A Survey on Machine-Learning Based Security Design for Cyber-Physical Systems
Abstract
:1. Introduction
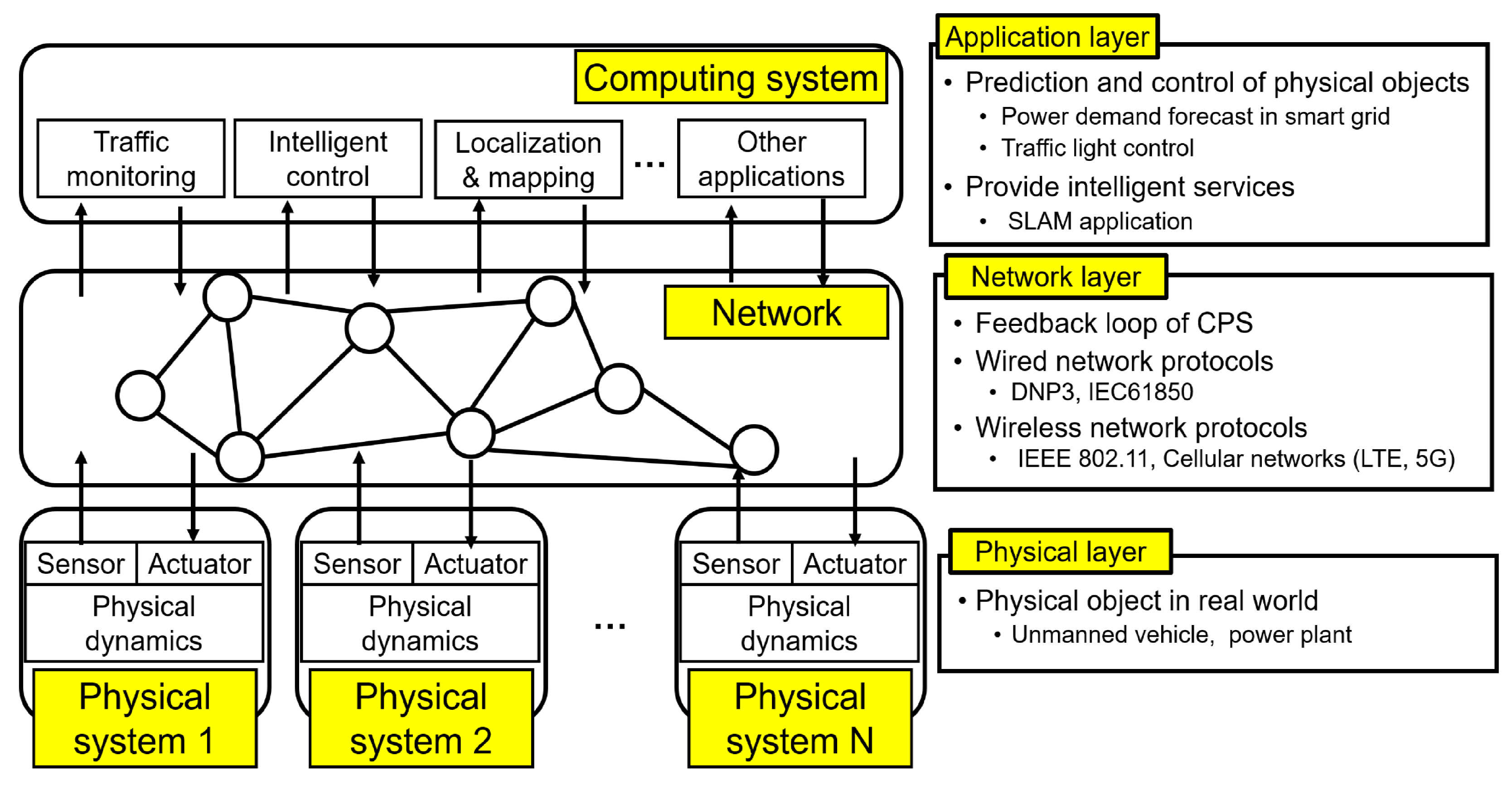
2. Hierarchical Structure of Cyber-Physical Systems
2.1. Physical System Layer
2.2. Network Layer
2.3. Application Layer
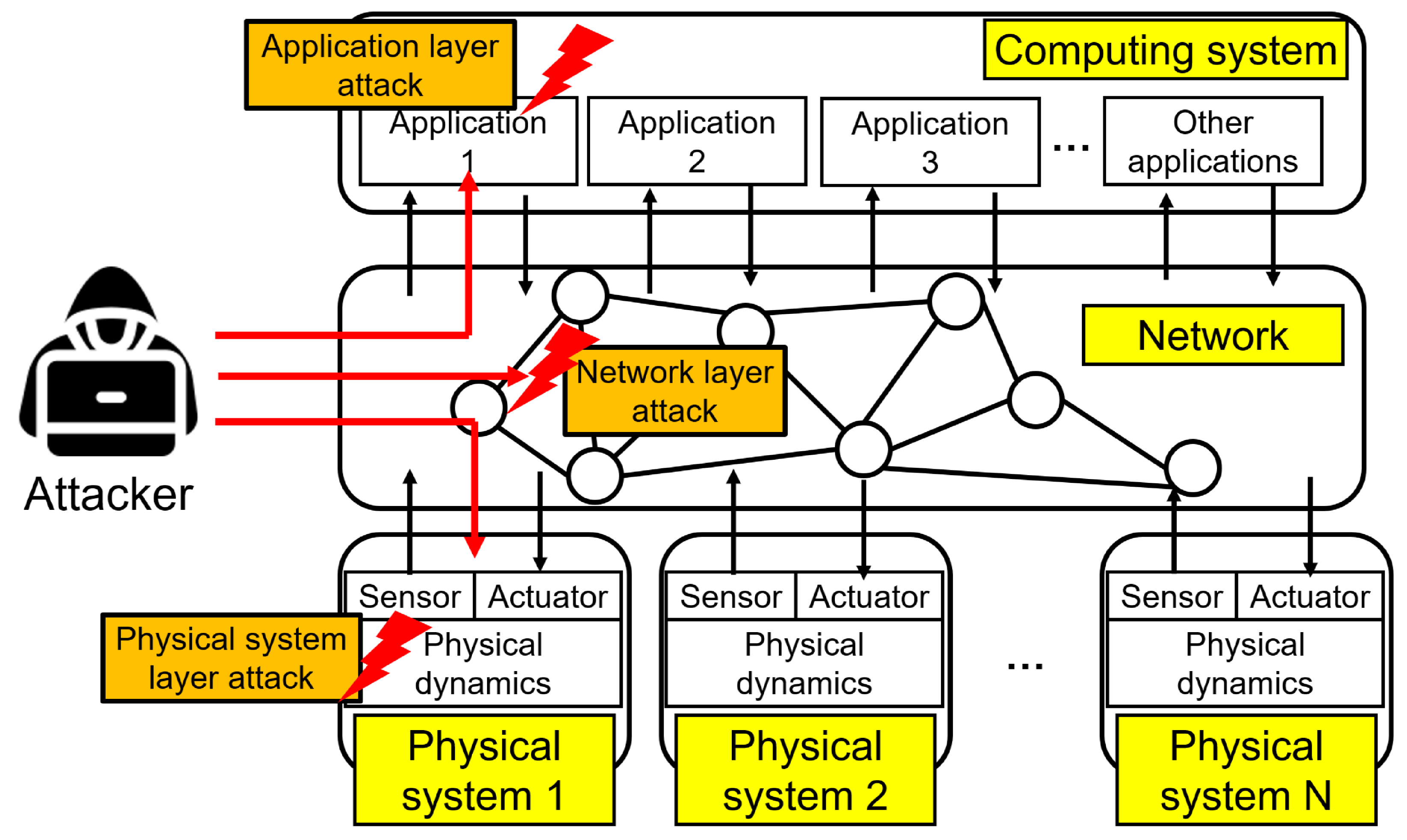
3. Taxonomy of Cyber-Physical Attacks
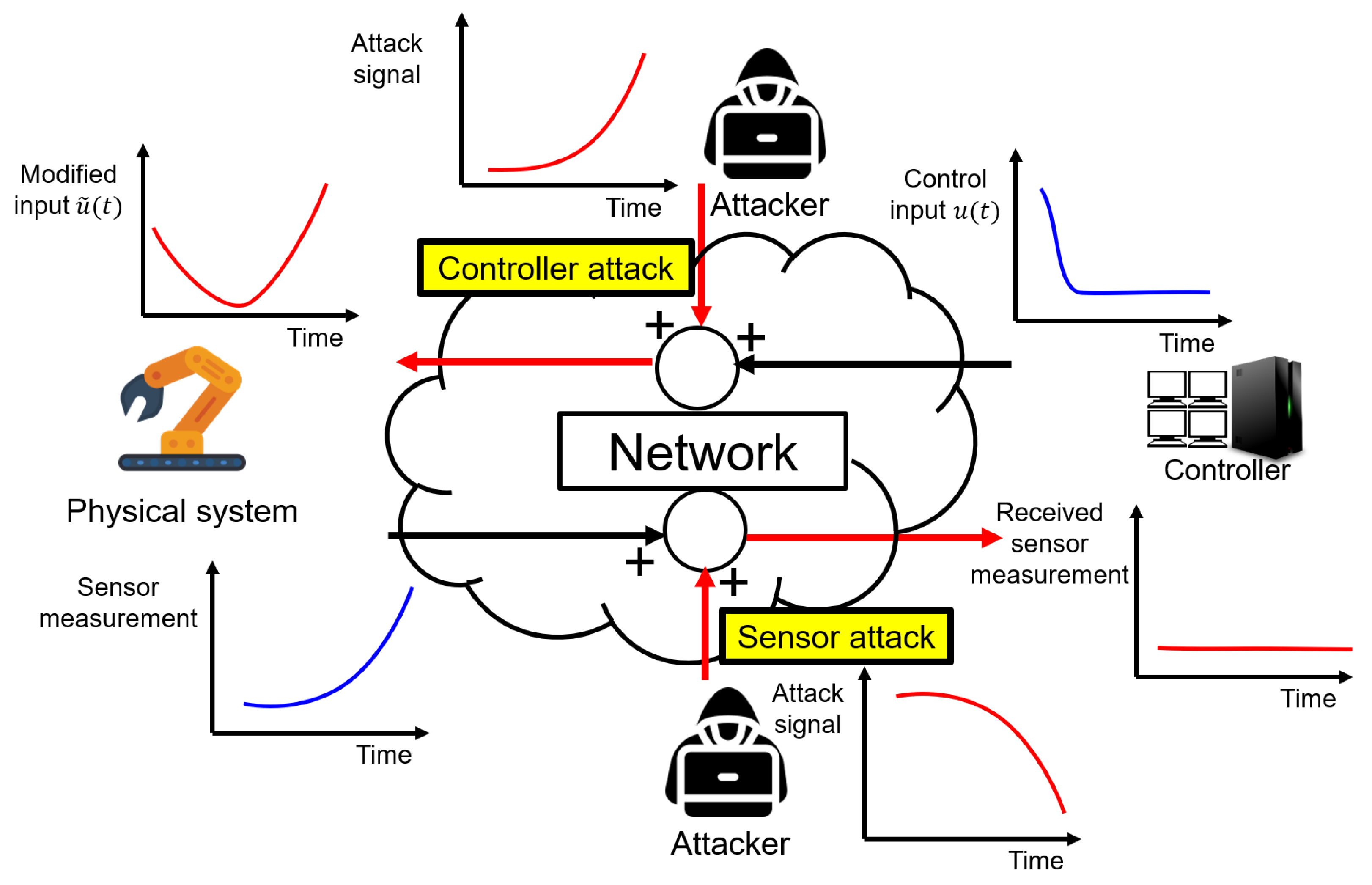
3.1. Physical System Layer
3.1.1. Sensor Attack
3.1.2. Controller Attack
3.1.3. Combined Attack
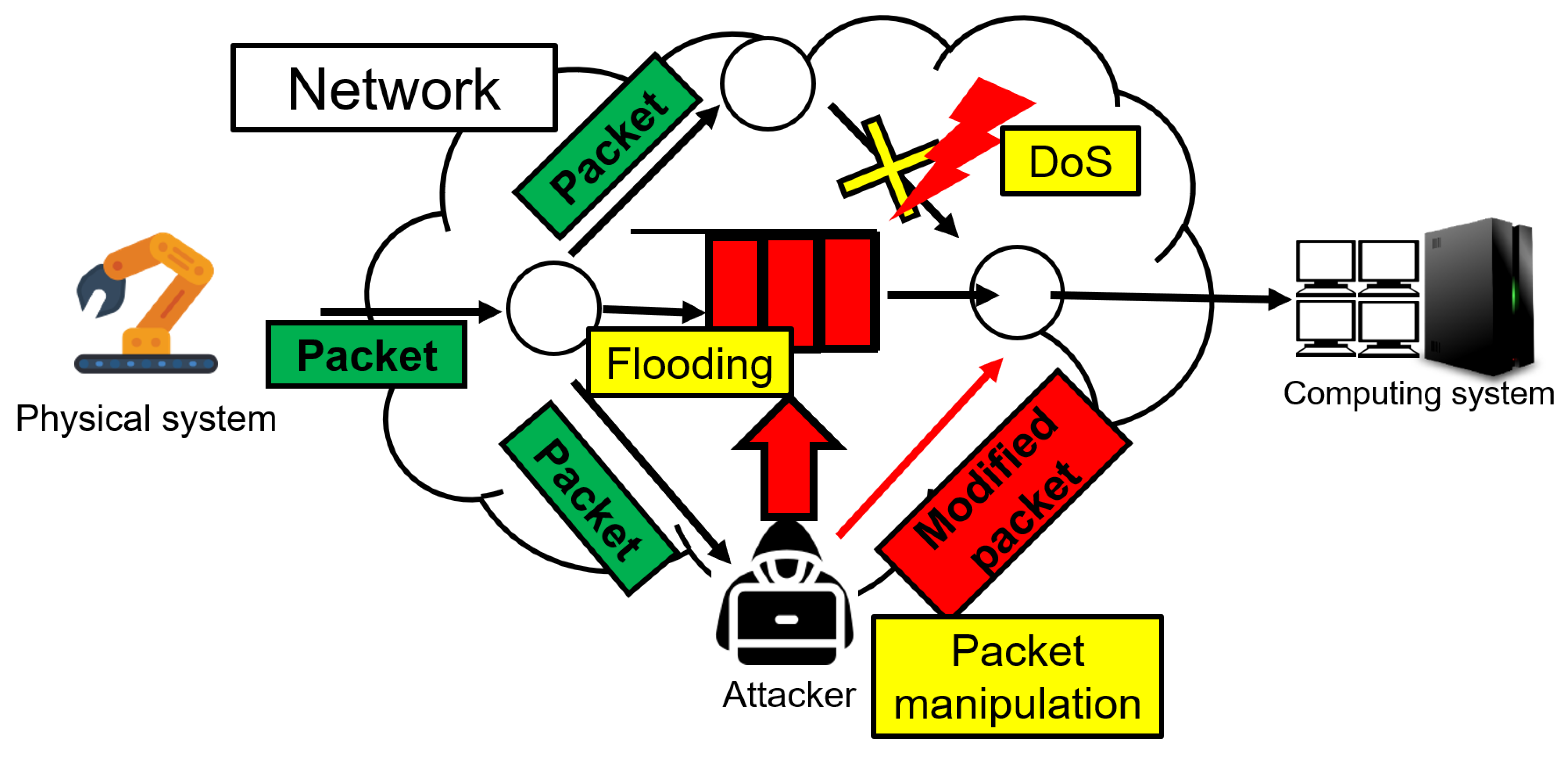
3.2. Network Layer
3.2.1. Denial of Service Attack
3.2.2. Flooding Attack
3.2.3. Packet Manipulation
3.3. Application Layer
3.3.1. Application Software Attack
3.3.2. Computing Hardware Attack
4. ML-Based Cyber-Physical Attack Detection
- Accuracy is defined as the number of correctly classified cases for the entire test dataset, whih is calculated as follows:where is the number of correctly classified anomalies, is the number of samples correctly classified as normal, is the number of normal samples classified as anomalies, and is the number of anomalies wrongly classified as normal.
- Precision is defined as true-positive detection from samples the detector has determined to be abnormal, and is calculated as follows:Precision is related to false-positive detection, which degrades the control performance of physical systems.
- Recall is defined as detection performance with real anomalies, and is calculated as follows:Recall is related to misdetection probability, where a missed detection makes the physical system unstable.
- The F1-score is calculated as the harmonic mean between precision and recall, and is obtained as follows:The F1-score shows the balance between precision and recall in an uneven sample distribution (a large number of normal samples).
4.1. Physical System Layer
4.2. Network Layer
4.3. Application Layer
5. Potential Research Directions
5.1. Real-Time Attack Detection in ML
5.2. Resilient Cyber-Physical System Design
5.3. Dataset Generation for Learning Malicious Behavior
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AODV | Ad-hoc on-demand distance vector |
| ARP | Address resolution protocol |
| CBTC | Communication-based train control |
| CAM | Cooperative awareness message |
| CAN | Control area network |
| CNN | Convolutional neural network |
| CPS | Cyber-physical system |
| CPU | Central processing unit |
| DNN | Deep neural network |
| DoS | Denial of service |
| DRAM | Dynamic random access memory |
| DRE | Density ratio estimation |
| DBN | Dynamic Bayesian network |
| ECU | Electronic control unit |
| FNN | Forward neural network |
| GAN | Generative adversarial network |
| HVAC | Heating, ventilation, and air conditioning |
| IDS | Intrusion detection system |
| KF | Kalman filter |
| KNN | K-nearest neighbor |
| LSTM | Long short-term memory |
| LTE | Long term evolution |
| MAC | Media access control |
| MITM | Man-in-the-middle |
| ML | Machine learning |
| MLP | Multi-layer perceptron |
| NIC | Network interface card |
| PDA | Pole-dynamics attack |
| RAM | Random access memory |
| RSU | Road side unit |
| RNN | Recursive neural network |
| SCADA | Supervisory control and data acquisition |
| SDN | Software-defined networking |
| SLAM | Simultaneous localization and mapping |
| SNR | Signal-to-noise ratio |
| SVM | Support vector machine |
| UAV | Unmanned aerial vehicle |
| VANET | Vehicular ad-hoc network |
| ZDA | Zero-dynamics attack |
References
- Park, K.J.; Zheng, R.; Liu, X. Cyber-physical systems: Milestones and research challenges. Comput. Commun. 2012, 36, 1–7. [Google Scholar] [CrossRef]
- Kim, D.; Won, Y.; Kim, S.; Eun, Y.; Park, K.J.; Johansson, K.H. Sampling rate optimization for IEEE 802.11 wireless control systems. In Proceedings of the ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Montreal, QC, Canada, 16–18 April 2019; pp. 87–96. [Google Scholar]
- Rajkumar, R.; Lee, I.; Sha, L.; Stankovic, J. Cyber-physical systems: The next computing revolution. In Proceedings of the Design Automation Conference, Anaheim, CA, USA, 13–18 June 2010; pp. 731–736. [Google Scholar]
- Kim, K.D.; Kumar, P.R. Cyber–physical systems: A perspective at the centennial. Proc. IEEE 2012, 100, 1287–1308. [Google Scholar]
- Ahlén, A.; Akerberg, J.; Eriksson, M.; Isaksson, A.J.; Iwaki, T.; Johansson, K.H.; Knorn, S.; Lindh, T.; Sandberg, H. Toward wireless control in industrial process automation: A case study at a paper mill. IEEE Control Syst. Mag. 2019, 39, 36–57. [Google Scholar]
- Wang, X.; Liu, L.; Tang, T.; Sun, W. Enhancing communication-based train control systems through train-to-train communications. IEEE Trans. Intell. Transp. Syst. 2019, 20, 1544–1561. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.; Debbah, M. A tutorial on UAVs for wireless networks: Applications, challenges, and open problems. IEEE Commun. Surv. Tutor. 2019, 21, 2334–2360. [Google Scholar] [CrossRef] [Green Version]
- Shumeye Lakew, D.; Sa’ad, U.; Dao, N.; Na, W.; Cho, S. Routing in flying ad hoc networks: A comprehensive survey. IEEE Commun. Surv. Tutor. 2020, 22, 1071–1120. [Google Scholar] [CrossRef]
- Farooq, J.; Soler, J. Radio communication for communications-based train control (CBTC): A tutorial and survey. IEEE Commun. Surv. Tutor. 2017, 19, 1377–1402. [Google Scholar] [CrossRef] [Green Version]
- Cho, B.M.; Jang, M.S.; Park, K.J. Channel-aware congestion control in vehicular cyber-physical systems. IEEE Access 2020, 8, 73193–73203. [Google Scholar] [CrossRef]
- Paranjothi, A.; Khan, M.S.; Zeadally, S. A survey on congestion detection and control in connected vehicles. Ad Hoc Netw. 2020, 108, 102277. [Google Scholar] [CrossRef]
- Meng, W.; Li, W.; Wang, Y.; Au, M.H. Detecting insider attacks in medical cyber–physical networks based on behavioral profiling. Future Gener. Comput. Syst. 2020, 108, 1258–1266. [Google Scholar] [CrossRef]
- Cho, B.M.; Park, K.J.; Park, E.C. Fairness-aware radio resource management for medical interoperability between WBAN and WLAN. Ann. Telecommun. 2016, 71, 441–451. [Google Scholar] [CrossRef]
- Manandhar, K.; Cao, X.; Hu, F.; Liu, Y. Detection of faults and attacks including false data injection attack in smart grid using Kalman filter. IEEE Trans. Control Netw. Syst. 2014, 1, 370–379. [Google Scholar] [CrossRef]
- Rawat, D.B.; Bajracharya, C. Detection of false data injection attacks in smart grid communication systems. IEEE Signal Process. Lett. 2015, 22, 1652–1656. [Google Scholar] [CrossRef]
- Kim, S.; Won, Y.; Park, I.H.; Eun, Y.; Park, K.J. Cyber-physical vulnerability analysis of communication-based train control. IEEE Internet Things J. 2019, 6, 6353–6362. [Google Scholar] [CrossRef]
- Koutsoukos, X. Systems science of secure and resilient cyberphysical systems. Computer 2020, 53, 57–61. [Google Scholar] [CrossRef]
- Teixeira, A.; Pérez, D.; Sandberg, H.; Johansson, K.H. Attack models and scenarios for networked control systems. In Proceedings of the International Conference on High Confidence Networked Systems, Beijing, China, 17–18 April 2012; pp. 55–64. [Google Scholar]
- Khalid, F.; Rehman, S.; Shafique, M. Overview of security for smart cyber-physical systems. In Security of Cyber-Physical Systems; Springer: Berlin/Heidelberg, Germany, 2020; pp. 5–24. [Google Scholar]
- Alladi, T.; Chamola, V.; Zeadally, S. Industrial control systems: Cyberattack trends and countermeasures. Comput. Commun. 2020, 155, 1–8. [Google Scholar] [CrossRef]
- Dibaji, S.M.; Pirani, M.; Flamholz, D.B.; Annaswamy, A.M.; Johansson, K.H.; Chakrabortty, A. A systems and control perspective of CPS security. Annu. Rev. Control 2019, 47, 394–411. [Google Scholar] [CrossRef] [Green Version]
- Shin, J.; Baek, Y.; Lee, J.; Lee, S. Cyber-physical attack detection and recovery based on RNN in automotive brake systems. Appl. Sci. 2019, 9, 82. [Google Scholar] [CrossRef] [Green Version]
- Brunton, S.L.; Kutz, J.N. Data-Driven Science and Engineering: Machine Learning, Dynamical Systems, and Control; Cambridge University Press: Cambridge, CA, USA, 2019; Volume 1. [Google Scholar]
- Isidori, A.; Sontag, E.; Thoma, M. Nonlinear Control Systems; Springer: Berlin/Heidelberg, Germany, 1995; Volume 3. [Google Scholar]
- Olowononi, F.O.; Rawat, D.B.; Liu, C. Resilient machine learning for networked cyber physical systems: A survey for machine learning security to securing machine learning for CPS. IEEE Commun. Surv. Tutor. 2021, 23, 524–552. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Differential privacy techniques for cyber physical systems: A survey. IEEE Commun. Surv. Tutor. 2020, 22, 746–789. [Google Scholar] [CrossRef] [Green Version]
- Giraldo, J.; Urbina, D.; Cardenas, A.; Valente, J.; Faisal, M.; Ruths, J.; Tippenhauer, N.O.; Sandberg, H.; Candell, R. A survey of physics-based attack detection in cyber-physical systems. ACM Comput. Surv. (CSUR) 2018, 51, 1–36. [Google Scholar] [CrossRef]
- Tan, S.; Guerrero, J.M.; Xie, P.; Han, R.; Vasquez, J.C. Brief survey on attack detection methods for cyber-physical systems. IEEE Syst. J. 2020, 14, 5329–5339. [Google Scholar] [CrossRef]
- Alsubhi, K.; Bouabdallah, N.; Boutaba, R. Performance analysis in intrusion detection and prevention systems. In Proceedings of the IFIP/IEEE International Symposium on Integrated Network Management (IM 2011) and Workshops, Dublin, Ireland, 23–27 May 2011; pp. 369–376. [Google Scholar]
- Mitchell, R.; Chen, R. Effect of intrusion detection and response on reliability of cyber physical systems. IEEE Trans. Reliab. 2013, 62, 199–210. [Google Scholar] [CrossRef] [Green Version]
- Mitchell, R.; Chen, I.R. A survey of intrusion detection techniques for cyber-physical systems. ACM Comput. Surv. (CSUR) 2014, 46, 1–29. [Google Scholar] [CrossRef] [Green Version]
- Won, Y.; Yu, B.; Park, J.; Park, I.H.; Jeong, H.; Baik, J.; Kang, K.; Lee, I.; Son, S.H.; Park, K.-J.; et al. An attack-resilient CPS architecture for hierarchical control: A case study on train control systems. Computer 2018, 51, 46–55. [Google Scholar] [CrossRef]
- Aceto, G.; Persico, V.; Pescapé, A. A survey on information and communication technologies for industry 4.0: State-of-the-art, taxonomies, perspectives, and challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3467–3501. [Google Scholar] [CrossRef]
- Fang, X.; Misra, S.; Xue, G.; Yang, D. Smart grid—The new and improved power grid: A survey. IEEE Commun. Surv. Tutor. 2012, 14, 944–980. [Google Scholar] [CrossRef]
- Williams, T.J. The Purdue enterprise reference architecture. Comput. Ind. 1994, 24, 141–158. [Google Scholar] [CrossRef]
- Van Every, P.M.; Rodriguez, M.; Jones, C.B.; Mammoli, A.A.; Martínez-Ramón, M. Advanced detection of HVAC faults using unsupervised SVM novelty detection and Gaussian process models. Energy Build. 2017, 149, 216–224. [Google Scholar] [CrossRef]
- Salinas, S.A.; Li, P. Privacy-preserving energy theft detection in microgrids: A state estimation approach. IEEE Trans. Power Syst. 2016, 31, 883–894. [Google Scholar] [CrossRef]
- Wang, H.; Zhao, H.; Zhang, J.; Ma, D.; Li, J.; Wei, J. Survey on unmanned aerial vehicle networks: A cyber physical system perspective. IEEE Commun. Surv. Tutor. 2020, 22, 1027–1070. [Google Scholar] [CrossRef] [Green Version]
- Peng, T.; Leckie, C.; Ramamohanarao, K. Survey of network-based defense mechanisms countering the DoS and DDoS problems. ACM Comput. Surv. (CSUR) 2007, 39, 3. [Google Scholar] [CrossRef]
- Lou, X.; Tran, C.; Tan, R.; Yau, D.K.; Kalbarczyk, Z.T. Assessing and mitigating impact of time delay attack: A case study for power grid frequency control. In Proceedings of the ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Montreal, QC, Canada, 16–18 April 2019; pp. 207–216. [Google Scholar]
- Cloosterman, M.B.; Van de Wouw, N.; Heemels, W.; Nijmeijer, H. Stability of networked control systems with uncertain time-varying delays. IEEE Trans. Autom. Control 2009, 54, 1575–1580. [Google Scholar] [CrossRef]
- Conti, M.; Dragoni, N.; Lesyk, V. A survey of man in the middle attacks. IEEE Commun. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Jiang, D.; Delgrossi, L. IEEE 802.11p: Towards an international standard for wireless access in vehicular environments. In Proceedings of the VTC Spring 2008-IEEE Vehicular Technology Conference, Marina Bay, Singapore, 11–14 May 2008; pp. 2036–2040. [Google Scholar]
- Naik, G.; Choudhury, B.; Park, J.M. IEEE 802.11bd 5G NR V2X: Evolution of radio access technologies for V2X communications. IEEE Access 2019, 7, 70169–70184. [Google Scholar] [CrossRef]
- Chen, S.; Hu, J.; Shi, Y.; Peng, Y.; Fang, J.; Zhao, R.; Zhao, L. Vehicle-to-everything (V2X) services supported by LTE-based systems and 5G. IEEE Commun. Stand. Mag. 2017, 1, 70–76. [Google Scholar] [CrossRef]
- Garcia, M.H.C.; Molina-Galan, A.; Boban, M.; Gozalvez, J.; Coll-Perales, B.; Şahin, T.; Kousaridas, A. A tutorial on 5G NR V2X communications. IEEE Commun. Surv. Tutor. 2021. [Google Scholar] [CrossRef]
- Rostan, M.; Stubbs, J.E.; Dzilno, D. EtherCAT enabled advanced control architecture. In Proceedings of the IEEE/SEMI Advanced Semiconductor Manufacturing Conference (ASMC), San Francisco, CA, USA, 11–13 July 2010; pp. 39–44. [Google Scholar]
- Dutertre, B. Formal modeling and analysis of the Modbus protocol. In Proceedings of the International Conference on Critical Infrastructure Protection; Springer: Boston, MA, USA, 2007; pp. 189–204. [Google Scholar]
- Gislason, D. Zigbee Wireless Networking; Newnes: Oxford, UK, 2008. [Google Scholar]
- Song, J.; Han, S.; Mok, A.; Chen, D.; Lucas, M.; Nixon, M.; Pratt, W. WirelessHART: Applying wireless technology in real-time industrial process control. In Proceedings of the IEEE Real-Time and Embedded Technology and Applications Symposium, St. Louis, MO, USA, 22–24 April 2008; pp. 377–386. [Google Scholar]
- IEEE Standards Association. IEEE Standard for Electric Power Systems Communications-Distributed Network Protocol (DNP3); IEEE: Piscataway, NJ, USA, 2014. [Google Scholar]
- Figueiredo, J.; da Costa, J.S. A SCADA system for energy management in intelligent buildings. Energy Build. 2012, 49, 85–98. [Google Scholar] [CrossRef] [Green Version]
- Haag, S.; Anderl, R. Digital twin—Proof of concept. Manuf. Lett. 2018, 15, 64–66. [Google Scholar] [CrossRef]
- Tao, F.; Zhang, H.; Liu, A.; Nee, A.Y.C. Digital twin in industry: State-of-the-art. IEEE Trans. Ind. Inform. 2019, 15, 2405–2415. [Google Scholar] [CrossRef]
- Hasan, M.; Mohan, S.; Shimizu, T.; Lu, H. Securing vehicle-to-everything (V2X) communication platforms. IEEE Trans. Intell. Veh. 2020, 5, 693–713. [Google Scholar] [CrossRef] [Green Version]
- Lim, H.; Hwang, S.; Myung, H. ERASOR: Egocentric ratio of pseudo occupancy-based dynamic object removal for static 3D point cloud map building. IEEE Robot. Autom. Lett. 2021, 6, 2272–2279. [Google Scholar] [CrossRef]
- Jeon, H.; Eun, Y. A stealthy sensor attack for uncertain cyber-physical systems. IEEE Internet Things J. 2019, 6, 6345–6352. [Google Scholar] [CrossRef]
- Kim, S.; Eun, Y.; Park, K.J. Stealthy sensor attack detection and real-time performance recovery for resilient CPS. IEEE Trans. Ind. Inform. 2021. [Google Scholar] [CrossRef]
- Hoagg, J.B.; Bernstein, D.S. Nonminimum-phase zeros—Much to do about nothing—Classical control—Revisited part II. IEEE Control Syst. Mag. 2007, 27, 45–57. [Google Scholar] [CrossRef]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. Revealing stealthy attacks in control systems. In Proceedings of the Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 1–5 October 2012; pp. 1806–1813. [Google Scholar]
- Yuz, J.I.; Goodwin, G.C. Sampled-Data Models for Linear and Nonlinear Systems; Springer: Berlin/Heidelberg, Germany, 2014. [Google Scholar]
- Kim, J.; Park, G.; Shim, H.; Eun, Y. Zero-stealthy attack for sampled-data control systems: The case of faster actuation than sensing. In Proceedings of the IEEE Conference on Decision and Control (CDC), Las Vegas, NV, USA, 12–14 December 2016; pp. 5956–5961. [Google Scholar]
- Mo, Y.; Sinopoli, B. Secure control against replay attacks. In Proceedings of the Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 30 September–2 October 2009; pp. 911–918. [Google Scholar]
- Smith, R.S. Covert misappropriation of networked control systems: Presenting a feedback structure. IEEE Control Syst. Mag. 2015, 35, 82–92. [Google Scholar]
- Schellenberger, C.; Zhang, P. Detection of covert attacks on cyber-physical systems by extending the system dynamics with an auxiliary system. In Proceedings of the IEEE Conference on Decision and Control (CDC), Melbourne, VIC, Australia, 12–15 December 2017; pp. 1374–1379. [Google Scholar]
- Cetinkaya, A.; Ishii, H.; Hayakawa, T. An overview on denial-of-service attacks in control systems: Attack models and security analyses. Entropy 2019, 21, 210. [Google Scholar] [CrossRef] [Green Version]
- De Persis, C.; Tesi, P. Input-to-state stabilizing control under denial-of-service. IEEE Trans. Autom. Control 2015, 60, 2930–2944. [Google Scholar] [CrossRef]
- Liu, J.; Yin, T.; Shen, M.; Xie, X.; Cao, J. State estimation for cyber–physical systems with limited communication resources, sensor saturation and denial-of-service attacks. ISA Trans. 2020, 104, 101–114. [Google Scholar] [CrossRef]
- Cetinkaya, A.; Ishii, H.; Hayakawa, T. A probabilistic characterization of random and malicious communication failures in multi-hop networked control. SIAM J. Control Optim. 2018, 56, 3320–3350. [Google Scholar] [CrossRef]
- Kim, W.; Park, J.; Jo, J.; Lim, H. Covert jamming using fake ACK frame injection on IEEE 802.11 wireless LANs. IEEE Wirel. Commun. Lett. 2019, 8, 1502–1505. [Google Scholar] [CrossRef]
- Rose, S.H.; Jayasree, T. Detection of jamming attack using timestamp for WSN. Ad Hoc Netw. 2019, 91, 101874. [Google Scholar] [CrossRef]
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A survey of intrusion detection for in-vehicle networks. IEEE Trans. Intell. Transp. Syst. 2020, 21, 919–933. [Google Scholar] [CrossRef]
- Lin, Y.; Chen, C.; Xiao, F.; Avatefipour, O.; Alsubhi, K.; Yunianta, A. An evolutionary deep learning anomaly detection framework for in-vehicle networks—CAN bus. IEEE Trans. Ind. Appl. 2020. [Google Scholar] [CrossRef]
- Lakshminarayana, S.; Karachiwala, J.S.; Chang, S.Y.; Revadigar, G.; Kumar, S.L.S.; Yau, D.K.; Hu, Y.C. Signal jamming attacks against communication-based train control: Attack impact and countermeasure. In Proceedings of the ACM Conference on Security & Privacy in Wireless and Mobile Networks, Stockholm, Sweden, 18–20 June 2018; pp. 160–171. [Google Scholar]
- Chang, S.Y.; Tran, B.A.N.; Hu, Y.C.; Jones, D.L. Jamming with power boost: Leaky waveguide vulnerability in train systems. In Proceedings of the IEEE International Conference on Parallel and Distributed Systems (ICPADS), Melbourne, VIC, Australia, 14–17 December 2015; pp. 37–43. [Google Scholar]
- Ali, S.; Al Balushi, T.; Nadir, Z.; Hussain, O.K. WSN security mechanisms for CPS. In Cyber Security for Cyber Physical Systems; Springer: Berlin/Heidelberg, Germany, 2018; pp. 65–87. [Google Scholar]
- Hsiao, H.C.; Studer, A.; Chen, C.; Perrig, A.; Bai, F.; Bellur, B.; Iyer, A. Flooding-resilient broadcast authentication for VANETs. In Proceedings of the 17th Annual International Conference on Mobile Computing and Networking, Las Vegas, NV, USA, 19–23 September 2011; pp. 193–204. [Google Scholar]
- Donkers, M.; Daafouz, J.; Heemels, W. Output-based controller synthesis for networked control systems with periodic protocols and time-varying transmission intervals and delays. IFAC Proc. Vol. 2014, 47, 6478–6483. [Google Scholar] [CrossRef] [Green Version]
- Kwon, Y.M.; Yu, J.; Cho, B.M.; Eun, Y.; Park, K.J. Empirical analysis of MAVLink protocol vulnerability for attacking unmanned aerial vehicles. IEEE Access 2018, 6, 43203–43212. [Google Scholar] [CrossRef]
- Chen, Y.; Poskitt, C.M.; Sun, J. Learning from mutants: Using code mutation to learn and monitor invariants of a cyber-physical system. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 648–660. [Google Scholar]
- Liu, K.; Dolan-Gavitt, B.; Garg, S. Fine-pruning: Defending against backdooring attacks on deep neural networks. In Proceedings of the International Symposium on Research in Attacks, Intrusions, and Defenses; Springer: Cham, Switzerland, 2018; pp. 273–294. [Google Scholar]
- Farwell, J.P.; Rohozinski, R. Stuxnet and the future of cyber war. Survival 2011, 53, 23–40. [Google Scholar] [CrossRef]
- Sani, A.S.; Yuan, D.; Yeoh, P.L.; Qiu, J.; Bao, W.; Vucetic, B.; Dong, Z.Y. CyRA: A real-time risk-based security assessment framework for cyber attacks prevention in industrial control systems. In Proceedings of the IEEE Power & Energy Society General Meeting (PESGM), Atlanta, GA, USA, 4–8 August 2019; pp. 1–5. [Google Scholar]
- Fang, D.; Xu, S.; Sharif, H. Security analysis of wireless train control systems. In Proceedings of the IEEE Globecom Workshops, Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Zhong, H.; Liao, C.; Squicciarini, A.C.; Zhu, S.; Miller, D. Backdoor embedding in convolutional neural network models via invisible perturbation. In Proceedings of the ACM Conference on Data and Application Security and Privacy, New Orleans, LA, USA, 16–18 March 2020; pp. 97–108. [Google Scholar]
- Abdi, F.; Chen, C.Y.; Hasan, M.; Liu, S.; Mohan, S.; Caccamo, M. Preserving physical safety under cyber attacks. IEEE Internet Things J. 2019, 6, 6285–6300. [Google Scholar] [CrossRef]
- Yoon, M.K.; Liu, B.; Hovakimyan, N.; Sha, L. VirtualDrone: Virtual sensing, actuation, and communication for attack-resilient unmanned aerial systems. In Proceedings of the ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Pittsburgh, PA, USA, 18–20 April 2017; pp. 143–154. [Google Scholar]
- Zhou, Y.; Feng, D. Side-channel attacks: Ten years after its publication and the impacts on cryptographic module security testing. IACR Cryptol. ePrint Arch. 2005, 2005, 388. [Google Scholar]
- Lawson, N. Side-channel attacks on cryptographic software. IEEE Secur. Priv. 2009, 7, 65–68. [Google Scholar] [CrossRef] [Green Version]
- Jang, M.; Lee, S.; Kung, J.; Kim, D. Defending against flush+reload attack with DRAM cache by bypassing shared SRAM cache. IEEE Access 2020, 8, 179837–179844. [Google Scholar] [CrossRef]
- Li, C.; Wang, Z.; Hou, X.; Chen, H.; Liang, X.; Guo, M. Power attack defense: Securing battery-backed data centers. ACM SIGARCH Comput. Archit. News 2016, 44, 493–505. [Google Scholar] [CrossRef]
- Gao, X.; Xu, Z.; Wang, H.; Li, L.; Wang, X. Why “some” like it hot too: Thermal attack on data centers. In Proceedings of the ACM SIGMETRICS/International Conference on Measurement and Modeling of Computer Systems, Urbana, IL, USA, 5–9 June 2017; pp. 23–24. [Google Scholar]
- Fournaris, A.P.; Pocero Fraile, L.; Koufopavlou, O. Exploiting hardware vulnerabilities to attack embedded system devices: A survey of potent microarchitectural attacks. Electronics 2017, 6, 52. [Google Scholar] [CrossRef] [Green Version]
- Mutlu, O. The RowHammer problem and other issues we may face as memory becomes denser. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Lausanne, Switzerland, 27–31 March 2017; pp. 1116–1121. [Google Scholar]
- Zhao, P.; Wang, S.; Gongye, C.; Wang, Y.; Fei, Y.; Lin, X. Fault sneaking attack: A stealthy framework for misleading deep neural networks. In Proceedings of the 56th ACM/IEEE Design Automation Conference (DAC), Las Vegas, NV, USA, 2–6 June 2019; pp. 1–6. [Google Scholar]
- Hong, S.; Frigo, P.; Kaya, Y.; Giuffrida, C.; Dumitraș, T. Terminal brain damage: Exposing the graceless degradation in deep neural networks under hardware fault attacks. In Proceedings of the USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; pp. 497–514. [Google Scholar]
- Handa, A.; Sharma, A.; Shukla, S.K. Machine learning in cybersecurity: A review. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2019, 9, e1306. [Google Scholar] [CrossRef]
- Liu, W.; Wang, Z.; Liu, X.; Zeng, N.; Liu, Y.; Alsaadi, F.E. A survey of deep neural network architectures and their applications. Neurocomputing 2017, 234, 11–26. [Google Scholar] [CrossRef]
- Elsayed, M.; Erol-Kantarci, M. Deep Q-learning for low-latency tactile applications: Microgrid communications. In Proceedings of the 2018 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Aalborg, Denmark, 29–31 October 2018; pp. 1–6. [Google Scholar]
- Afanador, N.L.; Smolinska, A.; Tran, T.N.; Blanchet, L. Unsupervised random forest: A tutorial with case studies. J. Chemom. 2016, 30, 232–241. [Google Scholar] [CrossRef]
- Burges, C.J. A tutorial on support vector machines for pattern recognition. Data Min. Knowl. Discov. 1998, 2, 121–167. [Google Scholar] [CrossRef]
- Gómez, Á.L.P.; Maimó, L.F.; Celdran, A.H.; Clemente, F.J.G.; Sarmiento, C.C.; Masa, C.J.D.C.; Nistal, R.M. On the generation of anomaly detection datasets in industrial control systems. IEEE Access 2019, 7, 177460–177473. [Google Scholar] [CrossRef]
- Cai, F.; Koutsoukos, X. Real-time out-of-distribution detection in learning-enabled cyber-physical systems. In Proceedings of the ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Sydney, NSW, Australia, 21–25 April 2020; pp. 174–183. [Google Scholar]
- Javed, A.R.; Usman, M.; Rehman, S.U.; Khan, M.U.; Haghighi, M.S. Anomaly detection in automated vehicles using multistage attention-based convolutional neural network. IEEE Trans. Intell. Transp. Syst. 2020, 1–10. [Google Scholar] [CrossRef]
- Wang, Y.; Masoud, N.; Khojandi, A. Real-time sensor anomaly detection and recovery in connected automated vehicle sensors. IEEE Trans. Intell. Transp. Syst. 2021, 22, 1411–1421. [Google Scholar] [CrossRef] [Green Version]
- Lin, Q.; Adepu, S.; Verwer, S.; Mathur, A. TABOR: A graphical model-based approach for anomaly detection in industrial control systems. In Proceedings of the Asia Conference on Computer and Communications Security, Incheon, Korea, 4 June 2018; pp. 525–536. [Google Scholar]
- Keliris, A.; Salehghaffari, H.; Cairl, B.; Krishnamurthy, P.; Maniatakos, M.; Khorrami, F. Machine learning-based defense against process-aware attacks on industrial control systems. In Proceedings of the IEEE International Test Conference (ITC), Fort Worth, TX, USA, 15–17 November 2016; pp. 1–10. [Google Scholar]
- Paridari, K.; O’Mahony, N.; Mady, A.E.D.; Chabukswar, R.; Boubekeur, M.; Sandberg, H. A framework for attack-resilient industrial control systems: Attack detection and controller reconfiguration. Proc. IEEE 2018, 106, 113–128. [Google Scholar] [CrossRef]
- KI Williams, C. Gaussian Processes for Machine Learning; Taylor & Francis Group: Abingdon, UK, 2006. [Google Scholar]
- Ravikumar, G.; Govindarasu, M. Anomaly detection and mitigation for wide-area damping control using machine learning. IEEE Trans. Smart Grid 2020. [Google Scholar] [CrossRef]
- Chakhchoukh, Y.; Liu, S.; Sugiyama, M.; Ishii, H. Statistical outlier detection for diagnosis of cyber attacks in power state estimation. In Proceedings of the IEEE Power and Energy Society General Meeting (PESGM), Boston, MA, USA, 17–21 July 2016; pp. 1–5. [Google Scholar]
- Ahmed, S.; Lee, Y.; Hyun, S.H.; Koo, I. Feature selection–based detection of covert cyber deception assaults in smart grid communications networks using machine learning. IEEE Access 2018, 6, 27518–27529. [Google Scholar] [CrossRef]
- Karimipour, H.; Dehghantanha, A.; Parizi, R.M.; Choo, K.K.R.; Leung, H. A deep and scalable unsupervised machine learning system for cyber-attack detection in large-scale smart grids. IEEE Access 2019, 7, 80778–80788. [Google Scholar] [CrossRef]
- Lyamin, N.; Kleyko, D.; Delooz, Q.; Vinel, A. AI-based malicious network traffic detection in VANETs. IEEE Netw. 2018, 32, 15–21. [Google Scholar] [CrossRef]
- Jeong, W.; Han, S.; Choi, E.; Lee, S.; Choi, J.W. CNN-based adaptive source node identifier for controller area network (CAN). IEEE Trans. Veh. Technol. 2020, 69, 13916–13920. [Google Scholar] [CrossRef]
- Singh, P.K.; Gupta, R.R.; Nandi, S.K.; Nandi, S. Machine learning based approach to detect wormhole attack in VANETs. In Proceedings of the Workshops of the International Conference on Advanced Information Networking and Applications; Springer: Cham, Switzerland, 2019; pp. 651–661. [Google Scholar]
- Maglaras, L.A.; Jiang, J.; Cruz, T. Integrated OCSVM mechanism for intrusion detection in SCADA systems. Electron. Lett. 2014, 50, 1935–1936. [Google Scholar] [CrossRef]
- Khan, I.A.; Pi, D.; Khan, Z.U.; Hussain, Y.; Nawaz, A. HML-IDS: A hybrid-multilevel anomaly prediction approach for intrusion detection in SCADA systems. IEEE Access 2019, 7, 89507–89521. [Google Scholar] [CrossRef]
- Hassan, M.M.; Huda, S.; Sharmeen, S.; Abawajy, J.; Fortino, G. An adaptive trust boundary protection for IIoT networks using deep-learning feature-extraction-based semisupervised model. IEEE Trans. Ind. Inform. 2021, 17, 2860–2870. [Google Scholar] [CrossRef]
- Gao, J.; Gan, L.; Buschendorf, F.; Zhang, L.; Liu, H.; Li, P.; Dong, X.; Lu, T. Omni SCADA intrusion detection using deep learning algorithms. IEEE Internet Things J. 2021, 8, 951–961. [Google Scholar] [CrossRef]
- Yin, X.C.; Liu, Z.G.; Nkenyereye, L.; Ndibanje, B. Toward an applied cyber security solution in IoT-based smart grids: An intrusion detection system approach. Sensors 2019, 19, 4952. [Google Scholar] [CrossRef] [Green Version]
- Kwon, S.; Yoo, H.; Shon, T. IEEE 1815.1-based power system security With bidirectional RNN-based network anomalous attack detection for cyber-physical system. IEEE Access 2020, 8, 77572–77586. [Google Scholar] [CrossRef]
- Yang, H.; Cheng, L.; Chuah, M.C. Deep-learning-based network intrusion detection for SCADA systems. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), Washington, DC, USA, 10–12 June 2019; pp. 1–7. [Google Scholar]
- da Silva, E.G.; Silva, A.S.d.; Wickboldt, J.A.; Smith, P.; Granville, L.Z.; Schaeffer-Filho, A. A one-class NIDS for SDN-based SCADA systems. In Proceedings of the IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA, 10–14 June 2016; pp. 303–312. [Google Scholar]
- Yoon, M.K.; Mohan, S.; Choi, J.; Christodorescu, M.; Sha, L. Learning execution contexts from system call distribution for anomaly detection in smart embedded system. In Proceedings of the Second International Conference on Internet-of-Things Design and Implementation, Pittsburgh, PA, USA, 18–21 April 2017; pp. 191–196. [Google Scholar]
- Wang, W.; Zhao, M.; Wang, J. Effective android malware detection with a hybrid model based on deep autoencoder and convolutional neural network. J. Ambient Intell. Humaniz. Comput. 2019, 10, 3035–3043. [Google Scholar] [CrossRef]
- Patel, N.K.; Krishnamurthy, P.; Amrouch, H.; Henkel, J.; Shamouilian, M.; Karri, R.; Khorrami, F. Towards a new thermal monitoring based framework for embedded CPS device security. IEEE Trans. Dependable Secur. Comput. 2020. [Google Scholar] [CrossRef]
- Wang, H.; Sayadi, H.; Sasan, A.; Rafatirad, S.; Mohsenin, T.; Homayoun, H. Comprehensive evaluation of machine learning countermeasures for detecting microarchitectural side-channel attacks. In Proceedings of the 2020 on Great Lakes Symposium on VLSI, 7–9 September 2020; pp. 181–186. [Google Scholar]
- Mushtaq, M.; Akram, A.; Bhatti, M.K.; Chaudhry, M.; Yousaf, M.; Farooq, U.; Lapotre, V.; Gogniat, G. Machine learning for security: The case of side-channel attack detection at run-time. In Proceedings of the IEEE International Conference on Electronics, Circuits and Systems (ICECS), Bordeaux, France, 9–12 December 2018; pp. 485–488. [Google Scholar]
- Cho, J.; Kim, T.; Kim, S.; Im, M.; Kim, T.; Shin, Y. Real-time detection for cache side channel attack using performance counter monitor. Appl. Sci. 2020, 10, 984. [Google Scholar] [CrossRef] [Green Version]
- Li, C.; Gaudiot, J.L. Detecting malicious attacks exploiting hardware vulnerabilities using performance counters. In Proceedings of the IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; pp. 588–597. [Google Scholar]
- Chakraborty, A.; Alam, M.; Mukhopadhyay, D. Deep learning based diagnostics for Rowhammer protection of DRAM chips. In Proceedings of the IEEE 28th Asian Test Symposium (ATS), Kolkata, India, 10–13 December 2019; pp. 86–91. [Google Scholar]
- Li, J.; Xia, Y.; Qi, X.; Gao, Z. On the necessity, scheme, and basis of the linear–nonlinear switching in active disturbance rejection control. IEEE Trans. Ind. Electron. 2017, 64, 1425–1435. [Google Scholar] [CrossRef]
- Quinonez, R.; Giraldo, J.; Salazar, L.; Bauman, E.; Cardenas, A.; Lin, Z. SAVIOR: Securing autonomous vehicles with robust physical invariants. In Proceedings of the USENIX Security Symposium (USENIX Security 20), 12–14 August 2020; pp. 895–912. [Google Scholar]
- Bak, S.; Chivukula, D.K.; Adekunle, O.; Sun, M.; Caccamo, M.; Sha, L. The system-level simplex architecture for improved real-time embedded system safety. In Proceedings of the IEEE Real-Time and Embedded Technology and Applications Symposium, San Francisco, CA, USA, 13–16 April 2009; pp. 99–107. [Google Scholar]
- Hu, F.; Hao, Q.; Bao, K. A survey on software-defined network and OpenFlow: From concept to implementation. IEEE Commun. Surv. Tutor. 2014, 16, 2181–2206. [Google Scholar] [CrossRef]
- Togou, M.A.; Chekired, D.A.; Khoukhi, L.; Muntean, G.M. A distributed control plane for path computation scalability in software-defined networks. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Sood, K.; Yu, S.; Xiang, Y. Software-defined wireless networking opportunities and challenges for Internet-of-Things: A review. IEEE Internet Things J. 2016, 3, 453–463. [Google Scholar] [CrossRef]
- Yang, H.; Zhan, K.; Kadoch, M.; Liang, Y.; Cheriet, M. BLCS: Brain-like distributed control security in cyber physical systems. IEEE Netw. 2020, 34, 8–15. [Google Scholar] [CrossRef]
- Jin, D.; Li, Z.; Hannon, C.; Chen, C.; Wang, J.; Shahidehpour, M.; Lee, C.W. Toward a cyber resilient and secure microgrid using software-defined networking. IEEE Trans. Smart Grid 2017, 8, 2494–2504. [Google Scholar] [CrossRef]
- Wang, H.; Xu, L.; Gu, G. Floodguard: A DoS attack prevention extension in software-defined networks. In Proceedings of the IEEE/IFIP International Conference on Dependable Systems and Networks, Rio de Janeiro, Brazil, 22–25 June 2015; pp. 239–250. [Google Scholar]
- Shang, G.; Zhe, P.; Bin, X.; Aiqun, H.; Kui, R. FloodDefender: Protecting data and control plane resources under SDN-aimed DoS attacks. In Proceedings of the IEEE INFOCOM 2017-IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017; pp. 1–9. [Google Scholar]
- Adi, Y.; Baum, C.; Cisse, M.; Pinkas, B.; Keshet, J. Turning your weakness into a strength: Watermarking deep neural networks by backdooring. In Proceedings of the USENIX Security Symposium (USENIX Security 18), Baltimore, MD, USA, 15–17 August 2018; pp. 1615–1631. [Google Scholar]
- Creswell, A.; White, T.; Dumoulin, V.; Arulkumaran, K.; Sengupta, B.; Bharath, A.A. Generative adversarial networks: An overview. IEEE Signal Process. Mag. 2018, 35, 53–65. [Google Scholar] [CrossRef] [Green Version]
- Li, D.; Chen, D.; Jin, B.; Shi, L.; Goh, J.; Ng, S.K. MAD-GAN: Multivariate anomaly detection for time series data with generative adversarial networks. In Proceedings of the International Conference on Artificial Neural Networks; Springer: Cham, Switzerland, 2019; pp. 703–716. [Google Scholar]
- Freitas de Araujo-Filho, P.; Kaddoum, G.; Campelo, D.R.; Gondim Santos, A.; Macêdo, D.; Zanchettin, C. Intrusion detection for cyber–physical systems using generative adversarial networks in fog environment. IEEE Internet Things J. 2021, 8, 6247–6256. [Google Scholar] [CrossRef]
- Chhetri, S.R.; Lopez, A.B.; Wan, J.; Al Faruque, M.A. GAN-Sec: Generative adversarial network modeling for the security analysis of cyber-physical production systems. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Florence, Italy, 25–29 March 2019; pp. 770–775. [Google Scholar]
- Shahriar, M.H.; Haque, N.I.; Rahman, M.A.; Alonso, M. G-IDS: Generative adversarial networks assisted intrusion detection system. In Proceedings of the IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, 13–17 July 2020; pp. 376–385. [Google Scholar]
- Lippmann, R.; Haines, J.W.; Fried, D.J.; Korba, J.; Das, K. The 1999 DARPA off-line intrusion detection evaluation. Comput. Netw. 2000, 34, 579–595. [Google Scholar] [CrossRef]
- Zixu, T.; Liyanage, K.S.K.; Gurusamy, M. Generative adversarial network and auto encoder based anomaly detection in distributed IoT networks. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–7. [Google Scholar]




| Reference | CPS Area | Defense Against | ML Model | Validation |
|---|---|---|---|---|
| [22] | Vehicle | Sensor | RNN | Experiment |
| [103] | Vehicle | Sensor | CNN | Simulation |
| [104] | Vehicle | Sensor | LSTM-CNN | Dataset |
| [105] | Vehicle | Sensor | SVM | Simulation |
| [106] | Water | Sensor | Various | Simulation |
| [107] | Chemical | Various | SVM | HILS |
| [108] | HVAC | Sensor | SVM | Simulation |
| [36] | HVAC | Various | SVM | Simulation |
| [110] | Power | Various | Various | HILS |
| [111] | Power | Sensor | DRE | Simulation |
| [112] | Power | Sensor | SVM | Simulation |
| [113] | power | Sensor | DBN | Simulation |
| Reference | CPS Area | Defense Against | ML Model | Validation |
|---|---|---|---|---|
| [114] | Vehicle (VANET) | DoS | DNN | Simulation |
| [115] | Vehicle (CAN) | DoS | CNN | Real-data |
| [73] | Vehicle (CAN) | Various | DNN | Real-data |
| [116] | Vehicle (VANET) | Manipulation | Various | Simulation |
| [117] | ICS | Various | Various | Experiment |
| [118] | Gas pipeline | Various | KNN | Real-data |
| [119] | ICS | Manipulation | Various | Experiment |
| [120] | ICS | Various | LSTM-FNN | Experiment |
| [121] | Power | Manipulation | Various | Simulation |
| [122] | Power | Various | RNN | Simulation |
| [123] | Power | Various | CNN | Experiment |
| [124] | power | DoS | SVM | Simulation |
| Reference | Defense Against | ML Model | Validation |
|---|---|---|---|
| [125,128,129] | Application software | Various | Experiment |
| [126,127] | Application software | CNN | Experiment |
| [130] | Application software | Softmax | Experiment |
| [131] | Computing hardware | Various | Experiment |
| [132] | Computing hardware | CNN | Experiment |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, S.; Park, K.-J. A Survey on Machine-Learning Based Security Design for Cyber-Physical Systems. Appl. Sci. 2021, 11, 5458. https://doi.org/10.3390/app11125458
Kim S, Park K-J. A Survey on Machine-Learning Based Security Design for Cyber-Physical Systems. Applied Sciences. 2021; 11(12):5458. https://doi.org/10.3390/app11125458
Chicago/Turabian StyleKim, Sangjun, and Kyung-Joon Park. 2021. "A Survey on Machine-Learning Based Security Design for Cyber-Physical Systems" Applied Sciences 11, no. 12: 5458. https://doi.org/10.3390/app11125458







