Systematic Approach to Malware Analysis (SAMA)
Abstract
Featured Application
Abstract
1. Introduction
- It does not depend on the complexity of the malware to be analyze
- It is independent of the tools used making easier its adoption
- In enhances the importance of the malware classification as one of the first steps to be done
- It considers the integration of any existing information of the malware as an input for the analysis
- It defines a specific sequence for the analysis based on making the analysis of code, before the dynamic or behavioral analysis
- It includes a systematic feedback loop to retake the process when malware complexity requires to do it, as well as to improve the current analysis feeding previous stages with the obtained results of later ones
2. Background
- To assess the malware detection capability of organizations’ protection systems
- To evaluate the damage caused by the intrusion and malware actions
- To discover other machines that have been affected by the same malware
- To identify the vulnerability that was exploited by the malware, to obtain the software update that mitigates it, if available
- To obtain enough data and information to implement the appropriate defense mechanisms to mitigate and neutralize the damage caused by the malware, including firewall rules, host and network intrusion detection systems, firewall, and antivirus
- To determine the level of malware sophistication and complexity
- If it is possible, to determine the origin of an attack and to identify the intruder and malware developer
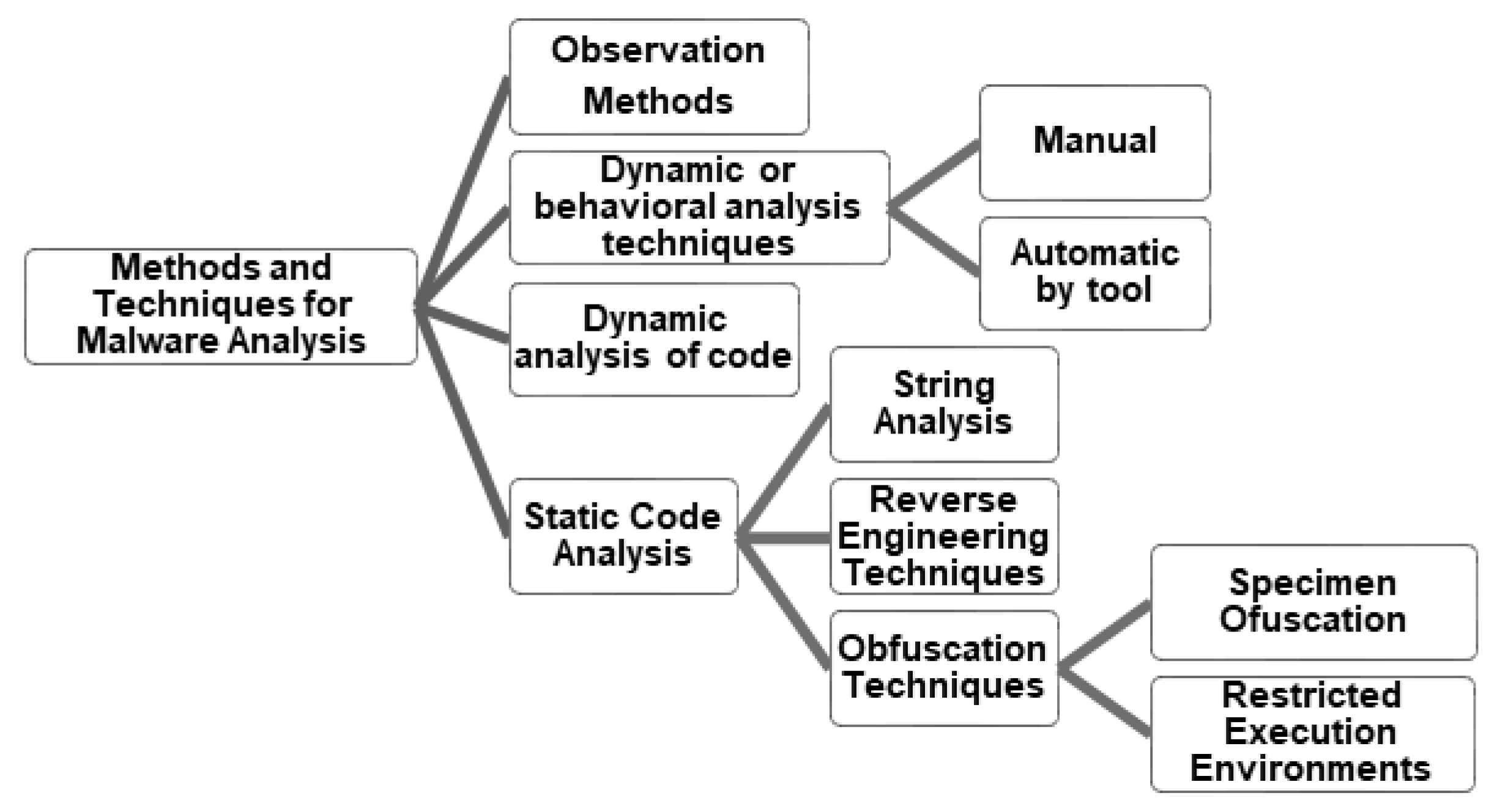
- Static Code Analysis: technique that collects as much information as possible of a binary without actually executing it. To do it, disassembly and reverse engineering techniques are used. This latter technique of analysis includes others more specific as string analysis, reverse engineering, packaging, obfuscation, restricted execution environments, etc. A tool to perform this type of analysis is IDA PRO [12] or GHIDRA [13].
- Dynamic code analysis: the analysis is basically done through a type of tools called ‘debuggers’ that are associated with the program code under analysis to take full control of them, allowing the possibility of executing it code line by code line. Some popular debuggers for malware analysis are OllyDbg [14], ImmunityDbg [15], and WinDbg [16].
- Dynamic or behavioral analysis: It analyzes the binary or specimen malware while it is running focusing on the supervision and monitorization of the malware interaction with the environment. The aim is to look for changes in the infected machine where it is running, network traffic and potential external communications with command and control servers. It can be done manually in a virtual or physical environment using different tools that collect the data of its interaction with the machine infected or automatically by “Sandbox” toolset [17].
3. Related Work
- Detection
- Isolation and extraction
- Behavioral analysis
- Code analysis
- One of the main differences with the methodology proposed in this paper is the execution order of the phases, performing the ‘code analysis’ phase first, before the ‘dynamic or behavioral analysis’ phase. That is why the information gathered during ‘code analysis’ is usually very useful for the following phase as passwords, installation commands, orders of command and control, possible execution paths, etc.
- MARE does not include the technique of ‘dynamic analysis of code’ by means of a debugger. This technique is very important to understand how malware works.
- It has not been published its application to a specific case study of a malware in order to test it and be validated. However, the methodology advanced has been applied to eight cases, two of them being included in this article.
4. Method Proposal
- Initial Actions. It consists of performing a series of actions mainly to obtain a record of the configuration of the machines involved in the analysis, with the purpose of obtaining a reference enabling us to compare the state of the same before and after running the malware under study. More specifically, in the next flow chart of the steps, it is as follows on Figure 4:
- ○
- Preserving integrity by deactivating services: System recovery and automatic updates
- ○
- Preservation of integrity by baseline generation of system configuration: snapshot (VMWare) of victim’s virtual machines, monitor and services; snapshot units C: (Systracer)
- ○
- Guarantee of the integrity of the generated samples: MD5 hash of the snapshot of the C units: by means of the tools “Md5sum” and verification with “WinMD5”.
- Classification. It is to examine the malware executable file, without accessing your code, to confirm it is some kind of malware and to obtain information in open sources, like the Internet, of its functionality that aid to realization of the following phases of analysis. It even enables the realization simple network firms, should be necessary for reasons of urgency in protecting systems. The tasks executed in this phase are:
- ○
- Transfer the malware
- ○
- Identify malware
- ○
- Check family of malware
- ○
- Finding information about the malware in open source
- ○
- Analysis of strings of malware binary
- ○
- Analyze techniques used in malware obfuscation
- ○
- Analyze file format
- Code Analysis. It consists of a static and dynamic analysis of the malware’s code, in assembly language, performing a detailed browsing process through it in order to get a better understanding of its functionality. It is a complex process that provides information for carrying out the next phase. It requires a reverse engineering analyst to find hidden features that involve new execution paths, which could be tried by the malware during the next phase to interact with the user. These discoveries will help to understand better its purpose and its functionality. In the next flow chart, the detail of the analysis steps is shown on Figure 7:
- Behavioral Analysis (See Figure 8). It consists in analyzing the implementation of malware in a lab that simulates a real environment, in order to observe malware behavior, network traffic generated and thus, the actions that are taken on the target system (registry modifications, files, etc.).
5. Study Cases
5.1. Red October Analysis
- To test the practical applicability of the presented methodology
- Identify future areas of development, to guarantee the evolution and adaptability of the methodology to the evolution of malware
- Reinforce the recognition of the importance of the development and evolution of methodologies that can effectively counteract the development of malware and serve to generate transferable knowledge
- To broaden the existing knowledge base on the evolution of malware development, a clear end to the design and use of malware analysis methodologies
- Host Server. To host the virtual environment to support the working environment.
- Victim. Its objective will be to constitute the platform where the malware will be executed and monitored in order to study its behavior. Built on a Windows machine.
- Monitoring and Windows services. Its objective is to record and monitor network traffic produced by malware, provide specific Windows system services such as SMB and another like DNS, FTP, and WEB.
- Services. The objective of this server is to provide services to malware in its interaction with the environment, such as HTTP, DHCP, Chat, IRC Server, FTP, DNS, and SMTP, to simulate its execution environment. Built on Sans Institute REMNUX malware analysis distribution. It has installed tools such as Inetsim and Netcat to simulate services for malware.
5.1.1. Malware Classification
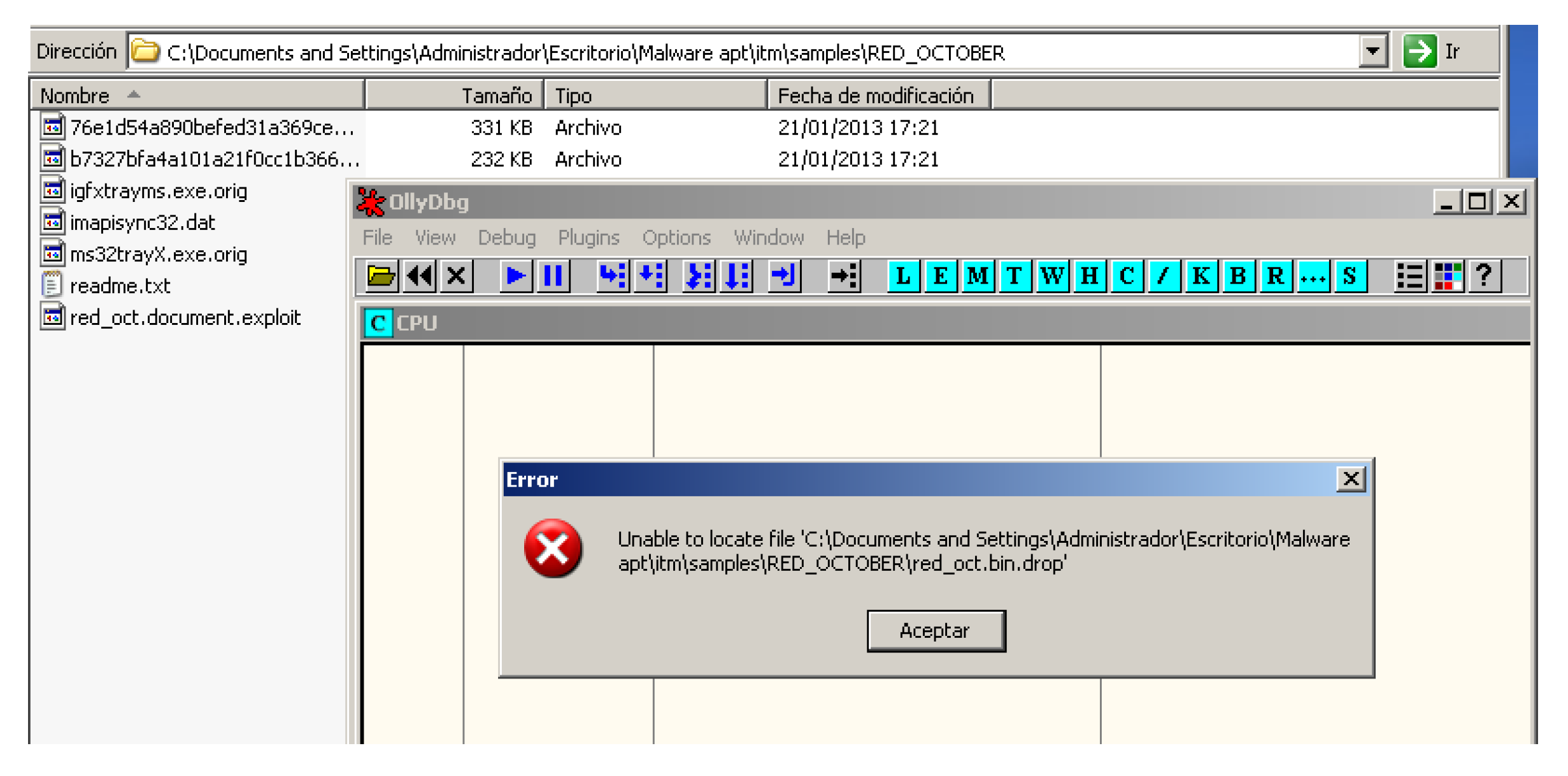
- Transfer. The malware is transferred via encrypted USB and decompressed:
- ○
- red_oct.document.exploit–(exploit)
- ○
- red_oct.bin.drop–(dropper)
- Identification (see Table 7). Obtaining the HASH MD5 signature of the files that theoretically contain the malware:
- Check for malware (see Table 8). Tested using online tools (virus total) and installable application Avira. Considering that Red October was detected in 2012, the results obtained from the verification phase confirm that we are analyzing a piece of malware.
- Open Source (OSINT). Derived from the previous steps, we are able to conduct an open source search very effectively. During this part of the analysis, high relevance information is obtained for the following phases of the methodology. The most important ones are listed below.
- ○
- Identification of the level of complexity of the malware in analysis. It is confirmed that it is an APT, which allows us to prepare and be aware that it is a highly complex malware.
- ○
- Identification of the vulnerabilities used by APT to infect victims. In particular, five potential attack vectors are identified:
- ➢
- CVE-2009-3129: XLS files (MS Excel)
- ➢
- CVE-2010-3333 DOC files (MS Word)
- ➢
- CVE-2012-0158 DOC files (MS Word)
- ➢
- CVE-2011-3544 Java-related vulnerability
- ➢
- CVE-2008-4250 Vulnerability to infect other computers on the network
- ○
- It is confirmed that the malware does not make use of any 0-Day vulnerability, thus taking advantage of systems not patched correctly or not updated.
- ○
- Key files used in the infection process are identified:
- ➢
- %TEMP%MSC.BAT
- ➢
- %ProgramFiles%WINDOWS NTLHAFD.GCP (This name may vary)
- ➢
- %ProgramFiles%WINDOWS NTSVCHOST.EXE
- ○
- The code of a critical file ‘MSC.BAT’ is identified. It is also verified that a command is executed to change the reference character table for coding which means that can be a correlation with the use of Cyrillic characters in its origin.
- ○
- MSC.BAT file has the following contents:
- chcp 1251
- Repeat
- attrib -a -s -h -r “%DROPPER_FILE%”
- of “%DROPPER_FILE%”
- if exist “%DROPPER_FILE%” goto Repeat
- of “%TEMP%msc.bat”
- ○
- It is identified that the malware does not interact if it is not able to establish an outside connection, in particular with the command and control (C & C).
- ○
- It is identified that once the back door is established, an exchange of information is initiated allowing the malware to install specific modules in order to develop a precisely attack adapted to the victim.
- Strings. ‘Bintext’ and ‘Strings’ tools are used to look for text strings in the code that can be helpful to the analysis. This part of the analysis yields a lot of information that needed to be analyzed in detail. The most relevant results obtained are presented below:
- ○
- Reference identification to the Excel.exe application
- ○
- Identification of TLS functions that can be used to avoid debuggers as well as a reference to the function ‘IsdebuggerPresent’
- ○
- Identification of strings related to encoding ‘Encodepointer’ and ‘DecodePointer’
- ○
- Sequences that may be related to memory write attempts and buffer overflow attacks (!%s)
- ○
- Identification of references to specific websites (SamLab.ws)
- Obfuscation techniques (see Figure 11). Thanks to the previous phase, it was identified that the file ‘red_oct.document.exploit’ had almost no ASCII chains that is a potential indicator of being an obfuscated program. The ‘PEiD’ tool is used, but is not capable of producing any valid results.
- Format and structure. We are in the last step of the classification stage and it is about analyzing the structure of the file to identify the use and the relationships between libraries, versions, dates and entry sections that may suggest that the code under analysis is a malware.
- ○
- Identification of the use of the ‘CRYPT32.DLL’ library and the ‘CryptStringToBinayW’ function that indicate the need to process encrypted code at runtime
- ○
- Identification of the use of the ‘MPR.DLL’ (multi provider router) module related to the establishment of different connections and the identification of key changes and session starts
- ○
- Identification of the use of the ‘SHELL32.DLL’ library, used to open different Windows components
- ○
- ‘OVERLAY’ function that allows to embed code, so once it is in execution time, malware can use additional memory to the one reserved for that program
5.1.2. Code Analysis
- Identification of the use of obfuscation techniques that increase the complexity of static code analysis
- Identification of additional malware protection mechanisms such as the need for external connection to be able to be fully executed.
- Functional check. The ‘red_oct.bin.drop’ file is checked using the ‘PE Explorer’ tool. However, this tool cannot unpack the file, although it provides us with the following information.
- ○
- Different entry point (00411A45) to the one shown in the classification phase (00011A45)
- ○
- Use of unconventional packaging
- ○
- File creation date 06/05/2011 7:58:13
- Dynamic code analysis. The ‘Ollydbg’ tool is used to develop this analysis. In the first place, it is decided to navigate through the code to obtain a generalized image and the following findings are made.
- ○
- Identification of protection measure by which it detects if the code is running in debug mode (see Figure 12)
- ○
- The point of creation of the file ‘MSC.bat’ previously identified in the classification phase is detected (see Figure 13)
- ○
- References to the files ‘scvhost.exe’ and ‘lhfd.gcp’, mentioned in the open sources consulted, are also identified
- ○
- Access to the ‘RPCRT4.DLL’ library is identified that means, with high probability, that it will be used to establish the back door
- ○
- Coded messages and text strings that mention the service ‘sshd’
- Static Code Analysis. The disassembly tool ‘IDA PRO’ (evaluation version) is used to develop this analysis. This analysis has made it possible to obtain information of analyzed file structure at the level of memory locations, used functions and the relationship between them.
- ○
- It is identified that within the structure of the code there is obfuscated code in each section, as well as empty memory blocks
- ○
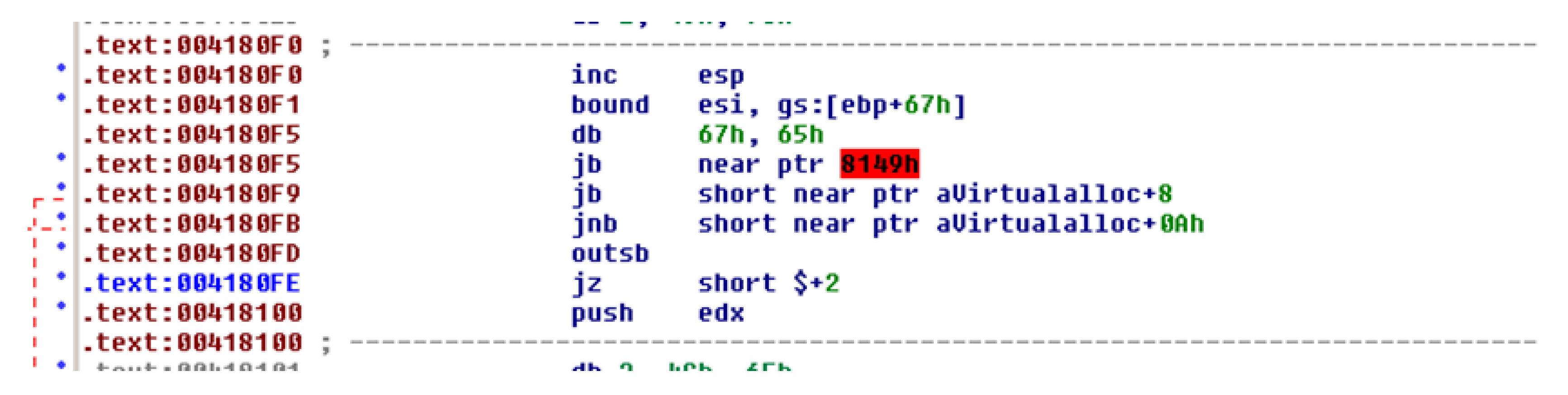
- The use of the ‘ISDebuggerPresent’ function stored in the memory position ‘004180F0′ is identified, potentially related to the protection measure detected in the previous phase (see Figure 14)
5.1.3. Behavior Analysis
- Initial Tasks. Situation of the analysis starting point and establishing two work areas: the execution environment and the monitoring environment.
- ○
- Considering that the malware has been identified requires a network communication environment, the victim’s host file has been modified to allow the monitoring team resolves queries about domains
- ○
- The monitor computer has been configured as the main DNS server being the authority over the domain.
- ○
- The monitoring tool used was ‘Wireshark’
- ○
- The configuration of the environment of the victim computer has been prepared by capturing its initial state using the tools ‘Systracer’, ‘Regshot. The paths in which the malware, supposedly, creates the files have been marked. Tools ‘Diskpulse’, ‘ProcessMonitor’ and VMMap’ have been installed to monitor the changes in real time.
- Running malware
- ○
- The file ‘red_oct.bin.drop’ is executed
- ○
- It is detected that after 15 s of its execution, the executed file disappears from the computer
- Activation of malware services
- ○
- Three modifications are detected in the DNS services. A first deactivation, an activation as a secondary server and an activation as a primary server.
- ○
- Considering that, the malware being analyzed is the piece in charge of the initial infection and establishment of the Backdoor, so the detected behavior makes sense.
- Subsequent Tasks. During this stage in the behavior analysis phase, the results are analyzed after the malware execution period. It is identified that the greatest activity after the execution of the file to analyze is done during the first 20 min. The changes detected at the victim and network are presented below.
- Victim host
- ○
- 12:04:25, the malware is run on the computer. A process named ‘red_oct-bin.exe’ and PID 2340 identifier is created that initiates access to registry variables related to communication processes
- ○
- 12:04:30, the files ‘svchost.exe’, ‘msc.bat’ and ‘hafd.gcp’ are created
- ○
- 12:04:36, the previously created ‘svchost.exe’ file is activated as a process with the PID identifier 2464 and it starts loading the malicious code into memory
- ○
- 12:04:40, the file ‘msc.bat’ is accessed
- ○
- 12:04:41, the file ‘red_oct.bin.exe’ is deleted. The process is created with the name ‘cmd.exe’. The file ‘msc.bat’ is deleted
- ○
- 12:19:44, the process ‘svchost.exe’ accesses registry variables related to communication processes. This phase coincides with the detection of network traffic related to the malware, concluding that it is, at this point, where it starts attempting to communicate with the C & C.
- ○
- 12:22:30, From this moment on, the process ‘svchost.exe’ initiates a cyclic behavior, every 3 min approximately, by means of which it tries to establish the connection with the exterior. It is interesting to detect the attempt to access routes related to web browsing applications such as Opera or Firefox, which could mean that the sample was aimed at a victim using this type of browser.
- ○
- The file ‘msc.bat’ remains temporarily in the system. This file is in charge of activating the infection inside the system (see Figure 15).
- ○
- The file ‘svchost.exe’ is a file that cannot be removed from the system. It is executed automatically by creating a process that contains encrypted code. Code analysis will be necessary.
- ○
- The ‘hafd.gcp’ file is a hidden and resident file. It is accessed only during the infection phase. It is an encrypted file.
- ○
- The use of the ‘VMMAP’ tool has made it possible to monitor the ‘svchost.exe’ process with PID2464. This monitoring has led to the following findings:
- ▪
- Text strings contained in the ‘Private Data’ section (00400000-00421FF) that refer to the ‘Get http’ method for downloading specific modules and names of external servers that can serve as proxies to communicate with the C & C.
- ▪
- The use of the tools ‘Systracer’ and ‘Regshot’ have allowed identifying the modification of user values (HKU) and the local computer (HKLM), used to allow the execution of all the tasks associated with the infection process.
- Network traffic analysis. It is identified that the malware is programmed to initiate communication several minutes after the infection process. In this case, it has been 19 min, although this time may vary depending on the environment where the infection occurs. The analysis has been divided into three parts:
- ○
- First malware execution with the DNS service disabled, where random requests are monitored trying to contact external DNS servers that operate as proxy.
- ○
- Second execution with the active DNS server where an interaction with the malware is checked, who asks the DNS server if it is an authorized server. Once the check is established, the malware no longer interacts. It was probably waiting for confirmation from C & C.
- ○
- Thirdly, the malware was executed and the file “hafd.gcp” was deleted, the communication sequence being identical to the second scenario.
- Dump and memory analysis. This is the last step in behavioral analysis. The ‘Winpmem’ tool has been used together with the ‘Volatility’ tool and its specific ‘malfind’ plugin to analyze malware. The most relevant findings based on the analysis of the file ‘svchost.exe’ with PID 1540 are the following:
- ○
- Identification of suspicious ‘hooks’ in both ‘user mode’ and ‘kernel mode’
- ○
- Identification of code and suspiciously injected or hidden DLLs
5.2. Flame Analysis
5.2.1. Malware Classification
- Transfer. The malware is transferred via encrypted USB and decompressed:
- ○
- mssecmgr.ocx.orig
- Identification
- ○
- File Type (see Table 9): type dynamic library.ocx
- Check for malware
- ○
- Names of malware: Flame, Flamer, and Skywiper
- ○
- Current detection capabilities antivirus: It is detected by 46 antiviruses
- Strings
- ○
- Use Database SQLLite and programming language C ++ and Lua
- ...
- CREATE VIRTUAL TABLE %T
- sqlite_temp_master
- sqlite_master
- ○
- UPDATE %Q.%s SET type=‘table’, name=%Q, tbl_name=%Q, rootpage=0, sql=%Q WHERE rowid=#%d
- Obfuscation techniques
- ○
- mssecmgr.ocx.orig: 2.4 MBit packed area, entropy 1
- ○
- Files accessed by the malware, entropy, first detected file type and whether it was possible to decode it (See Table 10)
- ○
- It uses three different mechanisms packaging (zlib algorithms, ppmd, libbzip) and RC4 encryption, XOR and transposition (see Table 11)
- ○
- Diffusing Capacity: File with Microsoft valid certificate, verified as correct with an MD5 hash.
- ○
- Exfiltrating capacity data: on the USB memory, once the malware has been executed, it creates a hidden file whose name is a single point (‘.’). The content is encrypted.
- ○
- Interact with command and control system. It uses the processes ‘winlogon.exe’, ‘explorer.exe’, and ‘iexplore.exe’. The fact that it is periodically opened the ‘Internet Explorer’ browser, suggests that it could be used to communicate with a ‘Command & Control’.
- Format and structure
- ○
- Supported operating systems: it supports operating systems based on Windows platform.
- ○
- Libraries required: it requires a total of 35 libraries: ADVAPI32.DLL, apphelp.dll, COMCTL32.DLL, COMDLG32.DLL, CRYPT32.DLL, Cryptui.dll, GDI32.DLL, IMAGEHLP.DLL, KERNEL32.DLL, lz32.dll, MPR.DLL, msasn1.dll, MSVCRT.DLL, NETAPI32.DLL, NTDLL.DLL, OLE32.DLL, OLEAUT32.DLL, Olecli32.dll, Olecnv32.dll, OLESVR32.DLL, OLETHK32.DLL, RPCRT4.DLL, SECUR32.DLL, SHDOCVW.DLL, SHELL32.DLL, SHLWAPI.DLL, URL.DLL, URLMON.DLL, USER32.DLL, Userenv.dll, Version.dll, WININET.DLL, Wintrust.dll, WLDAP32.DLL, WOW32.DLL.
- ○
- URLs: https://traffic-spot.com/wp-content/rss.php. This URL, for the analysis of the sample provided, was not available; domain “traffic-spot.com” does not exist anymore.
- ○
- DNS resolution requests, in this case, for the following domains:
- ▪
- windowsupdate.microsoft.com
- ▪
- traffic-spot.com
- ▪
- traffic-spot.biz
- ▪
- smart-access.net
- ▪
- quick-net.info
- ○
- It works only the resolution of the ‘windowsupdate.microsoft.com’ domain; the remaining domains are not accessible.
5.2.2. Code Analysis
- Programs that are blacklisted
- Program/malware modules and libraries
- Domain names (C & C servers): https://traffic-spot.com:443/wp-content/rss.php, https://traffic-spot.biz:443/wp-content/rss.php
- Used folder and file names, file extensions of interest...
- Registration keys accessed
- Queries to access ‘sqlite’ databases
5.2.3. Behavior Analysis
- Running malware
- ○
- Scripts and executables
- ▪
- Implementation of the specimen: start/ wait runddll32.exe mssecmgr.ocx.orig
- ○
- Capacity of Infection
- ▪
- The malware timed their actions so that they appear intertwined with legitimate activities and migrates between processes as needed. We also see that it creates many temporary files, some are deleted shortly after being created, and others remain at least for several minutes.
- ▪
- It migrates the process ‘rundll32.exe’ after its first execution to the process ‘services.exe’. It means that it infects using overwriting memory technique.
- ▪
- It performs a ‘hook’ back in the Windows API, in the ‘SHGetSpecialFolderPathW’ call ‘Explorer.exe’. It also infects the ‘iexplore.exe’ process.
- ▪
- In the process ‘services.exe’, specifically in the memory range ‘0x7e6a0000-0x7ecc7fff’, we can see that the ‘services.exe’ is another executable.
- Activation of malware services
- ○
- Files created (see Table 12)
- ○
- Registry modifications
- ▪
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\LSA\Authentication Packages added mssecmgr.ocx indicates packages that are loaded when a user logs on the victim machine.
- ○
- Memory analysis
- ▪
- In the memory of infected reference ‘services.exe’, it appears a process that performs an action of ‘not installed programs’ such as antivirus, firewalls, network monitors, etc., indicating that the malware has its own ‘blacklist’ within the code to avoid detection by these applications.
5.3. Other Analysis
6. Discussion
- Considering the current situation in the development of malware and its industrialization, within the analysis of malware, the technical analysis of the solution is a fundamental issue. It has been verified that the phases of classification and search in open sources are key to establish an optimal strategy of analysis in the following phases. Currently, there is a lot of information published by expert analysts that can help greatly to economize the use of resources in a specific analysis, either by reuse of code, by reuse of vulnerabilities to exploit or reuse of entire malware packages if the attack is characterized by the use of specific modules.
- During the application of the methodology to the piece of malware, two highly complex defense mechanisms have been identified: one is the packaging and obfuscation and the second is the detection of operation in debugging mode. To be able to deal with these types of measures, it requires a high level of specialization of the analyst team that is not available to everyone.
- However, thanks to the structure of the methodology, it is possible to identify this situation and, in case of incapacity, to derive that part of the analysis to qualified teams. This situation implies an optimization of resources at the level of analysis, guaranteeing a good use of work teams, starting with the detection of highly complex situations, as well as the possibility of deriving parts of the analysis to different teams.
- Code analysis capabilities are essential to develop a good analysis. This implies that the methodology depends, of course, on the capacity of the analyst, especially in the static analysis phase. However, the structure of the methodology makes it possible to derive this phase to a team or several teams in parallel, providing the possibility of crossing results and improving the analysis in two ways:
- ○
- By iteration between code analysis and behavior analysis
- ○
- By iteration between static and dynamic code analysis
- ○
- Through the joint work of different teams in these phases in order to consolidate the results
7. Conclusions
- The methodology is applicable regardless of the complexity of the malware. This makes it possible to analyze different types of malware models and obtain a homogeneous analysis result.
- The identification of the phases allows its execution by human teams with its specific tools. It allows to systematize the analysis optimizing each phase based on the existing capacities and to share the results of each phase with the rest of the involved analysts to improve the effectiveness of the results.
- The methodology establishes the type of analysis to be performed but it is independent of the tools. This guarantees the versatility and adaptability of the method to different analysis environments.
- The order established by the methodology guarantees an effective obtaining information process, starting from the classification based on searching in open sources. Later, this will make it possible to define an operative strategy in the analysis of the selected malware. Likewise, it allows, in the face of the same malware, to develop specific analysis work on specific aspects, a highly interesting issue for the development of intelligence on complex malware such as APTs.
- The inclusion of an iteration process in different phases of the methodology has made it possible to resolve and complete the different phases of the analysis by generating a greater global knowledge than the sum of each of the phases independently.
- The validity of the applicability of the methodology taken as a reference is strongly confirmed. The execution of the complete process according to the proposed order has guaranteed an orderly and coherent advance in the analysis of the ‘Red October’ and ‘Flame’ malware. The results of which, in accordance with those obtained by expert sources, proves its success.
- The classification phase has been identified as a critical one for the realization of this pilot. The information gathered has allowed the tests carried out to be effectively oriented, optimizing the analysis. This fact shows that this phase is vital in the analysis of this type malware that have been previously detected by third parties. In the case of unidentified malware, the relevance of this phase would diminish, drastically making the analysis more complex.
- During the code analysis phase, it is confirmed that the proposed innovation of exchanging the order, placing the dynamic code analysis first to the static one, facilitates the development of the malware study if it is highly complex and uses advanced obfuscation techniques. However, the need to include a cyclical and iterative process between both analyses has been detected—possibly conditioned by the level of the analyst—with the aim of focusing and performing deeper investigation as the knowledge about malware increases. This could be an innovation derived from the one described above.
- The need for the malware behavior analysis phase is confirmed, as it greatly increases the knowledge about the malware behavior being analyzed. However, the effectiveness of this phase is conditioned by the quality of the information obtained in the previous phases which drastically reduces any possible interest in executing this phase before the previous ones. The methodology includes an iterative mechanism consistent with the possibility of having to analyze new samples due to the complexity of malware. It can be materialized during execution, a situation that would have occurred if phase 2 of the APT ‘Red October’ had been initiated and specific modules were being downloaded from the C & C.
- During the execution of the tests, taking into account their scope, it has become clear that the tests in the phases of analysis of code analysis (static as well as behavior) can focus on the victim system, simplifying the number of tools to install in the rest of systems involved in the lab. This allows the analyst to focus on the target of the monitor system and the system services needed as key parts in the constitution of a realistic scenario in order to force the malware to show all its behavior.
- Management and classification of tools. The application of the methodology is based on the use of multiple tools, many of them of free use and others previous acquisition of license. Bearing in mind that the second type of tool already has legal conditions, the first one is more difficult to control (support, continuity, etc.). A line of development focused on the effective management and maintenance of these tools would improve the management of technical and human resources and could lead to possible standardizations in specific sectors.
- Apply the proposed methodology to other operating systems. While here it has been developed and validated for Windows based systems, as this type of operating system used mainly in the world, is can also be valid for other operating systems like Linux, Android, etc. Since, nowadays, malware is present in any of them. New lab design should consider other victim machines’ operating systems such as Linux and Android.
- Determine whether different analysis tools are compatible and, if not, look for the equivalent versions for Linux and Android operating systems.
Author Contributions
Funding
Conflicts of Interest
References
- Bencsáth, B.; Pék, G.; Buttyán, L.; Felegyhazi, M. The cousins of Stuxnet: Duqu, Flame, and Gauss. Future Internet 2012, 4, 971–1003. [Google Scholar] [CrossRef]
- Gandotra, E.; Bansal, D.; Sofat, S. Malware Analysis and Classification: A Survey. J. Inf. Secur. 2014, 5, 56–64. [Google Scholar] [CrossRef]
- Burrows, A.; Lockwood, M.; Borowczak, M.; Janak, E.; Barber, B. Integrated STEM: Focus on Informal Education and Community Collaboration through Engineering. Educ. Sci. 2018, 8, 4. [Google Scholar] [CrossRef]
- Orcos, L.; Jordán, C.; Magreñán, A. 3D visualization through the hologram for the learning of area and volume concepts. Mathematics 2019, 7, 247. [Google Scholar] [CrossRef]
- Grout, I. Remote Laboratories as a Means to Widen Participation in STEM Education. Educ. Sci. 2018, 7, 85. [Google Scholar] [CrossRef]
- Jordán, C.; Magreñán, Á.A.; Orcos, L. Considerations about flip education in the teaching of advanced mathematics. Educ. Sci. 2019, 9, 227. [Google Scholar] [CrossRef]
- Prieto, M.C.; Palma, L.O.; Tobías, P.J.B.; León, F.J.M. Student assessment of the use of kahoot in the learning process of science and mathematics. Educ. Sci. 2019, 9, 55. [Google Scholar] [CrossRef]
- Orcos, L.; Hernández-Carrera, R.M.; Espigares, M.J.; Magreñán, Á.A. The Kumon method: Its importance in the improvement on the teaching and learning of mathematics from the first levels of Early Childhood and Primary Education. Mathematics 2019, 7, 109. [Google Scholar] [CrossRef]
- Sikorski, M.; Honig, A. Practical Malware Analysis. In The Hands-On Guide to Dissecting Malicious Sofware; No Starch Press: San Francisco, CA, USA, 2012. [Google Scholar]
- Monnappa, K.A. Learning Malware Analysis; Packt Publishing Ltd.: Birmingham, UK, 2018; ISBN 978-1-78839-250-1. [Google Scholar]
- Theerthagiri, D. Reversing Malware: A Detection Intelligence with In-Depth Security Analysis. Ph.D. Thesis, Linköpings University, Linköping, Sweden, 2009. [Google Scholar]
- IDA Pro Disassembler. 2019. Available online: https://www.hex-rays.com/idapro/ (accessed on 2 November 2019).
- National Security Agency. Central Security Service. GHIDRA. 2019. Available online: https://www.nsa.gov/resources/everyone/ghidra/ (accessed on 2 November 2019).
- Olly Debugger. 2019. Available online: https://www.ollydbg.de/ (accessed on 2 November 2019).
- Immunity Debugger. 2019. Available online: https://www.immunityinc.com/products/debugger/ (accessed on 2 November 2019).
- Windows Debugging Tools. WinDBG. Available online: https://docs.microsoft.com/es-es/windows-hardware/drivers/debugger/debugger-download-tools (accessed on 2 November 2019).
- Ori Meir, N.N.; Yuval, E.; Lior, R. Dynamic Malware Analysis in the Modern Era—A State of the Art Survey. ACM Comput. Surv. 2019, 52, 1–48. [Google Scholar] [CrossRef]
- Moser, A.; Kruegel, C.; Kirda, E. Limits of Static Analysis for Malware Detection. In Proceedings of the Twenty-Third Annual Computer Security Applications Conference (ACSAC 2007), Miami Beach, FL, USA, 10–14 December 2007; pp. 421–430. [Google Scholar]
- Manuel, E.; Theodoor, S.; Engin, K.; Christopher, K. A survey on automated dynamic malware-analysis techniques and tools. ACM Comput. 2012, 44, 42. [Google Scholar]
- Mulukutla, V. Wolfsting: Extending Online Dynamic Malware Analysis Systems by Engaging Malware. Ph.D. Thesis, Faculty of North Carolina State University, Raleigh, NC, USA, 2010. [Google Scholar]
- Rieck, K.; Trinius, P.; Willems, C.; Holz, T. Automatic analysis of malware behavior using machine learning. J. Comput. Secur. 2011, 19, 639–668. [Google Scholar] [CrossRef]
- Yoshioka, K.; Matsumoto, T. Multi-Pass Malware Sandbox Analysis with Controlled Internet Connection. IEICE TRANSACTIONS on Fundamentals of Electronics. Commun. Comput. Sci. 2010, 93, 210–218. [Google Scholar]
- Wang, L.; Wang, B.; Liu, J.; Miao, Q.; Zhang, J. Cuckoo-based Malware Dynamic Analysis. Int. J. Perform. Eng. 2019, 15, 772–781. [Google Scholar] [CrossRef]
- Liu, X.; Zhang, J.; Lin, Y.; Li, H. Atmpa: Attacking machine learning-based malware visualization detection methods via adversarial examples. In Proceedings of the IEEE/ACM International Symposium on Quality of Service, Phoenix, AZ, USA, 24–25 June 2019. [Google Scholar]
- Analiz. Malware Dashboard. 2019. Available online: https://sandbox.anlyz.io/dashboard (accessed on 2 November 2019).
- Malwr. 2019. Available online: http://malwr.com/ (accessed on 2 November 2019).
- Threat Analyzer. Automated Threat Analysis. 2019. Available online: https://www.threattrack.com/malware-analysis.aspx (accessed on 2 November 2019).
- Pafish. 2019. Available online: https://github.com/a0rtega/pafish (accessed on 2 November 2019).
- Gómez Ramos, F.; Bermejo, J. We must simulate to improve our Cyber Defense. J. Atenea 2012, 35, 56–60. [Google Scholar]
- Cory, Q.N.; James, E.G. Malware analysis reverse engineering (MARE) methodology & malware defense (M.D.) timeline. In Proceedings of the Information Security Curriculum Development Conference (InfoSecCD ‘10), Kennesaw, GA, USA, October 2010; pp. 8–14. [Google Scholar]
- Rahman, S.; Khan, M.N.A. Review of Live Forensic Analysis Techniques. Int. J. Hybrid Inf. Technol. 2015, 8, 379–388. [Google Scholar] [CrossRef]
- Rafique, M.; Naeem, M.; Khan, A. Exploring Static and Live Digital Forensics: Methods, Practices and Tools. Computer Science: USA. 2013. Available online: https://www.semanticscholar.org/paper/Exploring-Static-and-Live-Digital-Forensics%3A-and-Rafique-Khan/45e51f18c4e8157836bb936997293adeced32a24 (accessed on 2 November 2019).
- Coryn, C.L. The fundamental characteristics of research. J. Multidiscip. Eval. 2007, 3, 124–133. [Google Scholar]
- Demeyer, S. Research Methods in Computer Science. In Proceedings of the IEEE 27th International Conference on Software Maintenance, ICSM 2011, Williamsburg, VA, USA, 25–30 September 2011. [Google Scholar]
- Runeson, P.; Höst, M. Guidelines for conducting and reporting case study research in software engineering. Empir. Softw. Eng. J. 2009, 14. [Google Scholar] [CrossRef]
- sKyWIper Analysis Team. A Complex Malware for Targeted Attacks. In Laboratory of Cryptography and System Security (CrySyS Lab); Budapest University of Technology and Economics: Budapest, Hungary, 2012. [Google Scholar]
- Kaspersky Labs. “Global Research & Analysis Team. Red October” Diplomatic Cyber Attacks Investigation”. 2013. Available online: https://securelist.com/analysis/36740/red-october-diplomatic-cyber-attacks-investigation/ (accessed on 2 November 2019).
- Christopher, C.E. Advanced Malware Analysis; McGraw-Hill Education: Pennsylvania Plaza, NY, USA, 2015; ISBN 978-0-07-181975-6. [Google Scholar]














| Malware Analysis Tool |
|---|
| Identification and classification of binary |
| Antivirus engines |
| String analysis |
| Analysis of changes in host machine |
| Traffic analysis and simulation of network services |
| Analysis disk images |
| Memory analysis |
| Analysis of binary files |
| Dynamic code analysis |
| Static code analysis |
| Objectives Malware Analysis | |
|---|---|
| Analysis Summary |
|
| Classification |
|
| Features |
|
| Dependencies |
|
| Conclusions code analysis and behavior |
|
| Support Elements |
|
| Incident Recommendations |
|
| Information to Obtain in Classification Step | ||
|---|---|---|
| MD5 Hash of binary file | Text strings | Number of sections in the section table |
| Hash MD5 PE sections | Protocol | Type of application |
| Hexadecimal signatures | IP Addresses | Required libraries |
| File metadata signatures | Password | Space requirements |
| Signature Patterns | M & C Commands | |
| Icon signatures | Archives | |
| PE file metadata strings | Techniques obfuscation used | |
| Malware families | Type of packaging | |
| Percentage of similarity between two different types of malware | Base address of the file | |
| Data in open sources | Address of point of entry | |
| Information to Obtain in Code Analysis Step |
|---|
| Information for running the malware. |
| Installation information. |
| Execution command. |
| Passwords. |
| Command and control commands. |
| Other execution routes, etc. |
| IRC channel and connection password. |
| Information to avoid operating restrictions in virtual environments. |
| Hidden functionalities. |
| Compression of the operation of the malware. |
| Information to obtain in Behavioral Analysis Step | |
|---|---|
| Detection of file system changes | Memory analysis: |
| Access to files | • Process |
| Changes in the registry | • Active Connections |
| Access to the register | • Mapped files |
| DNS queries | • Drivers |
| Command and control orders | • Executable |
| Start byte of a socket | • Files |
| Network traffic | • Cache Objects |
| Downloading files from the Internet | • Web Addresses • Text strings |
| • Passwords | |
| Victim | Monitor and Windows Services | Services | |
|---|---|---|---|
| WinMD5 | PEViewer | Md5sum | Netcat |
| Md5sum | Process Monitor | WinMD5 | HTTP Apache |
| Strings | RegShot | Strings | Aplicación FTP |
| BinText. | PeStudio | PEiD | Fake DNS |
| Avira | VMMap | Dependency Walker | Inetsim |
| Process Explorer | Systracer | PEBrowse | AVG |
| PEiD | DiskPulse | Ollydbg | F-prot |
| Dependency Walker | GMER | PE Explorer | Binwalk |
| Ollydbg | Winpmem | Wireshark | Volatility |
| PE Explorer | Wireshark | Foremost | |
| IDA Pro | |||
| File Name | File Size | MD5 |
|---|---|---|
| red_oct.document.exploit | 547 KB | bb2f6240402f765a9d0d650b79cd2560 |
| red_oct.bin.drop | 521 KB | 598ce670b5e4be42966dbfae18188792 |
| Entity | Detection |
|---|---|
| Avast | XLS:CVE-2009-3129 [Expl] |
| Kaspersky | Trojan-Dropper.MSWord.Agent.ga |
| TrendMicro | TROJ_OLEXP.B |
| Fortinet | MSExcel/CVE_2009_3129.A!exploit |
| McAfee-GW-Edition | Heuristic.BehavesLike.Exploit.X97.CodeExec.O |
| Microsoft | Exploit:Win32/CVE-2009-3129 |
| Ad-Aware | Exploit.CVE-2009-3129.Gen |
| BitDefender | Exploit.CVE-2009-3129.Gen |
| McAfee | Exploit-MSExcel.ac |
| AVG | Dropper.Generic_c.NZR |
| Symantec | Backdoor.Rocra |
| ClamAV | NO |
| Panda | NO |
| File Name | File Size | MD5 |
|---|---|---|
| mssecmgr.ocx.orig | 6.166528 MB | bdc9e04388bda8527b398a8c34667e180 |
| File | Entropy | Initial Content | Decoded |
|---|---|---|---|
| advnetcfg.ocx | 0.46 | PE32 executable | N/A |
| boot32drv.sys | 0.32 | Data encoded/encrypted | YES |
| ccalc32.sys | 1.00 | Data encoded/encrypted | NO |
| ~dra61.tmp | 1.01 | Data encoded/encrypted | NO |
| dstrlog.dat | 0.03 | Data encoded/encrypted | YES |
| Ef_trace.log | 0.56 | Data encoded/encrypted | NO |
| File “.” inside USB | 0.26 | Data encoded/encrypted | YES |
| ~HLV084.tmp | 1.00 | Data encoded/encrypted | NO |
| ~HLV294.tmp | 1.00 | Data encoded/encrypted | NO |
| ~HLV473.tmp | 0.98 | Data encoded/encrypted | YES |
| ~HLV927.tmp | 0.14 | Data encoded/encrypted | NO |
| ~KWI988.tmp | 0.86 | Data encoded/encrypted | NO |
| ~KWI989.tmp | 1.00 | Data encoded/encrypted | NO |
| lmcache.dat | 0.97 | Data encoded/encrypted | YES |
| mscrypt.dat | 0.53 | Data encoded/encrypted | YES |
| msglu32.ocx | 0.51 | PE32 executable | N/A |
| mssecmgr.ocx | 0.70 | PE32 executable | N/A |
| ntcache.dat | 0.70 | Data encoded/encrypted | YES |
| nteps32.ocx | 0.45 | PE32 executable | N/A |
| rccache.dat | - | Empty (0 bytes) | N/A |
| ~rf288h.tmp | 0.33 | Data encoded/encrypted | YES |
| ~rf288.tmp | 0.04 | Data encoded/encrypted | YES |
| ssitable | 0.03 | Data encoded/encrypted | YES |
| Algorithm | Files Detected |
|---|---|
| XOR 0xFF | boot32drv.sys |
| Transposition by table | dstrlog.dat lmcache.dat mscrypt.dat ntcache.dat ~rf288h.tmp ~rf288.tmp ssitable Fichero “.” |
| Zlib | ~HLV473.tmp |
| Name | Size (bytes) | Name | Size (bytes) |
|---|---|---|---|
| dstrlog.dat | 86,016 | soapr32.ocx | 200,000 |
| lmcache.dat | 0 | ~HLV084.tmp | 1604 |
| mscrypt.dat | 6,163,261 | ~HLV473.tmp | 85 |
| ntcache.dat | 38,400 | ~HLV927.tmp | 85 |
| rccache.dat | 0 | ~HLV294.tmp | 200,000 |
| ssitable | 1,572,896 | ~HLV927.tmp | |
| Ef_trace.log | 858 | ~KWI988.tmp | |
| advnetcfg.ocx | 643,072 | ~dra53.tmp | |
| boot32drv.sys | 1300 | ~mso2a0.tmp | |
| ccalc32.sys | 53,534 | ~mso2a2.tmp | |
| msglu32.ocx | 1,721,856 | ~rf288h.tmp | |
| mssecmgr.ocx | 6,166,528 | ~rf288.tmp | |
| nteps32.ocx | 827,392 | ~HLV084.tmp | 1604 |
| Initial Actions | Classification | Dynamic Code Analysis | Static Code Analysis | Behavior Analysis | |
|---|---|---|---|---|---|
| Flame | C | C | C | P | C |
| Red October | C | C | C | C | C |
| Stuxnet | C | C | C | P | P |
| Dark Comet | C | C | C | C | C |
| Poison Ivy | C | C | C | C | C |
| Locky | C | C | C | C | C |
| Careto | C | C | C | C | P |
| Wannacry | C | C | C | C | P |
| Sofacy Carberp | C | C | P | P | C |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bermejo Higuera, J.; Abad Aramburu, C.; Bermejo Higuera, J.-R.; Sicilia Urban, M.A.; Sicilia Montalvo, J.A. Systematic Approach to Malware Analysis (SAMA). Appl. Sci. 2020, 10, 1360. https://doi.org/10.3390/app10041360
Bermejo Higuera J, Abad Aramburu C, Bermejo Higuera J-R, Sicilia Urban MA, Sicilia Montalvo JA. Systematic Approach to Malware Analysis (SAMA). Applied Sciences. 2020; 10(4):1360. https://doi.org/10.3390/app10041360
Chicago/Turabian StyleBermejo Higuera, Javier, Carlos Abad Aramburu, Juan-Ramón Bermejo Higuera, Miguel Angel Sicilia Urban, and Juan Antonio Sicilia Montalvo. 2020. "Systematic Approach to Malware Analysis (SAMA)" Applied Sciences 10, no. 4: 1360. https://doi.org/10.3390/app10041360
APA StyleBermejo Higuera, J., Abad Aramburu, C., Bermejo Higuera, J.-R., Sicilia Urban, M. A., & Sicilia Montalvo, J. A. (2020). Systematic Approach to Malware Analysis (SAMA). Applied Sciences, 10(4), 1360. https://doi.org/10.3390/app10041360






