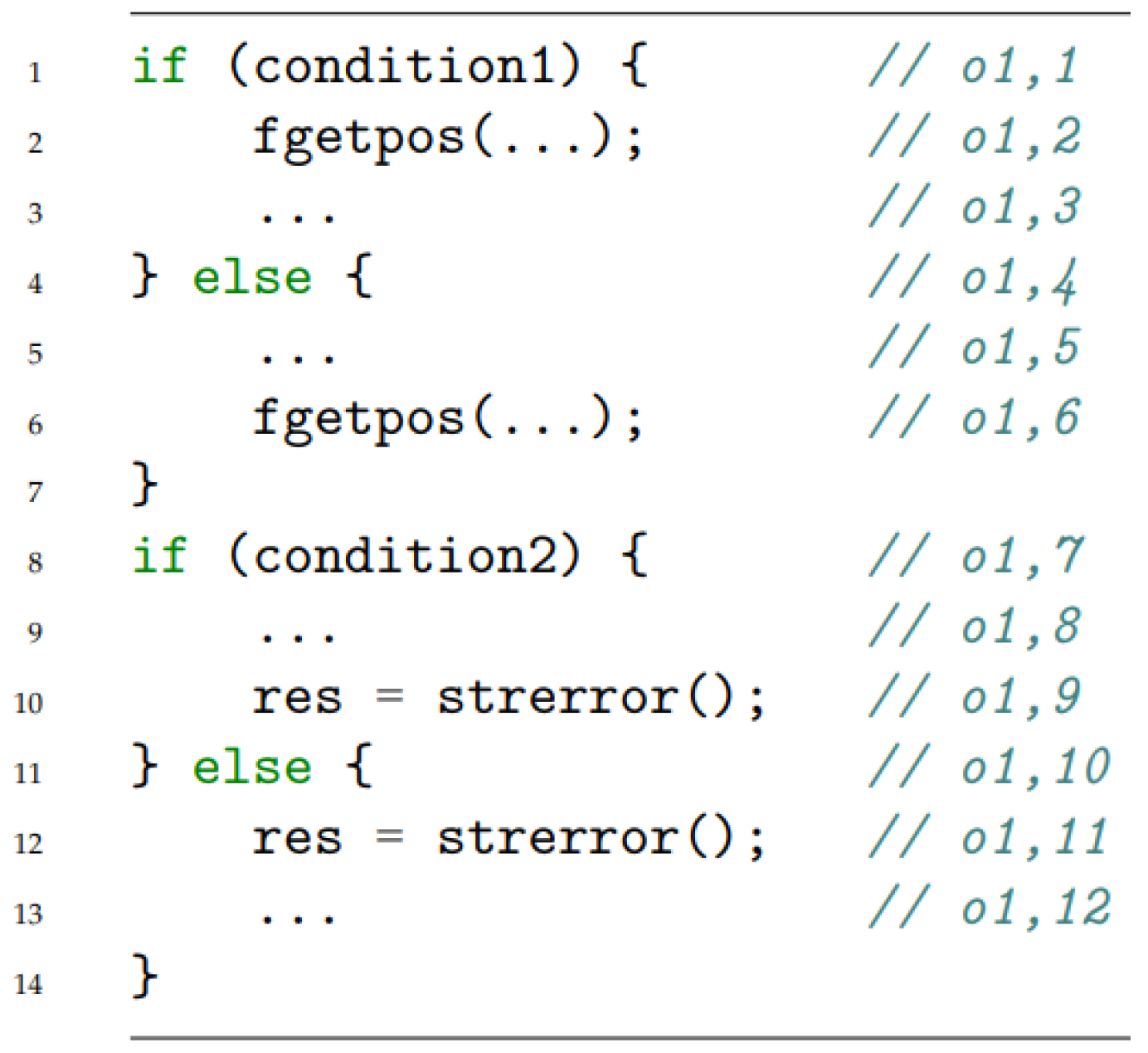



| Forward | Backward | Symmetric |
|---|---|---|
| fgetpos i strerror | ||
| fsetpos i strerror | ||
| ftell i strerror | ||
| atof i strerror | ||
| calloc i free | strtod i strerror | va_start i va_arg |
| malloc i free | strtol i strerror | va_arg i va_end |
| strtoul i strerror | ||
| calloc i realloc | ||
| malloc i realloc | ||
| srand i rand |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Giebas, D.; Wojszczyk, R. Atomicity Violation in Multithreaded Applications and Its Detection in Static Code Analysis Process. Appl. Sci. 2020, 10, 8005. https://doi.org/10.3390/app10228005
Giebas D, Wojszczyk R. Atomicity Violation in Multithreaded Applications and Its Detection in Static Code Analysis Process. Applied Sciences. 2020; 10(22):8005. https://doi.org/10.3390/app10228005
Chicago/Turabian StyleGiebas, Damian, and Rafał Wojszczyk. 2020. "Atomicity Violation in Multithreaded Applications and Its Detection in Static Code Analysis Process" Applied Sciences 10, no. 22: 8005. https://doi.org/10.3390/app10228005
APA StyleGiebas, D., & Wojszczyk, R. (2020). Atomicity Violation in Multithreaded Applications and Its Detection in Static Code Analysis Process. Applied Sciences, 10(22), 8005. https://doi.org/10.3390/app10228005






