Research and Applied Perspective to Blockchain Technology: A Comprehensive Survey
Abstract
:1. Introduction
1.1. Main Features of Blockchain
- Transparency: Blockchain stores every transaction in a block. Also, it is available to all the peers for verification [9].
- Security: Each block is added to the chain after validation. Also, each block contains a hash of the previous block [10]. It is computationally impossible to delete or update a block because it requires re-calculation of all the preceding block hashes.
- Fault Tolerant Network: Blockchain has a peer-to-peer network of nodes. All miner nodes process transactions in parallel [11]. The blockchain will continue working if some of the nodes fail to function.
1.2. Working Flow of Blockchain
1.3. Key Characteristics
- Consensus: All participants must agree on validity of a transaction for it to be valid. Blockchain offer a variety of consensus algorithms which are chosen by the users according to the requirement of blockchain application.
- Provenance: Participants know where the asset came from and how its ownership has changed over time.
- Immutability: No participant can tamper with a transaction after it has been recorded to the ledger [16,17]. If there is an error in a transaction, a new transaction must be used to reverse the error. Both these transactions are then visible [18]. The error in transaction means that the transactions are either failed or rejected by miners. Usually the transactions with very low fee are rejected.
- Finality: A single, shared ledger provides one place to go to determine the ownership of an asset or the completion of a transaction.
- Smart Contract: The smart contracts [19] are programs of computer that support in the transmission of money or anything of value. When a particular policy is met, these programs run automatically. Each smart contract contains a contract address, predefined functions and private storage. Ethereum [20], is an open-source and decentralized platform that executes smart contracts. To construct smart contract Ethereum platform uses solidity as programming language.
1.4. Research Questions
- How can blockchain can be deployed in different applications?
- What are the potential consensus methods for public and private blockchains?
- Which platforms offer development of blockchain?
- What are potential attacks for blockchain and what are the research issues in different applications of blockchain?
1.5. Research Contributions
- The core blockchain is discussed i.e., its architecture, its working flow and characteristics.
- The paper also discusses different applications of blockchain.
- This paper focuses on the survey of the consensus algorithms of the public and private blockchains.
- The algorithms are categorized according to their use in different scenarios and fields.
1.6. Organization
2. Types of Blockchain
- Public/Permissionless Blockchains for example Bitcoin and Ethereum etc.
- Private/Permissioned Blockchains for example Hyperledger and R3 Corda etc.
- Hybrid Blockchains for example Dragonchain etc.
2.1. Public/Permissionless Blockchains
2.2. Private/Permissioned Blockchains
2.3. Hybrid Blockchains
- Does business deals through trusted third parties?
- Do people frequently generate transactions?
- Are validation and data integrity important?
- Is the data integrity and process performance more important than confidentiality? However for time sensitive nature of the application it is not recommended as the transactions take time to be validated and verified.
- Blockchain can influence several emerging areas like smart cities, Internet of Vehicles, banking, Internet of Things, edge computing and cloud [33].
- Is blockchain required to be deployed as public or private?
3. Applications of Blockchain
3.1. Cryptocurrency
3.2. Private Data Storage
3.3. Reputation Management
3.4. Education
3.5. Banking
3.6. Finance-Payroll and Settlement
3.7. Taxation
3.8. Healthcare
3.9. Voting
3.10. Insurance
3.11. Smart Cities
3.12. Internet of Things (IOT)
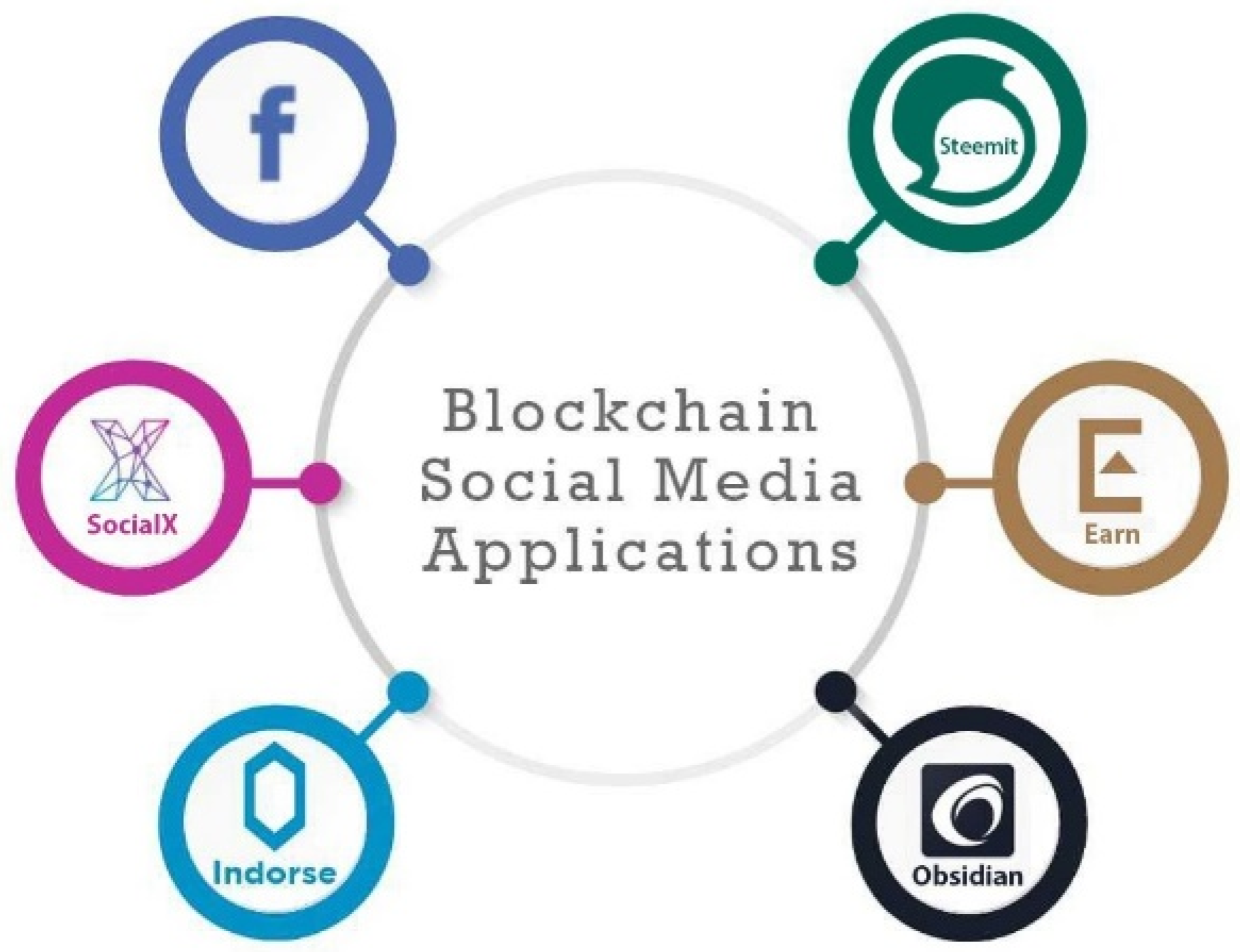
3.13. Blockchain in Social Media
3.13.1. Steemit
3.13.2. Earn
3.13.3. SocialX
3.13.4. Obsidian
3.13.5. Indorse
3.14. Blockchain in Power
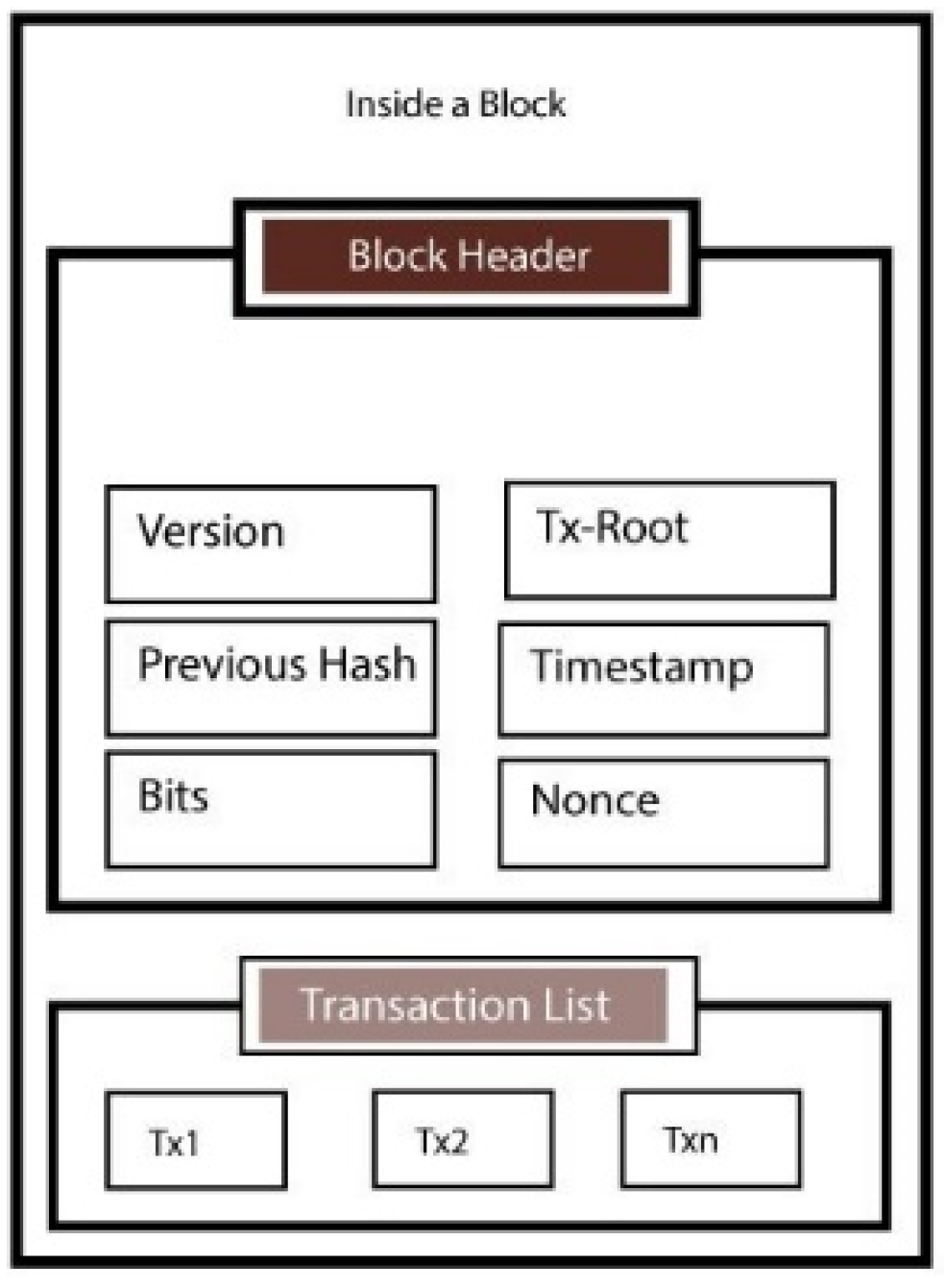
4. Blockchain’s Architecture
4.1. Previous Hash
4.2. Timestamp
4.3. Tx–Root
4.4. Version
4.5. Nonce
4.6. Bits
4.7. Transactions List
5. Consensus Algorithms
5.1. Consensus Algorithms Used by Various Cryptocurrencies
5.1.1. Proof of Work (PoW)
5.1.2. Delayed Proof of Work
5.1.3. Proof of Stake (PoS)
- Original PoS: Proof of stake uses the wealth of miners to win a ticket rather than computational power. PoS was first implemented in 2012 as cryptocurrency PeerCoin. PoS is kind of a hybrid design where PoW is used in the beginning for coin minting and later PoS is used for the security of the whole network. PoS works with the concept of a coin’s age which is explained by example. If there are 10 coins which are held for 10 days its age is 100 days. If these coins are spent, their age is consumed. In PoW the main chain with most work is followed, and in PoS a chain with most coin age is followed.
- Cardano’s Ouroboros: This protocol adds security measures to ensure persistence and liveness within the system. This implementation elects the stakeholders through a delegation process and takes the snapshots of current stakeholders labelled as an ‘epoch’. The subset of current stakeholders randomly decide who will be the next epoch stakeholder.
5.1.4. Stellar Consensus Protocol (SCP)
5.1.5. Delegated Proof of Stake (DPOS)
5.1.6. Leased Proof of Stake (LPoS)
5.1.7. Byzantine Fault Tolerance (BFT)
5.1.8. Directed Acyclic Graph (DAG)
- No More Double Spending: In traditional blockchain, a scenario of more than one miner tries to validate the same blockchain leads to double spending. This also leads to hard or soft forks. The DAG is safer and robust as it validates a particular transaction based on the previous number of transactions.
- Less Width: The transaction in another consensus algorithm gets added to the whole network but in DAG the transaction is added to the transaction graph. This makes the whole network less bulky and easy to validate a particular transaction.
- Smarter and Faster: As the blockless nature of DAG, it is much faster than PoW and PoS.
- Favorable to the Smaller Transactions: Bitcoin and Ethereum are not much friendly for the smaller amounts rather DAG seems perfect as transaction fee is neglected.
5.1.9. Proof of Weight (PoWeight)
5.1.10. Delegated Byzantine Fault Tolerance (DBFT)
5.1.11. Ripple Protocol Consensus Algorithm (RPCA)
- Each server puts all the valid transactions in the “candidate set” which is the public list.
- Each server gathers all candidate sets, from other Ripple servers which is found in its unique node list.
- Each server votes for the validity of transactions. This voting can be done in one or multiple rounds.
- A minimum of 80% yes is required for all the transactions in the final round to be written into the public ledger and then the ledger is closed [76].
5.1.12. Proof of Importance
5.1.13. Proof of Exercise (PoX)
5.1.14. Proof of Ownership
5.1.15. Proof of Luck (PoL)
5.1.16. Proof of Activity (PoA)
5.1.17. Proof of Publication (PoP)
5.1.18. Proof of Burn (PoB)
5.1.19. Proof of Retrievability (PoR)
5.1.20. Proof of Elapsed Time (PoET)
5.1.21. Proof of Capacity (PoC)
5.1.22. Proof of Existence
5.1.23. Proof of Authority
5.1.24. Ethash
5.1.25. Proof of Stake Velocity (PoSV)
5.1.26. Proof of SpaceTime (PoST)
5.1.27. A Federated Byzantine Agreement (FBA)
5.2. Healthcare Based Consensus
5.2.1. Proof of Interoperability
5.2.2. Proof of Disease
- Mobile devices and desktops are used as user devices and the server is cloud based application. Server and client communication is done via Java Script Object Notation (JSON) objects.
- The patients enter their details of disease in simple English and the server runs hunspell using corpus (customized medical dictionary) over the user text.
- The user text is parsed using metathesaurus and UMLS and then the text is converted into multiple UMLS (Unified Medical Language System) CUI (Concept Unique Identifier).
- UMLS CUI is converted into ICD10 and SNOMED CT (Systemized Nomenclature of Medicine—Clinical Terms) Codes.
- The important information is either taken from the user online if the information is not available in EMR/HER (Electronic Medical Record/Health Electronic Record).
- Using graph analysis merge SNOMED CD with phonemics databases to determine the fundamental disease concepts in machine understandable ontologies.
- The medical specialists called Medical Miner (MM), validates and confirms all the results from the above steps and commits into the blockchain.
- Additional biological databases are added and repeated over in cases, when the proof of disease cannot be determined. These are big-data databases Gene Ontology, Human Phenotype Ontology (HPO), Virtual Metabolic Human etc. [89].
5.2.3. Medical Information Sharing Using PBFT (Practical Byzantine Fault Tolerance)
5.3. Intelligent Transportation System (ITS) and Vehicular Ad Hoc Networks (VANETS) Consensus Algorithms
5.3.1. Proof of Movement
5.3.2. Proof of Driving
5.3.3. Proof of Reputation
5.4. Consensus in Supply Chain
5.4.1. Soft Consensus-Based Group Decision Making
5.4.2. Weight-Based PoS
5.5. Consensus in Internet of Things (IoT)
5.5.1. A Distributed Consensus Algorithm
5.5.2. Consensus Protocol of Diversified Services of Complex Internet of Things Applications
5.6. Consensus in Big Data
5.6.1. Paxos Algorithm for Consensus
5.6.2. Proof of Collaboration
5.7. Consensus in Cellular Networks
5.8. Proof-of-Location (PoL)
5.9. Consensus in Social Networks
Proof of Credibility
5.10. Consensus in Distributed Web Services and Storage
Proof of History
5.11. Consensus in Governance
5.12. Consensus in Entertainment
5.13. Consensus in Real Estate
5.14. Consensus in Power
5.15. General Consensus Algorithms
5.15.1. Proof of Vote
5.15.2. Tendermint
5.15.3. Proof of Human Work
5.15.4. Simplified Byzantine Fault Tolerance (SBFT)
5.15.5. Practical Byzantine Fault Tolerance (PBFT)
5.15.6. Raft
5.15.7. Proof of Proof
5.15.8. Proof of Believability
5.15.9. Proof of Property
6. Development Platforms
6.1. Ethereum
6.2. Cosmos
6.3. Cardano
6.4. Electro-Optical System (EOS)
6.5. Bitcoin
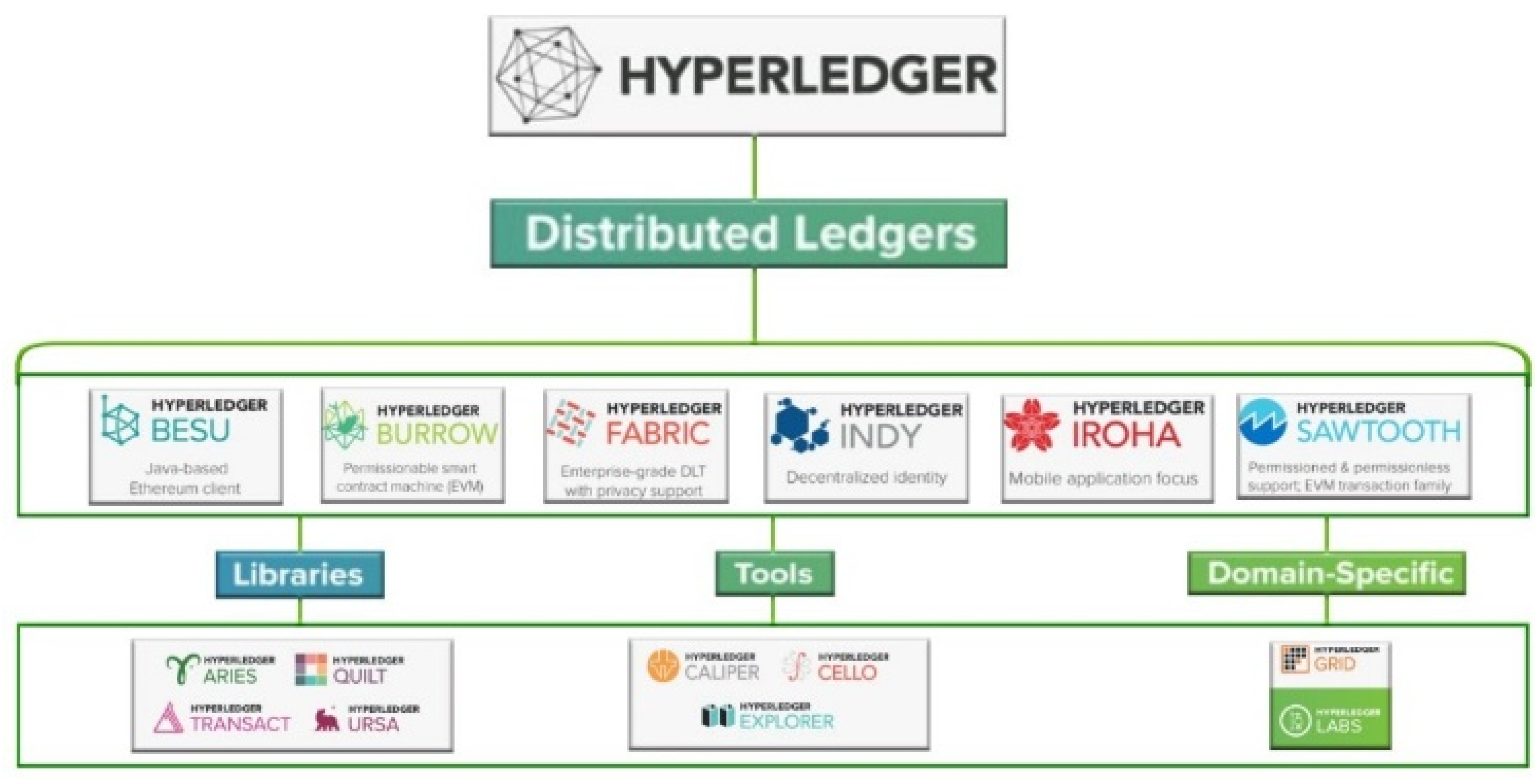
6.6. Hyperledger
6.7. Corda
7. Blockchain Challenges
7.1. Denial of Service (DoS) Attacks
7.2. Sybil Attacks
7.3. Eclipse Attacks
7.4. Routing Attacks
7.5. The 51% Attacks
7.6. Double Spending
7.7. Alternative History Attacks
7.8. Race Attacks
7.9. Finney Attack
8. Blockchain Research Issues
8.1. Blockchain-Based Research Issues in Healthcare
8.2. Blockchain-Based Research Issues/Future Work in Intelligent Transportation System (ITS) and Internet of Things (IoT)
8.3. Blockhain Research Issues/Future Work in Real Estate
9. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Velde, F. Bitcoin: A Primer; Essays on Issues the Federal Reserve Bank of Chicago Dec; Federal Reserve Bank of Chicago: Chicago, IL, USA, 2013. [Google Scholar]
- Shoker, A. Sustainable blockchain through proof of exercise. In Proceedings of the 2017 IEEE 16th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 30 October–1 November 2017; pp. 1–9. [Google Scholar]
- Brito, J.; Castillo, A. Bitcoin: A Primer for Policymakers; Mercatus Center at George Mason University: Fairfax, VA, USA, 2013. [Google Scholar]
- Swan, M. Blockchain thinking: The brain as a decentralized autonomous corporation [commentary]. IEEE Technol. Soc. Mag. 2015, 34, 41–52. [Google Scholar] [CrossRef]
- Bahga, A.; Madisetti, V. Blockchain Applications: A Hands-On Approach; Vpt, 2017; Available online: Laportecountymealsonwheels.org (accessed on 6 October 2018).
- El Ioini, N.; Pahl, C. A review of distributed ledger technologies. In OTM Confederated International Conferences “On the Move to Meaningful Internet Systems”; Springer: Cham, Switzerland, 2018; pp. 277–288. [Google Scholar]
- Anceaume, E.; Guellier, A.; Ludinard, R.; Sericola, B. Sycomore: A permissionless distributed ledger that self-adapts to transactions demand. In Proceedings of the 2018 IEEE 17th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 1–3 November 2018; pp. 1–8. [Google Scholar]
- Hughes, A.; Park, A.; Kietzmann, J.; Archer-Brown, C. Beyond Bitcoin: What blockchain and distributed ledger technologies mean for firms. Bus. Horiz. 2019, 62, 273–281. [Google Scholar] [CrossRef]
- Rizal Batubara, F.; Ubacht, J.; Janssen, M. Unraveling Transparency and Accountability in Blockchain. In Proceedings of the 20th Annual International Conference on Digital Government Research, Dubai, United Arab Emirates, 18–20 June 2019; pp. 204–213. [Google Scholar]
- Karame, G. On the security and scalability of bitcoin’s blockchain. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 1861–1862. [Google Scholar]
- Wattenhofer, R. Distributed Ledger Technology: The Science of the Blockchain; CreateSpace Independent, 2017; Available online: https://lib.hpu.edu.vn/handle/123456789/28113 (accessed on 8 May 2021).
- Xu, X.; Weber, I.; Staples, M. Architecture for Blockchain Applications; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Puthal, D.; Malik, N.; Mohanty, S.P.; Kougianos, E.; Yang, C. The blockchain as a decentralized security framework [future directions]. IEEE Consum. Electron. Mag. 2018, 7, 18–21. [Google Scholar] [CrossRef]
- Shahriar Hazari, S.; Mahmoud, Q.H. Improving Transaction Speed and Scalability of Blockchain Systems via Parallel Proof of Work. Future Internet 2020, 12, 125. [Google Scholar] [CrossRef]
- Chatzigiannis, P.; Baldimtsi, F.; Griva, I.; Li, J. Diversification across mining pools: Optimal mining strategies under pow. arXiv 2019, arXiv:1905.04624. [Google Scholar]
- Hofmann, F.; Wurster, S.; Ron, E.; Böhmecke-Schwafert, M. The immutability concept of blockchains and benefits of early standardization. In Proceedings of the 2017 ITU Kaleidoscope: Challenges for a Data-Driven Society (ITU K), Nanjing, China, 27–29 November 2017; pp. 1–8. [Google Scholar]
- Landerreche, E.; Stevens, M. On immutability of blockchains. In Proceedings of the 1st ERCIM Blockchain Workshop 2018, Amsterdam, The Netherlands, 8–9 May 2018; European Society for Socially Embedded Technologies (EUSSET): Zurich, Switzerland, 2018. [Google Scholar]
- Aste, T.; Tasca, P.; Di Matteo, T. Blockchain technologies: The foreseeable impact on society and industry. Computer 2017, 50, 18–28. [Google Scholar] [CrossRef] [Green Version]
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. Hawk: The blockchain model of cryptographyand privacy-preserving smart contracts. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 839–858. [Google Scholar]
- Buterin, V. A next-generation smart contract and decentralized application platform. White Pap. 2014, 3, 1–36. [Google Scholar]
- Bach, L.; Mihaljevic, B.; Zagar, M. Comparative analysis of blockchain consensus algorithms. In Proceedings of the 2018 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 21–25 May 2018; pp. 1545–1550. [Google Scholar]
- Chalaemwongwan, N.; Kurutach, W. State of the art and challenges facing consensus protocols on blockchain. In Proceedings of the 2018 International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 10–12 January 2018; pp. 957–962. [Google Scholar]
- Wang, W.; Hoang, D.T.; Hu, P.; Xiong, Z.; Niyato, D.; Wang, P.; Wen, Y.; Kim, D.I. A survey on consensus mechanisms and mining strategy management in blockchain networks. IEEE Access 2019, 7, 22328–22370. [Google Scholar] [CrossRef]
- Nguyen, G.T.; Kim, K. A Survey about Consensus Algorithms Used in Blockchain. J. Inf. Process. Syst. 2018, 14, 101–128. [Google Scholar]
- Chaudhry, N.; Yousaf, M.M. Consensus algorithms in blockchain: Comparative analysis, challenges and opportunities. In Proceedings of the 2018 12th International Conference on Open Source Systems and Technologies (ICOSST), Lahore, Pakistan, 19–21 December 2018; pp. 54–63. [Google Scholar]
- Zhao, W.; Yang, S.; Luo, X. On consensus in public blockchains. In Proceedings of the 2019 International Conference on Blockchain Technology, Honolulu, HI, USA, 15–18 March 2019; pp. 1–5. [Google Scholar]
- Aras, S.T.; Kulkarni, V. Blockchain and Its Applications–A Detailed Survey. Int. J. Comput. Appl. 2017, 180, 29–35. [Google Scholar]
- Mohan, C. State of public and private blockchains: Myths and reality. In Proceedings of the 2019 International Conference on Management of Data, Amsterdam, The Netherlands, 30 June–5 July 2019; pp. 404–411. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar]
- Sagirlar, G.; Carminati, B.; Ferrari, E.; Sheehan, J.D.; Ragnoli, E. Hybrid-iot: Hybrid blockchain architecture for internet of things-pow sub-blockchains. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1007–1016. [Google Scholar]
- Manian, Z.N.; Krishnan, R.; Sriram, S. Hybrid Blockchain. U.S. Patent 20,170,243,193A1, 24 August 2017. [Google Scholar]
- Ranade, A.; Shaikh, Z. A Survey on Blockchain Technology with Use-Cases in Governance. 2020. Available online: https://papers.ssrn.com/SSRN3568629 (accessed on 20 April 2020).
- Zhu, S.; Cai, Z.; Hu, H.; Li, Y.; Li, W. zkCrowd: A hybrid blockchain-based crowdsourcing platform. IEEE Trans. Ind. Inform. 2019, 16, 4196–4205. [Google Scholar] [CrossRef]
- Sun, J.; Yan, J.; Zhang, K.Z. Blockchain-based sharing services: What blockchain technology can contribute to smart cities. Financ. Innov. 2016, 2, 26. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.H. BIDaaS: Blockchain based ID as a service. IEEE Access 2017, 6, 2274–2278. [Google Scholar] [CrossRef]
- Hassani, H.; Huang, X.; Silva, E. Big-crypto: Big data, blockchain and cryptocurrency. Big Data Cogn. Comput. 2018, 2, 34. [Google Scholar] [CrossRef] [Green Version]
- Zyskind, G.; Nathan, O. Decentralizing privacy: Using blockchain to protect personal data. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar]
- Pavlov, E.; Rosenschein, J.S.; Topol, Z. Supporting privacy in decentralized additive reputation systems. In Proceedings of the International Conference on Trust Management, Oxford, UK, 29 March–1 April 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 108–119. [Google Scholar]
- Hasan, O.; Brunie, L.; Bertino, E. Preserving privacy of feedback providers in decentralized reputation systems. Comput. Secur. 2012, 31, 816–826. [Google Scholar] [CrossRef] [Green Version]
- Sharples, M.; Domingue, J. The blockchain and kudos: A distributed system for educational record, reputation and reward. In Proceedings of the European Conference on Technology Enhanced Learning, Lyon, France, 13–16 September 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 490–496. [Google Scholar]
- Albeanu, G. Blockchain technology and education. In Proceedings of the 12th International Conference on Virtual Learning ICVL, Sibiu, Romania, 28 October 2017; pp. 271–275. [Google Scholar]
- Alammary, A.; Alhazmi, S.; Almasri, M.; Gillani, S. Blockchain-based applications in education: A systematic review. Appl. Sci. 2019, 9, 2400. [Google Scholar] [CrossRef] [Green Version]
- Turkanović, M.; Hölbl, M.; Košič, K.; Heričko, M.; Kamišalić, A. EduCTX: A blockchain-based higher education credit platform. IEEE Access 2018, 6, 5112–5127. [Google Scholar] [CrossRef]
- Sestoft, P. Autonomous Pension Funds on the Blockchain; 1998 ACM Subject Classification, Report from Dagstuhl Seminar 17132, 26–29 March 2017. Available online: http://www.dagstuhl.de/17132 (accessed on 20 April 2019).
- Khezr, S.; Moniruzzaman, M.; Yassine, A.; Benlamri, R. Blockchain technology in healthcare: A comprehensive review and directions for future research. Appl. Sci. 2019, 9, 1736. [Google Scholar] [CrossRef] [Green Version]
- Yue, X.; Wang, H.; Jin, D.; Li, M.; Jiang, W. Healthcare data gateways: Found healthcare intelligence on blockchain with novel privacy risk control. J. Med. Syst. 2016, 40, 218. [Google Scholar] [CrossRef]
- Khan, M.A.; Algarni, F.; Quasim, M.T. Decentralised Internet of Things. In Decentralised Internet of Things; Springer: Berlin/Heidelberg, Germany, 2020; pp. 3–20. [Google Scholar]
- Shen, B.; Guo, J.; Yang, Y. MedChain: Efficient healthcare data sharing via blockchain. Appl. Sci. 2019, 9, 1207. [Google Scholar] [CrossRef] [Green Version]
- Parker, D. Blockchain Voting Used By Danish Political Party. CryptoCoinsNews. 23 April 2014. Available online: https://www.ccn.com/blockchain-voting-used-by-danish-political-party (accessed on 15 September 2019).
- Saroop, S. Block chain Technology: Assessment from Application Perspectives; Technical Report; University of Manchester EasyChair: Manchester, UK, 2020. [Google Scholar]
- Hjálmarsson, F.Þ.; Hreiðarsson, G.K.; Hamdaqa, M.; Hjálmtýsson, G. Blockchain-based e-voting system. In Proceedings of the 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 2–7 July 2018; pp. 983–986. [Google Scholar]
- Brophy, R. Blockchain and insurance: A review for operations and regulation. J. Financ. Regul. Compliance 2019, 28, 215–234. [Google Scholar] [CrossRef]
- Raikwar, M.; Mazumdar, S.; Ruj, S.; Gupta, S.S.; Chattopadhyay, A.; Lam, K.Y. A blockchain framework for insurance processes. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–4. [Google Scholar]
- Ibba, S.; Pinna, A.; Seu, M.; Pani, F.E. CitySense: Blockchain-oriented smart cities. In Proceedings of the XP2017 Scientific Workshops, Cologne, Germany, 22–26 May 2017; pp. 1–5. [Google Scholar]
- Wang, S.; Ouyang, L.; Yuan, Y.; Ni, X.; Han, X.; Wang, F.Y. Blockchain-Enabled Smart Contracts: Architecture, Applications, and Future Trends. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 2266–2277. [Google Scholar] [CrossRef]
- Ali, G.; Ahmad, N.; Cao, Y.; Asif, M.; Cruickshank, H.; Ali, Q.E. Blockchain based permission delegation and access control in Internet of Things (BACI). Comput. Secur. 2019, 86, 318–334. [Google Scholar] [CrossRef]
- Ali, G.; Ahmad, N.; Cao, Y.; Ali, Q.E.; Azim, F.; Cruickshank, H. BCON: Blockchain based access CONtrol across multiple conflict of interest domains. J. Netw. Comput. Appl. 2019, 147, 102440. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017; pp. 618–623. [Google Scholar]
- Chakravorty, A.; Rong, C. Ushare: User controlled social media based on blockchain. In Proceedings of the 11th International Conference on Ubiquitous Information Management and Communication, Beppu, Japan, 5–7 January 2017; p. 99. [Google Scholar]
- Basden, J.; Cottrell, M. How utilities are using blockchain to modernize the grid. Harv. Bus. Rev. 2017, 23, 1–8. [Google Scholar]
- Syed, T.A.; Alzahrani, A.; Jan, S.; Siddiqui, M.S.; Nadeem, A.; Alghamdi, T. A comparative analysis of blockchain architecture and its applications: Problems and recommendations. IEEE Access 2019, 7, 176838–176869. [Google Scholar] [CrossRef]
- Golosova, J.; Romanovs, A. Overview of the blockchain technology cases. In Proceedings of the 2018 59th International Scientific Conference on Information Technology and Management Science of Riga Technical University (ITMS), Riga, Latvia, 10–12 October 2018; pp. 1–6. [Google Scholar]
- Nofer, M.; Gomber, P.; Hinz, O.; Schiereck, D. Blockchain. Bus. Inf. Syst. Eng. 2017, 59, 183–187. [Google Scholar] [CrossRef]
- Beck, R. Beyond bitcoin: The rise of blockchain world. Computer 2018, 51, 54–58. [Google Scholar] [CrossRef] [Green Version]
- Lucas, B.; Páez, R.V. Consensus Algorithm for a Private Blockchain. In Proceedings of the 2019 IEEE 9th International Conference on Electronics Information and Emergency Communication (ICEIEC), Beijing, China, 12–14 July 2019; pp. 264–271. [Google Scholar]
- Gramoli, V. From blockchain consensus back to byzantine consensus. Future Gener. Comput. Syst. 2020, 107, 760–769. [Google Scholar] [CrossRef]
- Nakamoto, S.; Bitcoin, A. A Peer-to-Peer Electronic Cash System. Bitcoin. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 20 June 2019).
- Osadchuk, M.; Oliynykov, R. Method of Proof of Work consensus algorithms comparison. Paдиoтехника 2019, 198, 105–112. [Google Scholar] [CrossRef] [Green Version]
- Larimer, D. Delegated proof-of-stake (dpos). Bitshare Whitepaper 2014, 81, 85. [Google Scholar]
- Wahab, A.; Mehmood, W. Survey of consensus protocols. arXiv 2018, arXiv:1810.03357. [Google Scholar]
- Abraham, I.; Malkhi, D. The blockchain consensus layer and BFT. Bull. EATCS 2017, 3, 2017. [Google Scholar]
- Kotilevets; Ivanova, I.; Romanov, I.; Magomedov, S.; Nikonov, V.; Pavelev, S. Implementation of directed acyclic graph in blockchain network to improve security and speed of transactions. IFAC-PapersOnLine 2018, 51, 693–696. [Google Scholar] [CrossRef]
- Muratov, F.; Lebedev, A.; Iushkevich, N.; Nasrulin, B.; Takemiya, M. YAC: BFT consensus algorithm for blockchain. arXiv 2018, arXiv:1809.00554. [Google Scholar]
- Bamakan, S.M.H.; Motavali, A.; Bondarti, A.B. A survey of blockchain consensus algorithms performance evaluation criteria. Expert Syst. Appl. 2020, 154, 113385. [Google Scholar] [CrossRef]
- Zhang, S.; Lee, J.H. Analysis of the main consensus protocols of blockchain. ICT Express 2020, 6, 93–97. [Google Scholar] [CrossRef]
- Milutinovic, M.; He, W.; Wu, H.; Kanwal, M. Proof of luck: An efficient blockchain consensus protocol. In Proceedings of the 1st Workshop on System Software for Trusted Execution, Trento, Italy, 12–16 December 2016; p. 2. [Google Scholar]
- Miller, A.; Juels, A.; Shi, E.; Parno, B.; Katz, J. Permacoin: Repurposing bitcoin work for data preservation. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 18–21 May 2014; pp. 475–490. [Google Scholar]
- Corso, A. Performance Analysis of Proof-Of-Elapsed-Time (POET) Consensus in the Sawtooth Blockchain Framework. Master’s Thesis, University of Oregon, Eugene, OR, USA, 2019. [Google Scholar]
- Crosby, M.; Nachiappan; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain technology: Beyondbitcoin. Appl. Innov. 2016, 2, 71. [Google Scholar]
- De Angelis, S.; Aniello, L.; Baldoni, R.; Lombardi, F.; Margheri, A.; Sassone, V. Pbft vs proof-of- authority: Applying the cap theorem to permissioned blockchain. In Proceedings of the Second Italian Conference on Cyber Security, Milan, Italy, 6–9 February 2018. [Google Scholar]
- Ferdous, M.S.; Chowdhury, M.J.M.; Hoque, M.A.; Colman, A. Blockchain Consensuses Algorithms: A Survey. arXiv 2020, arXiv:2001.07091. [Google Scholar]
- Macdonald, M.; Liu-Thorrold, L.; Julien, R. The blockchain: A comparison of platforms and their uses beyond bitcoin. In Proceedings of the COMS4507-Adv. Computer and Network Security, The University of Queensland, Brisbane, Australia, 30 May 2017; Work Pap; pp. 1–18. [Google Scholar]
- Ren, L. Proof of Stake Velocity: Building the Social Currency of the Digital Age. Self-Publ. White Paper. 2014. Available online: https://www.semanticscholar.org/paper/Proof-of-Stake-Velocity%3A-Building-the-Social-of-the-Ren/8499c0b3d1138200fdebb88f964100d54a531878 (accessed on 6 July 2021).
- Moran, T.; Orlov, I. Proofs of Space-Time and Rational Proofs of Storage. IACR Cryptol. ePrint Arch. 2016, 2016, 35. [Google Scholar]
- Innerbichler, J.; Damjanovic-Behrendt, V. Federated byzantine agreement to ensure trustworthiness of digital manufacturing platforms. In Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems, Munich, Germany, 15 June 2018; pp. 111–116. [Google Scholar]
- Peterson, K.; Deeduvanu, R.; Kanjamala, P.; Boles, K. A blockchain-based approach to health information exchange networks. Proc. NIST Workshop Blockchain Healthc. 2016, 1, 1–10. [Google Scholar]
- Kumar, M.; Chand, S. MedHypChain: A patient-centered interoperability hyperledger-based medical healthcare system: Regulation in COVID-19 pandemic. J. Netw. Comput. Appl. 2021, 179, 102975. [Google Scholar] [CrossRef] [PubMed]
- Talukder, A.K.; Chaitanya, M.; Arnold, D.; Sakurai, K. Proof of disease: A blockchain consensus protocol for accurate medical decisions and reducing the disease burden. In Proceedings of the 2018 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Guangzhou, China, 8–12 October 2018; pp. 257–262. [Google Scholar]
- Chen, J.; Ma, X.; Du, M.; Wang, Z. A Blockchain Application for Medical Information Sharing. In Proceedings of the 2018 IEEE International Symposium on Innovation and Entrepreneurship (TEMS-ISIE), Beijing, China, 30 March–1 April 2018; pp. 1–7. [Google Scholar]
- Singh, M.; Kim, S. Blockchain based intelligent vehicle data sharing framework. arXiv 2017, arXiv:1708.09721. [Google Scholar]
- Yuan, Y.; Wang, F.Y. Towards blockchain-based intelligent transportation systems. In Proceedings of the 2016 IEEE 19th International Conference on Intelligent Transportation Systems (ITSC), Rio de Janeiro, Brazil, 1–4 November 2016; pp. 2663–2668. [Google Scholar]
- Yang, Z.; Zheng, K.; Yang, K.; Leung, V.C. A blockchain-based reputation system for data credibility assessment in vehicular networks. In Proceedings of the 2017 IEEE 28th annual international symposium on personal, indoor, and mobile radio communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–5. [Google Scholar]
- Kamilaris, A.; Fonts, A.; Prenafeta-Boldύ, F.X. The rise of blockchain technology in agriculture and food supply chains. Trends Food Sci. Technol. 2019, 91, 640–652. [Google Scholar] [CrossRef] [Green Version]
- Singh, R.; Benyoucef, L. A consensus based group decision making methodology for strategic selection problems of supply chain coordination. Eng. Appl. Artif. Intell. 2013, 26, 122–134. [Google Scholar] [CrossRef]
- Leng, K.; Bi, Y.; Jing, L.; Fu, H.C.; Van Nieuwenhuyse, I. Research on agricultural supply chain system with double chain architecture based on blockchain technology. Future Gener. Comput. Syst. 2018, 86, 641–649. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef] [Green Version]
- Aileni, R.M.; Suciu, G. IoMT: A blockchain perspective. In Decentralised Internet of Things; Springer: Berlin/Heidelberg, Germany, 2020; pp. 199–215. [Google Scholar]
- Li, S.; Oikonomou, G.; Tryfonas, T.; Chen, T.M.; Da Xu, L. A distributed consensus algorithm for decision making in service-oriented internet of things. IEEE Trans. Ind. Inform. 2014, 10, 1461–1468. [Google Scholar]
- Yang, C.; Li, X.; Yu, Y.; Wang, Z. Basing Diversified Services of Complex IIoT Applications on Scalable Block Graph Platform. IEEE Access 2019, 7, 22966–22975. [Google Scholar] [CrossRef]
- Lamport, L. Paxos made simple. ACM Sigact News 2001, 32, 18–25. [Google Scholar]
- Brambilla, G.; Amoretti, M.; Zanichelli, F. Using blockchain for peer-to-peer proof-of-location. arXiv 2016, arXiv:1607.00174. [Google Scholar]
- Fu, D.; Fang, L. Blockchain-based trusted computing in social network. In Proceedings of the 2016 2nd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 14–17 October 2016; pp. 19–22. [Google Scholar]
- O’Dair, M.; Beaven, Z.; Neilson, D.; Osborne, R.; Pacifico, P. Music On The Blockchain: Blockchain For Creative Industries Research Cluster. Middx. Univ. Rep. 2016, 1, 4–24. [Google Scholar]
- Spielman, A. Blockchain: Digitally Rebuilding the Real Estate Industry. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2016. [Google Scholar]
- Foroglou, G.; Tsilidou, A.L. Further applications of the blockchain. In Proceedings of the 12th Student Conference on Managerial Science and Technology, Athens, Greece, 14 May 2015. [Google Scholar]
- Baum, A. PropTech 3.0: The Future of Real Estate. 2017. Available online: https://www.sbs.ox.ac.uk/sites/default/files/2018-07/PropTech3.0.pdf (accessed on 20 May 2020).
- Guan, Z.; Si, G.; Zhang, X.; Wu, L.; Guizani, N.; Du, X.; Ma, Y. Privacy-preserving and efficient aggregation based on blockchain for power grid communications in smart communities. IEEE Commun. Mag. 2018, 56, 82–88. [Google Scholar] [CrossRef] [Green Version]
- Chen, Y. Proof of vote: A high-performance consensus protocol based on vote mechanism & consortium blockchain. In Proceedings of the 2017 IEEE 19th International Conference on High Performance Computing and Communications; IEEE 15th International Conference on Smart City; IEEE 3rd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Bangkok, Thailand, 18–20 December 2017; pp. 466–473. [Google Scholar]
- Buchman, E. Tendermint: Byzantine Fault Tolerance in the Age of Blockchains. Ph.D. Thesis, University of Guelph School of Engineering, Guelph, ON, Canada, 2016. [Google Scholar]
- Blocki, J.; Zhou, H.S. Designing proof of human-work puzzles for cryptocurrency and beyond. In Theory of Cryptography Conference; Springer: Berlin/Heidelberg, Germany, 2016; pp. 517–546. [Google Scholar]
- Namasudra, S.; Deka, G.C.; Johri, P.; Hosseinpour, M.; Gandomi, A.H. The revolution of blockchain: State-of-the-art and research challenges. Arch. Comput. Methods Eng. 2020, 28, 1497–1515. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. OSDI 1999, 99, 173–186. [Google Scholar]
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance and proactive recovery. ACM Trans. Comput. Syst. 2002, 20, 398–461. [Google Scholar] [CrossRef]
- Ongaro, D.; Ousterhout, J. The Raft Consensus Algorithm; Stanford University: Stanford, CA, USA, 2015. [Google Scholar]
- Huang, D.; Ma, X.; Zhang, S. Performance analysis of the Raft consensus algorithm for private blockchains. IEEE Trans. Syst. Man Cybern. Syst. 2019, 50, 172–181. [Google Scholar] [CrossRef] [Green Version]
- Ehmke, C.; Wessling, F.; Friedrich, C.M. Proof-of-property: A lightweight and scalable blockchain protocol. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May–3 June 2018; pp. 48–51. [Google Scholar]
- Dannen, C. Solidity programming. In Introducing Ethereum and Solidity; Springer: Berlin/Heidelberg, Germany, 2017; pp. 69–88. [Google Scholar]
- IO, E. EOS. IO Technical White Paper. EOS. IO. Available online: https://github.com/EOSIO/Documentation2017 (accessed on 18 December 2017).
- Lewenberg, Y.; Bachrach, Y.; Sompolinsky, Y.; Zohar, A.; Rosenschein, J.S. Bitcoin mining pools: A cooperative game theoretic analysis. In Proceedings of the 2015 International Conference on Autonomous Agents and Multiagent Systems, Istanbul, Turkey, 4–8 May 2015; pp. 919–927. [Google Scholar]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Workshop on Distributed Cryptocurrencies and Consensus Ledgers; IBM Research—Zurich CH-8803: Ruschlikon, Switzerland, 2016; Volume 310. [Google Scholar]
- Dhillon, V.; Metcalf, D.; Hooper, M. The hyperledger project. In Blockchain Enabled Applications; Springer: Berlin/Heidelberg, Germany, 2017; pp. 139–149. [Google Scholar]
- Valenta, M.; Sandner, P. Comparison of ethereum, hyperledger fabric and corda. Frankf. Sch. Blockchain Cent. 2017, 8, 1–8. [Google Scholar]
- Brown, R.G.; Carlyle, J.; Grigg, I.; Hearn, M. Corda: An introduction. R3 CEV 2016, 1, 15. [Google Scholar]
- Dinh, T.T.A.; Liu, R.; Zhang, M.; Chen, G.; Ooi, B.C.; Wang, J. Untangling blockchain: A data processing view of blockchain systems. IEEE Trans. Knowl. Data Eng. 2018, 30, 1366–1385. [Google Scholar] [CrossRef] [Green Version]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef] [Green Version]
- Sayeed, S.; Marco-Gisbert, H. Assessing blockchain consensus and security mechanisms against the 51% attack. Appl. Sci. 2019, 9, 1788. [Google Scholar] [CrossRef] [Green Version]
- Wüst, K.; Gervais, A. Ethereum Eclipse Attacks; Technical Report; ETH: Zurich, Germany, 2016. [Google Scholar]
- Nayak, K.; Kumar, S.; Miller, A.; Shi, E. Stubborn mining: Generalizing selfish mining and combining with an eclipse attack. In Proceedings of the 2016 IEEE European Symposium on Security and Privacy (EuroS&P), Saarbruecken, Germany, 21–24 March 2016; pp. 305–320. [Google Scholar]
- Sahay, R.; Geethakumari, G.; Mitra, B. A novel blockchain based framework to secure IoT-LLNs against routing attacks. Computing 2020, 102, 2445–2470. [Google Scholar] [CrossRef]
- Saad, M.; Cook, V.; Nguyen, L.; Thai, M.T.; Mohaisen, A. Partitioning attacks on bitcoin: Colliding space, time, and logic. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–10 July 2019; pp. 1175–1187. [Google Scholar]
- Natoli, C.; Gramoli, V. The blockchain anomaly. In Proceedings of the 2016 IEEE 15th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 31 October–2 November 2016; pp. 310–317. [Google Scholar]
- Pilkington, M. Blockchain Technology: Principles and Applications. In Research Handbook on Digital Transformations; Edward Elgar Publishing: Cheltenham, UK, 2016; Available online: https://www.elgaronline.com/ (accessed on 16 May 2021).
- Lee, H.; Shin, M.; Kim, K.S.; Kang, Y.; Kim, J. Recipient-oriented transaction for preventing double spending attacks in private blockchain. In Proceedings of the 2018 15th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Hong Kong, China, 11–13 June 2018; pp. 1–2. [Google Scholar]
- Rosenfeld, M. Analysis of hashrate-based double spending. arXiv 2014, arXiv:1402.2009. [Google Scholar]
- Pérez-Solà, C.; Delgado-Segura, S.; Navarro-Arribas, G.; Herrera-Joancomartí, J. Double-spending prevention for bitcoin zero-confirmation transactions. Int. J. Inf. Secur. 2019, 18, 451–463. [Google Scholar] [CrossRef] [Green Version]
- Malik, A.; Gautam, S.; Abidin, S.; Bhushan, B. Blockchain Technology-Future of IoT: Including Structure, Limitations and Various Possible Attacks. In Proceedings of the 2019 2nd International Conference on Intelligent Computing, Instrumentation and Control Technologies (ICICICT), Kannur, India, 5–6 July 2019; Volume 1, pp. 1100–1104. [Google Scholar]
- Mechkaroska, D.; Dimitrova, V.; Popovska-Mitrovikj, A. Analysis of the possibilities for improvement of BlockChain technology. In Proceedings of the 2018 26th Telecommunications Forum (TELFOR) IEEE, Belgrade, Serbia, 20–21 November 2018; pp. 1–4. [Google Scholar]
- Morganti, G.; Schiavone, E.; Bondavalli, A. Risk Assessment of Blockchain Technology. In Proceedings of the 2018 Eighth Latin-American Symposium on Dependable Computing (LADC), Belgrade, Serbia, 20–21 November 2018; pp. 87–96. [Google Scholar]
- Alkhalifah, A.; Ng, A.; Kayes, A.; Chowdhury, J.; Alazab, M.; Watters, P.A. A taxonomy of blockchain threats and vulnerabilities. In Blockchain for Cybersecurity and Privacy; CRC Press: Boca Raton, FL, USA, 2020; pp. 3–28. [Google Scholar]
- Dasgupta, D.; Shrein, J.M.; Gupta, K.D. A survey of blockchain from security perspective. J. Bank. Financ. Technol. 2019, 3, 1–17. [Google Scholar] [CrossRef]
- Alizadeh, M.; Andersson, K.; Schelén, O. A Survey of Secure Internet of Things in Relation to Blockchain. J. Internet Serv. Inf. Secur. 2020, 3, 47–75. [Google Scholar]
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.; Mohaisen, A. Exploring the attack surface of blockchain: A systematic overview. arXiv 2019, arXiv:1904.03487. [Google Scholar]
- Kaushik, A.; Choudhary, A.; Ektare, C.; Thomas, D.; Akram, S. Blockchain—Literature survey. In Proceedings of the 2017 2nd IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), Bangalore, India, 19–20 May 2017; pp. 2145–2148. [Google Scholar]
- Vokerla, R.R.; Shanmugam, B.; Azam, S.; Karim, A.; De Boer, F.; Jonkman, M.; Faisal, F. An Overview of Blockchain Applications and Attacks. In Proceedings of the 2019 International Conference on Vision Towards Emerging Trends in Communication and Networking (ViTECoN), Vellore, India, 30–31 March 2019; pp. 1–6. [Google Scholar]
- McGhin, T.; Choo, K.K.R.; Liu, C.Z.; He, D. Blockchain in healthcare applications: Research challenges and opportunities. J. Netw. Comput. Appl. 2019, 135, 62–75. [Google Scholar] [CrossRef]
- Lunardi, R.C.; Michelin, R.A.; Neu, C.V.; Nunes, H.C.; Zorzo, A.F.; Kanhere, S.S. Impact of consensus on appendable-block blockchain for IoT. In Proceedings of the 16th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, Houston, TX, USA, 12–14 November 2019; pp. 228–237. [Google Scholar]
- Zhang, L.; Peng, M.; Wang, W.; Su, Y.; Cui, S.; Kim, S. Secure and Efficient Data Storage and Sharing Scheme Based on Double Blockchain. CMC Comput. Mater. Contin. 2021, 66, 499–515. [Google Scholar]
- Ali, Q.E.; Ahmad, N.; Malik, A.H.; Ali, G.; Rehman, W.U. Issues, challenges, and research opportunities in intelligent transport system for security and privacy. Appl. Sci. 2018, 8, 1964. [Google Scholar] [CrossRef] [Green Version]
- Ali, Q.E.; Ahmad, N.; Malik, A.H.; Rehman, W.U.; Din, A.U.; Ali, G. ASPA: Advanced Strong Pseudonym based Authentication in Intelligent Transport System. PLoS ONE 2019, 14, e0221213. [Google Scholar] [CrossRef] [Green Version]
- Taleb, T.; Sakhaee, E.; Jamalipour, A.; Hashimoto, K.; Kato, N.; Nemoto, Y. A stable routing protocol to support ITS services in VANET networks. IEEE Trans. Veh. Technol. 2007, 56, 3337–3347. [Google Scholar] [CrossRef]
- Taleb, T.; Ochi, M.; Jamalipour, A.; Kato, N.; Nemoto, Y. An efficient vehicle-heading based routing protocol for VANET networks. In Proceedings of the IEEE Wireless Communications and Networking Conference, 2006, WCNC 2006, Las Vegas, NV, USA, 3–6 April 2006; Volume 4, pp. 2199–2204. [Google Scholar]
- Qi, W.; Landfeldt, B.; Song, Q.; Guo, L.; Jamalipour, A. Traffic differentiated clustering routing in DSRC and C-V2X hybrid vehicular networks. IEEE Trans. Veh. Technol. 2020, 69, 7723–7734. [Google Scholar] [CrossRef] [Green Version]
- Alghamdi, N.S.; Khan, M.A. Energy-Efficient and Blockchain-Enabled Model for Internet of Things (IoT) in Smart Cities. CMC Comput. Mater. Contin. 2021, 66, 2509–2524. [Google Scholar]
- Alamri, M.; Jhanjhi, N.; Humayun, M. Blockchain for Internet of Things (IoT) Research Issues Challenges & Future Directions: A Review. Int. J. Comput. Sci. Netw. Secur. 2019, 19, 244–258. [Google Scholar]
- Gauhar, A.; Ahmad, N.; Cao, Y.; Khan, S.; Cruickshank, H.; Qazi, E.A.; Ali, A. xDBAuth: Blockchain based cross domain authentication and authorization framework for Internet of Things. IEEE Access 2020, 8, 58800–58816. [Google Scholar] [CrossRef]
- Ahmad, I.; Alqarni, M.A.; Almazroi, A.A.; Alam, L. Real Estate Management via a Decentralized Blockchain Platform. CMC Comput. Mater. Contin. 2021, 66, 1813–1822. [Google Scholar]
- Li, M.; Shen, L.; Huang, G.Q. Blockchain-enabled workflow operating system for logistics resources sharing in E-commerce logistics real estate service. Comput. Ind. Eng. 2019, 135, 950–969. [Google Scholar] [CrossRef]









| Articles | Blockchain Applications | Blockchain Architecture | Development Platform | Crypto Currencies | Health Care | Intelligent Transport Systems and Vehicular Adhoc Networks | Supply Chain | Internet of Things | Big Data | Cellular Networks | Social Networks | Distributed Web Services and Storage | Governance | Entertainment | Real Estate | Power | General |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Comparative Analysis of Consensus Algorithms [21] | No | No | No | Yes | No | No | No | No | No | No | No | No | No | No | No | No | No |
| State of the Art and Challenges Facing Consensus Protocols on Blockchain [22] | No | No | No | Yes | No | No | No | No | No | No | No | No | No | No | No | No | Yes |
| A survey on Consensus Mechanisms and Mining Management in Blockchain Networks [23] | Yes | Yes | No | Yes | Yes | Yes | No | Yes | No | Yes | No | No | No | No | No | No | Yes |
| A survey about consensus algorithms used in blockchain [24] | No | Yes | No | Yes | No | No | No | No | No | No | No | No | No | No | No | No | No |
| Proposed work | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Existing Surveys | Proposed Survey |
|---|---|
| Applications of blockchain other than cryptocurrencies are rarely discussed [21,22]. | About 14 blockchain applications covered. |
| Blockchain architecture rarely discussed [21,22]. | Blockchain architecture covered. |
| Consensus algorithms used in cryptocurrencies discussed are few in number [21,22,23,24]. | Discusses a large number of consensus algorithms used in cryptocurrencies as well as of other applications. |
| Development platforms are not discussed [21,23,25]. | Development platforms are discussed. |
| Existing surveys related to consensus algorithms of blockchain can be read for the understanding of consensus based on a particular application [21,22,23,24,25]. | This paper gives a broader view of different blockchain applications and the consensus used in those applications, making it easy for the researchers to follow the same consensus for a specific application. However one can also compare the consensus for the optimized solution of their work. |
| S.No | Consensus Algorithms | Permissioned/Permissionless | Platform | Programming Language | Advantages | Disadvantages |
|---|---|---|---|---|---|---|
| 1 | Proof of Work (PoW) [67] | Permissionless | Bitcoin | C++ | Better security, Suitable for variety of applications | Wastes considerable energy, 51% Attack possible Advance hardware required |
| 2 | Delayed Proof of Work (DPoW) [68] | Permissionless (But it can be customized as permissioned) | Komodo | Python | Energy efficient, Increased security | Blockchain using Pow and PoS can be part of this consensus |
| 3 | Proof of Stack (PoS) [21] | Permissionless | Peercoin.Nxt, Blackcoin, Shadow coin, Ethereum | Java | High speed Less energy consumption, No advance hardware required | Rich get richer |
| 4 | Steller Consensus Protocol (SCP) [20] | Permissionless | Steller | C/C++, JavaScript, Go etc. | Fast transactions with low fees | Inefficient in case of number of messages sent |
| 5 | Delegated Proof of Stack (DPoS) [69] | Permissioned/Permissionless | Steem.it, EOS, Bitshares, Lisk | Javascript, C++, Ark | Secure Real-time Voting, Better distribution of rewards | Cartel formation, Easier for 51% attack, Partially decentralized |
| 6 | Leased Proof of Stack (LPoS) [70] | Permissioned | Waves | Scala | Fair usage, lease coins | Decentralization issue |
| 7 | Byzantine Fault Tolerance (BFT) [71,72] | Permissionless | Ripple, Steller, Hyperledger Fabric | Not known | Less Energy consumption, No advance hardware, Fast, Scalable | Less suitable for public blockchain |
| 8 | Directed Acyclic Graph (DAG) [73] | Permissionless | Iota, Hashgraph, Byteball, Raiblocks/Nano | Javascript, Rust, Java, Go, C++ | Low-cost Network, Scalable | Difficult implementation, Not good for smart contracts |
| 9 | Proof of Weight [74] | Not Known | Filecoin, Algorand, Chia | Succinct Non-interactive Argument of Knowledge (SNARK)/Succinct Transparent Argument of Knowledge (STARK) | Scalable, Customizable | Incentivization issue |
| 10 | Delegated Byzantine Fault Tolerance (DBFT) [75] | Permissioned/Permissionless | Neo | C#, Python, .NET, Java, C++, C, Go, Kotlin, Javascript | Fast, scalable | Conflictions on the chain |
| 11 | Ripple Protocol Consensus Algorithm (RPCA) [20,76] | Permissionless | XRP | Java, C++, Node.js | Energy efficient, quick | Centralization |
| 12 | Proof of Importance (PoI) [75] | Permissionless | XEM | Java, C++ | Vesting Transaction partnership | Decentralization issue |
| 13 | Proof of Exercise (PoE) [20] | Permissionless | NA | NA | Avoid wastage of computational power | Needs dedicated research for practical implementation |
| 14 | Proof of Ownership (PoO) [75] | Permissionless | Decentalized credits (Decred) | Go | Use of unique pseudonyms makes multiple attacks difficult | Not known |
| 15 | Proof of Luck (PoL) [77] | Not Known | TEE (Trusted Execution Environment) such as Intel SGX-enabled CPUs | Not known | Decentralized, Low latency with transaction validation, Power safe | Prone to revision attack Forking, Unfair |
| 16 | Proof of Activity (PoA) [75] | Permissionless | Bitcoin or Bitcoin related technologies | Solidity, Java, Python | Equal contribution, Reduces 51% attack | Better energy consumption, Double signing |
| 17 | Proof of Publication (PoP) [21] | Permissioned | Bitcoin or Bitcoin related technologies and General Applications | Python, C++, Shell, Javascript | Can be used in cryptocurrency and general applications | No Energy saving |
| 18 | Proof of Burn (PoB) [21] | Permissionless | Slimcoin/Redcoin | Golang, C++, Solidity, LLL Serpent | Network preservation | Coins wastage, Not good for short term investors |
| 19 | Proof of Retrievability (PoR) [78] | Permissioned/Permissionless | Microsoft, Permacoin | Golang, C++, Solidity, LLL Serpent | Efficient | Extending the quantity of queries is challenging |
| 20 | Proof of Elapsed Time (PoET) [79] | Permissioned/Permissionless | Hyperledger sawtooth | Python, Javascript, Go, C++, Java and Rust | Cheap participation | Special hardware, Not suitable for public blockchain |
| 21 | Proof of Capacity (PoC) [21] | Permissionless | Burstcoin, Chia and spacemint | Java | Efficient, Distributed, Cheap, Utilizes free dik space as a resource | Decentralization issue |
| 22 | Proof of Existence (PoE) [80] | Permissionless | Poex.io, Hero Node, Dragon Chain | Not known | Document time stamping, Document integrity | Not known |
| 23 | Proof of Authority [81] (PoAuthority) | Permissioned | PoA.Network, Ethereum, Kovan testnet, vechain | Solidity, Java, Python | Reduced maintenance costs | Centralization |
| 24 | Ethash [82,83] | Permissionless | Ethereum | Python, Go, Java, Javascript, Ruby, C++ | Avoids 51% attack | Memory intensive, Needs computers with powerful GPUs |
| 25 | Proof of Stake Velocity (PoSV) [84] | Permissionless | Redcoin | Not known | Reduces the time wastage of mining, Removes mining arms race | Not known |
| 26 | Proof of Space Time (PoST) [84] | Not Known | Filecoin | Go, Javascript | Cheap computationaly | Needs more interaction |
| 27 | Federated Byzantine Agreement (FBA) [85] | Permissioned/Permissionless | Steller and Ripple | C/C++, Javascript, Go, Java, Node.js | Less participants to achieve consensus’ Robust | The parties must accept the exact number of candidates |
| S.No | Consensus Algorithms | Permissioned/Permissionless | Platform | Applications | Programming Language | Advantages | Disadvantages |
|---|---|---|---|---|---|---|---|
| 1 | Proof of Vote [109] | Permissioned | Not Known | Consortium Blockchains | Any programming language can be used | Consistency, Availability, Partition tolerance | Problem in modular design and parallel processing |
| 2 | Tendermint [110] | Permissioned | Cosmos, Ethereum | ABCI (Application Blockchain Interface) | Rust, Go, Haskell, C/C++, Java etc | Does not require mining | Unfair |
| 3 | Proof of Human Work [111] | Not known | Humancoin | Cryptocurrency, password protection, Bot detection) | Not known | Fair | Requires an initial trusted setup, Prone to malicious attack |
| 4 | Simplified Byzantine Fault Tolerance [112] | Permissioned | Chain | Financial Applications | Java, Node, Ruby | Good security, Signature validation | Not for public blockchain |
| 5 | Practical Byzantine Fault Tolerance [112,113] | Permissioned | Hyperledger, Zilliqa | Cryptocurrency and other asynchronous systems | Golang, Java | High transaction throughput | Centralized |
| 6 | Raft [114,115] | More suitable for Private/Permissioned Blockchains [62] | Kaleido, IPFS Private Cluster, Quorum | CockroachDB | Go, C++, Java, Scala and Rust | Supports configuration changes, Simple and easy as compared to Paxos | Centralized |
| 7 | Proof of Proof | Not known | Veriblock | Not known | Not known | Security inheriting | Provides potential attack vectors |
| 8 | Proof of Believability | Not known | IOST | Not known | Not known | Fast finality and more decentralized than PoS, Scalability | Not known yet |
| 9 | Proof of Property [116] | Not known | Ethereum | Not known | Not known | Scalable, Save a lot of local space | Forking may create issues |
| Comparison Parameters | Ethereum | Cosmos | Cardano | EOS | Bitcoin | Hyperledger | Corda |
|---|---|---|---|---|---|---|---|
| Token | ETH | ATOM | ADA | EOS | Bitcoin | n/a | SDK |
| Public/Private | Public | Public/Private | Public | Public/Private | Public | Public/Private | Private |
| Programming Languages | Solidity | Java, C++, Python, Go | Haskell | JavaScript, Python, Ruby | Golang | Java, Golang, Node | Kotlin, Java |
| Consensus Algorithms | Proof of Work (Currently used), Proof of Stake (In Future) | Tendermint (Byzantine Fault-Tolerant, Proof of Stake) | Proof of Stack | Delegated Proof of Stack | Proof of Work | Practical Byzantine Fault Tolerance | Pluggable Consensus |
| Transactions Per Second | 25 | 10,000 | n/a | Millions (theoretically) | 1/3 to 1/7 | More than 1000 | Between 15 and 1678 TPS |
| Transaction Size | 1 MB | 250 bytes | n/a | n/a | 1 MB | Changeable (depending on framework) | Maximum size in bytes |
| Open Source | True | True | True | True | True | True | True |
| Pros | Anyone can write smart-contract and anyone can view that contract | Works like a hub for blockchains, based on Tendermint | Scalability, Side chain which reduce the risk of hacks. | Parallel processing, low latency, free usage (claimed not proven). | Safe and secure, High token value. | Don’t use cryptocurrency so it is ideal for business networks. | Designed specifically for financial applications |
| Cons | Scalability issue, 25 transactions per second is very slow | Complex technology which may have compatibility issues with latest technologies and new blockchains | Maintaining side chain is complicated and it will require its own miners. | Never actually free, not fully decentralized, the free transaction fee are imposed on everyone who have EOS. | Very slow, not ideal for programming while there are other faster technologies. | There are a lot of frameworks to choose from and they all have different requirements to implement and setup. | Partially decentralized, not much suitable for IoT resource constrained networks |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Johar, S.; Ahmad, N.; Asher, W.; Cruickshank, H.; Durrani, A. Research and Applied Perspective to Blockchain Technology: A Comprehensive Survey. Appl. Sci. 2021, 11, 6252. https://doi.org/10.3390/app11146252
Johar S, Ahmad N, Asher W, Cruickshank H, Durrani A. Research and Applied Perspective to Blockchain Technology: A Comprehensive Survey. Applied Sciences. 2021; 11(14):6252. https://doi.org/10.3390/app11146252
Chicago/Turabian StyleJohar, Sumaira, Naveed Ahmad, Warda Asher, Haitham Cruickshank, and Amad Durrani. 2021. "Research and Applied Perspective to Blockchain Technology: A Comprehensive Survey" Applied Sciences 11, no. 14: 6252. https://doi.org/10.3390/app11146252
APA StyleJohar, S., Ahmad, N., Asher, W., Cruickshank, H., & Durrani, A. (2021). Research and Applied Perspective to Blockchain Technology: A Comprehensive Survey. Applied Sciences, 11(14), 6252. https://doi.org/10.3390/app11146252






