Advancements and Research Trends in Microgrids Cybersecurity
Abstract
:1. Introduction
2. Cybersecurity in Smart Microgrids
3. The Action of IEC 62351
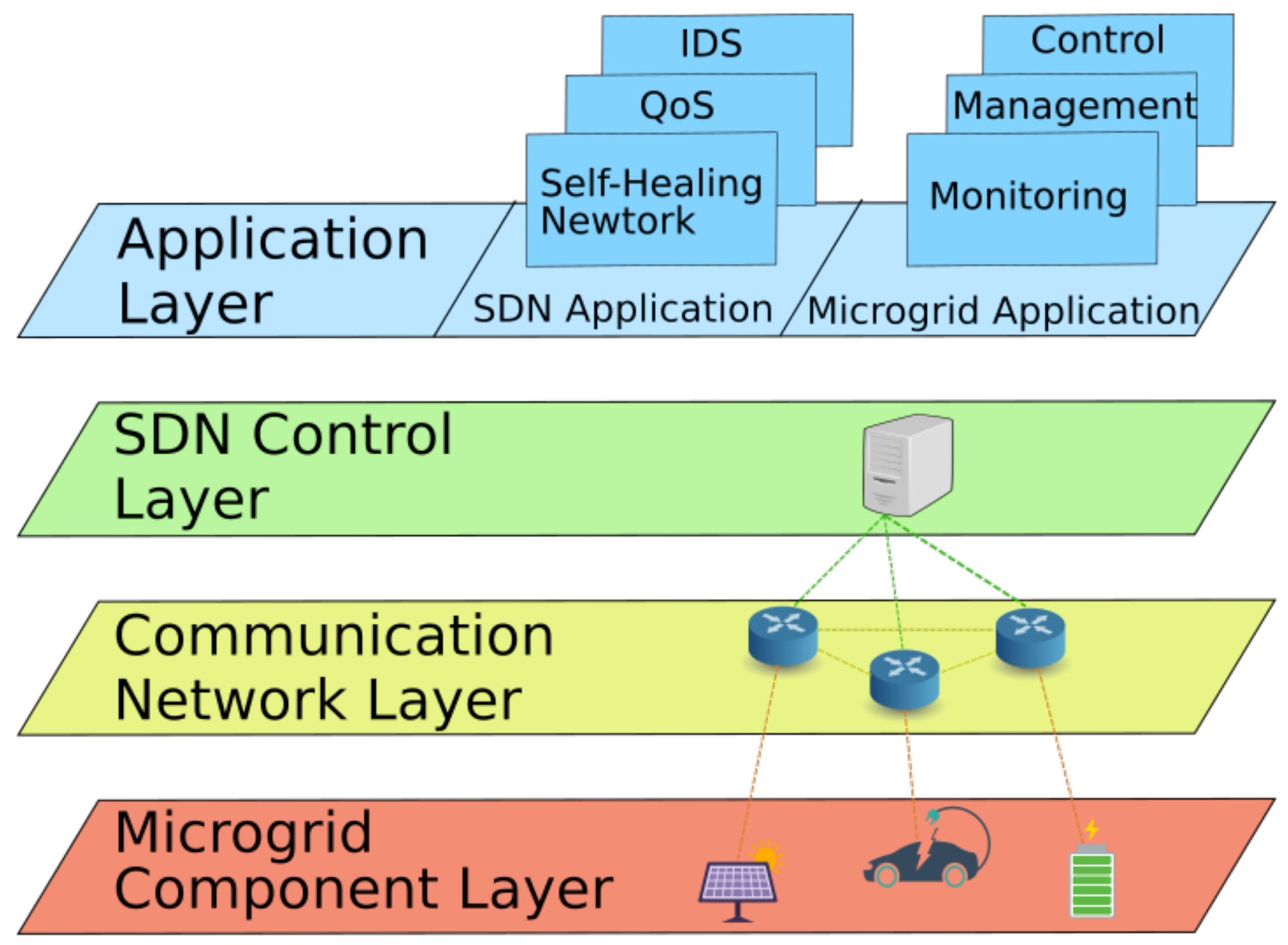
4. Software Defined Networking
- quick reset and reconfiguration of switches in order to isolate suspicious devices in the microgrid;
- establishment of application-specific filtering operations in the switches located close to attack sources; and
- on-demand path establishment for control commands to shrink attacker’s operation time window.
5. Intrusion Detection Systems
- Network Intrusion Detection Systems (NIDS) that analyze network traffic collected from one or more points of the communication network; and
- Host Intrusion Detection Systems (HIDS) that analyze the activity of a single host (i.e., a terminal) of the network.
- Configurability: capability to be configured as specified by the requirements of the target system;
- Configuration and Knowledge Security: HIDS configuration and used data should be protected against unauthorized access and modifications;
- Resiliency: HIDS action cannot affect the availability of the device;
- Low Performance Overhead: the execution of the HIDS on the target device should not negatively influence the performance of the underlying system;
- Low Detection Time: detection and response to intrusions should be as fast as possible; and
- Interoperability: the HIDS should be able to interact with other technologies, such as Security Information and Event Management (SIEM).
- IEC 60834 requires that the latency of the transmission and reception of a control signal related to a protective action has to be lower than 10 ms, while IEC 61850 imposes a latency lower than 3 ms;
- IEEE 1646-2004 requires information on protective actions to be exchanged by the devices inside the same substation in a time lower than a quarter of a period (i.e., 5 or 4 ms depending on the 50 or 60 Hz frequency); and
- less stringent limits (between 8 and 12 ms) are required for the exchange of information on protective actions with devices outside the substation.
6. Physics-Based Anomaly Detection
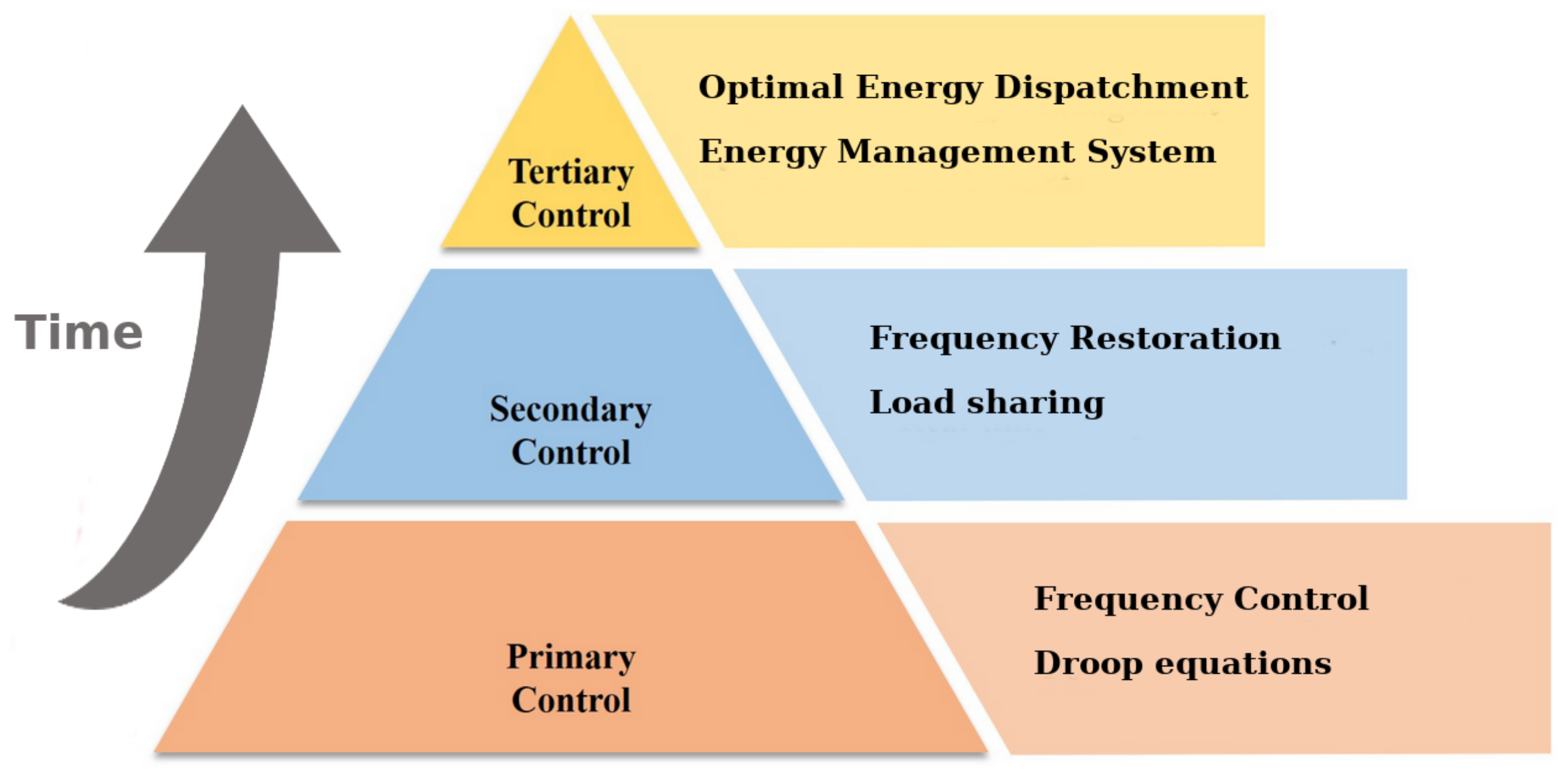
7. Resilient Control Strategies
- Primary Control: aimed at restoring the imbalance between generation and load by changing the frequency of the power system. In inverter-based microgrids, this is achieved through droop equations; it is the fastest among the three levels.
- Secondary Control: aimed at restoring the nominal value of the frequency and the power exchange among the power systems. It acts at longer time.
- Tertiary Control: aimed at optimizing the economical aspects of load sharing, usually through an Energy Management System (EMS).
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| ICT | Information and Communication Technology |
| SM | Smart Microgrid |
| DER | Distributed Energy Resources |
| SCADA | Supervisory Control And Data Acquisition |
| MMS | Manufacturing Message Specification |
| GOOSE | Generic Object Oriented Substation Event |
| SVM | Sampled Measured Values |
| SDN | Software Defined Network |
| ICS | Industrial Control Systems |
| NFV | Network Function Virtualization |
| PLC | Programmable Logic Controller |
| IDS | Intrusion Detection System |
| NIDS | Network Intrusion Detection System |
| HIDS | Host Intrusion Detection System |
| DoS | Denial of Service |
| IPS | Intrusion Prevention System |
| RTOS | Real-Time Operating Systems |
| RTU | Remote Terminal Unit |
| EMS | Energy Management System |
| PV | Photovoltaic |
References
- Falliere, N.; Murchu, L.O.; Chien, E. W32.Stuxnet Dossier; Symantec Security Response; Symantec Corp.: Tempe, AZ, USA, 2011; Volume 5, p. 29. [Google Scholar]
- Bencsáth, B.; Pék, G.; Buttyán, L.; Felegyhazi, M. The cousins of stuxnet: Duqu, flame, and gauss. Future Internet 2012, 4, 971–1003. [Google Scholar] [CrossRef] [Green Version]
- Case, D.U. Analysis of the Cyber Attack on the Ukrainian Power Grid; Electricity Information Sharing and Analysis Center (E-ISAC): Washington, DC, USA, 2016; p. 388. [Google Scholar]
- Liu, X.; Shahidehpour, M.; Cao, Y.; Wu, L.; Wei, W.; Liu, X. Microgrid risk analysis considering the impact of cyber attacks on solar PV and ESS control systems. IEEE Trans. Smart Grid 2016, 8, 1330–1339. [Google Scholar] [CrossRef]
- Qi, J.; Hahn, A.; Lu, X.; Wang, J.; Liu, C.C. Cybersecurity for distributed energy resources and smart inverters. IET Cyber-Phys. Syst. Theory Appl. 2016, 1, 28–39. [Google Scholar] [CrossRef] [Green Version]
- Hossain, E.; Kabalci, E.; Bayindir, R.; Perez, R. Microgrid testbeds around the world: State of art. Energy Convers. Manag. 2014, 86, 132–153. [Google Scholar] [CrossRef]
- Lee, A. Electric Sector Failure Scenarios and Impact Analyses; Electric Power Research Institute: Palo Alto, CA, USA, 2013; Volume 1. [Google Scholar]
- Wang, W.; Lu, Z. Cyber security in the smart grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A survey on cyber security for smart grid communications. IEEE Commun. Surv. Tutor. 2012, 14, 998–1010. [Google Scholar] [CrossRef] [Green Version]
- El Mrabet, Z.; Kaabouch, N.; El Ghazi, H.; El Ghazi, H. Cyber-security in smart grid: Survey and challenges. Comput. Electr. Eng. 2018, 67, 469–482. [Google Scholar] [CrossRef] [Green Version]
- Nejabatkhah, F.; Li, Y.W.; Liang, H.; Ahrabi, R.R. Cyber-Security of Smart Microgrids: A Survey. Energies 2021, 14, 27. [Google Scholar] [CrossRef]
- Canaan, B.; Colicchio, B.; Ould Abdeslam, D. Microgrid cyber-security: Review and challenges toward resilience. Appl. Sci. 2020, 10, 5649. [Google Scholar] [CrossRef]
- Volkova, A.; Niedermeier, M.; Basmadjian, R.; de Meer, H. Security challenges in control network protocols: A survey. IEEE Commun. Surv. Tutor. 2018, 21, 619–639. [Google Scholar] [CrossRef]
- Bani-Ahmed, A.; Weber, L.; Nasiri, A.; Hosseini, H. Microgrid communications: State of the art and future trends. In Proceedings of the 2014 International Conference on Renewable Energy Research and Application (ICRERA), Milwaukee, WI, USA, 19–22 October 2014; pp. 780–785. [Google Scholar]
- Reda, H.T.; Ray, B.; Peidaee, P.; Anwar, A.; Mahmood, A.; Kalam, A.; Islam, N. Vulnerability and Impact Analysis of the IEC 61850 GOOSE Protocol in the Smart Grid. Sensors 2021, 21, 1554. [Google Scholar] [CrossRef]
- Kang, B.; Maynard, P.; McLaughlin, K.; Sezer, S.; Andrén, F.; Seitl, C.; Kupzog, F.; Strasser, T. Investigating cyber-physical attacks against IEC 61850 photovoltaic inverter installations. In Proceedings of the 2015 IEEE 20th Conference on Emerging Technologies & Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar]
- Schlegel, R.; Obermeier, S.; Schneider, J. A security evaluation of IEC 62351. J. Inf. Secur. Appl. 2017, 34, 197–204. [Google Scholar] [CrossRef]
- Hussain, S.S.; Ustun, T.S.; Kalam, A. A review of IEC 62351 security mechanisms for IEC 61850 message exchanges. IEEE Trans. Ind. Inform. 2019, 16, 5643–5654. [Google Scholar] [CrossRef]
- Ustun, T.S.; Hussain, S.S. IEC 62351-4 Security Implementations for IEC 61850 MMS Messages. IEEE Access 2020, 8, 123979–123985. [Google Scholar] [CrossRef]
- Hussain, S.S.; Farooq, S.M.; Ustun, T.S. Analysis and implementation of message authentication code (MAC) algorithms for GOOSE message security. IEEE Access 2019, 7, 80980–80984. [Google Scholar] [CrossRef]
- Farooq, S.M.; Hussain, S.S.; Ustun, T.S. Performance evaluation and analysis of IEC 62351-6 probabilistic signature scheme for securing GOOSE messages. IEEE Access 2019, 7, 32343–32351. [Google Scholar] [CrossRef]
- Hu, F.; Hao, Q.; Bao, K. A survey on software-defined network and openflow: From concept to implementation. IEEE Commun. Surv. Tutor. 2014, 16, 2181–2206. [Google Scholar] [CrossRef]
- Rehmani, M.H.; Davy, A.; Jennings, B.; Assi, C. Software defined networks-based smart grid communication: A comprehensive survey. IEEE Commun. Surv. Tutor. 2019, 21, 2637–2670. [Google Scholar] [CrossRef]
- Ren, L.; Qin, Y.; Wang, B.; Zhang, P.; Luh, P.B.; Jin, R. Enabling resilient microgrid through programmable network. IEEE Trans. Smart Grid 2016, 8, 2826–2836. [Google Scholar] [CrossRef]
- Piedrahita, A.F.M.; Gaur, V.; Giraldo, J.; Cardenas, A.A.; Rueda, S.J. Leveraging software-defined networking for incident response in industrial control systems. IEEE Softw. 2017, 35, 44–50. [Google Scholar] [CrossRef]
- Genge, B.; Graur, F.; Haller, P. Experimental assessment of network design approaches for protecting industrial control systems. Int. J. Crit. Infrastruct. Prot. 2015, 11, 24–38. [Google Scholar] [CrossRef]
- Sándor, H.; Genge, B.; Szántó, Z.; Márton, L.; Haller, P. Cyber attack detection and mitigation: Software defined survivable industrial control systems. Int. J. Crit. Infrastruct. Prot. 2019, 25, 152–168. [Google Scholar] [CrossRef]
- Yang, J.; Zhou, C.; Tian, Y.C.; Yang, S.H. A software-defined security approach for securing field zones in industrial control systems. IEEE Access 2019, 7, 87002–87016. [Google Scholar] [CrossRef]
- Jin, D.; Li, Z.; Hannon, C.; Chen, C.; Wang, J.; Shahidehpour, M.; Lee, C.W. Toward a cyber resilient and secure microgrid using software-defined networking. IEEE Trans. Smart Grid 2017, 8, 2494–2504. [Google Scholar] [CrossRef]
- Fausto, A.; Marchese, M. Implementation details to reduce the latency of an SDN Statistical Fingerprint-Based IDS. In Proceedings of the 2019 International Symposium on Advanced Electrical and Communication Technologies (ISAECT), Rome, Italy, 27–29 November 2019; pp. 1–6. [Google Scholar]
- Danzi, P.; Angjelichinoski, M.; Stefanović, Č.; Dragičević, T.; Popovski, P. Software-defined microgrid control for resilience against denial-of-service attacks. IEEE Trans. Smart Grid 2018, 10, 5258–5268. [Google Scholar] [CrossRef]
- Li, Y.; Qin, Y.; Zhang, P.; Herzberg, A. SDN-enabled cyber-physical security in networked microgrids. IEEE Trans. Sustain. Energy 2018, 10, 1613–1622. [Google Scholar] [CrossRef]
- Haas, Z.J.; Culver, T.L.; Sarac, K. Vulnerability Challenges of Software Defined Networking. IEEE Commun. Mag. 2021, 59, 88–93. [Google Scholar] [CrossRef]
- Liu, M.; Xue, Z.; Xu, X.; Zhong, C.; Chen, J. Host-based intrusion detection system with system calls: Review and future trends. ACM Comput. Surv. (CSUR) 2018, 51, 1–36. [Google Scholar] [CrossRef]
- Martinez, C.V.; Vogel-Heuser, B. A host intrusion detection system architecture for embedded industrial devices. J. Frankl. Inst. 2019, 358, 210–236. [Google Scholar] [CrossRef]
- Vargas, C.; Langfinger, M.; Vogel-Heuser, B. A tiered security analysis of industrial control system devices. In Proceedings of the 2017 IEEE 15th International Conference on Industrial Informatics (INDIN), Emden, Germany, 24–26 July 2017; pp. 399–404. [Google Scholar]
- Giraldo, J.; Urbina, D.; Cardenas, A.; Valente, J.; Faisal, M.; Ruths, J.; Tippenhauer, N.O.; Sandberg, H.; Candell, R. A survey of physics-based attack detection in cyber-physical systems. ACM Comput. Surv. (CSUR) 2018, 51, 1–36. [Google Scholar] [CrossRef]
- Pimentel, M.A.; Clifton, D.A.; Clifton, L.; Tarassenko, L. A review of novelty detection. Signal Process. 2014, 99, 215–249. [Google Scholar] [CrossRef]
- Shi, D.; Lin, P.; Wang, Y.; Chu, C.C.; Xu, Y.; Wang, P. Deception Attack Detection of Isolated DC Microgrids under Consensus-Based Distributed Voltage Control Architecture. IEEE J. Emerg. Sel. Top. Circ. Syst. 2021, 11, 155–167. [Google Scholar] [CrossRef]
- Chavez, A.; Lai, C.; Jacobs, N.; Hossain-McKenzie, S.; Jones, C.B.; Johnson, J.; Summers, A. Hybrid Intrusion Detection System Design for Distributed Energy Resource Systems. In Proceedings of the 2019 IEEE CyberPELS (CyberPELS), Knoxville, TN, USA, 29 April–1 May 2019; pp. 1–6. [Google Scholar]
- Kosek, A.M. Contextual anomaly detection for cyber-physical security in smart grids based on an artificial neural network model. In Proceedings of the 2016 Joint Workshop on Cyber-Physical Security and Resilience in Smart Grids (CPSR-SG), Vienna, Austria, 12 April 2016; pp. 1–6. [Google Scholar]
- Li, F.; Xie, R.; Yang, B.; Guo, L.; Ma, P.; Shi, J.; Ye, J.; Song, W. Detection and identification of cyber and physical attacks on distribution power grids with pvs: An online high-dimensional data-driven approach. IEEE J. Emerg. Sel. Top. Power Electron. 2019. [Google Scholar] [CrossRef] [Green Version]
- Shilay, D.M.; Lorey, K.G.; Weiz, T.; Lovetty, T.; Cheng, Y. Catching Anomalous Distributed Photovoltaics: An Edge-based Multi-modal Anomaly Detection. arXiv 2017, arXiv:1709.08830. [Google Scholar]
- Gaggero, G.B.; Rossi, M.; Girdinio, P.; Marchese, M. Detecting System Fault/Cyberattack within a Photovoltaic System Connected to the Grid: A Neural Network-Based Solution. J. Sens. Actuator Netw. 2020, 9, 20. [Google Scholar] [CrossRef] [Green Version]
- Fotiadou, K.; Velivassaki, T.H.; Voulkidis, A.; Skias, D.; De Santis, C.; Zahariadis, T. Proactive Critical Energy Infrastructure Protection via Deep Feature Learning. Energies 2020, 13, 2622. [Google Scholar] [CrossRef]
- Zhou, Q.; Shahidehpour, M.; Alabdulwahab, A.; Abusorrah, A. A cyber-attack resilient distributed control strategy in islanded microgrids. IEEE Trans. Smart Grid 2020, 11, 3690–3701. [Google Scholar] [CrossRef]
- Deng, C.; Wang, Y.; Wen, C.; Xu, Y.; Lin, P. Distributed resilient control for energy storage systems in cyber—Physical microgrids. IEEE Trans. Ind. Inform. 2020, 17, 1331–1341. [Google Scholar] [CrossRef]
- Rath, S.; Pal, D.; Sharma, P.S.; Panigrahi, B.K. A Cyber-Secure Distributed Control Architecture for Autonomous AC Microgrid. IEEE Syst. J. 2020. [Google Scholar] [CrossRef]
- Liu, Y.; Ning, P.; Reiter, M.K. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. (TISSEC) 2011, 14, 1–33. [Google Scholar] [CrossRef]
- Hussain, A.; Heidemann, J.; Papadopoulos, C. A framework for classifying denial of service attacks. In Proceedings of the 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Karlsruhe, Germany, 25–29 August 2003; pp. 99–110. [Google Scholar]
- Hosseinzadeh, M.; Sinopoli, B.; Garone, E. Feasibility and detection of replay attack in networked constrained cyber-physical systems. In Proceedings of the 57th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 24–27 September 2019; pp. 712–717. [Google Scholar]
- Zhou, Q.; Shahidehpour, M.; Alabdulwahab, A.; Abusorrah, A.; Che, L.; Liu, X. Cross-Layer Distributed Control Strategy for Cyber Resilient Microgrids. IEEE Trans. Smart Grid 2021. [Google Scholar] [CrossRef]
- Liu, Y.; Li, Y.; Wang, Y.; Zhang, X.; Gooi, H.B.; Xin, H. Robust and Resilient Distributed Optimal Frequency Control for Microgrids Against Cyber Attacks. IEEE Trans. Ind. Inform. 2021. [Google Scholar] [CrossRef]
| Section | Description |
|---|---|
| Part 1 | Introduction to security issue |
| Part 2 | Glossary of terms |
| Part 3 | Profiles including TCP/IP |
| Part 4 | Profiles including MMS and derivatives |
| Part 5 | Security for IEC 60870-5 and derivatives |
| Part 6 | Security for IEC 61850 |
| Part 7 | Network and system management (NSM) data object models |
| Part 8 | Role-based access control for power system management |
| Part 9 | Cyber security key management for power system equipment |
| Part 10 | Security architecture guidelines |
| Part 11 | Security for eXtensible markup language (XML) documents |
| Part 12 | Resilience and security recommendations for power systems with DER cyber-physical systems |
| Part 13 | Guidelines on security topics to be covered in standards and specifications |
| Part 90-1 | Guidelines for handling role-based access control in power systems |
| Part 90-2 | Deep packet inspection of encrypted communications |
| Part 90-3 | Guidelines for network and system management |
| Part 100-1 | Conformance test cases for IEC TS 62351-5 and IEC TS 60870-5-7 |
| Part 100-3 | Conformance test cases for the IEC 62351-3, the secure communication extension for profiles including TCP/IP |
| IDS Classification | ||
|---|---|---|
| By monitored element | Network-IDS | Host-IDS |
| By actions | Passive (IDS) | Active (IDS and IPS) |
| By detection methods | Signature-based | Anomaly-based |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gaggero, G.B.; Girdinio, P.; Marchese, M. Advancements and Research Trends in Microgrids Cybersecurity. Appl. Sci. 2021, 11, 7363. https://doi.org/10.3390/app11167363
Gaggero GB, Girdinio P, Marchese M. Advancements and Research Trends in Microgrids Cybersecurity. Applied Sciences. 2021; 11(16):7363. https://doi.org/10.3390/app11167363
Chicago/Turabian StyleGaggero, Giovanni Battista, Paola Girdinio, and Mario Marchese. 2021. "Advancements and Research Trends in Microgrids Cybersecurity" Applied Sciences 11, no. 16: 7363. https://doi.org/10.3390/app11167363
APA StyleGaggero, G. B., Girdinio, P., & Marchese, M. (2021). Advancements and Research Trends in Microgrids Cybersecurity. Applied Sciences, 11(16), 7363. https://doi.org/10.3390/app11167363








