Privacy-Preserving Lightweight Authentication Protocol for Demand Response Management in Smart Grid Environment
Abstract
:1. Introduction
- Secure and efficient authentication and key agreement protocols are essential to ensure secure communication and privacy.
- The proposed authentication and key agreement protocol must withstand various attacks such as replay, masquerade, and off-line identity guessing attacks.
- Authentication and key agreement protocol should consider SG device limitations with respect to power consumption, communication bandwidth, and memory.
1.1. Adversary Model
- Trusted authority (TA) and UCs are assumed to be fully trusted and semi-trusted entities, respectively, and cannot be compromised by a malicious adversary.
1.2. Contributions
- We demonstrate that Kumar et al.’s protocol cannot withstand various attacks such as masquerade, SG devices stolen, and session key disclosure attacks. We also show that their protocol does not ensure secure mutual authentication.
- We present a privacy-preserving lightweight authentication protocol for the SG system using pseudo-identity and secret parameter to enhance the security weaknesses of Kumar et al.’s protocol. The proposed protocol can withstand against masquerade, session key disclosure, replay, and MITM attacks, as well as achieve secure mutual authentication and anonymity. Thus, the proposed protocol is more secure and efficient than Kumar et al.’s protocol because it utilizes only hash and XOR operations.
- We performed the widely known Burrows–Abadi–Needham (BAN) logic analysis [13] to prove that the proposed scheme provides secure mutual authentication. We utilized informal security analysis to prove the safety of the proposed protocol against potential attacks and also proved the session key security of proposed scheme utilizing ROR model [14].
- We performed formal security analysis utilizing the widely adopted Automated Validation of Internet Security Protocols and Applications (AVISPA) tool to evaluate that the proposed scheme is secure against replay and MITM attacks. Moreover, we present the performance analysis of the proposed protocol with existing protocols.
1.3. Organization
2. Related Works
3. System Model
4. Review of Kumar et al.’s Protocol
4.1. Smart Grid Device Registration Process
4.2. Utility Center Registration Process
4.3. Authentication Process
- Step 1:
- chooses a random number and generates a current timestamp . After that, computes and and sends authentication request message to the over insecure channel.
- Step 2:
- After receiving the message, checks , where is maximum transmission delay bound and is current timestamp. If the condition is valid, computes utilizing the corresponding of stored in the database.
- Step 3:
- then generates timestamp and a random number , and calculates , , the session key shared with as , and . After that, sends the authentication message to the over insecure channel.
- Step 4:
- After receiving the message, checks condition . If it is correct, further calculates , and session key shared with as , . If the condition , aborts communication. Otherwise, generates a timestamp and calculates . After that, sends acknowledgment message to the over insecure channel.
- Step 5:
- After receiving the message, checks the condition . If the condition is valid, computes and checks if holds. If the condition is valid, and store the common session key .
4.4. Dynamic Smart Grid Device Addition Process
- Step 1:
- Trusted authority selects an identity and calculates and .
- Step 2:
- After that, the pre-loads the data in the memory before it is deployed.
- Step 3:
- sends data for to all over secure channel. The needs to broadcast messages to the deployed regarding deployment of the so that and deployed can establish a common session key after mutual authentication.
4.5. Dynamic Utility Center Addition Process
- Step 1:
- The selects a identity and calculates and .
- Step 2:
- then pre-loads the data in the memory before it is deployed.
- Step 3:
- If a is already deployment prior to , pre-loads into the memory of .
5. Cryptanalysis of Kumar et al.’s Protocol
5.1. Masquerade Attack
- Step 1:
- generates a random number and calculates , . After that, sends message to over insecure channel.
- Step 2:
- After receiving the message from , checks . If the condition is valid, calculates and generates a timestamp . then selects a random number and computes , , , , and . After that, sends the message to .
- Step 3:
- After receiving the message from , checks condition . If the condition is valid, computes , , and . Then, generates a timestamp and computes . After that, sends message to over insecure channel.
- Step 4:
- After receiving the message from , checks condition . If the condition is valid, calculates and checks if holds. If the condition is valid, and store session key .
5.2. Smart Grid Device Stolen Attack
5.3. Session Key Disclosure Attack
5.4. Mutual Authentication
6. Proposed Scheme
6.1. Pre-Deployment Process
6.2. Smart Grid Device Registration Process
- Step 1:
- generates a random number for . After that, computes , , , and and stores in secure database. Finally, sends to .
- Step 2:
- After receiving the message, computes and stores in the memory.
6.3. Utility Center Registration Process
- Step 1:
- computes and retrieves in secure database. Then, computes and sends to .
- Step 2:
- After receiving the message, computes and stores in the database.
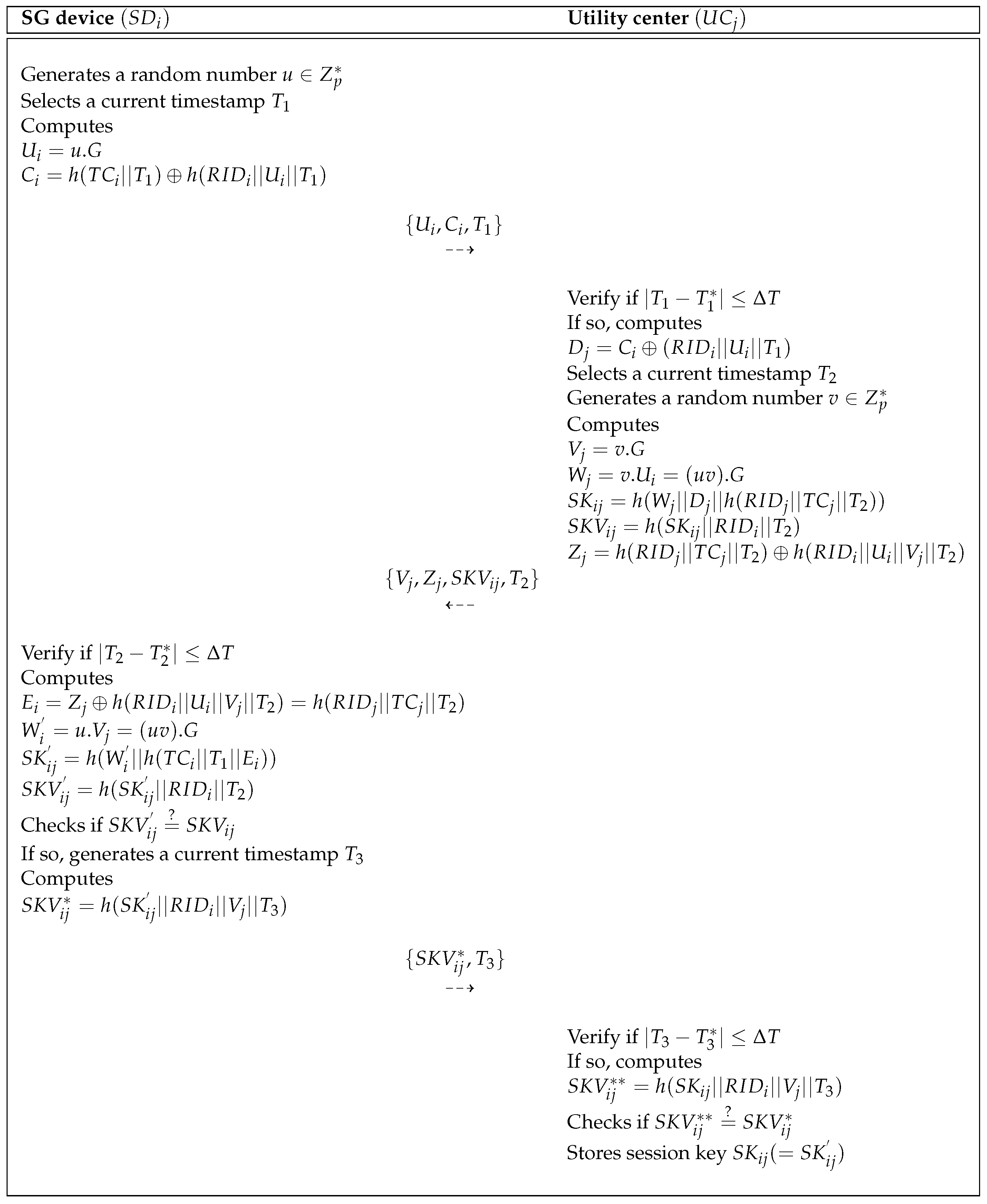
6.4. Authentication Process
- Step 1:
- computes , , , and . Then, checks whether . If the condition is valid, generates a random nonce and computes , , and . After that, sends authentication request message to over insecure channel.
- Step 2:
- After receiving the message from , retrieves in database and calculates , , and . Then, retrieves corresponding in database and checks whether . If the condition is valid, calculates and checks whether . If the condition is correct, generates a random nonce and computes , , and . Finally, sends authentication message to over insecure channel.
- Step 3:
- After receiving the message from , computes , , , and . After that, checks whether . If the condition is correct, the and achieve mutual authentication successfully.
6.5. Dynamic Smart Grid Device Addition Process
- Step 1:
- First, chooses a new to the over secure channel. After receiving the message, sends to the over secure channel. Then, generates a random number .
- Step 2:
- After that, computes , , , and . Finally, stores in secure database and sends its to the over secure channel.
- Step 3:
- After receiving the message, computes and stores in the memory.
6.6. Dynamic Utility Center Addition Process
- Step 1:
- The chooses a new and sends to over secure channel. After receiving the message, sends to the over secure channel. After that, computes and retrieves in the database.
- Step 2:
- Then, computes and sends to the .
- Step 3:
- After receiving the message, computes and stores in secure database.
7. Security Analysis
7.1. Informal Security Analysis
7.1.1. Masquerade Attack
7.1.2. Smart Grid Device Stolen Attack
7.1.3. Replay Attack
7.1.4. Session key disclosure attack
7.1.5. Insider attack
7.1.6. Mutual Authentication
7.1.7. Anonymity
7.2. Security Features
7.3. Formal Security Analysis Using BAN Logic
7.3.1. BAN Logic Rule
- Message meaning rule:
- Nonce verification rule:
- Jurisdiction rule:
- Freshness rule:
- Belief rule:
7.3.2. Goals
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
7.3.3. Idealized Forms
- :
- :
- :
- :
7.3.4. Assumptions
- :
- :
- :
- :
- :
- :
- :
- :
7.3.5. Proof Using BAN Logic
- Step 1:
- According to , we obtain
- Step 2:
- Using the message meaning rule with and , we can obtain
- Step 3:
- Using the freshness rule with , we can obtain
- Step 4:
- From the nonce verification rule with and , we can obtain
- Step 5:
- Using the belief rule with , we can obtain
- Step 6:
- Because of , from the and we can obtain
- Step 7:
- From the jurisdiction rule with and we can obtain
- Step 8:
- According to , we can obtain
- Step 9:
- Using the message meaning rule with and , we can obtain
- Step 10:
- Using the freshness rule with , we can obtain
- Step 11:
- Using the nonce verification rule with and , we can obtain
- Step 12:
- Using the belief rule with , we can obtain
- Step 13:
- Because of , from the and we can obtain
- Step 14:
- Using the jurisdiction rule with and we can obtain
7.4. Formal Security Analysis Using ROR Model
- Game: This game is the initial game in which selects the random bit c. In addition, this game denotes actual attack of for the protocol and c is guessed at the beginning of . According to this game, we can get,
- Game: This game denotes that performs an eavesdropping attack, in which it intercepts all transmitted messages and during authentication process utilizing query. Once the game ends, sends and queries. The output of the and queries decide if obtains random numbers and shared session key between and . To derive , needs secret information , , and . Thus, and are indistinguishable because the winning probability of is not increased. We then get,
- Game: In this game, the and queries are simulated. This game is modeled as an active attack, in which a malicious attacker eavesdrops all transmitted messages and during authentication process. All transmitted messages in authentication process are protected by utilizing the collision-resistant one-way hash function . In addition, random numbers and are used in the messages and . However, and are not derived from all transmitted messages due to the collision-resistant one-way hash function . makes and sends query, and then we can get the result using birthday paradox.
- Game: In this the final game, the query is simulated. Hence, a malicious attacker can extract the credential informations from memory of the SG device using power-analysis attack. Note that , and . It is computationally infeasible for to derive identity of correctly via the queries without ’s master key and secret parameter . As a result, and are indistinguishable if identity guessing attack is not implemented. Consequently, utilizing Zipf’s law [29], we can get the result as below:As all the games are executed, can only guess the exact bit c. Thus, we can get as below:Using Equations (1), (2), and (5), we can get the result as below:Using Equations (4)–(6), we obtain the result utilizing the triangular inequality as below:Finally, we obtain the required result by multiplying both sides of Equation (7) by a factor of 2.
7.5. Formal Security Analysis Using AVISPA
7.5.1. Detailed Specification of Roles
7.5.2. Results of AVISPA Analysis
8. Performance Analysis
8.1. Computation Overhead
8.2. Communication Overhead
8.3. Storage Overhead
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Park, Y.H.; Park, Y.H. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
- Tonyali, S.; Akkaya, K.; Saputro, N.; Uluagac, A.S.; Nojoumian, M. Privacy–preserving protocols for secure and reliable data aggregation in IoT–enabled Smart Metering systems. Future Gener. Comput. Syst. 2018, 78, 547–557. [Google Scholar] [CrossRef]
- Braeken, A.; Kumar, P.; Martin, A. Efficient and Privacy-Preserving Data Aggregation and Dynamic Billing in Smart Grid Metering Networks. Energies 2018, 11, 2085. [Google Scholar] [CrossRef] [Green Version]
- Kumar, P.; Gurtov, A.; Sain, M.; Martin, A.; Ha, P.H. Lightweight authentication and key agreement for smart metering in smart energy networks. IEEE Trans. Smart Grid 2019, 10, 4349–4359. [Google Scholar] [CrossRef] [Green Version]
- Department of Energy. Exploring the Imperative of Revitalizing America’s Electric Infrastructure. February 2017. Available online: https://www.energy.gov/sites/prod/files/oeprod/DocumentsandMedia/DOE_SG_Book_Single_Pages.pdf (accessed on 3 February 2020).
- Kumar, N.; Aujla, G.S.; Das, A.K.; Conti, M. ECCAuth: Secure authentication protocol for demand response management in smart grid systems. IEEE Trans. Ind. Inform. 2019, 15, 6572–6582. [Google Scholar] [CrossRef]
- Desai, S.; Alhadad, R.; Chilamkurti, N.; Mahmood, A. A survey of privacy preserving schemes in IoE enabled smart grid advanced metering infrastructure. Clust. Comput. 2019, 22, 43–69. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology—CRYPTO; Lecture Notes in Computer Science; Springer: Santa Barbara, CA, USA, 1999; pp. 388–397. [Google Scholar]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2012, 51, 541–552. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.Y.; Yu, S.J.; Park, K.S.; Park, Y.H.; Park, Y.H. Secure three-factor authentication protocol for multi-gateway IoT environments. Sensors 2019, 19, 2358. [Google Scholar] [CrossRef] [Green Version]
- Yu, S.J.; Park, K.S.; Park, Y.H. A secure lightweight three–factor authentication scheme for IoT in cloud computing environment. Sensors 2019, 19, 3598. [Google Scholar] [CrossRef] [Green Version]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password based authenticated key exchange in the three-party setting. In Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; pp. 65–84.
- Rottondi, C.; Fontana, S.; Verticale, G. Enabling privacy in vehicle-to-grid interactions for battery recharging. Energies 2014, 7, 2780–2798. [Google Scholar] [CrossRef] [Green Version]
- Jiang, Q.; Khan, M.K.; Lu, X.; Ma, J.; He, D. A privacy preserving three–factor authentication protocol for e-Health clouds. J. Supercomput. 2016, 72, 3826–3849. [Google Scholar] [CrossRef]
- Wan, Z.; Zhu, W.T.; Wang, G. PRAC: Efficient privacy protection for vehicle-to-grid communications in the smart grid. Comput. Secur. 2016, 62, 246–256. [Google Scholar] [CrossRef]
- Jo, H.J.; Kim, I.S.; Lee, D.H. Efficient and privacy-preserving metering protocols for smart grid systems. IEEE Trans. Smart Grid 2016, 7, 1732–1742. [Google Scholar] [CrossRef]
- Mahmood, K.; Chaudhry, S.A.; Naqvi, H.; Kumari, S.; Li, X.; Sangaiahm, A.K. An elliptic curve cryptography based lightweight authentication scheme for smart grid communication. Future Gener. Comput. Syst. 2018, 81, 557–565. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W. Secure anonymous key distribution scheme for smart grid. IEEE Trans. Smart Grid 2016, 7, 906–914. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Wazid, M.; Conti, M. Provably secure authenticated key agreement scheme for smart grid. IEEE Trans. Smart Grid 2016, 9, 1900–1910. [Google Scholar] [CrossRef]
- Doh, I.; Lim, J.; Chae, K. Secure authentication for structured smart grid system. In Proceedings of the International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS’15), Fukuoka, Japan, 8–10 July 2015; pp. 200–204. [Google Scholar]
- Saxena, N.; Choi, B.J.; Lu, R. Authentication and authorization scheme for various user roles and devices in smart grid. IEEE Trans. Inf. Forensics Secur. 2016, 11, 907–921. [Google Scholar] [CrossRef] [Green Version]
- He, D.; Wang, H.; Khan, M.K.; Wang, L. Lightweight anonymous key distribution scheme for smart grid using elliptic curve cryptography. IET Commun. 2016, 10, 1795–1802. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Rodrigues, J.P.C. Secure three-factor user authentication scheme for renewable energy based smart grid environment. IEEE Trans. Ind. Inform. 2017, 13, 3144–3153. [Google Scholar] [CrossRef]
- Weaver, K. A Perspective on How Smart Meters Invade Individual Privacy. 2014. Available online: https://skyvisionsolutions.files.wordpress.com/2014/08/utility-smart-meters-invade-privacy-22-aug-2014.pdf (accessed on 3 February 2020).
- Finster, S.; Baumgart, I. Privacy-aware smart metering: A survey. IEEE Commun. Surv. Tutor. 2015, 17, 1088–1101. [Google Scholar] [CrossRef]
- Wu, D.; Zhou, C. Fault-tolerant and scalable key management for smart grid. IEEE Trans. Smart Grid 2011, 2, 375–381. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Park, K.S.; Park, Y.H.; Park, Y.H.; Das, A.K. 2PAKEP: Provably secure and efficient two-party authenticated key exchange protocol for mobile environment. IEEE Access 2018, 6, 30225–30241. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V. Design of secure key management and user authentication scheme for fog computing services. Future Gener. Comput. Syst. 2019, 91, 475–492. [Google Scholar] [CrossRef]
- Das, A.K.; Wazid, M.; Kumar, N.; Khan, M.K.; Choo, K.K.R.; Park, Y.H. Design of secure and lightweight authentication protocol for wearable devices environment. IEEE J. Biomed. Health Inform. 2018, 22, 1310–1322. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J. TCALAS: Temporal credential based anonymous lightweight authentication scheme for internet of drones environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Tseng, Y.M.; Huang, S.S.; Tsai, T.T.; Ke, J.H. List-free id-based mutual authentication and key agreement protocol for multi-server architectures. IEEE Trans. Emerg. Top. Comput. 2016, 4, 102–112. [Google Scholar] [CrossRef]












| Notation | Description |
|---|---|
| Trusted authority | |
| device | |
| ’s identity | |
| ’s pseudo-identity | |
| Utility center or remote control center | |
| ’s identity | |
| Temporal credential | |
| Timestamp | |
| A nonsingular elliptic curve (mod p) | |
| G | A base point for elliptic curve |
| An elliptic curve point multiplication | |
| The public key for and | |
| x | ’s secret key |
| ’s master key | |
| Session key | |
| Hash function | |
| ⊕ | XOR operation |
| Concatenation operation |
| Security Feature | Wu–Zhou [28] | Tsai–Lo [20] | Odelu et al. [21] | Kumar et al. [6] | Ours |
|---|---|---|---|---|---|
| Masquerade attack | ∘ | ∘ | ∘ | × | ∘ |
| Smart grid device stolen attack | ∘ | ∘ | ∘ | × | ∘ |
| Replay attack | ∘ | ∘ | ∘ | ∘ | ∘ |
| Session key disclosure attack | × | × | ∘ | × | ∘ |
| Man-in-the-middle attack | ∘ | ∘ | ∘ | ∘ | ∘ |
| Mutual authentication | ∘ | ∘ | ∘ | × | ∘ |
| Anonymity | × | ∘ | ∘ | ∘ | ∘ |
| Dynamic node addition phase | × | × | × | ∘ | ∘ |
| Notation | Description |
|---|---|
| Qbelieves statement M | |
| Statement M is fresh | |
| Qsees statement M | |
| Q once said M | |
| Qcontrols statement M | |
| Formula M is combined with formula N | |
| Formula M is encrypted by key K | |
| Session key used in the current authentication session | |
| Q and W communicate utilizing K as the shared key |
| Query | Description |
|---|---|
| This query denotes that can eavesdrop transmitted messages between and over insecure channel. This query is modeled as an eavesdropping attack. | |
| This corrupt SG device query means that can extract sensitive information stored in the SG device utilizing power-analysis attack. This query is modeled as an active attack. | |
| This query denotes that can transmit message M to and can also receive the corresponding message from . This query is modeled as an active attack. | |
| This query means that an unbiased coin c is first flipped before the experiment begins and its output is used as a decider. execute this query and if session key between and is fresh, returns if or a random number when . Otherwise, it returns the null value ⊥. | |
| The query means that can compromise between and its partner in the current session. |
| Entity | |||||
|---|---|---|---|---|---|
| Pentium IV | ms | ms | ms | <1 ms | ms |
| HiPerSmart Card | s | s | s | <0.1 s | s |
| Schemes | Total Computation Cost |
|---|---|
| Wu–Zhou [28] | ms |
| Tsai–Lo [20] | ms |
| Odelu et al. [21] | ms |
| Kumar et al. [6] | ms |
| Ours | ms |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, S.; Park, K.; Lee, J.; Park, Y.; Park, Y.; Lee, S.; Chung, B. Privacy-Preserving Lightweight Authentication Protocol for Demand Response Management in Smart Grid Environment. Appl. Sci. 2020, 10, 1758. https://doi.org/10.3390/app10051758
Yu S, Park K, Lee J, Park Y, Park Y, Lee S, Chung B. Privacy-Preserving Lightweight Authentication Protocol for Demand Response Management in Smart Grid Environment. Applied Sciences. 2020; 10(5):1758. https://doi.org/10.3390/app10051758
Chicago/Turabian StyleYu, SungJin, KiSung Park, JoonYoung Lee, YoungHo Park, YoHan Park, SangWoo Lee, and BoHeung Chung. 2020. "Privacy-Preserving Lightweight Authentication Protocol for Demand Response Management in Smart Grid Environment" Applied Sciences 10, no. 5: 1758. https://doi.org/10.3390/app10051758







